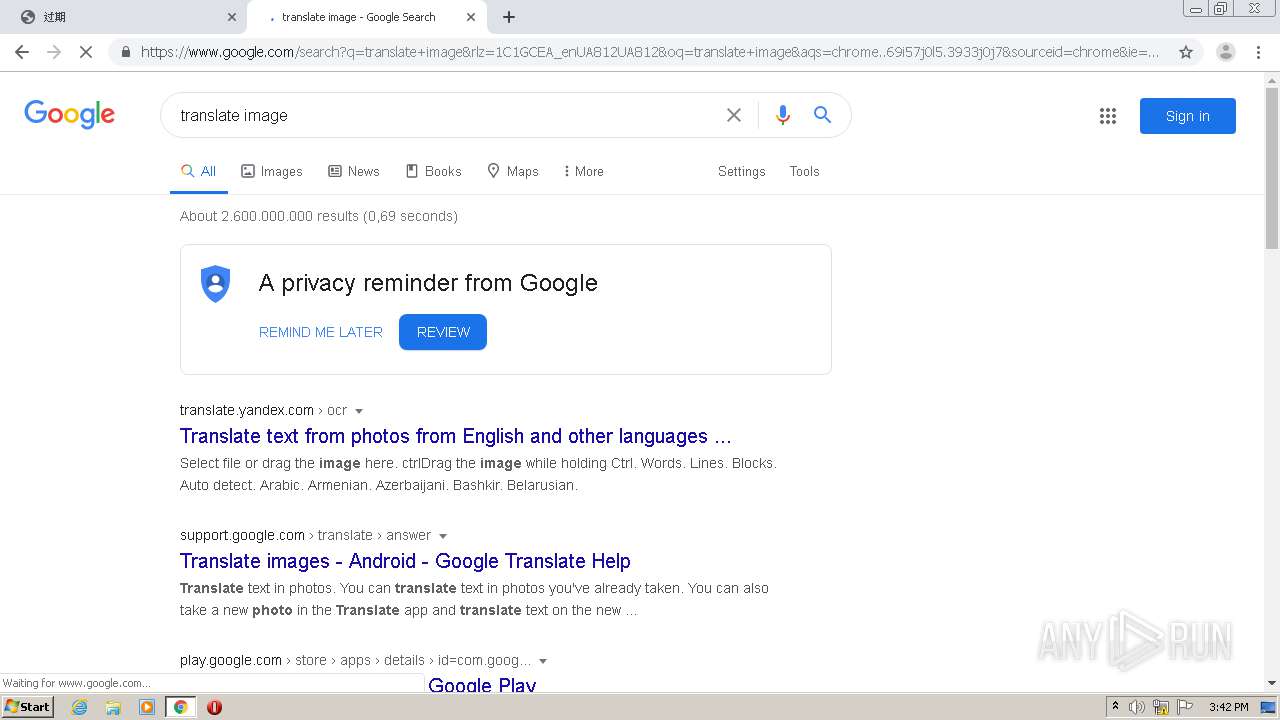
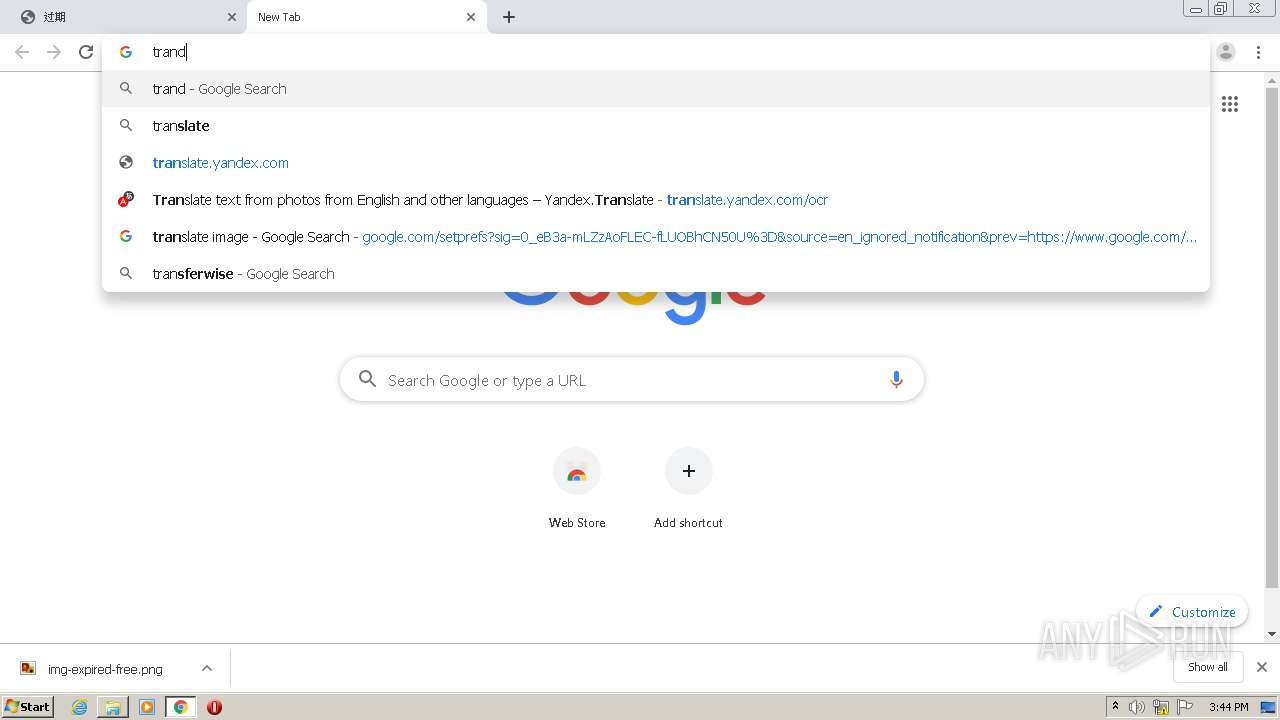
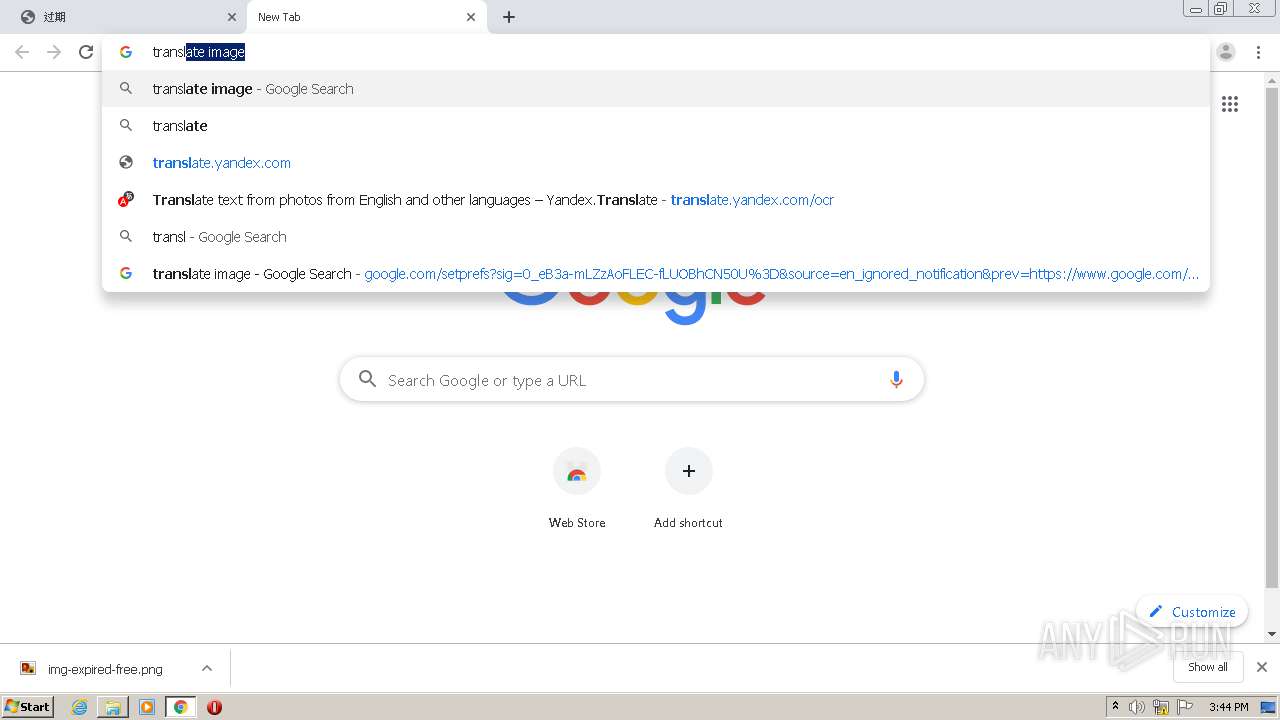
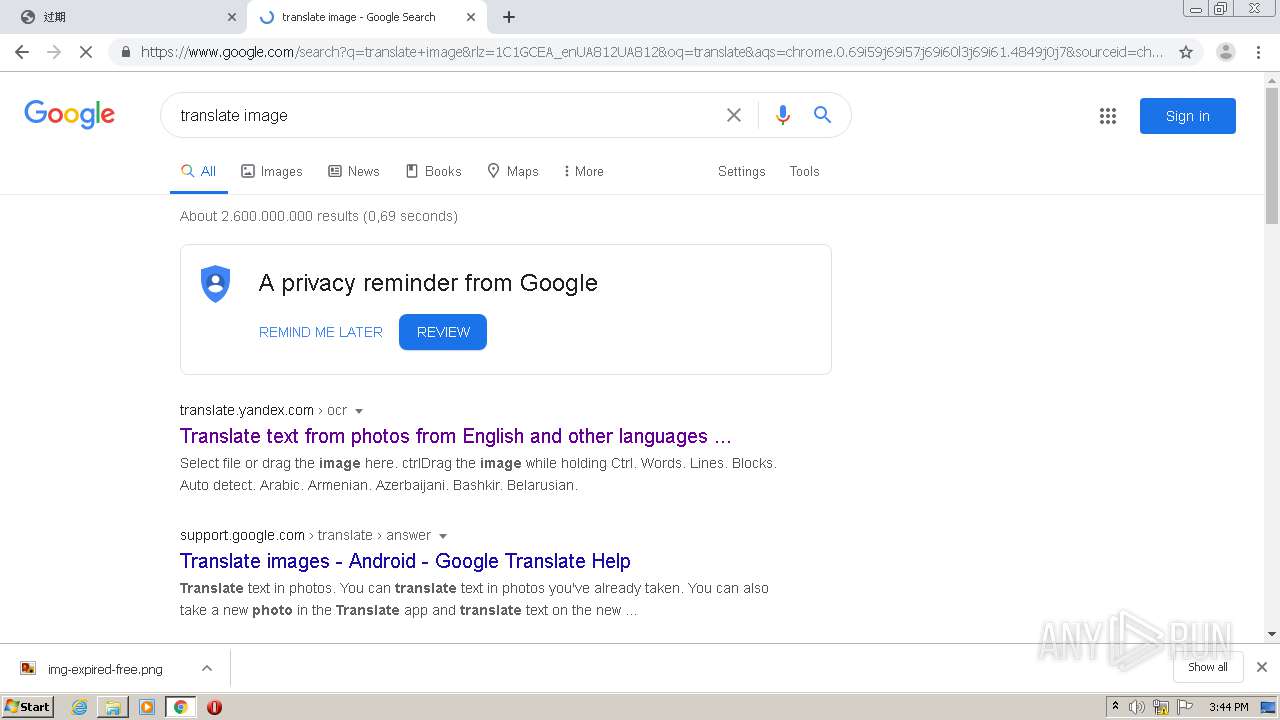
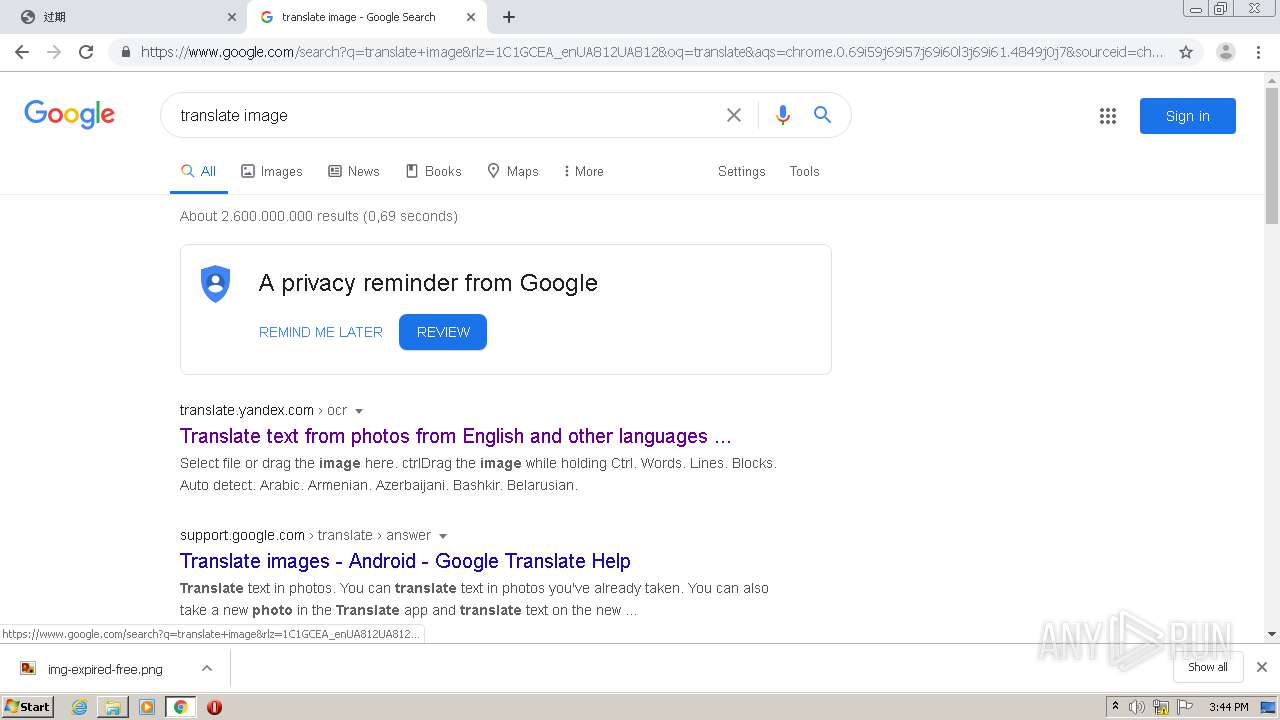
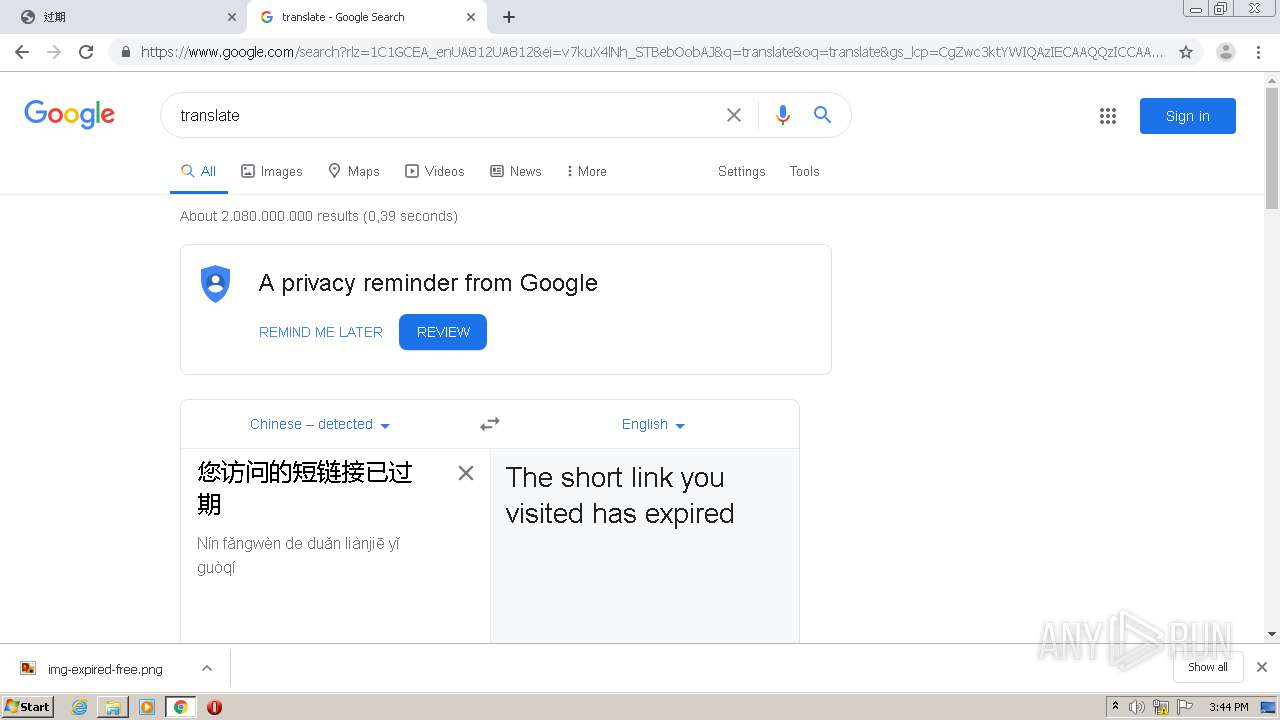
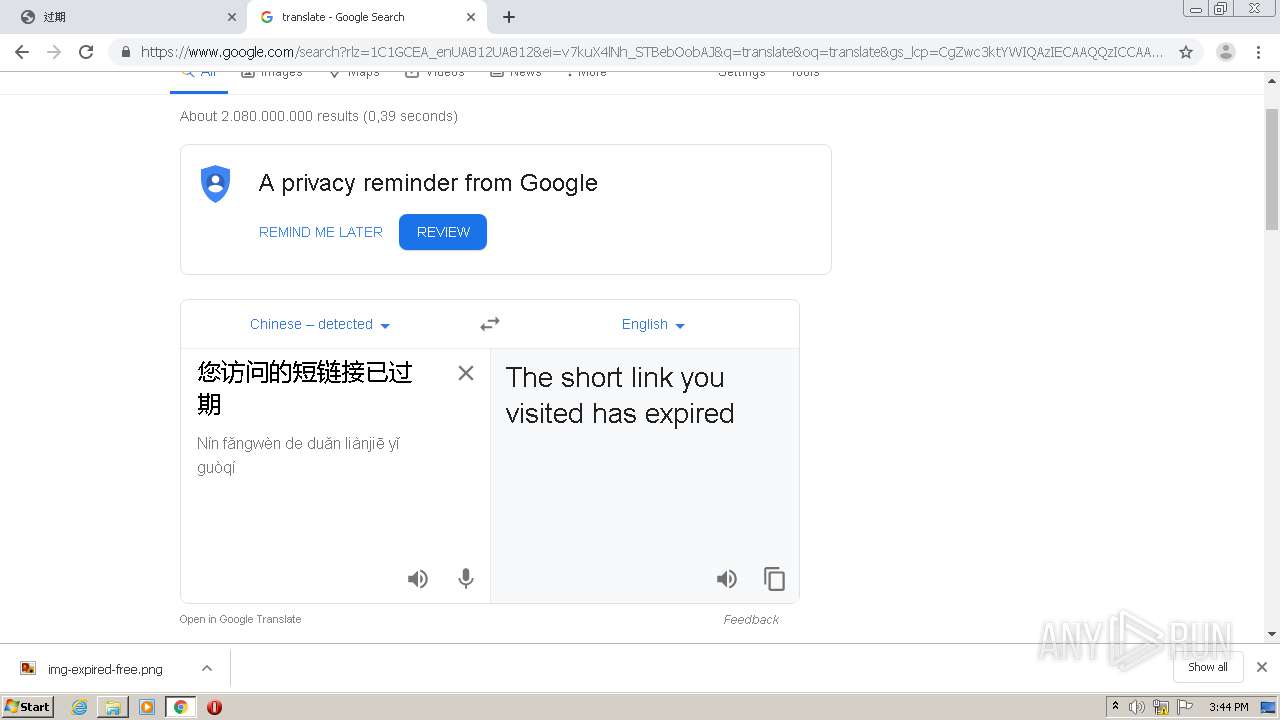
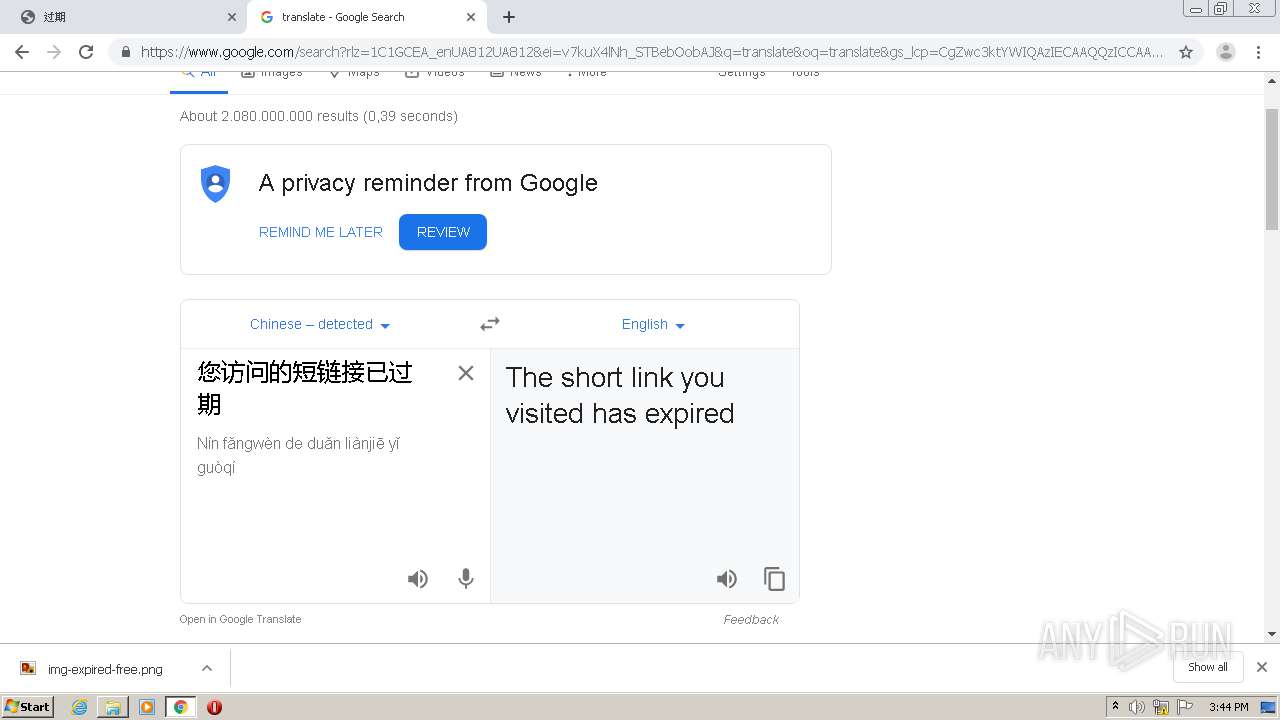
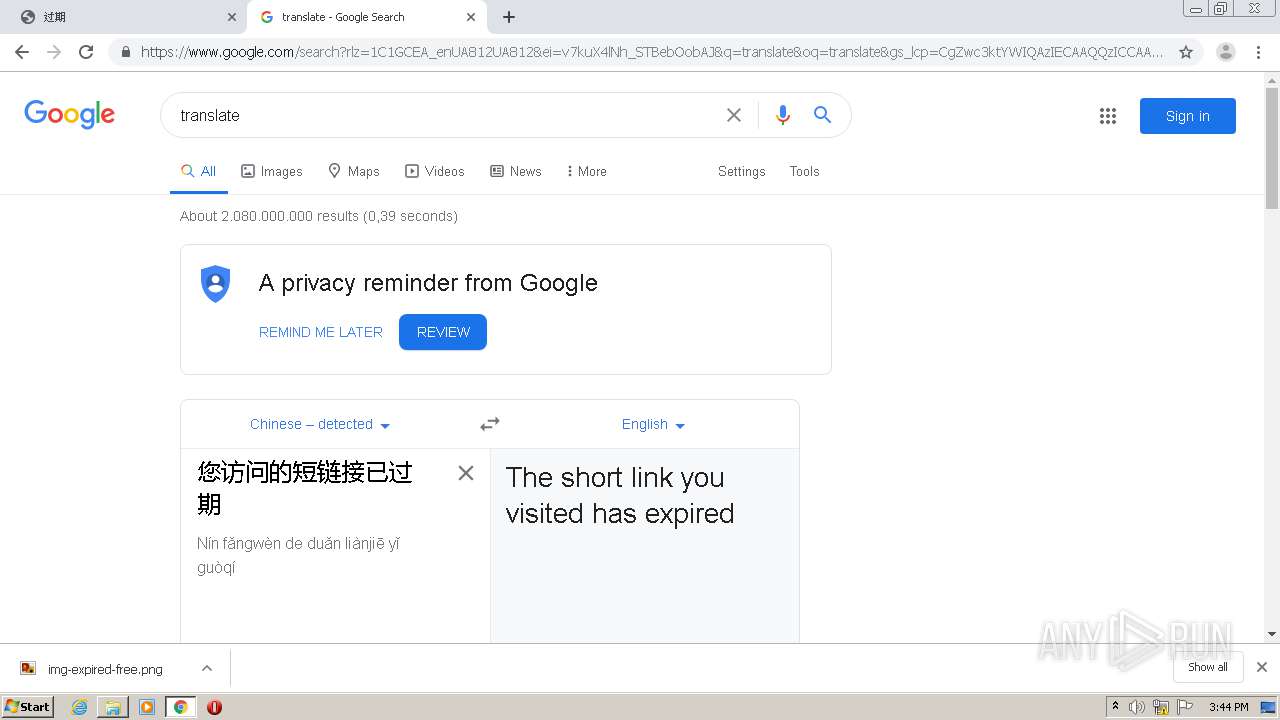
| URL: | http://mrw.so/5ikucu |
| Full analysis: | https://app.any.run/tasks/90cc892d-9942-4805-95bc-497d56829e0c |
| Verdict: | Malicious activity |
| Analysis date: | August 08, 2020, 14:40:35 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 6A2E155E0B439C30D9F557B5DB04FB93 |
| SHA1: | 4BF3EC29F3F20B1F4ECB8C793117E08DF9424077 |
| SHA256: | A3ACFE4AB51B4562E607940B5198CEC601E2FB5F8CDFFB5CC0DA03097C4A45F5 |
| SSDEEP: | 3:N1KTCiK4/H:Cb/ |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Reads the hosts file
- chrome.exe (PID: 1840)
- chrome.exe (PID: 2092)
Reads settings of System Certificates
- chrome.exe (PID: 1840)
Reads Internet Cache Settings
- chrome.exe (PID: 2092)
Application launched itself
- chrome.exe (PID: 2092)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
77
Monitored processes
33
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 544 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=2412 --on-initialized-event-handle=324 --parent-handle=328 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1132 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1012,12384402129235495018,323417566610675219,131072 --enable-features=PasswordImport --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=454779800454749030 --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2512 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1840 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1012,12384402129235495018,323417566610675219,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --service-request-channel-token=6826751727028570630 --mojo-platform-channel-handle=1628 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2092 | "C:\Program Files\Google\Chrome\Application\chrome.exe" "http://mrw.so/5ikucu" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2248 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1012,12384402129235495018,323417566610675219,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=9571467222736180475 --mojo-platform-channel-handle=3384 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2288 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1012,12384402129235495018,323417566610675219,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=17946476417383228672 --mojo-platform-channel-handle=3496 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2396 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1012,12384402129235495018,323417566610675219,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=5368779786164132788 --mojo-platform-channel-handle=3640 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2408 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1012,12384402129235495018,323417566610675219,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=14030039912735704966 --mojo-platform-channel-handle=3276 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2488 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=75.0.3770.100 --initial-client-data=0x7c,0x80,0x84,0x78,0x88,0x6e0ea9d0,0x6e0ea9e0,0x6e0ea9ec | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2496 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1012,12384402129235495018,323417566610675219,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=5198104624799759874 --mojo-platform-channel-handle=980 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
2 995
Read events
2 613
Write events
370
Delete events
12
Modification events
| (PID) Process: | (2092) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2092) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2092) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (2092) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (2092) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (544) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 2092-13241371249755375 |
Value: 259 | |||
| (PID) Process: | (2092) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (2092) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (2092) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 2832-13239195546717773 |
Value: 0 | |||
| (PID) Process: | (2092) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
Executable files
0
Suspicious files
82
Text files
132
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2092 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\f7b3e3f2-493e-48fc-88f8-809baf938fb1.tmp | — | |
MD5:— | SHA256:— | |||
| 2092 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000032.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2092 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\AutofillStrikeDatabase\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2092 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Session Storage\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2092 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\AutofillStrikeDatabase\000001.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2092 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2092 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old~RF14e79f.TMP | text | |
MD5:— | SHA256:— | |||
| 2092 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Feature Engagement Tracker\EventDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2092 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Last Tabs | binary | |
MD5:— | SHA256:— | |||
| 2092 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF14e751.TMP | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
41
DNS requests
26
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
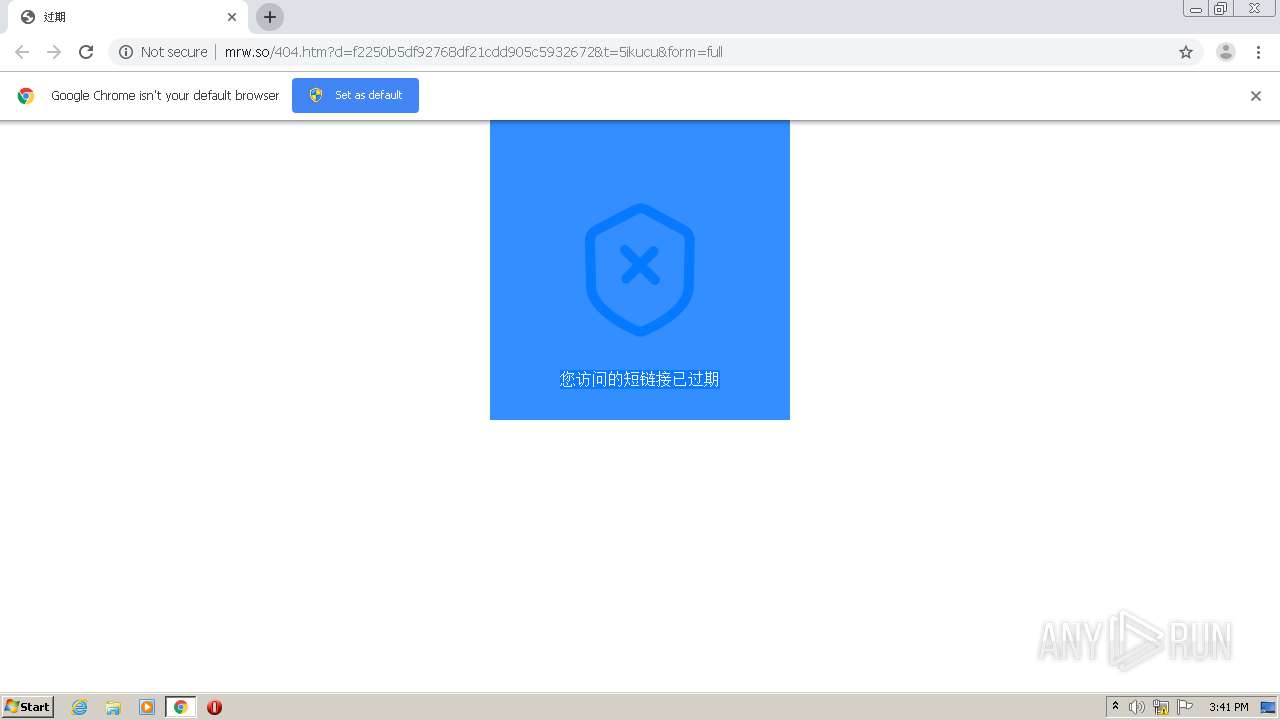
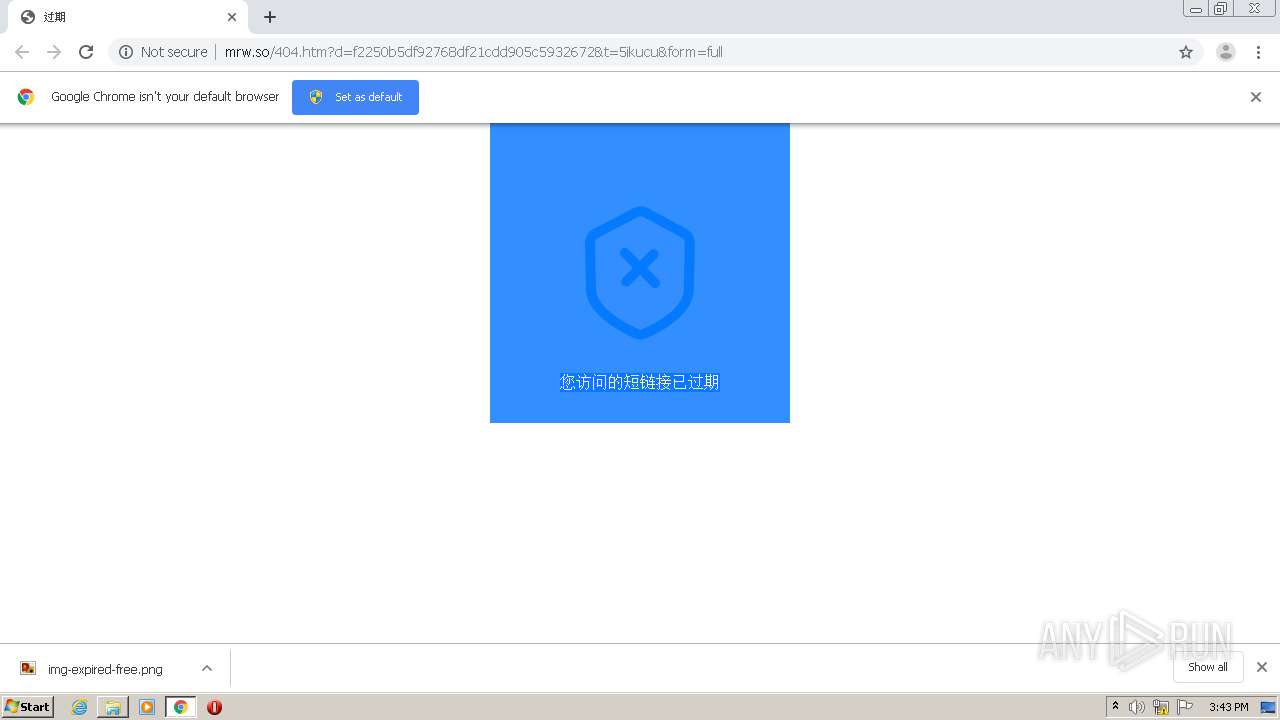
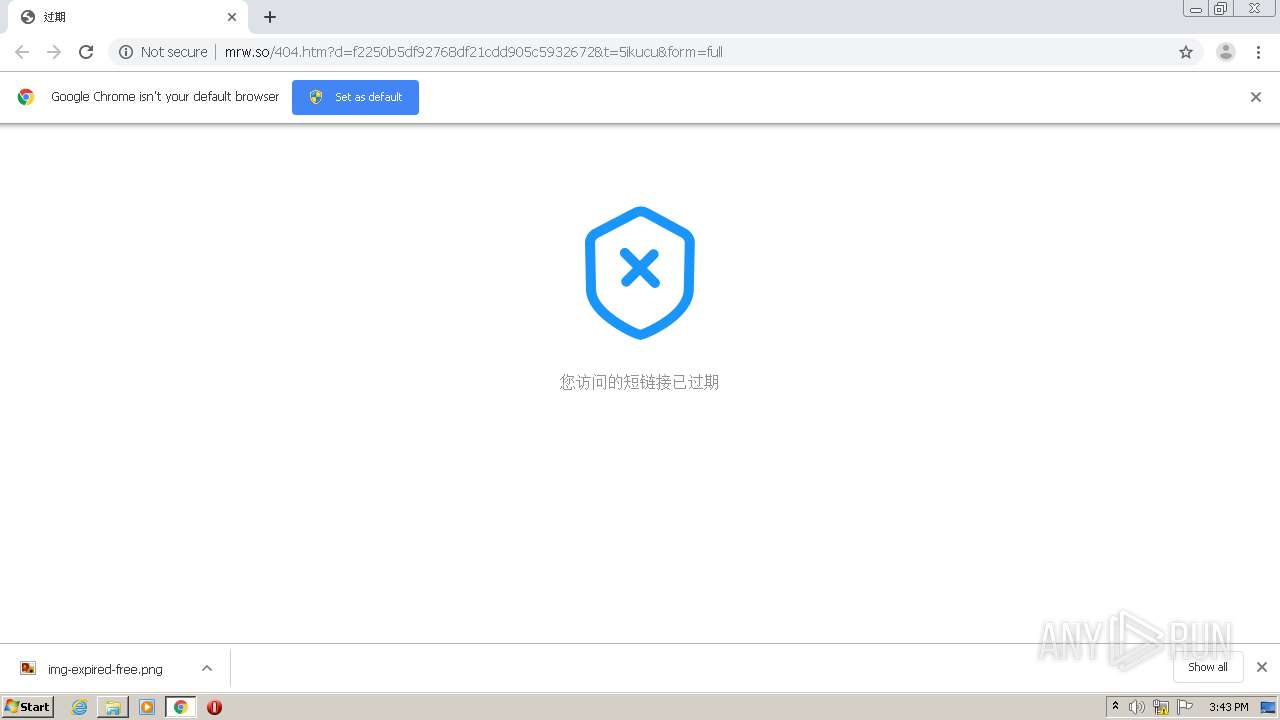
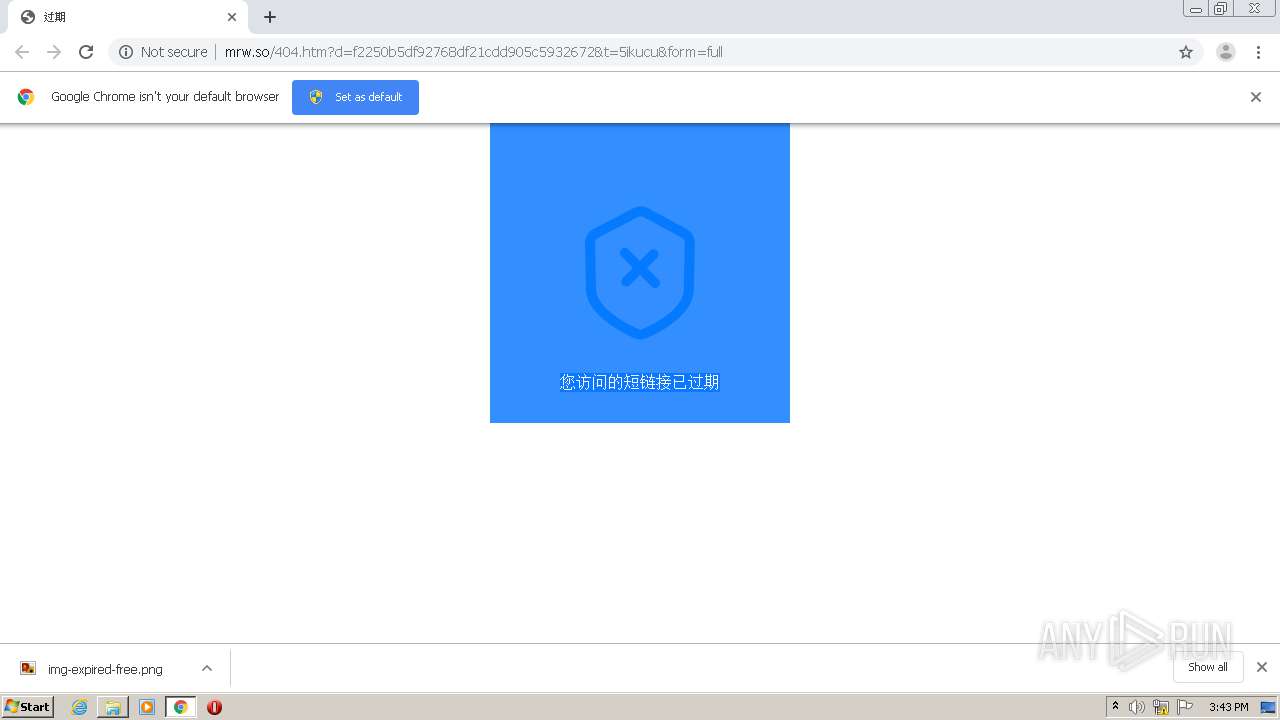
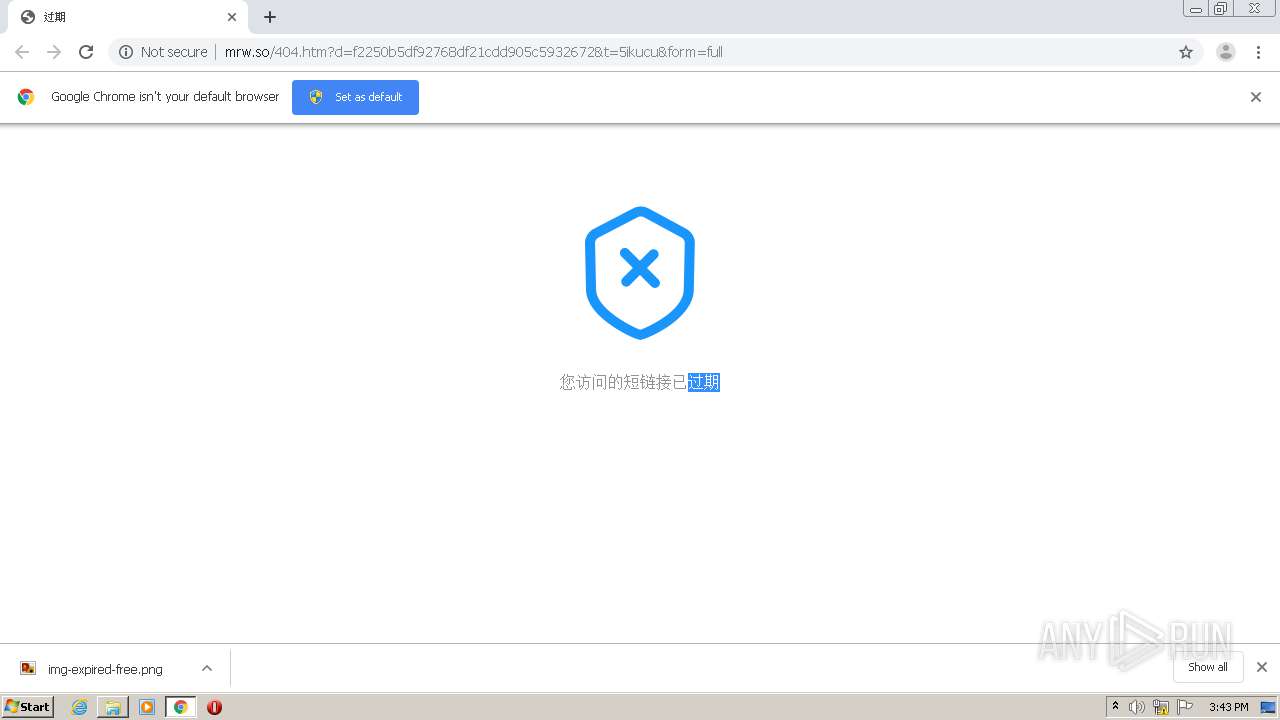
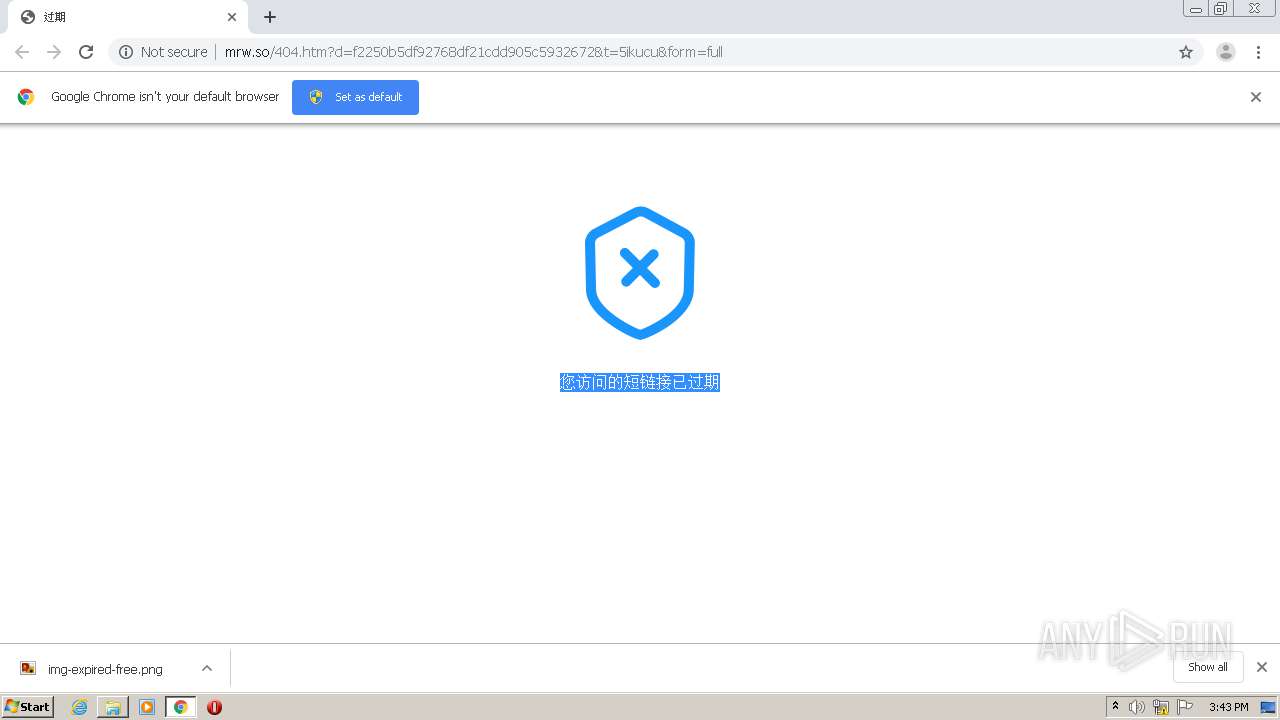
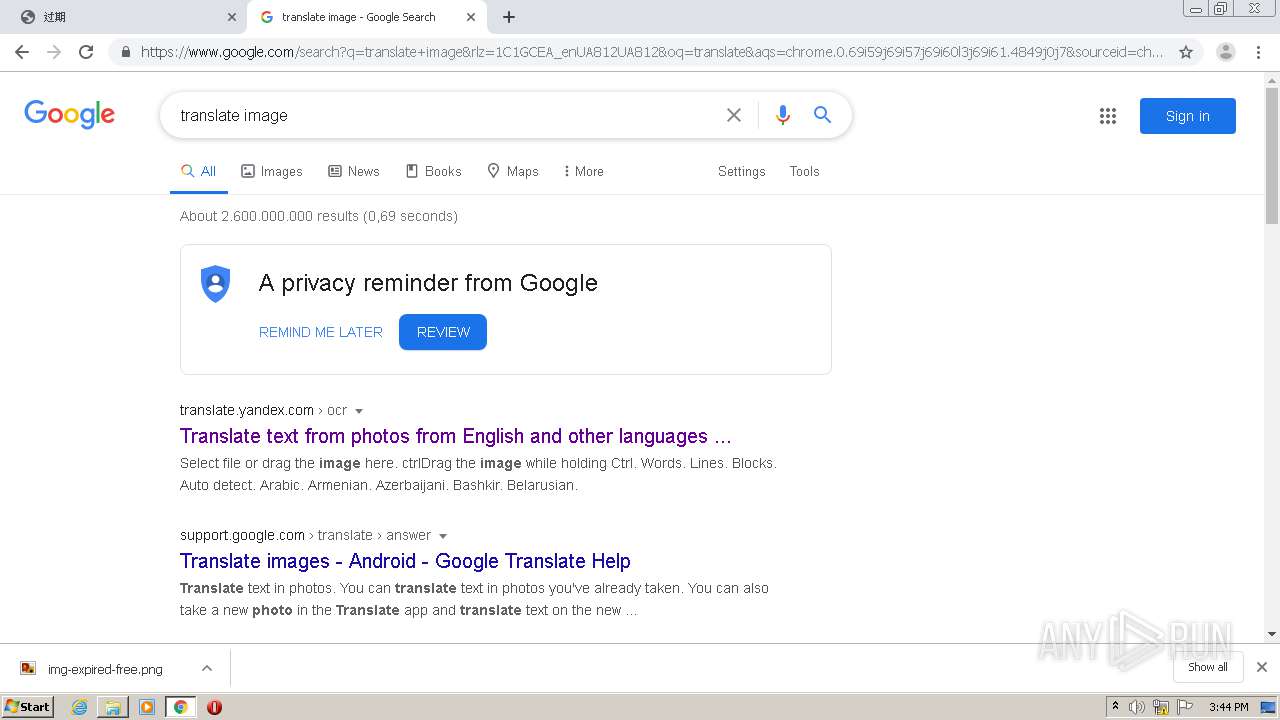
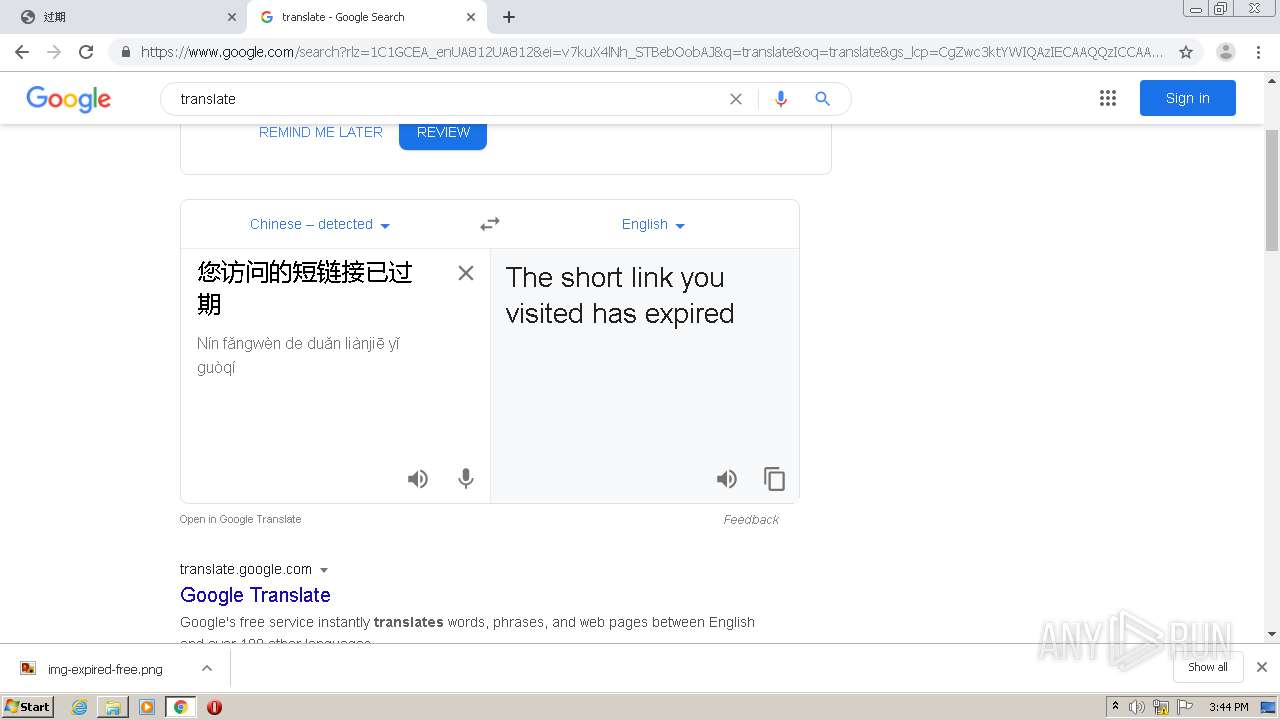
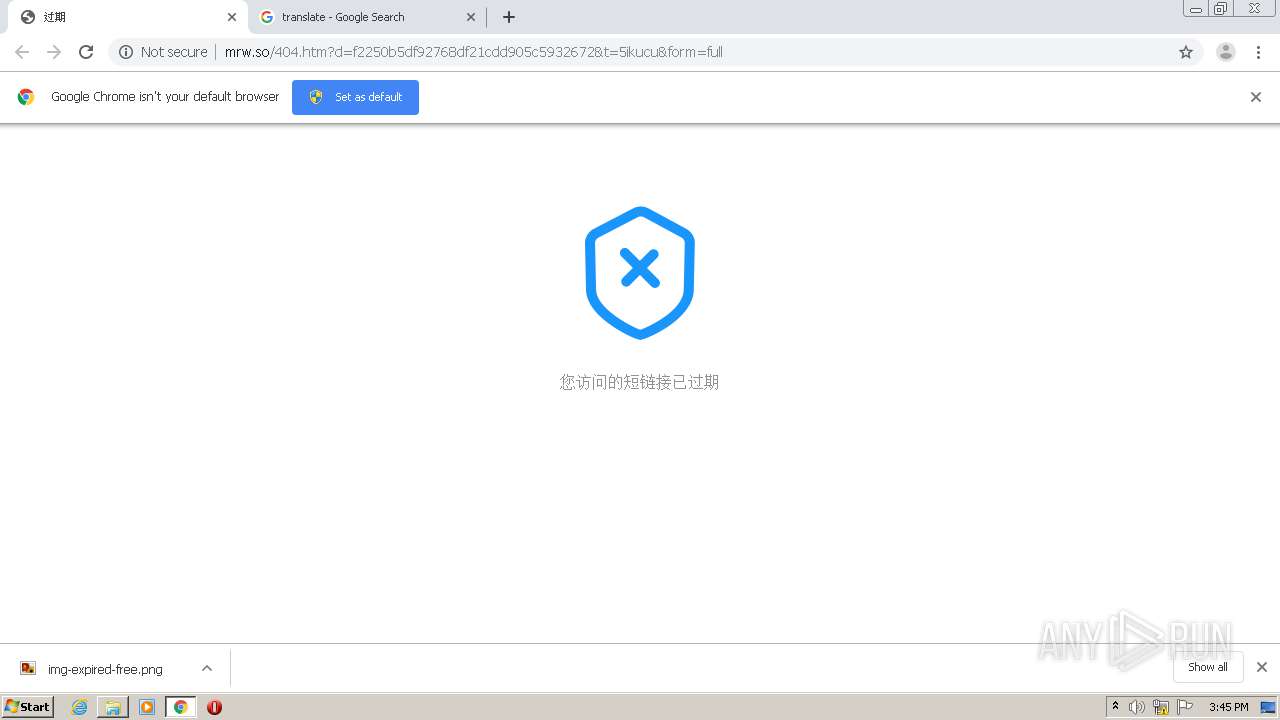
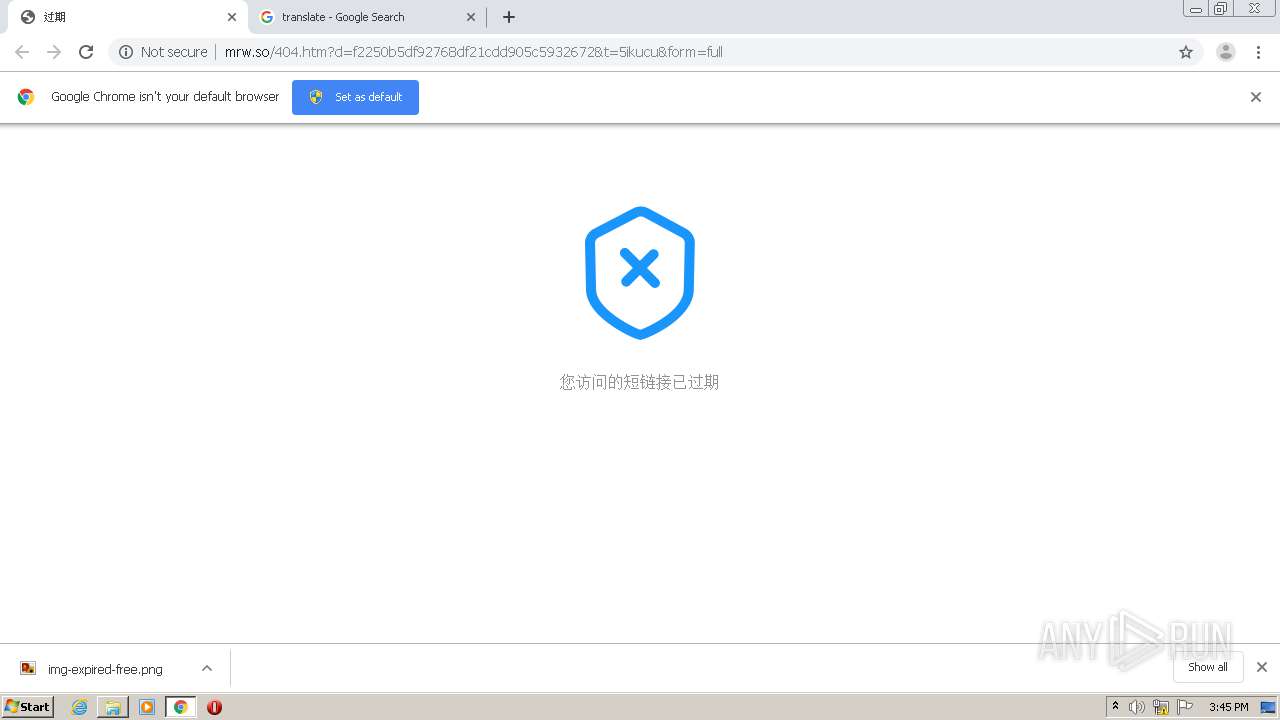
1840 | chrome.exe | GET | 302 | 211.97.73.224:80 | http://mrw.so/5ikucu | CN | — | — | malicious |
1840 | chrome.exe | GET | 301 | 49.79.239.104:80 | http://as.gllpsho.cn/n.htm?rid=123dddac28b0698a7b4baed3eab9842971b63642a49702bb84ebf00cb1dd7abd&t=128934dad27855a5b3ce086830d42b02&d=a522b4ce61edc67b5086fb5db528a3b2 | CN | — | — | suspicious |
1840 | chrome.exe | GET | 200 | 49.79.239.84:80 | http://static.suo.nz/static/css/temporarily-close.css | CN | text | 853 b | malicious |
1840 | chrome.exe | GET | 200 | 49.79.239.84:80 | http://static.suo.nz/static/css/reset.css | CN | text | 1.48 Kb | malicious |
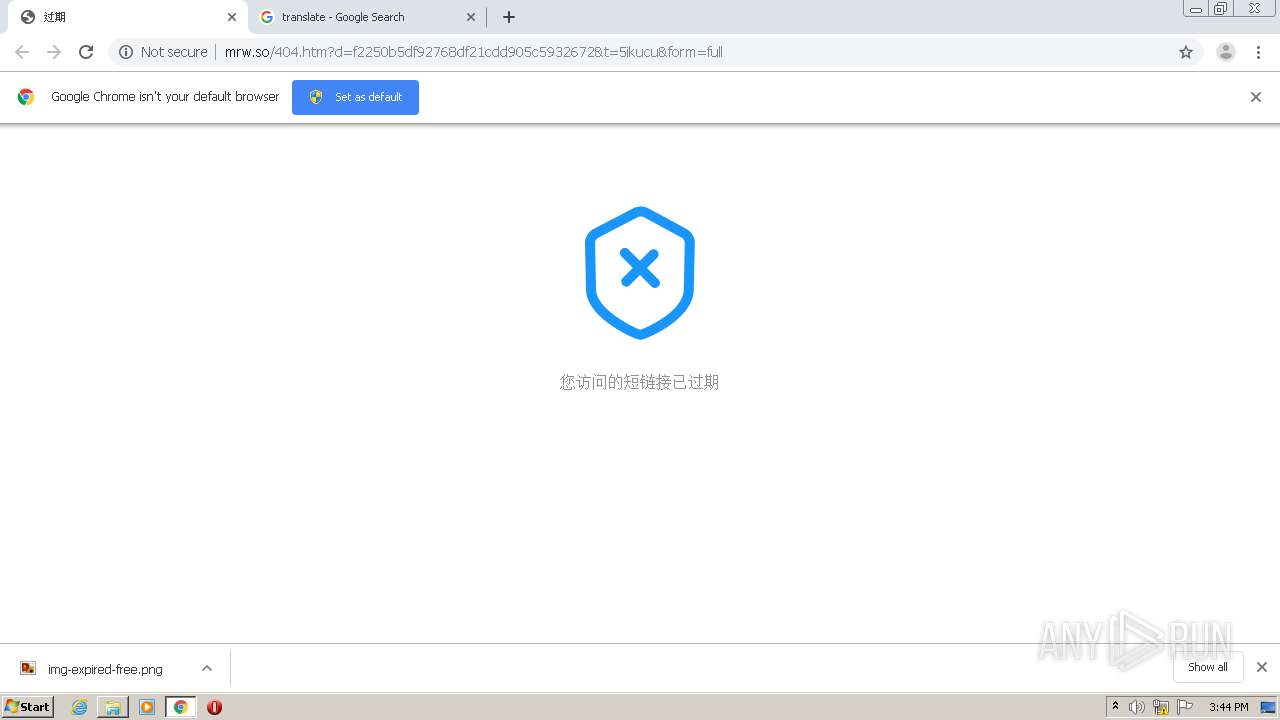
1840 | chrome.exe | GET | 200 | 211.97.73.224:80 | http://mrw.so/404.htm?d=f2250b5df92768df21cdd905c5932672&t=5ikucu&form=full | CN | html | 1.04 Kb | malicious |
1840 | chrome.exe | GET | 200 | 49.79.239.84:80 | http://static.suo.nz/static/images/img-expired-free.png | CN | image | 51.8 Kb | malicious |
1840 | chrome.exe | GET | 200 | 49.79.239.84:80 | http://static.suo.nz/static/js/rem.js | CN | text | 630 b | malicious |
1840 | chrome.exe | GET | 200 | 49.79.239.84:80 | http://static.suo.nz/static/js/jquery-3.2.1.min.js | CN | text | 34.4 Kb | malicious |
1840 | chrome.exe | GET | 404 | 211.97.73.224:80 | http://mrw.so/favicon.ico | CN | html | 564 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1840 | chrome.exe | 211.97.73.224:80 | mrw.so | CHINA UNICOM China169 Backbone | CN | unknown |
1840 | chrome.exe | 49.79.239.104:80 | as.gllpsho.cn | No.31,Jin-rong Street | CN | unknown |
1840 | chrome.exe | 49.79.239.84:80 | static.suo.nz | No.31,Jin-rong Street | CN | unknown |
1840 | chrome.exe | 172.217.18.110:443 | clients2.google.com | Google Inc. | US | whitelisted |
1840 | chrome.exe | 172.217.21.195:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
1840 | chrome.exe | 172.217.23.138:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
1840 | chrome.exe | 172.217.16.163:443 | www.gstatic.com | Google Inc. | US | whitelisted |
1840 | chrome.exe | 216.58.212.163:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
1840 | chrome.exe | 172.217.22.110:443 | apis.google.com | Google Inc. | US | whitelisted |
1840 | chrome.exe | 216.58.207.78:443 | clients1.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
mrw.so |
| malicious |
accounts.google.com |
| shared |
as.gllpsho.cn |
| suspicious |
static.suo.nz |
| malicious |
clients2.google.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
www.google.com |
| malicious |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |