| download: | /win/loki.ps1 |
| Full analysis: | https://app.any.run/tasks/14c251e5-b4f0-4cf1-9f8e-3af146b9f0ec |
| Verdict: | Malicious activity |
| Analysis date: | August 26, 2024, 08:41:42 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | Unicode text, UTF-8 text, with very long lines (1486) |
| MD5: | 1A1E81E87830100E082A15996E5E7BD3 |
| SHA1: | EA554117A99631E230805AED1F6F25DD3B2650C0 |
| SHA256: | A307CBFECD3FE71E51E460FB4ED20401BC3F94C6ACCA51B46204EE496AC60DD5 |
| SSDEEP: | 96:0O2ZtwjUuiunLn0z52jDQxDTm63h3MdYGAJ3C9vK21467vDkS:ouUB4Ql9m6R3MdYFIdK2v7vDkS |
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 240)
- powershell.exe (PID: 6612)
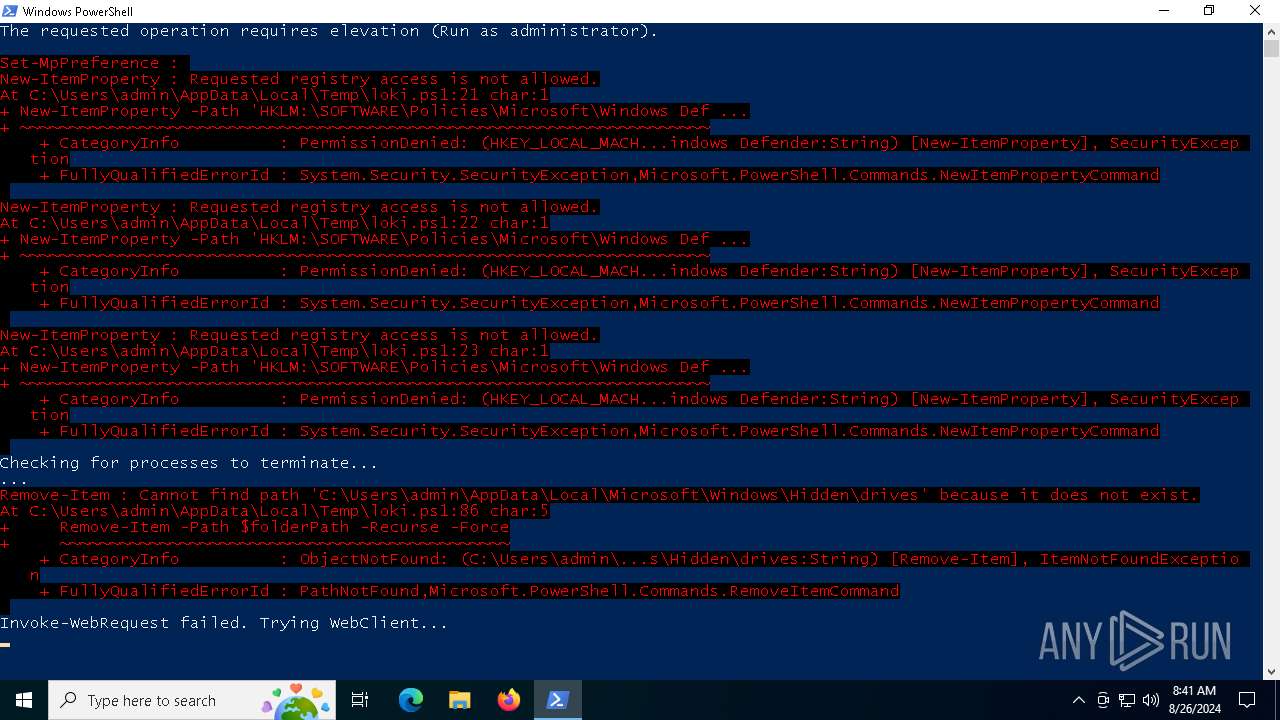
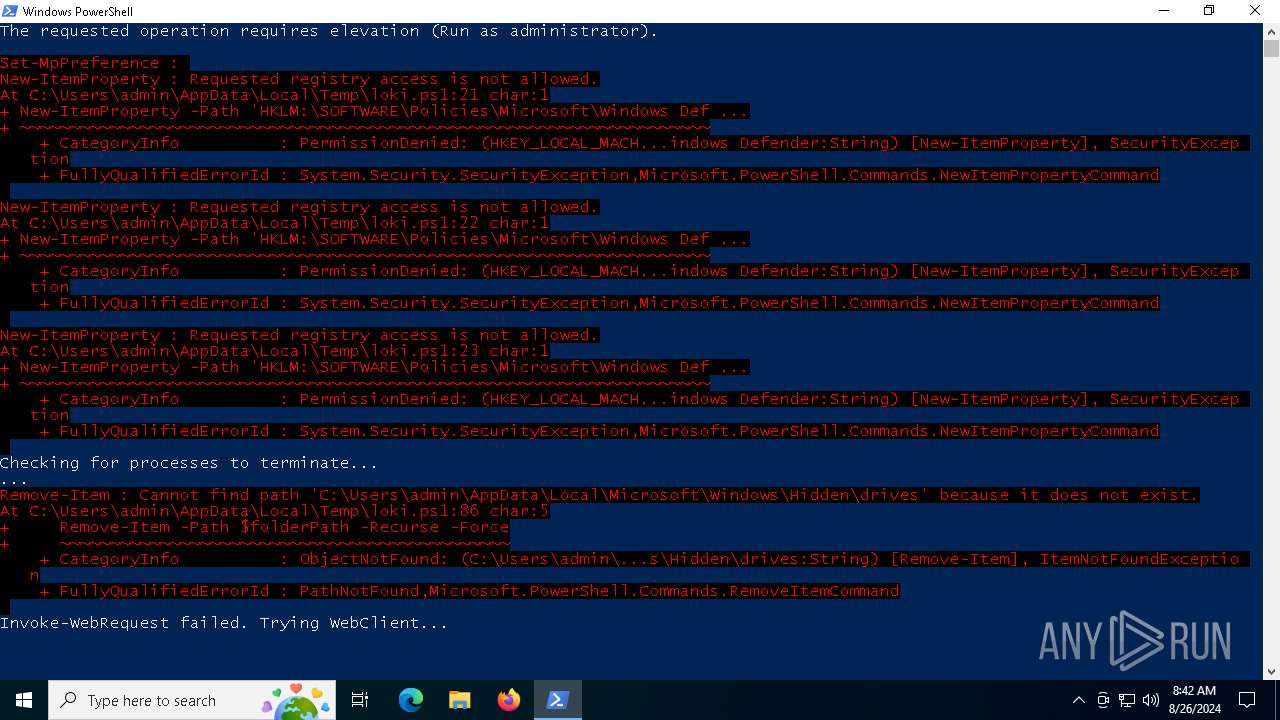
Modifies registry (POWERSHELL)
- powershell.exe (PID: 240)
PHISHING has been detected (SURICATA)
- powershell.exe (PID: 240)
XMRig has been detected
- csrsss.exe (PID: 6004)
Changes powershell execution policy (Bypass)
- powershell.exe (PID: 240)
SUSPICIOUS
Uses NETSH.EXE to change the status of the firewall
- powershell.exe (PID: 240)
Drops the executable file immediately after the start
- powershell.exe (PID: 240)
Executable content was dropped or overwritten
- powershell.exe (PID: 240)
The process executes Powershell scripts
- powershell.exe (PID: 240)
Drops a system driver (possible attempt to evade defenses)
- powershell.exe (PID: 240)
Connects to unusual port
- csrsss.exe (PID: 6004)
Starts POWERSHELL.EXE for commands execution
- powershell.exe (PID: 240)
Application launched itself
- powershell.exe (PID: 240)
INFO
Disables trace logs
- powershell.exe (PID: 240)
Checks proxy server information
- powershell.exe (PID: 240)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 240)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 240)
Checks supported languages
- csrsss.exe (PID: 6004)
The executable file from the user directory is run by the Powershell process
- csrsss.exe (PID: 6004)
Reads the computer name
- csrsss.exe (PID: 6004)
Reads the machine GUID from the registry
- csrsss.exe (PID: 6004)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
132
Monitored processes
6
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 240 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ep bypass C:\Users\admin\AppData\Local\Temp\loki.ps1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1184 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2256 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4440 | "C:\WINDOWS\system32\netsh.exe" advfirewall set allprofiles state off | C:\Windows\System32\netsh.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6004 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Hidden\drives\csrsss.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Hidden\drives\csrsss.exe | powershell.exe | ||||||||||||
User: admin Company: www.xmrig.com Integrity Level: MEDIUM Description: XMRig miner Version: 6.20.0 Modules
| |||||||||||||||
| 6612 | "C:\WINDOWS\System32\WindowsPowerShell\v1.0\powershell.exe" -ExecutionPolicy Bypass -File "C:\Users\admin\AppData\Local\Microsoft\Windows\Hidden\drives\balder.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
15 776
Read events
15 762
Write events
14
Delete events
0
Modification events
| (PID) Process: | (240) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (240) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (240) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (240) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (240) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (240) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (240) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (240) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (240) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (240) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
2
Suspicious files
6
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 240 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\6RPIGP1OTW740NVFG0R5.temp | binary | |
MD5:99A6703CAB8929C4A3271D387EF07E6E | SHA256:5DA32800AA4D358F202A788802064738032ED6B56CFB4D88932896B34B8323F4 | |||
| 240 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_gk2v0f0z.eq5.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 240 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:99A6703CAB8929C4A3271D387EF07E6E | SHA256:5DA32800AA4D358F202A788802064738032ED6B56CFB4D88932896B34B8323F4 | |||
| 240 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Hidden\drives\WinRing0x64.sys | executable | |
MD5:0C0195C48B6B8582FA6F6373032118DA | SHA256:11BD2C9F9E2397C9A16E0990E4ED2CF0679498FE0FD418A3DFDAC60B5C160EE5 | |||
| 240 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RF129fd2.TMP | binary | |
MD5:D040F64E9E7A2BB91ABCA5613424598E | SHA256:D04E0A6940609BD6F3B561B0F6027F5CA4E8C5CF0FB0D0874B380A0374A8D670 | |||
| 6612 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_f2xsyvuu.gso.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 240 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_o2r14fwc.12p.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 240 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:066BF588F08B2F8855751FB9E86F164B | SHA256:987865990838881CA7538BA48FEED1D2BAA34F2C12FE8006D4F179E9F6B8937F | |||
| 6612 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ny21ns0t.nd3.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 240 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Hidden\drives\csrsss.exe | executable | |
MD5:4813FA6D610E180B097EAE0CE636D2AA | SHA256:9EF2E8714E85DCD116B709894B43BABB4A0872225AE7363152013B7FD1BC95BC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
23
DNS requests
14
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1744 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2588 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2588 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6232 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6580 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
240 | powershell.exe | 104.16.231.132:443 | pens-finland-johns-adds.trycloudflare.com | CLOUDFLARENET | — | unknown |
6232 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6004 | csrsss.exe | 107.175.77.206:3399 | — | AS-COLOCROSSING | US | unknown |
3260 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1744 | svchost.exe | 40.126.32.136:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
pens-finland-johns-adds.trycloudflare.com |
| unknown |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Potentially Bad Traffic | ET POLICY Observed DNS Query to Commonly Abused Cloudflare Domain (trycloudflare .com) |
240 | powershell.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Cloudflare Domain Abuse for Phishing or OpenDir Purposes (RGDA) |
240 | powershell.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Cloudflare Domain Abuse for Phishing or OpenDir Purposes (RGDA) |
240 | powershell.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Cloudflare Domain Abuse for Phishing or OpenDir Purposes (RGDA) |