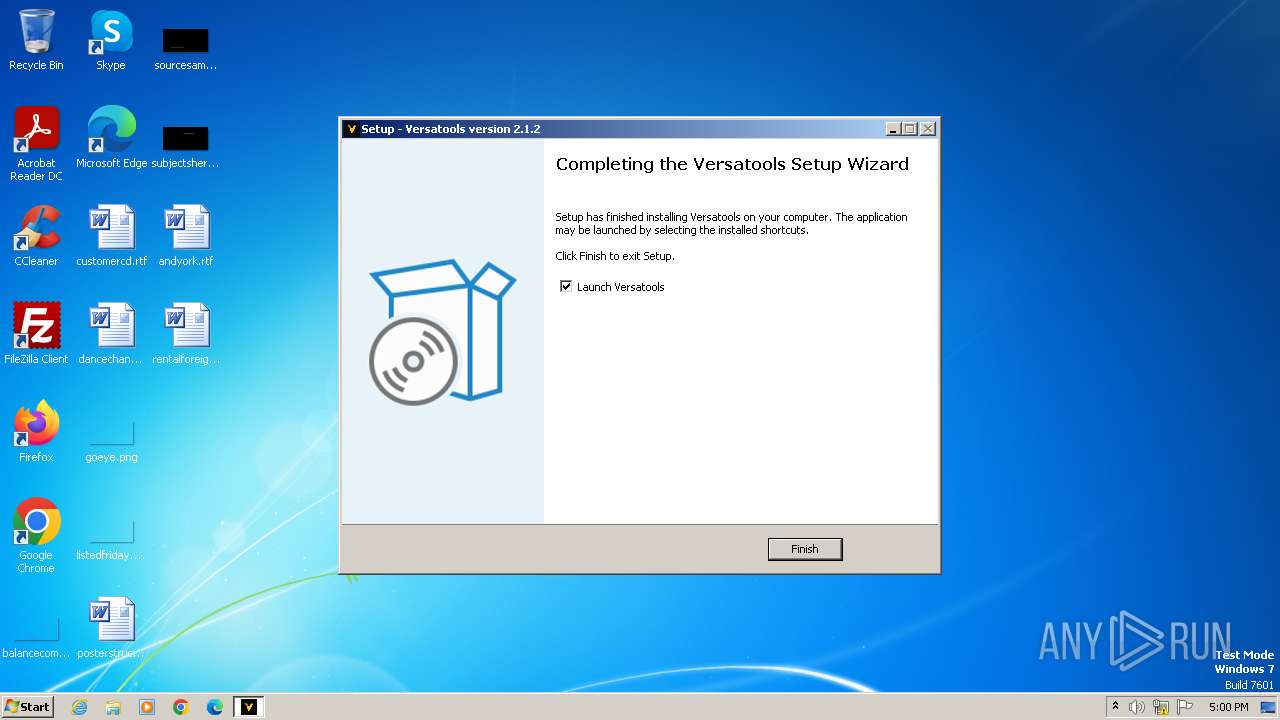
| File name: | versatools-setup.exe |
| Full analysis: | https://app.any.run/tasks/204f438a-7d9a-469d-88e6-9bcc83fd1422 |
| Verdict: | Malicious activity |
| Analysis date: | November 11, 2023, 17:00:17 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 6D4598D873675CAF9C34237F8CE2C2C0 |
| SHA1: | A816C99624214D989B55D14255F9937AE639CFCF |
| SHA256: | A332C64B37D3301ECB4544C594692E73D50AF3F9B6C159AEA691F80A45EBA568 |
| SSDEEP: | 98304:4+cD4dnn332vJUAZq6Wxu/jjfqlp1OISKiorIE9rqbCowwieQ74X40trmBuyXY+7:S0l0420j9CmVHjG0AgzJiuStvvbe |
MALICIOUS
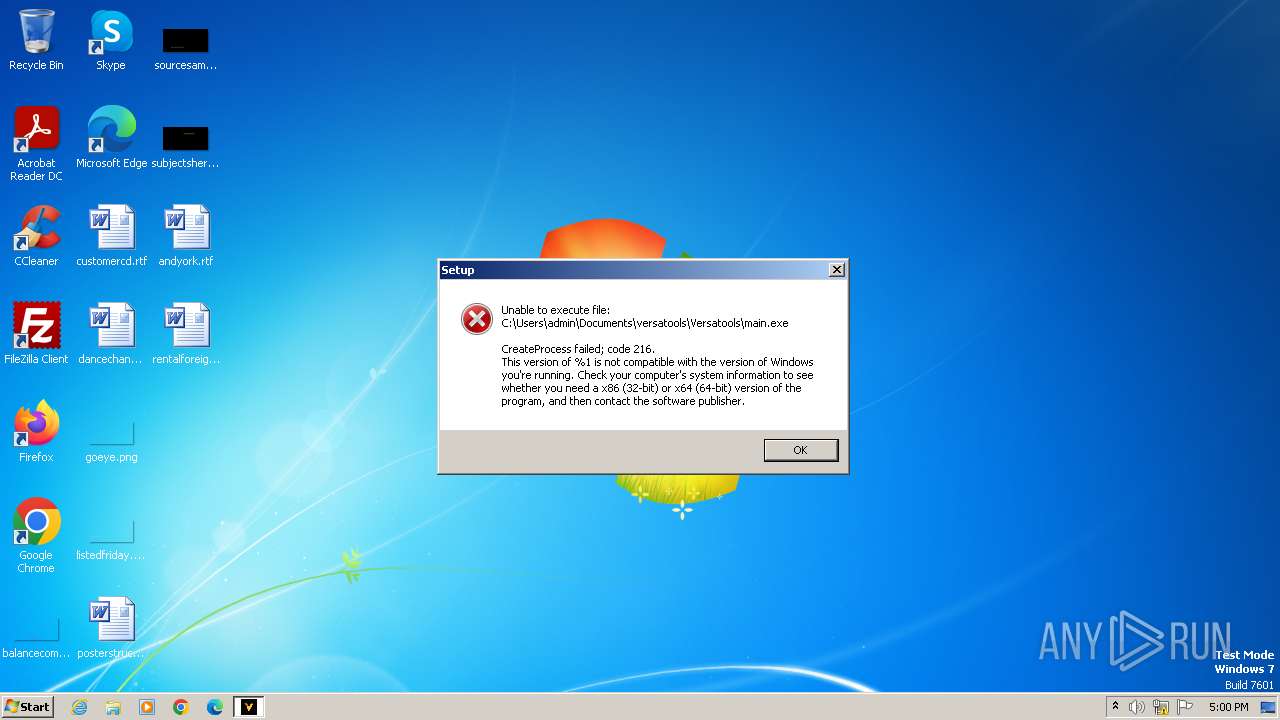
Drops the executable file immediately after the start
- versatools-setup.exe (PID: 3204)
- versatools-setup.tmp (PID: 3196)
Actions looks like stealing of personal data
- versatools-setup.tmp (PID: 3196)
SUSPICIOUS
Reads the Windows owner or organization settings
- versatools-setup.tmp (PID: 3196)
Process drops legitimate windows executable
- versatools-setup.tmp (PID: 3196)
The process drops C-runtime libraries
- versatools-setup.tmp (PID: 3196)
INFO
Checks supported languages
- versatools-setup.exe (PID: 3204)
- versatools-setup.tmp (PID: 3196)
Reads the computer name
- versatools-setup.tmp (PID: 3196)
Create files in a temporary directory
- versatools-setup.exe (PID: 3204)
Creates files or folders in the user directory
- versatools-setup.tmp (PID: 3196)
Manual execution by a user
- taskmgr.exe (PID: 3504)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (67.7) |
|---|---|---|
| .exe | | | Win32 EXE PECompact compressed (generic) (25.6) |
| .exe | | | Win32 Executable (generic) (2.7) |
| .exe | | | Win16/32 Executable Delphi generic (1.2) |
| .exe | | | Generic Win/DOS Executable (1.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:02:15 15:54:16+01:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 741888 |
| InitializedDataSize: | 139264 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb5eec |
| OSVersion: | 6.1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | GarryyBD |
| FileDescription: | Versatools Setup |
| FileVersion: | |
| LegalCopyright: | |
| OriginalFileName: | |
| ProductName: | Versatools |
| ProductVersion: | 2.1.2 |
Total processes
42
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
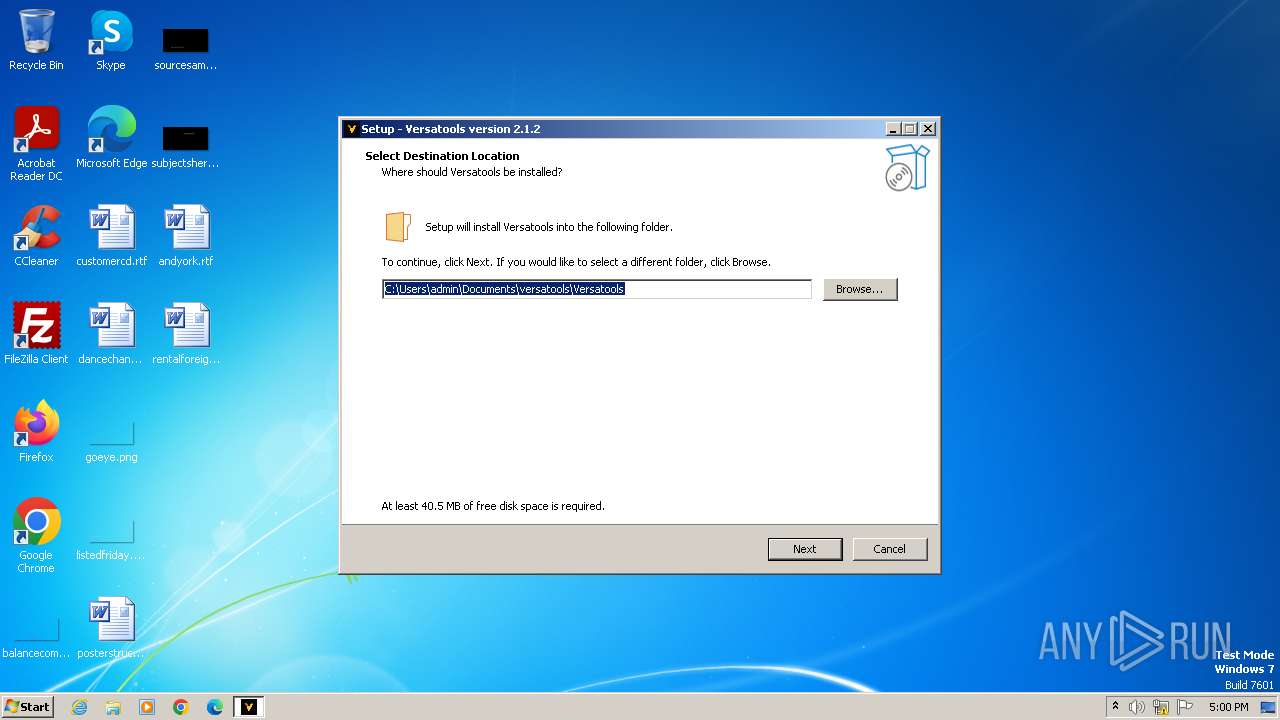
| 3196 | "C:\Users\admin\AppData\Local\Temp\is-7P0HT.tmp\versatools-setup.tmp" /SL5="$60134,15191796,882176,C:\Users\admin\AppData\Local\Temp\versatools-setup.exe" | C:\Users\admin\AppData\Local\Temp\is-7P0HT.tmp\versatools-setup.tmp | versatools-setup.exe | ||||||||||||
User: admin Company: GarryyBD Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 3204 | "C:\Users\admin\AppData\Local\Temp\versatools-setup.exe" | C:\Users\admin\AppData\Local\Temp\versatools-setup.exe | — | explorer.exe | |||||||||||
User: admin Company: GarryyBD Integrity Level: MEDIUM Description: Versatools Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 3504 | "C:\Windows\system32\taskmgr.exe" /4 | C:\Windows\System32\taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Exit code: 1073807364 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
891
Read events
884
Write events
1
Delete events
6
Modification events
| (PID) Process: | (3196) versatools-setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | RegFilesHash |
Value: 1274D6617D09B3C5796697A07F86A2F2EB17E867204C0821797B9DF13C5A4445 | |||
| (PID) Process: | (3196) versatools-setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | RegFiles0000 |
Value: C:\Users\admin\Documents\versatools\Versatools\main.exe | |||
| (PID) Process: | (3196) versatools-setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (3196) versatools-setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | SessionHash |
Value: 00290DB77DB7B27959C70C78CCDA545A374A0057236B6B1894030E2259B7C41B | |||
| (PID) Process: | (3196) versatools-setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | Owner |
Value: 7C0C0000EAA09993C014DA01 | |||
| (PID) Process: | (3196) versatools-setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3504) taskmgr.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\TaskManager |
| Operation: | write | Name: | Preferences |
Value: 30030000E803000001000000010000004401000076000000DC0200005C0200000200000001000000000000000000000001000000000000000100000000000000000000000200000004000000090000001D000000FFFFFFFF00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000009C00000040000000210000004600000052000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF0000000002000000010000000300000004000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF0500000000000000FFFFFFFF00000000020000000300000004000000FFFFFFFF00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000630060003C005A00FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF000000000000010000000200000003000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF0400000000000000FFFFFFFF02000000FFFFFFFF4F00000028000000970000003400000050000000000000000100000002000000030000000400000000000000FFFFFFFF43000000000000000000000001000000 | |||
Executable files
172
Suspicious files
20
Text files
108
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3196 | versatools-setup.tmp | C:\Users\admin\Documents\versatools\Versatools\is-K2GOL.tmp | executable | |
MD5:6D10D60891577FA2E338050EE7915594 | SHA256:01D2E92B4D5187620B7C4520509809F42EE07231FA1ECBB06CECD3DF1072604F | |||
| 3196 | versatools-setup.tmp | C:\Users\admin\Documents\versatools\Versatools\is-P58G4.tmp | executable | |
MD5:A5B142425B889F6B27F264C8C131A29C | SHA256:DC0D05807133D554EB817F7DB8BC4B1FFAEC784644CC8FB5924134C7FB144B8F | |||
| 3196 | versatools-setup.tmp | C:\Users\admin\Documents\versatools\Versatools\api-ms-win-core-console-l1-1-0.dll | executable | |
MD5:FA978D1DCBEFA3EB7C09AFC61758B4FD | SHA256:1E089F3FCF76338BFCB963924B4DE95CD8CA0FE9C99ACCD5FFDA38ECB2081629 | |||
| 3196 | versatools-setup.tmp | C:\Users\admin\Documents\versatools\Versatools\is-VUI56.tmp | executable | |
MD5:5F7D6B8BF064F49C3CA8887613DEC516 | SHA256:65A8808818DA35F78FB232C39DE9FBF8B2D87D3EDB438B5A1301F6AD3C734D82 | |||
| 3196 | versatools-setup.tmp | C:\Users\admin\Documents\versatools\Versatools\main.exe | executable | |
MD5:5F7D6B8BF064F49C3CA8887613DEC516 | SHA256:65A8808818DA35F78FB232C39DE9FBF8B2D87D3EDB438B5A1301F6AD3C734D82 | |||
| 3196 | versatools-setup.tmp | C:\Users\admin\Documents\versatools\Versatools\is-ISMK4.tmp | executable | |
MD5:FA978D1DCBEFA3EB7C09AFC61758B4FD | SHA256:1E089F3FCF76338BFCB963924B4DE95CD8CA0FE9C99ACCD5FFDA38ECB2081629 | |||
| 3196 | versatools-setup.tmp | C:\Users\admin\Documents\versatools\Versatools\unins000.exe | executable | |
MD5:6D10D60891577FA2E338050EE7915594 | SHA256:01D2E92B4D5187620B7C4520509809F42EE07231FA1ECBB06CECD3DF1072604F | |||
| 3196 | versatools-setup.tmp | C:\Users\admin\Documents\versatools\Versatools\api-ms-win-core-debug-l1-1-0.dll | executable | |
MD5:635BF381649D6BE0673D8357455631FA | SHA256:3A21F51D6111A46EB1F77C20AF566EE2BC4C5939110B99A3DAAEF9EE15895B86 | |||
| 3196 | versatools-setup.tmp | C:\Users\admin\Documents\versatools\Versatools\is-V2JI9.tmp | executable | |
MD5:635BF381649D6BE0673D8357455631FA | SHA256:3A21F51D6111A46EB1F77C20AF566EE2BC4C5939110B99A3DAAEF9EE15895B86 | |||
| 3196 | versatools-setup.tmp | C:\Users\admin\Documents\versatools\Versatools\is-8EG13.tmp | executable | |
MD5:E36AC4AF8B02564857EDAA68E2BBE1C0 | SHA256:4237C0D089329B605D5416DAE4005E1C4808A284B51DBAAFE07A4B2CC7FCFB00 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |