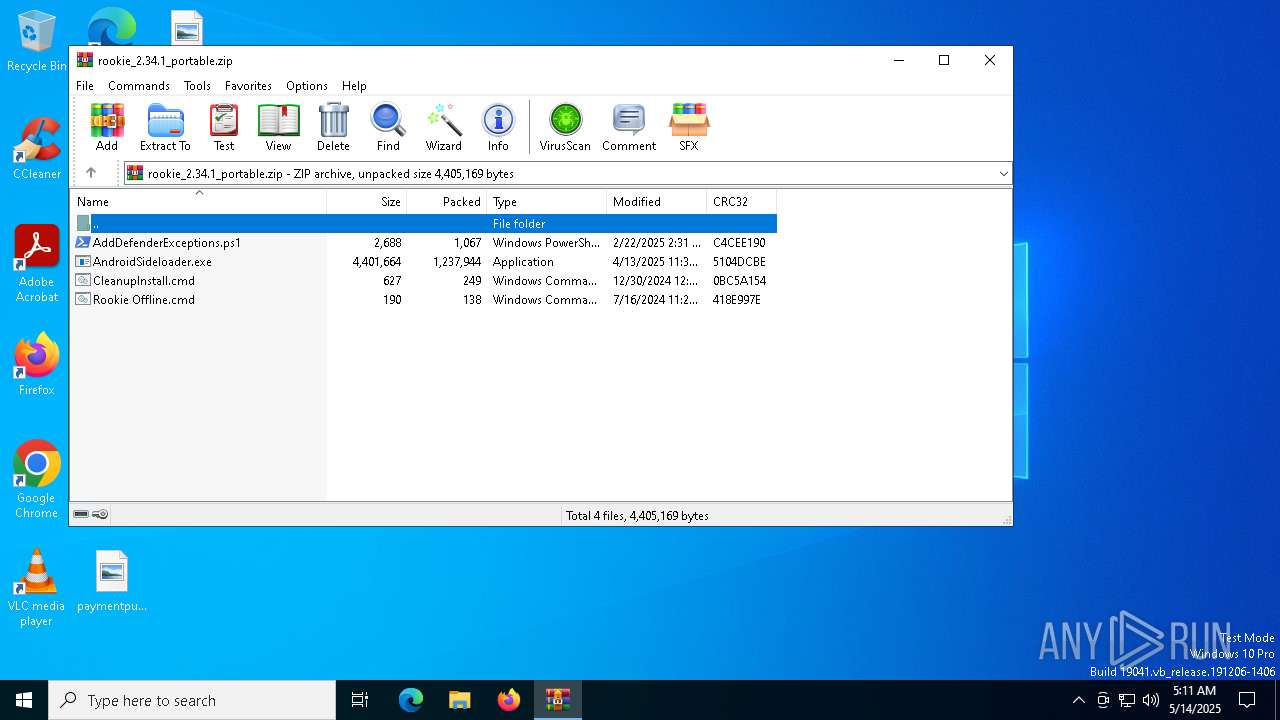
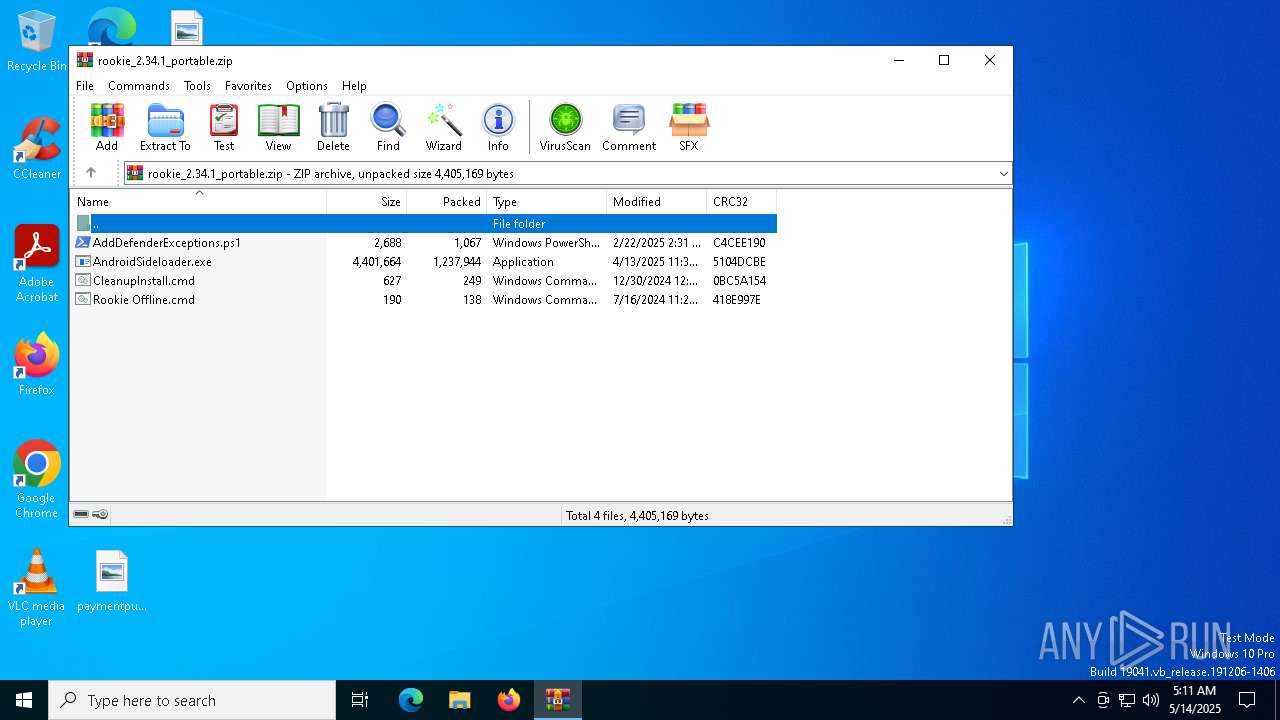
| download: | /downloads/rookie/rookie_2.34.1_portable.zip |
| Full analysis: | https://app.any.run/tasks/24cfdd37-c8df-4da1-b198-9fae82d2d39b |
| Verdict: | Malicious activity |
| Analysis date: | May 14, 2025, 05:11:10 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | F036FCDB20B031D103DDC48A7D4E3FDE |
| SHA1: | 1122163C4DF062887A6943826ED5213242200306 |
| SHA256: | A329B31B2FDA9F72C907B2688F6EE6D64B2E1A9A0D8EFD186B3D64B930550800 |
| SSDEEP: | 49152:9dfIxtxcItUxnyKtzSdEkuexaVDsBVZ4hCsgLUUK/JfCVODmXZw9xBjMnfqd7tLk:7fcTRKsdEtexaVIBVZ4h5gYUK/JfCVOS |
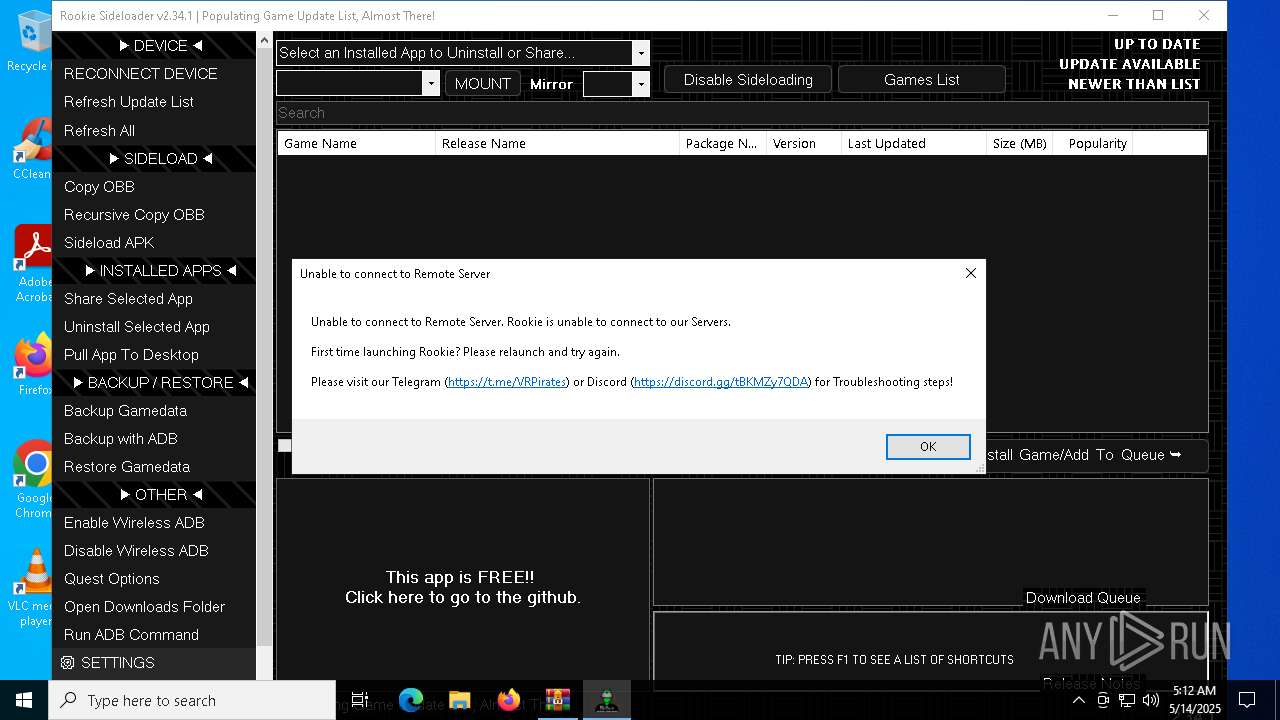
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 4756)
SUSPICIOUS
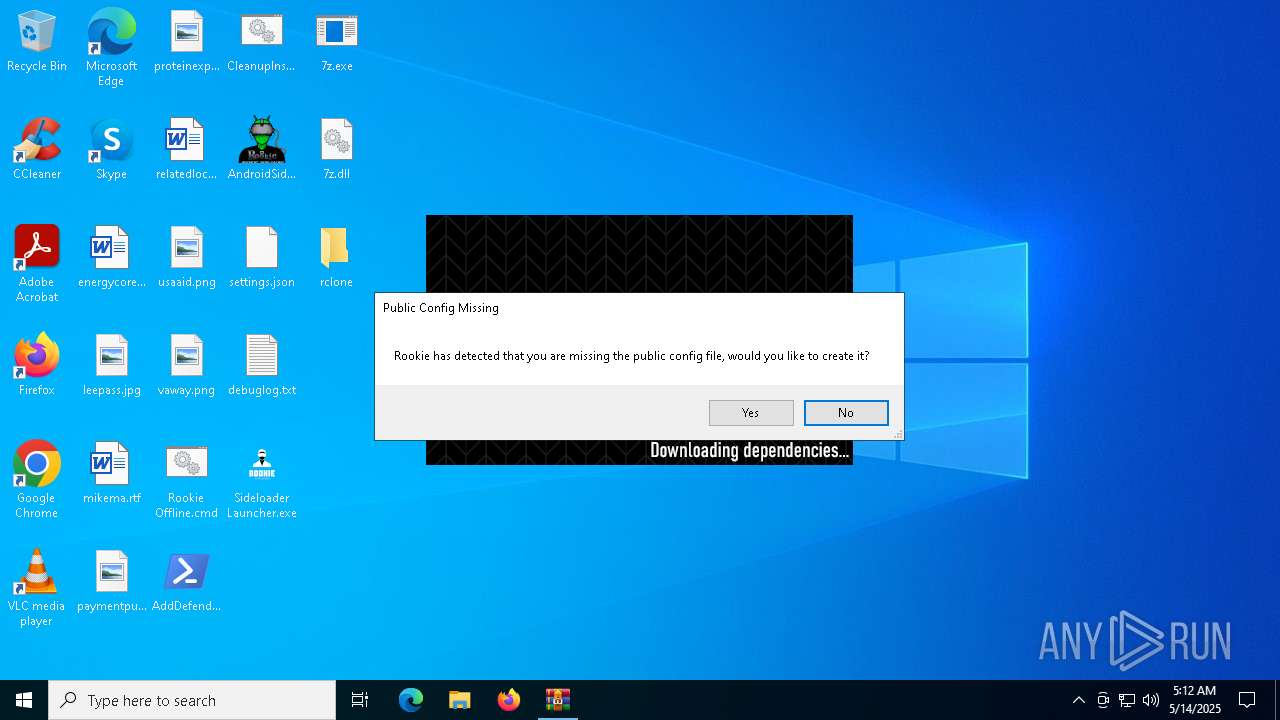
Drops 7-zip archiver for unpacking
- AndroidSideloader.exe (PID: 7908)
Reads security settings of Internet Explorer
- AndroidSideloader.exe (PID: 7908)
Executable content was dropped or overwritten
- AndroidSideloader.exe (PID: 7908)
- 7z.exe (PID: 7980)
RCLONE has been detected
- rclone.exe (PID: 5800)
- rclone.exe (PID: 4040)
Application launched itself
- adb.exe (PID: 5156)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4756)
Reads the computer name
- AndroidSideloader.exe (PID: 7908)
- 7z.exe (PID: 7980)
- 7z.exe (PID: 8076)
- adb.exe (PID: 4400)
- rclone.exe (PID: 4040)
- 7z.exe (PID: 6240)
- rclone.exe (PID: 5800)
Manual execution by a user
- AndroidSideloader.exe (PID: 7908)
Disables trace logs
- AndroidSideloader.exe (PID: 7908)
Checks supported languages
- AndroidSideloader.exe (PID: 7908)
- 7z.exe (PID: 7980)
- 7z.exe (PID: 8076)
- adb.exe (PID: 8140)
- adb.exe (PID: 4400)
- adb.exe (PID: 5156)
- rclone.exe (PID: 4040)
- rclone.exe (PID: 5800)
- 7z.exe (PID: 6240)
- adb.exe (PID: 7404)
- adb.exe (PID: 7360)
- adb.exe (PID: 7304)
- adb.exe (PID: 7408)
- adb.exe (PID: 7148)
Reads the software policy settings
- AndroidSideloader.exe (PID: 7908)
- rclone.exe (PID: 5800)
- slui.exe (PID: 7544)
- slui.exe (PID: 7244)
The sample compiled with english language support
- 7z.exe (PID: 7980)
- AndroidSideloader.exe (PID: 7908)
Reads the machine GUID from the registry
- AndroidSideloader.exe (PID: 7908)
- rclone.exe (PID: 5800)
Checks proxy server information
- AndroidSideloader.exe (PID: 7908)
- slui.exe (PID: 7544)
Create files in a temporary directory
- rclone.exe (PID: 5800)
- adb.exe (PID: 4400)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (66.6) |
|---|---|---|
| .zip | | | ZIP compressed archive (33.3) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:07:16 13:27:44 |
| ZipCRC: | 0x418e997e |
| ZipCompressedSize: | 138 |
| ZipUncompressedSize: | 190 |
| ZipFileName: | Rookie Offline.cmd |
Total processes
159
Monitored processes
30
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1188 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | rclone.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1280 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | adb.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3784 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | 7z.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4040 | "C:\Users\admin\Desktop\rclone\rclone.exe" listremotes --config vrp.download.config --inplace | C:\Users\admin\Desktop\rclone\rclone.exe | AndroidSideloader.exe | ||||||||||||
User: admin Company: https://rclone.org Integrity Level: MEDIUM Description: Rclone Exit code: 0 Version: 1.68.2 Modules
| |||||||||||||||
| 4400 | adb -L tcp:5037 fork-server server --reply-fd 600 | C:\RSL\platform-tools\adb.exe | — | adb.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 4756 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\rookie_2.34.1_portable.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 5156 | "C:\RSL\platform-tools\adb.exe" start-server | C:\RSL\platform-tools\adb.exe | — | AndroidSideloader.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 5324 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | rclone.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5800 | "C:\Users\admin\Desktop\rclone\rclone.exe" sync ":http:/meta.7z" "C:\Users\admin\Desktop" --inplace --http-url https://go.vrpyourself.online/ --tpslimit 1.0 --tpslimit-burst 3 | C:\Users\admin\Desktop\rclone\rclone.exe | AndroidSideloader.exe | ||||||||||||
User: admin Company: https://rclone.org Integrity Level: MEDIUM Description: Rclone Exit code: 1 Version: 1.68.2 Modules
| |||||||||||||||
| 5972 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | adb.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
12 605
Read events
12 567
Write events
25
Delete events
13
Modification events
| (PID) Process: | (4756) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4756) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4756) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4756) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\rookie_2.34.1_portable.zip | |||
| (PID) Process: | (4756) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4756) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4756) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4756) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4756) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (4756) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
Executable files
17
Suspicious files
3
Text files
19
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7908 | AndroidSideloader.exe | C:\Users\admin\Desktop\dependencies.7z | — | |
MD5:— | SHA256:— | |||
| 4756 | WinRAR.exe | C:\Users\admin\Desktop\AddDefenderExceptions.ps1 | text | |
MD5:598164F06F8ABD143A91D20C0562EB93 | SHA256:A8CDB6D8B436DDCA50FCB94F6A6118E6D3B7F01288F15C676D941EBFFDE76C37 | |||
| 7908 | AndroidSideloader.exe | C:\Users\admin\Desktop\7z.exe | executable | |
MD5:B6D5860F368B28CAA9DD14A51666A5CD | SHA256:E2CA3EC168AE9C0B4115CD4FE220145EA9B2DC4B6FC79D765E91F415B34D00DE | |||
| 7980 | 7z.exe | C:\RSL\platform-tools\aapt2.exe | executable | |
MD5:E771DC8631AFABE557001FED8521D48C | SHA256:CBFE5DEDA5F7074CE47B6F33818B456EE8046A076A11AF13E29C837D3C80C564 | |||
| 7980 | 7z.exe | C:\RSL\platform-tools\mke2fs.conf | text | |
MD5:699098CA95F87BA48BB94A3E848549B3 | SHA256:AD58A58DCDD24D85055814CA9CAC67DB89D4E67C434E96774BDCE0D0A007D067 | |||
| 7980 | 7z.exe | C:\RSL\platform-tools\aapt.exe | executable | |
MD5:0DD164F26A0485592B34F302D7631493 | SHA256:DB0BA2050B8F6B37185D2BA458D6E25B565AEFA3F3B96040ADF0A82C3469CE3C | |||
| 7908 | AndroidSideloader.exe | C:\Users\admin\Desktop\debuglog.txt | text | |
MD5:5F390DED1CD6F5F9FF41E8C338DDF66D | SHA256:A8B1CFC64CDCF726DDA1DCAB6CEE081873DD1B259AF60A384CB6636BE00C2B51 | |||
| 7980 | 7z.exe | C:\RSL\platform-tools\etc1tool.exe | executable | |
MD5:7E69E9643C14F5D64BF55407C77E58A1 | SHA256:DCAA07F97F357564847D2375FD15C4E39CADB5DB0FC70C6BC971049B65AC646F | |||
| 7908 | AndroidSideloader.exe | C:\Users\admin\Desktop\settings.json | binary | |
MD5:097AF0E5F90696E339D039F258147488 | SHA256:7E5C22E07D6B41B490196F5B9567DD80088804D86C3FF342759E042BDFFF1859 | |||
| 7980 | 7z.exe | C:\RSL\platform-tools\fastboot.exe | executable | |
MD5:72CC783D50EEDD9646A9CB46B4A1AA88 | SHA256:7277F971C67F5A60142903FD461D7DD8F40D00A0287D2D06D292A0BAE8C27E36 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
28
DNS requests
22
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7768 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7768 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.216.77.20:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.216.77.20:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.71:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
github.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
7908 | AndroidSideloader.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |