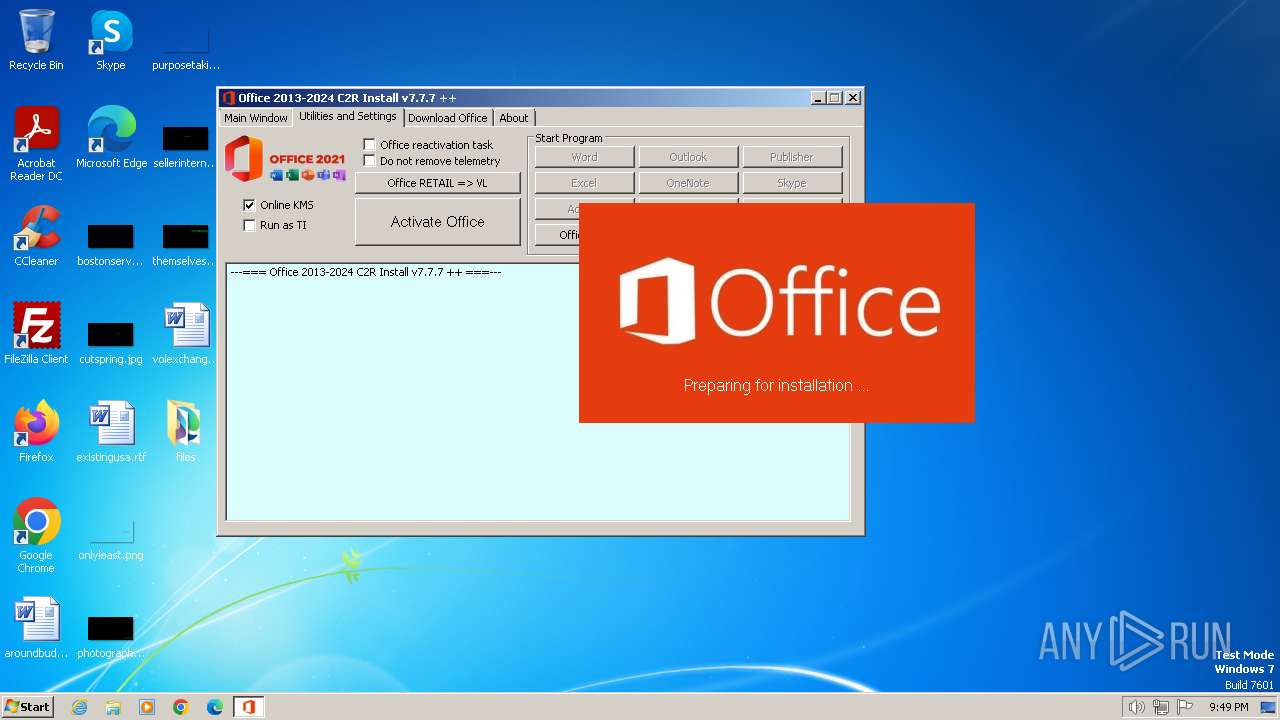
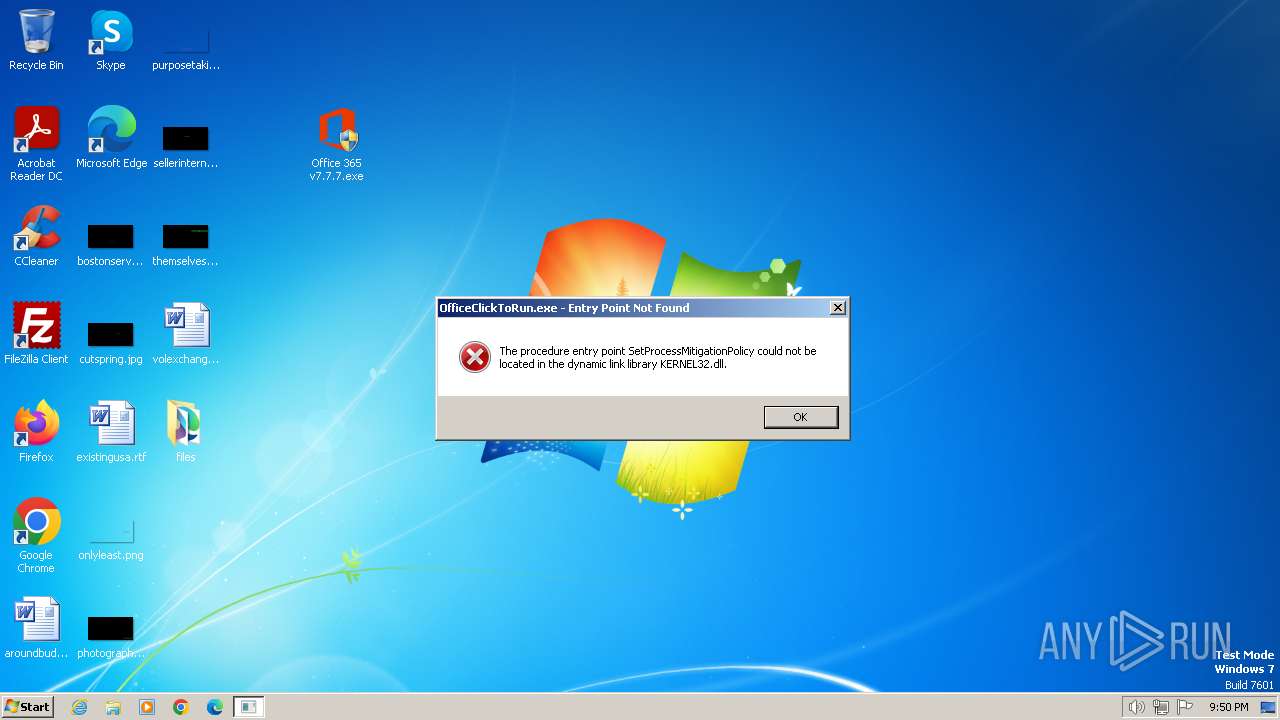
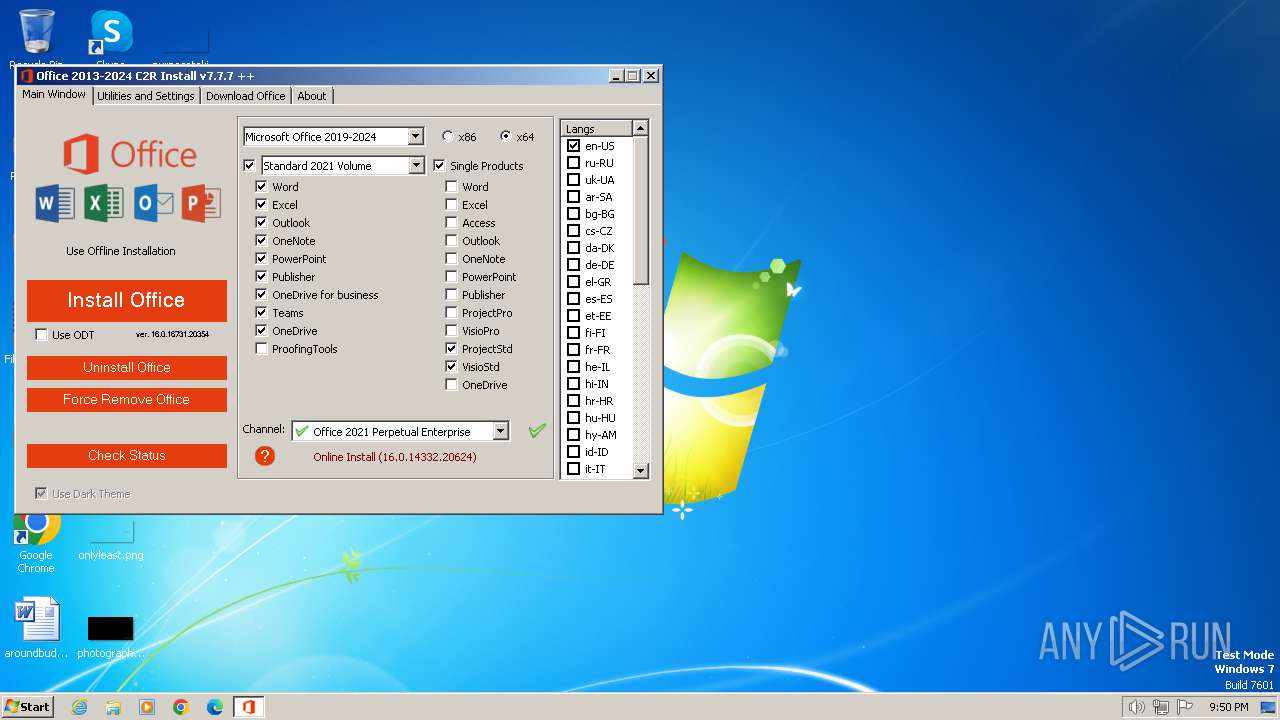
| File name: | Office 365 v7.7.7.zip |
| Full analysis: | https://app.any.run/tasks/80c979a4-cd91-44dc-bf0c-154b79f02aad |
| Verdict: | Malicious activity |
| Analysis date: | February 08, 2024, 21:48:39 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | B0614CD78DA331378868E8F1E46E4901 |
| SHA1: | 43E2A368F7DAFCF0347B30145E741BB51B9F8B59 |
| SHA256: | A3907B1676757FF85B728285AAFC4A5CD453273A976FB55B6E4E52DFF663F96D |
| SSDEEP: | 98304:TwHD+Mkc9VMbcgOtD6bzdSH1v4AZdwjLWYogn7a0GaGl3Fe59Kqm8fcVz15aj3Ps:6hwd204WjnfsTP0WK3Ut9 |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 1264)
- Office 365 v7.7.7.exe (PID: 3096)
- files.dat (PID: 3000)
SUSPICIOUS
Process drops legitimate windows executable
- Office 365 v7.7.7.exe (PID: 3096)
- files.dat (PID: 3000)
- expand.exe (PID: 3772)
Drops 7-zip archiver for unpacking
- Office 365 v7.7.7.exe (PID: 3096)
Uses REG/REGEDIT.EXE to modify registry
- Office 365 v7.7.7.exe (PID: 3096)
- cmd.exe (PID: 1348)
- cmd.exe (PID: 2960)
- cmd.exe (PID: 2152)
- cmd.exe (PID: 2904)
- cmd.exe (PID: 4068)
- cmd.exe (PID: 2968)
- cmd.exe (PID: 3964)
- cmd.exe (PID: 2292)
- cmd.exe (PID: 268)
Executable content was dropped or overwritten
- Office 365 v7.7.7.exe (PID: 3096)
- files.dat (PID: 3000)
- expand.exe (PID: 3772)
Starts application with an unusual extension
- cmd.exe (PID: 3052)
The process drops C-runtime libraries
- files.dat (PID: 3000)
- expand.exe (PID: 3772)
Starts CMD.EXE for commands execution
- Office 365 v7.7.7.exe (PID: 3096)
Probably download files using WebClient
- Office 365 v7.7.7.exe (PID: 3096)
Starts POWERSHELL.EXE for commands execution
- Office 365 v7.7.7.exe (PID: 3096)
Reads the Internet Settings
- powershell.exe (PID: 2932)
- powershell.exe (PID: 2840)
- Office 365 v7.7.7.exe (PID: 3096)
The Powershell connects to the Internet
- powershell.exe (PID: 2932)
- powershell.exe (PID: 2840)
Unusual connection from system programs
- powershell.exe (PID: 2932)
- powershell.exe (PID: 2840)
The executable file from the user directory is run by the CMD process
- test.exe (PID: 3912)
Connects to unusual port
- test.exe (PID: 3912)
INFO
Manual execution by a user
- Office 365 v7.7.7.exe (PID: 2028)
- Office 365 v7.7.7.exe (PID: 3096)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1264)
Checks supported languages
- Office 365 v7.7.7.exe (PID: 3096)
- files.dat (PID: 3000)
- aria2_oinstall.exe (PID: 3412)
- test.exe (PID: 3912)
Reads the computer name
- Office 365 v7.7.7.exe (PID: 3096)
- aria2_oinstall.exe (PID: 3412)
- test.exe (PID: 3912)
Reads Environment values
- Office 365 v7.7.7.exe (PID: 3096)
Create files in a temporary directory
- Office 365 v7.7.7.exe (PID: 3096)
- aria2_oinstall.exe (PID: 3412)
Reads the machine GUID from the registry
- aria2_oinstall.exe (PID: 3412)
- test.exe (PID: 3912)
Creates files in the program directory
- Office 365 v7.7.7.exe (PID: 3096)
- expand.exe (PID: 3772)
- expand.exe (PID: 4008)
Reads Microsoft Office registry keys
- reg.exe (PID: 1768)
- reg.exe (PID: 2480)
Drops the executable file immediately after the start
- expand.exe (PID: 3772)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2023:11:20 12:48:46 |
| ZipCRC: | 0xebe1a0b2 |
| ZipCompressedSize: | 11501896 |
| ZipUncompressedSize: | 18649512 |
| ZipFileName: | Office 365 v7.7.7.exe |
Total processes
114
Monitored processes
47
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | reg.exe add HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Office\ClickToRun\Configuration /v AudienceId /t REG_SZ /d 5030841d-c919-4594-8d2d-84ae4f96e58e /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 268 | "C:\Windows\System32\cmd.exe" /c REG QUERY HKLM\Software\WOW6432Node\Microsoft\Office /s /v Path | C:\Windows\System32\cmd.exe | — | Office 365 v7.7.7.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 584 | REG QUERY HKLM\Software\WOW6432Node\Microsoft\Office /s /v Path | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 748 | reg.exe add HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Office\ClickToRun\Configuration /v UpdateUrl /t REG_SZ /d http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 784 | "C:\Windows\System32\reg.exe" add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SoftwareProtectionPlatform" /v KeyManagementServicePort /t REG_SZ /d 1688 /f | C:\Windows\System32\reg.exe | — | Office 365 v7.7.7.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 844 | "C:\Windows\System32\cmd.exe" /D /c cscript.exe "" //NoLogo /act | C:\Windows\System32\cmd.exe | — | Office 365 v7.7.7.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 984 | "C:\Windows\System32\cmd.exe" /D /c cscript.exe "" //NoLogo /setprt:1688 | C:\Windows\System32\cmd.exe | — | Office 365 v7.7.7.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1264 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Office 365 v7.7.7.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1348 | "C:\Windows\System32\cmd.exe" /D /c reg.exe add HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Office\ClickToRun\Configuration /v UpdateChannel /t REG_SZ /d http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e /f | C:\Windows\System32\cmd.exe | — | Office 365 v7.7.7.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1540 | cscript.exe "" //NoLogo /setprt:1688 | C:\Windows\System32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 1 Version: 5.8.7600.16385 Modules
| |||||||||||||||
Total events
4 550
Read events
4 519
Write events
31
Delete events
0
Modification events
| (PID) Process: | (1264) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1264) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (1264) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (1264) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (1264) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (1264) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1264) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1264) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1264) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1264) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
Executable files
222
Suspicious files
13
Text files
30
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2932 | powershell.exe | C:\Users\admin\AppData\Local\Temp\over227734\i320.cab | — | |
MD5:— | SHA256:— | |||
| 1264 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1264.43138\Office 365 v7.7.7.exe | executable | |
MD5:B3EF471608291771890D2EF8D3E8AF41 | SHA256:3980BE5DC7DD6A5E27E8116B181D4B007FF9E3AF2702FEADAC0818708142D87B | |||
| 3096 | Office 365 v7.7.7.exe | C:\Users\admin\Desktop\files\setup.exe | executable | |
MD5:6B6F44E4EF1EE8FB94EA28AED02964FB | SHA256:CAF295438040ECA0632D475EEECF51A16307A23CB87DCFCE796D274E8E8FF221 | |||
| 3412 | aria2_oinstall.exe | C:\Users\admin\AppData\Local\Temp\ver.txt.aria2__temp | binary | |
MD5:21421FD87C164C31331AE33726F71FA6 | SHA256:97B06FD389BBBFEC7B3C0365CE5E8146624300FC11AA5EFC9D8AFA70C245E16C | |||
| 3000 | files.dat | C:\Users\admin\Desktop\files\x86\cleanospp.exe | executable | |
MD5:98821A7A5737D656633D10A3AFB724BD | SHA256:04BA4487F95290E0B0557B44300C18F637FBAF0872EE96E3111013B8A1539F25 | |||
| 3096 | Office 365 v7.7.7.exe | C:\Users\admin\AppData\Local\Temp\aria2_oinstall.exe | executable | |
MD5:B95DBDE252CC8EA490E1D9D04EC5FE0D | SHA256:0AE98794B3523634B0AF362D6F8C04A9BBD32AEDA959B72CA0E7FC24E84D2A66 | |||
| 3412 | aria2_oinstall.exe | C:\Users\admin\AppData\Local\Temp\ver.txt.aria2 | binary | |
MD5:21421FD87C164C31331AE33726F71FA6 | SHA256:97B06FD389BBBFEC7B3C0365CE5E8146624300FC11AA5EFC9D8AFA70C245E16C | |||
| 2932 | powershell.exe | C:\Users\admin\AppData\Local\Temp\ikiqbty2.se4.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 3096 | Office 365 v7.7.7.exe | C:\Users\admin\AppData\Local\Temp\newui.reg | text | |
MD5:7FB2BDA7CA25568909EAB0B872416ADA | SHA256:92DC5F009E30E42D18B80FDCCE0E029DF6D56E387EB38E16C5585A9C5A0B41A7 | |||
| 2932 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:446DD1CF97EABA21CF14D03AEBC79F27 | SHA256:A7DE5177C68A64BD48B36D49E2853799F4EBCFA8E4761F7CC472F333DC5F65CF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
11
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
488 | lsass.exe | GET | 304 | 184.24.77.199:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?fa455765e490287c | unknown | — | — | unknown |
488 | lsass.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | binary | 471 b | unknown |
1080 | svchost.exe | GET | 200 | 46.228.146.128:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?a414549a770d7263 | unknown | compressed | 65.2 Kb | unknown |
2932 | powershell.exe | GET | 200 | 2.21.20.154:80 | http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e/Office/Data/16.0.14332.20624/i320.cab | unknown | compressed | 23.5 Mb | unknown |
2840 | powershell.exe | GET | 200 | 2.21.20.154:80 | http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e/Office/Data/16.0.14332.20624/i321033.cab | unknown | compressed | 9.86 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3412 | aria2_oinstall.exe | 52.109.89.117:443 | mrodevicemgr.officeapps.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
488 | lsass.exe | 184.24.77.199:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
488 | lsass.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
2932 | powershell.exe | 2.21.20.154:80 | officecdn.microsoft.com | Akamai International B.V. | DE | unknown |
1080 | svchost.exe | 46.228.146.128:80 | ctldl.windowsupdate.com | LLNW | US | unknown |
2840 | powershell.exe | 2.21.20.154:80 | officecdn.microsoft.com | Akamai International B.V. | DE | unknown |
3912 | test.exe | 106.55.134.25:1688 | kms.loli.best | Shenzhen Tencent Computer Systems Company Limited | CN | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
mrodevicemgr.officeapps.live.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
officecdn.microsoft.com |
| whitelisted |
kms.loli.best |
| unknown |