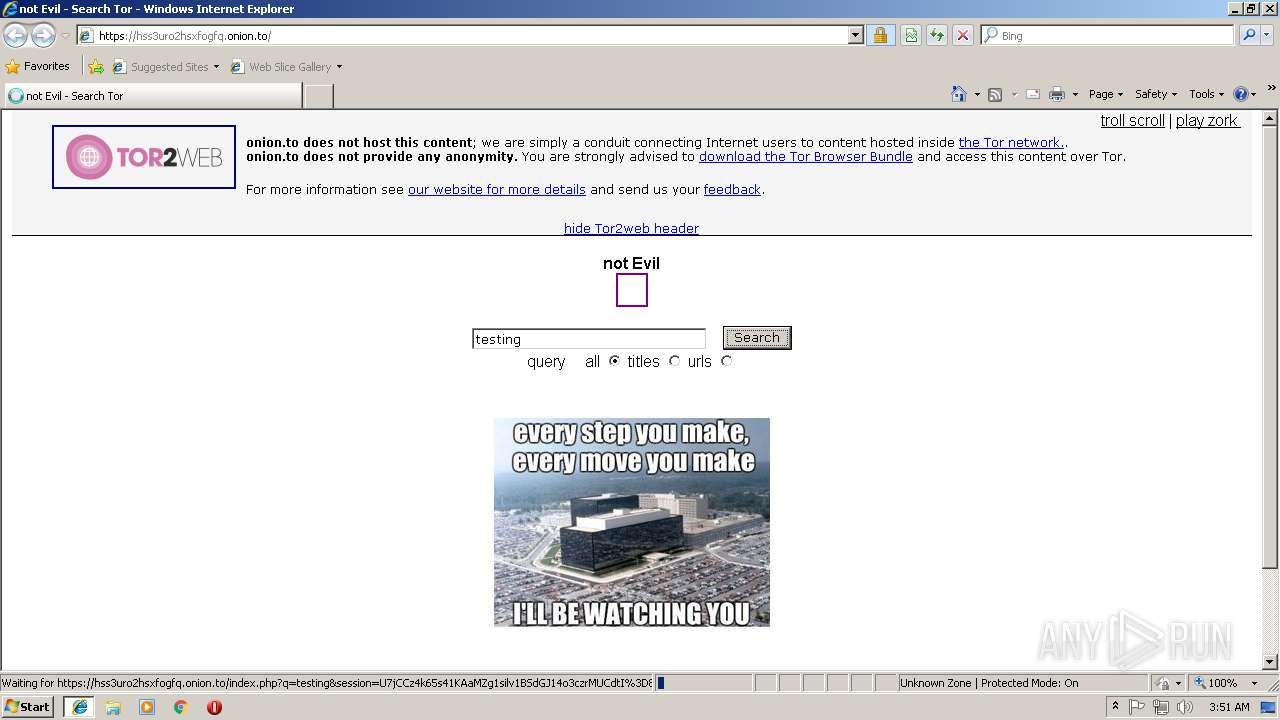
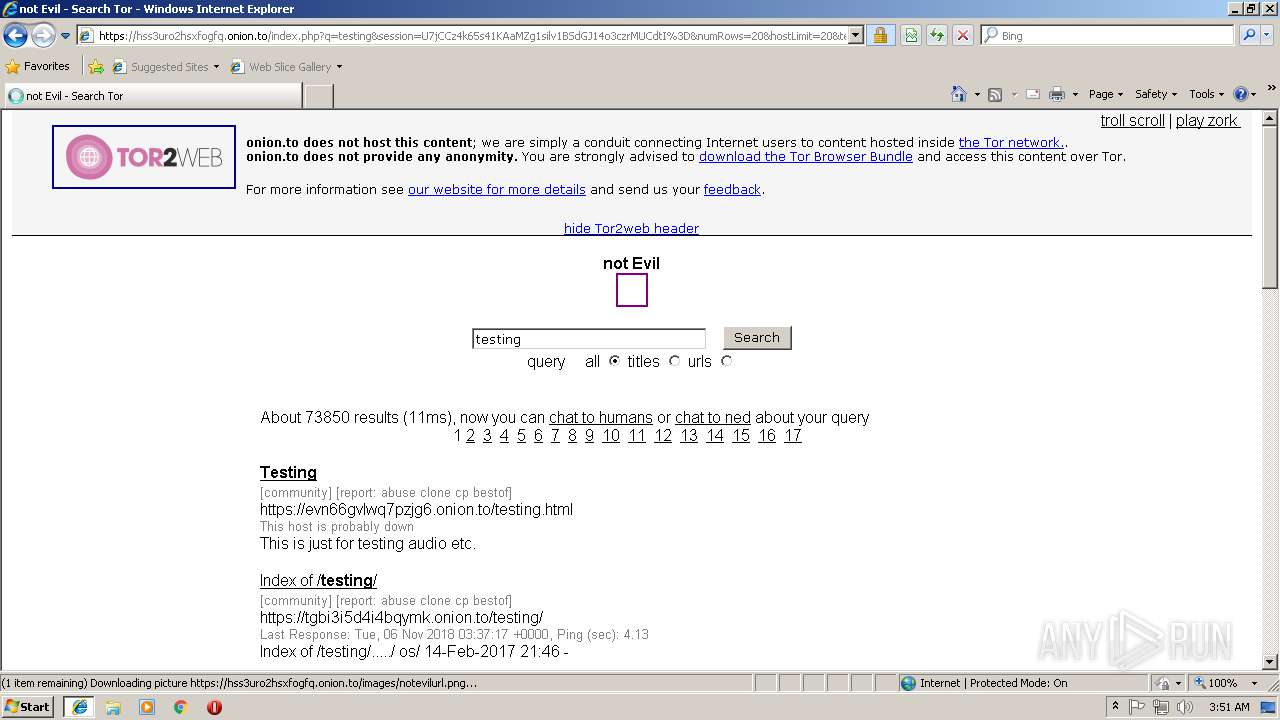
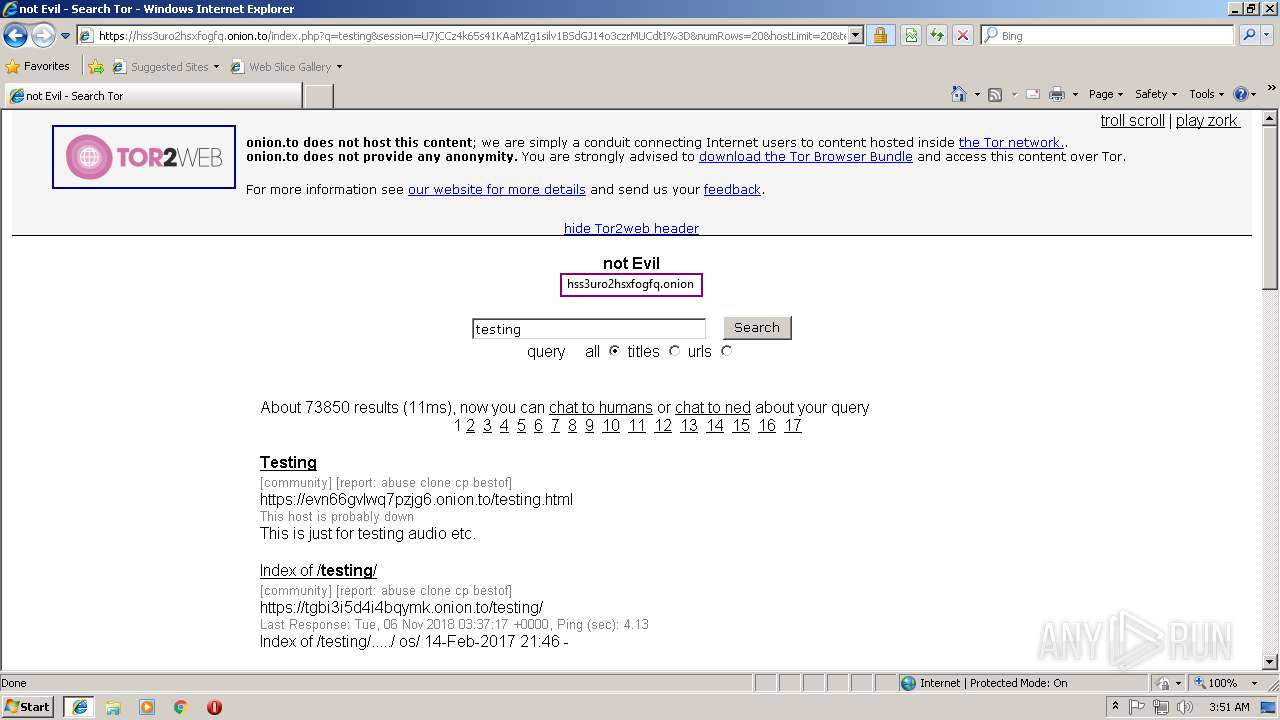
| URL: | https://hss3uro2hsxfogfq.onion.to |
| Full analysis: | https://app.any.run/tasks/137b904c-4286-41b6-920f-d7b5ed044358 |
| Verdict: | Malicious activity |
| Analysis date: | November 13, 2018, 03:50:19 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 440351163F1CE39659EF0C7601700BFA |
| SHA1: | 5BE2E17DB7BDA544587B4A92A29331A7A96C94A5 |
| SHA256: | A348ACB746264AB8545BAA4787832D08CE174C16C2191E32DE1C8AD70F4E88BD |
| SSDEEP: | 3:N8qWqGLMK/s:2qWqcMl |
MALICIOUS
Connects to CnC server
- iexplore.exe (PID: 3068)
SUSPICIOUS
No suspicious indicators.INFO
Changes internet zones settings
- iexplore.exe (PID: 3360)
Application launched itself
- iexplore.exe (PID: 3360)
Creates files in the user directory
- iexplore.exe (PID: 3360)
- iexplore.exe (PID: 3068)
Reads Internet Cache Settings
- iexplore.exe (PID: 3068)
Dropped object may contain TOR URL's
- iexplore.exe (PID: 3068)
- iexplore.exe (PID: 3360)
Dropped object may contain URL to Tor Browser
- iexplore.exe (PID: 3068)
Reads settings of System Certificates
- iexplore.exe (PID: 3360)
Reads internet explorer settings
- iexplore.exe (PID: 3068)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
34
Monitored processes
2
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3068 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3360 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3360 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
441
Read events
368
Write events
70
Delete events
3
Modification events
| (PID) Process: | (3360) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3360) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3360) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3360) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (3360) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3360) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000069000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3360) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {4C0193C7-E6F7-11E8-BFAB-5254004AAD11} |
Value: 0 | |||
| (PID) Process: | (3360) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (3360) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 3 | |||
| (PID) Process: | (3360) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E2070B0002000D00030032002D00E701 | |||
Executable files
0
Suspicious files
1
Text files
8
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3360 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\RB73MZ6Y\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 3360 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3068 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\PP6KS563\tor2web[1].css | — | |
MD5:— | SHA256:— | |||
| 3068 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\PP6KS563\tor2web-small[1].png | — | |
MD5:— | SHA256:— | |||
| 3068 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\tor2web[1].css | — | |
MD5:— | SHA256:— | |||
| 3068 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\tor2web-small[1].png | — | |
MD5:— | SHA256:— | |||
| 3068 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\hss3uro2hsxfogfq_onion_to[1].htm | html | |
MD5:— | SHA256:— | |||
| 3068 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\U2ZG9DE0\tor2web[1].js | text | |
MD5:— | SHA256:— | |||
| 3068 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\notevilurl[1].png | image | |
MD5:— | SHA256:— | |||
| 3360 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\SystemCertificates\My\Certificates\E02357FC7708441D4B0BE5F371F4B28961870F70 | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
10
DNS requests
3
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3360 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3068 | iexplore.exe | 35.170.95.94:443 | www.vpnranks.com | Amazon.com, Inc. | US | unknown |
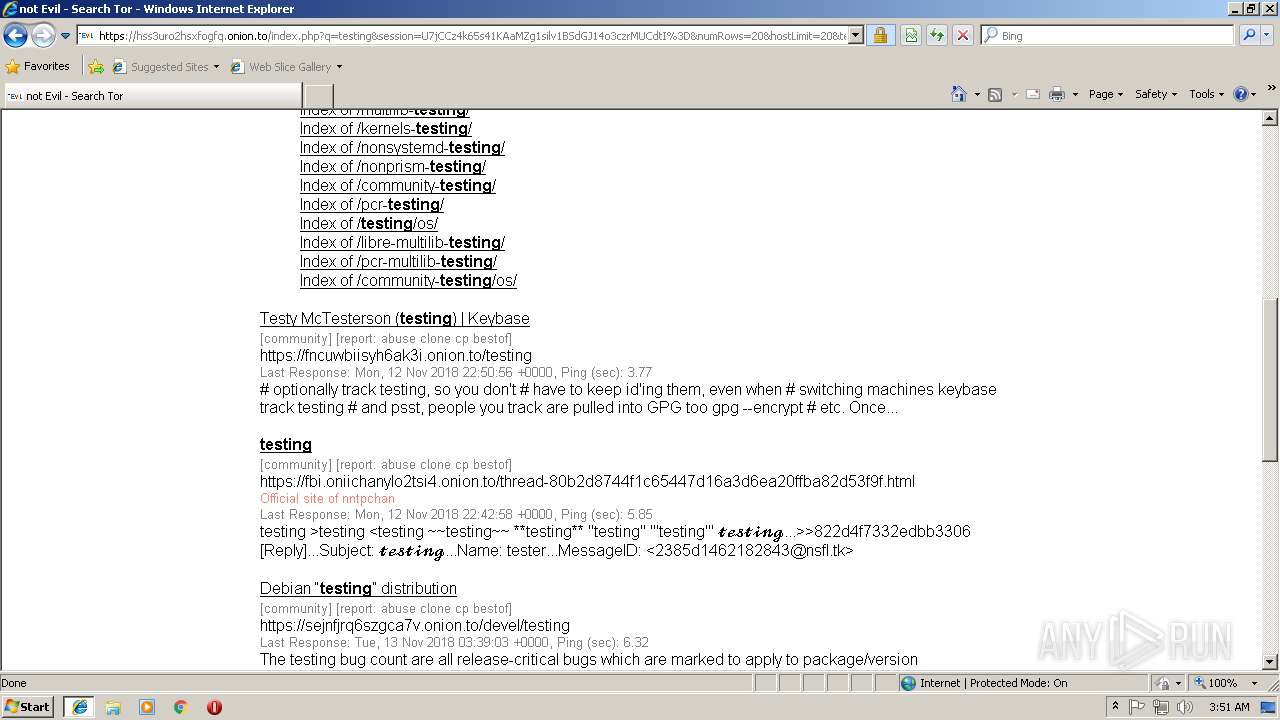
3360 | iexplore.exe | 185.100.85.150:443 | hss3uro2hsxfogfq.onion.to | Flokinet Ltd | RO | malicious |
3068 | iexplore.exe | 185.100.85.150:443 | hss3uro2hsxfogfq.onion.to | Flokinet Ltd | RO | malicious |
3360 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
hss3uro2hsxfogfq.onion.to |
| malicious |
www.vpnranks.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1056 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to .onion proxy Domain (onion.to) |
3068 | iexplore.exe | A Network Trojan was detected | ET CNC Ransomware Tracker Reported CnC Server group 23 |
3068 | iexplore.exe | A Network Trojan was detected | ET CURRENT_EVENTS Tor2Web .onion Proxy Service SSL Cert (2) |
3068 | iexplore.exe | A Network Trojan was detected | ET CURRENT_EVENTS Tor2Web .onion Proxy Service SSL Cert (2) |
3068 | iexplore.exe | A Network Trojan was detected | ET CURRENT_EVENTS Tor2Web .onion Proxy Service SSL Cert (2) |
3068 | iexplore.exe | A Network Trojan was detected | ET CURRENT_EVENTS Tor2Web .onion Proxy Service SSL Cert (2) |
3068 | iexplore.exe | A Network Trojan was detected | ET CURRENT_EVENTS Tor2Web .onion Proxy Service SSL Cert (2) |
3360 | iexplore.exe | A Network Trojan was detected | ET CURRENT_EVENTS Tor2Web .onion Proxy Service SSL Cert (2) |