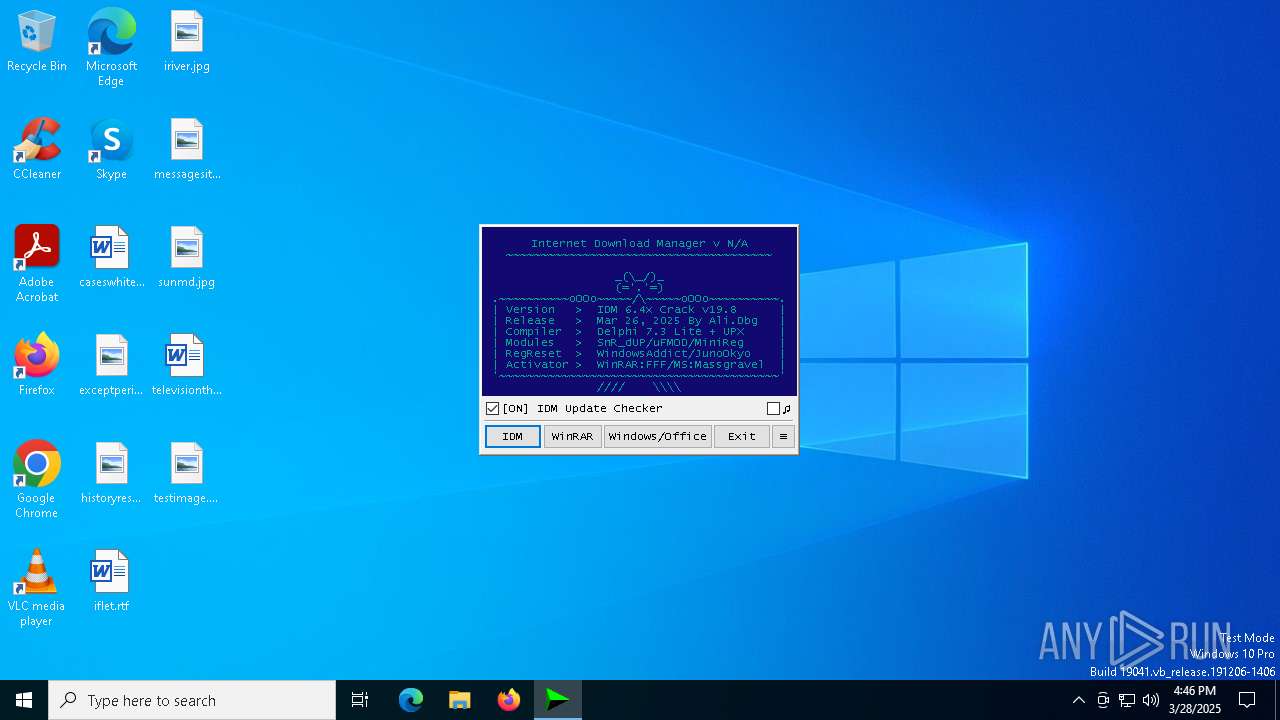
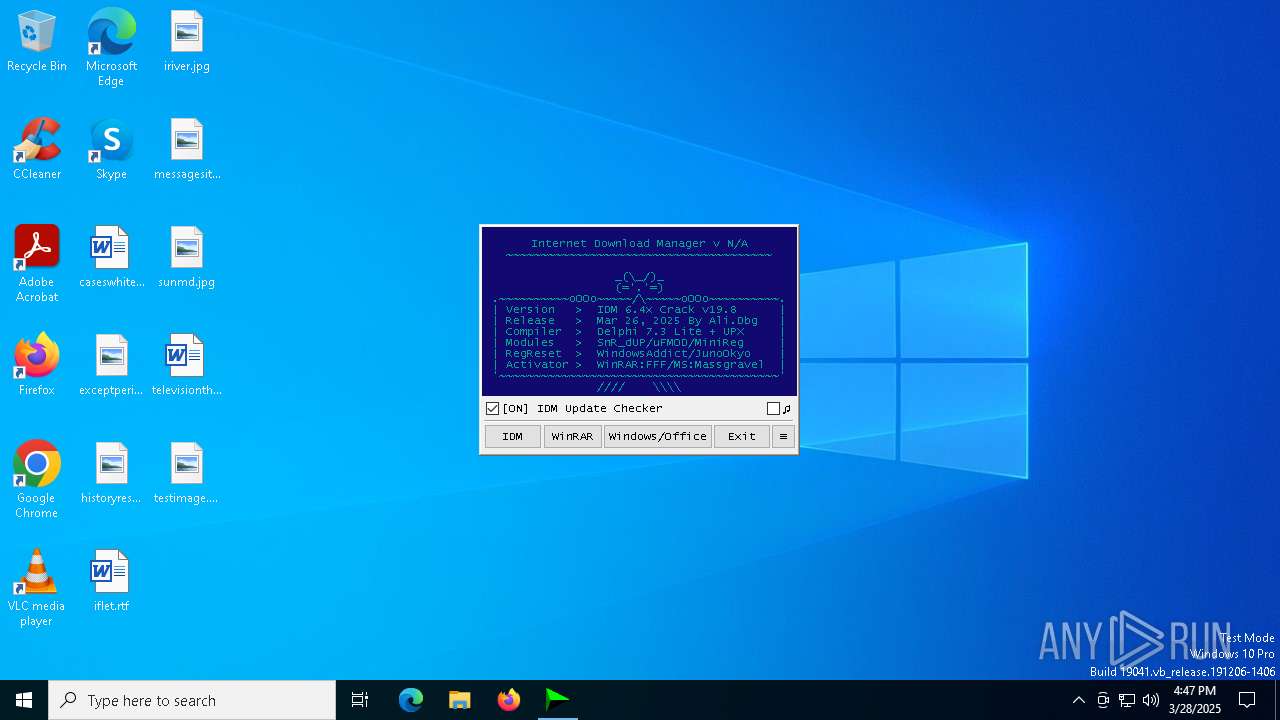
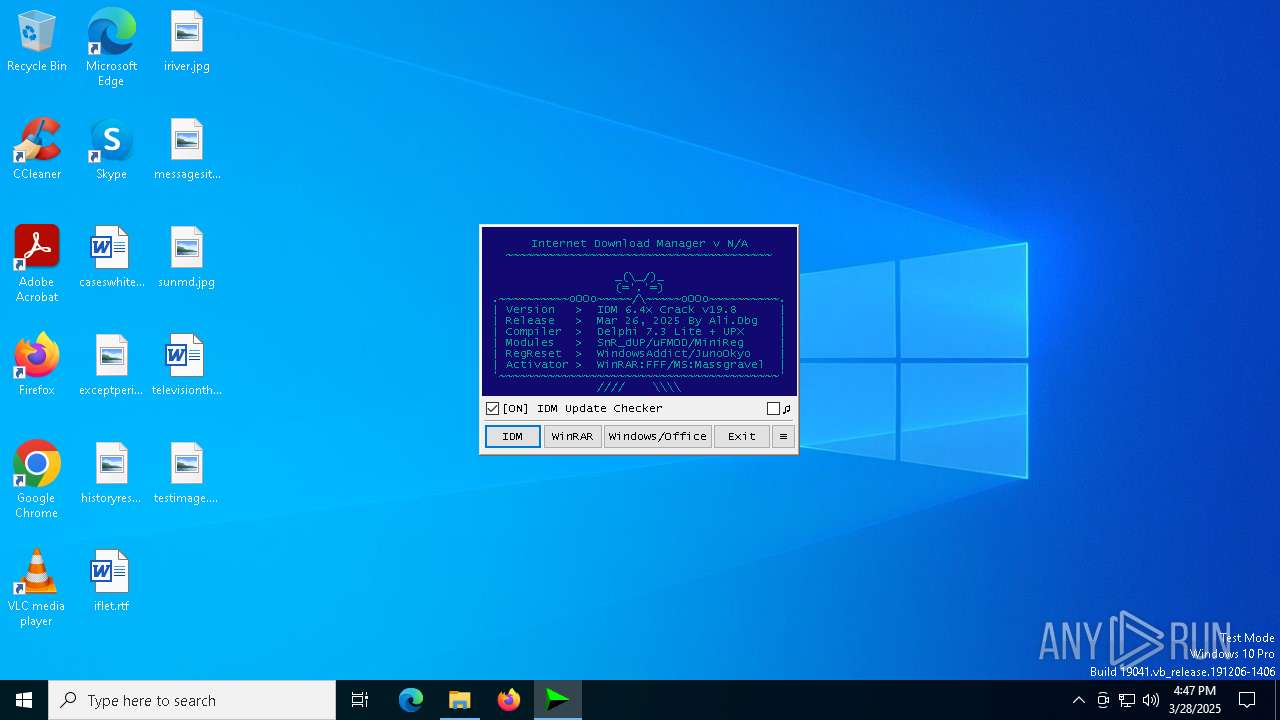
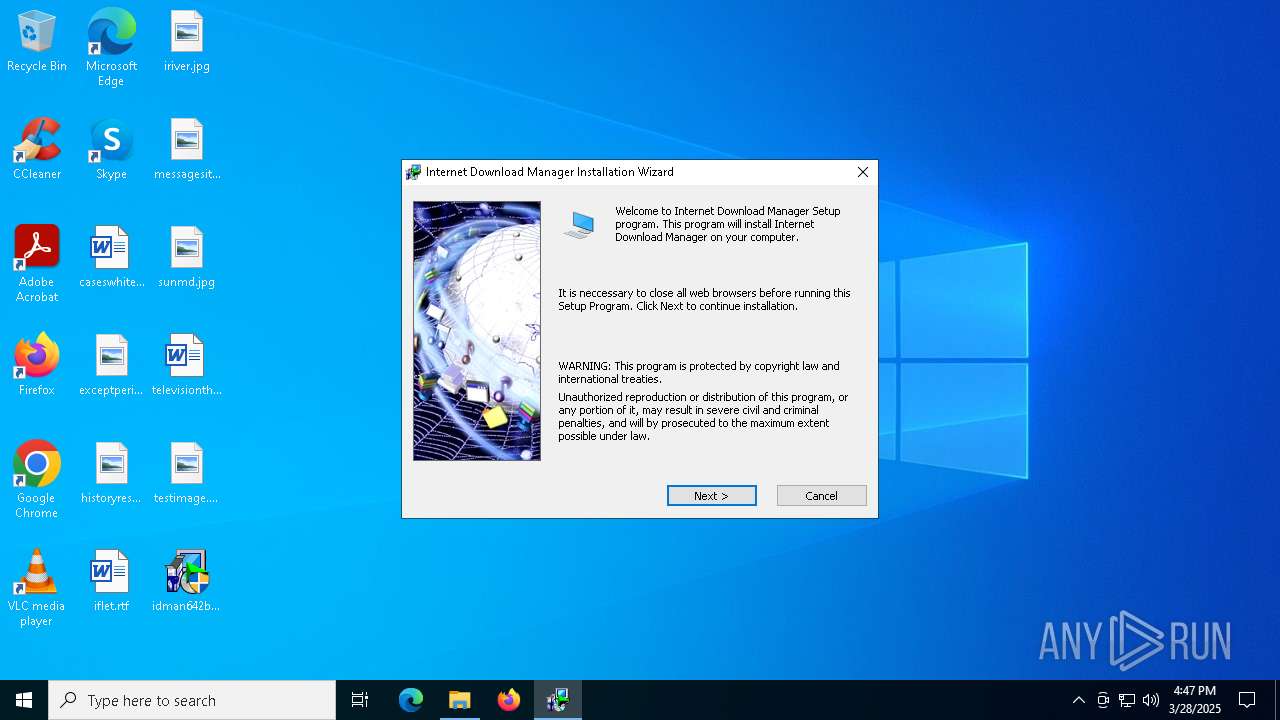
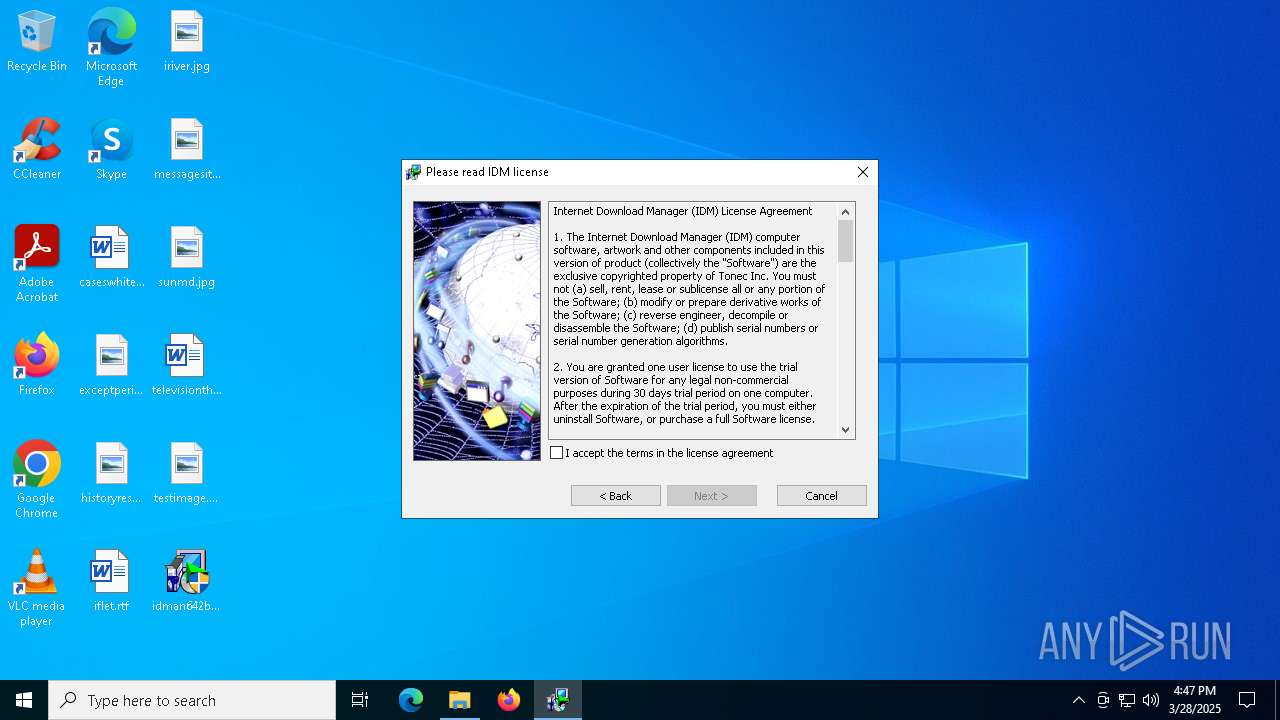
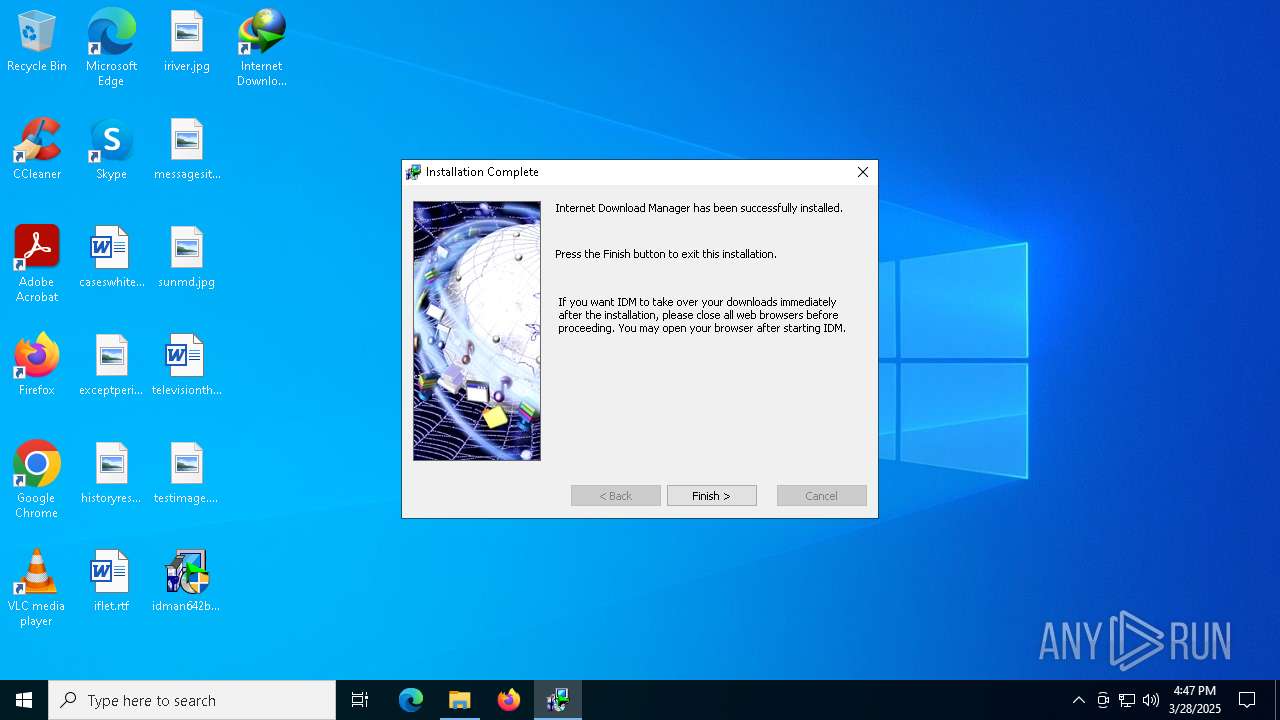
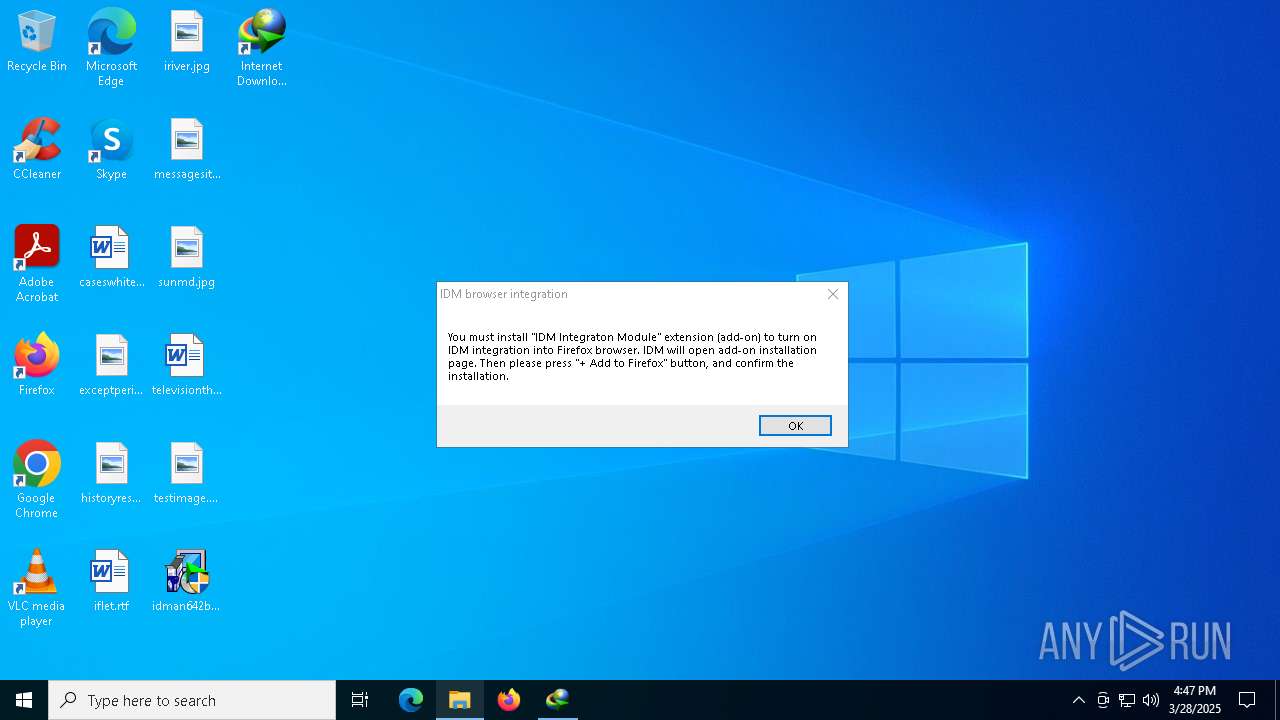
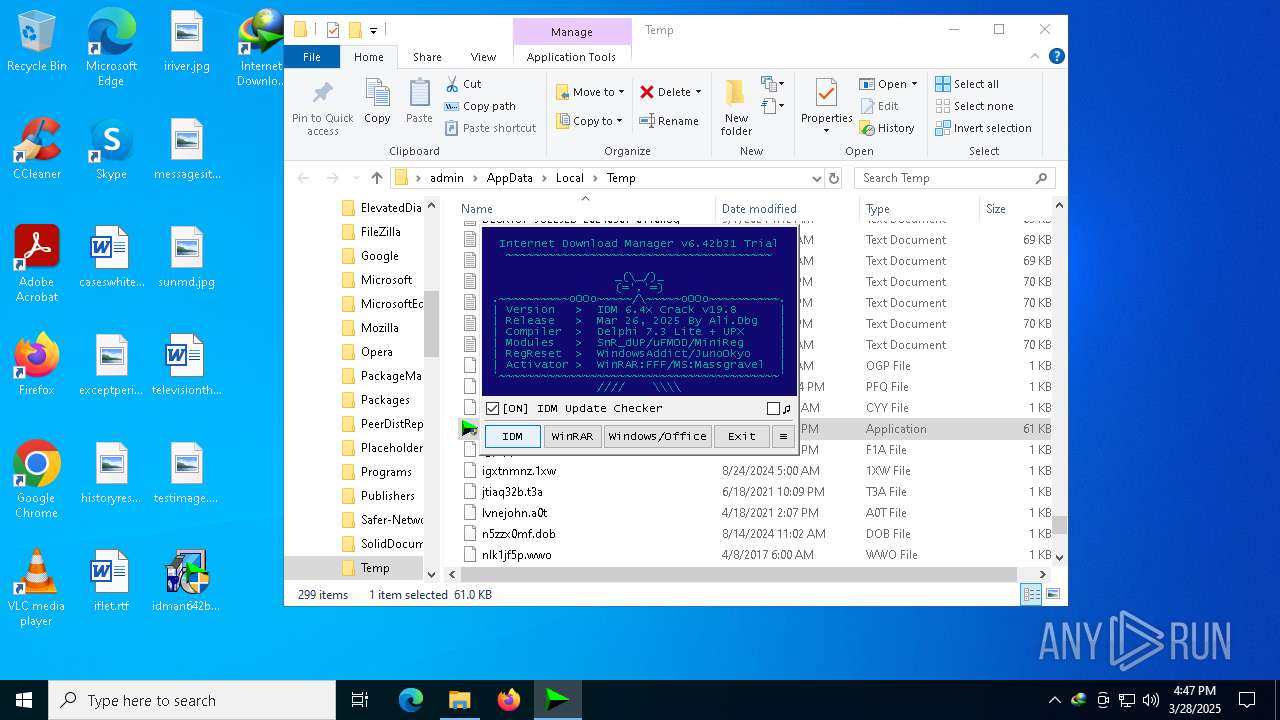
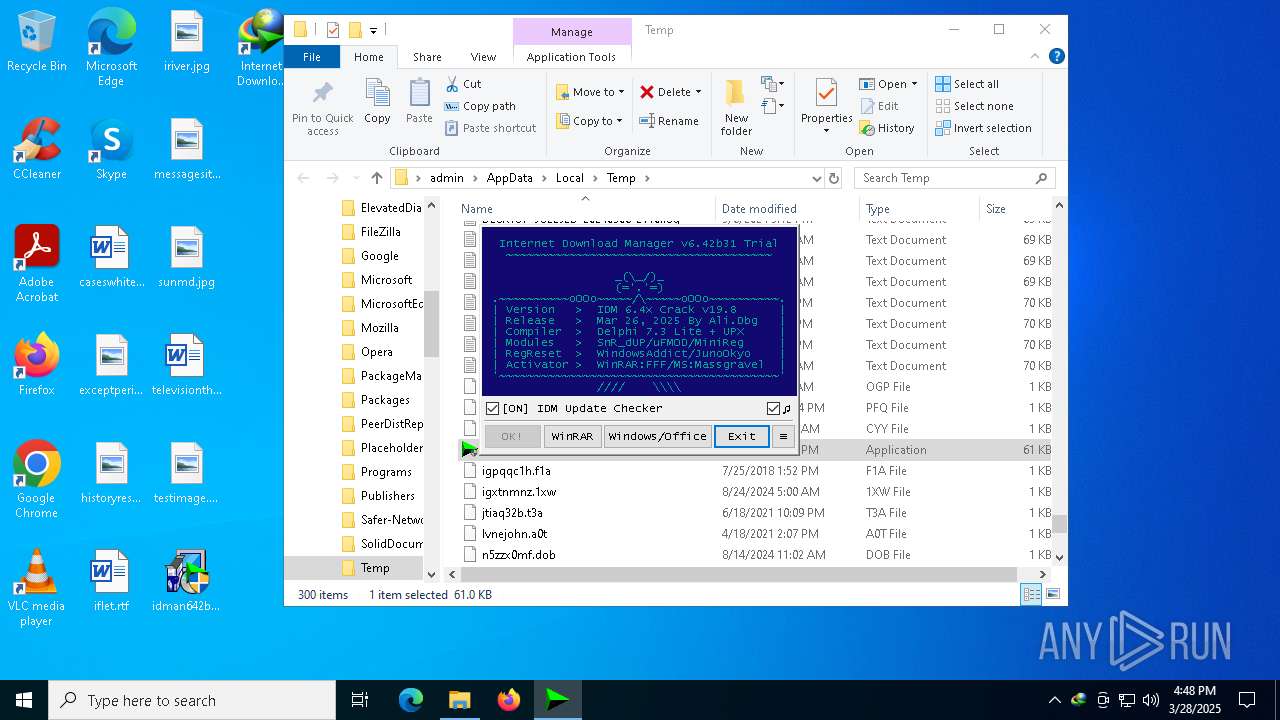
| File name: | IDM_6.4x_Crack_v19.8.exe |
| Full analysis: | https://app.any.run/tasks/ae8d4d71-12ac-4b2d-8776-1665a5f3b260 |
| Verdict: | Malicious activity |
| Analysis date: | March 28, 2025, 16:46:39 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 3 sections |
| MD5: | 147667512461439ABE9690424442C62D |
| SHA1: | 066BEFFBAA9BA1F5566CC02DCB9E24C04AEEDE28 |
| SHA256: | A3C228EB6FDE01355FECEFE5B450B9E75453EE3290497736ED52ED6DD777516A |
| SSDEEP: | 1536:Ve+j44XuunMS2dIZVs8wfQytejHpWkbhzAKYfXgRC4tPQ2NPxA9:Ve+04X9MksZlCHp34gRJNlxA9 |
MALICIOUS
Sends HTTP request (SCRIPT)
- wscript.exe (PID: 6944)
- wscript.exe (PID: 7232)
Deletes a file (SCRIPT)
- wscript.exe (PID: 6944)
- wscript.exe (PID: 7232)
Creates internet connection object (SCRIPT)
- wscript.exe (PID: 6944)
- wscript.exe (PID: 7232)
Accesses environment variables (SCRIPT)
- wscript.exe (PID: 6944)
- wscript.exe (PID: 7232)
Opens an HTTP connection (SCRIPT)
- wscript.exe (PID: 6944)
- wscript.exe (PID: 7232)
Registers / Runs the DLL via REGSVR32.EXE
- IDM1.tmp (PID: 5728)
- IDMan.exe (PID: 5956)
- Uninstall.exe (PID: 616)
- IDMan.exe (PID: 7616)
Changes the autorun value in the registry
- rundll32.exe (PID: 5124)
Starts NET.EXE for service management
- Uninstall.exe (PID: 616)
- net.exe (PID: 8100)
SUSPICIOUS
The process executes VB scripts
- IDM_6.4x_Crack_v19.8.exe (PID: 900)
- IDM_6.4x_Crack_v19.8.exe (PID: 8120)
Gets full path of the running script (SCRIPT)
- wscript.exe (PID: 6944)
- wscript.exe (PID: 7232)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 6944)
- wscript.exe (PID: 7232)
Starts application with an unusual extension
- idman642build31.exe (PID: 6512)
- cmd.exe (PID: 6036)
Creates a software uninstall entry
- IDM1.tmp (PID: 5728)
The process creates files with name similar to system file names
- IDM1.tmp (PID: 5728)
Creates/Modifies COM task schedule object
- IDM1.tmp (PID: 5728)
- IDMan.exe (PID: 5956)
- regsvr32.exe (PID: 6136)
Reads security settings of Internet Explorer
- IDM1.tmp (PID: 5728)
- IDMan.exe (PID: 5956)
- Uninstall.exe (PID: 616)
- IDMan.exe (PID: 4572)
Uses RUNDLL32.EXE to load library
- Uninstall.exe (PID: 616)
Executable content was dropped or overwritten
- rundll32.exe (PID: 5124)
- drvinst.exe (PID: 3272)
- IDMan.exe (PID: 5956)
- IDM_6.4x_Crack_v19.8.exe (PID: 8120)
Drops a system driver (possible attempt to evade defenses)
- rundll32.exe (PID: 5124)
- drvinst.exe (PID: 3272)
Creates files in the driver directory
- drvinst.exe (PID: 3272)
Creates or modifies Windows services
- Uninstall.exe (PID: 616)
Executing commands from a ".bat" file
- IDM_6.4x_Crack_v19.8.exe (PID: 8120)
- cmd.exe (PID: 6036)
Uses REG/REGEDIT.EXE to modify registry
- IDM_6.4x_Crack_v19.8.exe (PID: 8120)
- cmd.exe (PID: 684)
- cmd.exe (PID: 6036)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 7332)
- cmd.exe (PID: 6036)
- IDM_6.4x_Crack_v19.8.exe (PID: 8120)
Application launched itself
- cmd.exe (PID: 7332)
- cmd.exe (PID: 6036)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 6036)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 6036)
- cmd.exe (PID: 7744)
- cmd.exe (PID: 208)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 6036)
Hides command output
- cmd.exe (PID: 7744)
- cmd.exe (PID: 684)
INFO
Checks supported languages
- IDM_6.4x_Crack_v19.8.exe (PID: 900)
- IDM1.tmp (PID: 5728)
- idmBroker.exe (PID: 6372)
- IDMan.exe (PID: 5956)
- IDMan.exe (PID: 7616)
- Uninstall.exe (PID: 616)
- IDMIntegrator64.exe (PID: 3396)
Reads the computer name
- IDM_6.4x_Crack_v19.8.exe (PID: 900)
- idmBroker.exe (PID: 6372)
- IDMIntegrator64.exe (PID: 3396)
INTERNETDOWNLOADMANAGER mutex has been found
- IDM1.tmp (PID: 5728)
- IDMan.exe (PID: 5956)
- IDMan.exe (PID: 7616)
- IDMan.exe (PID: 4572)
- IDMIntegrator64.exe (PID: 3396)
Creates files in the program directory
- IDM1.tmp (PID: 5728)
- IDMan.exe (PID: 5956)
Manual execution by a user
- Taskmgr.exe (PID: 6184)
- Taskmgr.exe (PID: 3240)
- idman642build31.exe (PID: 6456)
- idman642build31.exe (PID: 6512)
- firefox.exe (PID: 5036)
- IDM_6.4x_Crack_v19.8.exe (PID: 6724)
- IDM_6.4x_Crack_v19.8.exe (PID: 8120)
- IDMan.exe (PID: 4572)
Create files in a temporary directory
- IDM_6.4x_Crack_v19.8.exe (PID: 900)
- idman642build31.exe (PID: 6512)
- IDM1.tmp (PID: 5728)
- IDMan.exe (PID: 5956)
- rundll32.exe (PID: 5124)
- reg.exe (PID: 8084)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 3240)
Creates files or folders in the user directory
- IDM1.tmp (PID: 5728)
- IDMan.exe (PID: 5956)
Reads the software policy settings
- IDMan.exe (PID: 5956)
- IDMan.exe (PID: 4572)
Reads the machine GUID from the registry
- IDMan.exe (PID: 5956)
- IDMan.exe (PID: 4572)
Process checks computer location settings
- IDMan.exe (PID: 5956)
- Uninstall.exe (PID: 616)
Application launched itself
- firefox.exe (PID: 5036)
- firefox.exe (PID: 1180)
The sample compiled with english language support
- IDMan.exe (PID: 5956)
- rundll32.exe (PID: 5124)
- drvinst.exe (PID: 3272)
- IDM_6.4x_Crack_v19.8.exe (PID: 8120)
Checks operating system version
- cmd.exe (PID: 6036)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 7552)
- powershell.exe (PID: 7104)
Changes the display of characters in the console
- cmd.exe (PID: 6036)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .dll | | | Win32 Dynamic Link Library (generic) (38.3) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (26.2) |
| .exe | | | Win16/32 Executable Delphi generic (12) |
| .exe | | | Generic Win/DOS Executable (11.6) |
| .exe | | | DOS Executable Generic (11.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 57344 |
| InitializedDataSize: | 8192 |
| UninitializedDataSize: | 188416 |
| EntryPoint: | 0x3cc30 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
259
Monitored processes
114
Malicious processes
10
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | C:\WINDOWS\system32\cmd.exe /c powershell.exe "(Get-Date).ToString('yyyyMMdd-HHmmssfff')" | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 616 | "C:\Program Files (x86)\Internet Download Manager\Uninstall.exe" -instdriv | C:\Program Files (x86)\Internet Download Manager\Uninstall.exe | — | IDMan.exe | |||||||||||
User: admin Company: Tonec Inc. Integrity Level: HIGH Description: Internet Download Manager installer Exit code: 1 Version: 6, 42, 20, 1 Modules
| |||||||||||||||
| 632 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 660 | "C:\Users\admin\AppData\Local\Temp\IDM_6.4x_Crack_v19.8.exe" | C:\Users\admin\AppData\Local\Temp\IDM_6.4x_Crack_v19.8.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 684 | /s "C:\Program Files (x86)\Internet Download Manager\IDMIECC64.dll" | C:\Windows\System32\regsvr32.exe | — | regsvr32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 684 | C:\WINDOWS\system32\cmd.exe /c reg query "HKU\S-1-5-21-1693682860-607145093-2874071422-1001\Software\DownloadManager" /v ExePath 2>nul | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 864 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 900 | "C:\Users\admin\AppData\Local\Temp\IDM_6.4x_Crack_v19.8.exe" | C:\Users\admin\AppData\Local\Temp\IDM_6.4x_Crack_v19.8.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1096 | "C:\Windows\System32\regsvr32.exe" /s "C:\Program Files (x86)\Internet Download Manager\IDMIECC64.dll" | C:\Windows\SysWOW64\regsvr32.exe | — | IDM1.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1132 | powershell.exe "(Get-Date).ToString('yyyyMMdd-HHmmssfff')" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
62 336
Read events
61 418
Write events
718
Delete events
200
Modification events
| (PID) Process: | (900) IDM_6.4x_Crack_v19.8.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Script Host\Settings |
| Operation: | write | Name: | Enabled |
Value: 1 | |||
| (PID) Process: | (900) IDM_6.4x_Crack_v19.8.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Wow6432Node\Microsoft\Windows Script Host\Settings |
| Operation: | write | Name: | Enabled |
Value: 1 | |||
| (PID) Process: | (900) IDM_6.4x_Crack_v19.8.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows Script Host\Settings |
| Operation: | write | Name: | Enabled |
Value: 1 | |||
| (PID) Process: | (900) IDM_6.4x_Crack_v19.8.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | DisableRegistryTools |
Value: 0 | |||
| (PID) Process: | (900) IDM_6.4x_Crack_v19.8.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | DisableCMD |
Value: 0 | |||
| (PID) Process: | (900) IDM_6.4x_Crack_v19.8.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | DisableTaskMgr |
Value: 0 | |||
| (PID) Process: | (900) IDM_6.4x_Crack_v19.8.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer |
| Operation: | write | Name: | NoRun |
Value: 0 | |||
| (PID) Process: | (900) IDM_6.4x_Crack_v19.8.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer |
| Operation: | write | Name: | DisallowRun |
Value: 0 | |||
| (PID) Process: | (900) IDM_6.4x_Crack_v19.8.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\PowerShell |
| Operation: | write | Name: | EnableScripts |
Value: 1 | |||
| (PID) Process: | (900) IDM_6.4x_Crack_v19.8.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\PowerShell\1\ShellIds\ScriptedDiagnostics |
| Operation: | write | Name: | ExecutionPolicy |
Value: Bypass | |||
Executable files
16
Suspicious files
99
Text files
36
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5728 | IDM1.tmp | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\Uninstall IDM.lnk | lnk | |
MD5:3B8A5E40DF4A20C583B1D38404D6B4F7 | SHA256:48B43CE679AEDA9A3B79871D751841B86A423AD51C740AE92B53A3119643B986 | |||
| 5728 | IDM1.tmp | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\Uninstall IDM.lnk | binary | |
MD5:C998BF0642CB4B6CE249B1649C8ECE69 | SHA256:84FD67EDAA92EBCB5CE5A1B83A795C25516A694D3D9EFFDDDDA12536498BCE8D | |||
| 5728 | IDM1.tmp | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\license.lnk | binary | |
MD5:8930596AA344075918075BEEE9118AB1 | SHA256:0A80EB2182848B21A24ACC4B432E7D7999B79FFA8E7494221822FDAC3F9B9A4A | |||
| 5728 | IDM1.tmp | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\IDM Help.lnk | binary | |
MD5:55A05F30E839732BB84A6AEA19BF2A85 | SHA256:C5A04FA6B8039F43242D5211586D67C47C951508944F4A748BDB3A557794810E | |||
| 5728 | IDM1.tmp | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\license.lnk | binary | |
MD5:809655C13AEA292386A77A0DCA9AF68F | SHA256:23C7D5F19AD23EF9C54790459F22535C0A5C9144EC9EEB066A3D4D853B07529C | |||
| 3240 | Taskmgr.exe | C:\Users\admin\AppData\Local\D3DSCache\3534848bb9f4cb71\F4EB2D6C-ED2B-4BDD-AD9D-F913287E6768.lock | text | |
MD5:F49655F856ACB8884CC0ACE29216F511 | SHA256:7852FCE59C67DDF1D6B8B997EAA1ADFAC004A9F3A91C37295DE9223674011FBA | |||
| 5728 | IDM1.tmp | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\IDM Help.lnk | binary | |
MD5:46B0FA14C512EAD98EF8B28CABE51B82 | SHA256:62DF8927E2D53D0E8B696E25724C56FE5F4B7C49C96E96FF66E4FB8FB2AFCA8D | |||
| 5728 | IDM1.tmp | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\Internet Download Manager.lnk | binary | |
MD5:134F42E88F573B45CB707FBC69312002 | SHA256:CBF77E8C2FEA98236FCBB33A3A4B1DC5A5EF970ECCB6E987629A3C2374288A17 | |||
| 5728 | IDM1.tmp | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\TUTORIALS.lnk | lnk | |
MD5:C3BE41EF238E75B1EC01343178904632 | SHA256:9E18C56AE53160015E0B278921CC36D9DC9100E4694B43CA487C36AF1631EC2C | |||
| 5728 | IDM1.tmp | C:\Users\admin\AppData\Local\Temp\IDM_Setup_Temp\IDMSetup2.log | binary | |
MD5:5A032ACD38AB177AE8FBD17D52335C22 | SHA256:10F2E057D9A43BC3E7C1D26CA19BC84E43BEB32D79A02EE6744468A2A0FDD808 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
20
TCP/UDP connections
53
DNS requests
94
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5964 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1180 | firefox.exe | POST | 200 | 184.24.77.62:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
1180 | firefox.exe | POST | 200 | 142.250.185.131:80 | http://o.pki.goog/we2 | unknown | — | — | whitelisted |
1180 | firefox.exe | POST | 200 | 142.250.185.131:80 | http://o.pki.goog/s/wr3/UTA | unknown | — | — | whitelisted |
1180 | firefox.exe | POST | 200 | 142.250.185.131:80 | http://o.pki.goog/we2 | unknown | — | — | whitelisted |
1180 | firefox.exe | POST | 200 | 142.250.185.131:80 | http://o.pki.goog/s/wr3/UTA | unknown | — | — | whitelisted |
4156 | SystemSettings.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
4156 | SystemSettings.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6972 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5964 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6944 | wscript.exe | 188.114.96.3:443 | idm.0dy.ir | CLOUDFLARENET | NL | unknown |
3216 | svchost.exe | 172.172.255.218:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5364 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 20.190.159.23:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
6972 | backgroundTaskHost.exe | 20.223.35.26:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6972 | backgroundTaskHost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
idm.0dy.ir |
| unknown |
client.wns.windows.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |