| File name: | Trojan-Ransom.Win32.Crypmod.aaxv-5b73019c232adbd1627b986bfc476de96c230ad54a9a014932f3f32d814fc744.7z |
| Full analysis: | https://app.any.run/tasks/10f8fe9d-e9de-486c-869d-5ef5129be3b0 |
| Verdict: | Malicious activity |
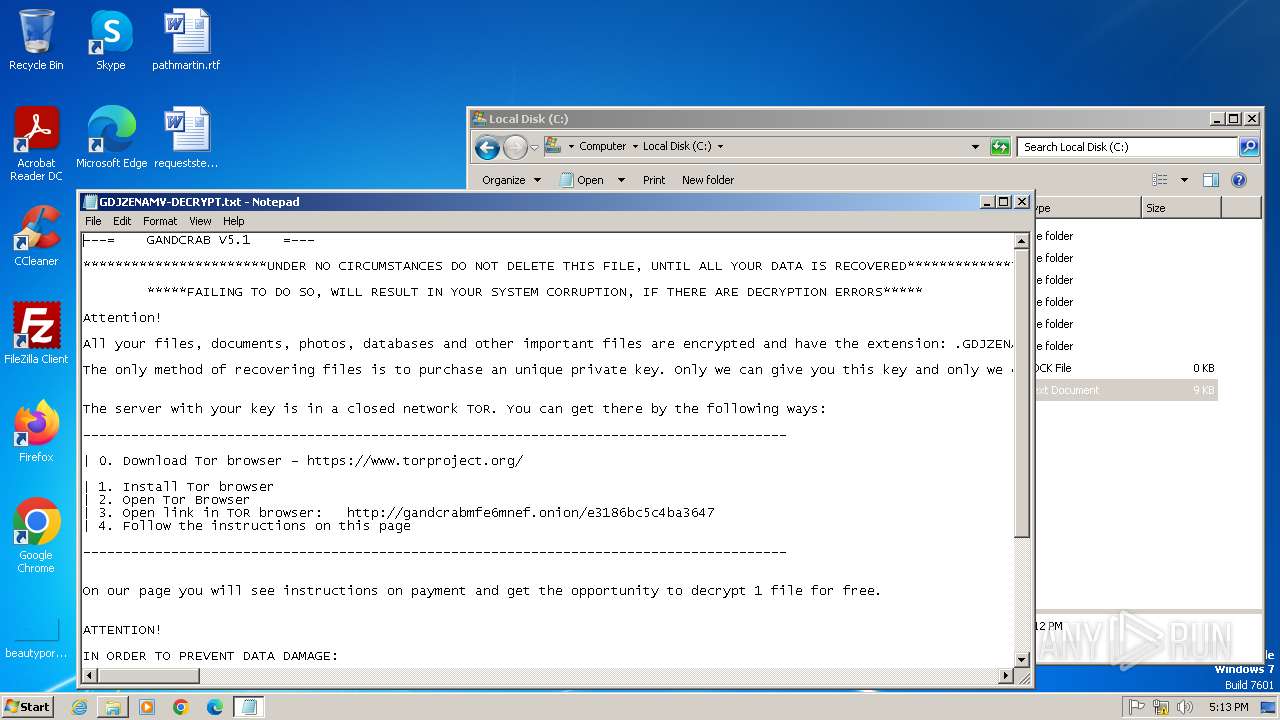
| Threats: | GandCrab is probably one of the most famous Ransomware. A Ransomware is a malware that asks the victim to pay money in order to restore access to encrypted files. If the user does not cooperate the files are forever lost. |
| Analysis date: | May 09, 2025, 16:12:21 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | E7F94B456822030DBA9F5FA4507D1DE5 |
| SHA1: | 870863663D8EC36C51AD06A988DBD35D1FD5B87C |
| SHA256: | A3F94050E13E8CE215367F7597E595EA0788E6A992BC75EA0BA82ABBCEEB0F51 |
| SSDEEP: | 6144:12/9sc7cxgHS1466cdx6FcgqnCrF7AHv9xv9Be5RJ:G6EXS1466cdXgqnwFcP9xv9cL |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 2624)
GandCrab keys are found
- Trojan-Ransom.Win32.Crypmod.aaxv-5b73019c232adbd1627b986bfc476de96c230ad54a9a014932f3f32d814fc744.exe (PID: 2516)
SUSPICIOUS
Smart Card resource manager service initialization
- Trojan-Ransom.Win32.Crypmod.aaxv-5b73019c232adbd1627b986bfc476de96c230ad54a9a014932f3f32d814fc744.exe (PID: 2516)
Creates file in the systems drive root
- Trojan-Ransom.Win32.Crypmod.aaxv-5b73019c232adbd1627b986bfc476de96c230ad54a9a014932f3f32d814fc744.exe (PID: 2516)
There is functionality for taking screenshot (YARA)
- Trojan-Ransom.Win32.Crypmod.aaxv-5b73019c232adbd1627b986bfc476de96c230ad54a9a014932f3f32d814fc744.exe (PID: 2516)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2624)
The sample compiled with english language support
- WinRAR.exe (PID: 2624)
Reads CPU info
- Trojan-Ransom.Win32.Crypmod.aaxv-5b73019c232adbd1627b986bfc476de96c230ad54a9a014932f3f32d814fc744.exe (PID: 2516)
Manual execution by a user
- Trojan-Ransom.Win32.Crypmod.aaxv-5b73019c232adbd1627b986bfc476de96c230ad54a9a014932f3f32d814fc744.exe (PID: 2516)
- explorer.exe (PID: 1560)
- notepad.exe (PID: 3684)
Checks supported languages
- Trojan-Ransom.Win32.Crypmod.aaxv-5b73019c232adbd1627b986bfc476de96c230ad54a9a014932f3f32d814fc744.exe (PID: 2516)
Reads the computer name
- Trojan-Ransom.Win32.Crypmod.aaxv-5b73019c232adbd1627b986bfc476de96c230ad54a9a014932f3f32d814fc744.exe (PID: 2516)
Reads product name
- Trojan-Ransom.Win32.Crypmod.aaxv-5b73019c232adbd1627b986bfc476de96c230ad54a9a014932f3f32d814fc744.exe (PID: 2516)
Reads Environment values
- Trojan-Ransom.Win32.Crypmod.aaxv-5b73019c232adbd1627b986bfc476de96c230ad54a9a014932f3f32d814fc744.exe (PID: 2516)
Reads the machine GUID from the registry
- Trojan-Ransom.Win32.Crypmod.aaxv-5b73019c232adbd1627b986bfc476de96c230ad54a9a014932f3f32d814fc744.exe (PID: 2516)
Creates files in the program directory
- Trojan-Ransom.Win32.Crypmod.aaxv-5b73019c232adbd1627b986bfc476de96c230ad54a9a014932f3f32d814fc744.exe (PID: 2516)
Creates files or folders in the user directory
- Trojan-Ransom.Win32.Crypmod.aaxv-5b73019c232adbd1627b986bfc476de96c230ad54a9a014932f3f32d814fc744.exe (PID: 2516)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 2019:11:20 19:42:12+00:00 |
| ArchivedFileName: | Trojan-Ransom.Win32.Crypmod.aaxv-5b73019c232adbd1627b986bfc476de96c230ad54a9a014932f3f32d814fc744.exe |
Total processes
42
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1560 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2516 | "C:\Users\admin\Desktop\Trojan-Ransom.Win32.Crypmod.aaxv-5b73019c232adbd1627b986bfc476de96c230ad54a9a014932f3f32d814fc744.exe" | C:\Users\admin\Desktop\Trojan-Ransom.Win32.Crypmod.aaxv-5b73019c232adbd1627b986bfc476de96c230ad54a9a014932f3f32d814fc744.exe | explorer.exe | ||||||||||||
User: admin Company: IBE Software Integrity Level: HIGH Description: Contention One Vs Modules
| |||||||||||||||
| 2624 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\Trojan-Ransom.Win32.Crypmod.aaxv-5b73019c232adbd1627b986bfc476de96c230ad54a9a014932f3f32d814fc744.7z | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3684 | "C:\Windows\system32\NOTEPAD.EXE" C:\GDJZENAMV-DECRYPT.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
13 271
Read events
13 245
Write events
26
Delete events
0
Modification events
| (PID) Process: | (2624) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2624) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2624) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2624) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2624) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (2624) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2624) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Trojan-Ransom.Win32.Crypmod.aaxv-5b73019c232adbd1627b986bfc476de96c230ad54a9a014932f3f32d814fc744.7z | |||
| (PID) Process: | (2624) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2624) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2624) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
7
Suspicious files
626
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2516 | Trojan-Ransom.Win32.Crypmod.aaxv-5b73019c232adbd1627b986bfc476de96c230ad54a9a014932f3f32d814fc744.exe | C:\Recovery\345b46fe-a9f9-11e7-a83c-e8a4f72b1d33\Winre.wim | — | |
MD5:— | SHA256:— | |||
| 2516 | Trojan-Ransom.Win32.Crypmod.aaxv-5b73019c232adbd1627b986bfc476de96c230ad54a9a014932f3f32d814fc744.exe | C:\Recovery\345b46fe-a9f9-11e7-a83c-e8a4f72b1d33\Winre.wim.gdjzenamv | — | |
MD5:— | SHA256:— | |||
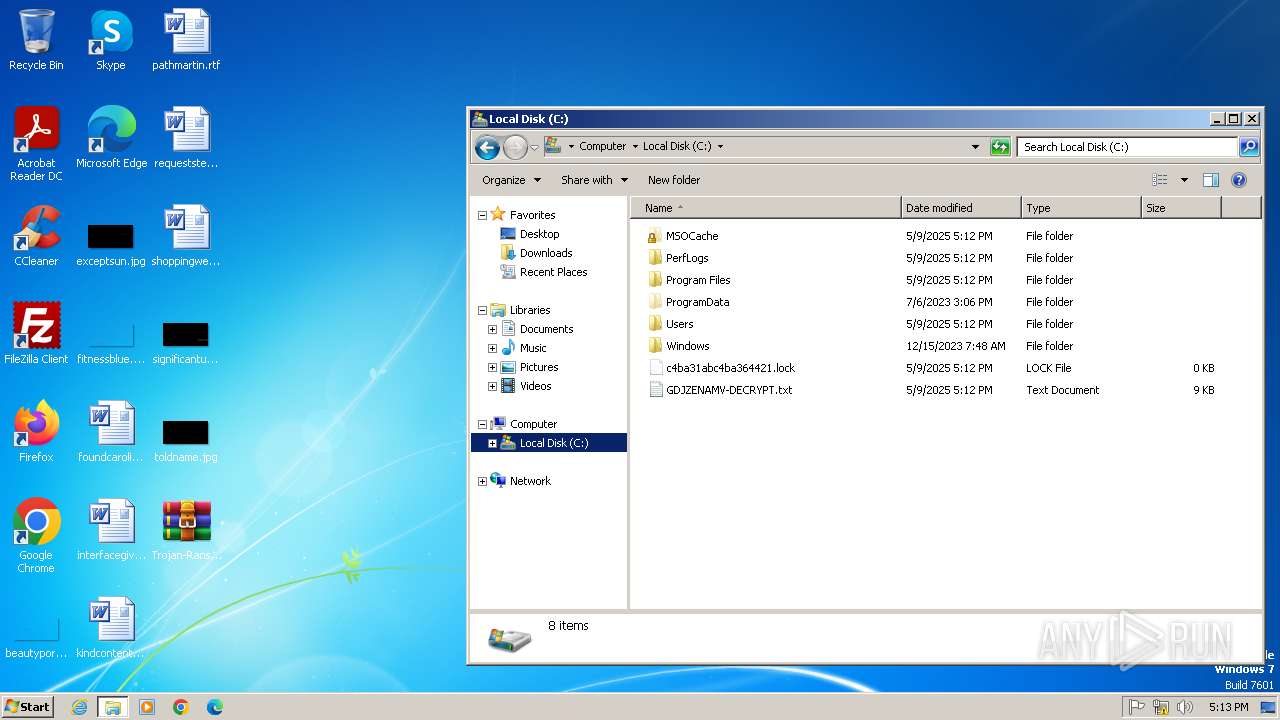
| 2516 | Trojan-Ransom.Win32.Crypmod.aaxv-5b73019c232adbd1627b986bfc476de96c230ad54a9a014932f3f32d814fc744.exe | C:\GDJZENAMV-DECRYPT.txt | binary | |
MD5:92F07FDE7A0FF8F81480B12793BE6E83 | SHA256:563AABF21D40DAFFDFCC2970D396344804195067BBE0EF7451D85A1490FEA718 | |||
| 2624 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2624.46238\Trojan-Ransom.Win32.Crypmod.aaxv-5b73019c232adbd1627b986bfc476de96c230ad54a9a014932f3f32d814fc744.exe | executable | |
MD5:C70CCCC83EDC3F6C757C267CD08D4687 | SHA256:5B73019C232ADBD1627B986BFC476DE96C230AD54A9A014932F3F32D814FC744 | |||
| 2516 | Trojan-Ransom.Win32.Crypmod.aaxv-5b73019c232adbd1627b986bfc476de96c230ad54a9a014932f3f32d814fc744.exe | C:\$Recycle.Bin\S-1-5-21-1302019708-1500728564-335382590-500\GDJZENAMV-DECRYPT.txt | binary | |
MD5:92F07FDE7A0FF8F81480B12793BE6E83 | SHA256:563AABF21D40DAFFDFCC2970D396344804195067BBE0EF7451D85A1490FEA718 | |||
| 2516 | Trojan-Ransom.Win32.Crypmod.aaxv-5b73019c232adbd1627b986bfc476de96c230ad54a9a014932f3f32d814fc744.exe | C:\MSOCache\GDJZENAMV-DECRYPT.txt | binary | |
MD5:92F07FDE7A0FF8F81480B12793BE6E83 | SHA256:563AABF21D40DAFFDFCC2970D396344804195067BBE0EF7451D85A1490FEA718 | |||
| 2516 | Trojan-Ransom.Win32.Crypmod.aaxv-5b73019c232adbd1627b986bfc476de96c230ad54a9a014932f3f32d814fc744.exe | C:\$Recycle.Bin\S-1-5-21-1302019708-1500728564-335382590-1000\GDJZENAMV-DECRYPT.txt | binary | |
MD5:92F07FDE7A0FF8F81480B12793BE6E83 | SHA256:563AABF21D40DAFFDFCC2970D396344804195067BBE0EF7451D85A1490FEA718 | |||
| 2516 | Trojan-Ransom.Win32.Crypmod.aaxv-5b73019c232adbd1627b986bfc476de96c230ad54a9a014932f3f32d814fc744.exe | C:\PerfLogs\GDJZENAMV-DECRYPT.txt | binary | |
MD5:92F07FDE7A0FF8F81480B12793BE6E83 | SHA256:563AABF21D40DAFFDFCC2970D396344804195067BBE0EF7451D85A1490FEA718 | |||
| 2516 | Trojan-Ransom.Win32.Crypmod.aaxv-5b73019c232adbd1627b986bfc476de96c230ad54a9a014932f3f32d814fc744.exe | C:\$Recycle.Bin\GDJZENAMV-DECRYPT.txt | binary | |
MD5:92F07FDE7A0FF8F81480B12793BE6E83 | SHA256:563AABF21D40DAFFDFCC2970D396344804195067BBE0EF7451D85A1490FEA718 | |||
| 2516 | Trojan-Ransom.Win32.Crypmod.aaxv-5b73019c232adbd1627b986bfc476de96c230ad54a9a014932f3f32d814fc744.exe | C:\Users\GDJZENAMV-DECRYPT.txt | binary | |
MD5:92F07FDE7A0FF8F81480B12793BE6E83 | SHA256:563AABF21D40DAFFDFCC2970D396344804195067BBE0EF7451D85A1490FEA718 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |