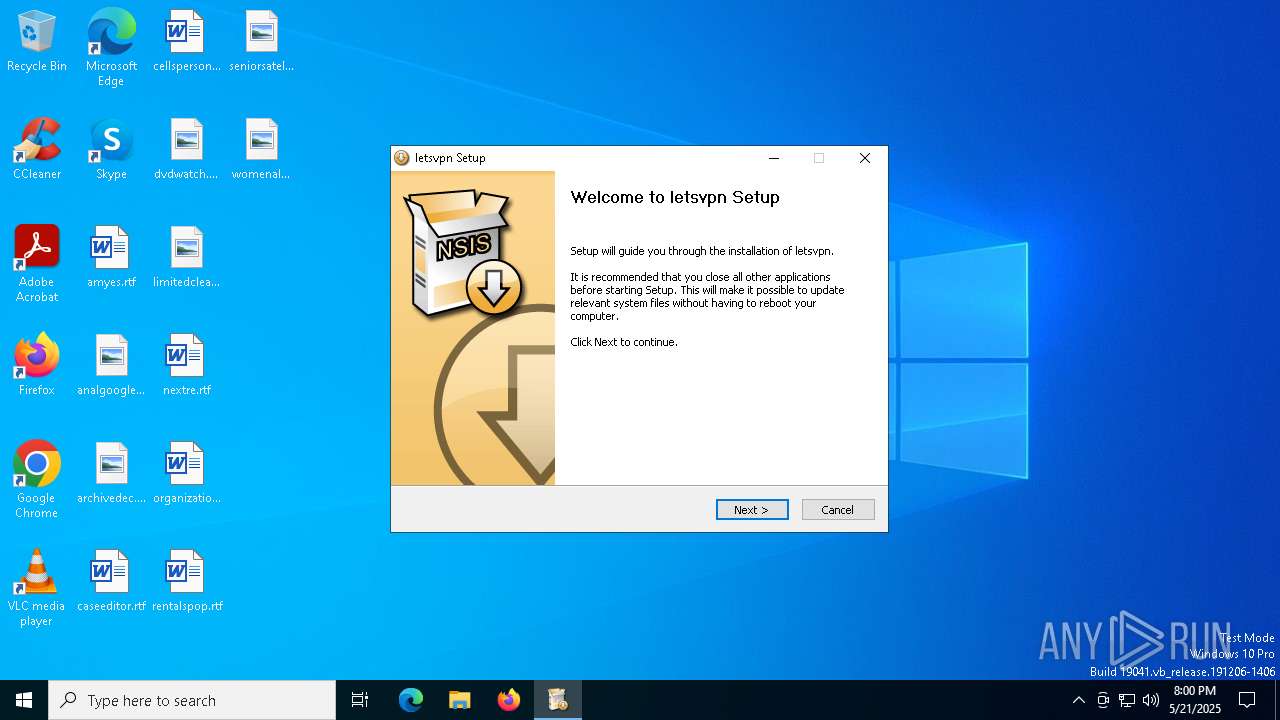
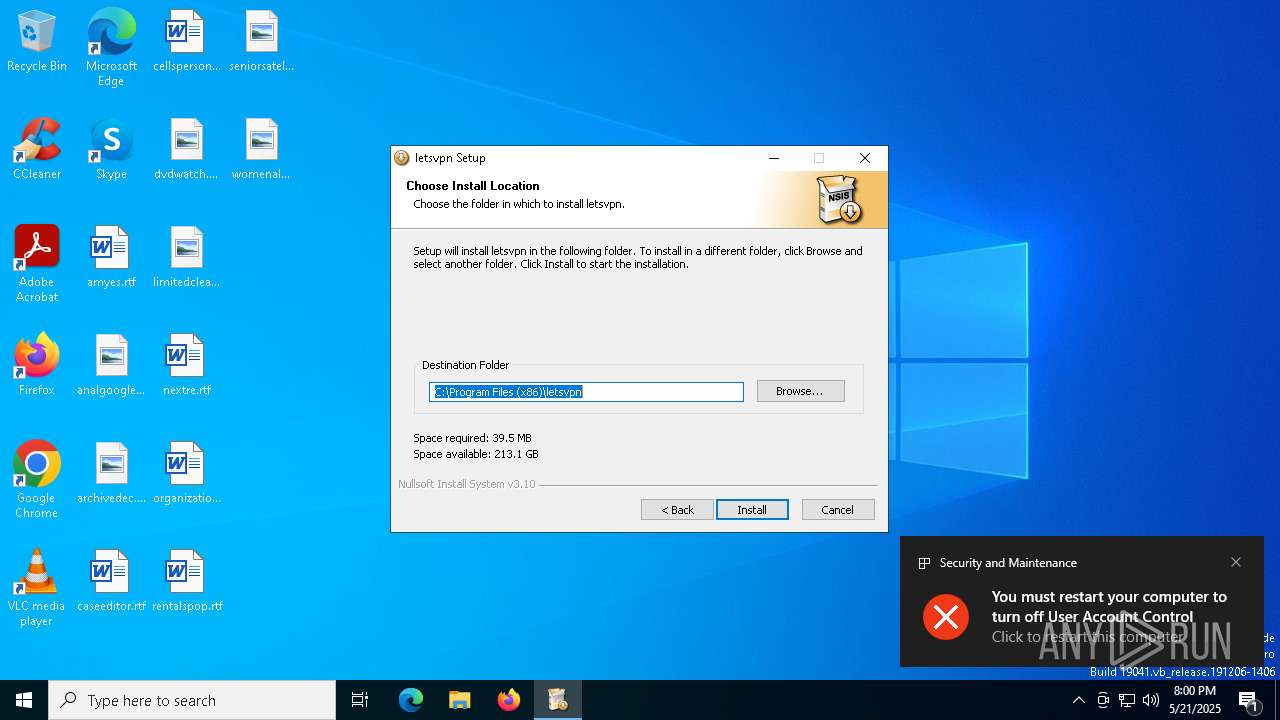
| File name: | letslavpnX64.exe |
| Full analysis: | https://app.any.run/tasks/27e809ba-b99b-43e1-9191-11cf30dd9e2d |
| Verdict: | Malicious activity |
| Analysis date: | May 21, 2025, 19:59:41 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | 147651E9D91CC64967EF278AFA9926CD |
| SHA1: | 2A47E9A17FB32387930E5E47E8E5DF58FB23603A |
| SHA256: | A4170FA0F47AB88E7FFA5529C9E4048F2A19E955CA16953E7A8B445D1E977A97 |
| SSDEEP: | 196608:22IPXAa3MfVmKbOkOisgbxI1VfVOuWIzU1K2zZawh:ji8ftbOkOPgb6dOXSUFZDh |
MALICIOUS
Executing a file with an untrusted certificate
- letslavpnX64.exe (PID: 7232)
- letslavpnX64.exe (PID: 7340)
Antivirus name has been found in the command line (generic signature)
- powershell.exe (PID: 1188)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 6808)
Changes the autorun value in the registry
- iusb3mon.exe (PID: 7828)
Changes powershell execution policy (Bypass)
- letsvpn-latest.exe (PID: 6944)
Bypass execution policy to execute commands
- powershell.exe (PID: 7484)
SUSPICIOUS
Executable content was dropped or overwritten
- letslavpnX64.exe (PID: 7340)
- irsetup.exe (PID: 7388)
- letsvpn-latest.exe (PID: 6944)
- tapinstall.exe (PID: 6480)
- drvinst.exe (PID: 7920)
- drvinst.exe (PID: 7520)
Reads security settings of Internet Explorer
- letslavpnX64.exe (PID: 7340)
- irsetup.exe (PID: 7388)
Starts POWERSHELL.EXE for commands execution
- irsetup.exe (PID: 7388)
- iusb3mon.exe (PID: 7828)
- letsvpn-latest.exe (PID: 6944)
Get information on the list of running processes
- irsetup.exe (PID: 7388)
The process drops C-runtime libraries
- irsetup.exe (PID: 7388)
Process drops legitimate windows executable
- irsetup.exe (PID: 7388)
- letsvpn-latest.exe (PID: 6944)
Malware-specific behavior (creating "System.dll" in Temp)
- letsvpn-latest.exe (PID: 6944)
The process creates files with name similar to system file names
- letsvpn-latest.exe (PID: 6944)
Starts CMD.EXE for commands execution
- iusb3mon.exe (PID: 7828)
- LetsPRO.exe (PID: 6416)
- letsvpn-latest.exe (PID: 6944)
Probably obfuscated PowerShell command line is found
- iusb3mon.exe (PID: 7828)
Removes files via Powershell
- powershell.exe (PID: 7780)
Manipulates environment variables
- powershell.exe (PID: 7780)
Base64-obfuscated command line is found
- iusb3mon.exe (PID: 7828)
The process bypasses the loading of PowerShell profile settings
- iusb3mon.exe (PID: 7828)
There is functionality for taking screenshot (YARA)
- letsvpn-latest.exe (PID: 6944)
- iusb3mon.exe (PID: 7828)
There is functionality for VM detection Parallels (YARA)
- iusb3mon.exe (PID: 7828)
There is functionality for VM detection VMWare (YARA)
- iusb3mon.exe (PID: 7828)
PowerShell delay command usage (probably sleep evasion)
- powershell.exe (PID: 7780)
There is functionality for VM detection VirtualBox (YARA)
- iusb3mon.exe (PID: 7828)
Drops a system driver (possible attempt to evade defenses)
- letsvpn-latest.exe (PID: 6944)
- drvinst.exe (PID: 7920)
- tapinstall.exe (PID: 6480)
- drvinst.exe (PID: 7520)
Connects to unusual port
- iusb3mon.exe (PID: 7828)
The process executes Powershell scripts
- letsvpn-latest.exe (PID: 6944)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- cmd.exe (PID: 6044)
- cmd.exe (PID: 5244)
- cmd.exe (PID: 5352)
- cmd.exe (PID: 8176)
- cmd.exe (PID: 8152)
Executes as Windows Service
- WmiApSrv.exe (PID: 7992)
Process uses IPCONFIG to discover network configuration
- cmd.exe (PID: 6640)
Suspicious use of NETSH.EXE
- LetsPRO.exe (PID: 6416)
Process uses ARP to discover network configuration
- cmd.exe (PID: 5408)
Uses ROUTE.EXE to obtain the routing table information
- cmd.exe (PID: 2316)
INFO
Checks supported languages
- letslavpnX64.exe (PID: 7340)
- irsetup.exe (PID: 7388)
- iusb3mon.exe (PID: 7828)
- letsvpn-latest.exe (PID: 6944)
Reads the computer name
- irsetup.exe (PID: 7388)
- letslavpnX64.exe (PID: 7340)
- letsvpn-latest.exe (PID: 6944)
Create files in a temporary directory
- letslavpnX64.exe (PID: 7340)
- irsetup.exe (PID: 7388)
- letsvpn-latest.exe (PID: 6944)
- iusb3mon.exe (PID: 7828)
- SecEdit.exe (PID: 8120)
Process checks computer location settings
- letslavpnX64.exe (PID: 7340)
- irsetup.exe (PID: 7388)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 8092)
- powershell.exe (PID: 4692)
- powershell.exe (PID: 1188)
- powershell.exe (PID: 668)
- powershell.exe (PID: 7520)
- powershell.exe (PID: 1628)
The process uses Lua
- irsetup.exe (PID: 7388)
The sample compiled with english language support
- irsetup.exe (PID: 7388)
- letslavpnX64.exe (PID: 7340)
- letsvpn-latest.exe (PID: 6944)
- tapinstall.exe (PID: 6480)
- drvinst.exe (PID: 7920)
- drvinst.exe (PID: 7520)
Creates files or folders in the user directory
- irsetup.exe (PID: 7388)
Creates files in the program directory
- irsetup.exe (PID: 7388)
The sample compiled with chinese language support
- irsetup.exe (PID: 7388)
UPX packer has been detected
- irsetup.exe (PID: 7388)
- iusb3mon.exe (PID: 7828)
Auto-launch of the file from Registry key
- iusb3mon.exe (PID: 7828)
Manual execution by a user
- iusb3mon.exe (PID: 4688)
Prints a route via ROUTE.EXE
- ROUTE.EXE (PID: 8188)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (43.5) |
|---|---|---|
| .exe | | | Win32 EXE Yoda's Crypter (42.7) |
| .exe | | | Win32 Executable (generic) (7.2) |
| .exe | | | Generic Win/DOS Executable (3.2) |
| .exe | | | DOS Executable Generic (3.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2012:06:14 16:16:10+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 10 |
| CodeSize: | 22528 |
| InitializedDataSize: | 48128 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x29e1 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 9.1.0.0 |
| ProductVersionNumber: | 9.1.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Private build |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| Comments: | Created with Setup Factory |
| FileDescription: | Setup Application |
| FileVersion: | 9.1.0.0 |
| InternalName: | suf_launch |
| LegalCopyright: | Setup Engine Copyright © 2004-2012 Indigo Rose Corporation |
| LegalTrademarks: | Setup Factory is a trademark of Indigo Rose Corporation. |
| OriginalFileName: | suf_launch.exe |
| ProductName: | Setup Factory Runtime |
| ProductVersion: | 9.1.0.0 |
Total processes
218
Monitored processes
70
Malicious processes
4
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 668 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" Get-Process ([IO.Path]::GetFileNameWithoutExtension(\"mpcopyaccelerator.exe\")); | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | irsetup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 668 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | tapinstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 924 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1184 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1188 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" Get-Process ([IO.Path]::GetFileNameWithoutExtension(\"msmpeng.exe\")); | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | irsetup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1628 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" Get-Process ([IO.Path]::GetFileNameWithoutExtension(\"securityhealthsystray.exe\")); | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | irsetup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1912 | "C:\Program Files (x86)\letsvpn\LetsPRO.exe" checkNetFramework | C:\Program Files (x86)\letsvpn\LetsPRO.exe | — | letsvpn-latest.exe | |||||||||||
User: admin Integrity Level: HIGH Description: LetsVPN Exit code: 0 Version: 3.12.0 Modules
| |||||||||||||||
| 2316 | "cmd.exe" /C route print | C:\Windows\SysWOW64\cmd.exe | — | LetsPRO.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2420 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2984 | schtasks.exe /create /tn "Intel USB 3.0 eXtensible Host Controller" /xml "C:\Users\admin\AppData\Local\Temp\1123375_t.xml" | C:\Windows\SysWOW64\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
84 393
Read events
84 198
Write events
170
Delete events
25
Modification events
| (PID) Process: | (7828) iusb3mon.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | MicrosoftUSBMonitor |
Value: C:\Users\admin\AppData\Local\AppData\iusb3mon.exe | |||
| (PID) Process: | (7828) iusb3mon.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | MicrosoftUSBMonitor |
Value: C:\Users\admin\AppData\Local\AppData\iusb3mon.exe | |||
| (PID) Process: | (8120) SecEdit.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows NT\CurrentVersion\SecEdit |
| Operation: | delete value | Name: | LastWinlogonConfig |
Value: | |||
| (PID) Process: | (7828) iusb3mon.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | ConsentPromptBehaviorAdmin |
Value: 0 | |||
| (PID) Process: | (7828) iusb3mon.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | EnableLUA |
Value: 0 | |||
| (PID) Process: | (7828) iusb3mon.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | PromptOnSecureDesktop |
Value: 0 | |||
| (PID) Process: | (6644) ShellExperienceHost.exe | Key: | \REGISTRY\A\{6ba9da3e-51f3-c328-bb69-c8eedf6f2c53}\LocalState |
| Operation: | write | Name: | PeekBadges |
Value: 5B005D000000F58500018BCADB01 | |||
| (PID) Process: | (6644) ShellExperienceHost.exe | Key: | \REGISTRY\A\{6ba9da3e-51f3-c328-bb69-c8eedf6f2c53}\LocalState |
| Operation: | write | Name: | PeekBadges |
Value: 5B005D0000002FE802018BCADB01 | |||
| (PID) Process: | (7828) iusb3mon.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | DisableLockWorkstation |
Value: 0 | |||
| (PID) Process: | (6944) letsvpn-latest.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\lets |
| Operation: | write | Name: | InstallTimeStamp |
Value: 20250521200038.806 | |||
Executable files
237
Suspicious files
43
Text files
38
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7388 | irsetup.exe | C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\IRIMG1.JPG | image | |
MD5:3220A6AEFB4FC719CC8849F060859169 | SHA256:988CF422CBF400D41C48FBE491B425A827A1B70691F483679C1DF02FB9352765 | |||
| 7340 | letslavpnX64.exe | C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\irsetup.exe | executable | |
MD5:DEC931E86140139380EA0DF57CD132B6 | SHA256:5FFD4B20DCCFB84C8890ABDB780184A7651E760AEFBA4AB0C6FBA5B2A81F97D9 | |||
| 7388 | irsetup.exe | C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\irsetup.dat | binary | |
MD5:BAE8DA65578B2F27F37CF2914178D928 | SHA256:0C049ACA113D19E9232F005ACB39AFFFB1CBCF294BD3FD0D50F18337409CCE21 | |||
| 4692 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_5q20xp5p.u5l.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7388 | irsetup.exe | C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\IRIMG2.JPG | image | |
MD5:AC40DED6736E08664F2D86A65C47EF60 | SHA256:F35985FE1E46A767BE7DCEA35F8614E1EDD60C523442E6C2C2397D1E23DBD3EA | |||
| 7340 | letslavpnX64.exe | C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\lua5.1.dll | executable | |
MD5:B5FC476C1BF08D5161346CC7DD4CB0BA | SHA256:12CB9B8F59C00EF40EA8F28BFC59A29F12DC28332BF44B1A5D8D6A8823365650 | |||
| 7460 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ufukprrp.pzw.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7460 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:DA98DBD1C0BFAB988F265E613AF45671 | SHA256:C44A15FCFA77C51A53E31CC3498B5899944D3AFF71275A565F4933DD3396CEB9 | |||
| 8092 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_5tqt0nzk.oxt.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7460 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ka1tamsa.n45.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
126
DNS requests
37
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6148 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6148 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5984 | SIHClient.exe | GET | 200 | 95.100.102.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5984 | SIHClient.exe | GET | 200 | 95.100.102.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6416 | LetsPRO.exe | GET | 200 | 104.18.21.226:80 | http://ocsp.globalsign.com/codesigningrootr45/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBQVFZP5vqhCrtRN5SWf40Rn6NM1IAQUHwC%2FRoAK%2FHg5t6W0Q9lWULvOljsCEQCBTkIXoSl%2F7VrM1Bf4ka11 | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6416 | LetsPRO.exe | GET | 101 | 18.140.201.48:80 | http://ws-ap1.pusher.com/app/4fc436ef36f4026102d7?protocol=5&client=pusher-dotnet-client&version=1.1.2 | unknown | — | — | whitelisted |
6416 | LetsPRO.exe | GET | 200 | 104.18.21.226:80 | http://ocsp.globalsign.com/gsgccr45codesignca2020/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBTLuA3ygnKW%2F7xuSx%2F09F%2BhHVuEUQQU2rONwCSQo2t30wygWd0hZ2R2C3gCDFxLOsCV0WoYXJJrOQ%3D%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4628 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.64:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
6148 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
example.org |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6416 | LetsPRO.exe | Not Suspicious Traffic | INFO [ANY.RUN] Websocket Upgrade Request |