analyze malware
- Huge database of samples and IOCs
- Custom VM setup
- Unlimited submissions
- Interactive approach
| File name: | a.doc |
| Full analysis: | https://app.any.run/tasks/aaae3ca8-a6eb-4ebc-878e-44e6b3cbf098 |
| Verdict: | Malicious activity |
| Analysis date: | June 19, 2019, 02:22:55 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/rtf |
| File info: | Rich Text Format data, version 1, unknown character set |
| MD5: | A7AEAD565341C4A3A3F8867A3CA3C9AB |
| SHA1: | 61EDA60023DA167657C1B89251E4C11CC40DF87A |
| SHA256: | A2D41FFA099E587EB692A7E90B37B978A4A49E4F2A00BA383027F1DBC10328AC |
| SSDEEP: | 768:qaKf8YDEP6d3MzuuUdjTCMJhIS4NX8l0l/cHnQeEHpljeDXrdBj1ANlY7S4cwHNX:qfCqNdjOi4UHHQxJlwrdboY7Scttt |
MALICIOUS
Starts CMD.EXE for commands execution
- EXCEL.EXE (PID: 4032)
Unusual execution from Microsoft Office
- EXCEL.EXE (PID: 4032)
Runs PING.EXE for delay simulation
- cmd.exe (PID: 292)
- cmd.exe (PID: 2616)
Loads dropped or rewritten executable
- cmd.exe (PID: 292)
- cmd.exe (PID: 2616)
- WScript.exe (PID: 3532)
- svchost.exe (PID: 848)
- SearchProtocolHost.exe (PID: 2920)
- amsi.dll (PID: 3224)
- wscript.exe (PID: 2036)
Application was dropped or rewritten from another process
- WScript.exe (PID: 3408)
- WScript.exe (PID: 3532)
- amsi.dll (PID: 3224)
- wscript.exe (PID: 2036)
- amsi.dll (PID: 1472)
Writes to a start menu file
- amsi.dll (PID: 3224)
- amsi.dll (PID: 1472)
Changes settings of System certificates
- amsi.dll (PID: 3224)
- amsi.dll (PID: 1472)
Changes the autorun value in the registry
- amsi.dll (PID: 3224)
- amsi.dll (PID: 1472)
SUSPICIOUS
Executed via COM
- EXCEL.EXE (PID: 4032)
Executes scripts
- cmd.exe (PID: 2616)
- cmd.exe (PID: 292)
- amsi.dll (PID: 3224)
Starts itself from another location
- WScript.exe (PID: 3532)
- amsi.dll (PID: 3224)
Executable content was dropped or overwritten
- WScript.exe (PID: 3532)
Starts application with an unusual extension
- WScript.exe (PID: 3532)
- wscript.exe (PID: 2036)
Creates files in the user directory
- amsi.dll (PID: 3224)
Adds / modifies Windows certificates
- amsi.dll (PID: 3224)
- amsi.dll (PID: 1472)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 284)
- EXCEL.EXE (PID: 4032)
Creates files in the user directory
- WINWORD.EXE (PID: 284)
- EXCEL.EXE (PID: 4032)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rtf | | | Rich Text Format (100) |
|---|
EXIF
RTF
| Author: | Karla |
|---|---|
| LastModifiedBy: | Karla |
| CreateDate: | 2019:06:16 21:51:00 |
| ModifyDate: | 2019:06:16 21:53:00 |
| RevisionNumber: | 1 |
| TotalEditTime: | 2 minutes |
| Pages: | 1 |
| Words: | 6 |
| Characters: | 34 |
| CharactersWithSpaces: | 39 |
| InternalVersionNumber: | 57433 |
Total processes
45
Monitored processes
13
Malicious processes
8
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
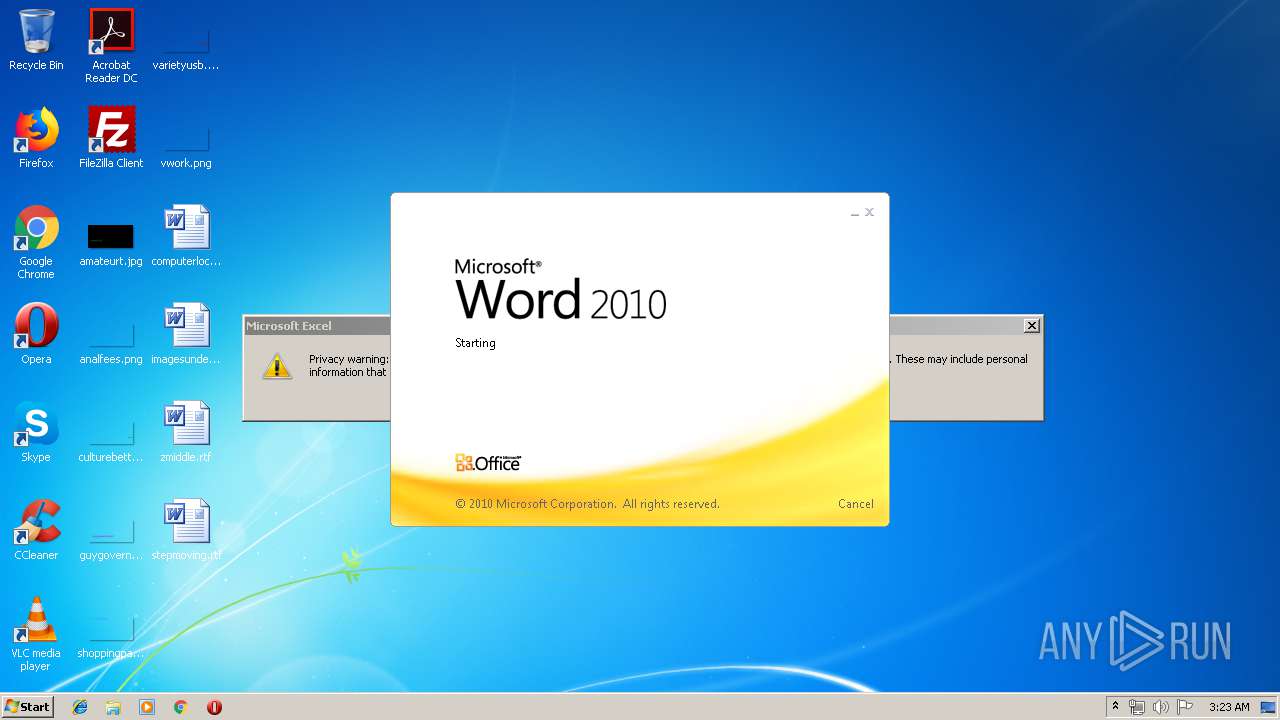
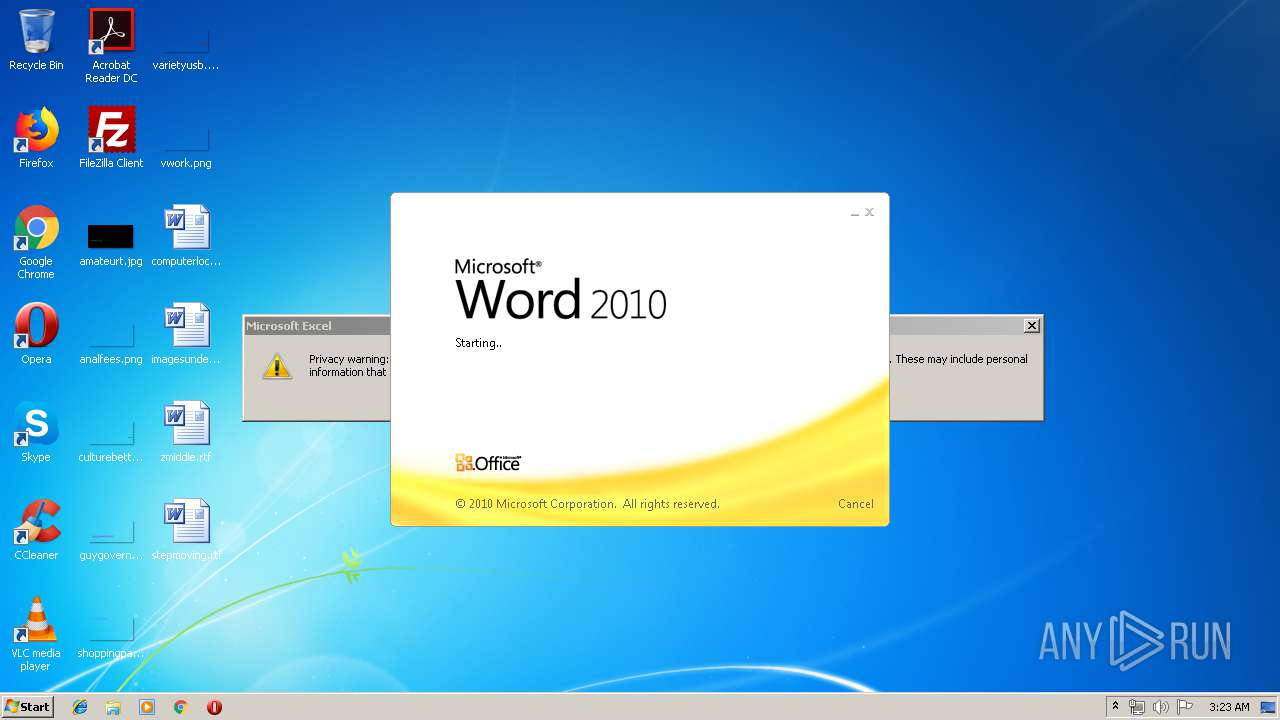
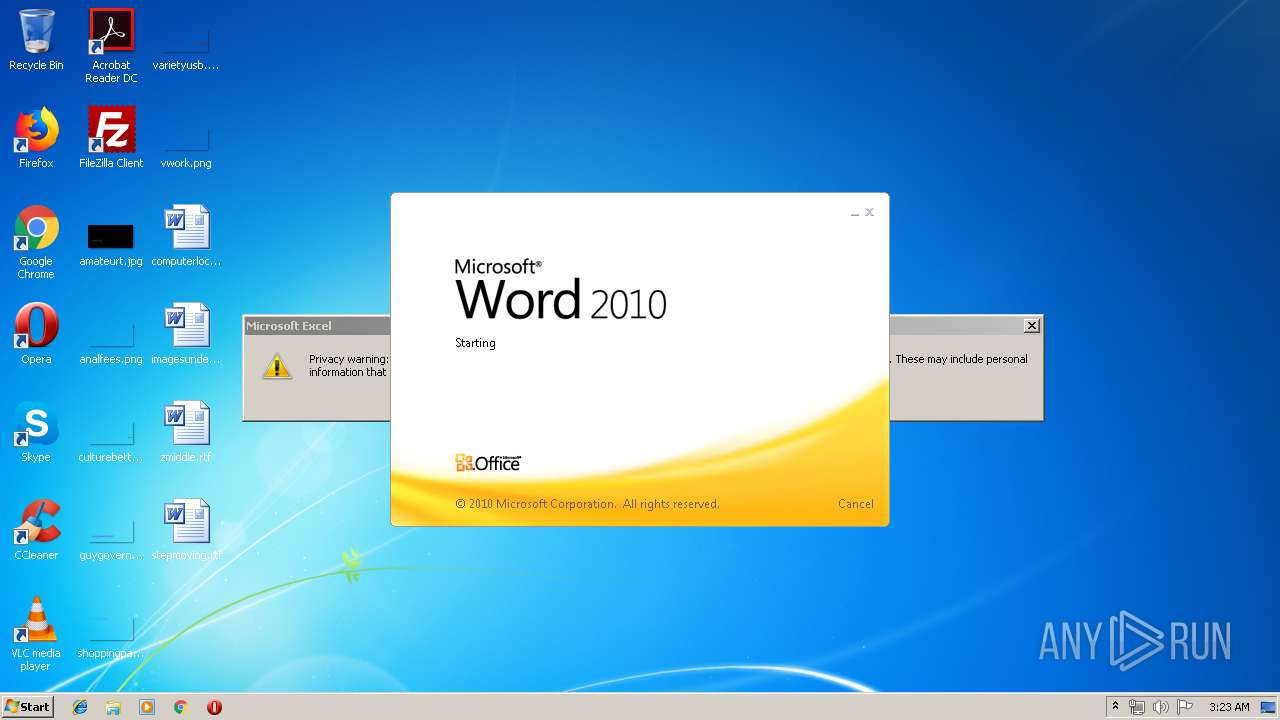
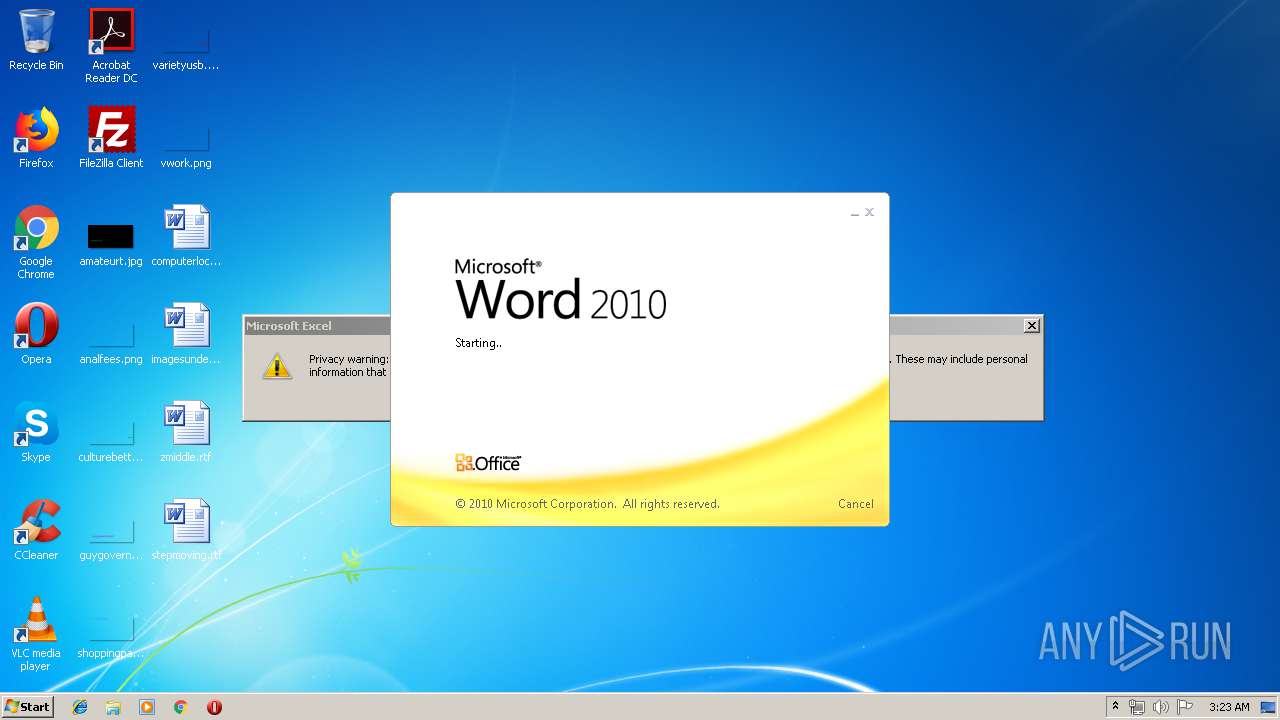
| 284 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\a.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 14.0.6024.1000 | ||||
| 4032 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" -Embedding | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | svchost.exe | |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Version: 14.0.6024.1000 | ||||
| 2616 | "C:\Windows\System32\cmd.exe" /c ping 127.0.0.1 -n 3 > nul & start C:\Users\Public\WindowsDefender.vbs | C:\Windows\System32\cmd.exe | — | EXCEL.EXE |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) | ||||
| 292 | "C:\Windows\System32\cmd.exe" /c ping 127.0.0.1 -n 5 > nul & start C:\Users\Public\atach.vbs | C:\Windows\System32\cmd.exe | — | EXCEL.EXE |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) | ||||
| 3480 | ping 127.0.0.1 -n 3 | C:\Windows\system32\PING.EXE | — | cmd.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
| 2352 | ping 127.0.0.1 -n 5 | C:\Windows\system32\PING.EXE | — | cmd.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
| 3408 | "C:\Windows\System32\WScript.exe" "C:\Users\Public\WindowsDefender.vbs" | C:\Windows\System32\WScript.exe | — | cmd.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 | ||||
| 3532 | "C:\Windows\System32\WScript.exe" "C:\Users\Public\atach.vbs" | C:\Windows\System32\WScript.exe | cmd.exe | |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 | ||||
| 3224 | "C:\Users\Public\amsi.dll" "C:\Users\Public\atach.vbs" | C:\Users\Public\amsi.dll | WScript.exe | |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 | ||||
| 848 | C:\Windows\system32\svchost.exe -k netsvcs | C:\Windows\System32\svchost.exe | services.exe | |
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
Total events
1 087
Read events
867
Write events
0
Delete events
0
Modification events
Executable files
1
Suspicious files
0
Text files
11
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 284 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR4682.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 4032 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR4E81.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 284 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\2EE8A7F1.emf | emf | |
MD5:D2F4DCA5A3F6A962C07D9F02B1FC3B46 | SHA256:7213805F4C566EA9F382050E9AB2FB0D2A7BFCE2FBD43F6A055E692325076F27 | |||
| 284 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:0F5BA6C2A5C3B478DAEE33B9B52E7387 | SHA256:5EF5D2016C6C1E44613F96651F62F1D4A7C2F6F86EABE0E3389E8524BBDAA6A5 | |||
| 848 | svchost.exe | C:\Windows\appcompat\programs\RecentFileCache.bcf | txt | |
MD5:71CA7046B0B8C29B86E377E31888B3D7 | SHA256:1EF7983D907EA8D5C152B0A6352827CA3F4133C26E42A77E66AF092D86073AD0 | |||
| 284 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$a.doc | pgc | |
MD5:114505677F8DF174F297EDD50A20C934 | SHA256:28B8690ACB4EE66C4244447DFD295B6A1D6F9F0E418C99B9C8486F19F25CCA45 | |||
| 4032 | EXCEL.EXE | C:\Users\Public\atach.vbs | text | |
MD5:6A38E73B9B0B30879A19EF216E19AB91 | SHA256:0E2DB9B565821E3DE073F9E3124F88EB1D795226B8241554A005086141EA4FCD | |||
| 4032 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\admin@pastebin[1].txt | text | |
MD5:5DCB9A66C046F179B57240EA3D069983 | SHA256:359B47C2256506A76EB9A9219D50500A981B9A308FCDEA40AC5DB11CE8AD56AC | |||
| 4032 | EXCEL.EXE | C:\Users\Public\WindowsDefender.vbs | text | |
MD5:7F2A202549A7CE9E21FA866B234E6E1F | SHA256:81D128737CE4EC69BCAB76FFA039B80C84A1E8001DB603029DA878E766BD0E9D | |||
| 1472 | amsi.dll | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\vb8yZXjq[1].txt | text | |
MD5:0752C4A687E5F6F80DEF2A017DA47BF3 | SHA256:E91E821C14A5FE33982952D83BE3917515E720DC8D6E7E91BC91B504A2FE7D95 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
26
DNS requests
4
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3224 | amsi.dll | 104.20.208.21:443 | pastebin.com | Cloudflare Inc | US | shared |
4032 | EXCEL.EXE | 104.20.208.21:443 | pastebin.com | Cloudflare Inc | US | shared |
1472 | amsi.dll | 168.197.229.117:70 | bylgay.hopto.org | GIGASAT SERVIÇOS DE PROCESSAMENTOS DE DADOS LTDA | BR | malicious |
1472 | amsi.dll | 104.20.208.21:443 | pastebin.com | Cloudflare Inc | US | shared |
1472 | amsi.dll | 79.134.225.20:70 | microsoftoutlook.duckdns.org | Andreas Fink trading as Fink Telecom Services | CH | malicious |
— | — | 168.197.229.117:70 | bylgay.hopto.org | GIGASAT SERVIÇOS DE PROCESSAMENTOS DE DADOS LTDA | BR | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
pastebin.com |
| shared |
bylgay.hopto.org |
| malicious |
soucdtevoceumcuzao.duckdns.org |
| malicious |
microsoftoutlook.duckdns.org |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
— | — | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |