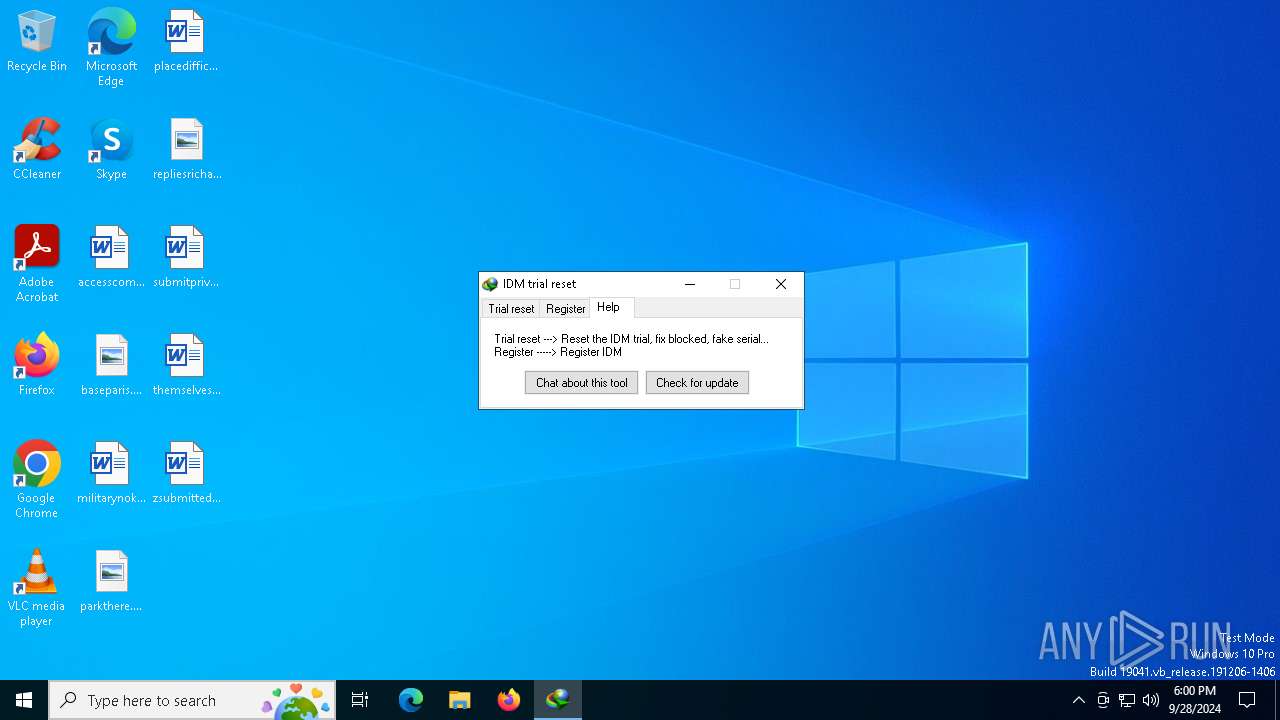
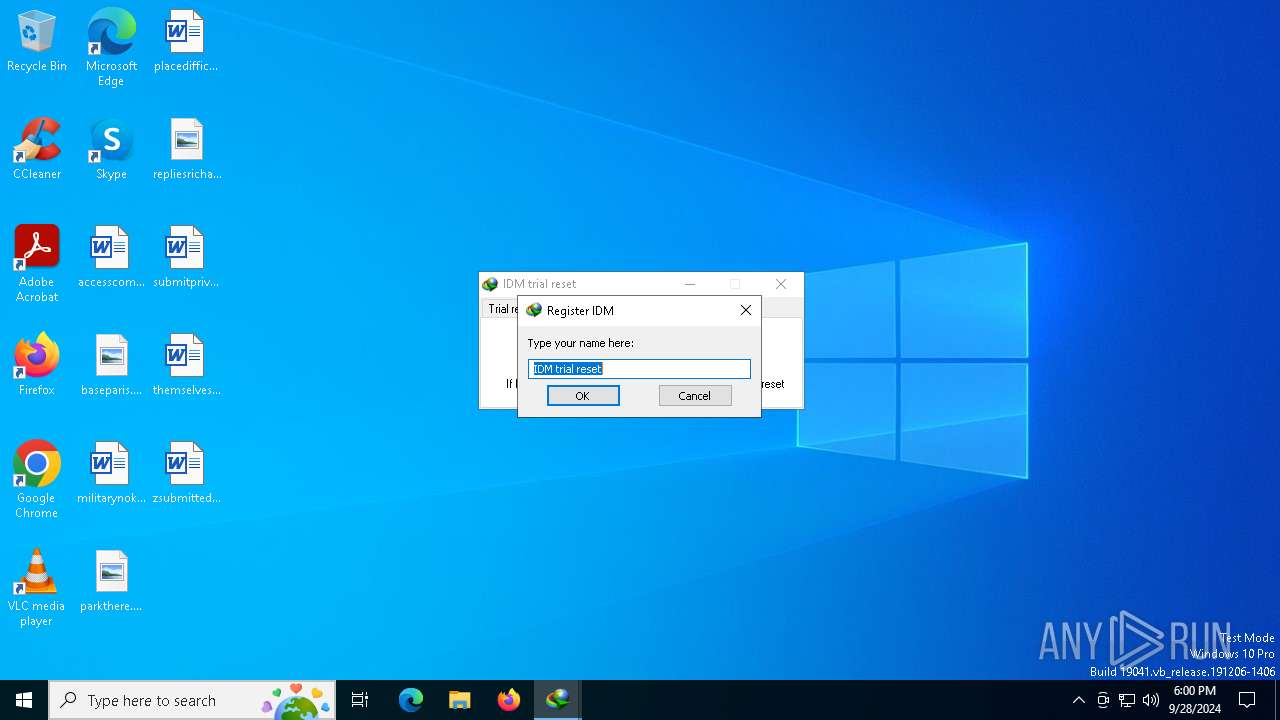
| File name: | IDM Trial Reset.exe |
| Full analysis: | https://app.any.run/tasks/8b03f1bb-fe8f-4928-b149-f073ade2b27b |
| Verdict: | Malicious activity |
| Analysis date: | September 28, 2024, 17:59:57 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed |
| MD5: | 064F82094AE6A6E22C28A6F1EF868A26 |
| SHA1: | E034CF1FA855EEF53FD46A5EC213ADA99E2ECE19 |
| SHA256: | A2D2B22CD0D5628976EB5996A8B20F3B5AC468907910DBC3F826F1069D435587 |
| SSDEEP: | 12288:fozGdX0M4ornOmZIzfMwHHQmRROXKFHhFjvVAcJlbqm9is3MjNindDO4FVALS/BB:f4GHnhIzOarrVuy8jadVFZIV7Um5iJL |
MALICIOUS
Antivirus name has been found in the command line (generic signature)
- IDM Trial Reset.exe (PID: 1164)
SUSPICIOUS
Executable content was dropped or overwritten
- IDM Trial Reset.exe (PID: 1164)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 1988)
- IDM Trial Reset.exe (PID: 1164)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 6212)
- cmd.exe (PID: 5984)
Starts CMD.EXE for commands execution
- IDM Trial Reset.exe (PID: 1164)
INFO
UPX packer has been detected
- IDM Trial Reset.exe (PID: 1164)
The process uses AutoIt
- IDM Trial Reset.exe (PID: 1164)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (28.6) |
|---|---|---|
| .exe | | | UPX compressed Win32 Executable (28) |
| .exe | | | Win32 EXE Yoda's Crypter (27.5) |
| .dll | | | Win32 Dynamic Link Library (generic) (6.8) |
| .exe | | | Win32 Executable (generic) (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2016:09:05 22:20:25+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 12 |
| CodeSize: | 352256 |
| InitializedDataSize: | 544768 |
| UninitializedDataSize: | 1073152 |
| EntryPoint: | 0x15cac0 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | English (British) |
| CharacterSet: | Unicode |
| FileVersion: | 1.0.0.0 |
| Comments: | Use IDM forever without cracking |
| FileDescription: | Use IDM forever without cracking |
| ProductVersion: | 1.0.0.0 |
| LegalCopyright: | (C) 2016 idmresettrial All rights reserved. |
| InternalName: | IDM Trial Reset.exe |
| OriginalFileName: | IDM Trial Reset.exe |
| ProductName: | IDM Trial Reset |
| CompanyName: | J2TeaM |
| Website: | https://junookyo.blogspot.com/ |
| BuildTime: | 5:20:25 AM - 06/09/2016 |
Total processes
311
Monitored processes
181
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 420 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | reg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 420 | "C:\Users\admin\AppData\Local\Temp\SetACLx64.exe" -on HKCU\Software\Classes\Wow6432Node\CLSID\{5ED60779-4DE2-4E07-B862-974CA4FF2E9C} -ot reg -actn setowner -ownr "n:S-1-0-0" -silent | C:\Users\admin\AppData\Local\Temp\SetACLx64.exe | — | IDM Trial Reset.exe | |||||||||||
User: admin Company: Helge Klein Integrity Level: MEDIUM Description: SetACL 3 Exit code: 5 Version: 3.0.6.0 Modules
| |||||||||||||||
| 440 | "C:\Users\admin\AppData\Local\Temp\SetACLx64.exe" -on HKLM\Software\Classes\Wow6432Node\CLSID\{7B8E9164-324D-4A2E-A46D-0165FB2000EC} -ot reg -actn ace -ace "n:everyone;p:full" -actn setprot -op "dacl:p_nc;sacl:p_nc" -silent | C:\Users\admin\AppData\Local\Temp\SetACLx64.exe | — | IDM Trial Reset.exe | |||||||||||
User: admin Company: Helge Klein Integrity Level: MEDIUM Description: SetACL 3 Exit code: 12 Version: 3.0.6.0 Modules
| |||||||||||||||
| 448 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SetACLx64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 608 | "C:\Users\admin\AppData\Local\Temp\SetACLx64.exe" -on HKCU\Software\Classes\Wow6432Node\CLSID\{7B8E9164-324D-4A2E-A46D-0165FB2000EC} -ot reg -actn ace -ace "n:everyone;p:read" -actn setprot -op "dacl:p_nc;sacl:p_nc" -silent | C:\Users\admin\AppData\Local\Temp\SetACLx64.exe | — | IDM Trial Reset.exe | |||||||||||
User: admin Company: Helge Klein Integrity Level: MEDIUM Description: SetACL 3 Exit code: 12 Version: 3.0.6.0 Modules
| |||||||||||||||
| 752 | "C:\Users\admin\AppData\Local\Temp\SetACLx64.exe" -on HKCU\Software\Classes\CLSID\{7B8E9164-324D-4A2E-A46D-0165FB2000EC} -ot reg -actn ace -ace "n:everyone;p:read" -actn setprot -op "dacl:p_nc;sacl:p_nc" -silent | C:\Users\admin\AppData\Local\Temp\SetACLx64.exe | — | IDM Trial Reset.exe | |||||||||||
User: admin Company: Helge Klein Integrity Level: MEDIUM Description: SetACL 3 Exit code: 12 Version: 3.0.6.0 Modules
| |||||||||||||||
| 832 | "C:\Users\admin\AppData\Local\Temp\SetACLx64.exe" -on HKCU\Software\Classes\Wow6432Node\CLSID\{D5B91409-A8CA-4973-9A0B-59F713D25671} -ot reg -actn setowner -ownr "n:S-1-1-0" -silent | C:\Users\admin\AppData\Local\Temp\SetACLx64.exe | — | IDM Trial Reset.exe | |||||||||||
User: admin Company: Helge Klein Integrity Level: MEDIUM Description: SetACL 3 Exit code: 5 Version: 3.0.6.0 Modules
| |||||||||||||||
| 832 | reg delete "HKCU\Software\Microsoft\Windows\CurrentVersion\Run" /v "IDM trial reset" /f | C:\Windows\SysWOW64\reg.exe | — | IDM Trial Reset.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 840 | "C:\Users\admin\AppData\Local\Temp\SetACLx64.exe" -on HKCU\Software\Classes\CLSID\{D5B91409-A8CA-4973-9A0B-59F713D25671} -ot reg -actn ace -ace "n:everyone;p:full" -actn setprot -op "dacl:p_nc;sacl:p_nc" -silent | C:\Users\admin\AppData\Local\Temp\SetACLx64.exe | — | IDM Trial Reset.exe | |||||||||||
User: admin Company: Helge Klein Integrity Level: MEDIUM Description: SetACL 3 Exit code: 12 Version: 3.0.6.0 Modules
| |||||||||||||||
| 884 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SetACLx64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
24 539
Read events
24 523
Write events
10
Delete events
6
Modification events
| (PID) Process: | (5196) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\DownloadManager |
| Operation: | delete value | Name: | FName |
Value: | |||
| (PID) Process: | (5196) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\DownloadManager |
| Operation: | delete value | Name: | LName |
Value: | |||
| (PID) Process: | (5196) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\DownloadManager |
| Operation: | delete value | Name: | |
Value: | |||
| (PID) Process: | (5196) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\DownloadManager |
| Operation: | delete value | Name: | Serial |
Value: | |||
| (PID) Process: | (6576) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\DownloadManager |
| Operation: | delete value | Name: | auto_reset_trial |
Value: | |||
| (PID) Process: | (832) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | IDM trial reset |
Value: | |||
| (PID) Process: | (1948) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\DownloadManager |
| Operation: | write | Name: | FName |
Value: IDM trial reset | |||
| (PID) Process: | (1948) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\DownloadManager |
| Operation: | write | Name: | LName |
Value: (http://bit.ly/IDMresetTrialForum) | |||
| (PID) Process: | (1948) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\DownloadManager |
| Operation: | write | Name: | |
Value: your@email.com | |||
| (PID) Process: | (1948) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\DownloadManager |
| Operation: | write | Name: | Serial |
Value: 9QNBL-L2641-Y7WVE-QEN3I | |||
Executable files
2
Suspicious files
5
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1164 | IDM Trial Reset.exe | C:\Users\admin\AppData\Local\Temp\aut633B.tmp | binary | |
MD5:D71743C02DF05822F49FF9E232DE76F0 | SHA256:62AAECFD2ECA11B635DDC0AC246F9EFC991A56CAE43E009EABA9367BB287AD89 | |||
| 1164 | IDM Trial Reset.exe | C:\Users\admin\AppData\Local\Temp\aut634D.tmp | binary | |
MD5:90585D687B4426794D2DED4DD0E5FBE2 | SHA256:84DE96E94FEAFB174FD2BF79007F27BC8B43C462FB7B4A1C5137D8BA0EEB8840 | |||
| 1164 | IDM Trial Reset.exe | C:\Users\admin\AppData\Local\Temp\idm_trial.reg | text | |
MD5:237962E36948F3D0C9EC42EFA289AC52 | SHA256:40AD93CF424EEE41A0877B11ACB92F7F12D58AB3AA6FA6D64D92CFBBE11695A2 | |||
| 1164 | IDM Trial Reset.exe | C:\Users\admin\AppData\Local\Temp\aut634C.tmp | binary | |
MD5:E68C65421712C99C0FA515EB087B412B | SHA256:2CE685037E366A0FD2FF1827C20F1866BCBE23D646DFCE30A459B8FF3C1B4F2E | |||
| 1164 | IDM Trial Reset.exe | C:\Users\admin\AppData\Local\Temp\aut635E.tmp | binary | |
MD5:2EBB8A2070729BC3CAE5B5E1CC27C963 | SHA256:B951A1F1EC92F71EEF08E59988267CC19BF35286B90A2CBE50C4B1062C2FD0AC | |||
| 1164 | IDM Trial Reset.exe | C:\Users\admin\AppData\Local\Temp\SetACLx64.exe | executable | |
MD5:3E350EB5DF15C06DEC400A39DD1C6F29 | SHA256:427FF43693CB3CA2812C4754F607F107A6B2D3F5A8B313ADDEE57D89982DF419 | |||
| 1164 | IDM Trial Reset.exe | C:\Users\admin\AppData\Local\Temp\idm_reg.reg | text | |
MD5:3DEDFE7770A57CA2BCB76D01D1756EE6 | SHA256:832134EB65B2A91BE5B6584B48AB69B4B7CE9B6228EA4738F6D1B7A8A0E1915E | |||
| 1164 | IDM Trial Reset.exe | C:\Users\admin\AppData\Local\Temp\SetACLx32.exe | executable | |
MD5:451AE03D3C92777F09840CA56F08AB62 | SHA256:D5E779D151772504662E8226EB4107330FFA7A51209EEE42B6D5883D99100BA9 | |||
| 1164 | IDM Trial Reset.exe | C:\Users\admin\AppData\Local\Temp\aut639D.tmp | binary | |
MD5:715EC543E4A386475E2105954DAD0929 | SHA256:C28E0CB287457A5B00BF34983D00256E263C00231B5CBB0F8BEF4233C47F7D55 | |||
| 1164 | IDM Trial Reset.exe | C:\Users\admin\AppData\Local\Temp\idm_reset.reg | text | |
MD5:17EBF21FCCAC9756EAB46EB64BA6C029 | SHA256:290A3F67BBBDBD5C1101E90921475C2B95E97DC69A3141412FBAC79FCADD3EE8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
45
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6912 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2144 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
1684 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1684 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6432 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3260 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6912 | svchost.exe | 20.190.160.14:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6912 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |