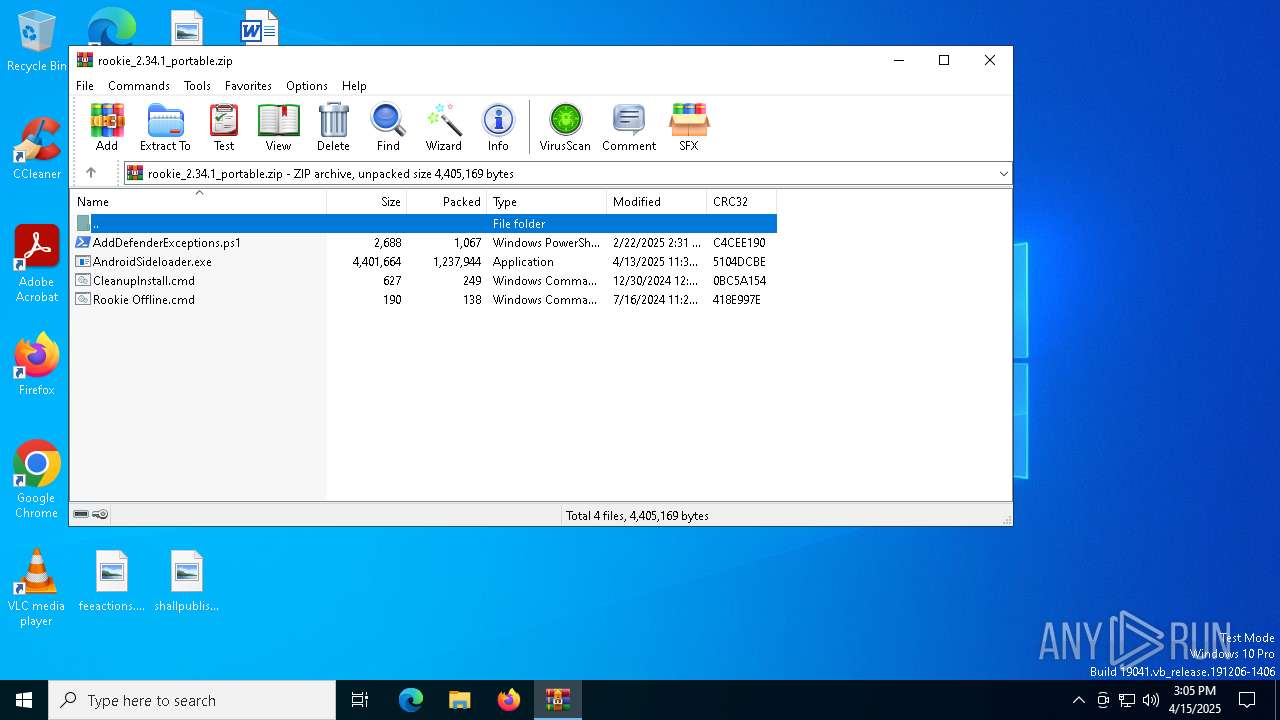
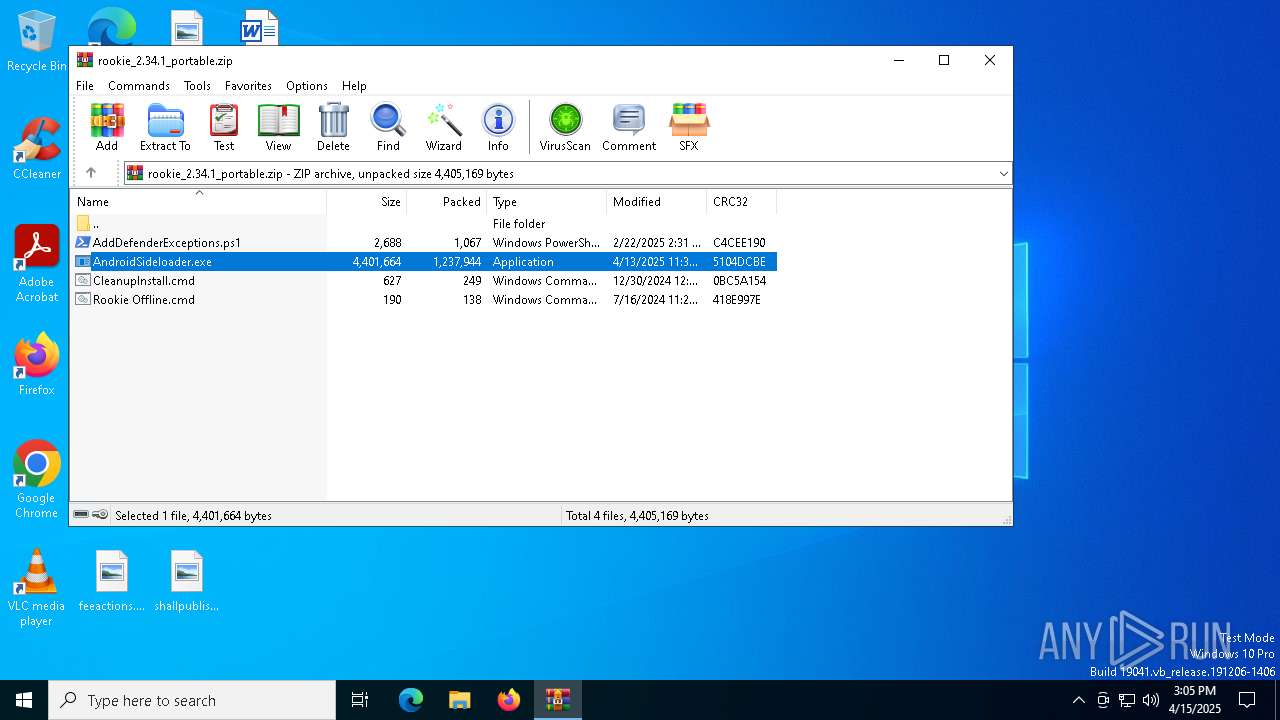
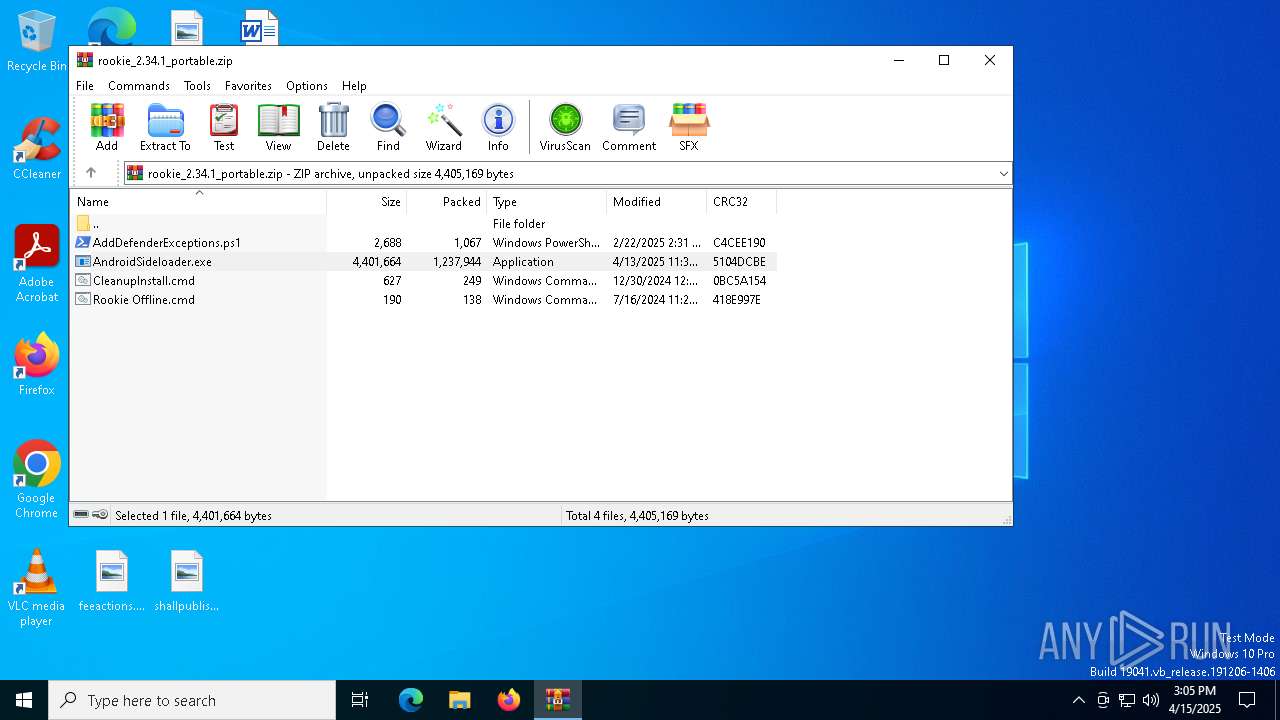
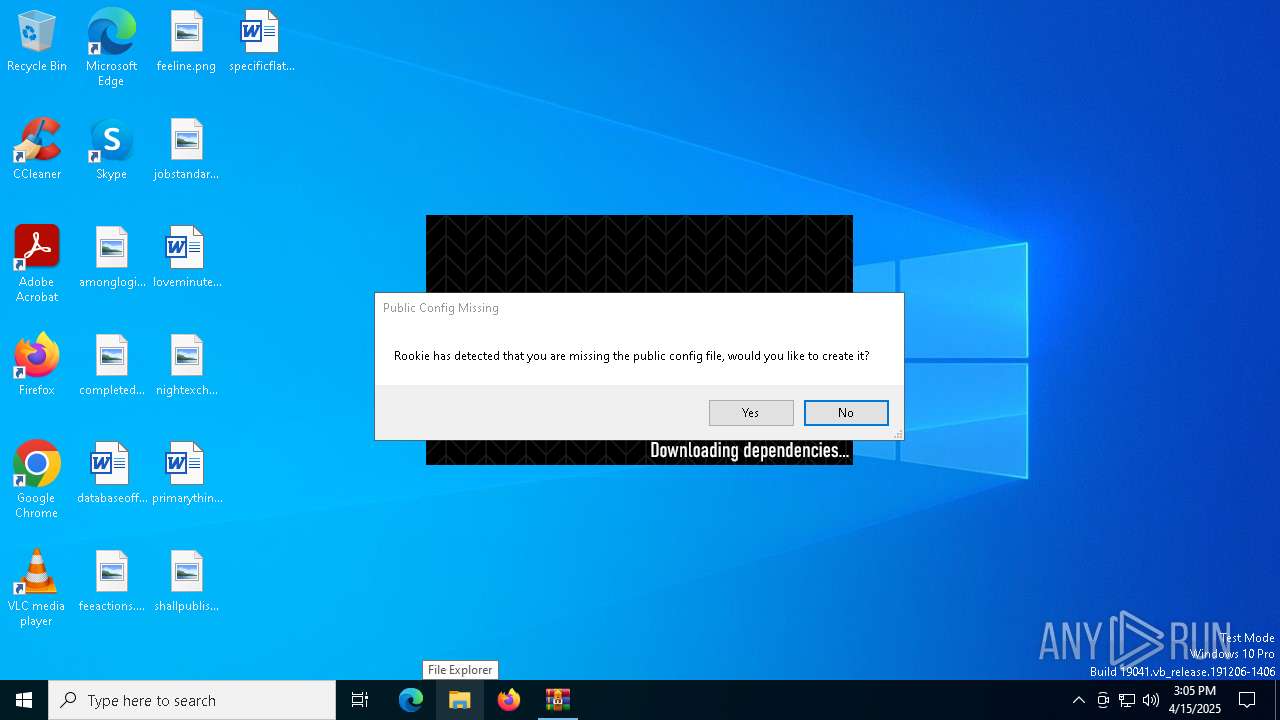
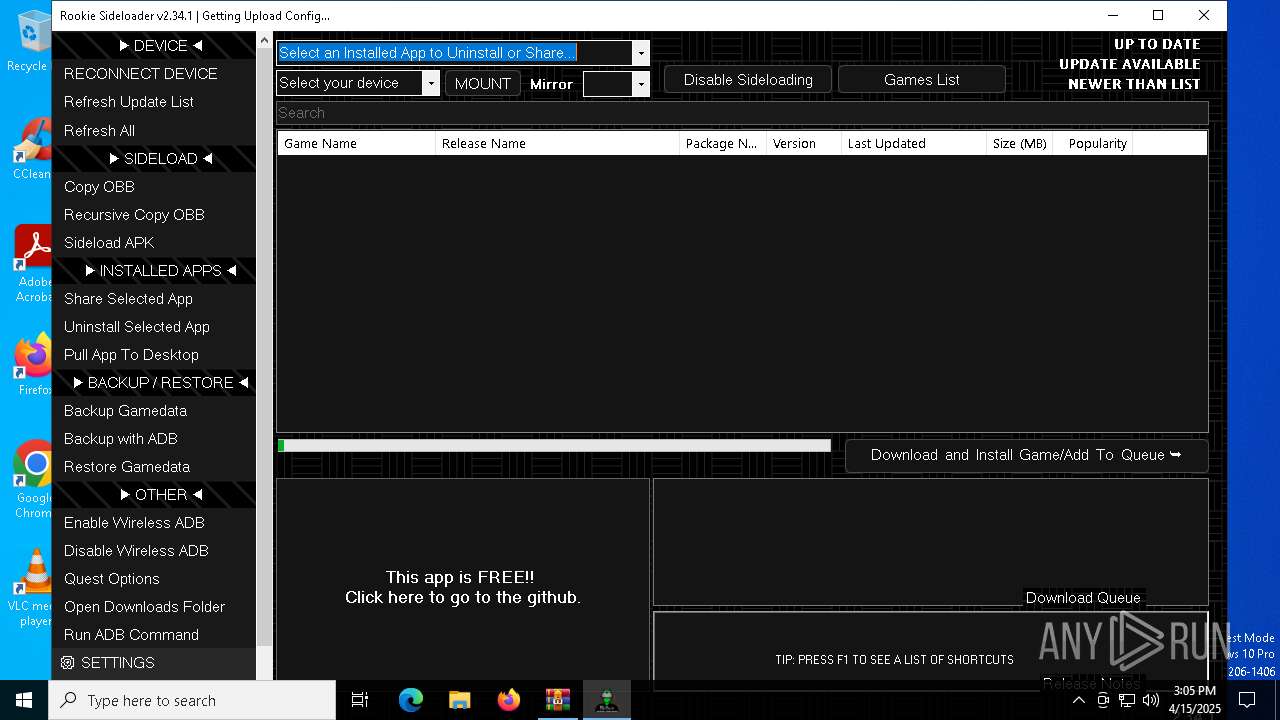
| File name: | rookie_2.34.1_portable.zip |
| Full analysis: | https://app.any.run/tasks/fe6190b5-08e7-4b92-8492-b16767a2194a |
| Verdict: | Malicious activity |
| Analysis date: | April 15, 2025, 15:05:02 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | F036FCDB20B031D103DDC48A7D4E3FDE |
| SHA1: | 1122163C4DF062887A6943826ED5213242200306 |
| SHA256: | A329B31B2FDA9F72C907B2688F6EE6D64B2E1A9A0D8EFD186B3D64B930550800 |
| SSDEEP: | 49152:9dfIxtxcItUxnyKtzSdEkuexaVDsBVZ4hCsgLUUK/JfCVODmXZw9xBjMnfqd7tLk:7fcTRKsdEtexaVIBVZ4h5gYUK/JfCVOS |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6028)
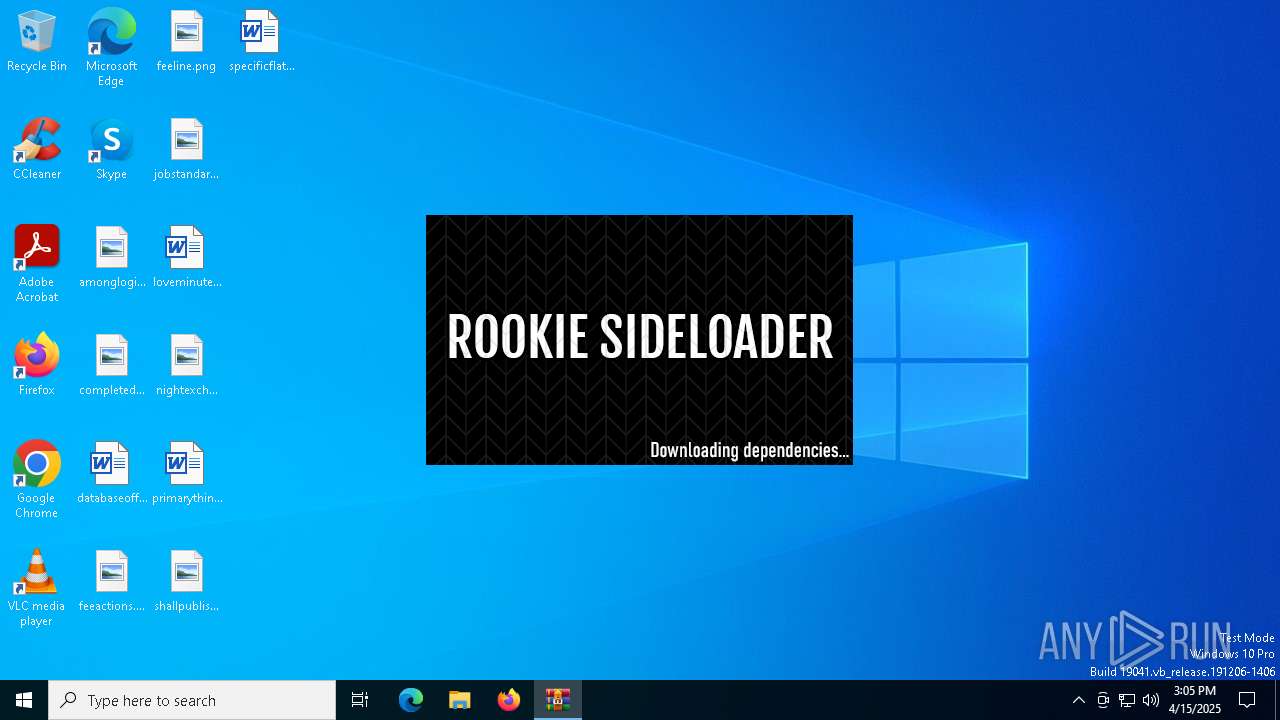
- AndroidSideloader.exe (PID: 7672)
- AndroidSideloader.exe (PID: 7776)
Executable content was dropped or overwritten
- AndroidSideloader.exe (PID: 7672)
- 7z.exe (PID: 7820)
- AndroidSideloader.exe (PID: 7776)
Drops 7-zip archiver for unpacking
- AndroidSideloader.exe (PID: 7672)
- AndroidSideloader.exe (PID: 7776)
Application launched itself
- adb.exe (PID: 1324)
- adb.exe (PID: 8116)
RCLONE has been detected
- rclone.exe (PID: 5868)
- rclone.exe (PID: 7328)
- rclone.exe (PID: 7500)
- rclone.exe (PID: 7624)
INFO
Create files in a temporary directory
- AndroidSideloader.exe (PID: 7672)
- 7z.exe (PID: 8144)
- AndroidSideloader.exe (PID: 7776)
- adb.exe (PID: 1628)
- 7z.exe (PID: 2392)
- 7z.exe (PID: 616)
- rclone.exe (PID: 7624)
- rclone.exe (PID: 7328)
Checks supported languages
- AndroidSideloader.exe (PID: 7672)
- 7z.exe (PID: 8144)
- adb.exe (PID: 1760)
- 7z.exe (PID: 7820)
- AndroidSideloader.exe (PID: 7776)
- adb.exe (PID: 1324)
- adb.exe (PID: 1628)
- rclone.exe (PID: 5868)
- rclone.exe (PID: 7328)
- 7z.exe (PID: 2392)
- adb.exe (PID: 1164)
- adb.exe (PID: 6272)
- rclone.exe (PID: 7500)
- rclone.exe (PID: 7624)
- 7z.exe (PID: 616)
- adb.exe (PID: 7960)
- adb.exe (PID: 6584)
- adb.exe (PID: 2236)
- 7z.exe (PID: 6576)
- adb.exe (PID: 8116)
- adb.exe (PID: 5984)
- adb.exe (PID: 668)
- adb.exe (PID: 1660)
Reads the computer name
- AndroidSideloader.exe (PID: 7672)
- AndroidSideloader.exe (PID: 7776)
- 7z.exe (PID: 8144)
- 7z.exe (PID: 7820)
- adb.exe (PID: 1628)
- rclone.exe (PID: 5868)
- rclone.exe (PID: 7328)
- 7z.exe (PID: 2392)
- rclone.exe (PID: 7500)
- 7z.exe (PID: 616)
- rclone.exe (PID: 7624)
- adb.exe (PID: 7960)
- 7z.exe (PID: 6576)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6028)
Reads the machine GUID from the registry
- AndroidSideloader.exe (PID: 7672)
- AndroidSideloader.exe (PID: 7776)
- rclone.exe (PID: 7328)
- rclone.exe (PID: 7624)
Reads the software policy settings
- AndroidSideloader.exe (PID: 7672)
- AndroidSideloader.exe (PID: 7776)
- rclone.exe (PID: 7624)
- slui.exe (PID: 7244)
- rclone.exe (PID: 7328)
- slui.exe (PID: 7296)
Disables trace logs
- AndroidSideloader.exe (PID: 7672)
- AndroidSideloader.exe (PID: 7776)
The sample compiled with english language support
- AndroidSideloader.exe (PID: 7672)
- AndroidSideloader.exe (PID: 7776)
- 7z.exe (PID: 7820)
Checks proxy server information
- AndroidSideloader.exe (PID: 7672)
- AndroidSideloader.exe (PID: 7776)
- slui.exe (PID: 7296)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (66.6) |
|---|---|---|
| .zip | | | ZIP compressed archive (33.3) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:07:16 13:27:44 |
| ZipCRC: | 0x418e997e |
| ZipCompressedSize: | 138 |
| ZipUncompressedSize: | 190 |
| ZipFileName: | Rookie Offline.cmd |
Total processes
178
Monitored processes
46
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 616 | "7z.exe" x "C:\Users\admin\AppData\Local\Temp\Rar$EXa6028.34057\meta.7z" -y -o"C:\Users\admin\AppData\Local\Temp\Rar$EXa6028.34057\meta" -p"gL59VfgPxoHR" -bsp1 | C:\Users\admin\AppData\Local\Temp\Rar$EXa6028.34057\7z.exe | — | AndroidSideloader.exe | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip Console Exit code: 0 Version: 24.09 Modules
| |||||||||||||||
| 668 | "C:\RSL\platform-tools\adb.exe" shell df | C:\RSL\platform-tools\adb.exe | — | AndroidSideloader.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 1052 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | adb.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1164 | "C:\RSL\platform-tools\adb.exe" kill-server | C:\RSL\platform-tools\adb.exe | — | AndroidSideloader.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1272 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | rclone.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1324 | "C:\RSL\platform-tools\adb.exe" start-server | C:\RSL\platform-tools\adb.exe | — | AndroidSideloader.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1628 | adb -L tcp:5037 fork-server server --reply-fd 576 | C:\RSL\platform-tools\adb.exe | — | adb.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1660 | "C:\RSL\platform-tools\adb.exe" shell pm list packages -3 | C:\RSL\platform-tools\adb.exe | — | AndroidSideloader.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 1760 | "C:\RSL\platform-tools\adb.exe" kill-server | C:\RSL\platform-tools\adb.exe | — | AndroidSideloader.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1764 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | 7z.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
21 212
Read events
21 190
Write events
22
Delete events
0
Modification events
| (PID) Process: | (6028) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6028) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6028) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6028) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\rookie_2.34.1_portable.zip | |||
| (PID) Process: | (6028) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6028) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6028) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6028) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7672) AndroidSideloader.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\AndroidSideloader_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (7672) AndroidSideloader.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\AndroidSideloader_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
Executable files
21
Suspicious files
7
Text files
2 279
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7672 | AndroidSideloader.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6028.33424\dependencies.7z | — | |
MD5:— | SHA256:— | |||
| 7672 | AndroidSideloader.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6028.33424\Sideloader Launcher.exe | executable | |
MD5:A53A5E70248EB3DA58DEFA74B0554704 | SHA256:98BC8CF1C6A59EF70D6431E1E92887984E5B21C8FBC85B4AD23CCC70589C4B1F | |||
| 7672 | AndroidSideloader.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6028.33424\7z.dll | executable | |
MD5:C4AABD70DC28C9516809B775A30FDD3F | SHA256:882063948D675EE41B5AE68DB3E84879350EC81CF88D15B9BABF2FA08E332863 | |||
| 6028 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6028.33424\AddDefenderExceptions.ps1 | text | |
MD5:598164F06F8ABD143A91D20C0562EB93 | SHA256:A8CDB6D8B436DDCA50FCB94F6A6118E6D3B7F01288F15C676D941EBFFDE76C37 | |||
| 6028 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6028.33424\AndroidSideloader.exe | executable | |
MD5:552E9C39473CA27A5DE66AB0C87ACEAA | SHA256:5FBEC60B550076E3436AB83683211F3DB39EEE46BD14139A18A36B79F929F67E | |||
| 7776 | AndroidSideloader.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6028.34057\settings.json | binary | |
MD5:C6EA7FAFC8E6C3AAE88FC4E4631A52ED | SHA256:26762A4C94C68CAC0D856D7DF25902E60ED21073A9EBA6CE5CF4D943EBAD7CCE | |||
| 6028 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6028.34057\AndroidSideloader.exe | executable | |
MD5:552E9C39473CA27A5DE66AB0C87ACEAA | SHA256:5FBEC60B550076E3436AB83683211F3DB39EEE46BD14139A18A36B79F929F67E | |||
| 6028 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6028.33424\Rookie Offline.cmd | text | |
MD5:83B85F3A19C77666117DB1DFBBFD782B | SHA256:5286FC09CBBC098A5DA63096676B180BD7FD28DCD96A79F41F4D92784CC262D1 | |||
| 7672 | AndroidSideloader.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6028.33424\settings.json | binary | |
MD5:DDCF4E6649AADECC2C85892CA28D9A7F | SHA256:447F9C6295AF17DA000A0049B9E99321203E93F0A84E0DF4BCE9DAB8EFFB19F7 | |||
| 7672 | AndroidSideloader.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6028.33424\debuglog.txt | text | |
MD5:11B7FF8130F3E178170A081EFF3B8BB0 | SHA256:5DE0E5F4BFF0D7E3F2229E725A1BA1E20A57F1E9399D619A00656732858837EB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
41
DNS requests
25
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.193:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
8004 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
8004 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7192 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.48.23.193:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6544 | svchost.exe | 20.190.159.71:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2112 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
github.com |
| whitelisted |
raw.githubusercontent.com |
| whitelisted |
downloads.rclone.org |
| unknown |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
7776 | AndroidSideloader.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |
7672 | AndroidSideloader.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |