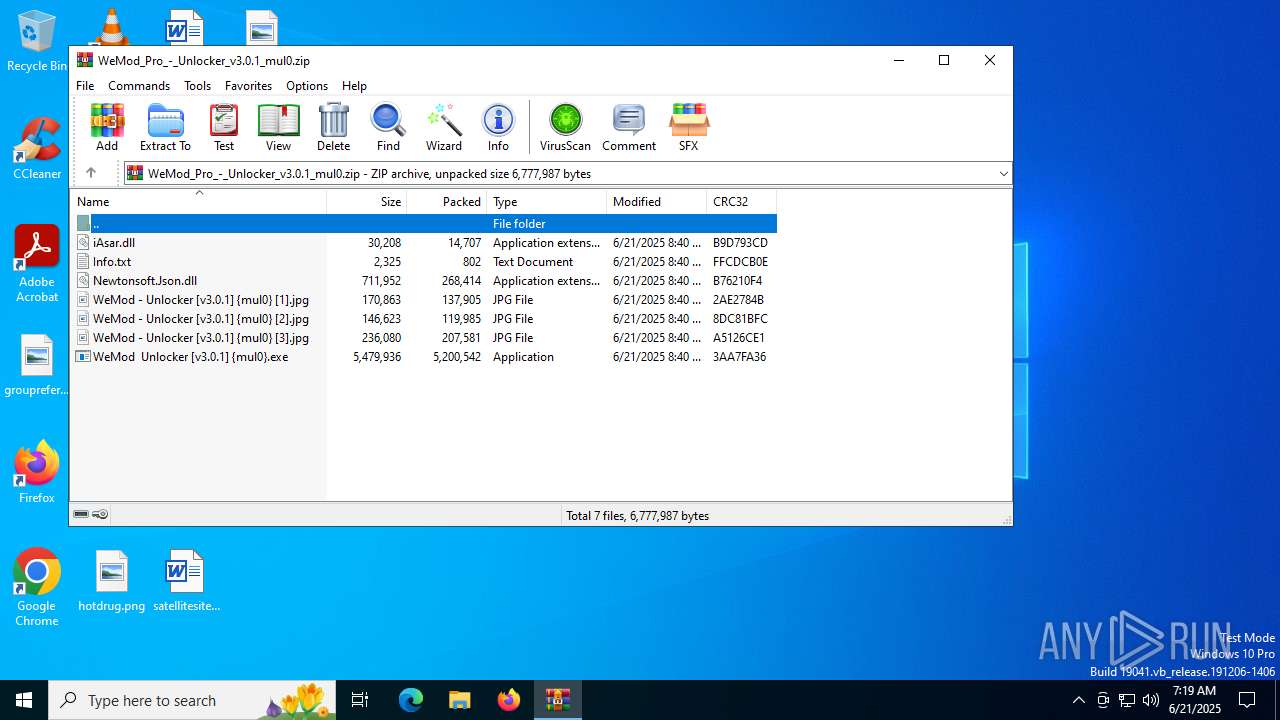
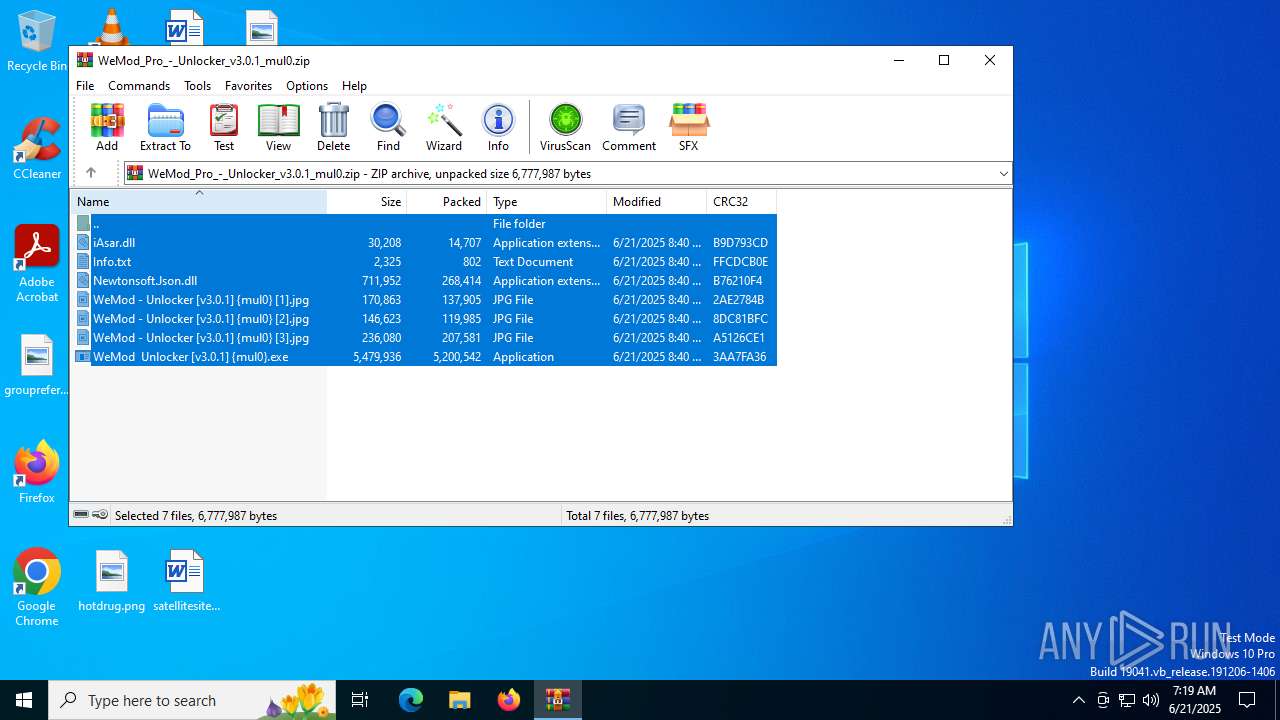
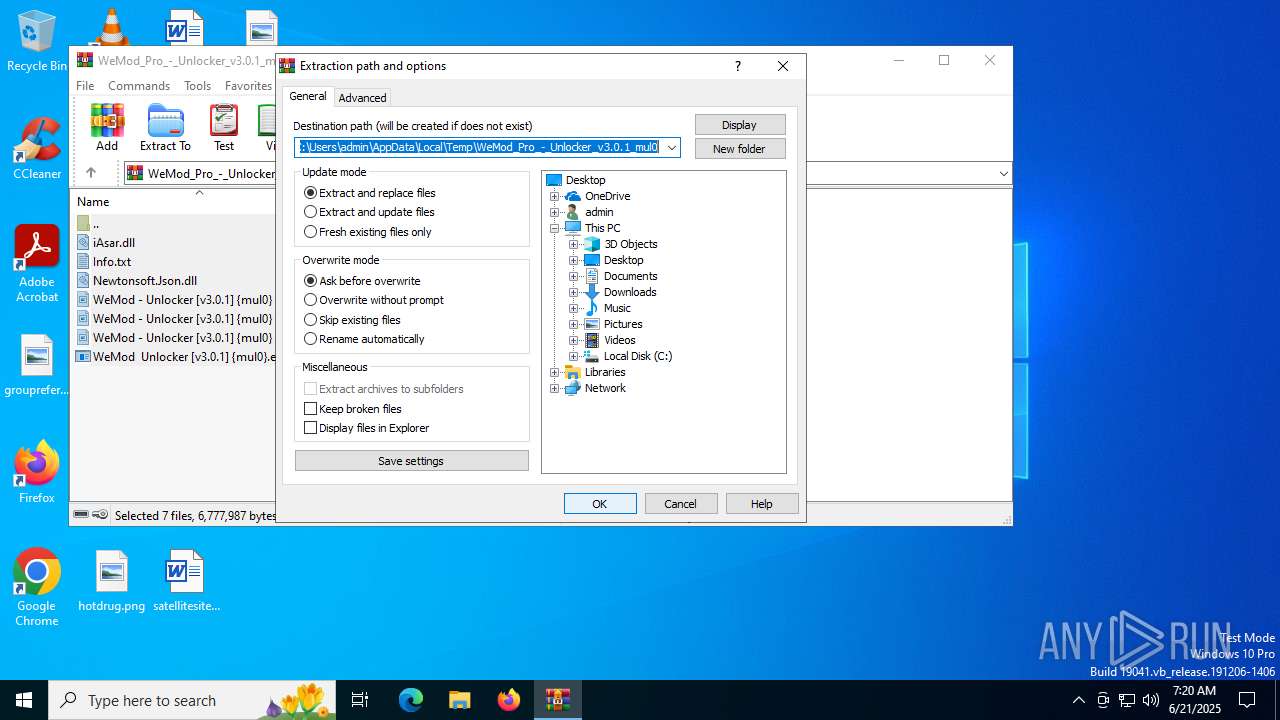
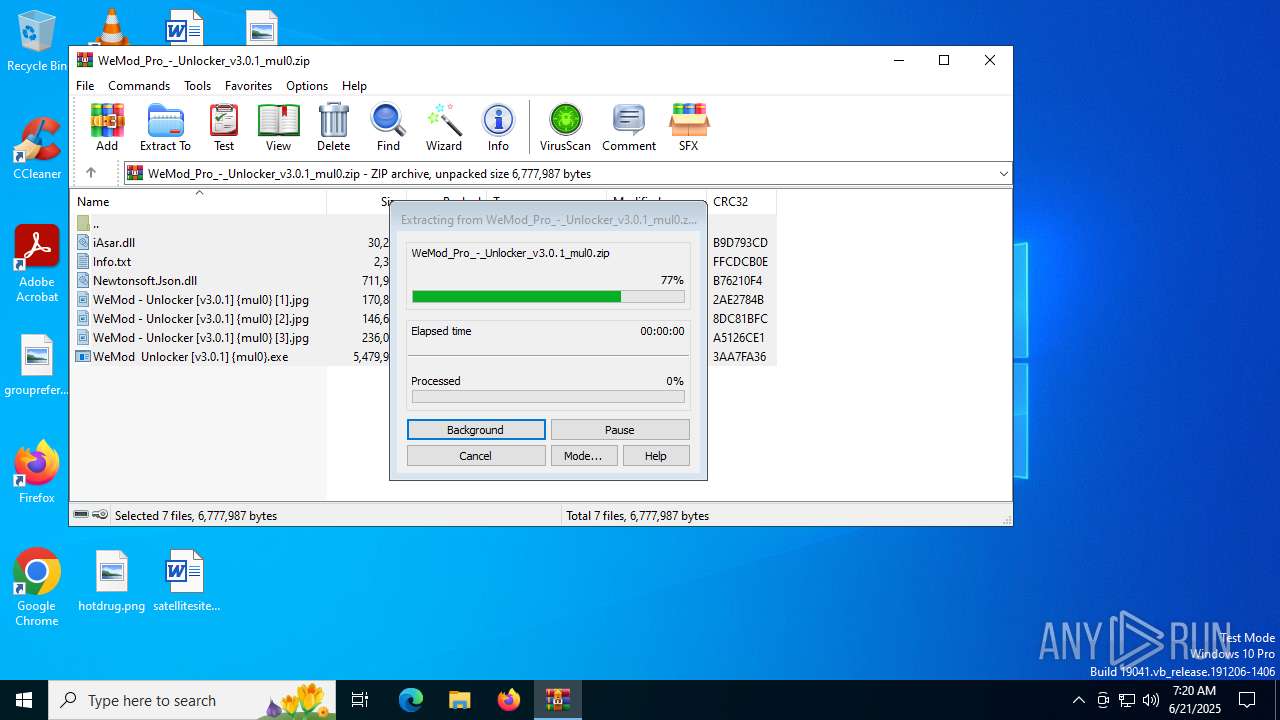
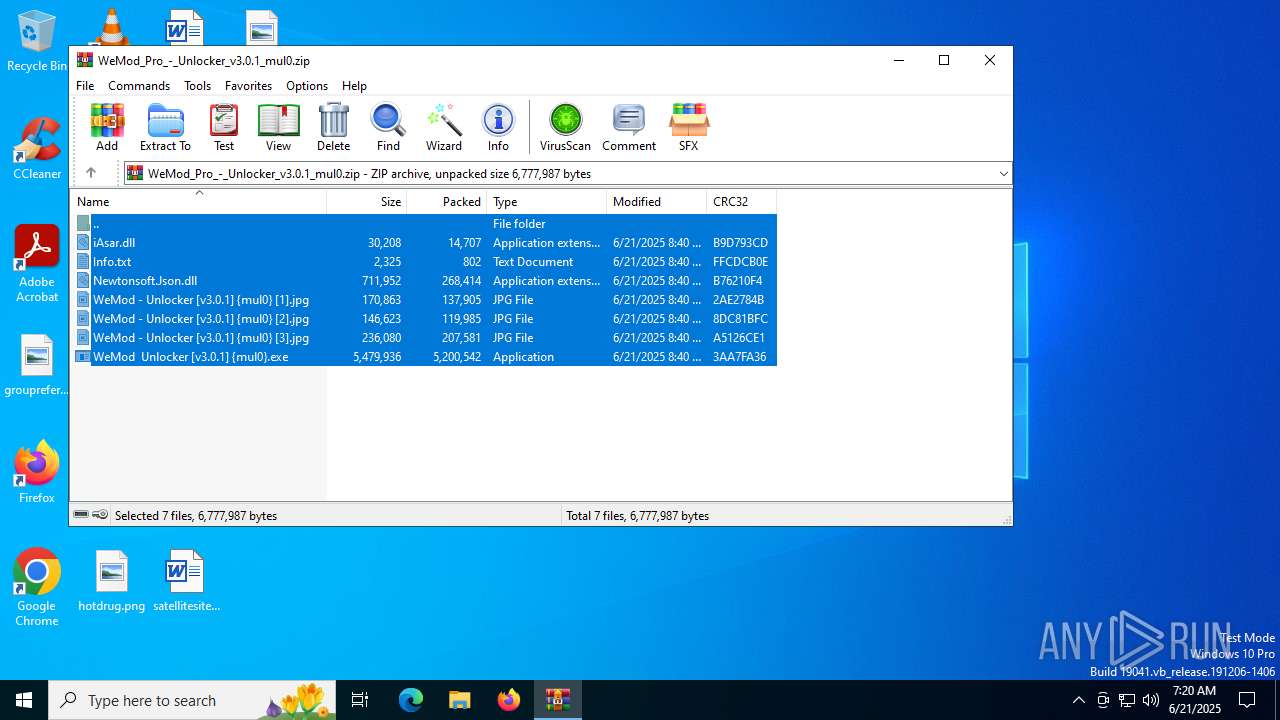
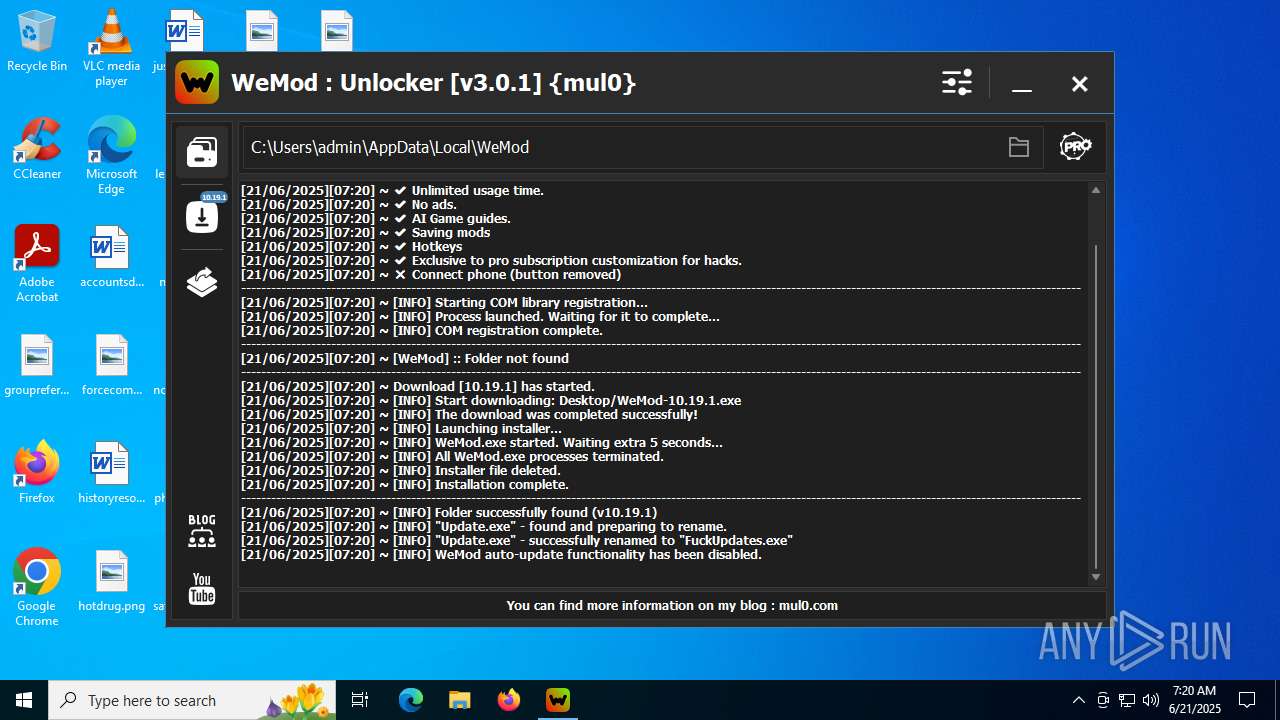
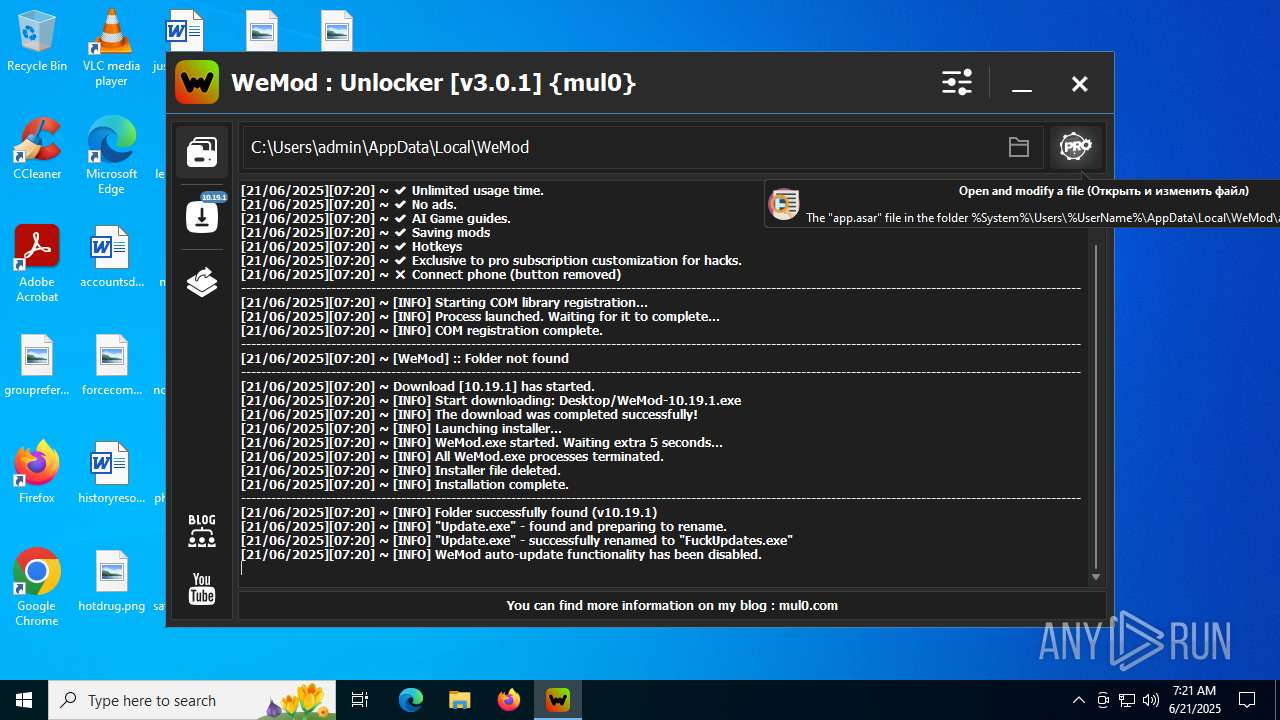
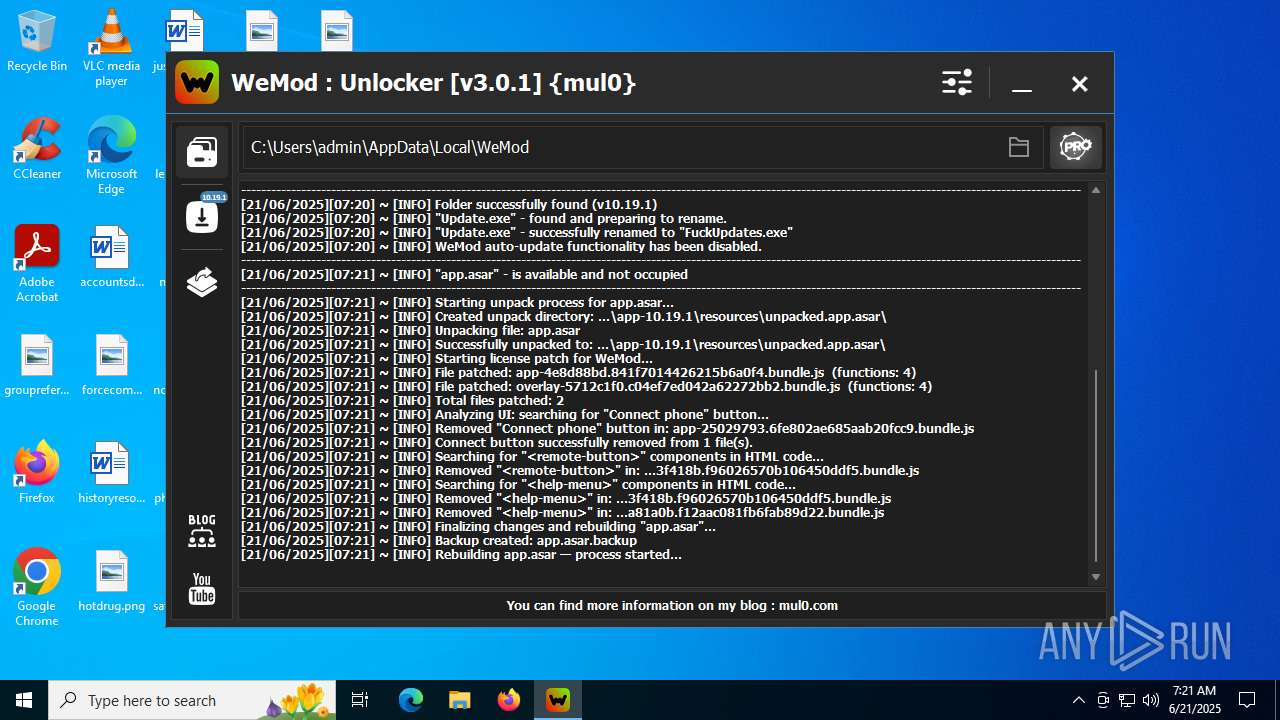
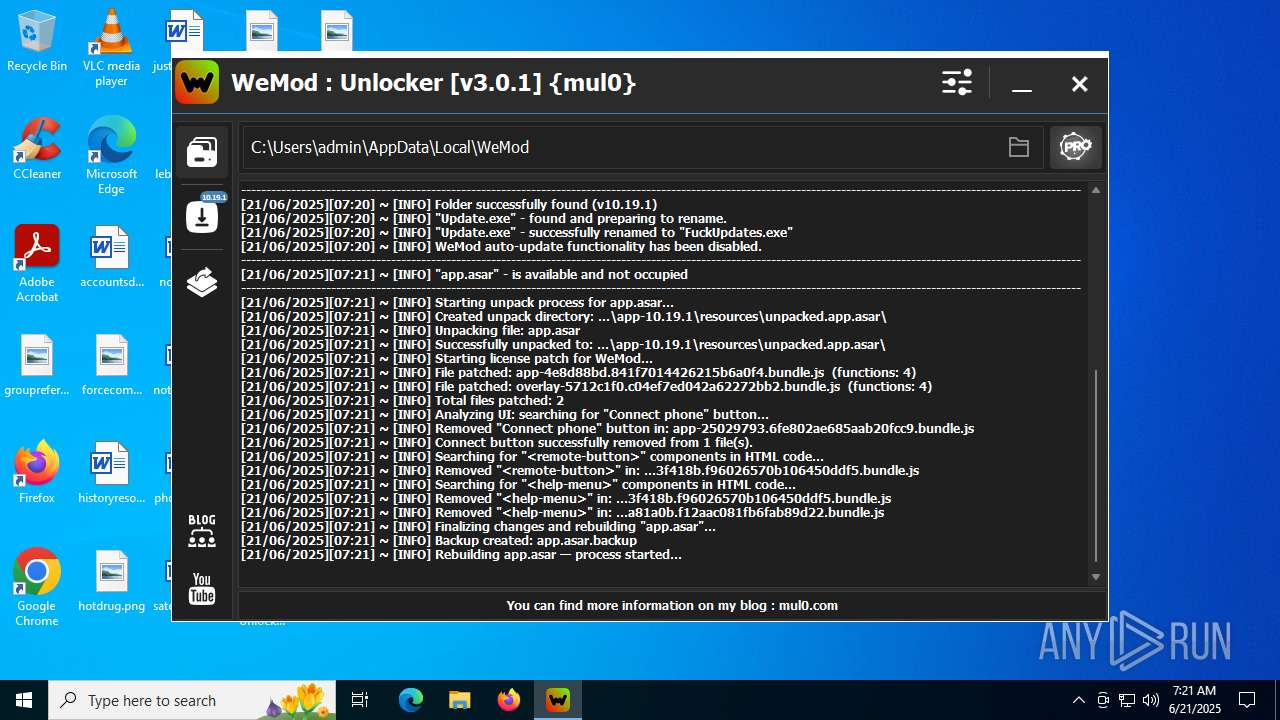
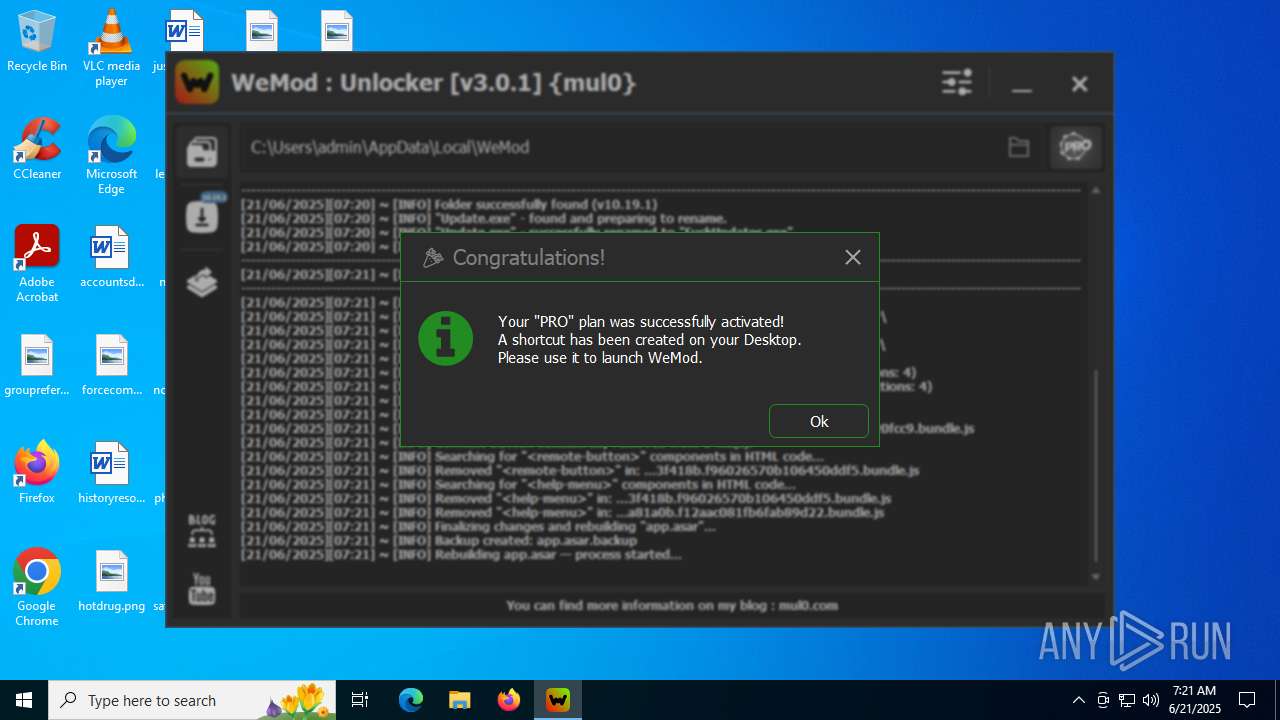
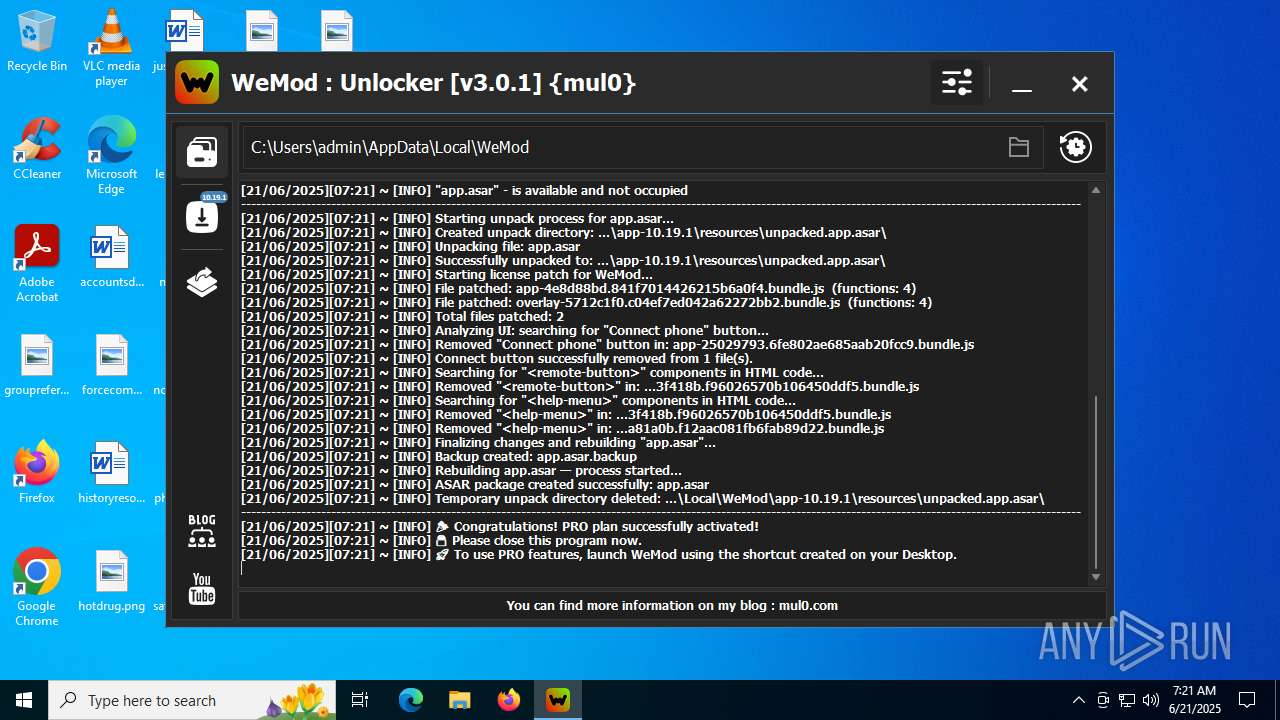
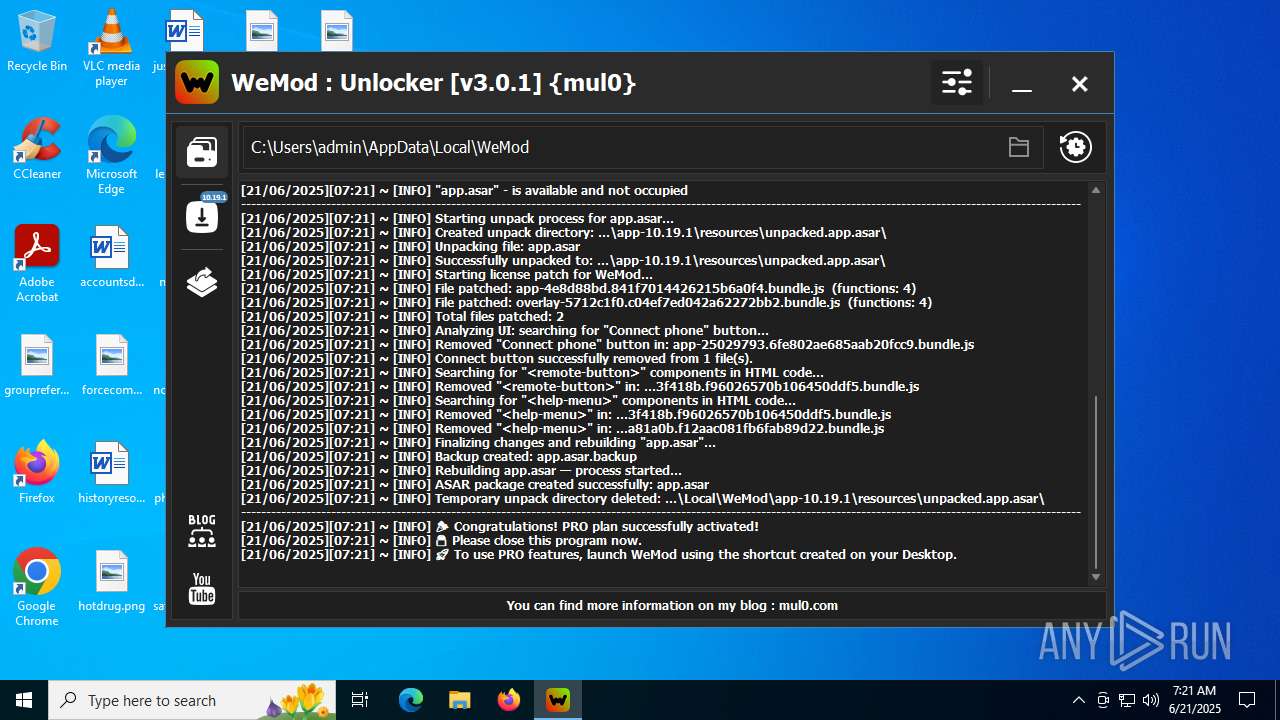
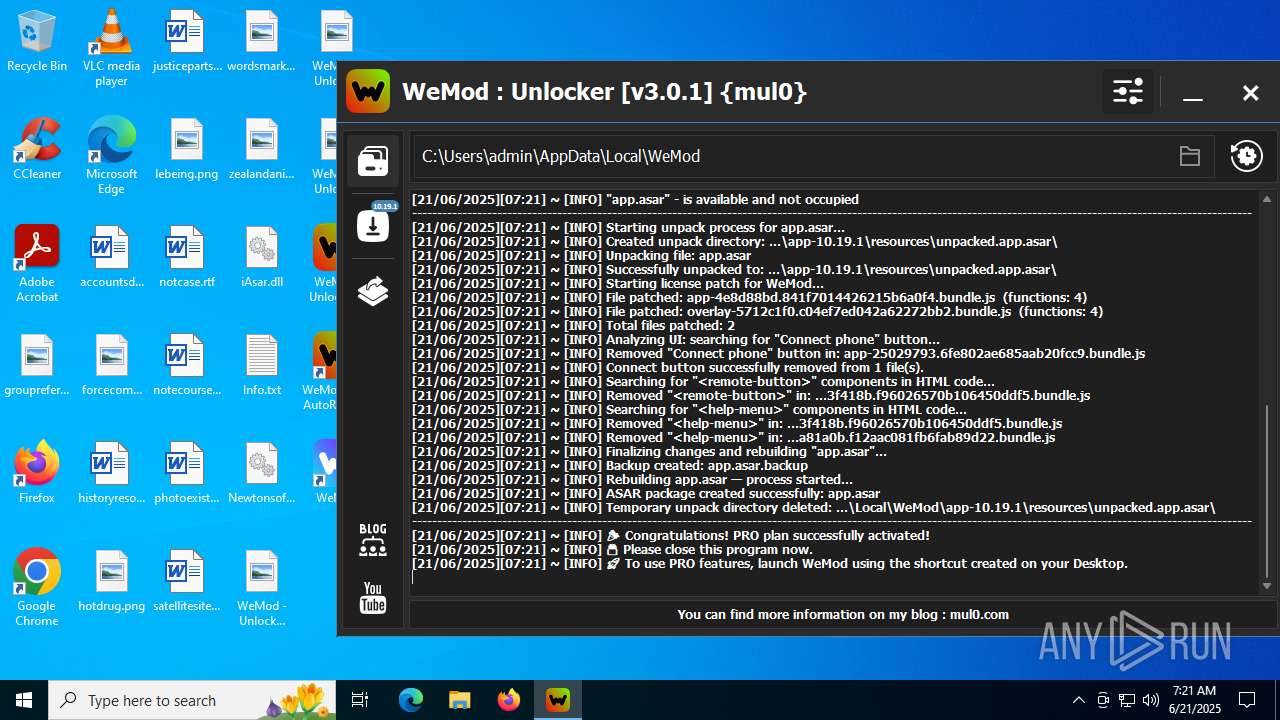
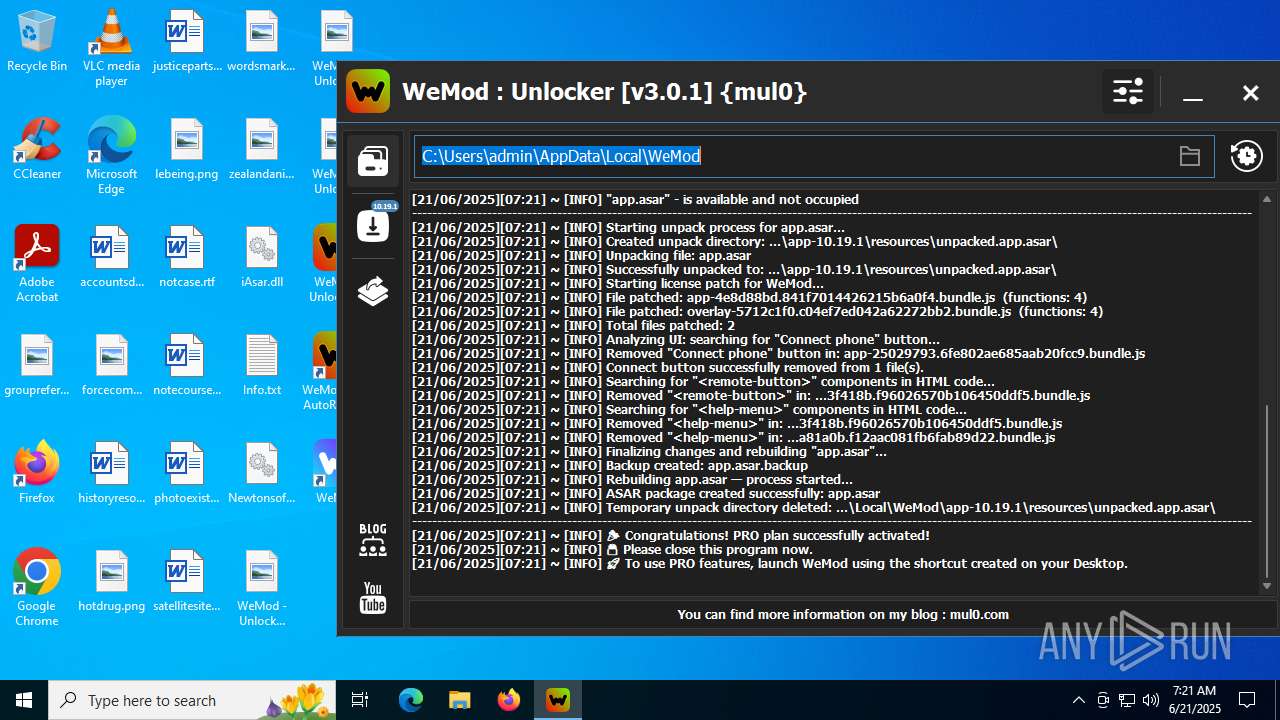
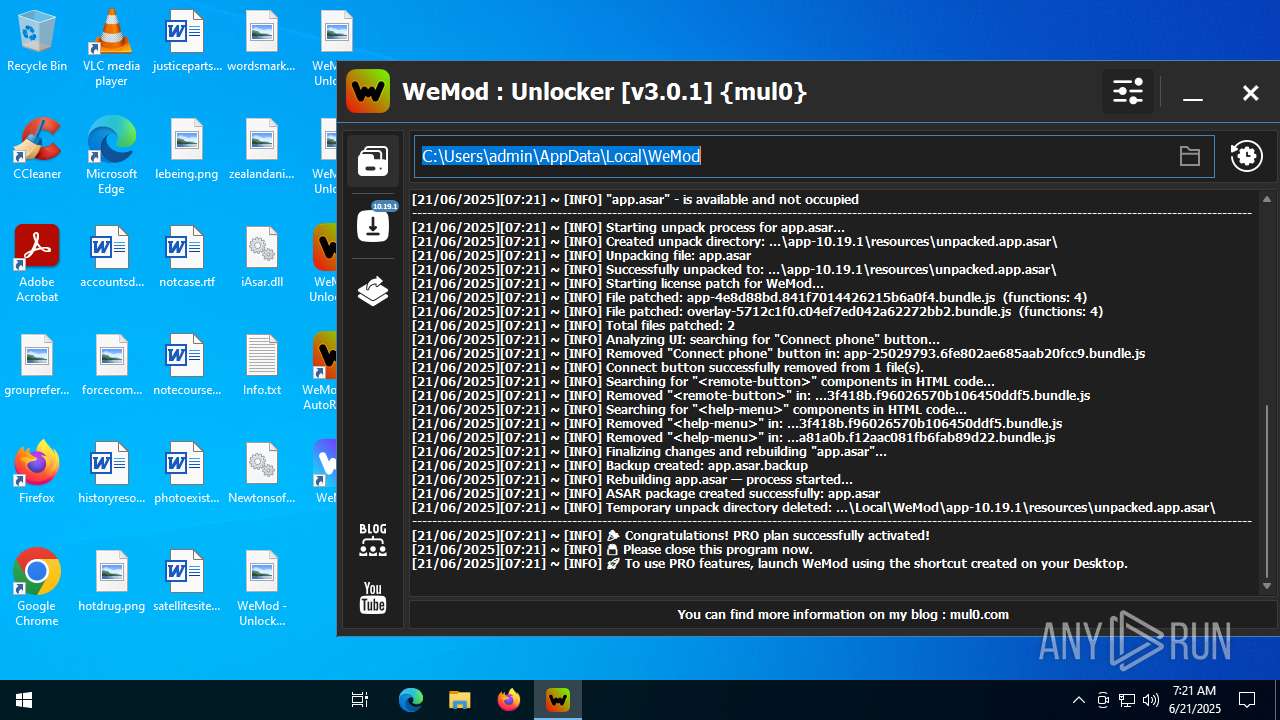
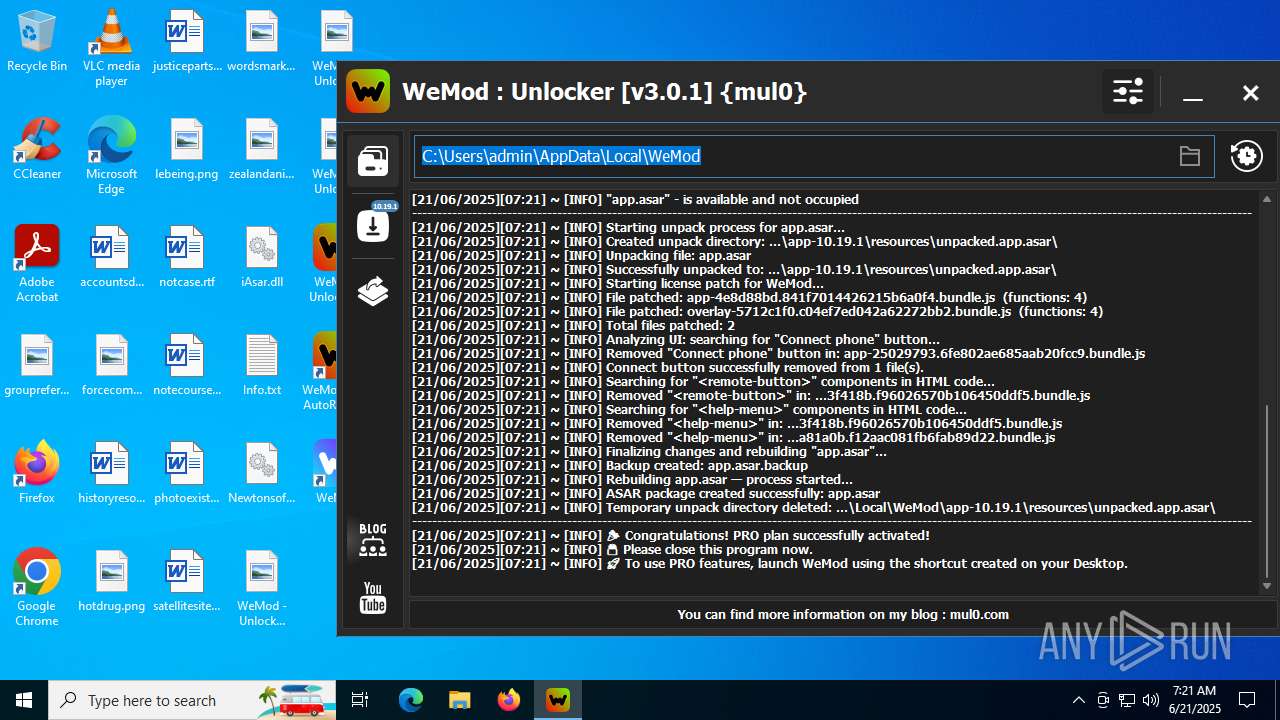
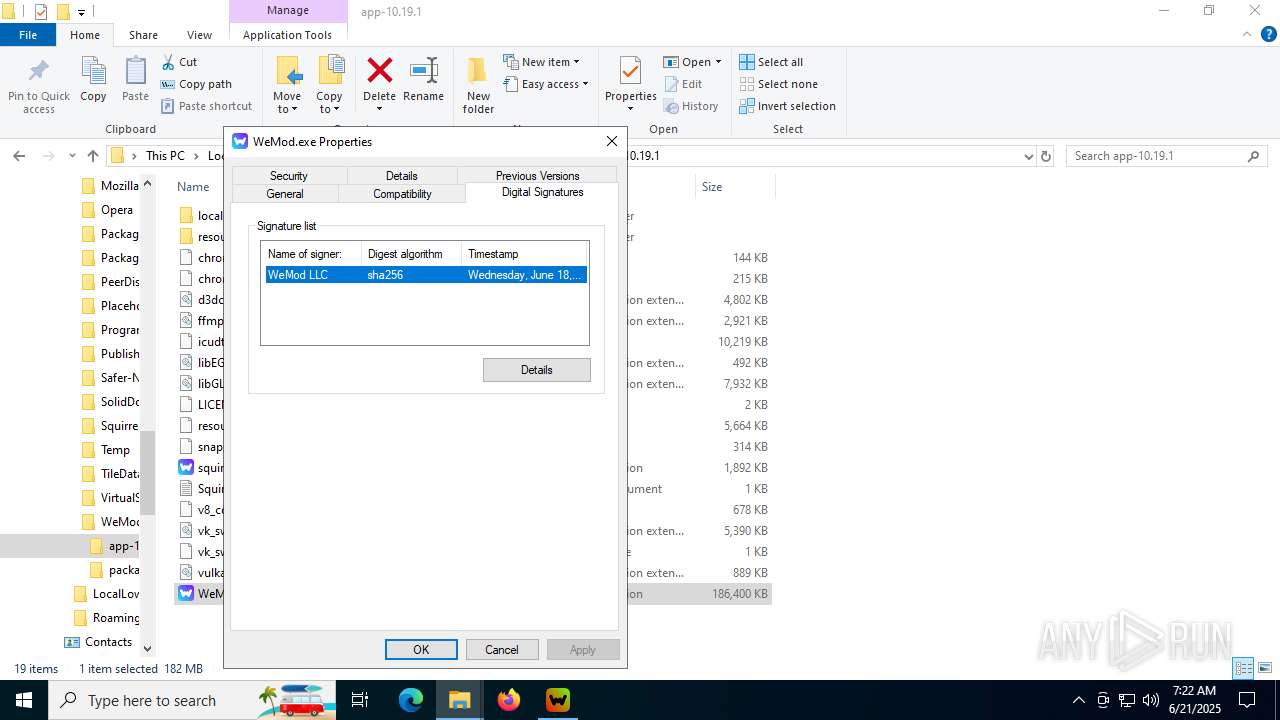
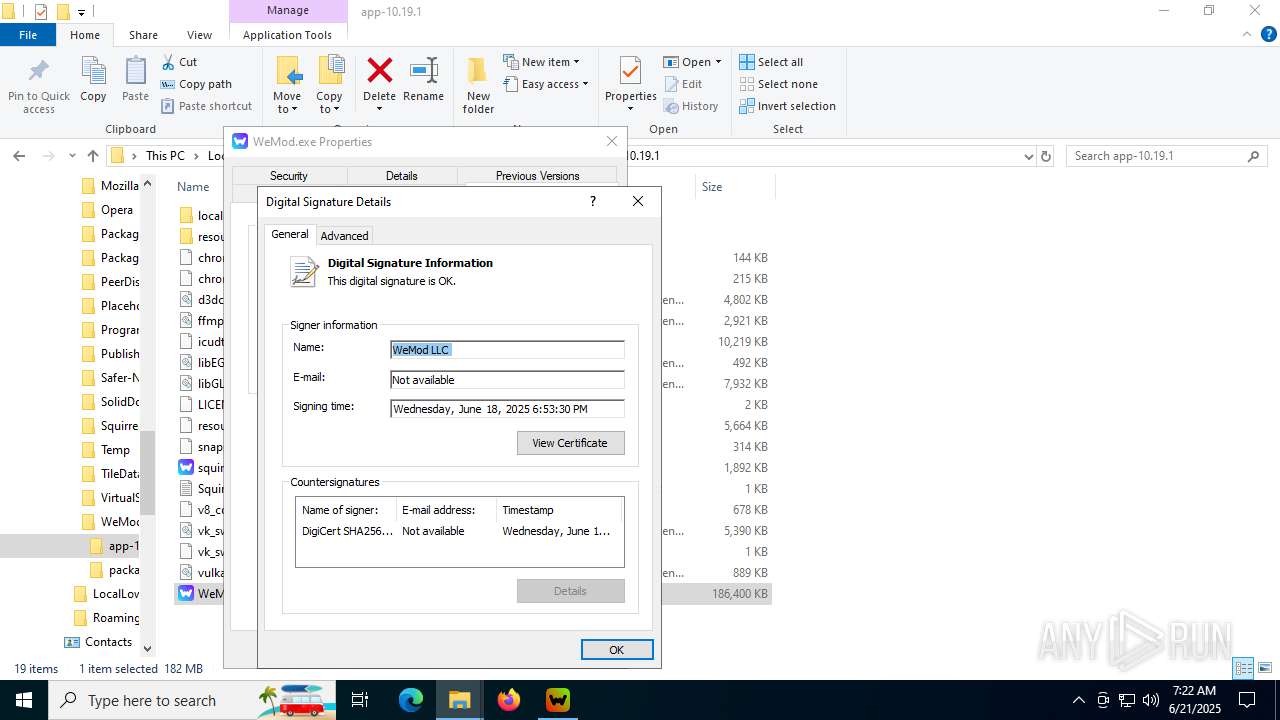
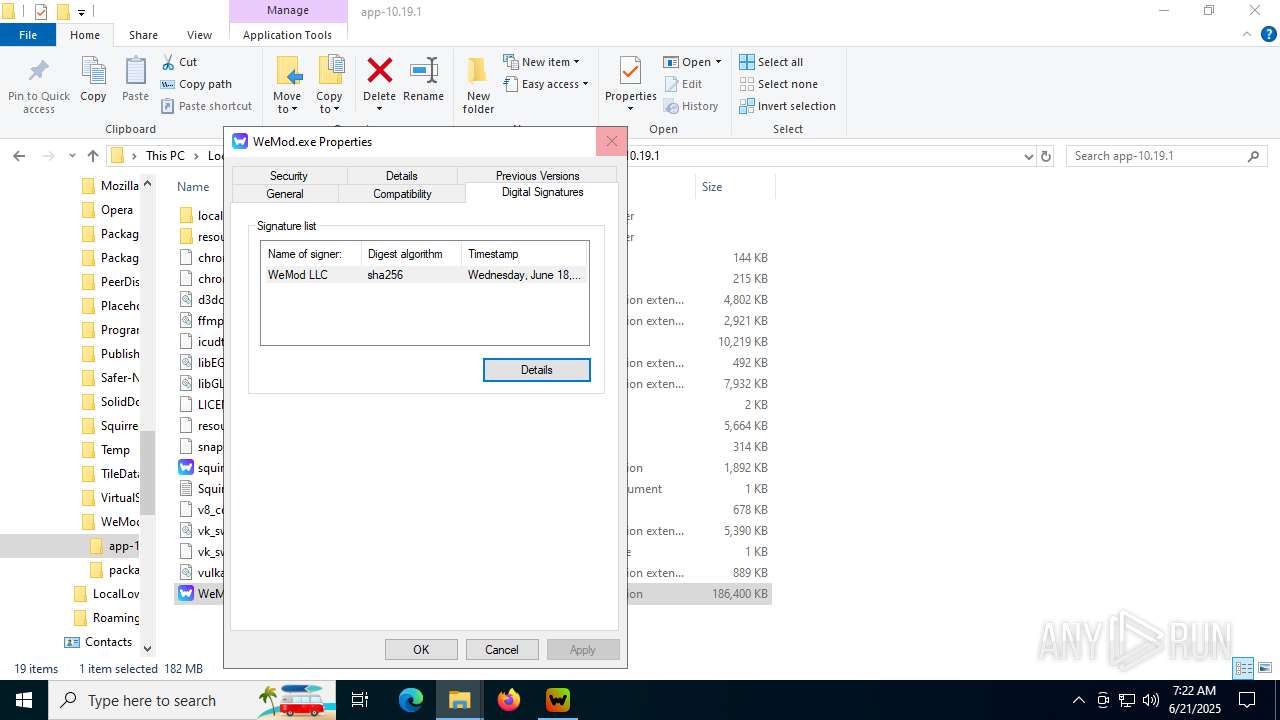
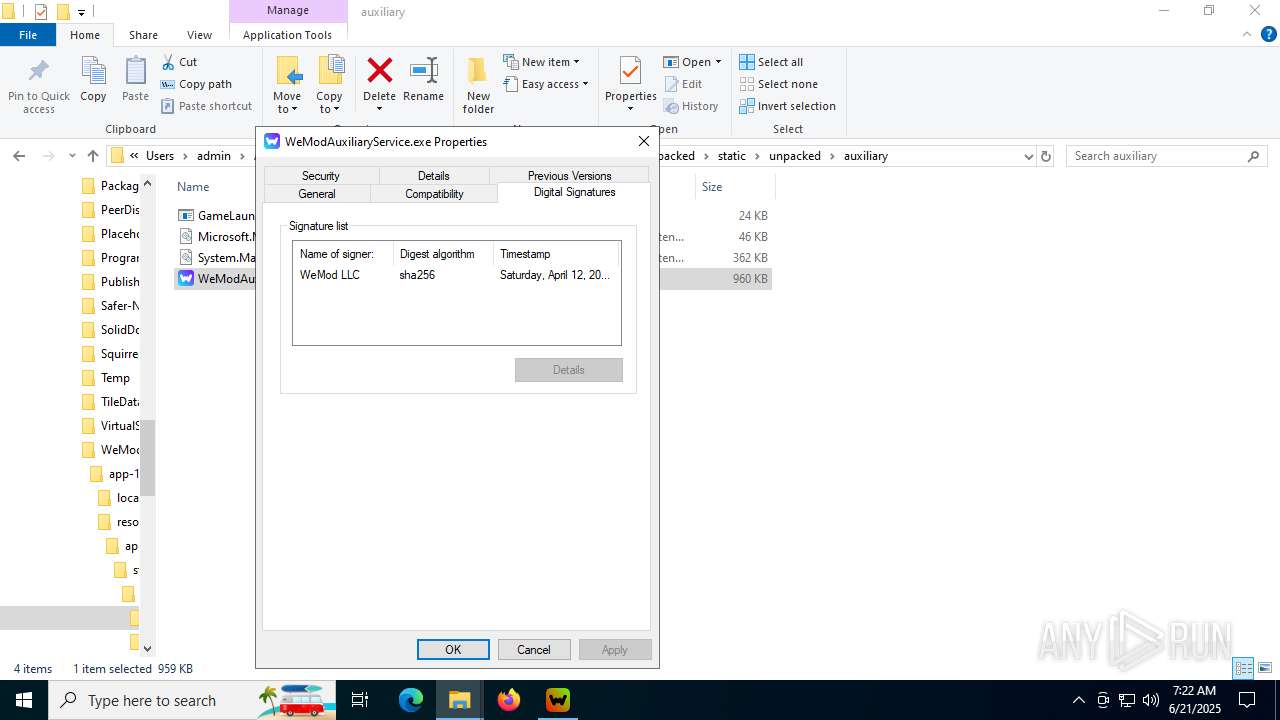
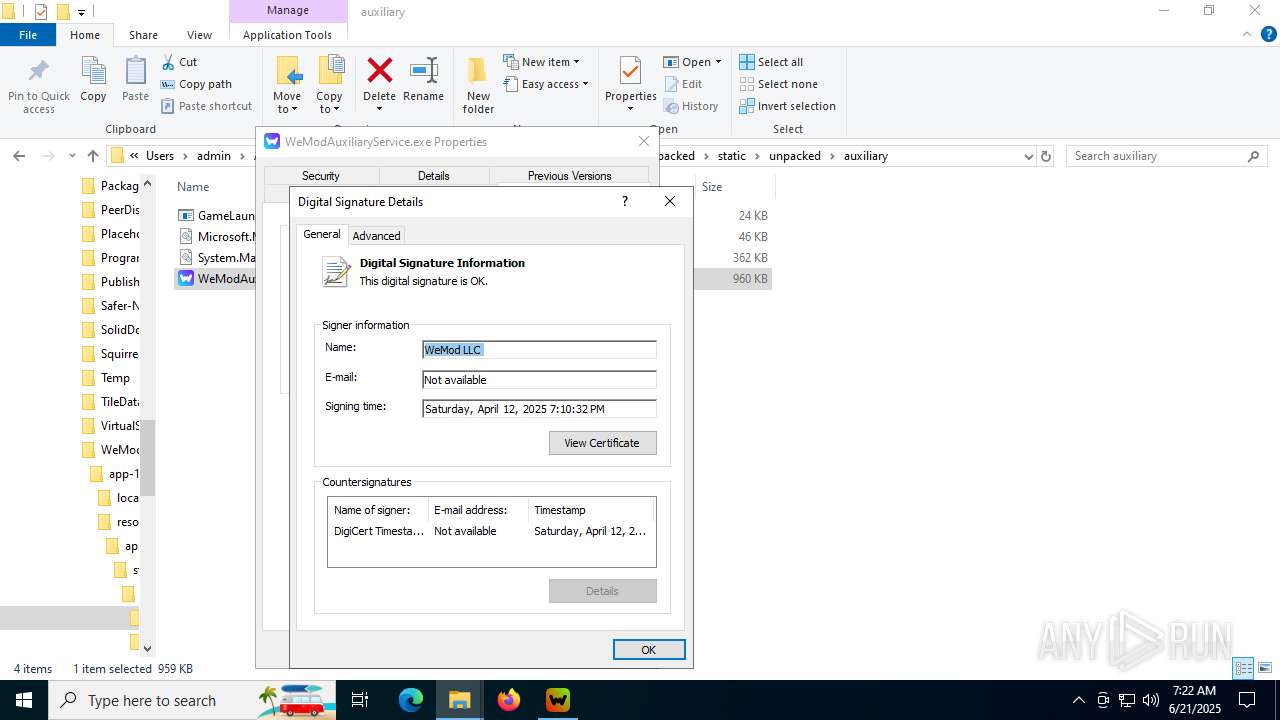
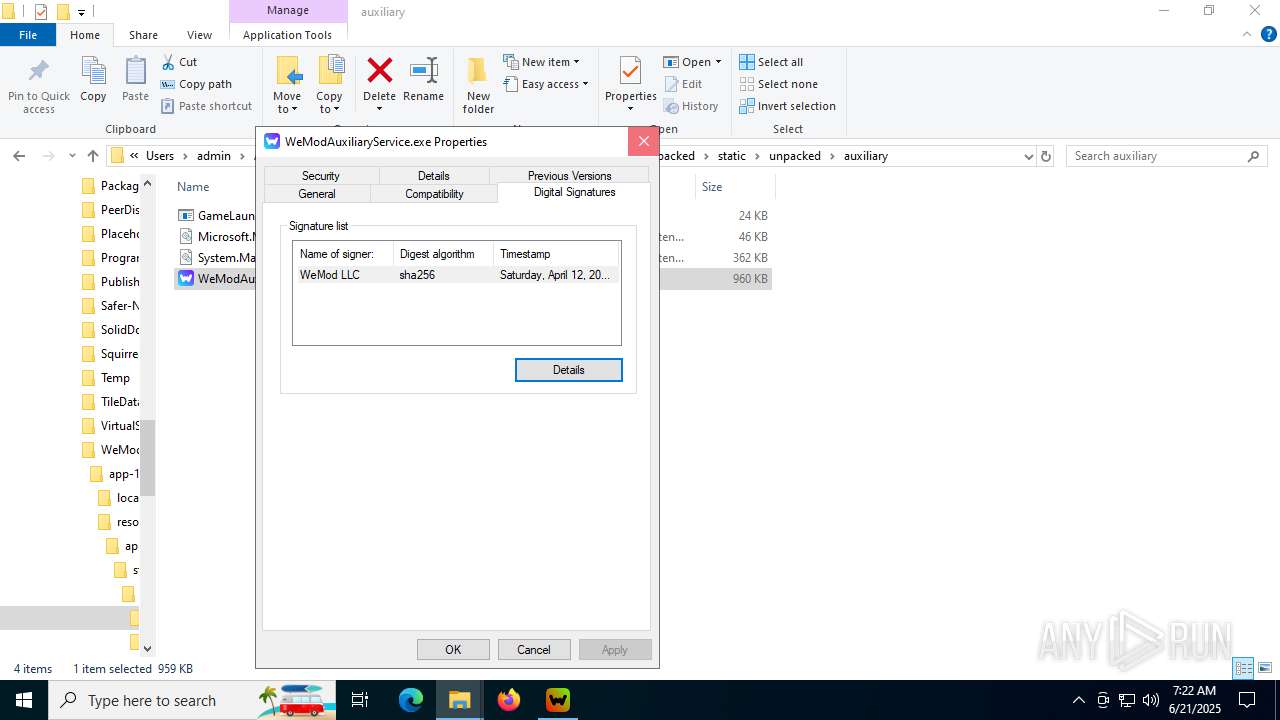
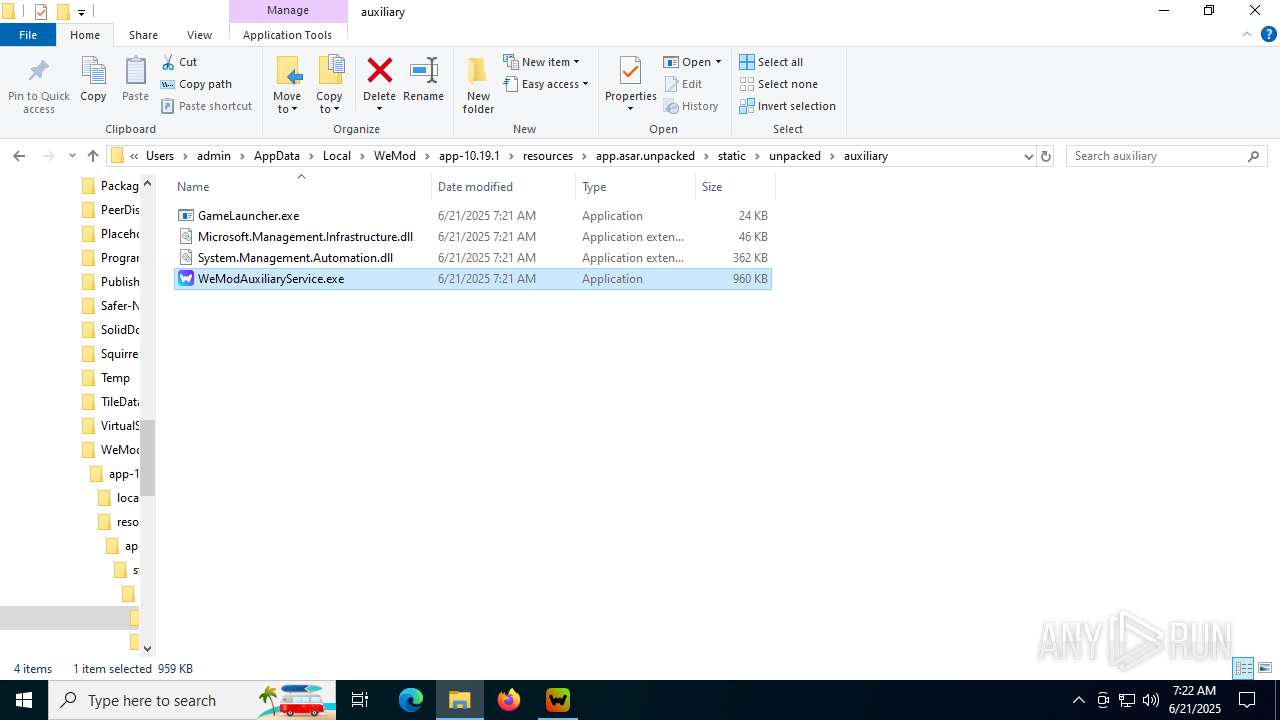
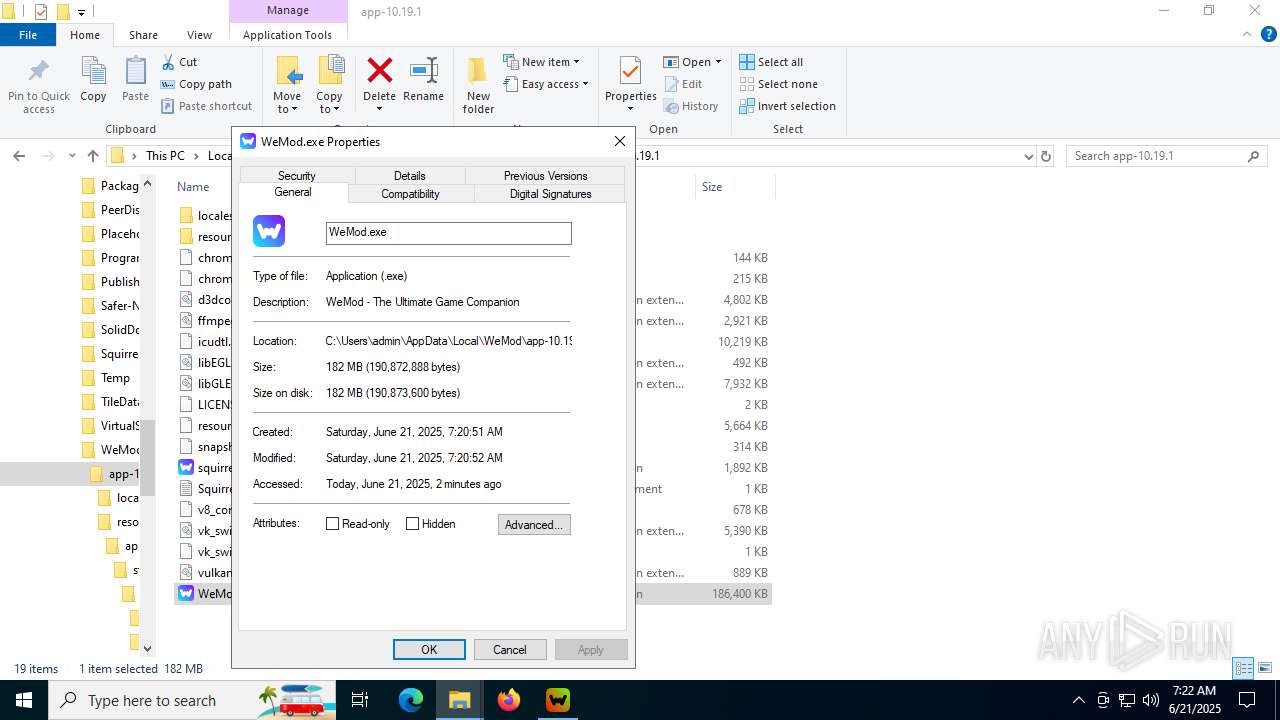
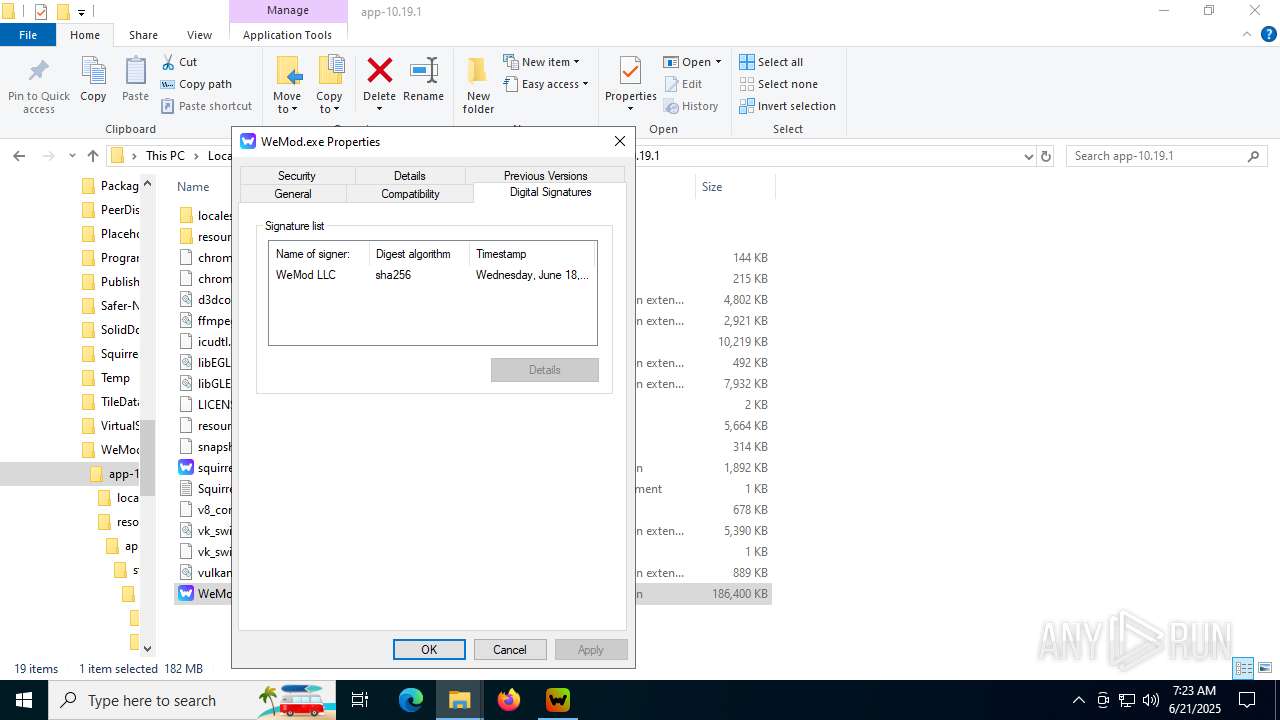
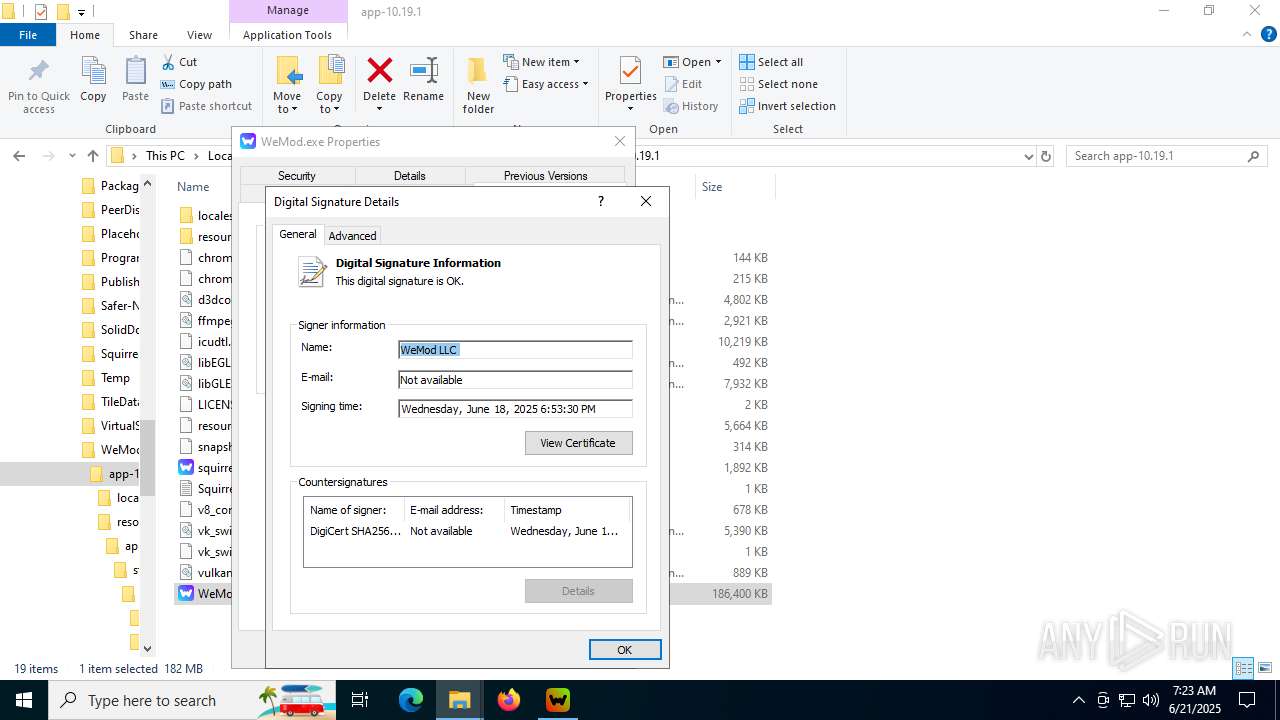
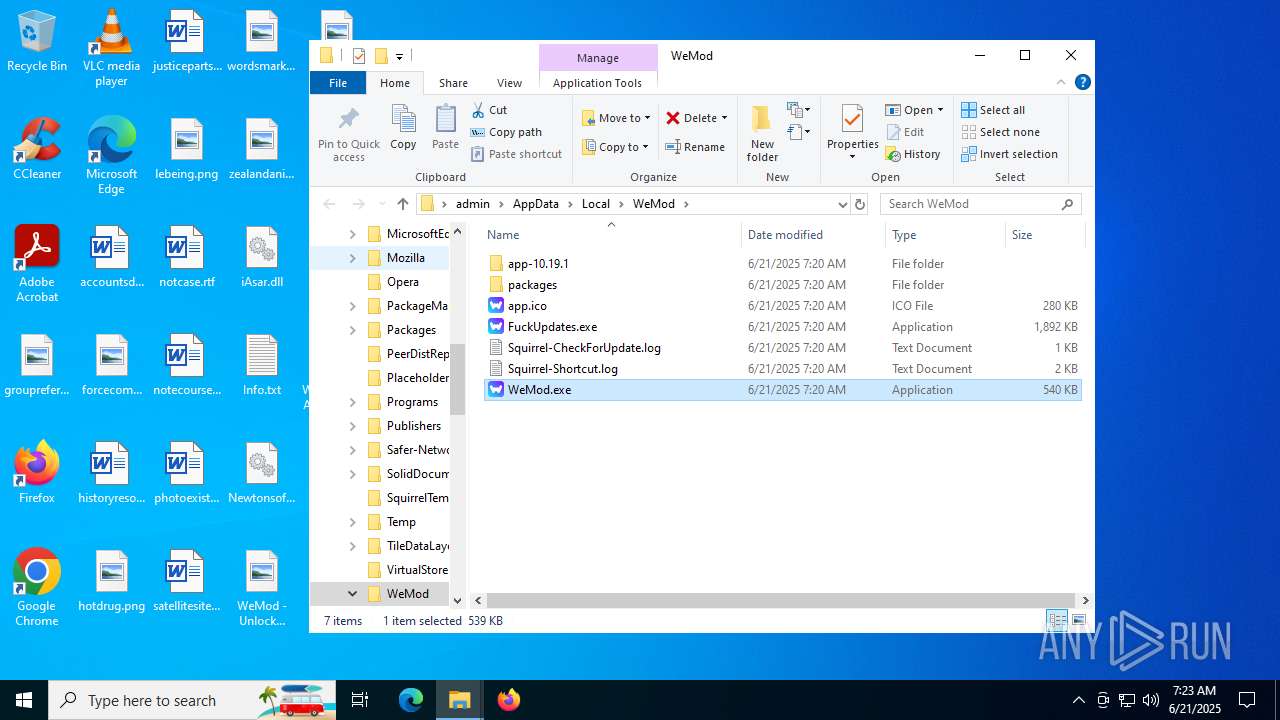
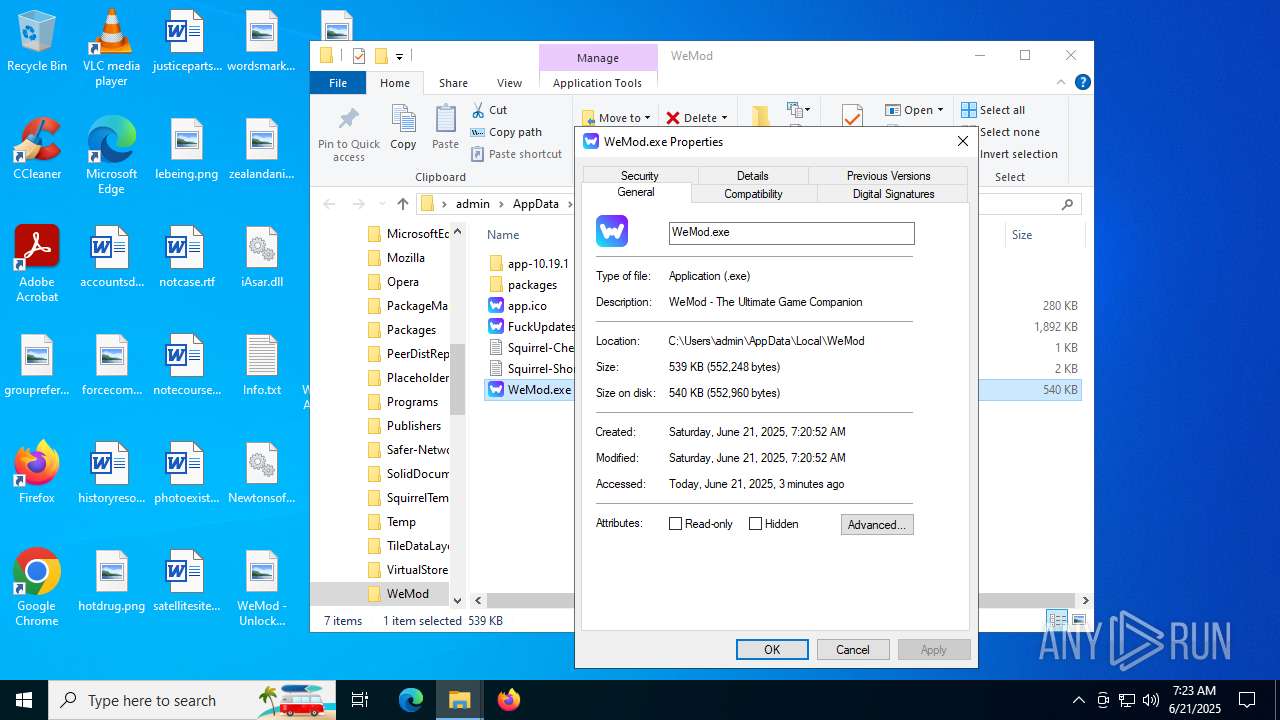
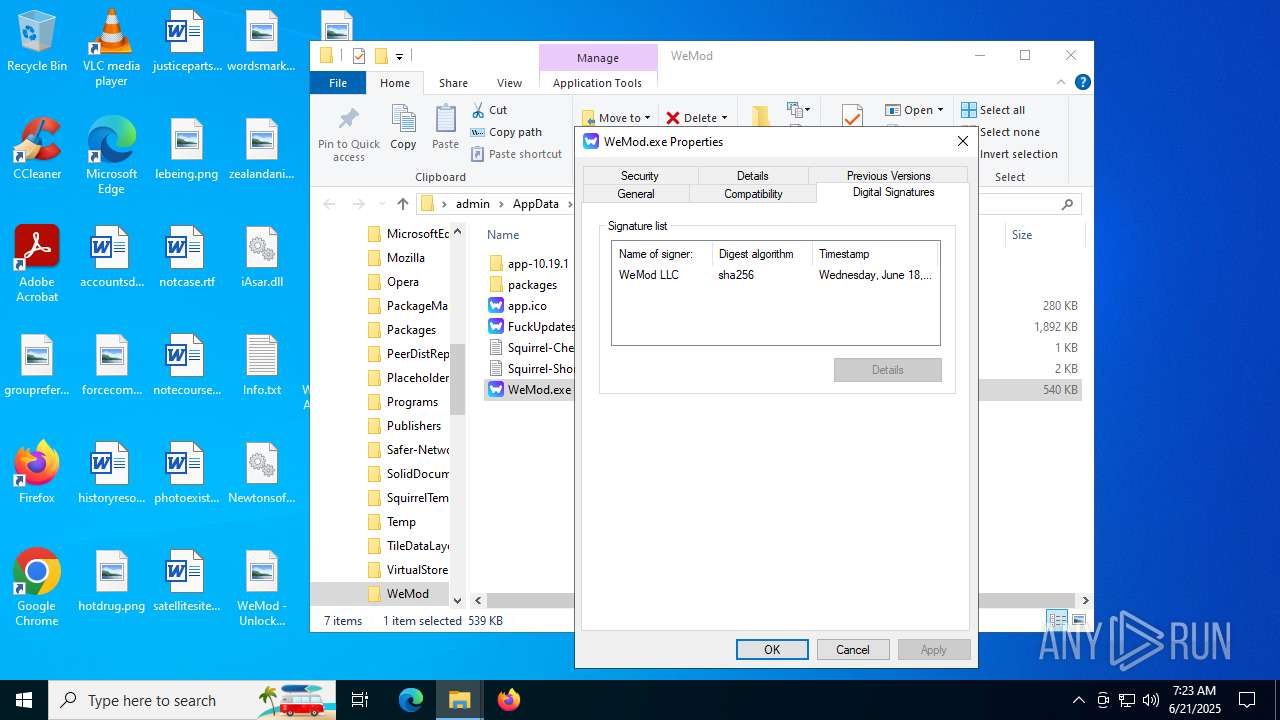
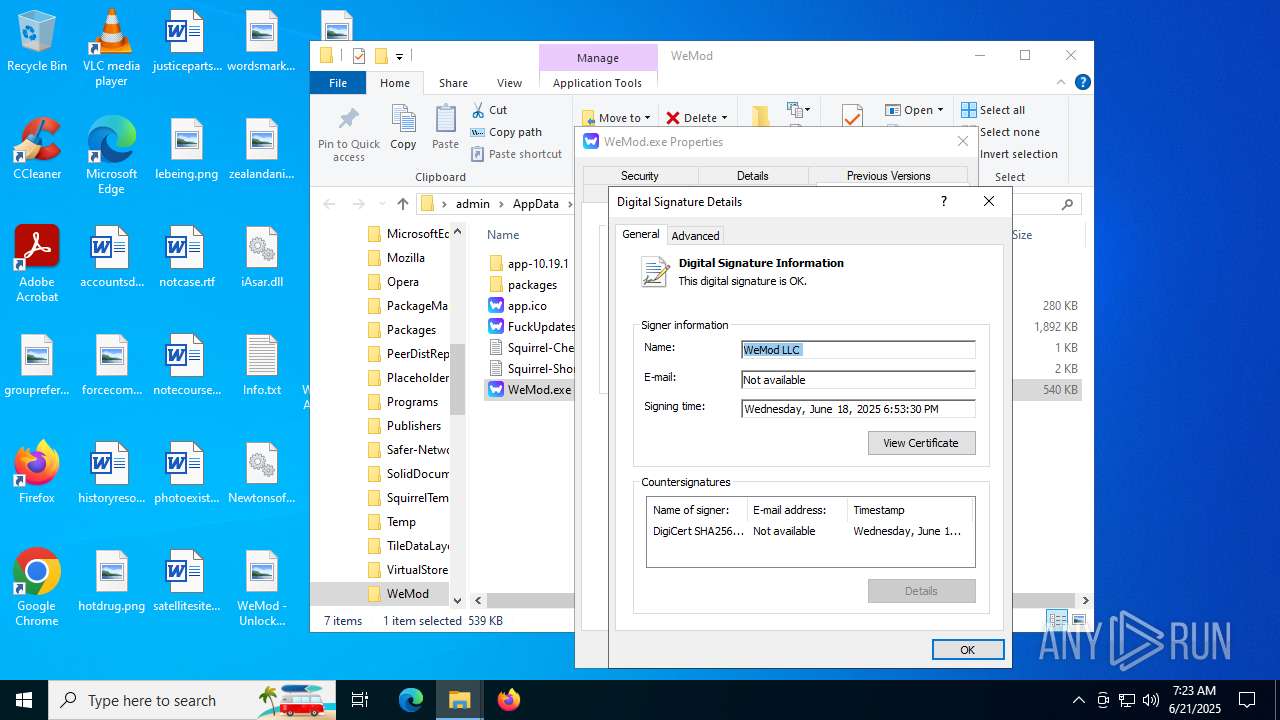
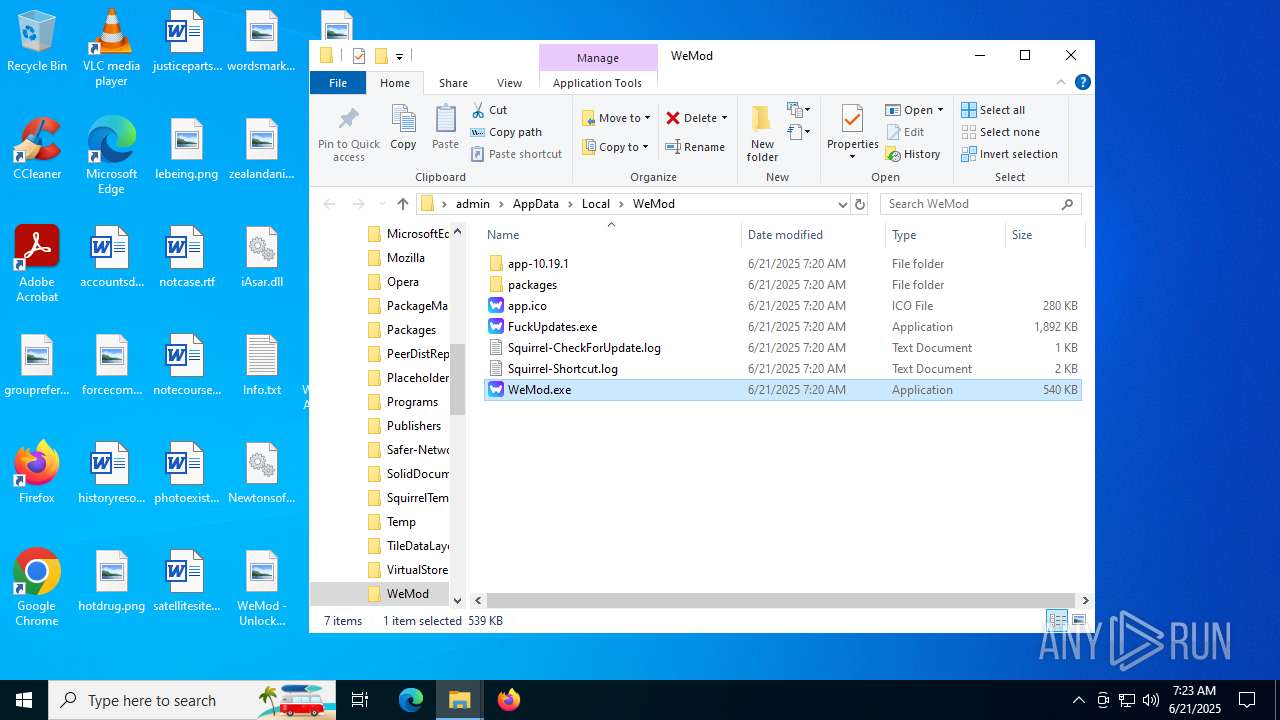
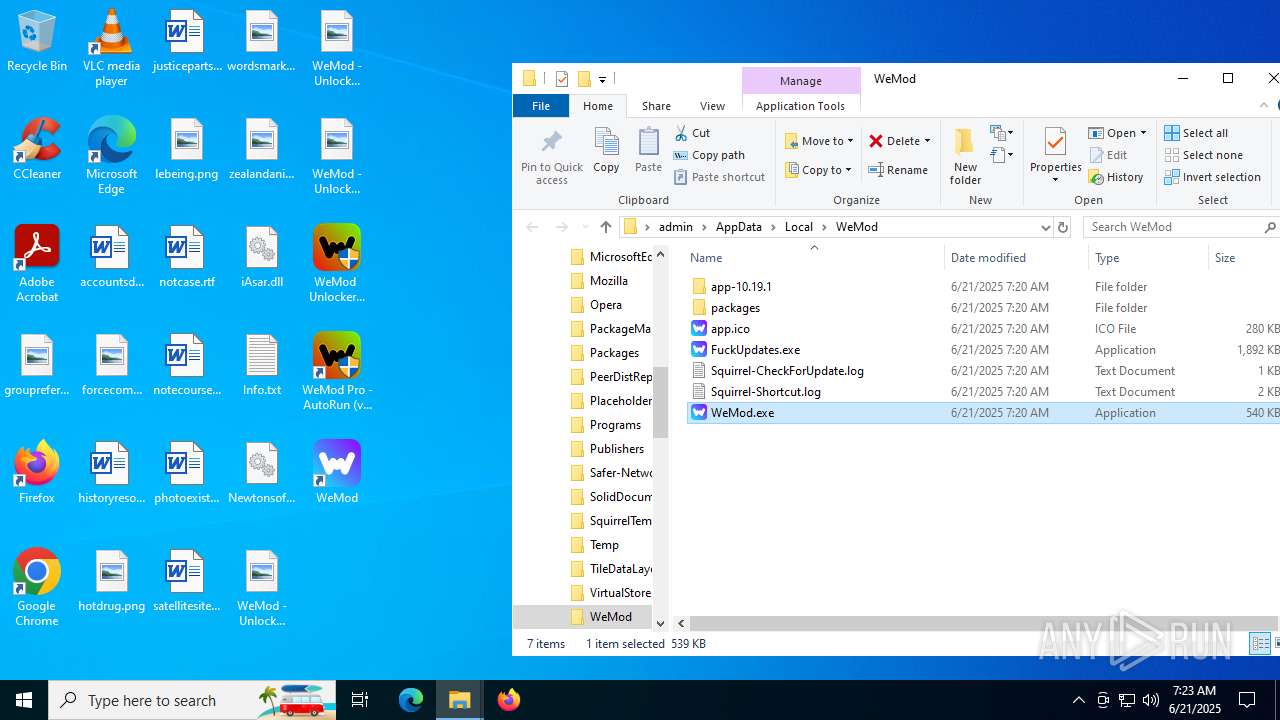
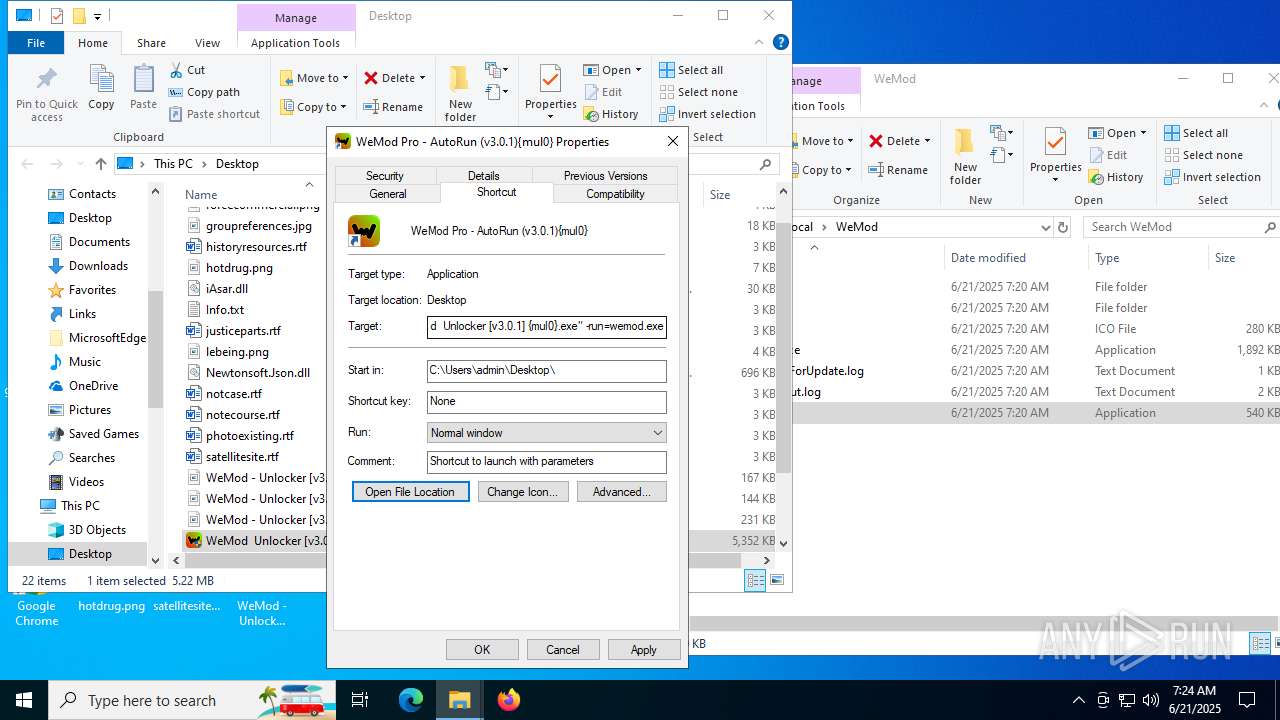
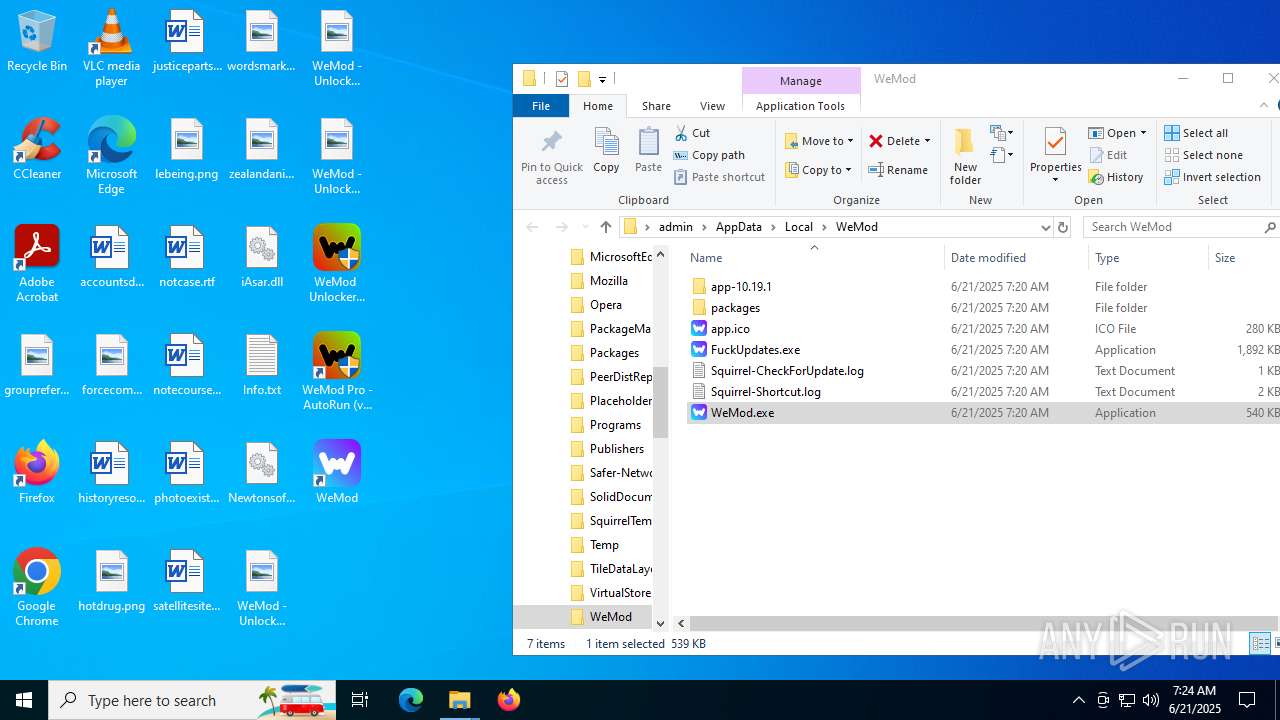
| File name: | WeMod_Pro_-_Unlocker_v3.0.1_mul0.zip |
| Full analysis: | https://app.any.run/tasks/d73d2154-24eb-4a8d-8f01-56a7cd872353 |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2025, 07:19:45 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 5C37F8E0120FA3C4D84AE3A567EFBC8C |
| SHA1: | 35E221969743A0A7761690E2851CED8A15104893 |
| SHA256: | A2C1B5CEE789D699352A25B4EC30EC52C55639D61E44FC770C76DEABD4E4032A |
| SSDEEP: | 98304:BqQrjpYLfVoHvPNjOJCYGMe8ly1VjjQjIfbhbF86h1GbPf6qqj4KHoejWuIiKDQq:BB15Lyav7deVTrqu |
MALICIOUS
No malicious indicators.SUSPICIOUS
Generic archive extractor
- WinRAR.exe (PID: 1604)
Reads the date of Windows installation
- WeMod Unlocker [v3.0.1] {mul0}.exe (PID: 6776)
- Update.exe (PID: 6772)
- WeMod Unlocker [v3.0.1] {mul0}.exe (PID: 4580)
Reads security settings of Internet Explorer
- WeMod Unlocker [v3.0.1] {mul0}.exe (PID: 6776)
- RegAsm.exe (PID: 6732)
- Update.exe (PID: 6772)
- WeModAuxiliaryService.exe (PID: 5560)
- WeMod Unlocker [v3.0.1] {mul0}.exe (PID: 4580)
- RegAsm.exe (PID: 7008)
- WeModAuxiliaryService.exe (PID: 3832)
Creates/Modifies COM task schedule object
- RegAsm.exe (PID: 6732)
- RegAsm.exe (PID: 7008)
Executable content was dropped or overwritten
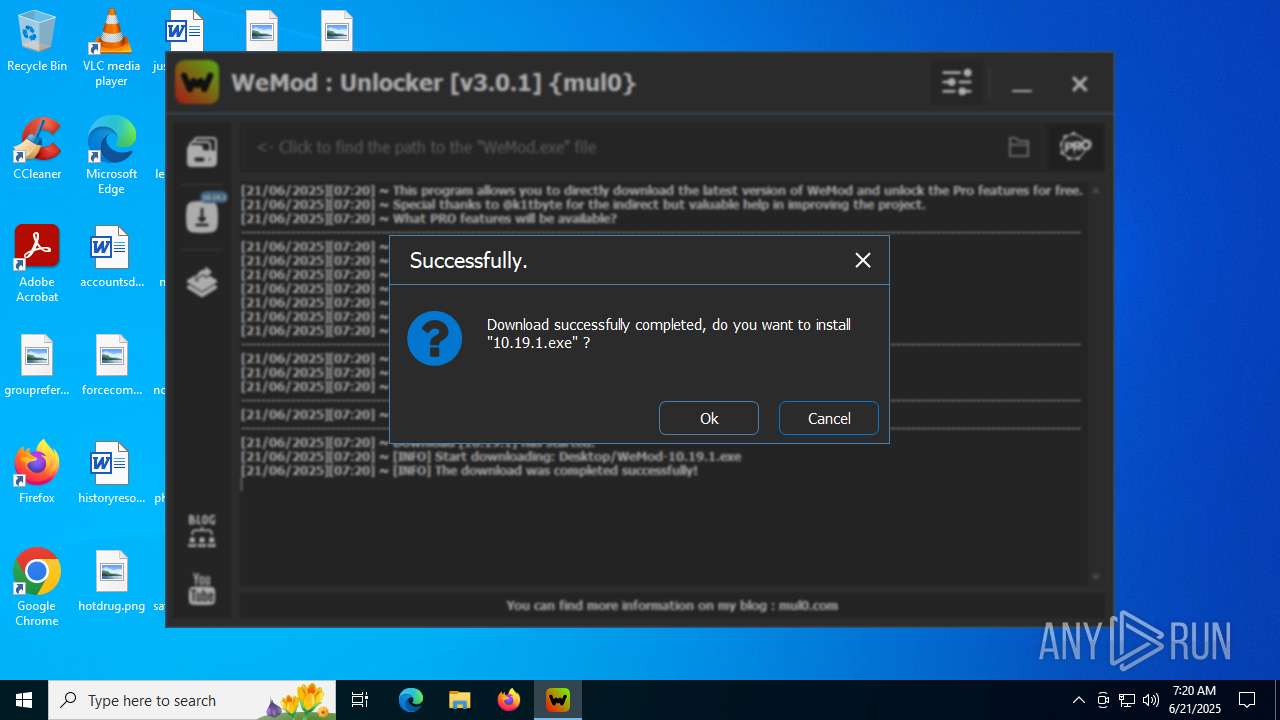
- WeMod-10.19.1.exe (PID: 1136)
- Update.exe (PID: 6772)
- WeMod Unlocker [v3.0.1] {mul0}.exe (PID: 6776)
Process drops legitimate windows executable
- Update.exe (PID: 6772)
Application launched itself
- WeMod.exe (PID: 1332)
- WeMod.exe (PID: 1180)
- WeMod.exe (PID: 760)
- WeMod.exe (PID: 3400)
Searches for installed software
- Update.exe (PID: 6772)
Creates a software uninstall entry
- Update.exe (PID: 6772)
The process checks if it is being run in the virtual environment
- WeMod Unlocker [v3.0.1] {mul0}.exe (PID: 6776)
INFO
Manual execution by a user
- WeMod Unlocker [v3.0.1] {mul0}.exe (PID: 6776)
- WeMod Unlocker [v3.0.1] {mul0}.exe (PID: 3672)
- WeMod-10.19.1.exe (PID: 1136)
- WeMod.exe (PID: 5612)
- WeMod.exe (PID: 4172)
- WeMod Unlocker [v3.0.1] {mul0}.exe (PID: 4580)
- WeMod Unlocker [v3.0.1] {mul0}.exe (PID: 856)
The sample compiled with english language support
- WinRAR.exe (PID: 1604)
- Update.exe (PID: 6772)
- WeMod Unlocker [v3.0.1] {mul0}.exe (PID: 6776)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1604)
Reads product name
- WeMod Unlocker [v3.0.1] {mul0}.exe (PID: 6776)
- WeMod.exe (PID: 4968)
- WeMod.exe (PID: 760)
- WeMod.exe (PID: 1180)
- WeMod.exe (PID: 3400)
- WeMod Unlocker [v3.0.1] {mul0}.exe (PID: 4580)
Checks supported languages
- WeMod Unlocker [v3.0.1] {mul0}.exe (PID: 6776)
- RegAsm.exe (PID: 6732)
- Update.exe (PID: 6772)
- WeMod-10.19.1.exe (PID: 6840)
- WeMod-10.19.1.exe (PID: 1136)
- squirrel.exe (PID: 5012)
- Update.exe (PID: 3732)
- WeMod.exe (PID: 760)
- WeMod.exe (PID: 4968)
- WeMod.exe (PID: 1332)
- WeMod.exe (PID: 1180)
- WeMod.exe (PID: 6980)
- WeMod.exe (PID: 2148)
- Update.exe (PID: 1660)
- WeModAuxiliaryService.exe (PID: 5560)
- WeMod.exe (PID: 1080)
- SearchApp.exe (PID: 5328)
- WeMod.exe (PID: 5612)
- WeMod.exe (PID: 4172)
- WeMod.exe (PID: 6336)
- WeMod Unlocker [v3.0.1] {mul0}.exe (PID: 4580)
- RegAsm.exe (PID: 7008)
- WeMod.exe (PID: 7152)
- WeMod.exe (PID: 3980)
- WeMod.exe (PID: 5724)
- WeModAuxiliaryService.exe (PID: 3832)
- WeMod.exe (PID: 3400)
Reads the computer name
- WeMod Unlocker [v3.0.1] {mul0}.exe (PID: 6776)
- RegAsm.exe (PID: 6732)
- WeMod-10.19.1.exe (PID: 6840)
- Update.exe (PID: 6772)
- squirrel.exe (PID: 5012)
- Update.exe (PID: 3732)
- WeMod.exe (PID: 1180)
- WeMod.exe (PID: 6980)
- WeMod.exe (PID: 2148)
- Update.exe (PID: 1660)
- WeModAuxiliaryService.exe (PID: 5560)
- WeMod Unlocker [v3.0.1] {mul0}.exe (PID: 4580)
- RegAsm.exe (PID: 7008)
- WeMod.exe (PID: 3400)
- WeMod.exe (PID: 7152)
- WeMod.exe (PID: 3980)
- WeModAuxiliaryService.exe (PID: 3832)
Reads Microsoft Office registry keys
- WeMod Unlocker [v3.0.1] {mul0}.exe (PID: 6776)
- WeMod Unlocker [v3.0.1] {mul0}.exe (PID: 4580)
Create files in a temporary directory
- WeMod Unlocker [v3.0.1] {mul0}.exe (PID: 6776)
- Update.exe (PID: 6772)
- WeMod.exe (PID: 1180)
- Update.exe (PID: 1660)
- WeMod Unlocker [v3.0.1] {mul0}.exe (PID: 4580)
- WeMod.exe (PID: 3400)
Creates files or folders in the user directory
- WeMod Unlocker [v3.0.1] {mul0}.exe (PID: 6776)
- WeMod-10.19.1.exe (PID: 1136)
- Update.exe (PID: 6772)
- Update.exe (PID: 3732)
- squirrel.exe (PID: 5012)
- WeMod.exe (PID: 1180)
- WeMod.exe (PID: 2148)
- Update.exe (PID: 1660)
- WeModAuxiliaryService.exe (PID: 5560)
- WeMod Unlocker [v3.0.1] {mul0}.exe (PID: 4580)
- WeMod.exe (PID: 3400)
- WeMod.exe (PID: 3980)
Reads Environment values
- WeMod Unlocker [v3.0.1] {mul0}.exe (PID: 6776)
- WeMod.exe (PID: 4968)
- WeMod.exe (PID: 760)
- WeMod.exe (PID: 1180)
- Update.exe (PID: 6772)
- Update.exe (PID: 1660)
- WeMod Unlocker [v3.0.1] {mul0}.exe (PID: 4580)
- WeMod.exe (PID: 3400)
Checks proxy server information
- WeMod Unlocker [v3.0.1] {mul0}.exe (PID: 6776)
- WeMod.exe (PID: 1180)
- Update.exe (PID: 6772)
- Update.exe (PID: 1660)
- WeModAuxiliaryService.exe (PID: 5560)
- slui.exe (PID: 3800)
- WeMod Unlocker [v3.0.1] {mul0}.exe (PID: 4580)
- WeMod.exe (PID: 3400)
Reads the software policy settings
- WeMod Unlocker [v3.0.1] {mul0}.exe (PID: 6776)
- Update.exe (PID: 6772)
- Update.exe (PID: 1660)
- WeModAuxiliaryService.exe (PID: 5560)
- slui.exe (PID: 3800)
- SearchApp.exe (PID: 5328)
- WeMod Unlocker [v3.0.1] {mul0}.exe (PID: 4580)
- WeModAuxiliaryService.exe (PID: 3832)
Process checks computer location settings
- WeMod Unlocker [v3.0.1] {mul0}.exe (PID: 6776)
- Update.exe (PID: 6772)
- WeMod.exe (PID: 1180)
- WeMod.exe (PID: 1080)
- SearchApp.exe (PID: 5328)
- WeMod Unlocker [v3.0.1] {mul0}.exe (PID: 4580)
- WeMod.exe (PID: 5724)
- WeMod.exe (PID: 3400)
UPX packer has been detected
- WeMod Unlocker [v3.0.1] {mul0}.exe (PID: 6776)
Compiled with Borland Delphi (YARA)
- WeMod Unlocker [v3.0.1] {mul0}.exe (PID: 6776)
- slui.exe (PID: 3800)
Reads the machine GUID from the registry
- Update.exe (PID: 6772)
- RegAsm.exe (PID: 6732)
- squirrel.exe (PID: 5012)
- Update.exe (PID: 3732)
- WeMod.exe (PID: 1180)
- Update.exe (PID: 1660)
- WeModAuxiliaryService.exe (PID: 5560)
- SearchApp.exe (PID: 5328)
- WeMod Unlocker [v3.0.1] {mul0}.exe (PID: 6776)
- RegAsm.exe (PID: 7008)
- WeMod.exe (PID: 3400)
- WeModAuxiliaryService.exe (PID: 3832)
Disables trace logs
- Update.exe (PID: 6772)
- Update.exe (PID: 1660)
Reads CPU info
- WeMod.exe (PID: 1180)
- WeMod.exe (PID: 3400)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0808 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:06:21 08:40:26 |
| ZipCRC: | 0xb9d793cd |
| ZipCompressedSize: | 14707 |
| ZipUncompressedSize: | 30208 |
| ZipFileName: | iAsar.dll |
Total processes
179
Monitored processes
34
Malicious processes
6
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
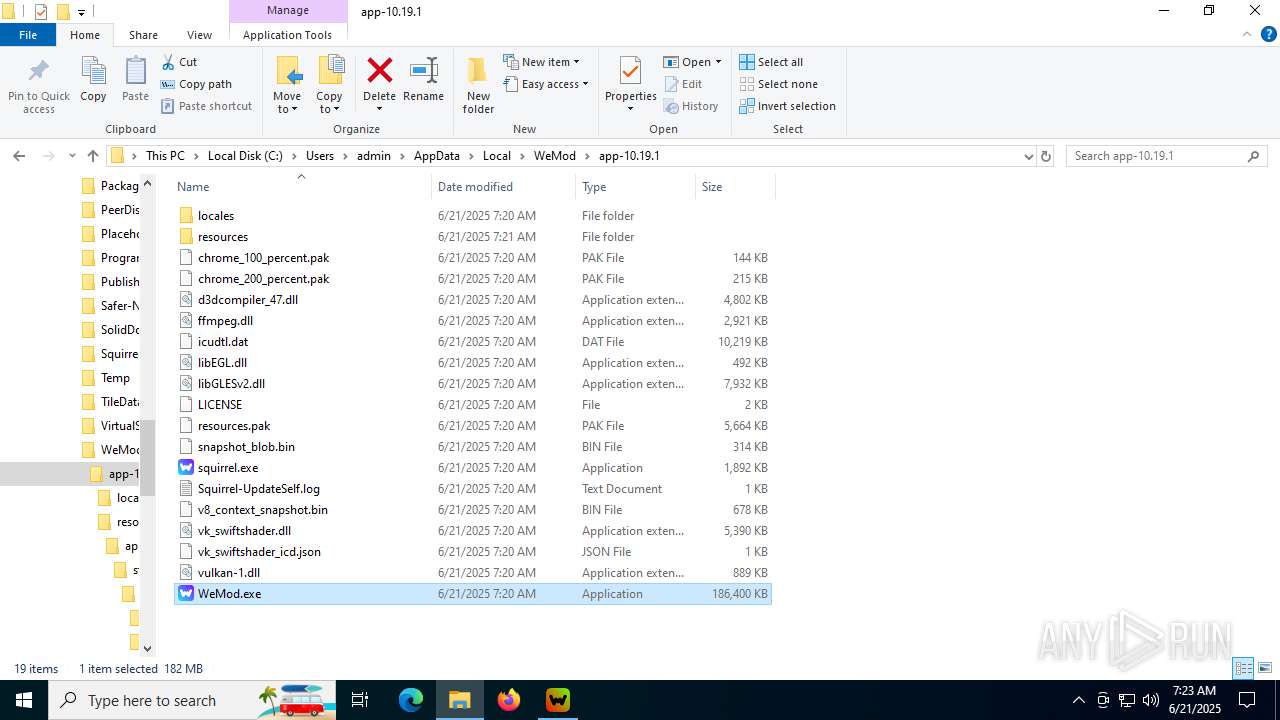
| 760 | "C:\Users\admin\AppData\Local\WeMod\app-10.19.1\WeMod.exe" --squirrel-firstrun | C:\Users\admin\AppData\Local\WeMod\app-10.19.1\WeMod.exe | — | Update.exe | |||||||||||
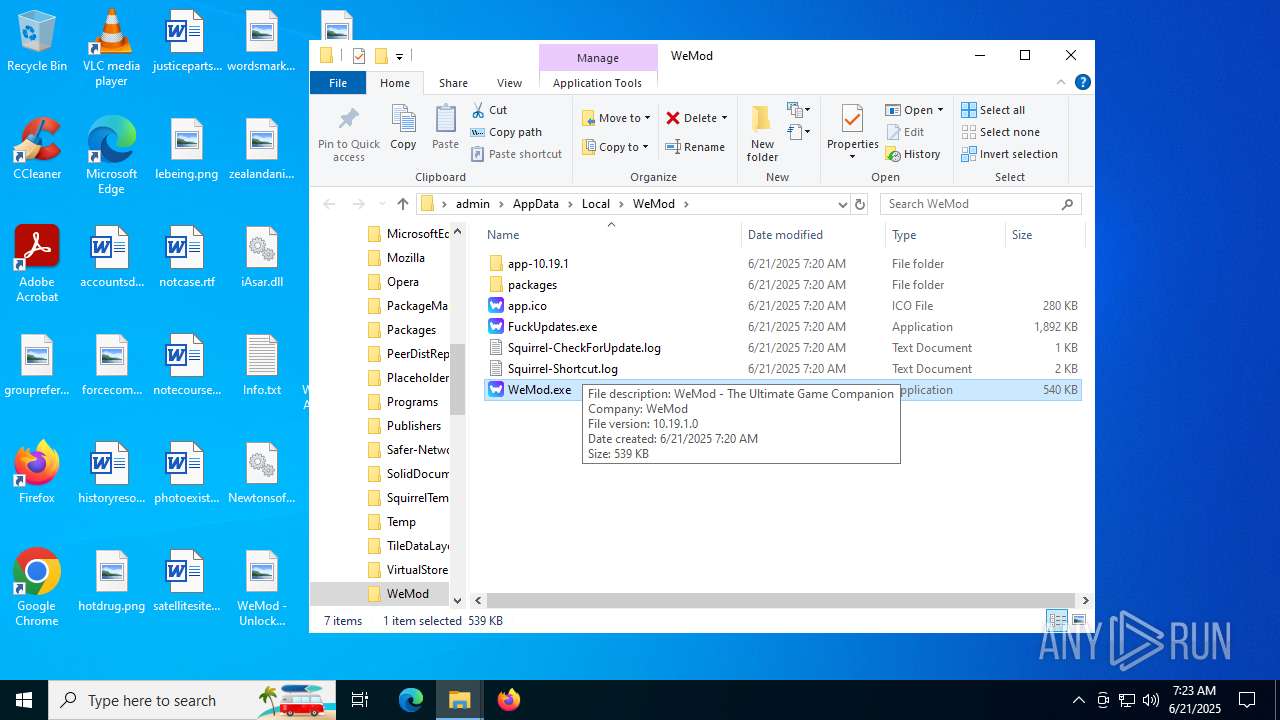
User: admin Company: WeMod Integrity Level: MEDIUM Description: WeMod - The Ultimate Game Companion Exit code: 0 Version: 10.19.1 Modules
| |||||||||||||||
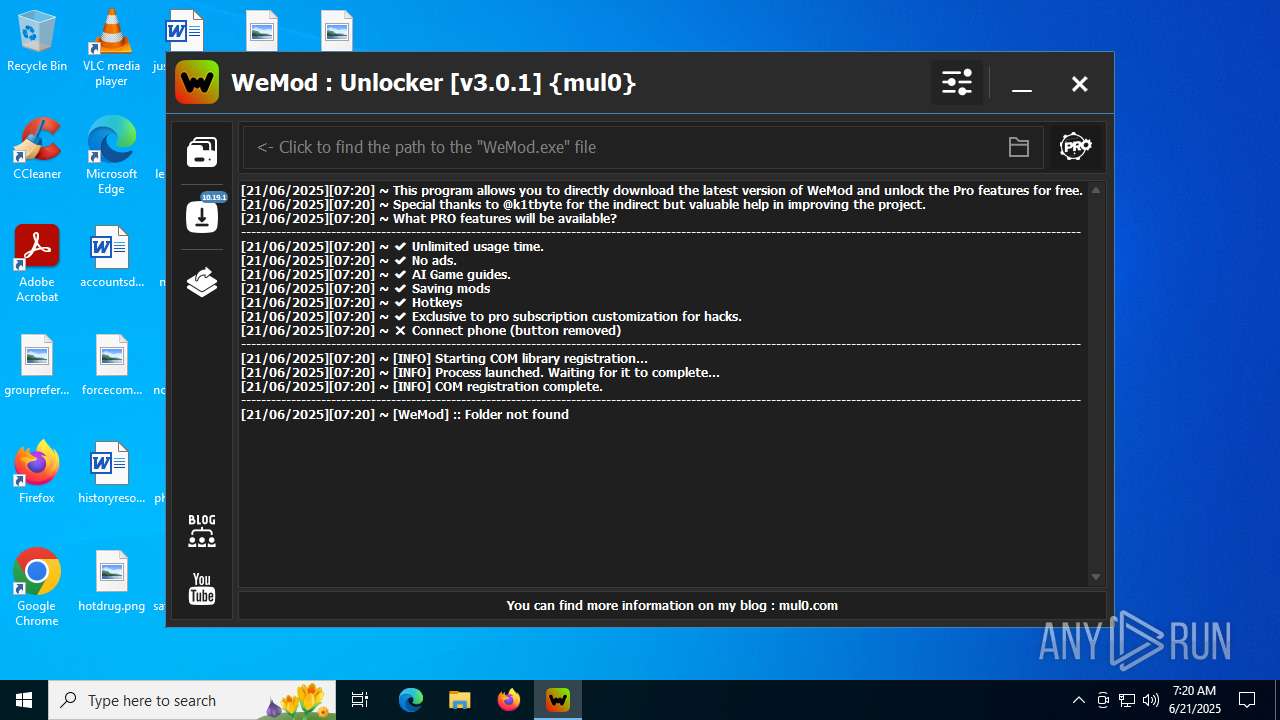
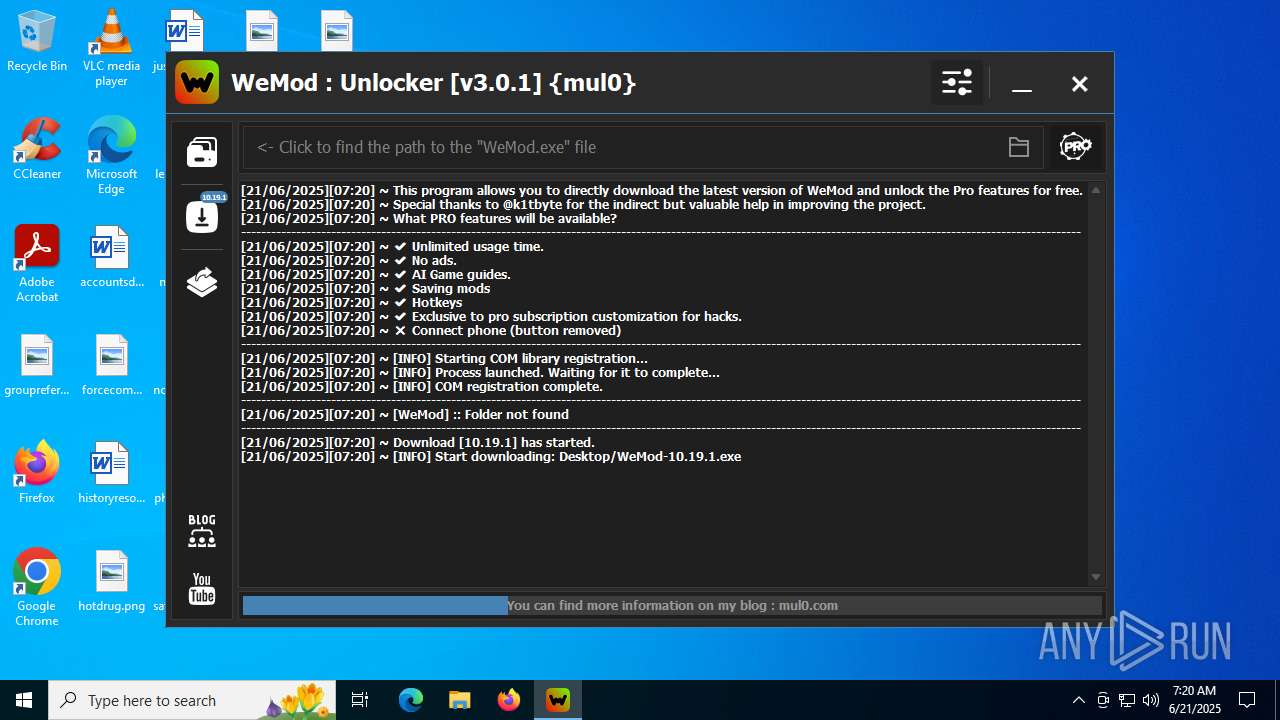
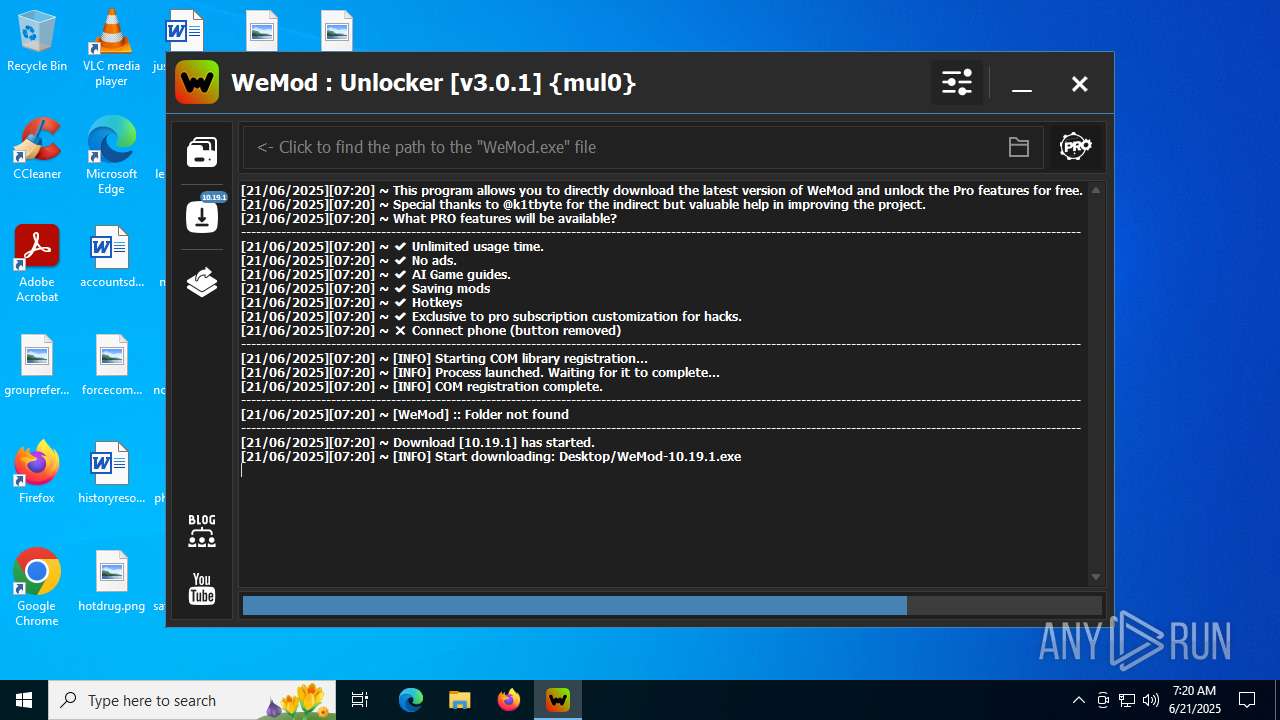
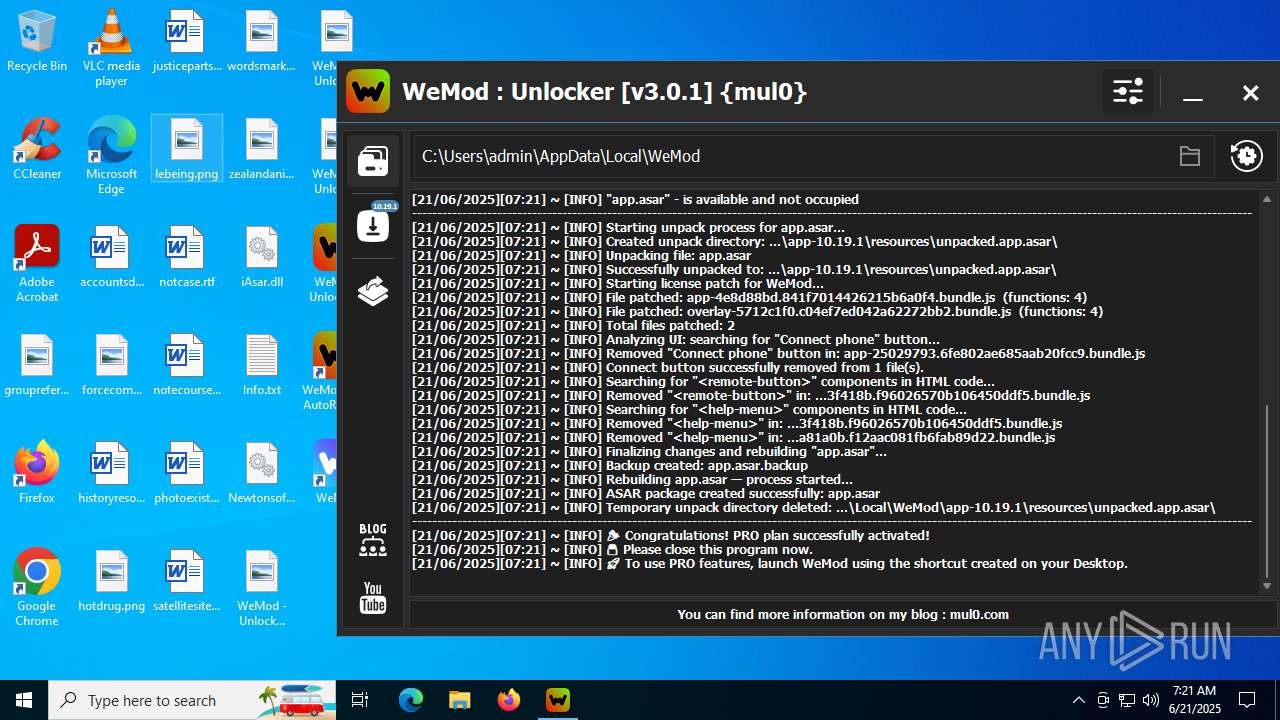
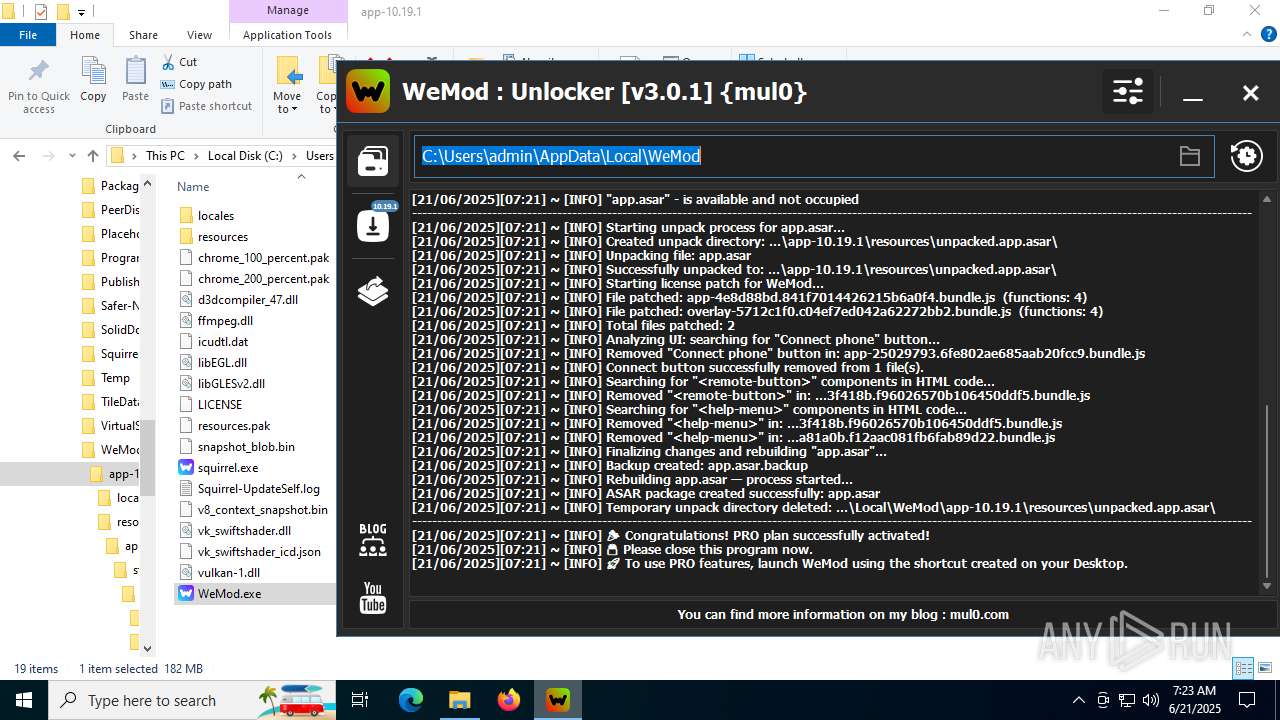
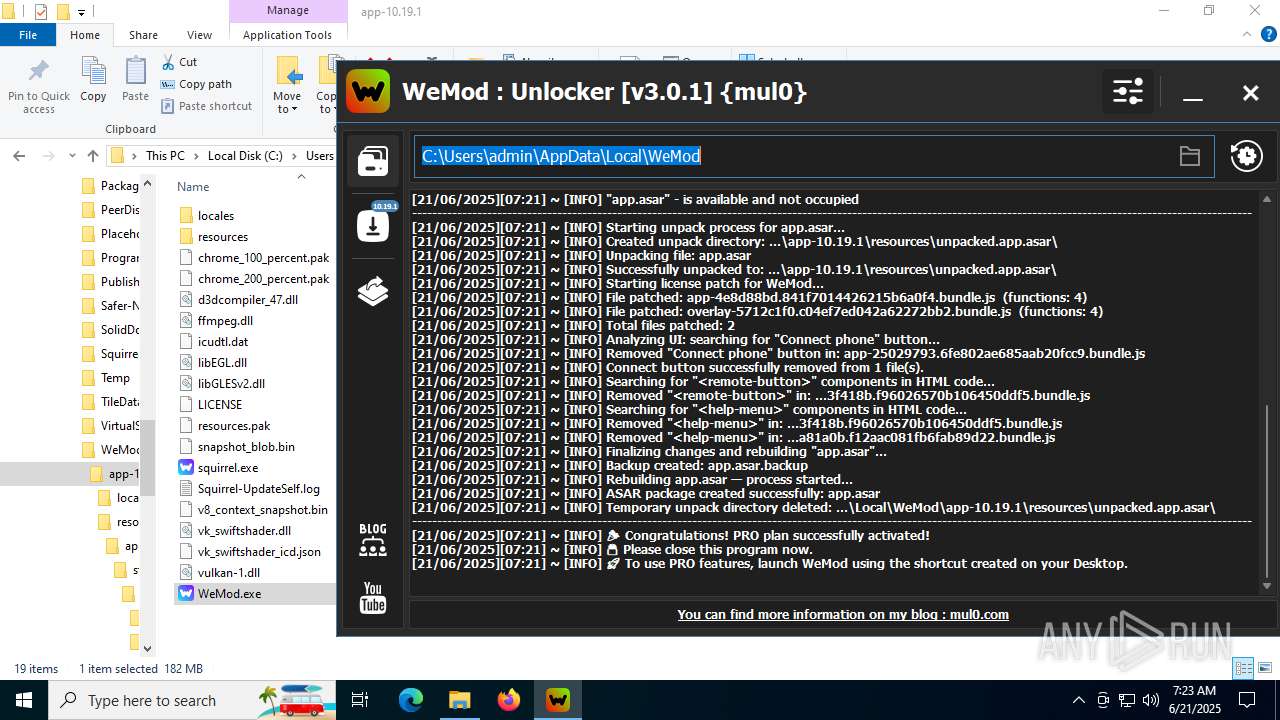
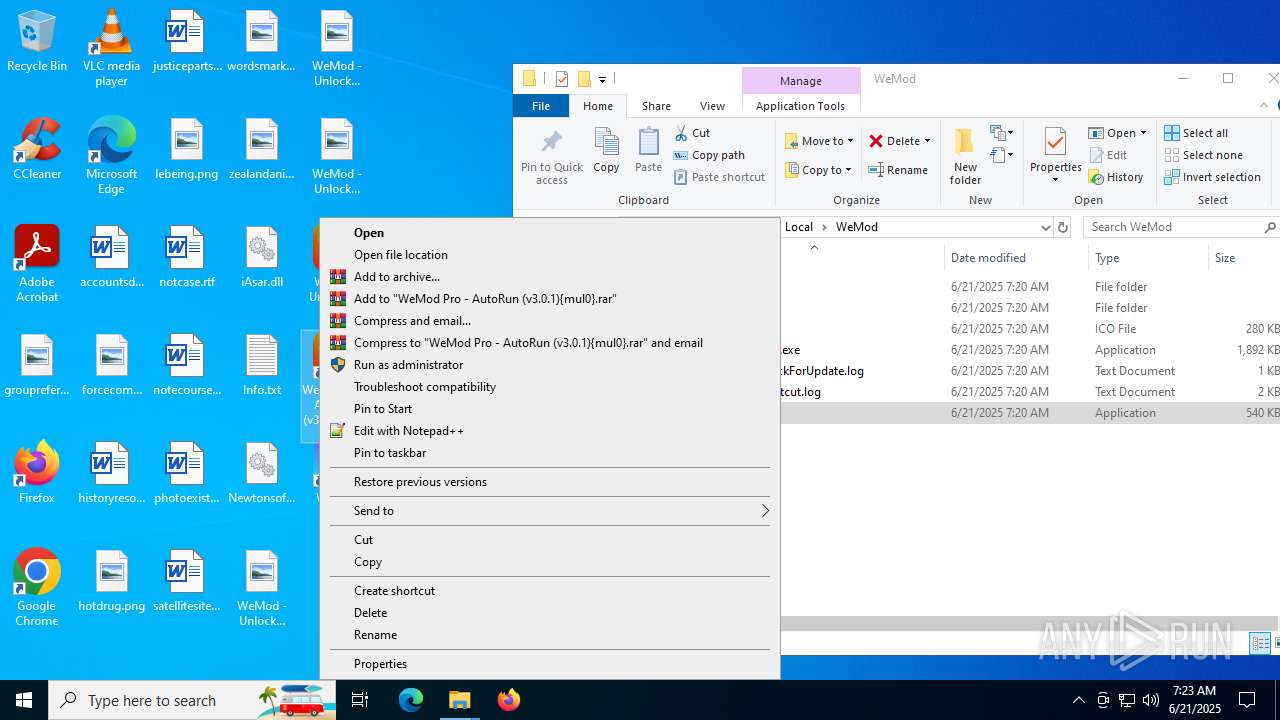
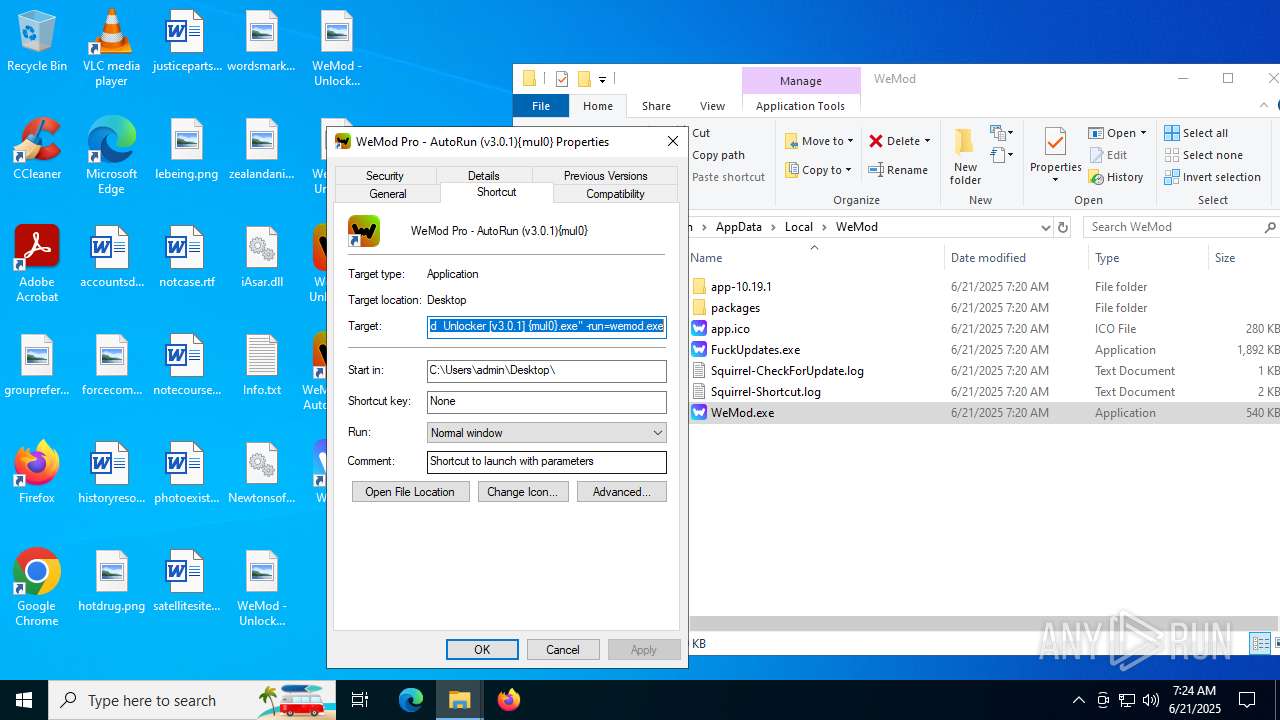
| 856 | "C:\Users\admin\Desktop\WeMod Unlocker [v3.0.1] {mul0}.exe" -run=wemod.exe | C:\Users\admin\Desktop\WeMod Unlocker [v3.0.1] {mul0}.exe | — | explorer.exe | |||||||||||
User: admin Company: mul0 Integrity Level: MEDIUM Description: WeMod : Unlocker [v3.0.1] {mul0} Exit code: 3221226540 Version: 3.0.1.51 Modules
| |||||||||||||||
| 1068 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1080 | "C:\Users\admin\AppData\Local\WeMod\app-10.19.1\WeMod.exe" --type=renderer --user-data-dir="C:\Users\admin\AppData\Roaming\WeMod" --app-user-model-id=com.squirrel.WeMod.WeMod --app-path="C:\Users\admin\AppData\Local\WeMod\app-10.19.1\resources\app.asar" --no-sandbox --no-zygote --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=4 --field-trial-handle=2532,i,2390660475506407798,11009775550871908919,262144 --disable-features=SpareRendererForSitePerProcess,WinDelaySpellcheckServiceInit,WinRetrieveSuggestionsOnlyOnDemand --variations-seed-version --mojo-platform-channel-handle=2528 /prefetch:1 | C:\Users\admin\AppData\Local\WeMod\app-10.19.1\WeMod.exe | — | WeMod.exe | |||||||||||
User: admin Company: WeMod Integrity Level: MEDIUM Description: WeMod - The Ultimate Game Companion Exit code: 0 Version: 10.19.1 Modules
| |||||||||||||||
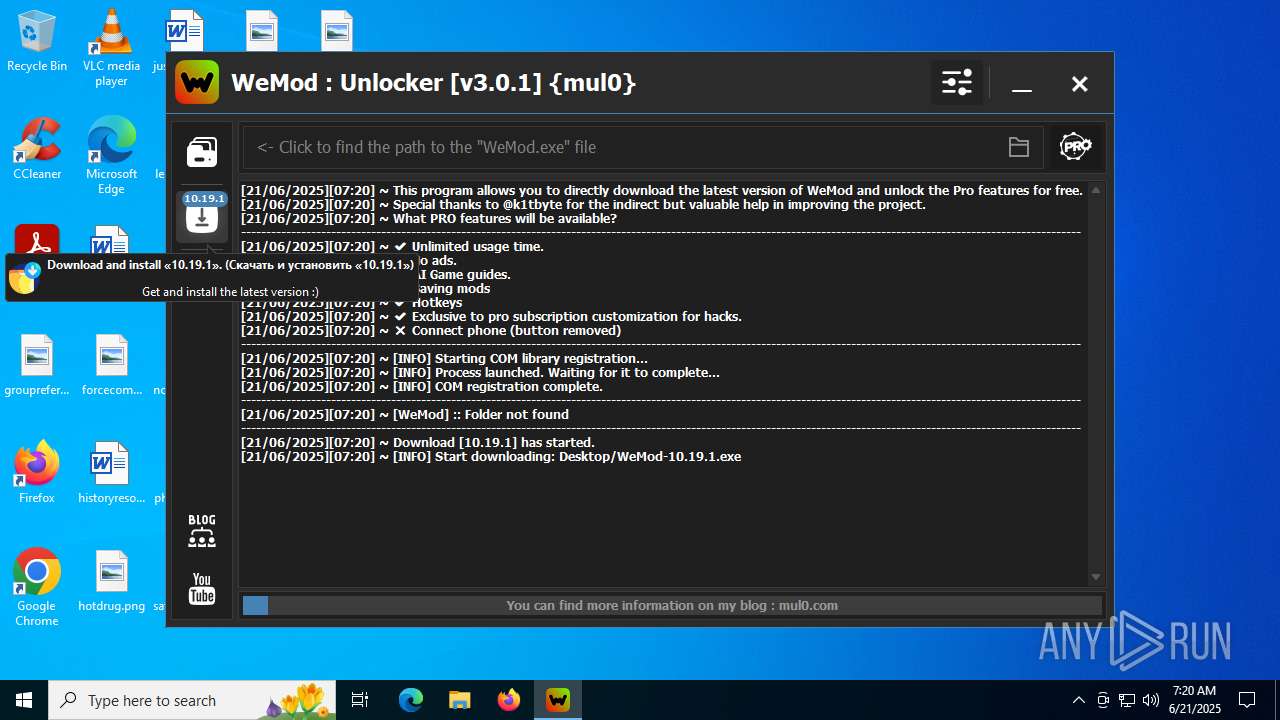
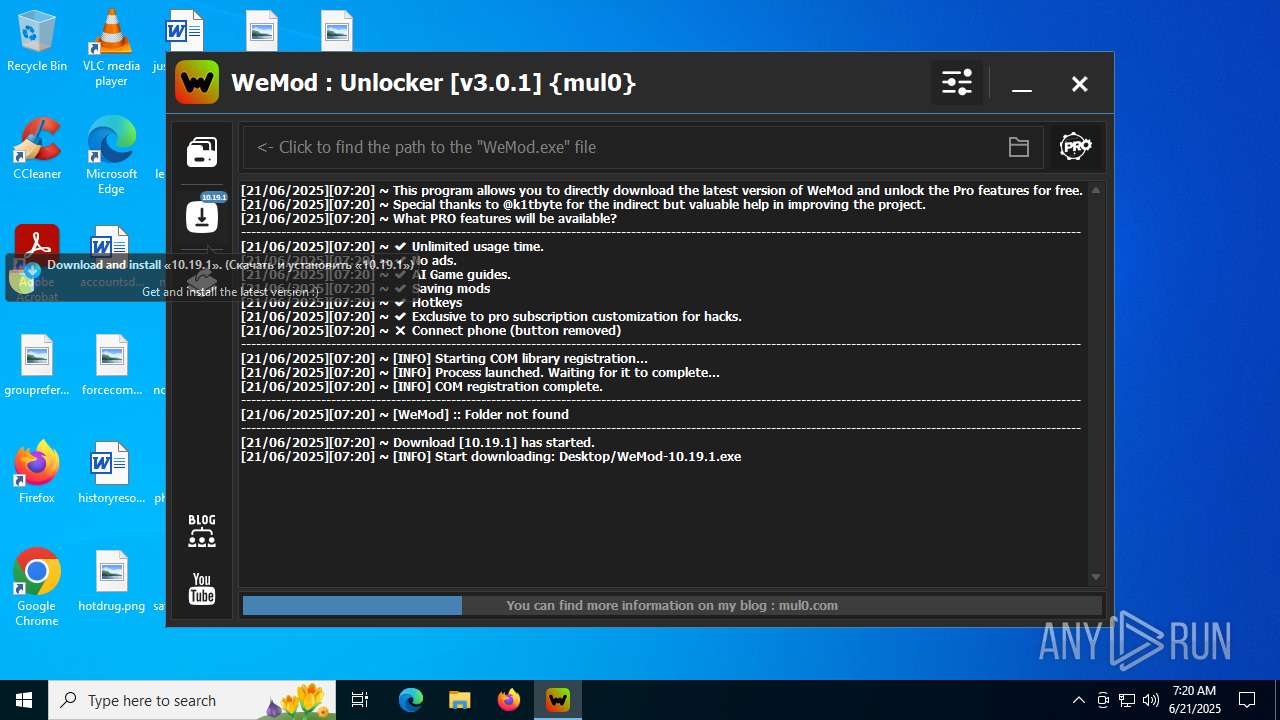
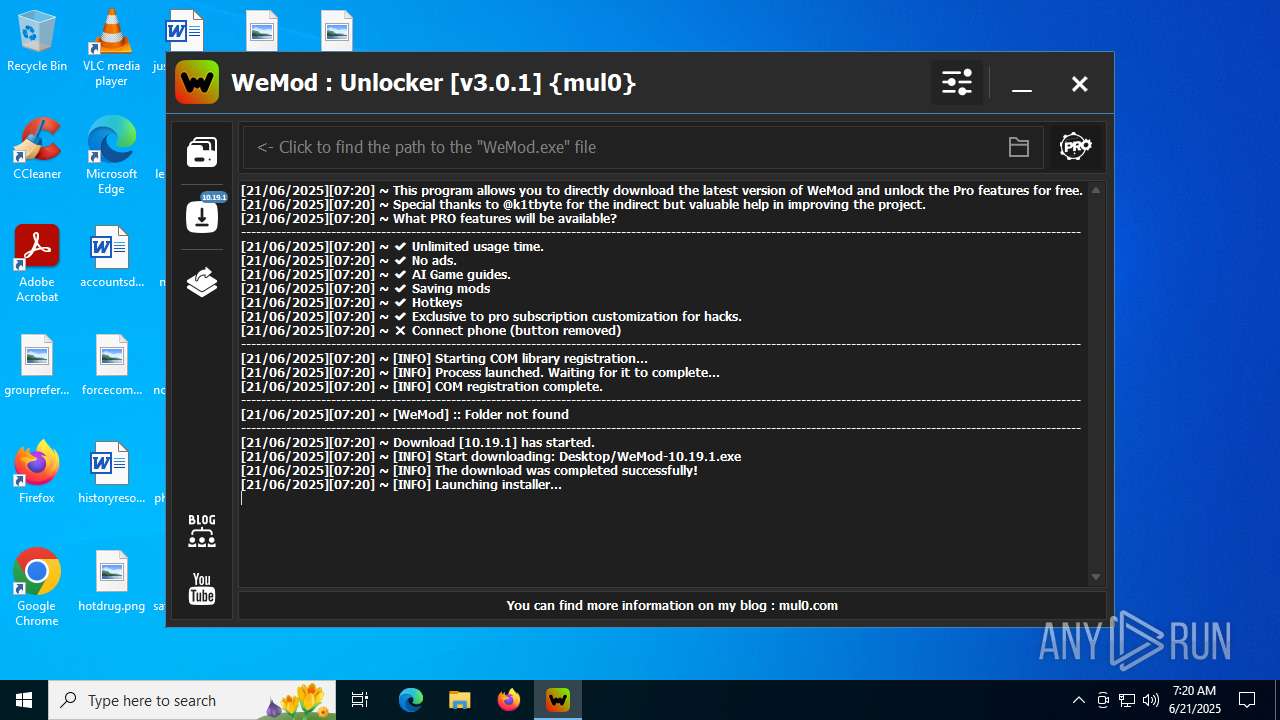
| 1136 | "C:\Users\admin\Desktop\WeMod-10.19.1.exe" --rerunningWithoutUAC | C:\Users\admin\Desktop\WeMod-10.19.1.exe | explorer.exe | ||||||||||||
User: admin Company: WeMod Integrity Level: MEDIUM Description: WeMod - The Ultimate Gaming Companion Exit code: 0 Version: 10.19.1 Modules
| |||||||||||||||
| 1180 | "C:\Users\admin\AppData\Local\WeMod\app-10.19.1\WeMod.exe" | C:\Users\admin\AppData\Local\WeMod\app-10.19.1\WeMod.exe | — | WeMod.exe | |||||||||||
User: admin Company: WeMod Integrity Level: MEDIUM Description: WeMod - The Ultimate Game Companion Exit code: 0 Version: 10.19.1 Modules
| |||||||||||||||
| 1332 | "C:\Users\admin\AppData\Local\WeMod\app-10.19.1\WeMod.exe" --type=relauncher --no-sandbox --- "C:\Users\admin\AppData\Local\WeMod\app-10.19.1\WeMod.exe" | C:\Users\admin\AppData\Local\WeMod\app-10.19.1\WeMod.exe | — | WeMod.exe | |||||||||||
User: admin Company: WeMod Integrity Level: MEDIUM Description: WeMod - The Ultimate Game Companion Exit code: 0 Version: 10.19.1 Modules
| |||||||||||||||
| 1604 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\WeMod_Pro_-_Unlocker_v3.0.1_mul0.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1660 | C:\Users\admin\AppData\Local\WeMod\Update.exe --checkForUpdate https://api.wemod.com/client/channels/stable?osVersion=10.0.19045 | C:\Users\admin\AppData\Local\WeMod\Update.exe | WeMod.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2148 | "C:\Users\admin\AppData\Local\WeMod\app-10.19.1\WeMod.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --force-ui-direction=ltr --user-data-dir="C:\Users\admin\AppData\Roaming\WeMod" --field-trial-handle=2292,i,2390660475506407798,11009775550871908919,262144 --disable-features=SpareRendererForSitePerProcess,WinDelaySpellcheckServiceInit,WinRetrieveSuggestionsOnlyOnDemand --variations-seed-version --mojo-platform-channel-handle=2288 /prefetch:3 | C:\Users\admin\AppData\Local\WeMod\app-10.19.1\WeMod.exe | WeMod.exe | ||||||||||||
User: admin Company: WeMod Integrity Level: MEDIUM Description: WeMod - The Ultimate Game Companion Exit code: 0 Version: 10.19.1 Modules
| |||||||||||||||
Total events
26 584
Read events
26 178
Write events
353
Delete events
53
Modification events
| (PID) Process: | (1604) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (1604) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (1604) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (1604) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\WeMod_Pro_-_Unlocker_v3.0.1_mul0.zip | |||
| (PID) Process: | (1604) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1604) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1604) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1604) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1604) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (1604) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
Executable files
134
Suspicious files
510
Text files
299
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1136 | WeMod-10.19.1.exe | C:\Users\admin\AppData\Local\SquirrelTemp\WeMod-10.19.1-full.nupkg | — | |
MD5:— | SHA256:— | |||
| 6772 | Update.exe | C:\Users\admin\AppData\Local\WeMod\packages\WeMod-10.19.1-full.nupkg | — | |
MD5:— | SHA256:— | |||
| 6772 | Update.exe | C:\Users\admin\AppData\Local\WeMod\app-10.19.1\icudtl.dat | — | |
MD5:— | SHA256:— | |||
| 1604 | WinRAR.exe | C:\Users\admin\Desktop\WeMod Unlocker [v3.0.1] {mul0}.exe | executable | |
MD5:04BD025FB88BA71194893BBB90666A76 | SHA256:207A3C7A88C275729BFC164F69CDA5B9B6DC0EA8426B5665725BA3E359A5E734 | |||
| 1604 | WinRAR.exe | C:\Users\admin\Desktop\Newtonsoft.Json.dll | executable | |
MD5:195FFB7167DB3219B217C4FD439EEDD6 | SHA256:E1E27AF7B07EEEDF5CE71A9255F0422816A6FC5849A483C6714E1B472044FA9D | |||
| 1604 | WinRAR.exe | C:\Users\admin\Desktop\Info.txt | text | |
MD5:CB9409181D36F6D6AE9F007EFD9210C8 | SHA256:3F74B17C7F9C8E5FEF4FC4D18B03BCDB327BC9A73FD39D0E8AA63AF581C51DBD | |||
| 1604 | WinRAR.exe | C:\Users\admin\Desktop\WeMod - Unlocker [v3.0.1] {mul0} [1].jpg | image | |
MD5:917909A23EFCC2F1116FBE3E82EB5484 | SHA256:318BA2F987704F7BB5CDB89B353571EB629AD51DBBB40C3D3D1105B13CEB5ADD | |||
| 1604 | WinRAR.exe | C:\Users\admin\Desktop\WeMod - Unlocker [v3.0.1] {mul0} [2].jpg | image | |
MD5:DEBFE35D8C1B686DD5BB8082FC838136 | SHA256:EA826149EA88470DAA2CCF32A3C483983D2C54354CD23A84D07180C02A702B50 | |||
| 6772 | Update.exe | C:\Users\admin\AppData\Local\WeMod\app-10.19.1\libEGL.dll | executable | |
MD5:4F78AB44FC64117EE9CB54B5FC2703F6 | SHA256:42FB94F98ABA346A412DDC6AFC6882765B792342987CC8C81E09447E2A73CBAE | |||
| 6772 | Update.exe | C:\Users\admin\AppData\Local\WeMod\app-10.19.1\chrome_100_percent.pak | binary | |
MD5:001AA2A7D5DCAF2D0987804A37E21DB9 | SHA256:0B84B7680630DD51CB36A2FCDD7CC3B031636FE6B91F81772822BE9E514132FE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
52
DNS requests
34
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2864 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1816 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2864 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5560 | WeModAuxiliaryService.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
5560 | WeModAuxiliaryService.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
5560 | WeModAuxiliaryService.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEALWLoqHGp2y9P4x7Rdh11E%3D | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 23.209.209.135:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4648 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1816 | svchost.exe | 20.190.160.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1816 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1268 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2336 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
1268 | svchost.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |