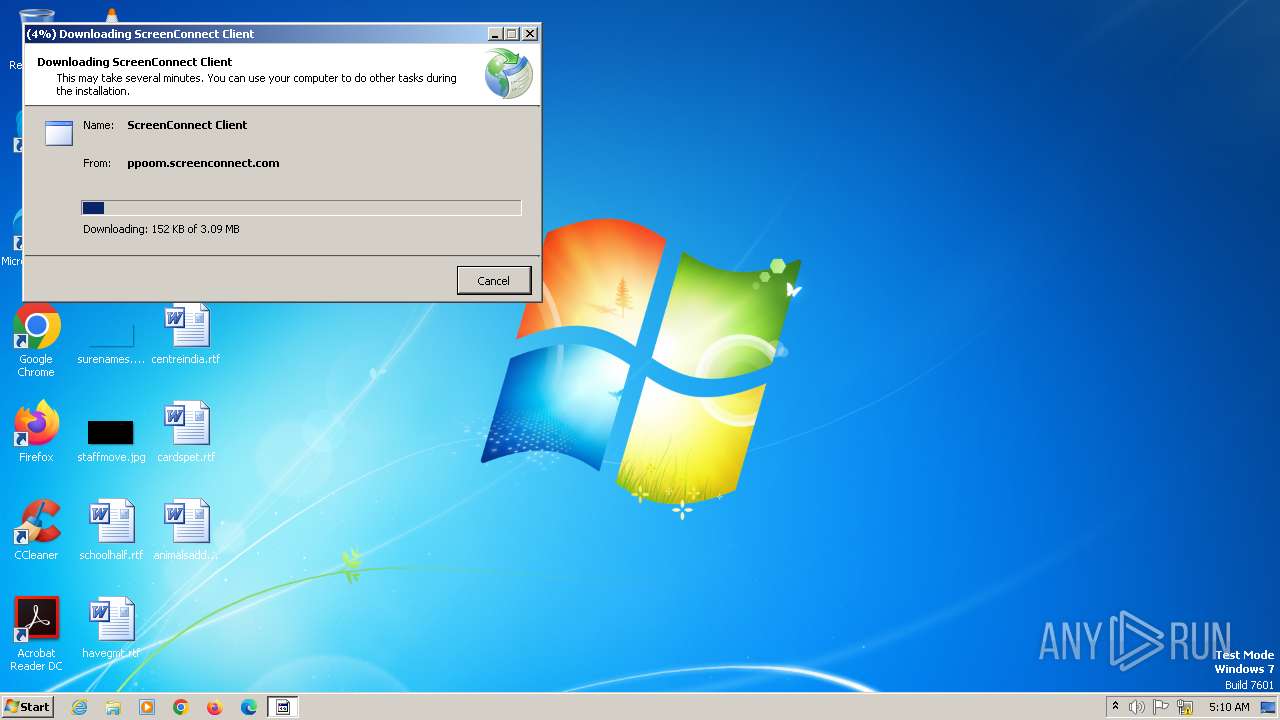
| File name: | ScreenConnect.Client.exe |
| Full analysis: | https://app.any.run/tasks/1b268998-0afa-4ce7-980a-3e12b42ad40a |
| Verdict: | Malicious activity |
| Analysis date: | November 20, 2023, 05:10:28 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | D44830359674C8FA9087A1DDD6DF2073 |
| SHA1: | BE3E2A249341B9F41889E6E3615D05DDF6A28D25 |
| SHA256: | A419FBF91823E03369DE6114AADF03D894241343A414D10E448AE69F472BC053 |
| SSDEEP: | 3072:MjLHcVw8licpWQog5Ms+f+l6xPVfqRsA1:MfoocptD5QPVfqX1 |
MALICIOUS
Connects to the CnC server
- ScreenConnect.ClientService.exe (PID: 2476)
SCREENCONNECT has been detected (SURICATA)
- ScreenConnect.ClientService.exe (PID: 2476)
Creates a writable file the system directory
- ScreenConnect.WindowsClient.exe (PID: 1788)
Drops the executable file immediately after the start
- dfsvc.exe (PID: 572)
SUSPICIOUS
Reads the Internet Settings
- dfsvc.exe (PID: 572)
- ScreenConnect.ClientService.exe (PID: 1556)
- ScreenConnect.WindowsClient.exe (PID: 2204)
- ScreenConnect.WindowsClient.exe (PID: 2120)
Reads settings of System Certificates
- dfsvc.exe (PID: 572)
Checks Windows Trust Settings
- dfsvc.exe (PID: 572)
Reads Internet Explorer settings
- dfsvc.exe (PID: 572)
The process creates files with name similar to system file names
- dfsvc.exe (PID: 572)
Executes as Windows Service
- ScreenConnect.ClientService.exe (PID: 2476)
Creates or modifies Windows services
- ScreenConnect.ClientService.exe (PID: 2476)
INFO
Checks supported languages
- dfsvc.exe (PID: 572)
- ScreenConnect.Client.exe (PID: 2944)
- ScreenConnect.ClientService.exe (PID: 1556)
- ScreenConnect.ClientService.exe (PID: 2476)
- ScreenConnect.WindowsClient.exe (PID: 2120)
- ScreenConnect.WindowsClient.exe (PID: 1788)
- ScreenConnect.WindowsClient.exe (PID: 2204)
Reads the computer name
- dfsvc.exe (PID: 572)
- ScreenConnect.Client.exe (PID: 2944)
- ScreenConnect.ClientService.exe (PID: 1556)
- ScreenConnect.ClientService.exe (PID: 2476)
- ScreenConnect.WindowsClient.exe (PID: 2120)
- ScreenConnect.WindowsClient.exe (PID: 1788)
- ScreenConnect.WindowsClient.exe (PID: 2204)
Reads the machine GUID from the registry
- ScreenConnect.Client.exe (PID: 2944)
- dfsvc.exe (PID: 572)
- ScreenConnect.ClientService.exe (PID: 1556)
- ScreenConnect.ClientService.exe (PID: 2476)
- ScreenConnect.WindowsClient.exe (PID: 2120)
- ScreenConnect.WindowsClient.exe (PID: 1788)
- ScreenConnect.WindowsClient.exe (PID: 2204)
Creates files or folders in the user directory
- dfsvc.exe (PID: 572)
- ScreenConnect.WindowsClient.exe (PID: 2204)
- ScreenConnect.ClientService.exe (PID: 2476)
Reads Environment values
- dfsvc.exe (PID: 572)
Checks proxy server information
- dfsvc.exe (PID: 572)
Create files in a temporary directory
- dfsvc.exe (PID: 572)
Process checks are UAC notifies on
- dfsvc.exe (PID: 572)
Reads CPU info
- ScreenConnect.WindowsClient.exe (PID: 1788)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2022:11:18 20:55:37+01:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.33 |
| CodeSize: | 40448 |
| InitializedDataSize: | 32768 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x14ba |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
41
Monitored processes
7
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 572 | "C:\Windows\Microsoft.NET\Framework64\v4.0.30319\dfsvc.exe" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\dfsvc.exe | ScreenConnect.Client.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: ClickOnce Exit code: 0 Version: 4.7.2558.0 built by: NET471REL1 Modules
| |||||||||||||||
| 1556 | "C:\Users\admin\AppData\Local\Apps\2.0\OJGQ8A5E.CEO\KCZTCVLY.DMB\scre..tion_25b0fbb6ef7eb094_0017.0008_71c7df92685f2786\ScreenConnect.ClientService.exe" "?e=Support&y=Guest&h=instance-hxd7fl-relay.screenconnect.com&p=443&s=e8d3fac8-f4f2-4f91-83b0-a8027fdc9827&k=BgIAAACkAABSU0ExAAgAAAEAAQBJocOfX%2bz4thKH88FcRtmzq0yDajutuI0jrZQAIvWr0TG84%2byzfMKLKUa67%2bZy1gwdapj%2bL2gOiLUcmAReVnp1tuz7jzfoMZhTTbHMIKGPkcxXdWyJvgZCMiCVVu8HG%2bnguZY27oo37JcZxSUw8qcOAiFklv3mtemStNZzccjH75%2bAcE3zy0XK%2fWVPACw10EYZgsIaJWsP1LreyXUiW02ZYOFZLzlJ7Tmm4JLJmFZLqwMdB1ojJjIuBlwOnsfLd%2f8WHwGcsBVrBvKRxVfEpB9SM3BjrNFX%2f2wocEq7E81QiR7KW5rOCJB%2fNwzc7bCk5U2FiO%2bRO%2fVyP3wIJQbjT1%2bw&r=&i=Untitled%20Session" "1" | C:\Users\admin\AppData\Local\Apps\2.0\OJGQ8A5E.CEO\KCZTCVLY.DMB\scre..tion_25b0fbb6ef7eb094_0017.0008_71c7df92685f2786\ScreenConnect.ClientService.exe | ScreenConnect.WindowsClient.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 23.8.5.8707 Modules
| |||||||||||||||
| 1788 | "C:\Users\admin\AppData\Local\Apps\2.0\OJGQ8A5E.CEO\KCZTCVLY.DMB\scre..tion_25b0fbb6ef7eb094_0017.0008_71c7df92685f2786\ScreenConnect.WindowsClient.exe" "RunRole" "eea7ae19-d25b-4563-86b1-fa377aa7acee" "System" | C:\Users\admin\AppData\Local\Apps\2.0\OJGQ8A5E.CEO\KCZTCVLY.DMB\scre..tion_25b0fbb6ef7eb094_0017.0008_71c7df92685f2786\ScreenConnect.WindowsClient.exe | — | ScreenConnect.ClientService.exe | |||||||||||
User: SYSTEM Company: ScreenConnect Software Integrity Level: SYSTEM Description: ScreenConnect Client Exit code: 0 Version: 23.8.5.8707 Modules
| |||||||||||||||
| 2120 | "C:\Users\admin\AppData\Local\Apps\2.0\OJGQ8A5E.CEO\KCZTCVLY.DMB\scre..tion_25b0fbb6ef7eb094_0017.0008_71c7df92685f2786\ScreenConnect.WindowsClient.exe" "RunRole" "5b7667fe-20a5-4f61-bc15-dabe8579dad8" "User" | C:\Users\admin\AppData\Local\Apps\2.0\OJGQ8A5E.CEO\KCZTCVLY.DMB\scre..tion_25b0fbb6ef7eb094_0017.0008_71c7df92685f2786\ScreenConnect.WindowsClient.exe | — | ScreenConnect.ClientService.exe | |||||||||||
User: admin Company: ScreenConnect Software Integrity Level: MEDIUM Description: ScreenConnect Client Exit code: 0 Version: 23.8.5.8707 Modules
| |||||||||||||||
| 2204 | "C:\Users\admin\AppData\Local\Apps\2.0\OJGQ8A5E.CEO\KCZTCVLY.DMB\scre..tion_25b0fbb6ef7eb094_0017.0008_71c7df92685f2786\ScreenConnect.WindowsClient.exe" | C:\Users\admin\AppData\Local\Apps\2.0\OJGQ8A5E.CEO\KCZTCVLY.DMB\scre..tion_25b0fbb6ef7eb094_0017.0008_71c7df92685f2786\ScreenConnect.WindowsClient.exe | — | dfsvc.exe | |||||||||||
User: admin Company: ScreenConnect Software Integrity Level: MEDIUM Description: ScreenConnect Client Exit code: 0 Version: 23.8.5.8707 Modules
| |||||||||||||||
| 2476 | "C:\Users\admin\AppData\Local\Apps\2.0\OJGQ8A5E.CEO\KCZTCVLY.DMB\scre..tion_25b0fbb6ef7eb094_0017.0008_71c7df92685f2786\ScreenConnect.ClientService.exe" "?e=Support&y=Guest&h=instance-hxd7fl-relay.screenconnect.com&p=443&s=e8d3fac8-f4f2-4f91-83b0-a8027fdc9827&k=BgIAAACkAABSU0ExAAgAAAEAAQBJocOfX%2bz4thKH88FcRtmzq0yDajutuI0jrZQAIvWr0TG84%2byzfMKLKUa67%2bZy1gwdapj%2bL2gOiLUcmAReVnp1tuz7jzfoMZhTTbHMIKGPkcxXdWyJvgZCMiCVVu8HG%2bnguZY27oo37JcZxSUw8qcOAiFklv3mtemStNZzccjH75%2bAcE3zy0XK%2fWVPACw10EYZgsIaJWsP1LreyXUiW02ZYOFZLzlJ7Tmm4JLJmFZLqwMdB1ojJjIuBlwOnsfLd%2f8WHwGcsBVrBvKRxVfEpB9SM3BjrNFX%2f2wocEq7E81QiR7KW5rOCJB%2fNwzc7bCk5U2FiO%2bRO%2fVyP3wIJQbjT1%2bw&r=&i=Untitled%20Session" "1" | C:\Users\admin\AppData\Local\Apps\2.0\OJGQ8A5E.CEO\KCZTCVLY.DMB\scre..tion_25b0fbb6ef7eb094_0017.0008_71c7df92685f2786\ScreenConnect.ClientService.exe | services.exe | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Exit code: 0 Version: 23.8.5.8707 Modules
| |||||||||||||||
| 2944 | "C:\Users\admin\Downloads\ScreenConnect.Client.exe" | C:\Users\admin\Downloads\ScreenConnect.Client.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
4 331
Read events
4 238
Write events
69
Delete events
24
Modification events
| (PID) Process: | (2944) ScreenConnect.Client.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\156\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (572) dfsvc.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (572) dfsvc.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (572) dfsvc.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (572) dfsvc.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (572) dfsvc.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (572) dfsvc.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000C1000000010000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (572) dfsvc.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (572) dfsvc.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (572) dfsvc.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\156\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
14
Suspicious files
18
Text files
22
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 572 | dfsvc.exe | C:\Users\admin\AppData\Local\Temp\Deployment\26L4JEWQ.TOJ\QGBTT1VW.PP4.application | xml | |
MD5:91CDA0F600C8490A526496E5280517CD | SHA256:74D8A6062A729074AA84A1A749F548913DC76C76BC9422641CC1FCE68659556B | |||
| 572 | dfsvc.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\F2E248BEDDBB2D85122423C41028BFD4 | binary | |
MD5:37F461BDCF4251A8B700685F647ECDC5 | SHA256:11C05D2C9B13E762E93DA1EDFBC4DEEDB72E40D7A18AFF35DF2E70A22FBAABC4 | |||
| 572 | dfsvc.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\C56C4404C4DEF0DC88E5FCD9F09CB2F1 | binary | |
MD5:D91299E84355CD8D5A86795A0118B6E9 | SHA256:46011EDE1C147EB2BC731A539B7C047B7EE93E48B9D3C3BA710CE132BBDFAC6B | |||
| 572 | dfsvc.exe | C:\Users\admin\AppData\Local\Temp\CabB442.tmp | compressed | |
MD5:F3441B8572AAE8801C04F3060B550443 | SHA256:6720349E7D82EE0A8E73920D3C2B7CB2912D9FCF2EDB6FD98F2F12820158B0BF | |||
| 572 | dfsvc.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\F2E248BEDDBB2D85122423C41028BFD4 | binary | |
MD5:78F2FCAA601F2FB4EBC937BA532E7549 | SHA256:552F7BDCF1A7AF9E6CE672017F4F12ABF77240C78E761AC203D1D9D20AC89988 | |||
| 572 | dfsvc.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:F3441B8572AAE8801C04F3060B550443 | SHA256:6720349E7D82EE0A8E73920D3C2B7CB2912D9FCF2EDB6FD98F2F12820158B0BF | |||
| 572 | dfsvc.exe | C:\Users\admin\AppData\Roaming\Microsoft\Crypto\RSA\S-1-5-21-3896776584-4254864009-862391680-1000\932a2db58c237abd381d22df4c63a04a_eeeb5d54-7880-42a7-b542-739bbc26cf4b | binary | |
MD5:D2DED43CE07BFCE4D1C101DFCAA178C8 | SHA256:8EEE9284E733B9D4F2E5C43F71B81E27966F5CD8900183EB3BB77A1F1160D050 | |||
| 572 | dfsvc.exe | C:\Users\admin\AppData\Local\Temp\Deployment\N11DYNBH.7HQ\4G4AY8YO.0PM\ScreenConnect.WindowsClient.exe | executable | |
MD5:19E093BC974D1ED6399F50B7FA3BE1F8 | SHA256:EA38CFF329692F6B4C8ADE15970B742A9A8BB62A44F59227C510CB2882FA436F | |||
| 572 | dfsvc.exe | C:\Users\admin\AppData\Local\Temp\Deployment\N11DYNBH.7HQ\4G4AY8YO.0PM\ScreenConnect.Windows.dll | executable | |
MD5:44B736A074B7E0BBE0C6C5F7DEBE0F3D | SHA256:F8C648E09FB42F145B581ED80B2A0C88E9F18041EFD03AD3187A6229F17A14B8 | |||
| 572 | dfsvc.exe | C:\Users\admin\AppData\Local\Temp\Deployment\N11DYNBH.7HQ\4G4AY8YO.0PM\ScreenConnect.WindowsClient.exe.config | xml | |
MD5:728175E20FFBCEB46760BB5E1112F38B | SHA256:87C640D3184C17D3B446A72D5F13D643A774B4ECC7AFBEDFD4E8DA7795EA8077 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
9
DNS requests
4
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
572 | dfsvc.exe | GET | 200 | 87.248.205.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?da11ba0e816cf75c | unknown | compressed | 61.6 Kb | unknown |
572 | dfsvc.exe | GET | 200 | 192.229.221.95:80 | http://cacerts.digicert.com/DigiCertTrustedG4CodeSigningRSA4096SHA3842021CA1.crt | unknown | binary | 1.68 Kb | unknown |
572 | dfsvc.exe | GET | 200 | 192.229.221.95:80 | http://cacerts.digicert.com/DigiCertTrustedRootG4.crt | unknown | der | 1.39 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1956 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
572 | dfsvc.exe | 147.75.81.6:443 | ppoom.screenconnect.com | PACKET | NL | unknown |
324 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
572 | dfsvc.exe | 192.229.221.95:80 | cacerts.digicert.com | EDGECAST | US | whitelisted |
572 | dfsvc.exe | 87.248.205.0:80 | ctldl.windowsupdate.com | LLNW | US | unknown |
2476 | ScreenConnect.ClientService.exe | 147.75.81.4:443 | instance-hxd7fl-relay.screenconnect.com | PACKET | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ppoom.screenconnect.com |
| unknown |
cacerts.digicert.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
instance-hxd7fl-relay.screenconnect.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2476 | ScreenConnect.ClientService.exe | Misc activity | ET INFO ScreenConnect/ConnectWise Initial Checkin Packet M2 |
2476 | ScreenConnect.ClientService.exe | Potential Corporate Privacy Violation | REMOTE [ANY.RUN] ScreenConnect Server Response |
2 ETPRO signatures available at the full report
Process | Message |
|---|---|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\amd64fre\base\isolation\hier_hierarchy.cpp, line 230
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\amd64fre\base\isolation\hier_hierarchy.cpp, line 230
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\amd64fre\base\isolation\hier_hierarchy.cpp, line 230
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\amd64fre\base\isolation\hier_hierarchy.cpp, line 230
|
dfsvc.exe |
*** Status Originated: -1073741772
*** Source File: d:\iso_whid\amd64fre\base\isolation\win32\isoreg_direct.cpp, line 1127
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\amd64fre\base\isolation\hier_hierarchy.cpp, line 230
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\amd64fre\base\isolation\hier_hierarchy.cpp, line 230
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\amd64fre\base\isolation\hier_hierarchy.cpp, line 230
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\amd64fre\base\isolation\hier_hierarchy.cpp, line 230
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\amd64fre\base\isolation\hier_hierarchy.cpp, line 230
|