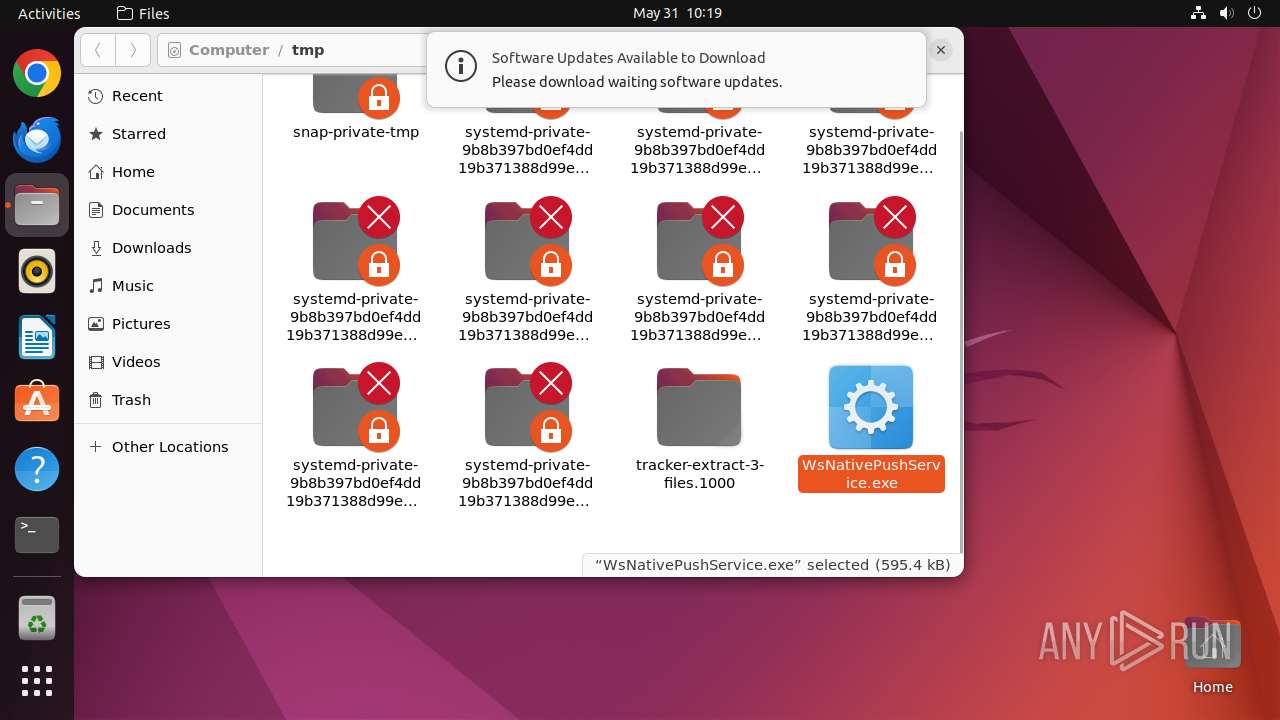
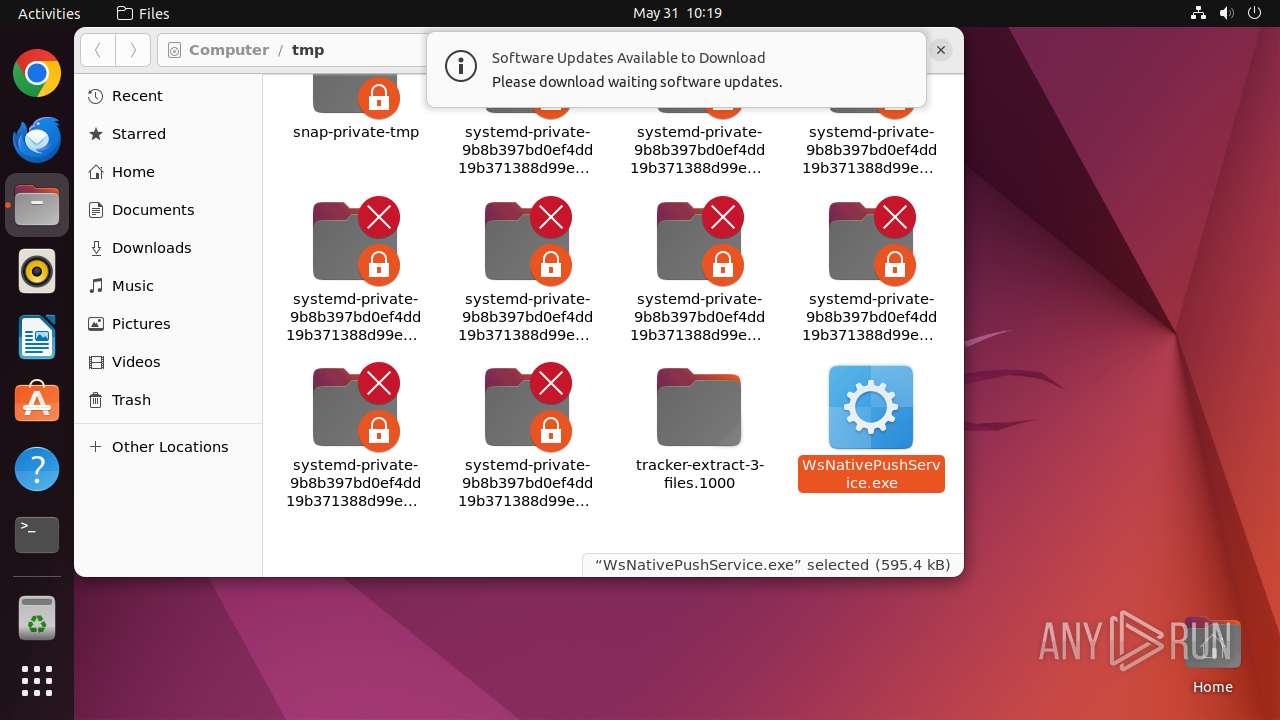
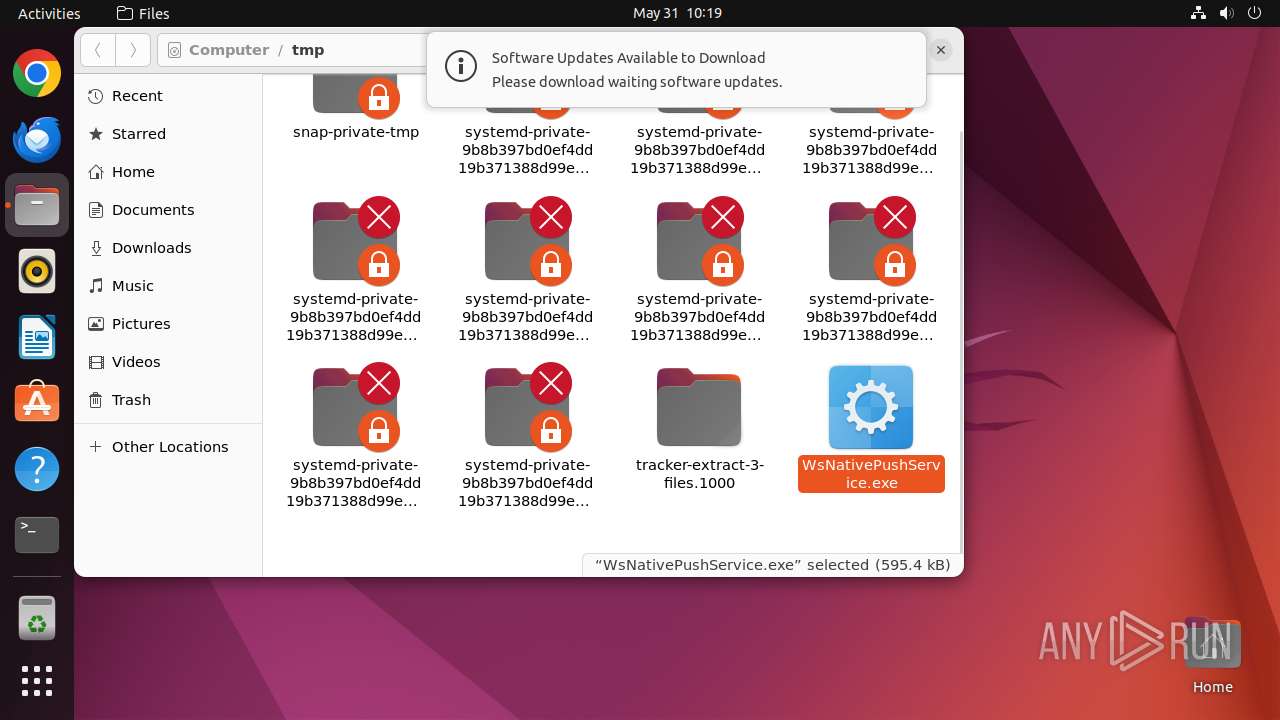
| File name: | WsNativePushService.exe |
| Full analysis: | https://app.any.run/tasks/caba314e-0853-4f76-bb12-881810b4c208 |
| Verdict: | Malicious activity |
| Analysis date: | May 31, 2024, 09:19:41 |
| OS: | Ubuntu 22.04.2 |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (console) x86-64, for MS Windows |
| MD5: | 05D4608C1564F4BC4F2237D17129A9A0 |
| SHA1: | 46B1EAFFCE9E156B44741FC6CFECCA2FC0ED87D9 |
| SHA256: | A32F330083DA08FB2C1B56E9EAEDDD46BE96EDC39A3C2ABA30779D4533E0A402 |
| SSDEEP: | 24576:u4E+vTdRbc06hSj5tlqcyg8WNOYRLDlMJ/YhNzSXm:u4E+vTdRA06hSj5tlqcyg8WNOYRLDlM2 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Checks DMI information (probably VM detection)
- systemd-hostnamed (PID: 11971)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2023:08:22 11:36:38+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.29 |
| CodeSize: | 427520 |
| InitializedDataSize: | 153088 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x38360 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 1.0.1.0 |
| ProductVersionNumber: | 1.0.1.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Wondershare |
| FileDescription: | WsNativePushService |
| FileVersion: | 1.0.1.0 |
| InternalName: | WsNativePushService.exe |
| LegalCopyright: | Copyright(c) 2023 Wondershare. All rights reserved. |
| OriginalFileName: | WsNativePushService.exe |
| ProductName: | Wondershare NativePush |
| ProductVersion: | 1.0.1.0 |
Total processes
222
Monitored processes
9
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 11949 | /bin/sh -c "DISPLAY=:0 sudo -iu user nautilus /tmp/WsNativePushService\.exe " | /bin/sh | — | any-guest-agent |
User: root Integrity Level: UNKNOWN | ||||
| 11950 | sudo -iu user nautilus /tmp/WsNativePushService.exe | /usr/bin/sudo | — | sh |
User: root Integrity Level: UNKNOWN | ||||
| 11951 | systemctl --user --global is-enabled snap.snapd-desktop-integration.snapd-desktop-integration.service | /usr/bin/systemctl | — | snapd |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 11952 | nautilus /tmp/WsNativePushService.exe | /usr/bin/nautilus | — | sudo |
User: user Integrity Level: UNKNOWN | ||||
| 11953 | /usr/bin/locale-check C.UTF-8 | /usr/bin/locale-check | — | nautilus |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 11954 | systemctl --user --global is-enabled snap.snapd-desktop-integration.snapd-desktop-integration.service | /usr/bin/systemctl | — | snapd |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 11971 | /lib/systemd/systemd-hostnamed | /lib/systemd/systemd-hostnamed | — | systemd |
User: root Integrity Level: UNKNOWN Exit code: 482 | ||||
| 11978 | systemctl --user --global is-enabled snap.snapd-desktop-integration.snapd-desktop-integration.service | /usr/bin/systemctl | — | snapd |
User: root Integrity Level: UNKNOWN Exit code: 482 | ||||
| 11979 | systemctl --user --global is-enabled snap.snapd-desktop-integration.snapd-desktop-integration.service | /usr/bin/systemctl | — | snapd |
User: root Integrity Level: UNKNOWN Exit code: 482 | ||||
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 11952 | nautilus | /home/user/.local/share/nautilus/tags/meta.db-wal | — | |
MD5:— | SHA256:— | |||
| 11952 | nautilus | /home/user/.local/share/nautilus/tags/meta.db-shm | — | |
MD5:— | SHA256:— | |||
| 11952 | nautilus | /home/user/.local/share/nautilus/tags/.meta.isrunning | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
6
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 204 | 91.189.91.48:80 | http://connectivity-check.ubuntu.com/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
470 | avahi-daemon | 224.0.0.251:5353 | — | — | — | unknown |
— | — | 91.189.91.48:80 | — | Canonical Group Limited | US | unknown |
— | — | 91.189.91.97:80 | — | Canonical Group Limited | US | unknown |
— | — | 185.125.188.55:443 | api.snapcraft.io | Canonical Group Limited | GB | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.snapcraft.io |
| unknown |
175.100.168.192.in-addr.arpa |
| unknown |
connectivity-check.ubuntu.com |
| unknown |