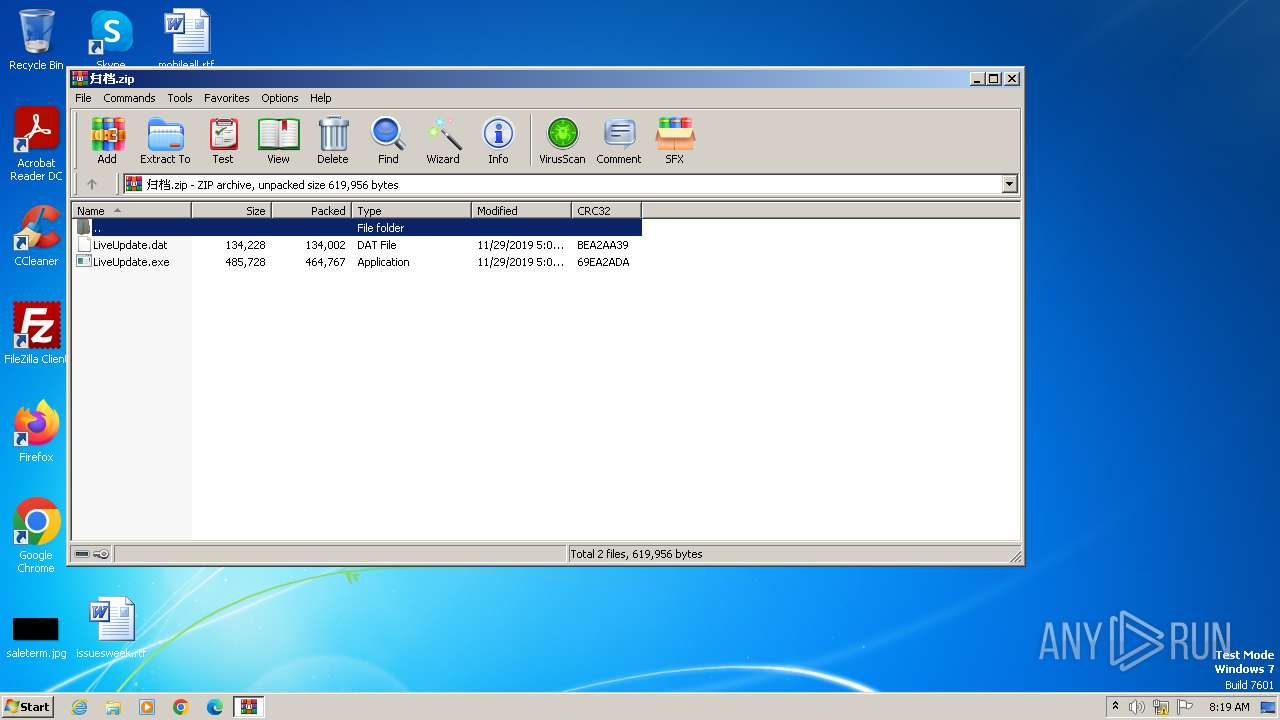
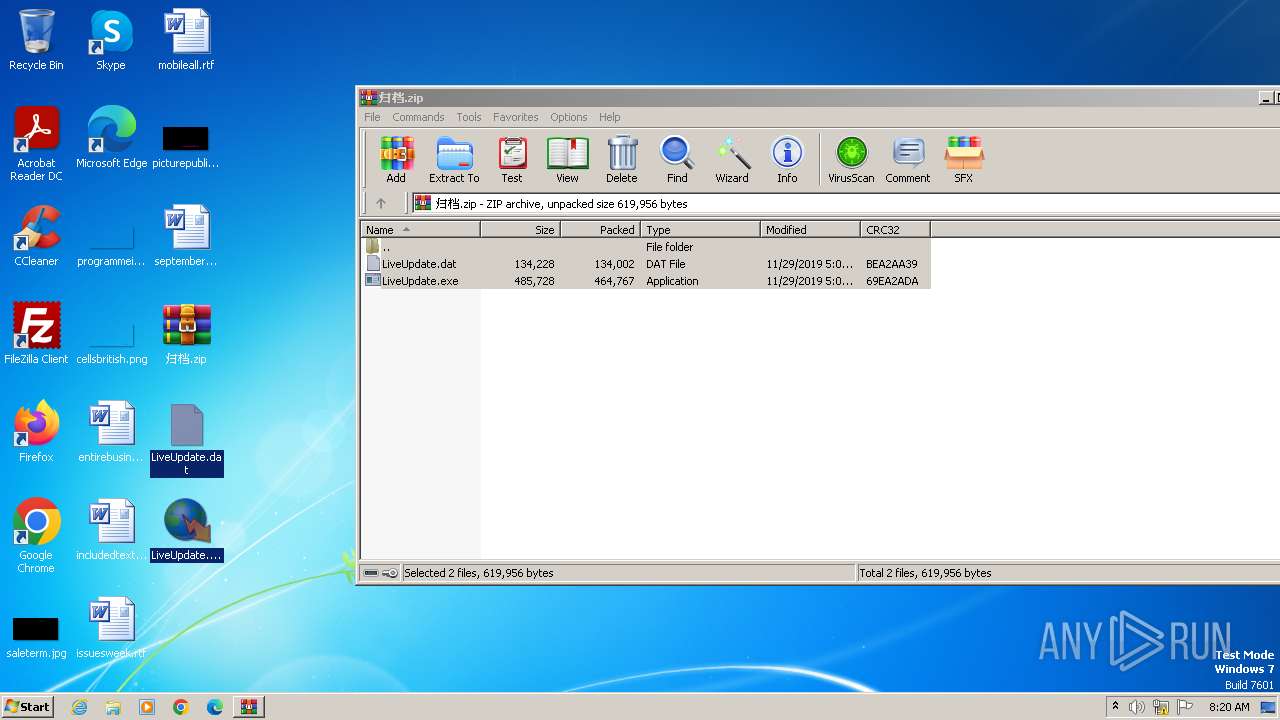
| File name: | 归档.zip |
| Full analysis: | https://app.any.run/tasks/7baf4f7e-e22d-4d95-9369-e24039b261f6 |
| Verdict: | Malicious activity |
| Analysis date: | May 06, 2024, 07:19:31 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 5E79BF1942BFA085570B880093465CA7 |
| SHA1: | 967DF8C89F90AD6B62828895C82780488F7599AB |
| SHA256: | A347401E7C7A6BDA32728E056898DE93FB6B00C369C05ED33221310843184415 |
| SSDEEP: | 24576:yvjOMZUmAgz1GBKtQLuhWaAaepzzF4Mi5LgeIe3EwKThAHcqABH0qcDLomLGgPV1:yvjOMZUmAmcMtQLuhWaAaepzzF4Mi5Ll |
MALICIOUS
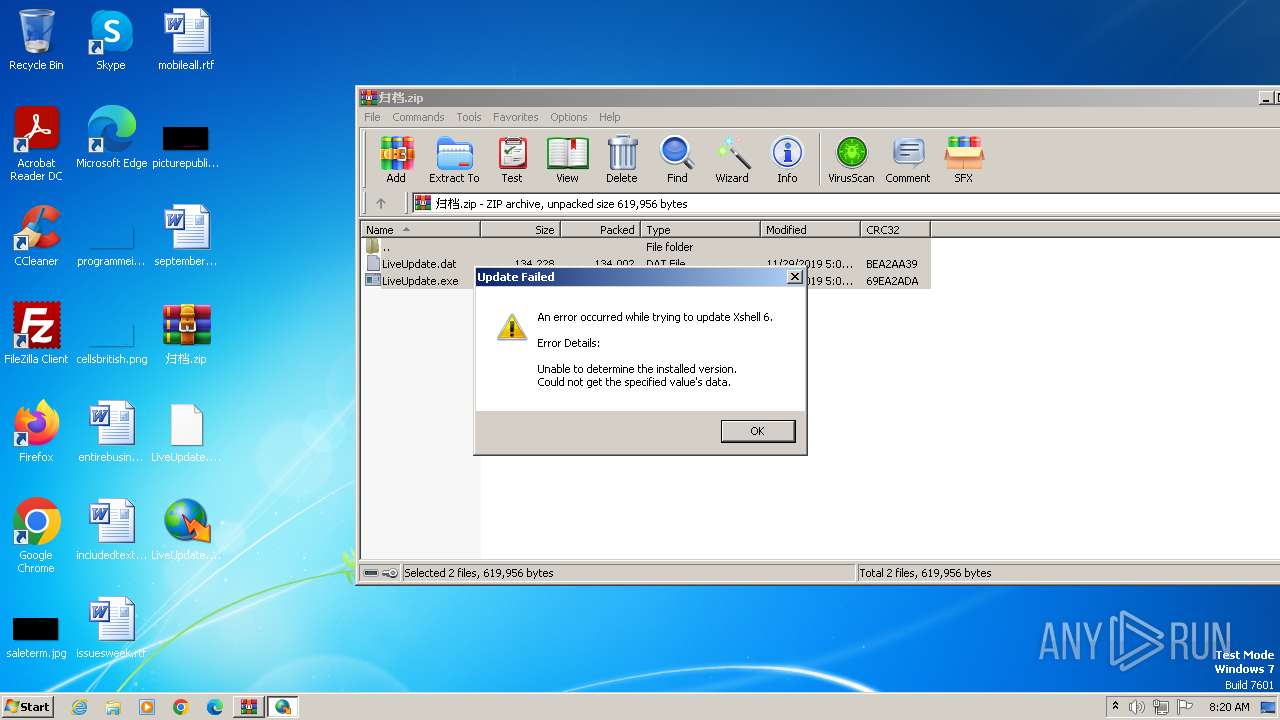
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3988)
- LiveUpdate.exe (PID: 752)
- xsh1.tmp (PID: 316)
SUSPICIOUS
Reads the Windows owner or organization settings
- LiveUpdate.exe (PID: 752)
- LiveUpdate.exe (PID: 588)
Reads the Internet Settings
- LiveUpdate.exe (PID: 752)
- LiveUpdate.exe (PID: 588)
Executable content was dropped or overwritten
- xsh1.tmp (PID: 316)
- LiveUpdate.exe (PID: 752)
Starts itself from another location
- xsh1.tmp (PID: 316)
Reads security settings of Internet Explorer
- LiveUpdate.exe (PID: 752)
- LiveUpdate.exe (PID: 588)
Checks Windows Trust Settings
- LiveUpdate.exe (PID: 752)
- LiveUpdate.exe (PID: 588)
Reads settings of System Certificates
- LiveUpdate.exe (PID: 752)
- LiveUpdate.exe (PID: 588)
Starts application with an unusual extension
- LiveUpdate.exe (PID: 752)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3988)
Manual execution by a user
- LiveUpdate.exe (PID: 752)
- wmpnscfg.exe (PID: 1652)
Reads the computer name
- LiveUpdate.exe (PID: 752)
- wmpnscfg.exe (PID: 1652)
- LiveUpdate.exe (PID: 588)
Checks supported languages
- LiveUpdate.exe (PID: 752)
- xsh1.tmp (PID: 316)
- wmpnscfg.exe (PID: 1652)
- LiveUpdate.exe (PID: 588)
Create files in a temporary directory
- LiveUpdate.exe (PID: 752)
- xsh1.tmp (PID: 316)
- LiveUpdate.exe (PID: 588)
Reads the machine GUID from the registry
- LiveUpdate.exe (PID: 752)
- LiveUpdate.exe (PID: 588)
Checks proxy server information
- LiveUpdate.exe (PID: 752)
- LiveUpdate.exe (PID: 588)
Creates files or folders in the user directory
- LiveUpdate.exe (PID: 752)
Reads the software policy settings
- LiveUpdate.exe (PID: 752)
- LiveUpdate.exe (PID: 588)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0008 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:11:29 13:09:28 |
| ZipCRC: | 0xbea2aa39 |
| ZipCompressedSize: | 134002 |
| ZipUncompressedSize: | 134228 |
| ZipFileName: | LiveUpdate.dat |
Total processes
39
Monitored processes
5
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 316 | "C:\Users\admin\AppData\Local\Temp\xsh1.tmp" "/TUCPS:LiveUpdate.exe" "/DATFILE:C:\Users\admin\AppData\Local\Temp\Liv1.tmp" /TURC | C:\Users\admin\AppData\Local\Temp\xsh1.tmp | LiveUpdate.exe | ||||||||||||
User: admin Company: Indigo Rose Corporation Integrity Level: MEDIUM Description: TrueUpdate Client Exit code: 0 Version: 3.8.1.0 Modules
| |||||||||||||||
| 588 | "C:\Users\admin\AppData\Local\Temp\LiveUpdate.exe" "/TUDEL:xsh1.tmp" "/DATFILE:C:\USERS\ADMIN\APPDATA\LOCAL\TEMP\LIV1.TMP" "/TURC" | C:\Users\admin\AppData\Local\Temp\LiveUpdate.exe | xsh1.tmp | ||||||||||||
User: admin Company: Indigo Rose Corporation Integrity Level: MEDIUM Description: TrueUpdate Client Exit code: 0 Version: 3.8.1.0 Modules
| |||||||||||||||
| 752 | "C:\Users\admin\Desktop\LiveUpdate.exe" | C:\Users\admin\Desktop\LiveUpdate.exe | explorer.exe | ||||||||||||
User: admin Company: Indigo Rose Corporation Integrity Level: MEDIUM Description: TrueUpdate Client Exit code: 12 Version: 3.8.0.0 Modules
| |||||||||||||||
| 1652 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3988 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\归档.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
12 523
Read events
12 373
Write events
128
Delete events
22
Modification events
| (PID) Process: | (3988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3988) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\归档.zip | |||
| (PID) Process: | (3988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
3
Suspicious files
16
Text files
10
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3988 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3988.33922\LiveUpdate.exe | executable | |
MD5:9050AC019B4C8DDDBC5E250BB87CF9F2 | SHA256:83D225323C8783C84D70AEE1DA5B507DDE1E717AB3233F784FBB1B749DBA11B9 | |||
| 752 | LiveUpdate.exe | C:\Users\admin\AppData\Local\Temp\_ir_tu2_temp_0\_TUProjDT.dat | text | |
MD5:C5B22CBDAF3D5F0BCBB13C668478EA3E | SHA256:E2B81E502E88F393C354B51DE166052C57B4D021D91E6B521F28B8E3BC6866AB | |||
| 752 | LiveUpdate.exe | C:\Users\admin\AppData\Local\Temp\Xshell 6 Update Log.txt | text | |
MD5:719778F8B7986334C7413A972951962D | SHA256:7245D325F76CE72333ED3BD6A5C317C0BCCB8801D54ED5D2A710E49FDE46EB8C | |||
| 752 | LiveUpdate.exe | C:\Users\admin\AppData\Local\Temp\_ir_tu2_temp_0\_tu_DATUP_0\xshell6Beta.ts2 | — | |
MD5:— | SHA256:— | |||
| 752 | LiveUpdate.exe | C:\Users\admin\AppData\Local\Temp\_ir_tu2_temp_0\IRIMG1.JPG | image | |
MD5:E39405E85E09F64CCDE0F59392317DD3 | SHA256:CFD9677E1C0E10B1507F520C4ECD40F68DB78154C0D4E6563403D540F3BF829F | |||
| 752 | LiveUpdate.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B66240B0F6C84BD4857ABA60CF5CE4A0_5043E0F5DF723415C9EECC201C838A62 | binary | |
MD5:E1BAA661F2288EB1D07E4CC8E66CDCD3 | SHA256:AEE9C7588AA6D21852E34F1D027B06D977FC14947184A741677BD4D7FDE1C3F7 | |||
| 3988 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3988.33922\LiveUpdate.dat | compressed | |
MD5:F04205E024C79BEF6B94441B1C98999F | SHA256:FD8ED22B34558606B9F6E0039BAD08612BB4A8FDC472D1B0D716DDDE27C6E07A | |||
| 752 | LiveUpdate.exe | C:\Users\admin\AppData\Local\Temp\_ir_tu2_temp_0\IRIMG2.JPG | image | |
MD5:F6BF82A293B69AA5B47D4E2DE305D45A | SHA256:6A9368CDD7B3FF9B590E206C3536569BC45C338966D0059784959F73FE6281E0 | |||
| 752 | LiveUpdate.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\BAD725C80F9E10846F35D039A996E4A8_88B6AE015495C1ECC395D19C1DD02894 | binary | |
MD5:E5B2BC34FCFC3F95866CFAD27384C421 | SHA256:C84CCF515A77DC7BE2183B746C670AC767CA7AD6E95C146C33B1BD87A4083AB1 | |||
| 752 | LiveUpdate.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:CC63F8B9FADC797D87C8C544B6986865 | SHA256:66B0585929DDE077AF50A06C8115CA0F3440AFE5A347A7D7965091EDECC75598 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
17
DNS requests
10
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
752 | LiveUpdate.exe | GET | 200 | 18.245.65.219:80 | http://ocsp.r2m03.amazontrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQqHI%2BsdmapawQncL1rpCEZZ8gTSAQUVdkYX9IczAHhWLS%2Bq9lVQgHXLgICEAX5O75jmJWGuyFKZzFTNDk%3D | unknown | — | — | unknown |
752 | LiveUpdate.exe | GET | 200 | 216.58.206.67:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | — | — | unknown |
752 | LiveUpdate.exe | GET | 200 | 216.58.206.67:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFCjJ1PwkYAi7fE%3D | unknown | — | — | unknown |
1088 | svchost.exe | GET | 304 | 92.123.77.35:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?90076af29193d397 | unknown | — | — | unknown |
752 | LiveUpdate.exe | GET | 304 | 92.123.77.25:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?be36ae1029c3a67f | unknown | — | — | unknown |
752 | LiveUpdate.exe | GET | 200 | 18.245.39.64:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwdzEkzUBtJnwJkc3SmanzgxeYU%3D | unknown | — | — | unknown |
752 | LiveUpdate.exe | GET | 200 | 18.245.39.64:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | unknown | — | — | unknown |
752 | LiveUpdate.exe | GET | 200 | 108.138.2.173:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
752 | LiveUpdate.exe | 54.218.235.37:443 | transact.netsarang.com | AMAZON-02 | US | unknown |
752 | LiveUpdate.exe | 92.123.77.25:80 | ctldl.windowsupdate.com | Akamai International B.V. | NL | unknown |
752 | LiveUpdate.exe | 108.138.2.173:80 | o.ss2.us | AMAZON-02 | US | unknown |
752 | LiveUpdate.exe | 18.245.39.64:80 | ocsp.rootg2.amazontrust.com | — | US | unknown |
752 | LiveUpdate.exe | 18.245.65.219:80 | ocsp.r2m03.amazontrust.com | — | US | unknown |
752 | LiveUpdate.exe | 172.67.69.54:443 | cdn.netsarang.net | CLOUDFLARENET | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
transact.netsarang.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
o.ss2.us |
| whitelisted |
ocsp.rootg2.amazontrust.com |
| whitelisted |
ocsp.rootca1.amazontrust.com |
| shared |
ocsp.r2m03.amazontrust.com |
| unknown |
cdn.netsarang.net |
| unknown |
ocsp.pki.goog |
| whitelisted |
update.netsarangapi.com |
| unknown |