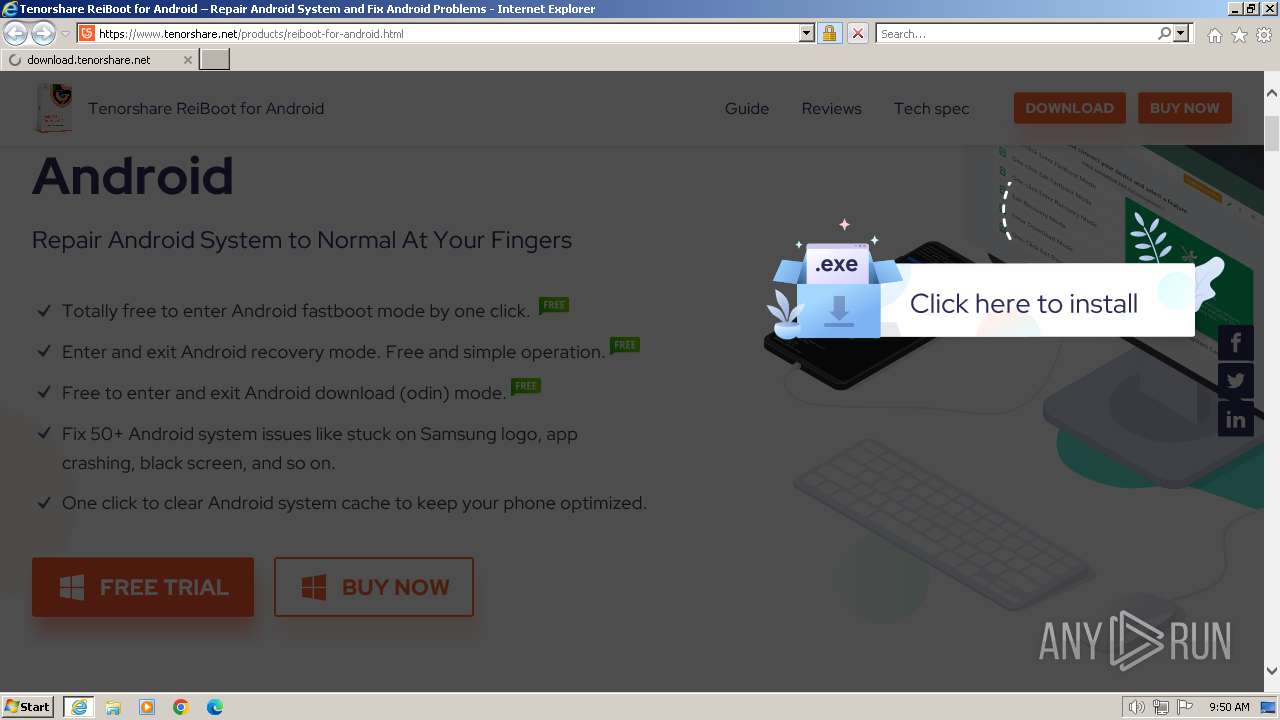
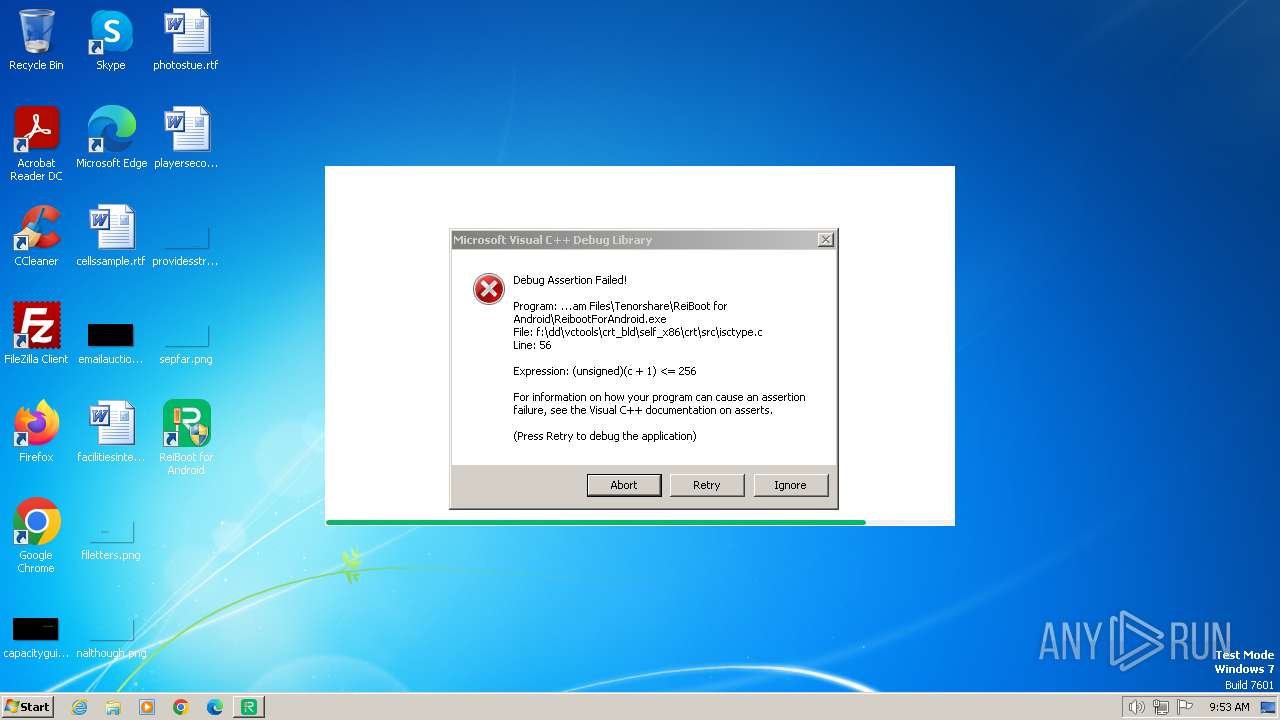
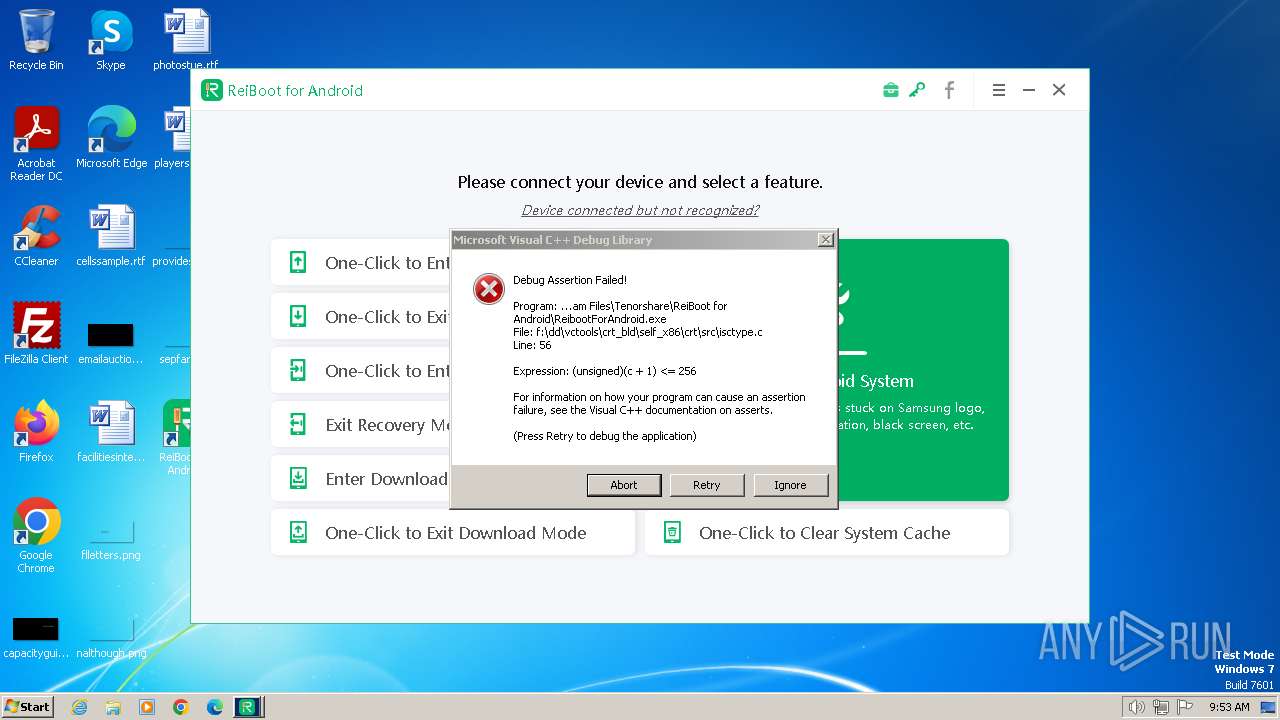
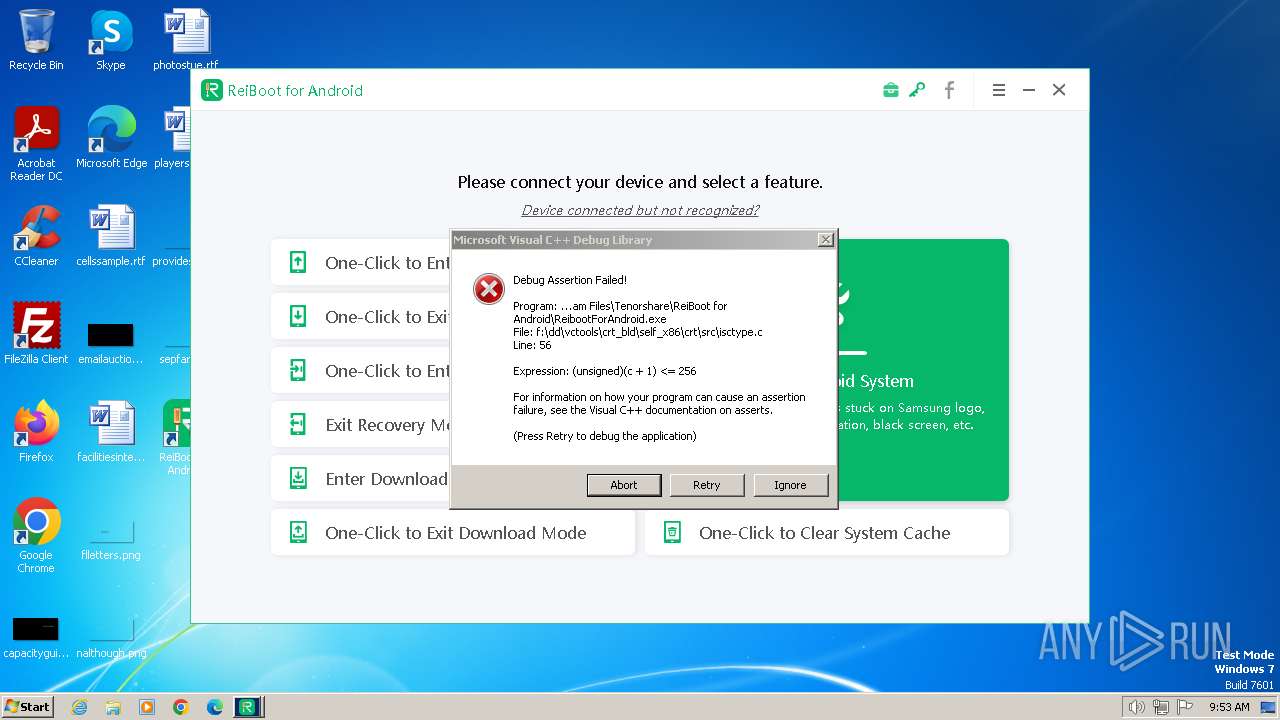
| URL: | https://www.tenorshare.net/products/reiboot-for-android.html |
| Full analysis: | https://app.any.run/tasks/07a3ba85-88e0-4583-acc9-4afac7c4cccf |
| Verdict: | Malicious activity |
| Analysis date: | January 01, 2024, 09:50:03 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 3BFE5329ED4A1D258A7F44B09B787B7A |
| SHA1: | 69BF81CB35D76538CD3046FA33EAD7C4BE7E9130 |
| SHA256: | A41845D5BD9357A6C28F0B1555FB6B5D34E7DBB9115DC4F6DFA1CB203FCD9380 |
| SSDEEP: | 3:N8DSLbXILLz9aQGRWMNIDMDRwJn:2OLELMTRWnQDR8n |
MALICIOUS
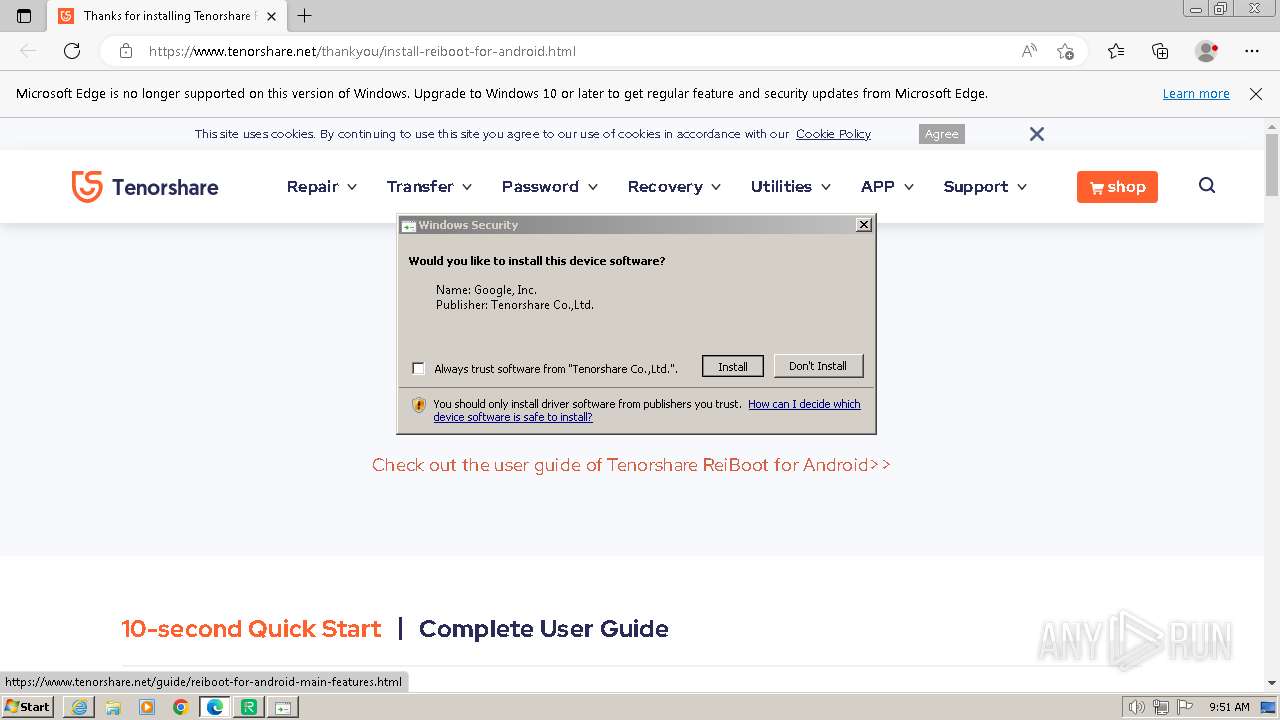
Creates a writable file in the system directory
- drvinst.exe (PID: 3424)
- drvinst.exe (PID: 2740)
- drvinst.exe (PID: 3360)
- drvinst.exe (PID: 3532)
- drvinst.exe (PID: 3860)
SUSPICIOUS
Reads the Internet Settings
- reiboot-for-android.exe (PID: 2572)
- Start.exe (PID: 2356)
- ReibootForAndroid.exe (PID: 2824)
- Start.exe (PID: 1820)
- ReibootForAndroid.exe (PID: 1832)
Reads security settings of Internet Explorer
- reiboot-for-android.exe (PID: 2572)
- ReibootForAndroid.exe (PID: 2824)
- ReibootForAndroid.exe (PID: 1832)
Checks Windows Trust Settings
- reiboot-for-android.exe (PID: 2572)
- drvinst.exe (PID: 3424)
- ReibootForAndroid.exe (PID: 2824)
- drvinst.exe (PID: 2740)
- drvinst.exe (PID: 3360)
- drvinst.exe (PID: 3860)
- drvinst.exe (PID: 3532)
- ReibootForAndroid.exe (PID: 1832)
Reads settings of System Certificates
- reiboot-for-android.exe (PID: 2572)
- rundll32.exe (PID: 3520)
- ReibootForAndroid.exe (PID: 2824)
- rundll32.exe (PID: 3484)
- ReibootForAndroid.exe (PID: 1832)
Reads the Windows owner or organization settings
- reibootforandroid_net_2.1.19.tmp (PID: 2844)
Drops a system driver (possible attempt to evade defenses)
- reibootforandroid_net_2.1.19.tmp (PID: 2844)
- DPInst32.exe (PID: 3364)
- drvinst.exe (PID: 3860)
- drvinst.exe (PID: 3532)
Searches for installed software
- ReibootForAndroid.exe (PID: 2824)
- ReibootForAndroid.exe (PID: 1832)
Creates a software uninstall entry
- ReibootForAndroid.exe (PID: 2824)
- ReibootForAndroid.exe (PID: 1832)
Starts CMD.EXE for commands execution
- ReibootForAndroid.exe (PID: 2824)
- ReibootForAndroid.exe (PID: 1832)
Creates files in the driver directory
- drvinst.exe (PID: 3424)
- drvinst.exe (PID: 2740)
- drvinst.exe (PID: 3360)
- drvinst.exe (PID: 3532)
- drvinst.exe (PID: 3860)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 2944)
- cmd.exe (PID: 3740)
- cmd.exe (PID: 3960)
- cmd.exe (PID: 3732)
Changes Internet Explorer settings (feature browser emulation)
- ReibootForAndroid.exe (PID: 1832)
INFO
Drops the executable file immediately after the start
- iexplore.exe (PID: 2032)
- iexplore.exe (PID: 116)
- reibootforandroid_net_2.1.19.exe (PID: 2360)
- ReibootForAndroid.exe (PID: 2824)
- reibootforandroid_net_2.1.19.tmp (PID: 2844)
- DPInst32.exe (PID: 3364)
- drvinst.exe (PID: 3424)
- drvinst.exe (PID: 2740)
- drvinst.exe (PID: 3360)
- drvinst.exe (PID: 3860)
- drvinst.exe (PID: 3532)
Reads Environment values
- reiboot-for-android.exe (PID: 2572)
- ReibootForAndroid.exe (PID: 2824)
- ReibootForAndroid.exe (PID: 1832)
Checks proxy server information
- reiboot-for-android.exe (PID: 2572)
- ReibootForAndroid.exe (PID: 2824)
- ReibootForAndroid.exe (PID: 1832)
Connects to the CnC server
- reiboot-for-android.exe (PID: 2572)
Checks for external IP
- reiboot-for-android.exe (PID: 2572)
Create files in a temporary directory
- reibootforandroid_net_2.1.19.exe (PID: 2360)
- reibootforandroid_net_2.1.19.tmp (PID: 2844)
- reiboot-for-android.exe (PID: 2572)
- ReibootForAndroid.exe (PID: 2824)
- DPInst32.exe (PID: 3364)
- adb.exe (PID: 2152)
- ReibootForAndroid.exe (PID: 1832)
Creates files in the program directory
- reiboot-for-android.exe (PID: 2572)
- reibootforandroid_net_2.1.19.tmp (PID: 2844)
- Start.exe (PID: 2356)
- ReibootForAndroid.exe (PID: 2824)
Checks supported languages
- reibootforandroid_net_2.1.19.tmp (PID: 2844)
- reibootforandroid_net_2.1.19.exe (PID: 2360)
- Start.exe (PID: 2356)
- ReibootForAndroid.exe (PID: 2824)
- reiboot-for-android.exe (PID: 2572)
- fastboot.exe (PID: 3260)
- fastboot.exe (PID: 3300)
- DPInst32.exe (PID: 3364)
- InstallAndDriver.exe (PID: 3232)
- repair.exe (PID: 3276)
- drvinst.exe (PID: 3424)
- fastboot.exe (PID: 3388)
- fastboot.exe (PID: 3872)
- fastboot.exe (PID: 1900)
- fastboot.exe (PID: 2376)
- fastboot.exe (PID: 188)
- fastboot.exe (PID: 3012)
- fastboot.exe (PID: 2840)
- fastboot.exe (PID: 3088)
- fastboot.exe (PID: 1020)
- drvinst.exe (PID: 2740)
- fastboot.exe (PID: 3776)
- fastboot.exe (PID: 2504)
- fastboot.exe (PID: 2748)
- fastboot.exe (PID: 3468)
- fastboot.exe (PID: 1044)
- fastboot.exe (PID: 568)
- fastboot.exe (PID: 3328)
- drvinst.exe (PID: 3532)
- fastboot.exe (PID: 3424)
- adb.exe (PID: 1796)
- adb.exe (PID: 1804)
- drvinst.exe (PID: 3860)
- fastboot.exe (PID: 908)
- adb.exe (PID: 2492)
- adb.exe (PID: 2152)
- fastboot.exe (PID: 2168)
- adb.exe (PID: 3780)
- adb.exe (PID: 3816)
- fastboot.exe (PID: 2948)
- adb.exe (PID: 3464)
- adb.exe (PID: 1600)
- fastboot.exe (PID: 452)
- adb.exe (PID: 4040)
- fastboot.exe (PID: 568)
- fastboot.exe (PID: 3064)
- fastboot.exe (PID: 2452)
- fastboot.exe (PID: 3864)
- fastboot.exe (PID: 3704)
- fastboot.exe (PID: 996)
- fastboot.exe (PID: 3488)
- fastboot.exe (PID: 3628)
- fastboot.exe (PID: 2356)
- fastboot.exe (PID: 2296)
- fastboot.exe (PID: 2816)
- fastboot.exe (PID: 2756)
- fastboot.exe (PID: 240)
- fastboot.exe (PID: 1344)
- fastboot.exe (PID: 3652)
- fastboot.exe (PID: 1268)
- fastboot.exe (PID: 2852)
- fastboot.exe (PID: 1924)
- fastboot.exe (PID: 1992)
- fastboot.exe (PID: 1840)
- drvinst.exe (PID: 3360)
- fastboot.exe (PID: 1844)
- fastboot.exe (PID: 3208)
- fastboot.exe (PID: 1036)
- fastboot.exe (PID: 1804)
- fastboot.exe (PID: 2496)
- fastboot.exe (PID: 3932)
- Start.exe (PID: 1820)
- fastboot.exe (PID: 3328)
- InstallAndDriver.exe (PID: 3388)
- fastboot.exe (PID: 3424)
- repair.exe (PID: 3864)
- ReibootForAndroid.exe (PID: 1832)
- fastboot.exe (PID: 3768)
- fastboot.exe (PID: 3872)
- fastboot.exe (PID: 1784)
- fastboot.exe (PID: 1528)
- fastboot.exe (PID: 2788)
- DPInst32.exe (PID: 3916)
- fastboot.exe (PID: 3876)
- fastboot.exe (PID: 2888)
- fastboot.exe (PID: 2256)
- fastboot.exe (PID: 2856)
- fastboot.exe (PID: 2928)
- fastboot.exe (PID: 1636)
- fastboot.exe (PID: 2328)
- fastboot.exe (PID: 2448)
- fastboot.exe (PID: 2952)
- fastboot.exe (PID: 2368)
- fastboot.exe (PID: 2764)
- fastboot.exe (PID: 3644)
Creates files or folders in the user directory
- reiboot-for-android.exe (PID: 2572)
- ReibootForAndroid.exe (PID: 2824)
- ReibootForAndroid.exe (PID: 1832)
Reads the computer name
- reibootforandroid_net_2.1.19.tmp (PID: 2844)
- ReibootForAndroid.exe (PID: 2824)
- Start.exe (PID: 2356)
- reiboot-for-android.exe (PID: 2572)
- fastboot.exe (PID: 3260)
- fastboot.exe (PID: 3300)
- DPInst32.exe (PID: 3364)
- drvinst.exe (PID: 3424)
- fastboot.exe (PID: 3388)
- fastboot.exe (PID: 3872)
- fastboot.exe (PID: 188)
- fastboot.exe (PID: 1900)
- fastboot.exe (PID: 2376)
- fastboot.exe (PID: 3012)
- fastboot.exe (PID: 2840)
- fastboot.exe (PID: 1020)
- fastboot.exe (PID: 3088)
- drvinst.exe (PID: 2740)
- fastboot.exe (PID: 3776)
- fastboot.exe (PID: 2748)
- fastboot.exe (PID: 2504)
- fastboot.exe (PID: 3468)
- fastboot.exe (PID: 568)
- drvinst.exe (PID: 3532)
- fastboot.exe (PID: 3328)
- drvinst.exe (PID: 3360)
- drvinst.exe (PID: 3860)
- fastboot.exe (PID: 3424)
- fastboot.exe (PID: 2948)
- adb.exe (PID: 2492)
- adb.exe (PID: 2152)
- fastboot.exe (PID: 908)
- fastboot.exe (PID: 2168)
- fastboot.exe (PID: 3704)
- fastboot.exe (PID: 996)
- fastboot.exe (PID: 3864)
- fastboot.exe (PID: 568)
- fastboot.exe (PID: 452)
- fastboot.exe (PID: 3064)
- fastboot.exe (PID: 2452)
- fastboot.exe (PID: 2356)
- fastboot.exe (PID: 3488)
- fastboot.exe (PID: 3628)
- fastboot.exe (PID: 2816)
- fastboot.exe (PID: 2296)
- fastboot.exe (PID: 2756)
- fastboot.exe (PID: 240)
- fastboot.exe (PID: 1344)
- fastboot.exe (PID: 1268)
- fastboot.exe (PID: 2852)
- fastboot.exe (PID: 1924)
- fastboot.exe (PID: 1036)
- fastboot.exe (PID: 1044)
- fastboot.exe (PID: 1992)
- fastboot.exe (PID: 3208)
- fastboot.exe (PID: 3652)
- fastboot.exe (PID: 2496)
- fastboot.exe (PID: 1804)
- fastboot.exe (PID: 3932)
- fastboot.exe (PID: 1844)
- fastboot.exe (PID: 3328)
- fastboot.exe (PID: 3424)
- Start.exe (PID: 1820)
- ReibootForAndroid.exe (PID: 1832)
- DPInst32.exe (PID: 3916)
- fastboot.exe (PID: 3768)
- fastboot.exe (PID: 1528)
- fastboot.exe (PID: 3872)
- fastboot.exe (PID: 1784)
- fastboot.exe (PID: 2788)
- fastboot.exe (PID: 3876)
- fastboot.exe (PID: 2764)
- fastboot.exe (PID: 2856)
- fastboot.exe (PID: 2928)
- fastboot.exe (PID: 1636)
- fastboot.exe (PID: 2448)
- fastboot.exe (PID: 2328)
- fastboot.exe (PID: 2952)
- fastboot.exe (PID: 2256)
- fastboot.exe (PID: 2888)
- fastboot.exe (PID: 2368)
- fastboot.exe (PID: 3644)
- fastboot.exe (PID: 1840)
Process drops legitimate windows executable
- reibootforandroid_net_2.1.19.tmp (PID: 2844)
- DPInst32.exe (PID: 3364)
- drvinst.exe (PID: 3424)
- drvinst.exe (PID: 2740)
- drvinst.exe (PID: 3360)
The process drops C-runtime libraries
- reibootforandroid_net_2.1.19.tmp (PID: 2844)
Process drops legitimate windows executable (CertUtil.exe)
- reibootforandroid_net_2.1.19.tmp (PID: 2844)
Drops 7-zip archiver for unpacking
- reibootforandroid_net_2.1.19.tmp (PID: 2844)
- ReibootForAndroid.exe (PID: 2824)
Reads the machine GUID from the registry
- ReibootForAndroid.exe (PID: 2824)
- reiboot-for-android.exe (PID: 2572)
- DPInst32.exe (PID: 3364)
- drvinst.exe (PID: 3424)
- drvinst.exe (PID: 2740)
- drvinst.exe (PID: 3532)
- drvinst.exe (PID: 3860)
- adb.exe (PID: 2492)
- adb.exe (PID: 2152)
- drvinst.exe (PID: 3360)
- ReibootForAndroid.exe (PID: 1832)
- DPInst32.exe (PID: 3916)
Application launched itself
- iexplore.exe (PID: 116)
- msedge.exe (PID: 3792)
- msedge.exe (PID: 2016)
- adb.exe (PID: 1796)
- adb.exe (PID: 3816)
The process uses the downloaded file
- iexplore.exe (PID: 116)
Reads security settings of Internet Explorer
- rundll32.exe (PID: 3520)
- rundll32.exe (PID: 3484)
Executes as Windows Service
- VSSVC.exe (PID: 3696)
Manual execution by a user
- msedge.exe (PID: 2016)
- notepad++.exe (PID: 568)
- Start.exe (PID: 2128)
- Start.exe (PID: 1820)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
335
Monitored processes
204
Malicious processes
14
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://www.tenorshare.net/products/reiboot-for-android.html" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 124 | "cmd.exe" /C "C:\tenorshare\adb\fastboot.exe" devices | C:\Windows\System32\cmd.exe | — | ReibootForAndroid.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 188 | C:\tenorshare\adb\fastboot.exe devices | C:\tenorshare\adb\fastboot.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 240 | C:\tenorshare\adb\fastboot.exe devices | C:\tenorshare\adb\fastboot.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 240 | "cmd.exe" /C "C:\tenorshare\adb\fastboot.exe" devices | C:\Windows\System32\cmd.exe | — | ReibootForAndroid.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 452 | "cmd.exe" /C "C:\tenorshare\adb\fastboot.exe" devices | C:\Windows\System32\cmd.exe | — | ReibootForAndroid.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 452 | C:\tenorshare\adb\fastboot.exe devices | C:\tenorshare\adb\fastboot.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 568 | C:\tenorshare\adb\fastboot.exe devices | C:\tenorshare\adb\fastboot.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 568 | C:\tenorshare\adb\fastboot.exe devices | C:\tenorshare\adb\fastboot.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 568 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Program Files\Tenorshare\ReiBoot for Android\Start.exe" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.91 Modules
| |||||||||||||||
Total events
61 571
Read events
60 996
Write events
566
Delete events
9
Modification events
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
332
Suspicious files
314
Text files
237
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2032 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CAF4703619713E3F18D8A9D5D88D6288_F2DAF19C1F776537105D08FC8D978464 | binary | |
MD5:2282A4BDC3A4F23DFA1C2899086E824C | SHA256:9F8FCFA95025D3C306EC846103CB6CA423BD234684EB9D3D370211E0716FB9D5 | |||
| 2032 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_F2DAF19C1F776537105D08FC8D978464 | binary | |
MD5:8202A1CD02E7D69597995CABBE881A12 | SHA256:58F381C3A0A0ACE6321DA22E40BD44A597BD98B9C9390AB9258426B5CF75A7A5 | |||
| 2032 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:B686D1C4DECB96BEBD5F5E8D782A8CEF | SHA256:7870C6592639AF694DCFB12DAF05D546321B9D2B914E36482045F101EBB0347B | |||
| 2032 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\swiper-4.2.0.min[1].css | text | |
MD5:E15E63828BF778572D6535E497A718A2 | SHA256:64953D2C7897A65562B575DE3776B259D31815910919F82AE40035F923721887 | |||
| 2032 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\DNBG1FNU.txt | text | |
MD5:FCFCBFD67A368A57E8CC748609BAA94A | SHA256:EEA0C1446657A71227EF18140C36239C2599C2B5543EA3499A5C8A62E3F7EF45 | |||
| 2032 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\reiboot-for-android[1].htm | html | |
MD5:BD88999D7B6F3D77D55E17C9374C6F24 | SHA256:0DF04DBB223CF51FB22F1FAC1833B89EF12E4133BB3988532BA4D5DA9789617D | |||
| 2032 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\app.bundle[1].js | text | |
MD5:54A942DB3467561955074AE54B9D0C7C | SHA256:4B8D342B06C72DEA82A33204835511A55702A23FACFD490536CEFACBFDF2DC80 | |||
| 2032 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 2032 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | binary | |
MD5:AC89A852C2AAA3D389B2D2DD312AD367 | SHA256:0B720E19270C672F9B6E0EC40B468AC49376807DE08A814573FE038779534F45 | |||
| 2032 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\reiboot-android-pic03[1].svg | image | |
MD5:707F9B08458388A1D63F904B29A35871 | SHA256:A1CE59552950500289A2ABB02009BEF2160D150992861CF870B1D666BE3F93A8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
57
TCP/UDP connections
224
DNS requests
135
Threats
11
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2032 | iexplore.exe | GET | 200 | 23.32.238.242:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?53bfb7cf8a6cf97e | unknown | compressed | 4.66 Kb | unknown |
2032 | iexplore.exe | GET | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFCjJ1PwkYAi7fE%3D | unknown | binary | 724 b | unknown |
2032 | iexplore.exe | GET | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQClj3zJOwEs2AlR6v%2BfUXog | unknown | binary | 472 b | unknown |
2032 | iexplore.exe | GET | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEA1uFYrLabZxEtE2U5X5DGM%3D | unknown | binary | 471 b | unknown |
2032 | iexplore.exe | GET | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCZXmpIP%2Bo%2BHhJmodADfw%2Fc | unknown | binary | 472 b | unknown |
2032 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAqvpsXKY8RRQeo74ffHUxc%3D | unknown | binary | 471 b | unknown |
2032 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAVG%2Fhgj9%2BGUHaOfzhTEYXM%3D | unknown | binary | 471 b | unknown |
2032 | iexplore.exe | GET | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEGupzMnM%2BqGaCjIQPyd58u0%3D | unknown | binary | 471 b | unknown |
2032 | iexplore.exe | GET | 200 | 23.32.238.242:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?6b21170b0e7a1648 | unknown | compressed | 4.66 Kb | unknown |
2032 | iexplore.exe | GET | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2032 | iexplore.exe | 104.18.11.138:443 | www.tenorshare.net | CLOUDFLARENET | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2032 | iexplore.exe | 23.32.238.242:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
2032 | iexplore.exe | 142.250.186.131:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
2032 | iexplore.exe | 142.250.186.42:443 | fonts.googleapis.com | GOOGLE | US | whitelisted |
2032 | iexplore.exe | 104.18.24.249:443 | images.tenorshare.com | CLOUDFLARENET | — | unknown |
2032 | iexplore.exe | 104.18.10.138:443 | www.tenorshare.net | CLOUDFLARENET | — | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2032 | iexplore.exe | 142.250.186.72:443 | www.googletagmanager.com | GOOGLE | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.tenorshare.net |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
images.tenorshare.com |
| whitelisted |
images.tenorshare.net |
| unknown |
www.googletagmanager.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
rpc.tenorshare.com |
| unknown |
bat.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2572 | reiboot-for-android.exe | Potential Corporate Privacy Violation | ET POLICY Unsupported/Fake Windows NT Version 5.0 |
2572 | reiboot-for-android.exe | Potential Corporate Privacy Violation | ET POLICY Unsupported/Fake Windows NT Version 5.0 |
2572 | reiboot-for-android.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
2572 | reiboot-for-android.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
2572 | reiboot-for-android.exe | Possibly Unwanted Program Detected | ET ADWARE_PUP Tensorshare Google Analytics Checkin |
2824 | ReibootForAndroid.exe | Potential Corporate Privacy Violation | ET POLICY Unsupported/Fake Windows NT Version 5.0 |
1832 | ReibootForAndroid.exe | Potential Corporate Privacy Violation | ET POLICY Unsupported/Fake Windows NT Version 5.0 |
4 ETPRO signatures available at the full report
Process | Message |
|---|---|
ReibootForAndroid.exe | log4net:ERROR XmlHierarchyConfigurator: No appender named [ConsoleAppender] could be found.
|
ReibootForAndroid.exe | log4net:ERROR Appender named [ConsoleAppender] not found.
|
ReibootForAndroid.exe | Native library pre-loader is trying to load native SQLite library "C:\Program Files\Tenorshare\ReiBoot for Android\x86\SQLite.Interop.dll"...
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\plugins\Config\nppPluginList.dll
|