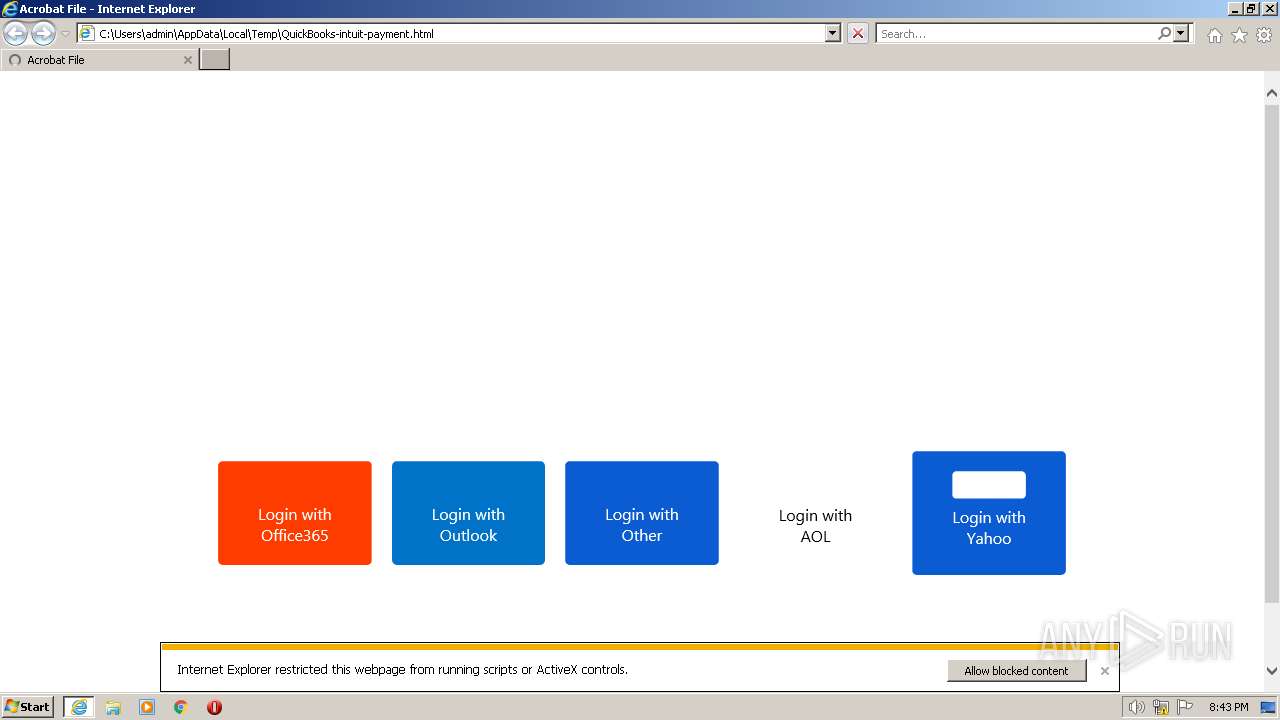
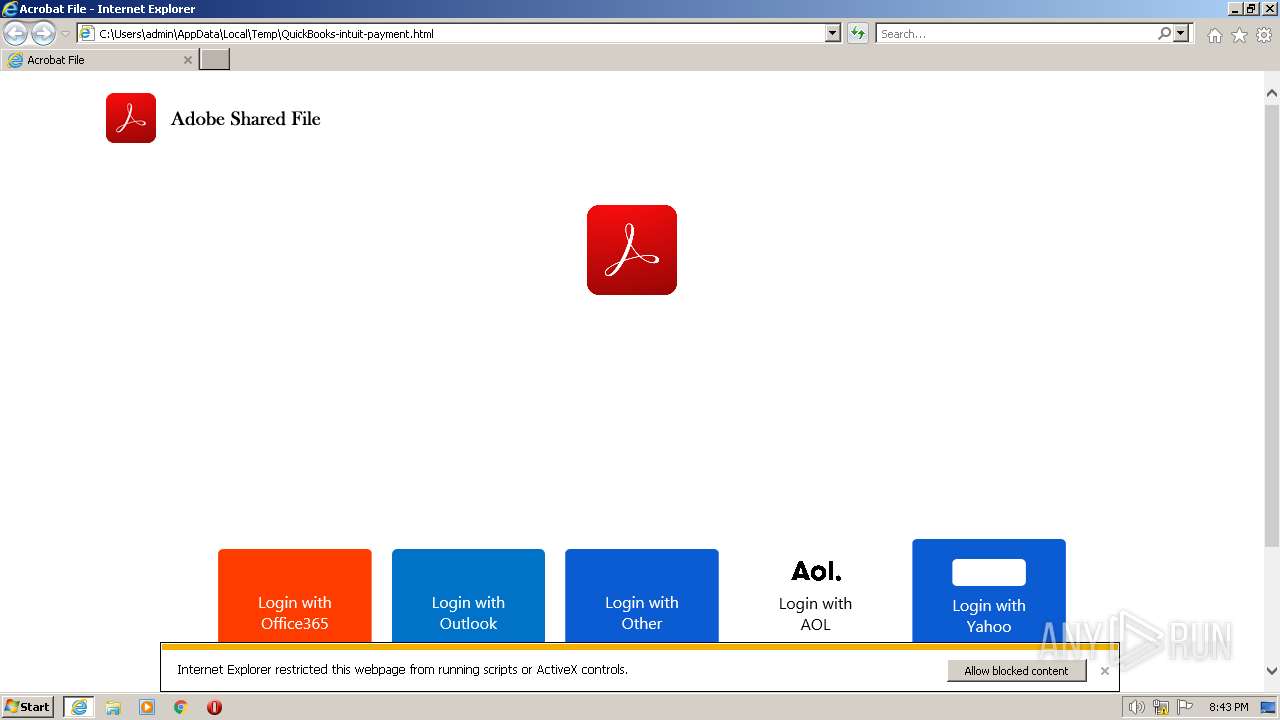
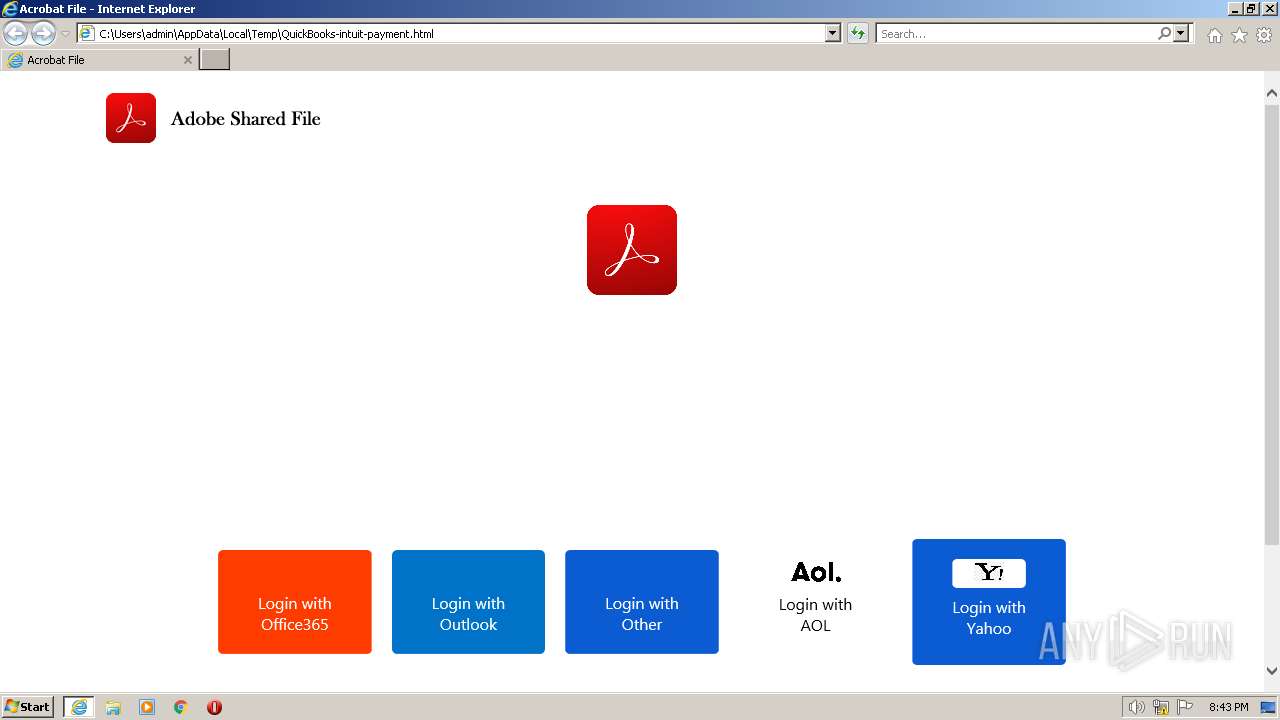
| File name: | QuickBooks-intuit-payment.html |
| Full analysis: | https://app.any.run/tasks/8dda1fb8-6156-4bce-84b5-b3b638c9a73d |
| Verdict: | Malicious activity |
| Analysis date: | May 15, 2023, 19:42:55 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, UTF-8 Unicode text, with CRLF line terminators |
| MD5: | 5970C8AEA450534D5101A77BCCE3A7E8 |
| SHA1: | 78C347285C43B78A48189F584E44B04B57E0D053 |
| SHA256: | A3C39646CE5065D8AA7E567F5CFF561B2C639AD2753C4694C480F0E416FD4D80 |
| SSDEEP: | 768:7GS43OcWkwJCrP/wUIm/5uQmuR8rQNAkWnQzTPTbQxCCWjQzF1gsEa:yAJgYQVR8rQukWnQ/PTbQkCWjQ51gsEa |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- iexplore.exe (PID: 3964)
- iexplore.exe (PID: 1924)
Create files in a temporary directory
- iexplore.exe (PID: 3964)
- iexplore.exe (PID: 1924)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .html | | | HyperText Markup Language (100) |
|---|
EXIF
HTML
| Title: | Acrobat File |
|---|---|
| Viewport: | width=device-width, initial-scale=1.0 |
| HTTPEquivXUACompatible: | IE=edge |
Total processes
40
Monitored processes
3
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1924 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3964 CREDAT:144385 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2232 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3964 CREDAT:398593 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3964 | "C:\Program Files\Internet Explorer\iexplore.exe" "C:\Users\admin\AppData\Local\Temp\QuickBooks-intuit-payment.html" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
80 796
Read events
80 384
Write events
390
Delete events
22
Modification events
| (PID) Process: | (3964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (3964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (3964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (3964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
0
Suspicious files
58
Text files
20
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1924 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:DFF21389C1F4DBA25792A050622EA7B3 | SHA256:2FF01E0F0F0222ED8B18C3DFE6A8B01FFCEA47B30555F0C00657321942218565 | |||
| 3964 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\favicon[1].ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 1924 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B398B80134F72209547439DB21AB308D_ADE4E4D3A3BCBCA5C39C54D362D88565 | binary | |
MD5:45A146C95440C0422D89B7655F8975B1 | SHA256:B20EE8288C8B8592C24AB45D5B01C7B23AD53278D381A4340FA8402B1A043CA1 | |||
| 1924 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B2FAF7692FD9FFBD64EDE317E42334BA_D7393C8F62BDE4D4CB606228BC7A711E | binary | |
MD5:A9A657BB9FBF982C38587EE2B9590A7D | SHA256:D08E18FF8411D67ED596EDCBF1AA36365D0CAB8F4DE48C7ABFDB4062C4AB2B9C | |||
| 1924 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:F50C35561F70DE54C3233710A66E3066 | SHA256:6141CC67D693DAD6250FB211A65D4BB830EEFEFD6CADFF498E1A342E2E9EDCA0 | |||
| 1924 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\aol[1].png | image | |
MD5:7C7CF7681AEE5E76CA1A7DBF2EC7C318 | SHA256:6A9935D6D50E144151E34C0B42B5222853231EE05F51533CC8F1DE146E275F8D | |||
| 1924 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B2FAF7692FD9FFBD64EDE317E42334BA_D7393C8F62BDE4D4CB606228BC7A711E | binary | |
MD5:D839DA0E42B3B52F59A38FBF3DEA7087 | SHA256:BE825D73E6D7CB1B5996C4C7D1A181AE0368AAF6FCF62D34AE29B8F608DDE452 | |||
| 1924 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B398B80134F72209547439DB21AB308D_ADE4E4D3A3BCBCA5C39C54D362D88565 | der | |
MD5:4E05FFEC40AD7B949E3208603989CA27 | SHA256:B1C55365D55E186E012B1CB00EEF1533DFC81741E384ED3270A8749BD71F9DBD | |||
| 1924 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:3AC860860707BAAF32469FA7CC7C0192 | SHA256:D015145D551ECD14916270EFAD773BBC9FD57FAD2228D2C24559F696C961D904 | |||
| 1924 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\CabCF77.tmp | compressed | |
MD5:3AC860860707BAAF32469FA7CC7C0192 | SHA256:D015145D551ECD14916270EFAD773BBC9FD57FAD2228D2C24559F696C961D904 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
28
TCP/UDP connections
98
DNS requests
22
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1924 | iexplore.exe | GET | 200 | 8.248.149.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?381e019789a55c9a | US | compressed | 4.70 Kb | whitelisted |
1924 | iexplore.exe | GET | 200 | 8.248.149.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?51b71478173405f8 | US | compressed | 4.70 Kb | whitelisted |
1924 | iexplore.exe | GET | 200 | 8.248.149.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?341bed8607e1ae36 | US | compressed | 4.70 Kb | whitelisted |
1924 | iexplore.exe | GET | 200 | 8.248.149.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?211fb4cdac3a9cb0 | US | compressed | 4.70 Kb | whitelisted |
1924 | iexplore.exe | GET | 200 | 8.248.149.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?b8ffa55856bb0726 | US | compressed | 4.70 Kb | whitelisted |
1924 | iexplore.exe | GET | 200 | 104.18.32.68:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | US | binary | 2.18 Kb | whitelisted |
1924 | iexplore.exe | GET | 200 | 8.248.149.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?3c253398292a2075 | US | compressed | 4.70 Kb | whitelisted |
1924 | iexplore.exe | GET | 200 | 8.248.149.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?84429901c55bc80e | US | compressed | 4.70 Kb | whitelisted |
1924 | iexplore.exe | GET | 200 | 8.248.149.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?41688a9f1cd5605f | US | compressed | 4.70 Kb | whitelisted |
1924 | iexplore.exe | GET | 200 | 172.64.155.188:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | US | der | 1.42 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3404 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1924 | iexplore.exe | 69.16.175.42:443 | code.jquery.com | STACKPATH-CDN | US | malicious |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1924 | iexplore.exe | 18.66.97.87:443 | cdn.glitch.me | — | US | unknown |
1924 | iexplore.exe | 151.101.2.132:443 | cdn.glitch.global | FASTLY | US | malicious |
1924 | iexplore.exe | 104.17.24.14:443 | cdnjs.cloudflare.com | CLOUDFLARENET | — | suspicious |
1924 | iexplore.exe | 142.250.186.170:443 | ajax.googleapis.com | GOOGLE | US | whitelisted |
1924 | iexplore.exe | 104.18.26.189:443 | cdn2.downdetector.com | CLOUDFLARENET | — | suspicious |
1924 | iexplore.exe | 91.198.174.208:443 | upload.wikimedia.org | WIKIMEDIA | US | suspicious |
1924 | iexplore.exe | 66.29.154.202:443 | www.clipartmax.com | NAMECHEAP-NET | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
code.jquery.com |
| whitelisted |
cdn.glitch.global |
| malicious |
ajax.googleapis.com |
| whitelisted |
cdnjs.cloudflare.com |
| whitelisted |
cdn.glitch.me |
| whitelisted |
cdn2.downdetector.com |
| suspicious |
www.clipartmax.com |
| suspicious |
cdn.glitch.com |
| shared |
upload.wikimedia.org |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |