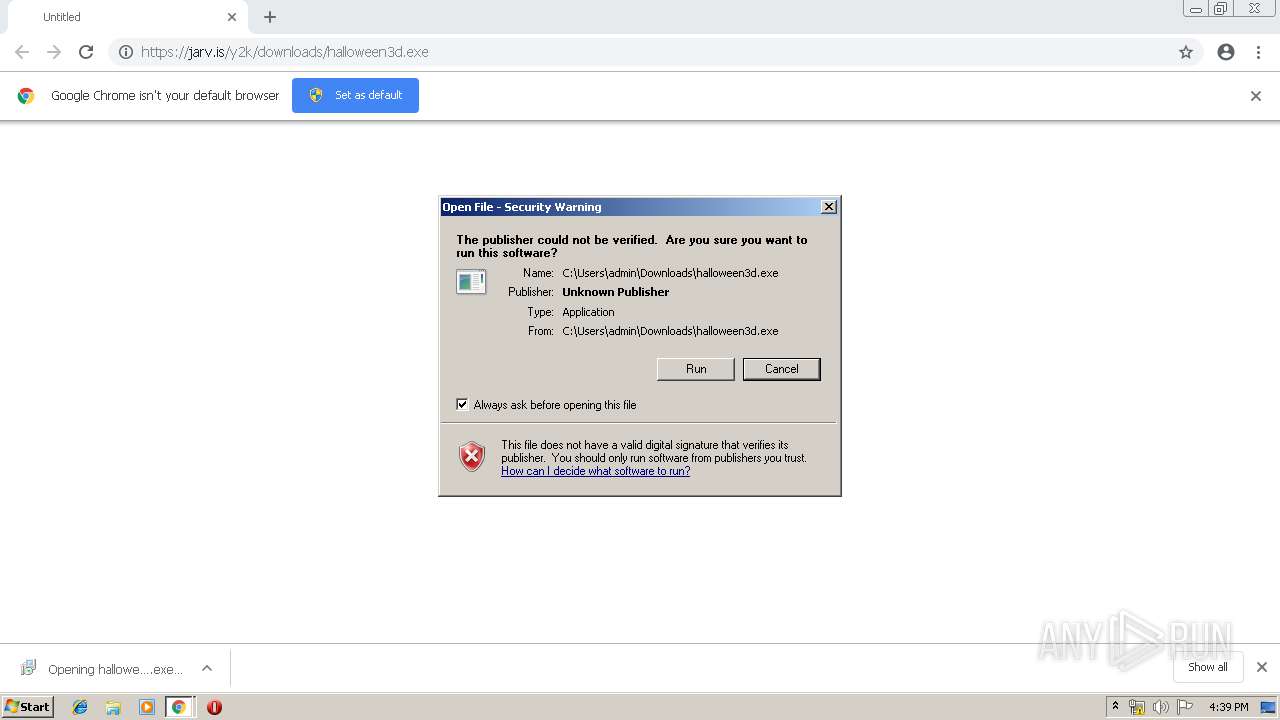
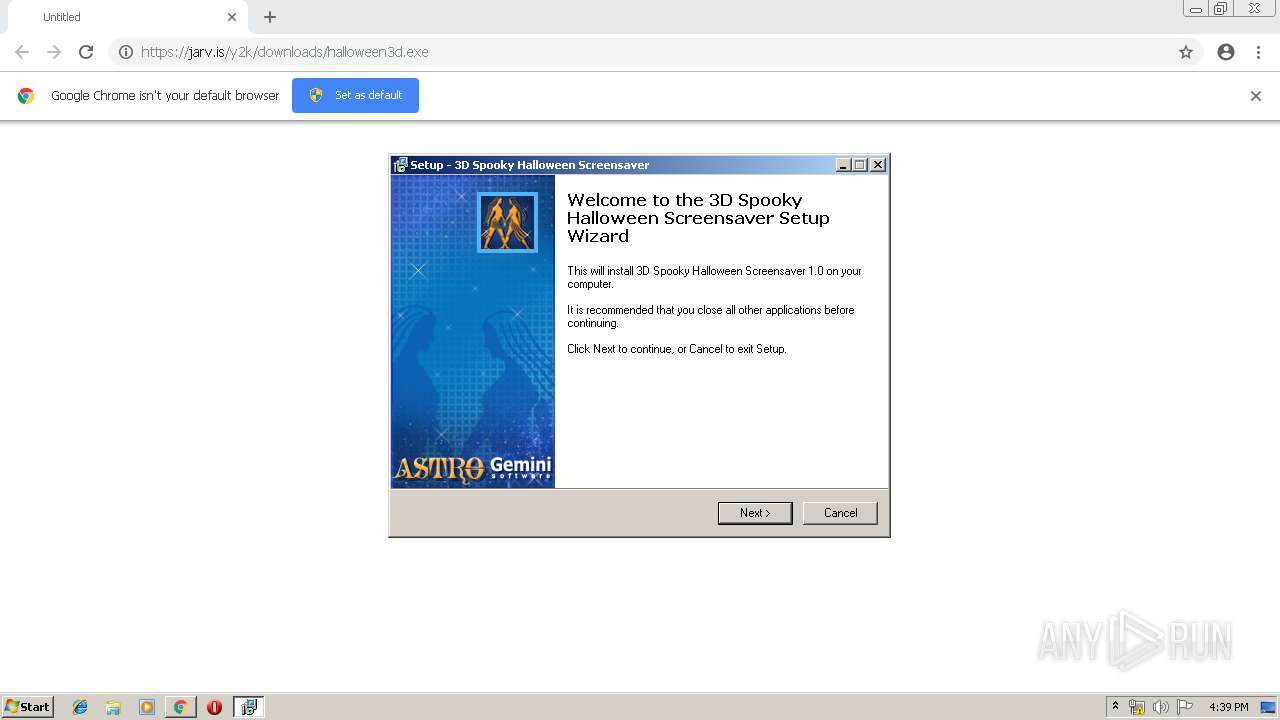
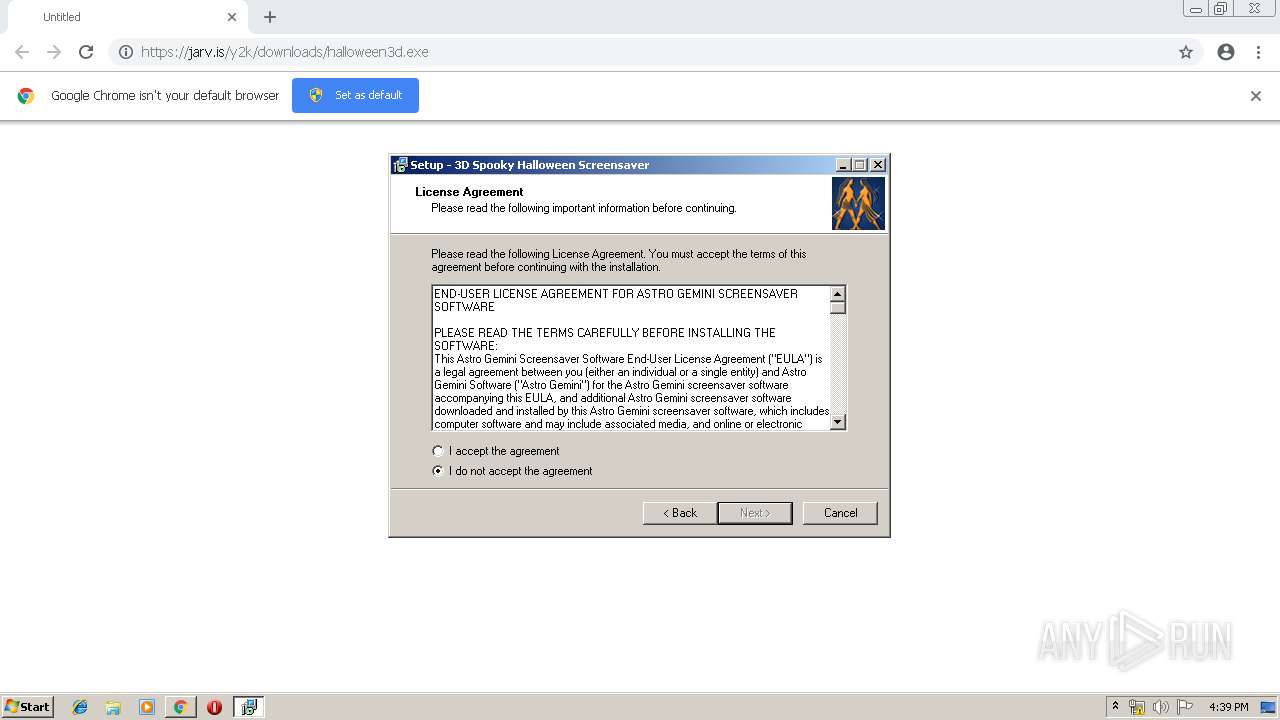
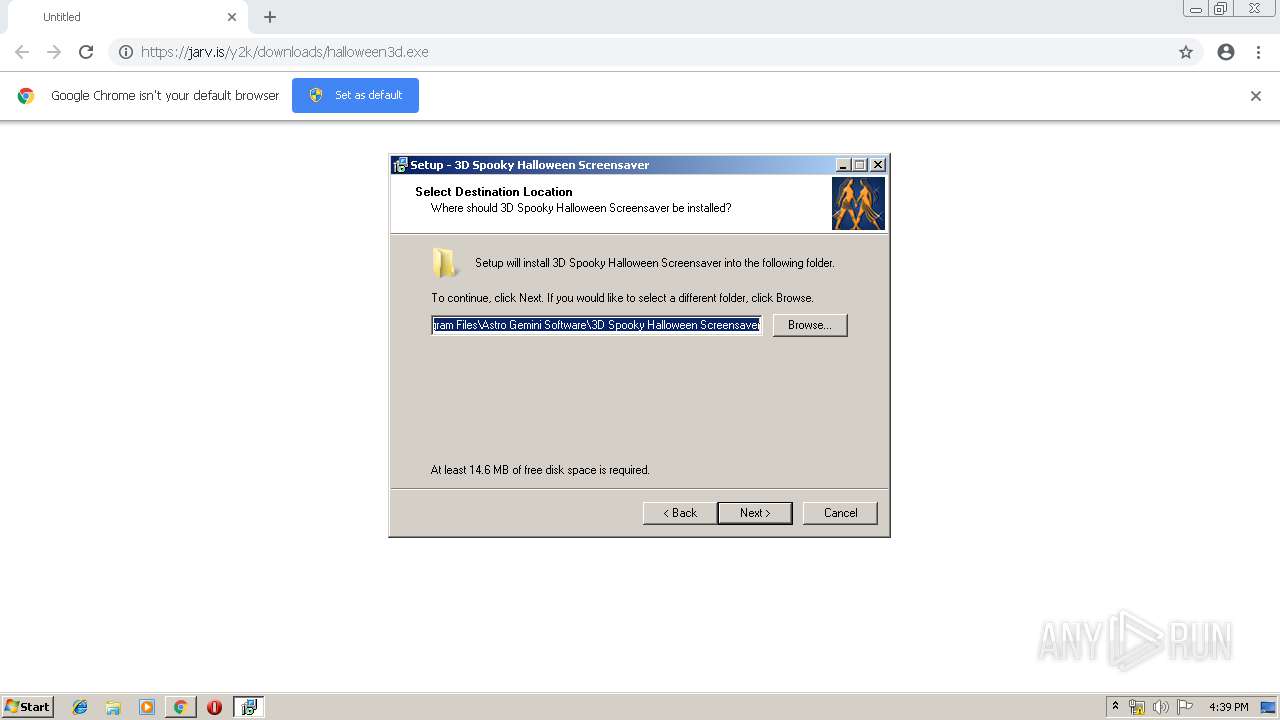
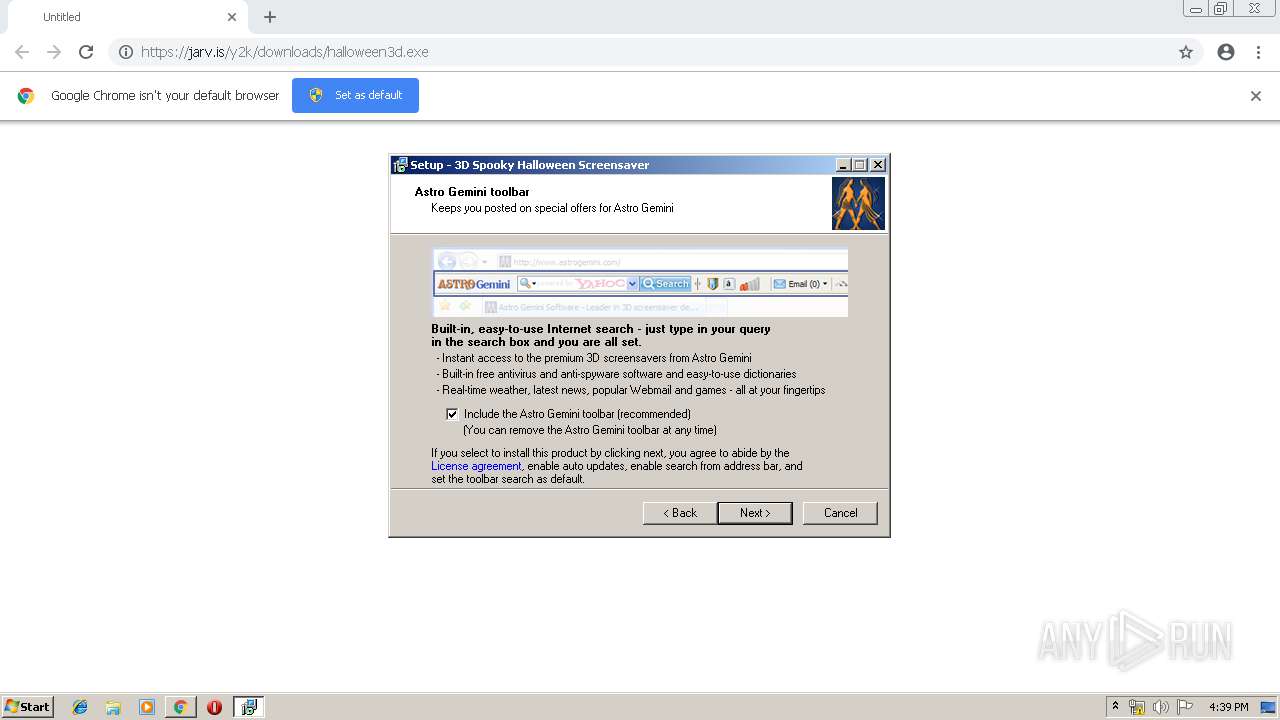
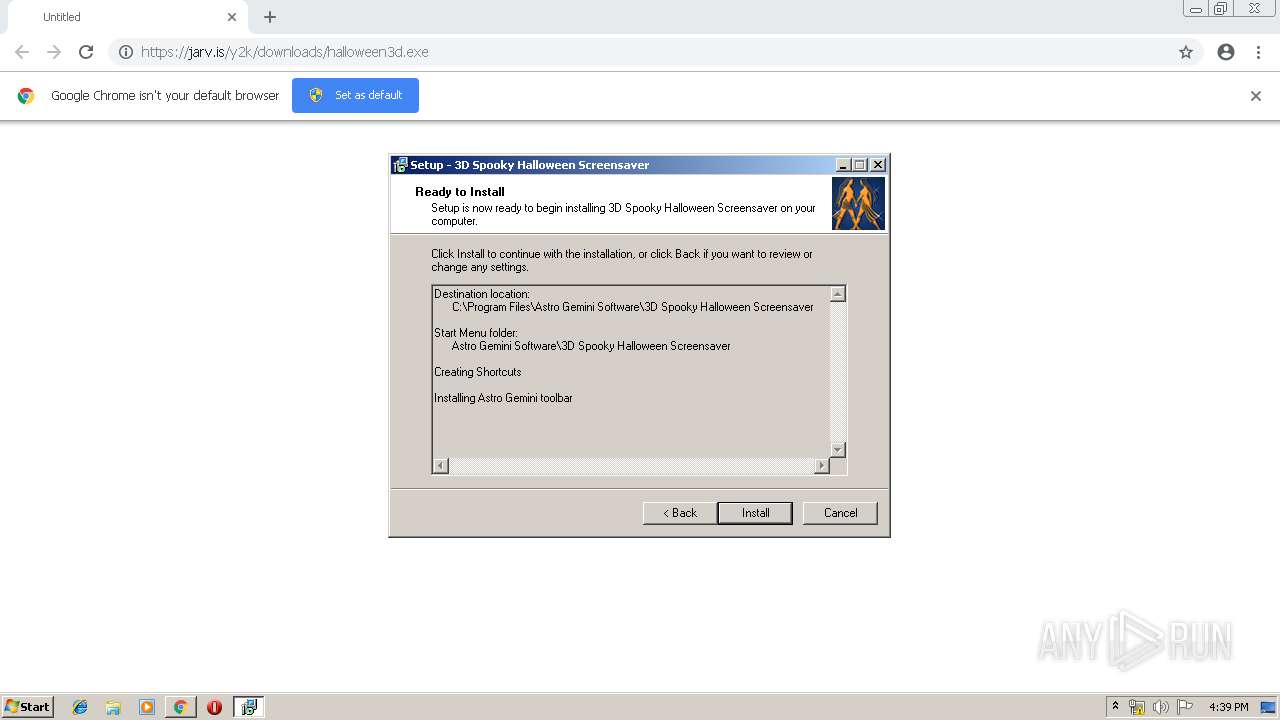
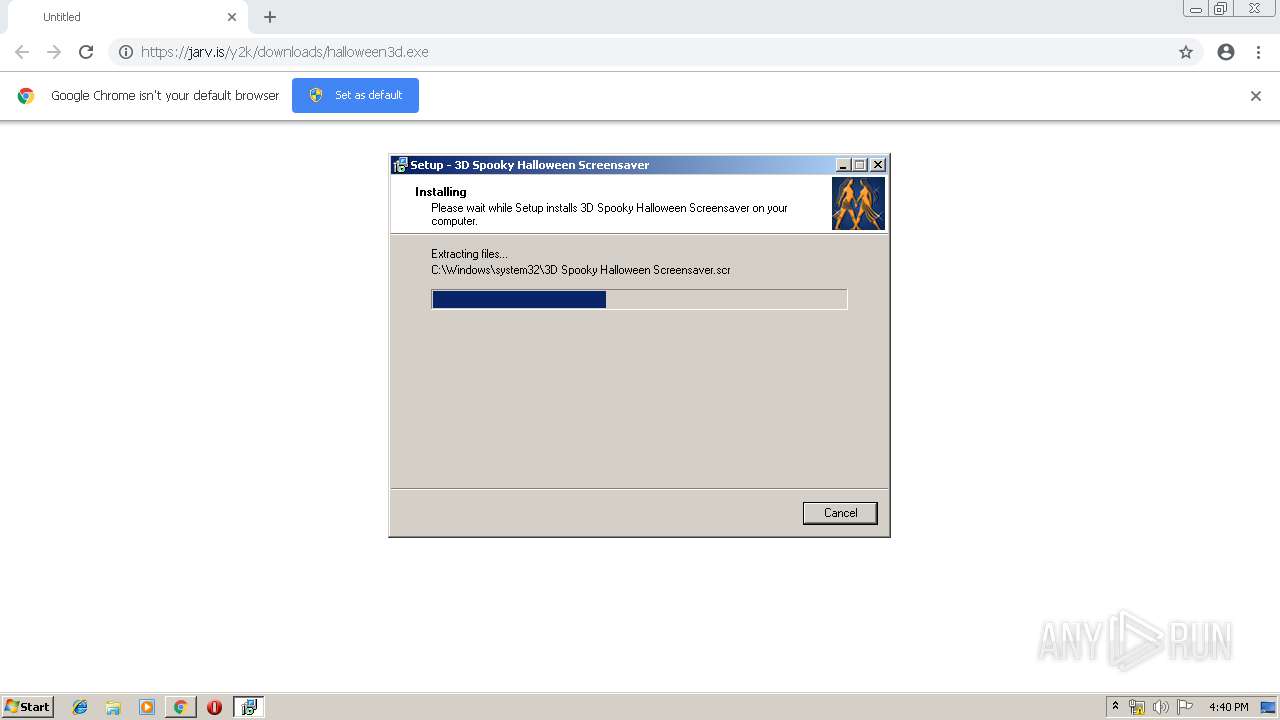
| URL: | https://jarv.is/y2k/downloads/halloween3d.exe |
| Full analysis: | https://app.any.run/tasks/e194e63a-d28c-480e-90c5-771f3647530d |
| Verdict: | Malicious activity |
| Analysis date: | May 24, 2019, 15:39:02 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | F5C23EEDFA843A4CF1D5B1A02ED82A29 |
| SHA1: | 6FEC5C7C179854AC2D156818D2EE49EC32CCC075 |
| SHA256: | A419D510CECA01B06A938B4B5A3A9DD13C3075AF5504A92C7489C273CD30B175 |
| SSDEEP: | 3:N8k3eS94KWHKSAAi9N:28eSVWHKzAi9N |
MALICIOUS
Application was dropped or rewritten from another process
- halloween3d.exe (PID: 996)
- halloween3d.exe (PID: 2420)
- Manager.exe (PID: 3596)
- Astro Gemini Screensaver Manager.exe (PID: 988)
- CA_VMN_anti-spywareSetup.exe (PID: 2164)
- 3D Spooky Halloween Screensaver.scr (PID: 2916)
- vmnlite_gemv2.exe (PID: 3912)
Loads dropped or rewritten executable
- CA_VMN_anti-spywareSetup.exe (PID: 2164)
Changes settings of System certificates
- 3D Spooky Halloween Screensaver.scr (PID: 2916)
SUSPICIOUS
Executable content was dropped or overwritten
- chrome.exe (PID: 3676)
- halloween3d.exe (PID: 996)
- halloween3d.exe (PID: 2420)
- halloween3d.tmp (PID: 2904)
- ags-manager-2.0.exe (PID: 896)
- ags-manager-2.0.tmp (PID: 2576)
- Astro_Gemini.exe (PID: 1492)
- CA_VMN_anti-spywareSetup.exe (PID: 2164)
- vmnlite_gemv2.exe (PID: 3912)
Creates files in the Windows directory
- halloween3d.tmp (PID: 2904)
- ags-manager-2.0.tmp (PID: 2576)
Creates files in the user directory
- halloween3d.tmp (PID: 2904)
- Manager.exe (PID: 3596)
- ags-manager-2.0.tmp (PID: 2576)
- Astro_Gemini.exe (PID: 1492)
- vmnlite_gemv2.exe (PID: 3912)
Starts Internet Explorer
- halloween3d.tmp (PID: 2904)
Creates COM task schedule object
- Astro_Gemini.exe (PID: 1492)
- CA_VMN_anti-spywareSetup.exe (PID: 2164)
Creates files in the program directory
- CA_VMN_anti-spywareSetup.exe (PID: 2164)
- vmnlite_gemv2.exe (PID: 3912)
Creates a software uninstall entry
- CA_VMN_anti-spywareSetup.exe (PID: 2164)
Reads internet explorer settings
- Manager.exe (PID: 3596)
Starts application with an unusual extension
- Manager.exe (PID: 3596)
Adds / modifies Windows certificates
- 3D Spooky Halloween Screensaver.scr (PID: 2916)
INFO
Application launched itself
- chrome.exe (PID: 3676)
- iexplore.exe (PID: 3824)
Reads Internet Cache Settings
- chrome.exe (PID: 3676)
- iexplore.exe (PID: 1704)
- iexplore.exe (PID: 3824)
Creates files in the user directory
- chrome.exe (PID: 3676)
- iexplore.exe (PID: 1704)
Application was dropped or rewritten from another process
- halloween3d.tmp (PID: 236)
- halloween3d.tmp (PID: 2904)
- ags-manager-2.0.exe (PID: 896)
- ags-manager-2.0.tmp (PID: 2576)
- Astro_Gemini.exe (PID: 1492)
Loads dropped or rewritten executable
- halloween3d.tmp (PID: 2904)
- ags-manager-2.0.tmp (PID: 2576)
- Astro_Gemini.exe (PID: 1492)
Creates files in the program directory
- halloween3d.tmp (PID: 2904)
- ags-manager-2.0.tmp (PID: 2576)
- Astro_Gemini.exe (PID: 1492)
Creates a software uninstall entry
- halloween3d.tmp (PID: 2904)
- ags-manager-2.0.tmp (PID: 2576)
- Astro_Gemini.exe (PID: 1492)
Changes internet zones settings
- iexplore.exe (PID: 3824)
Reads internet explorer settings
- iexplore.exe (PID: 1704)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
61
Monitored processes
24
Malicious processes
11
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 236 | "C:\Users\admin\AppData\Local\Temp\is-OLEMQ.tmp\halloween3d.tmp" /SL5="$301C4,12659577,53248,C:\Users\admin\Downloads\halloween3d.exe" | C:\Users\admin\AppData\Local\Temp\is-OLEMQ.tmp\halloween3d.tmp | — | halloween3d.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.49.0.0 Modules
| |||||||||||||||
| 792 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=964,8812356221339311642,6170884054344634227,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=5096725030556117724 --mojo-platform-channel-handle=2620 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 896 | "C:\Users\admin\AppData\Local\Temp\is-CGAS2.tmp\ags-manager-2.0.exe" /verysilent | C:\Users\admin\AppData\Local\Temp\is-CGAS2.tmp\ags-manager-2.0.exe | halloween3d.tmp | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: Astro Gemini Screensaver Manager Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 988 | "C:\Users\admin\AppData\Roaming\Astro Gemini Software\Screensaver Manager 2.0\Astro Gemini Screensaver Manager.exe" /i halloween-screensaver | C:\Users\admin\AppData\Roaming\Astro Gemini Software\Screensaver Manager 2.0\Astro Gemini Screensaver Manager.exe | — | halloween3d.tmp | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 996 | "C:\Users\admin\Downloads\halloween3d.exe" | C:\Users\admin\Downloads\halloween3d.exe | chrome.exe | ||||||||||||
User: admin Company: Integrity Level: MEDIUM Description: 3D Spooky Halloween Screensaver Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 1492 | "C:\Users\admin\AppData\Local\Temp\is-CGAS2.tmp\Astro_Gemini.exe" /S | C:\Users\admin\AppData\Local\Temp\is-CGAS2.tmp\Astro_Gemini.exe | halloween3d.tmp | ||||||||||||
User: admin Company: Visicom Media Inc. Integrity Level: HIGH Description: VMN Toolbar Exit code: 0 Version: 2.2.0.1 Modules
| |||||||||||||||
| 1704 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3824 CREDAT:79873 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2164 | C:\Users\admin\AppData\Local\Temp\CA_VMN_anti-spywareSetup.exe /S | C:\Users\admin\AppData\Local\Temp\CA_VMN_anti-spywareSetup.exe | Astro_Gemini.exe | ||||||||||||
User: admin Company: CA Integrity Level: HIGH Description: CA VMN Anti-Spyware 2.12 Exit code: 0 Version: 2.1.2.3 Modules
| |||||||||||||||
| 2420 | "C:\Users\admin\Downloads\halloween3d.exe" /SPAWNWND=$4017A /NOTIFYWND=$301C4 | C:\Users\admin\Downloads\halloween3d.exe | halloween3d.tmp | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: 3D Spooky Halloween Screensaver Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 2424 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=964,8812356221339311642,6170884054344634227,131072 --enable-features=PasswordImport --service-pipe-token=7173601207124317648 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=7173601207124317648 --renderer-client-id=5 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2044 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
Total events
3 994
Read events
3 059
Write events
817
Delete events
118
Modification events
| (PID) Process: | (3676) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3676) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3676) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (3676) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3148) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 3676-13203185961694000 |
Value: 259 | |||
| (PID) Process: | (3676) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3676) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3676) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (3676) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3488-13197474229333984 |
Value: 0 | |||
| (PID) Process: | (3676) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
Executable files
43
Suspicious files
25
Text files
827
Unknown types
16
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3676 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\index | — | |
MD5:— | SHA256:— | |||
| 3676 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_0 | — | |
MD5:— | SHA256:— | |||
| 3676 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_1 | — | |
MD5:— | SHA256:— | |||
| 3676 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_2 | — | |
MD5:— | SHA256:— | |||
| 3676 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_3 | — | |
MD5:— | SHA256:— | |||
| 3676 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\7a515d9d-8472-472c-a6e7-0985b8a74db3.tmp | — | |
MD5:— | SHA256:— | |||
| 3676 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000018.dbtmp | — | |
MD5:— | SHA256:— | |||
| 3676 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\GPUCache\index | — | |
MD5:— | SHA256:— | |||
| 3676 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\GPUCache\data_0 | — | |
MD5:— | SHA256:— | |||
| 3676 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\GPUCache\data_1 | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
130
TCP/UDP connections
19
DNS requests
13
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1704 | iexplore.exe | GET | 200 | 52.58.211.20:80 | http://www.astrogemini.com/img/left-button/specialty.gif | DE | image | 1.78 Kb | unknown |
1704 | iexplore.exe | GET | 200 | 52.58.211.20:80 | http://www.astrogemini.com/img/left-button/space.gif | DE | image | 1.76 Kb | unknown |
1704 | iexplore.exe | GET | 200 | 52.58.211.20:80 | http://www.astrogemini.com/img/legs-bottom1.gif | DE | image | 3.00 Kb | unknown |
1704 | iexplore.exe | GET | 200 | 52.58.211.20:80 | http://www.astrogemini.com/img/leftcoldownbg.gif | DE | image | 1.03 Kb | unknown |
1704 | iexplore.exe | GET | 200 | 52.58.211.20:80 | http://www.astrogemini.com/img/go!.gif | DE | image | 653 b | unknown |
1704 | iexplore.exe | GET | 200 | 52.58.211.20:80 | http://www.astrogemini.com/img/flag/en.gif | DE | image | 220 b | unknown |
1704 | iexplore.exe | GET | 200 | 52.58.211.20:80 | http://www.astrogemini.com/install.html?utm_medium=thnx&utm_campaign=install&utm_source=halloween-screensaver | DE | html | 6.62 Kb | unknown |
1704 | iexplore.exe | GET | 200 | 52.58.211.20:80 | http://www.astrogemini.com/js/JsHttpRequest.js | DE | html | 24.5 Kb | unknown |
1704 | iexplore.exe | GET | 200 | 52.58.211.20:80 | http://www.astrogemini.com/js/common.js | DE | text | 21.0 Kb | unknown |
1704 | iexplore.exe | GET | 200 | 52.58.211.20:80 | http://www.astrogemini.com/css/fixes/IEFixes.css | DE | text | 812 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3676 | chrome.exe | 104.31.66.47:443 | jarv.is | Cloudflare Inc | US | shared |
3676 | chrome.exe | 172.217.22.109:443 | accounts.google.com | Google Inc. | US | whitelisted |
3676 | chrome.exe | 172.217.18.4:443 | www.google.com | Google Inc. | US | whitelisted |
3676 | chrome.exe | 172.217.22.78:443 | sb-ssl.google.com | Google Inc. | US | whitelisted |
3676 | chrome.exe | 216.58.208.35:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
1704 | iexplore.exe | 52.58.211.20:80 | www.astrogemini.com | Amazon.com, Inc. | DE | unknown |
3824 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
1704 | iexplore.exe | 216.58.208.46:80 | www.google-analytics.com | Google Inc. | US | whitelisted |
3676 | chrome.exe | 172.217.22.35:443 | www.gstatic.com | Google Inc. | US | whitelisted |
3676 | chrome.exe | 216.58.207.67:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
jarv.is |
| unknown |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| malicious |
sb-ssl.google.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
www.astrogemini.com |
| unknown |
www.bing.com |
| whitelisted |
www.google-analytics.com |
| whitelisted |
search.vmn.net |
| malicious |
Threats
1 ETPRO signatures available at the full report