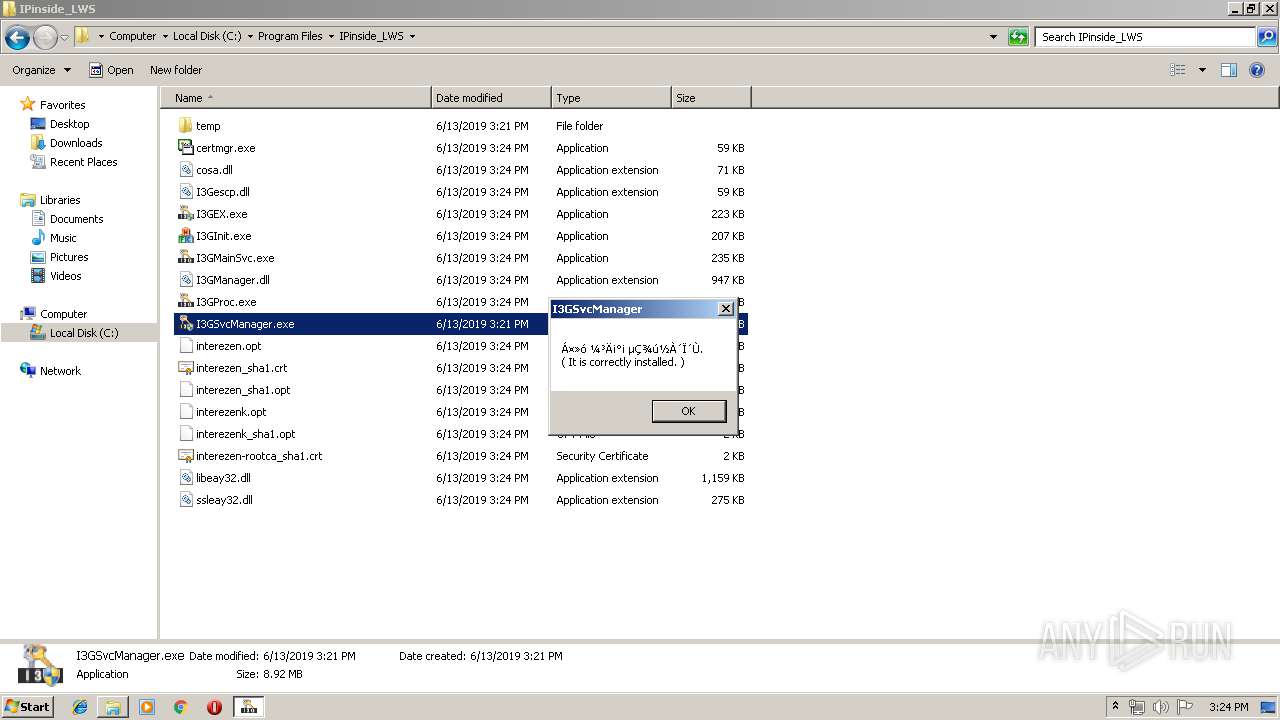
| File name: | I3GSvcManager.exe |
| Full analysis: | https://app.any.run/tasks/f4325b92-3699-40d6-86e7-03e7f5df49f5 |
| Verdict: | Malicious activity |
| Analysis date: | June 13, 2019, 14:20:58 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 2AADCA037C8A01021E1892C07D8206FB |
| SHA1: | 5F4226F02CFE33760A4BDB510DFBBEC69E277808 |
| SHA256: | A30BDFCED314A2C27598568D79CFF3787E703964FC60522368531036CDF2EEFF |
| SSDEEP: | 196608:XtvZfxhyaau9vuhR0zxkqYZ6iG+mwZwoZhJ0E2SQ66:XyaLMc+mOwox0wQ6 |
MALICIOUS
Loads dropped or rewritten executable
- install.exe (PID: 2412)
- I3GProc.exe (PID: 3640)
- certutil.exe (PID: 2496)
- certutil.exe (PID: 980)
- certutil.exe (PID: 2544)
- I3GProc.exe (PID: 1536)
- certutil.exe (PID: 3660)
- I3GProc.exe (PID: 2416)
- certutil.exe (PID: 1528)
- I3GProc.exe (PID: 3276)
- certutil.exe (PID: 2604)
Changes settings of System certificates
- certmgr.exe (PID: 3008)
- certmgr.exe (PID: 2424)
- I3GInit.exe (PID: 3564)
- msiexec.exe (PID: 252)
- certmgr.exe (PID: 3328)
- certmgr.exe (PID: 2896)
- I3GInit.exe (PID: 3168)
- certmgr.exe (PID: 804)
- certmgr.exe (PID: 2632)
- rundll32.exe (PID: 460)
- I3GInit.exe (PID: 3992)
Application was dropped or rewritten from another process
- install.exe (PID: 2412)
- vcredist_x86.exe (PID: 3608)
- I3GMainSvc.exe (PID: 3036)
- I3GMainSvc.exe (PID: 1028)
- I3GProc.exe (PID: 3640)
- I3GInit.exe (PID: 3564)
- certutil.exe (PID: 980)
- I3GMainSvc.exe (PID: 1152)
- certmgr.exe (PID: 2424)
- certutil.exe (PID: 2496)
- certmgr.exe (PID: 3008)
- I3GMainSvc.exe (PID: 3408)
- I3GMainSvc.exe (PID: 2860)
- certmgr.exe (PID: 3328)
- certutil.exe (PID: 3660)
- certutil.exe (PID: 2544)
- I3GMainSvc.exe (PID: 2552)
- certmgr.exe (PID: 2896)
- I3GEX.exe (PID: 1900)
- I3GInit.exe (PID: 3168)
- certmgr.exe (PID: 3772)
- I3GMainSvc.exe (PID: 3284)
- I3GEX.exe (PID: 4052)
- I3GProc.exe (PID: 1536)
- I3GMainSvc.exe (PID: 592)
- I3GEX.exe (PID: 2612)
- I3GEX.exe (PID: 3484)
- I3GMainSvc.exe (PID: 2748)
- I3GProc.exe (PID: 2416)
- I3GMainSvc.exe (PID: 2556)
- I3GMainSvc.exe (PID: 2648)
- I3GInit.exe (PID: 2524)
- certmgr.exe (PID: 804)
- certmgr.exe (PID: 2632)
- certutil.exe (PID: 1528)
- certutil.exe (PID: 2604)
- I3GProc.exe (PID: 3276)
- I3GInit.exe (PID: 3992)
- I3GMainSvc.exe (PID: 3888)
- I3GMainSvc.exe (PID: 2128)
- I3GMainSvc.exe (PID: 3944)
Changes the autorun value in the registry
- I3GSvcManager.exe (PID: 808)
- I3GSvcManager.exe (PID: 2732)
- I3GSvcManager.exe (PID: 2312)
SUSPICIOUS
Creates a software uninstall entry
- I3GSvcManager.exe (PID: 808)
- I3GSvcManager.exe (PID: 2732)
- I3GSvcManager.exe (PID: 2312)
Creates files in the Windows directory
- I3GSvcManager.exe (PID: 808)
- msiexec.exe (PID: 252)
- I3GSvcManager.exe (PID: 2732)
- I3GSvcManager.exe (PID: 2312)
Executable content was dropped or overwritten
- msiexec.exe (PID: 252)
- I3GSvcManager.exe (PID: 808)
- vcredist_x86.exe (PID: 3608)
- I3GSvcManager.exe (PID: 2732)
- I3GSvcManager.exe (PID: 2312)
Creates files in the user directory
- certutil.exe (PID: 2496)
- I3GSvcManager.exe (PID: 808)
Removes files from Windows directory
- msiexec.exe (PID: 252)
- I3GSvcManager.exe (PID: 2732)
- I3GSvcManager.exe (PID: 2312)
Executed as Windows Service
- I3GMainSvc.exe (PID: 1028)
- I3GMainSvc.exe (PID: 592)
- I3GMainSvc.exe (PID: 2128)
Uses NETSH.EXE for network configuration
- I3GSvcManager.exe (PID: 808)
- I3GSvcManager.exe (PID: 2732)
- I3GSvcManager.exe (PID: 2312)
Adds / modifies Windows certificates
- msiexec.exe (PID: 252)
Creates files in the program directory
- I3GSvcManager.exe (PID: 2732)
- I3GSvcManager.exe (PID: 2312)
- I3GSvcManager.exe (PID: 808)
INFO
Creates a software uninstall entry
- msiexec.exe (PID: 252)
Manual execution by user
- explorer.exe (PID: 1360)
- I3GSvcManager.exe (PID: 2732)
- I3GSvcManager.exe (PID: 1184)
- explorer.exe (PID: 3964)
- certmgr.exe (PID: 3772)
- I3GEX.exe (PID: 4052)
- I3GEX.exe (PID: 1900)
- I3GEX.exe (PID: 2612)
- I3GEX.exe (PID: 3484)
- I3GProc.exe (PID: 2416)
- I3GSvcManager.exe (PID: 2844)
- I3GSvcManager.exe (PID: 2312)
- I3GMainSvc.exe (PID: 2748)
- rundll32.exe (PID: 460)
- I3GInit.exe (PID: 2524)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (54.3) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (34.8) |
| .exe | | | Win32 Executable (generic) (5.6) |
| .exe | | | Generic Win/DOS Executable (2.5) |
| .exe | | | DOS Executable Generic (2.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2017:06:17 04:21:47+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 9 |
| CodeSize: | 1228288 |
| InitializedDataSize: | 8123392 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x105cdb |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.0.0.5 |
| ProductVersionNumber: | 3.0.0.5 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Windows, Korea (Shift - KSC 5601) |
| Comments: | I3GManager LWS Module Installer |
| CompanyName: | Interezen. Co., Ltd. |
| FileDescription: | I3GManager LWS Module Installer |
| FileVersion: | 3.0.0.5 |
| InternalName: | I3GManager |
| LegalCopyright: | Interezen. Copyright ⓒ 2009 ~ |
| OriginalFileName: | I3GSvcManager.exe |
| ProductName: | I3GManager |
| ProductVersion: | 3.0.0.5 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 17-Jun-2017 02:21:47 |
| Detected languages: |
|
| Debug artifacts: |
|
| Comments: | I3GManager LWS Module Installer |
| CompanyName: | Interezen. Co., Ltd. |
| FileDescription: | I3GManager LWS Module Installer |
| FileVersion: | 3.0.0.5 |
| InternalName: | I3GManager |
| LegalCopyright: | Interezen. Copyright ⓒ 2009 ~ |
| OriginalFilename: | I3GSvcManager.exe |
| ProductName: | I3GManager |
| ProductVersion: | 3.0.0.5 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000100 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 17-Jun-2017 02:21:47 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x0012BD22 | 0x0012BE00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.54962 |
.rdata | 0x0012D000 | 0x000427CA | 0x00042800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.196 |
.data | 0x00170000 | 0x0000D280 | 0x00005800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.70185 |
.rsrc | 0x0017E000 | 0x0074F984 | 0x0074FA00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 7.90398 |
.reloc | 0x008CE000 | 0x0002780C | 0x00027A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 4.98912 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.19856 | 1016 | Latin 1 / Western European | English - United States | RT_MANIFEST |
2 | 3.02695 | 308 | Latin 1 / Western European | Korean - Korea | RT_CURSOR |
3 | 2.74274 | 180 | Latin 1 / Western European | Korean - Korea | RT_CURSOR |
4 | 2.34038 | 308 | Latin 1 / Western European | Korean - Korea | RT_CURSOR |
5 | 2.34004 | 308 | Latin 1 / Western European | Korean - Korea | RT_CURSOR |
6 | 2.51649 | 308 | Latin 1 / Western European | Korean - Korea | RT_CURSOR |
7 | 2.39851 | 78 | Latin 1 / Western European | Korean - Korea | RT_STRING |
8 | 2.34864 | 308 | Latin 1 / Western European | Korean - Korea | RT_CURSOR |
9 | 2.34505 | 308 | Latin 1 / Western European | Korean - Korea | RT_CURSOR |
10 | 2.34864 | 308 | Latin 1 / Western European | Korean - Korea | RT_CURSOR |
Imports
ADVAPI32.dll |
COMCTL32.dll |
COMDLG32.dll |
GDI32.dll |
IMM32.dll |
KERNEL32.dll |
MSIMG32.dll |
OLEACC.dll (delay-loaded) |
OLEAUT32.dll |
SHELL32.dll |
Total processes
129
Monitored processes
54
Malicious processes
22
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 252 | C:\Windows\system32\msiexec.exe /V | C:\Windows\system32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 460 | "C:\Windows\system32\rundll32.exe" cryptext.dll,CryptExtOpenCER C:\Program Files\IPinside_LWS\interezen-rootca_sha1.crt | C:\Windows\system32\rundll32.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 592 | "C:\Program Files\IPinside_LWS\I3GMainSvc.exe" | C:\Program Files\IPinside_LWS\I3GMainSvc.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Interezen. Co., Ltd. Integrity Level: SYSTEM Description: Interezen Service Program Exit code: 0 Version: 3.0.0.1 Modules
| |||||||||||||||
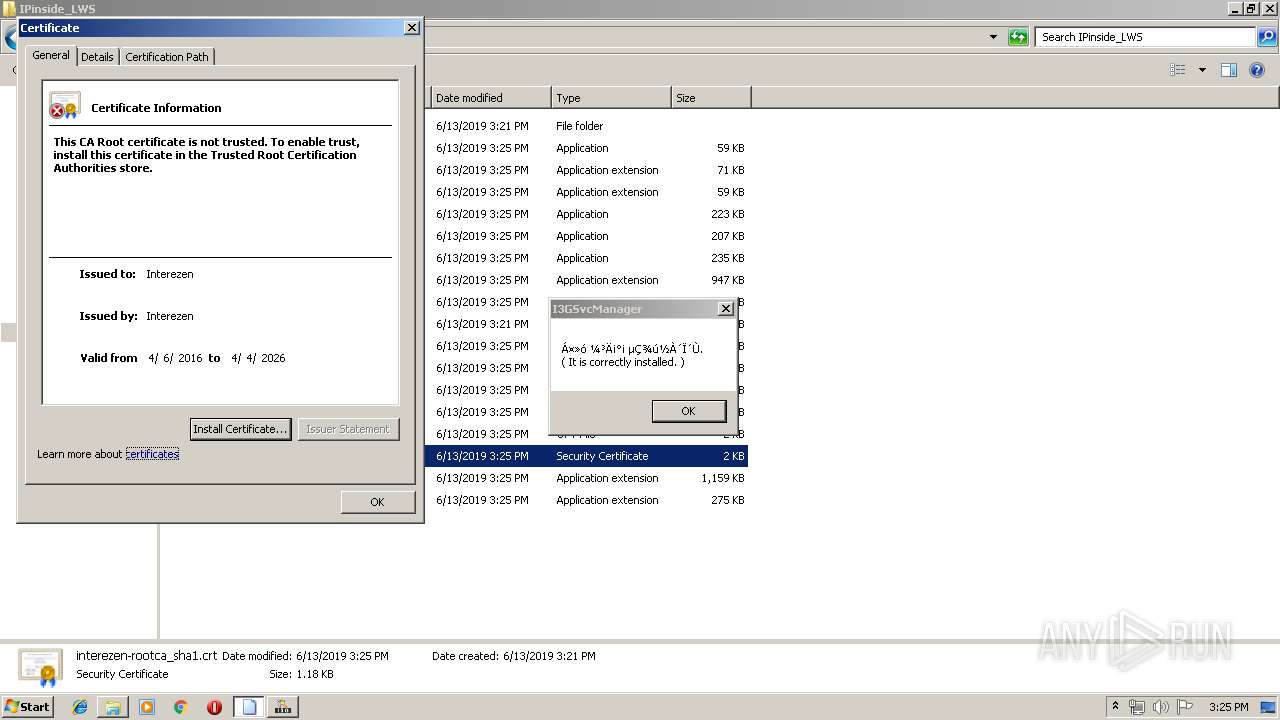
| 804 | "C:\Program Files\IPinside_LWS\certmgr.exe" /add /c interezen-rootca.crt /s /r localMachine root | C:\Program Files\IPinside_LWS\certmgr.exe | — | I3GSvcManager.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: ECM Certificate Manager Exit code: 0 Version: 5.131.1863.1 Modules
| |||||||||||||||
| 808 | "C:\Users\admin\AppData\Local\Temp\I3GSvcManager.exe" | C:\Users\admin\AppData\Local\Temp\I3GSvcManager.exe | explorer.exe | ||||||||||||
User: admin Company: Interezen. Co., Ltd. Integrity Level: HIGH Description: I3GManager LWS Module Installer Exit code: 0 Version: 3.0.0.5 Modules
| |||||||||||||||
| 980 | "C:\Program Files\IPinside_LWS\certfr\certutil.exe" -A -n "Interezen CA" -t "C,C,C" -i "C:\Program Files\IPinside_LWS\interezen.crt" -d "C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default" | C:\Program Files\IPinside_LWS\certfr\certutil.exe | — | I3GSvcManager.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1028 | "C:\Program Files\IPinside_LWS\I3GMainSvc.exe" | C:\Program Files\IPinside_LWS\I3GMainSvc.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Interezen. Co., Ltd. Integrity Level: SYSTEM Description: Interezen Service Program Exit code: 0 Version: 3.0.0.1 Modules
| |||||||||||||||
| 1152 | "C:\Program Files\IPinside_LWS\I3GMainSvc.exe" -install | C:\Program Files\IPinside_LWS\I3GMainSvc.exe | — | I3GSvcManager.exe | |||||||||||
User: admin Company: Interezen. Co., Ltd. Integrity Level: HIGH Description: Interezen Service Program Exit code: 0 Version: 3.0.0.1 Modules
| |||||||||||||||
| 1184 | "C:\Program Files\IPinside_LWS\I3GSvcManager.exe" | C:\Program Files\IPinside_LWS\I3GSvcManager.exe | — | explorer.exe | |||||||||||
User: admin Company: Interezen. Co., Ltd. Integrity Level: MEDIUM Description: I3GManager LWS Module Installer Exit code: 3221226540 Version: 3.0.0.5 Modules
| |||||||||||||||
| 1360 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 449
Read events
817
Write events
610
Delete events
22
Modification events
| (PID) Process: | (808) I3GSvcManager.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Compatibility Assistant\Persisted |
| Operation: | write | Name: | C:\Users\admin\AppData\Local\Temp\I3GSvcManager.exe |
Value: 1 | |||
| (PID) Process: | (808) I3GSvcManager.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\IPinside LWS Agent |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Program Files\IPinside_LWS\I3GSvcManager.exe | |||
| (PID) Process: | (808) I3GSvcManager.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\IPinside LWS Agent |
| Operation: | write | Name: | DisplayName |
Value: IPinside LWS Agent | |||
| (PID) Process: | (808) I3GSvcManager.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\IPinside LWS Agent |
| Operation: | write | Name: | DisplayVersion |
Value: 3.0.0.5 | |||
| (PID) Process: | (808) I3GSvcManager.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\IPinside LWS Agent |
| Operation: | write | Name: | Publisher |
Value: interezen | |||
| (PID) Process: | (808) I3GSvcManager.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\IPinside LWS Agent |
| Operation: | write | Name: | UninstallPath |
Value: C:\Program Files\IPinside_LWS\I3GSvcManager.exe | |||
| (PID) Process: | (808) I3GSvcManager.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\IPinside LWS Agent |
| Operation: | write | Name: | UninstallString |
Value: C:\Program Files\IPinside_LWS\I3GSvcManager.exe /uninstall | |||
| (PID) Process: | (808) I3GSvcManager.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (808) I3GSvcManager.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3684) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
89
Suspicious files
20
Text files
326
Unknown types
20
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 808 | I3GSvcManager.exe | C:\Program Files\IPinside_LWS\I3GManager.dll | executable | |
MD5:— | SHA256:— | |||
| 808 | I3GSvcManager.exe | C:\Program Files\IPinside_LWS\I3GProc.exe | executable | |
MD5:— | SHA256:— | |||
| 808 | I3GSvcManager.exe | C:\Program Files\IPinside_LWS\I3GMainSvc.exe | executable | |
MD5:— | SHA256:— | |||
| 808 | I3GSvcManager.exe | C:\Program Files\IPinside_LWS\interezen_sha1.crt | text | |
MD5:B01FF24277E42E70975C6A5BE073564C | SHA256:AF1BC2C6D2D7783810682456A4EF9587947CF35DB2D787A48CA47E638F0B58C9 | |||
| 808 | I3GSvcManager.exe | C:\Program Files\IPinside_LWS\I3GInit.exe | executable | |
MD5:— | SHA256:— | |||
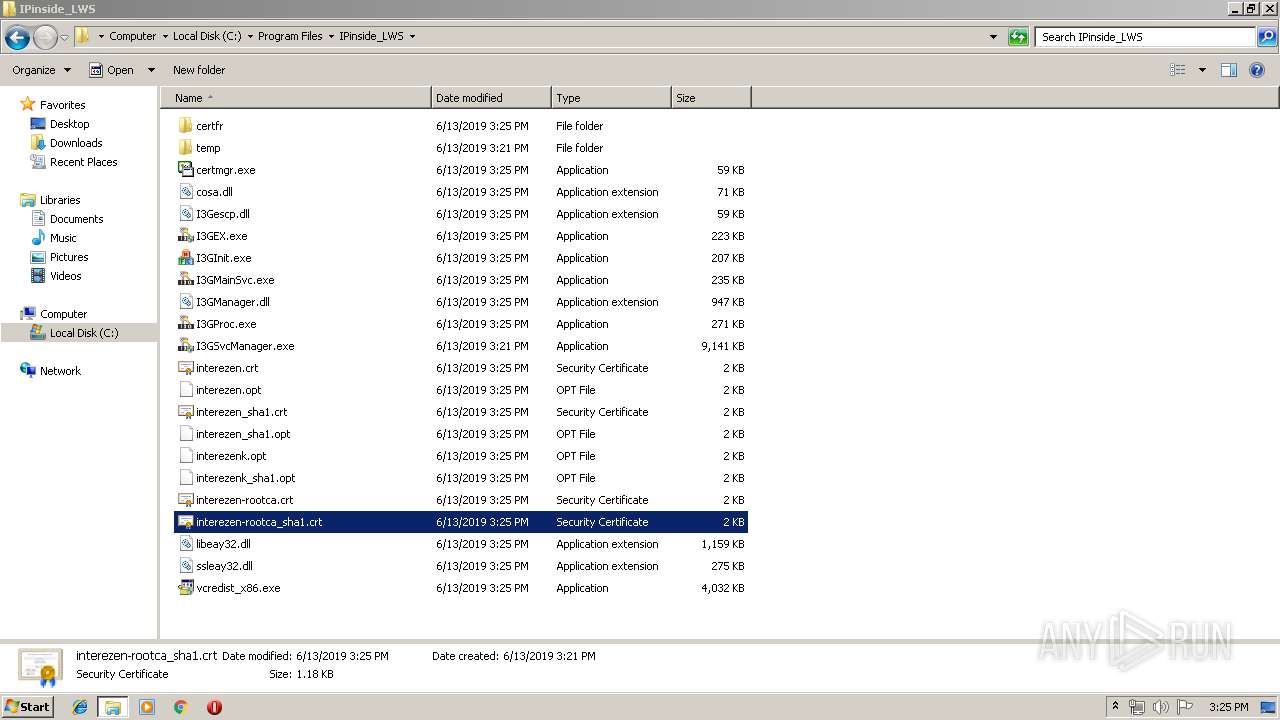
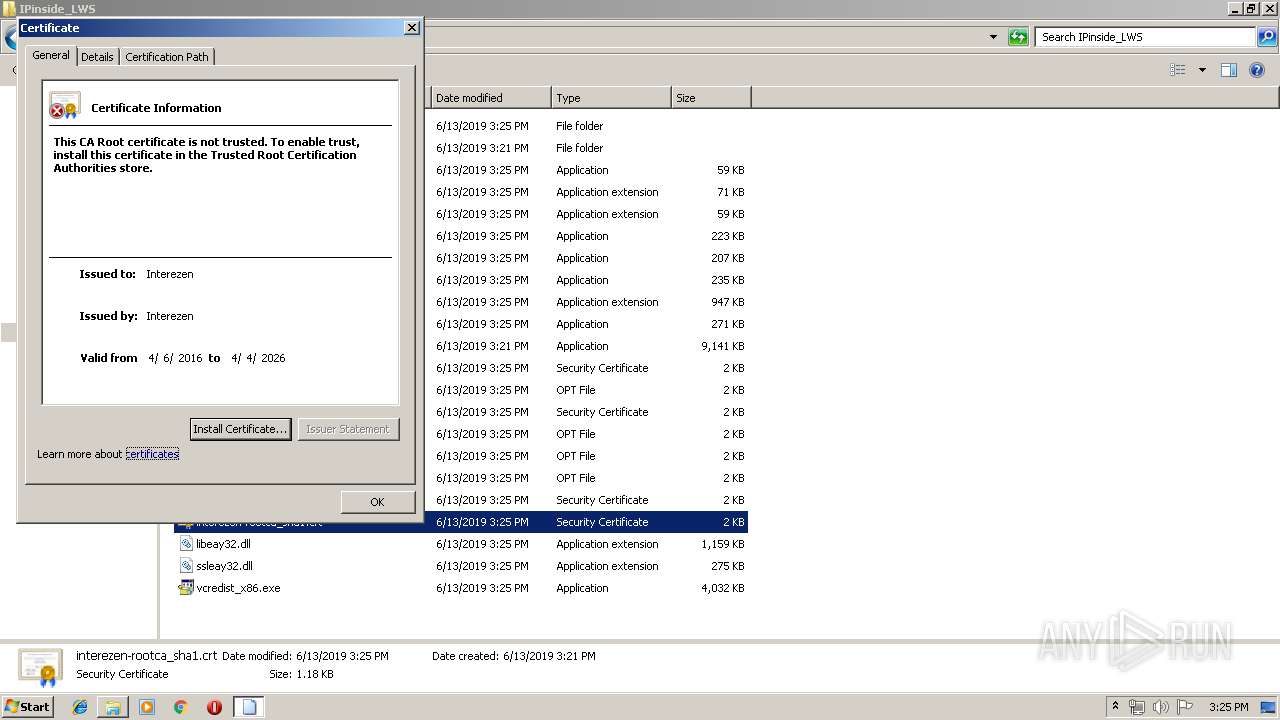
| 808 | I3GSvcManager.exe | C:\Program Files\IPinside_LWS\interezen-rootca.crt | text | |
MD5:AFEFC9AB3F8AA8A34852F492204EFBA3 | SHA256:F0788C52B6F612F41AF4D546907B860AB0262DBAFF897AF34240F5DAA9B9D8CD | |||
| 808 | I3GSvcManager.exe | C:\Program Files\IPinside_LWS\interezenk.opt | text | |
MD5:69E8EBE6AEE27E0D901142A94A64D186 | SHA256:A1616E97F94700D437E93F9AC96D4DEBFFC4869BB955FC46F7208D402CF3248B | |||
| 808 | I3GSvcManager.exe | C:\Program Files\IPinside_LWS\I3Gescp.dll | executable | |
MD5:— | SHA256:— | |||
| 808 | I3GSvcManager.exe | C:\Program Files\IPinside_LWS\interezenk_sha1.opt | text | |
MD5:55B9E53C17C35F2C2E36F049696F7D70 | SHA256:FED161EF27CFAF595E558AF52C8F2DD56E04533DA9C8F37C127DE7138EA76EB3 | |||
| 808 | I3GSvcManager.exe | C:\Program Files\IPinside_LWS\ssleay32.dll | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
1
DNS requests
1
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
460 | rundll32.exe | GET | 200 | 2.16.186.56:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | unknown | compressed | 56.2 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
460 | rundll32.exe | 2.16.186.56:80 | www.download.windowsupdate.com | Akamai International B.V. | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.download.windowsupdate.com |
| whitelisted |