| URL: | example.com |
| Full analysis: | https://app.any.run/tasks/e8ecaed5-b7c5-4827-bf56-2b10914d5b44 |
| Verdict: | Malicious activity |
| Analysis date: | September 17, 2025, 17:28:50 |
| OS: | Ubuntu 22.04.2 |
| Tags: | |
| Indicators: | |
| MD5: | 5ABABD603B22780302DD8D83498E5172 |
| SHA1: | 0CAAF24AB1A0C33440C06AFE99DF986365B0781F |
| SHA256: | A379A6F6EEAFB9A55E378C118034E2751E682FAB9F2D30AB13D2125586CE1947 |
| SSDEEP: | 3:4VJT:4/ |
MALICIOUS
PHISHING has been detected (SURICATA)
- systemd-resolved (PID: 418)
SUSPICIOUS
Executes commands using command-line interpreter
- sudo (PID: 1903)
- gnome-terminal-server (PID: 2119)
- chrome (PID: 1906)
Reads passwd file
- tnftp (PID: 2147)
- tnftp (PID: 2174)
- tnftp (PID: 2189)
- dumpe2fs (PID: 2215)
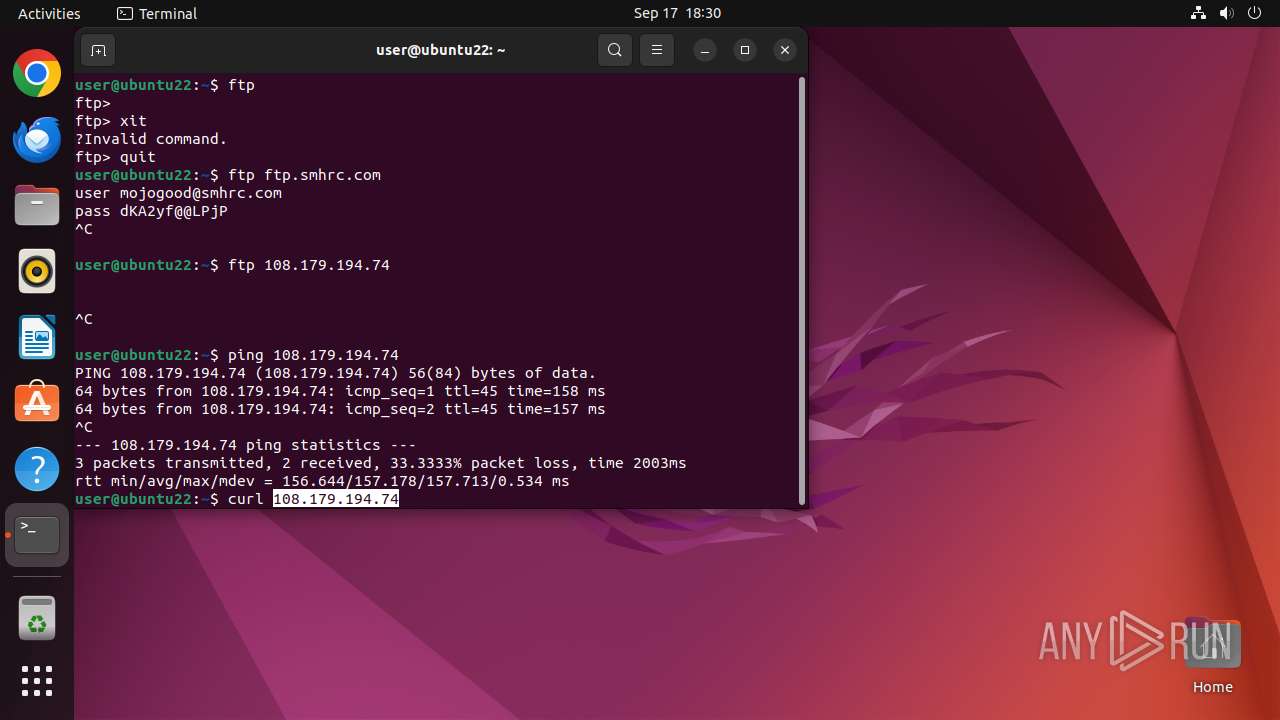
- curl (PID: 2191)
- dumpe2fs (PID: 2216)
- curl (PID: 2247)
- curl (PID: 2276)
Checks the user who created the process
- tnftp (PID: 2147)
- tnftp (PID: 2189)
- tnftp (PID: 2174)
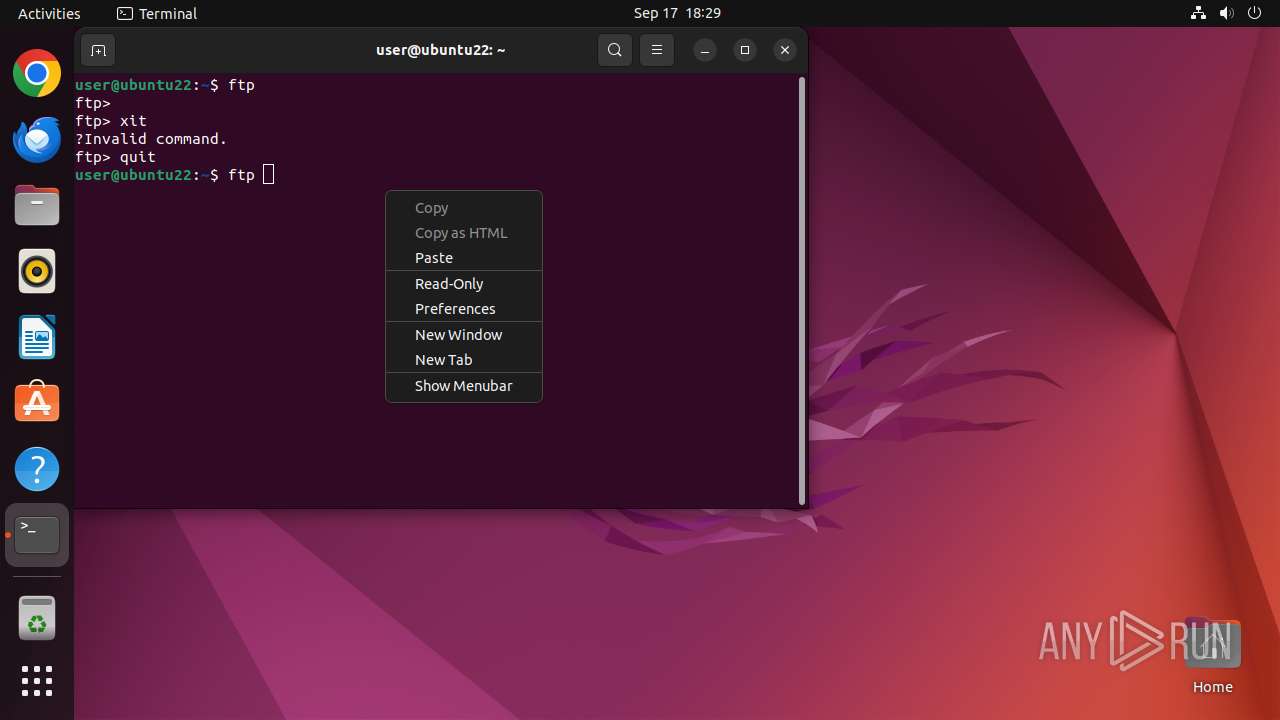
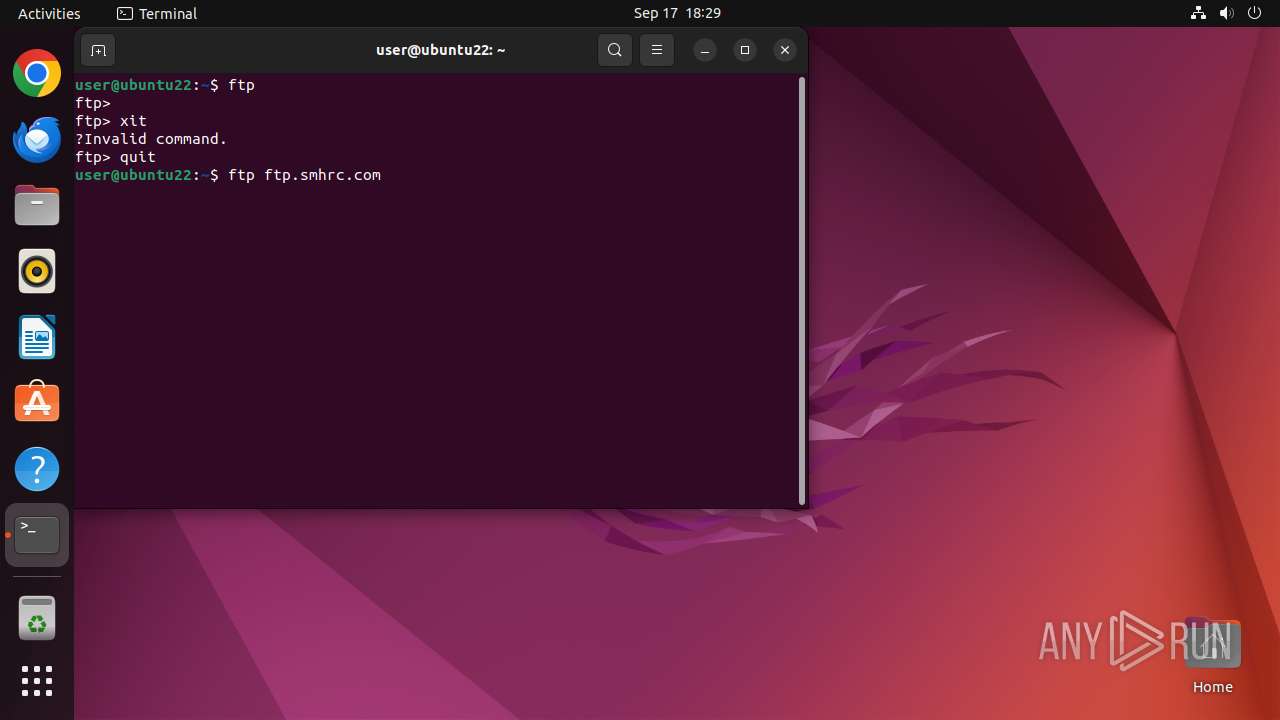
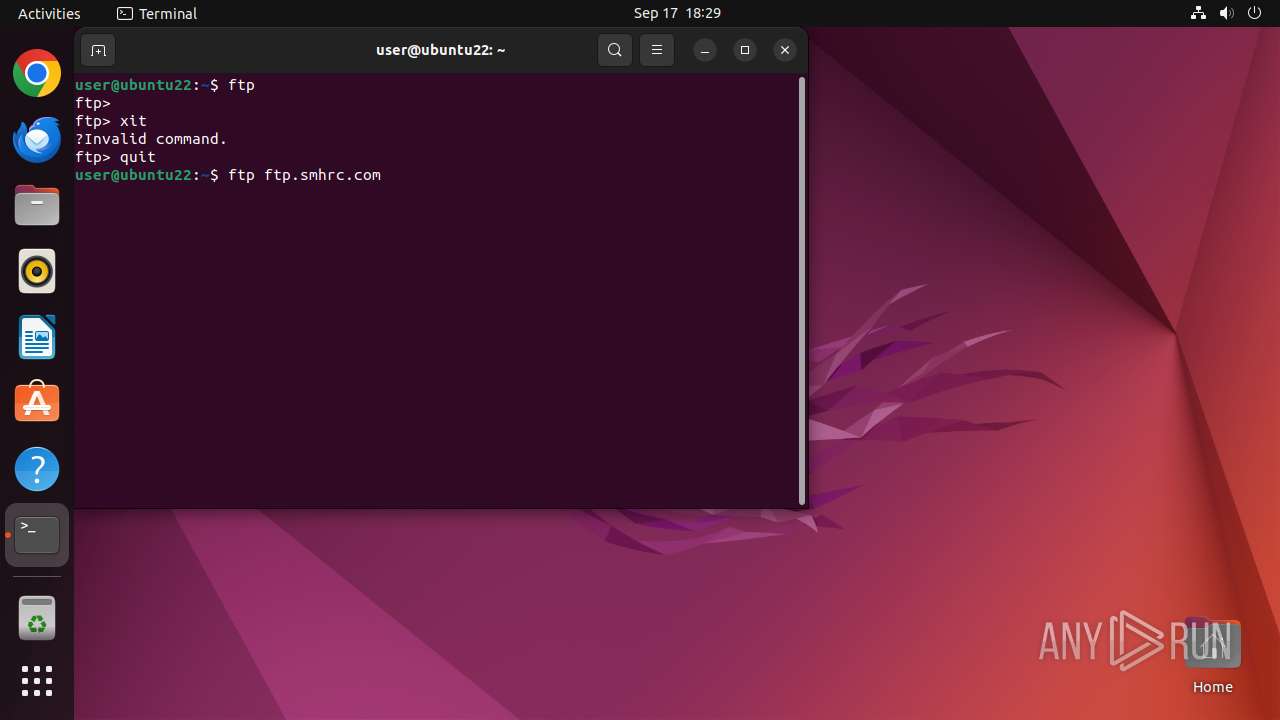
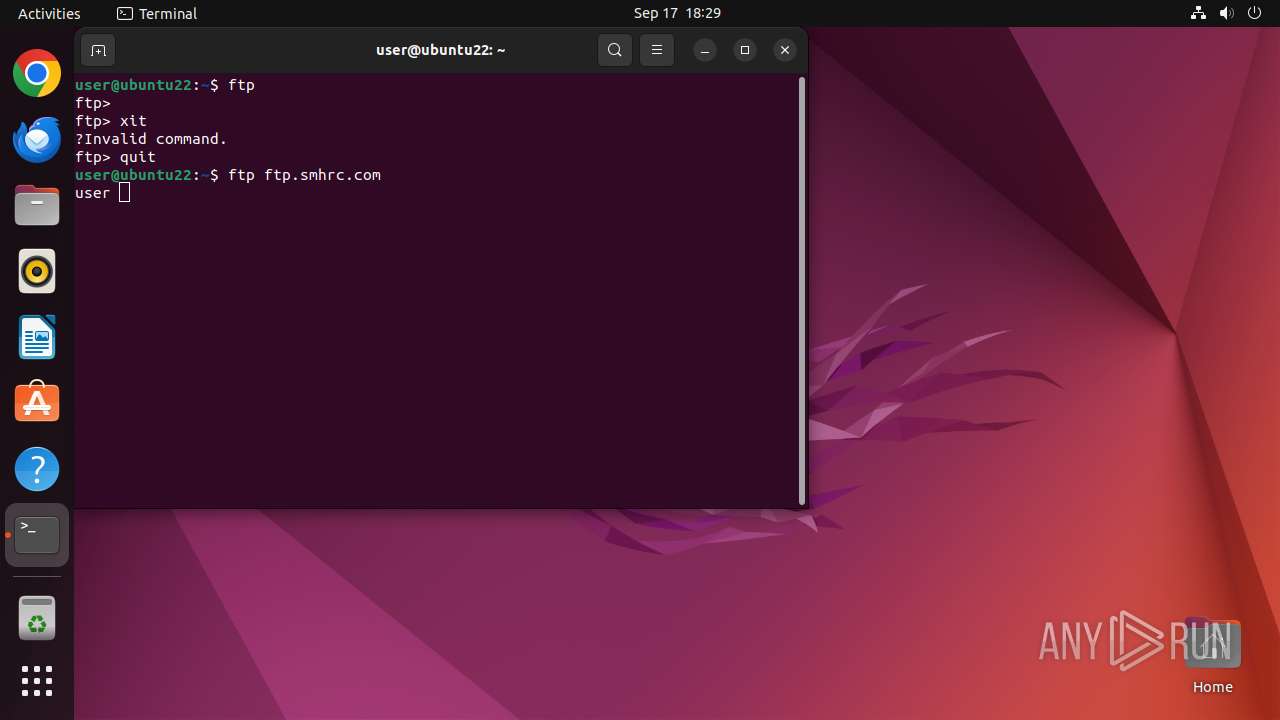
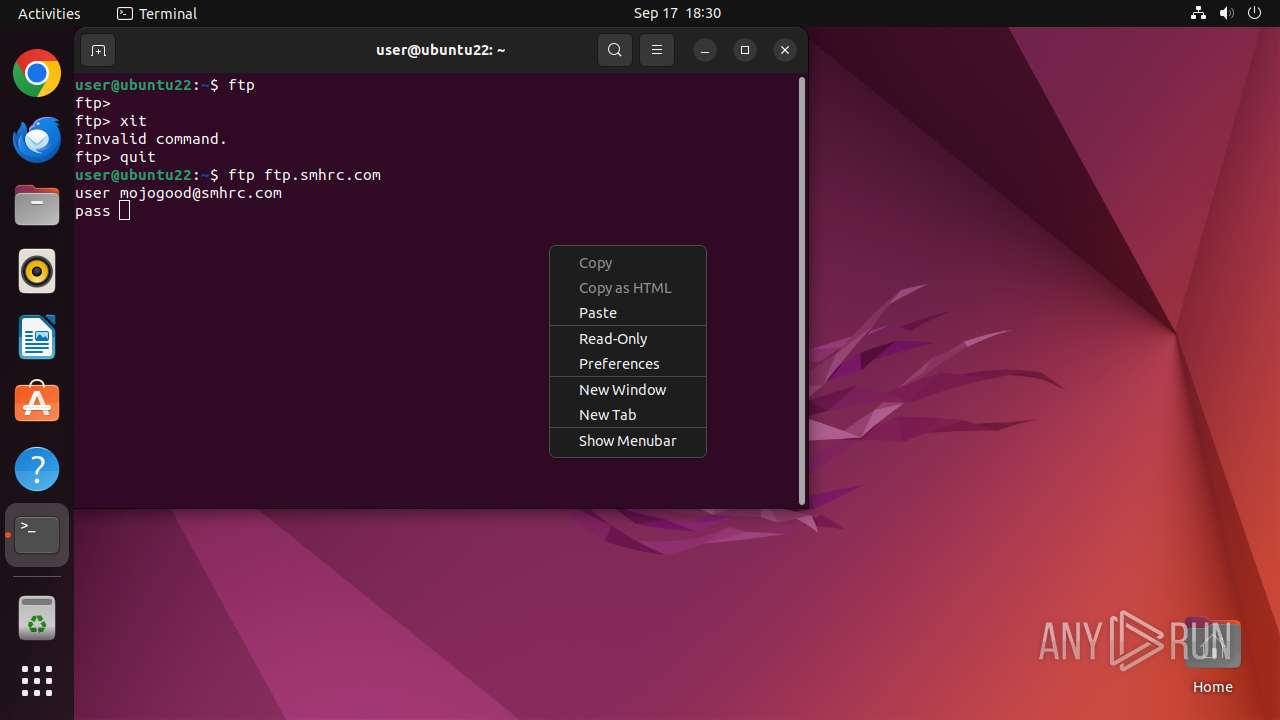
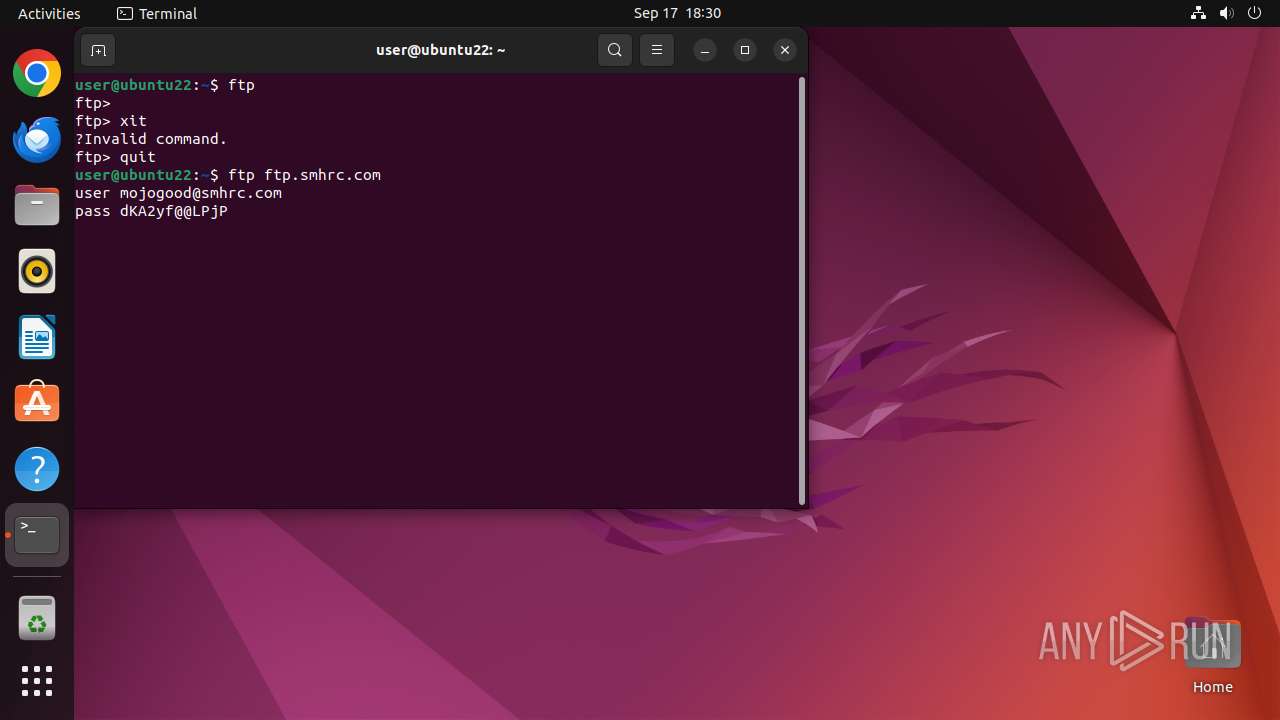
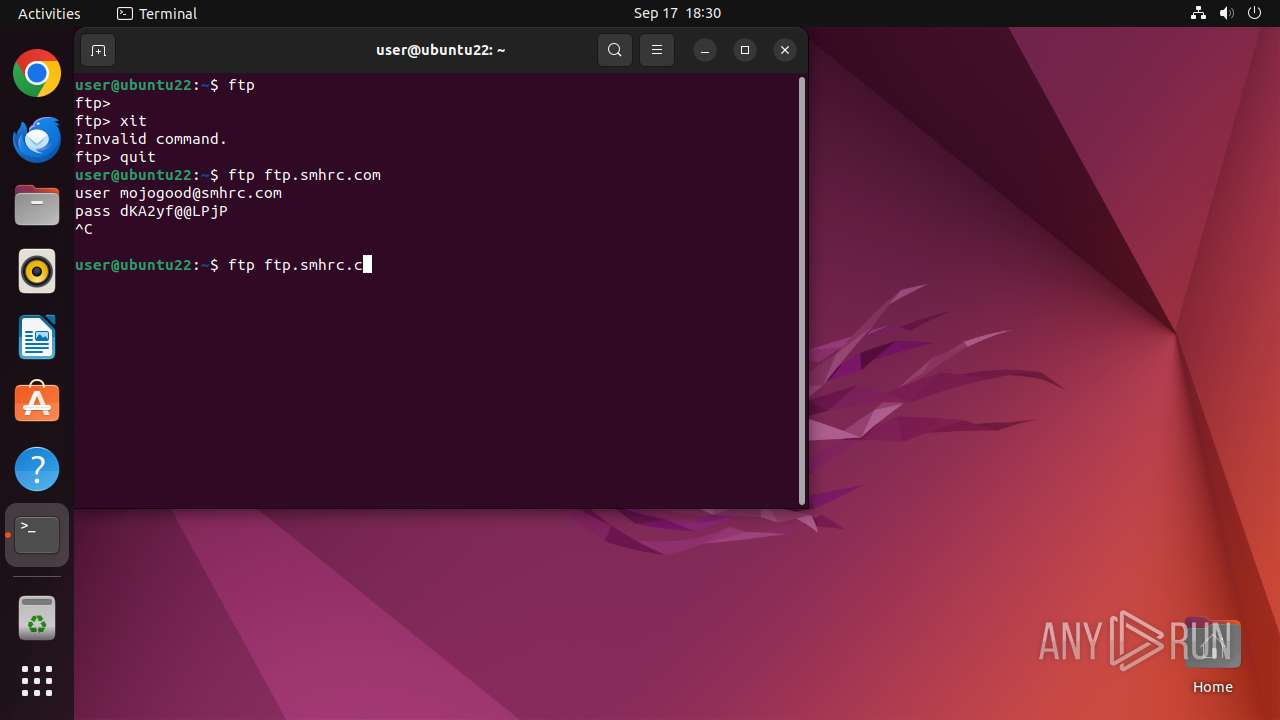
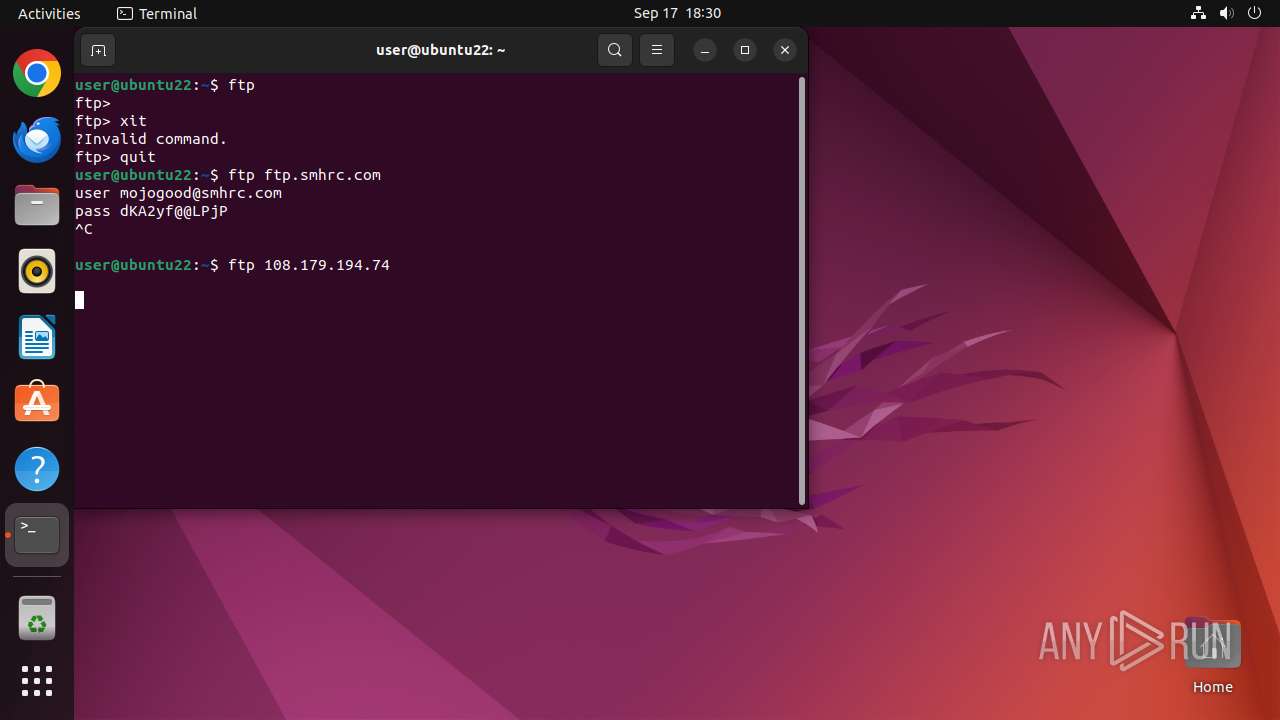
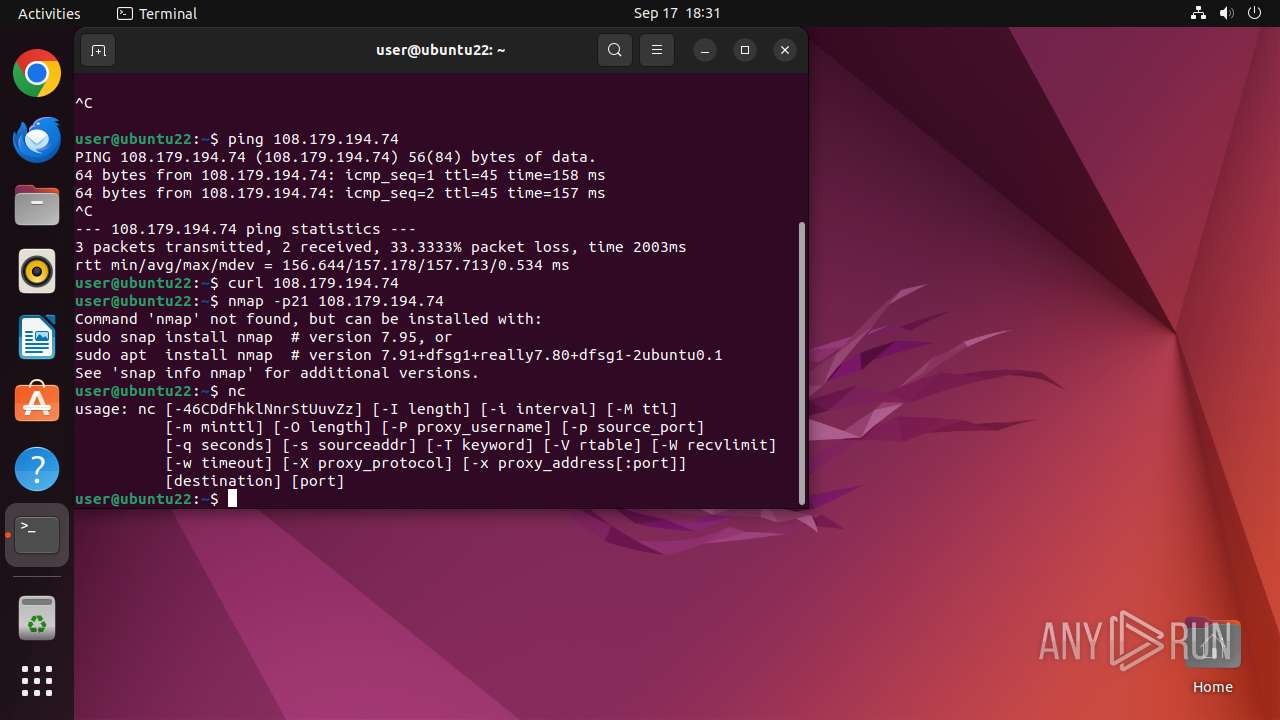
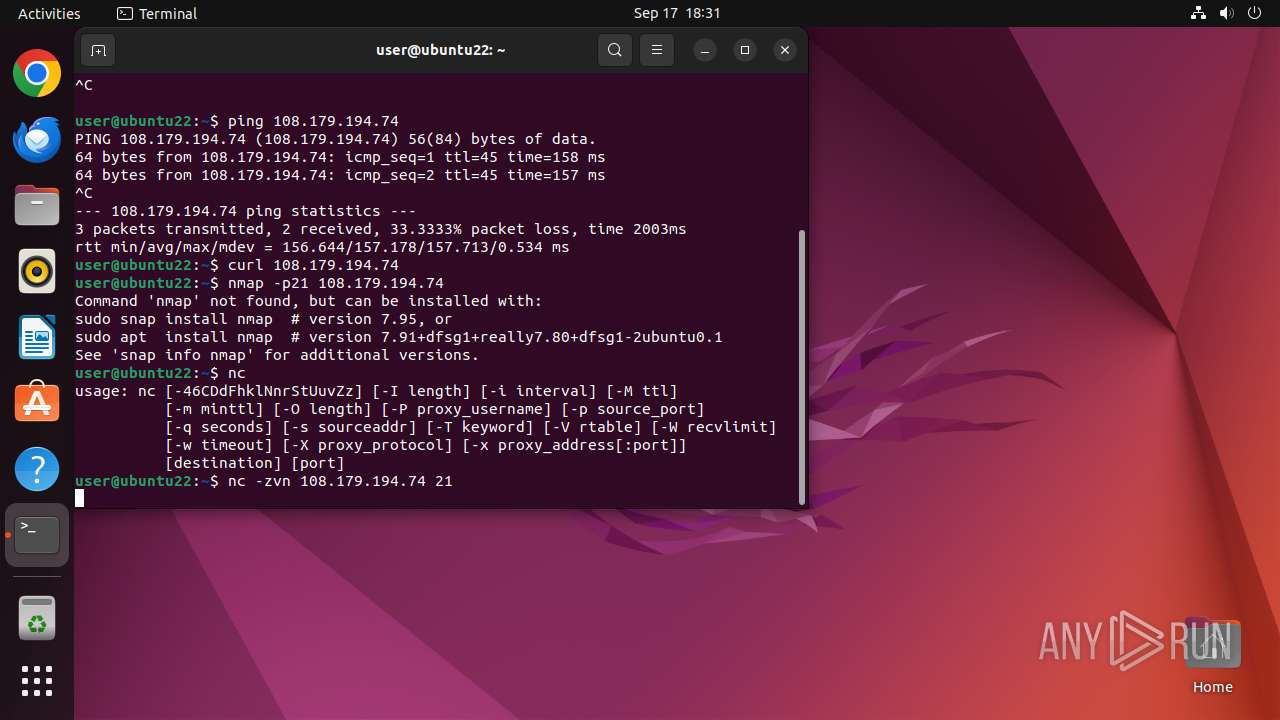
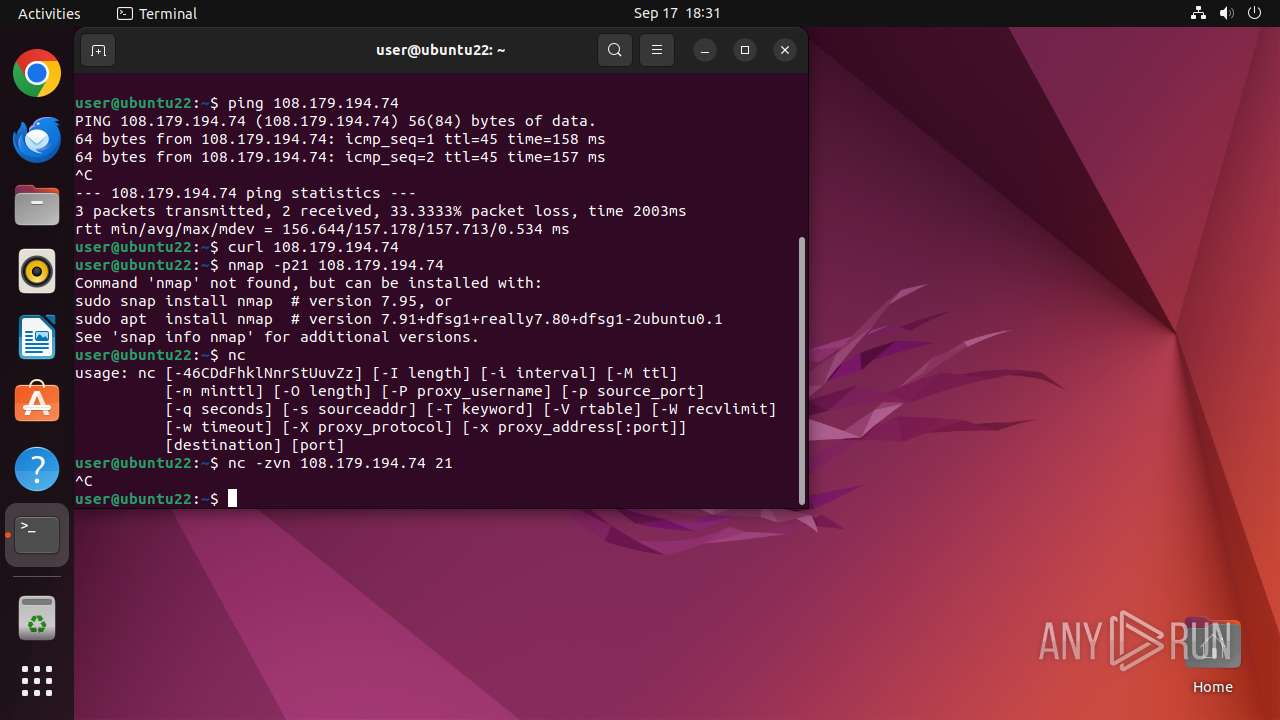
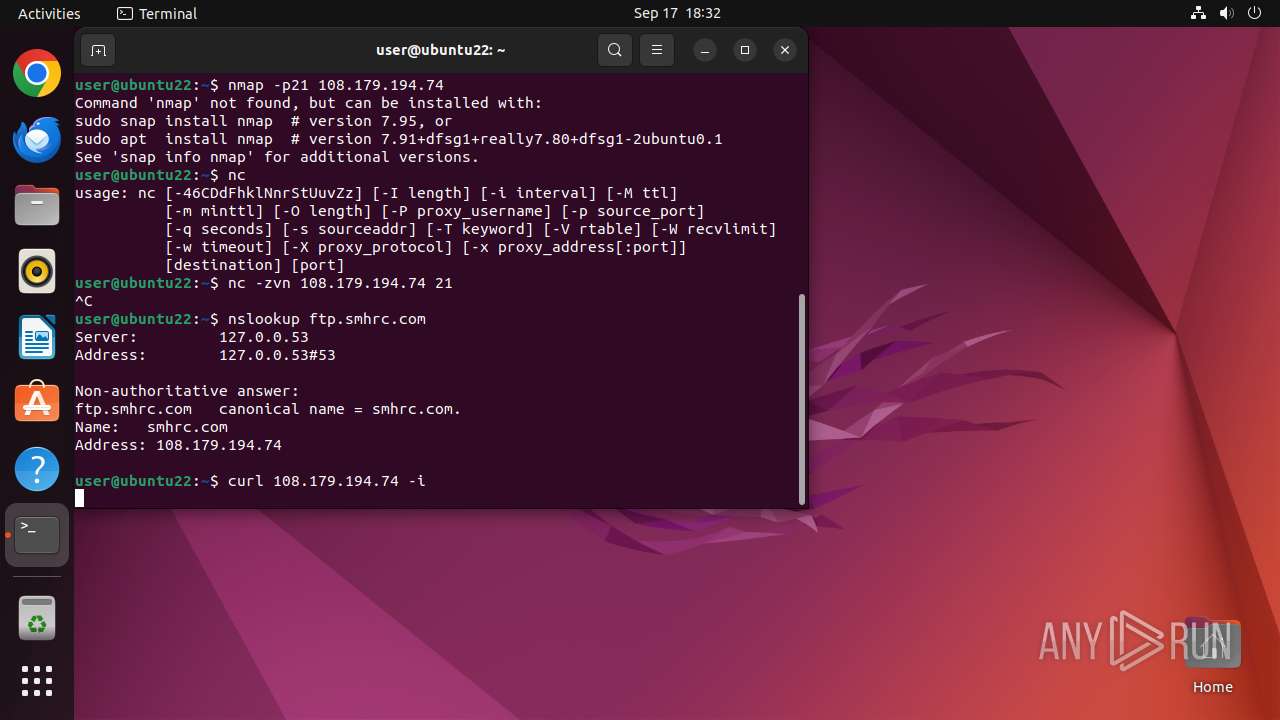
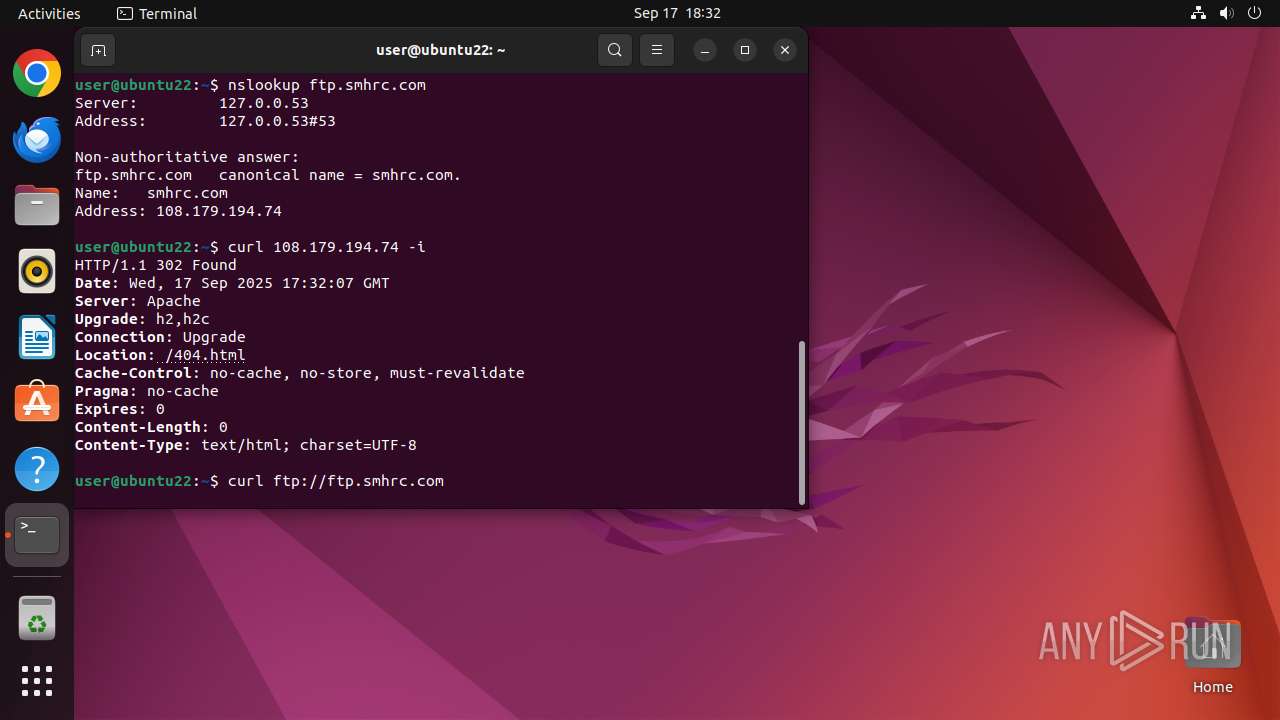
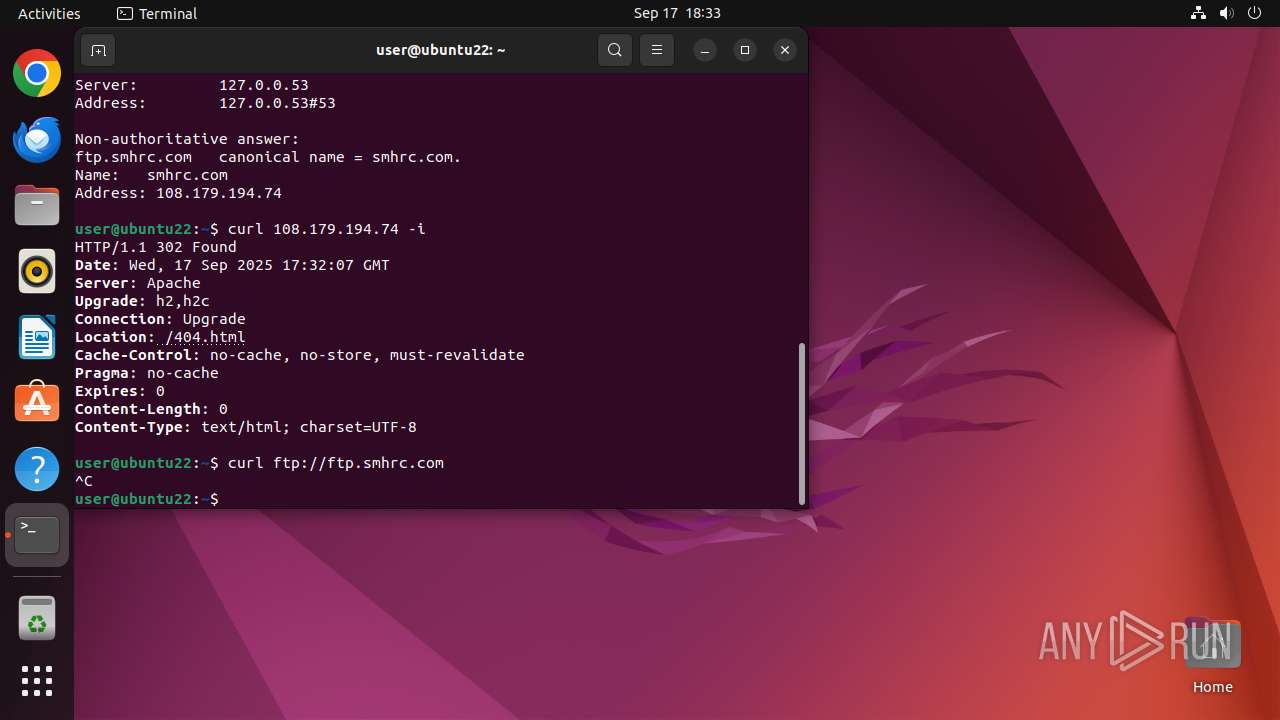
Connects to FTP
- tnftp (PID: 2189)
- curl (PID: 2276)
Check the Environment Variables Related to System Identification (os-release)
- curl (PID: 2191)
- snap (PID: 2230)
- curl (PID: 2247)
- curl (PID: 2276)
Connection to a remote server via Netcat
- bash (PID: 2137)
INFO
Checks timezone
- chrome (PID: 1906)
- python3.10 (PID: 2112)
- tnftp (PID: 2147)
- tnftp (PID: 2174)
- tnftp (PID: 2189)
- dumpe2fs (PID: 2215)
- dumpe2fs (PID: 2216)
- python3.10 (PID: 2229)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
242
Monitored processes
113
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 418 | /lib/systemd/systemd-resolved | /usr/lib/systemd/systemd-resolved | systemd | ||||||||||||
User: systemd-resolve Integrity Level: UNKNOWN Exit code: 0 Modules
| |||||||||||||||
| 1902 | /bin/sh -c "DISPLAY=:0 sudo -iu user google-chrome example\.com " | /usr/bin/dash | — | zhqBI23Omt06cXXL | |||||||||||
User: root Integrity Level: UNKNOWN Exit code: 0 Modules
| |||||||||||||||
| 1903 | sudo -iu user google-chrome example.com | /usr/bin/sudo | — | dash | |||||||||||
User: root Integrity Level: UNKNOWN Exit code: 0 Modules
| |||||||||||||||
| 1906 | /usr/bin/google-chrome example.com | /opt/google/chrome/chrome | — | sudo | |||||||||||
User: user Integrity Level: UNKNOWN Exit code: 0 Modules
| |||||||||||||||
| 1907 | /usr/bin/locale-check C.UTF-8 | /usr/bin/locale-check | — | chrome | |||||||||||
User: user Integrity Level: UNKNOWN Exit code: 0 Modules
| |||||||||||||||
| 1908 | readlink -f /usr/bin/google-chrome | /usr/bin/readlink | — | chrome | |||||||||||
User: user Integrity Level: UNKNOWN Exit code: 0 Modules
| |||||||||||||||
| 1909 | dirname /opt/google/chrome/google-chrome | /usr/bin/dirname | — | chrome | |||||||||||
User: user Integrity Level: UNKNOWN Exit code: 0 Modules
| |||||||||||||||
| 1910 | mkdir -p /home/user/.local/share/applications | /usr/bin/mkdir | — | chrome | |||||||||||
User: user Integrity Level: UNKNOWN Exit code: 0 Modules
| |||||||||||||||
| 1911 | cat | /usr/bin/cat | — | chrome | |||||||||||
User: user Integrity Level: UNKNOWN Exit code: 0 Modules
| |||||||||||||||
| 1912 | cat | /usr/bin/cat | — | chrome | |||||||||||
User: user Integrity Level: UNKNOWN Exit code: 0 Modules
| |||||||||||||||
Executable files
0
Suspicious files
98
Text files
9
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1906 | chrome | /home/user/.config/google-chrome/ShaderCache/data_3 | binary | |
MD5:— | SHA256:— | |||
| 1906 | chrome | /home/user/.config/google-chrome/ShaderCache/data_2 | binary | |
MD5:— | SHA256:— | |||
| 1906 | chrome | /home/user/.config/google-chrome/ShaderCache/data_0 | binary | |
MD5:— | SHA256:— | |||
| 1906 | chrome | /home/user/.config/google-chrome/Default/Sync Data/LevelDB/MANIFEST-000001 | binary | |
MD5:— | SHA256:— | |||
| 1906 | chrome | /home/user/.config/google-chrome/Default/shared_proto_db/metadata/MANIFEST-000001 | binary | |
MD5:— | SHA256:— | |||
| 1906 | chrome | /home/user/.config/google-chrome/Default/Extension State/MANIFEST-000001 | binary | |
MD5:— | SHA256:— | |||
| 1906 | chrome | /home/user/.config/google-chrome/Default/shared_proto_db/MANIFEST-000001 | binary | |
MD5:— | SHA256:— | |||
| 1906 | chrome | /home/user/.config/google-chrome/GrShaderCache/data_3 | binary | |
MD5:— | SHA256:— | |||
| 1906 | chrome | /home/user/.config/google-chrome/GrShaderCache/data_0 | binary | |
MD5:— | SHA256:— | |||
| 1906 | chrome | /home/user/.config/google-chrome/GrShaderCache/data_2 | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
50
DNS requests
36
Threats
10
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
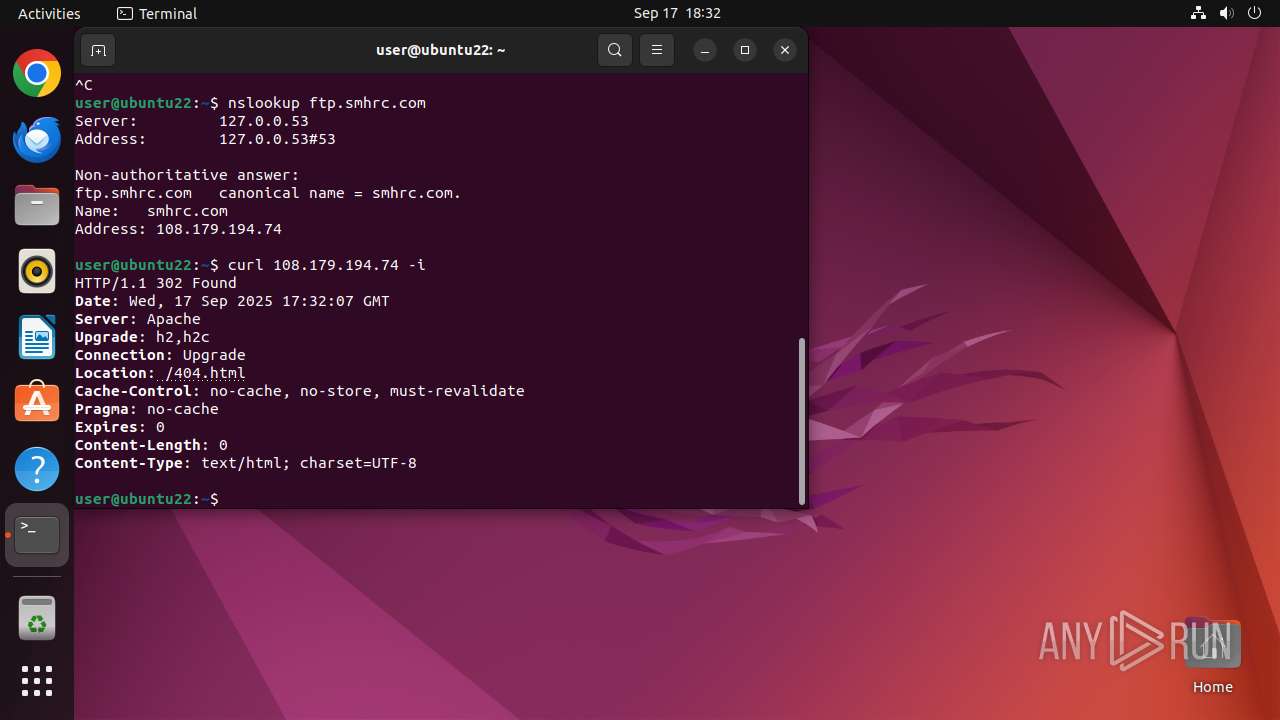
2191 | curl | GET | 302 | 108.179.194.74:80 | http://108.179.194.74/ | unknown | — | — | unknown |
— | — | GET | 204 | 91.189.91.98:80 | http://connectivity-check.ubuntu.com/ | unknown | — | — | whitelisted |
2247 | curl | GET | 302 | 108.179.194.74:80 | http://108.179.194.74/ | unknown | — | — | unknown |
481 | NetworkManager | GET | 204 | 185.125.190.98:80 | http://connectivity-check.ubuntu.com/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
477 | avahi-daemon | 224.0.0.251:5353 | — | — | — | whitelisted |
— | — | 79.127.216.204:443 | odrs.gnome.org | Ipex Ltd. | CZ | whitelisted |
— | — | 185.125.190.17:80 | connectivity-check.ubuntu.com | Canonical Group Limited | GB | whitelisted |
— | — | 91.189.91.98:80 | connectivity-check.ubuntu.com | Canonical Group Limited | US | whitelisted |
— | — | 185.125.190.58:123 | ntp.ubuntu.com | — | — | unknown |
— | — | 195.181.170.18:443 | odrs.gnome.org | Datacamp Limited | DE | whitelisted |
— | — | 185.125.188.58:443 | api.snapcraft.io | Canonical Group Limited | GB | whitelisted |
— | — | 185.125.188.57:443 | api.snapcraft.io | Canonical Group Limited | GB | whitelisted |
— | — | 185.125.188.59:443 | api.snapcraft.io | Canonical Group Limited | GB | whitelisted |
496 | snapd | 185.125.188.58:443 | api.snapcraft.io | Canonical Group Limited | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
odrs.gnome.org |
| whitelisted |
google.com |
| whitelisted |
ntp.ubuntu.com |
| unknown |
connectivity-check.ubuntu.com |
| whitelisted |
api.snapcraft.io |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
safebrowsingohttpgateway.googleapis.com |
| whitelisted |
example.com |
| whitelisted |
accounts.google.com |
| whitelisted |
google-ohttp-relay-safebrowsing.fastly-edge.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1952 | chrome | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
1952 | chrome | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
1952 | chrome | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
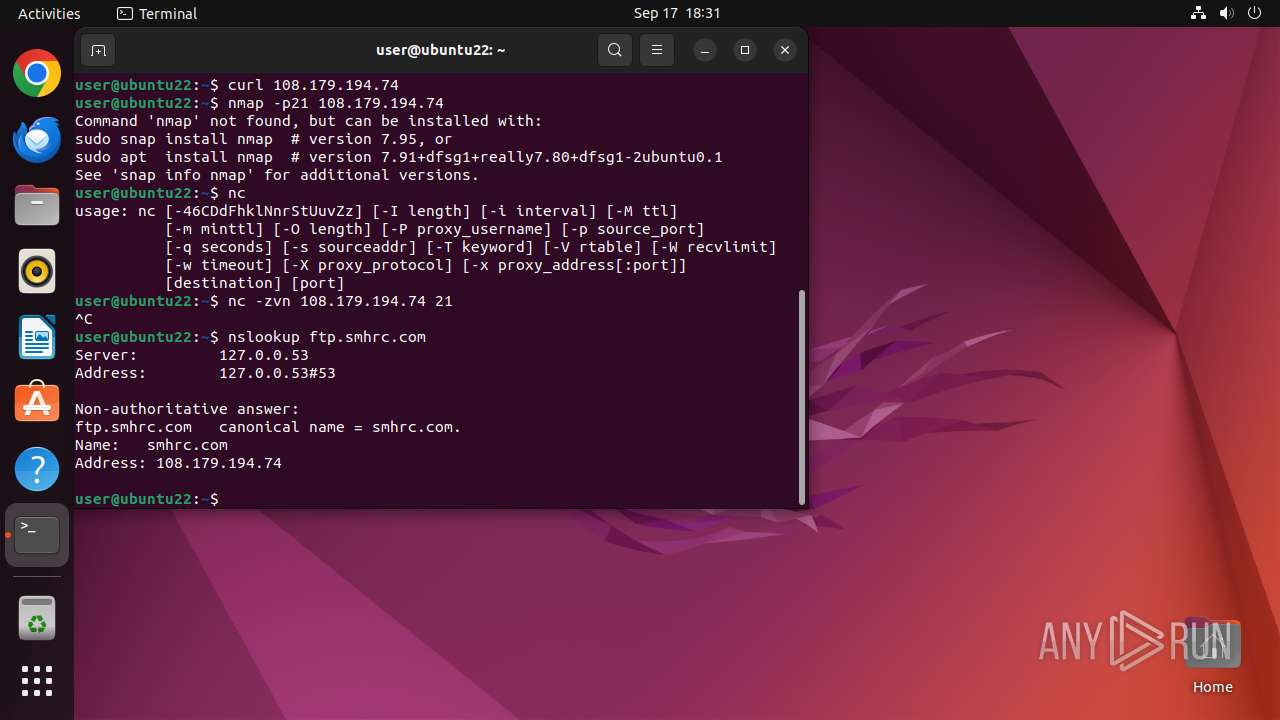
418 | systemd-resolved | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected AllBass Phishing (smhrc .com) |
418 | systemd-resolved | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected AllBass Phishing (smhrc .com) |
418 | systemd-resolved | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected AllBass Phishing (smhrc .com) |
2191 | curl | Potentially Bad Traffic | ET HUNTING curl User-Agent to Dotted Quad |
418 | systemd-resolved | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected AllBass Phishing (smhrc .com) |
2247 | curl | Potentially Bad Traffic | ET HUNTING curl User-Agent to Dotted Quad |
418 | systemd-resolved | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected AllBass Phishing (smhrc .com) |