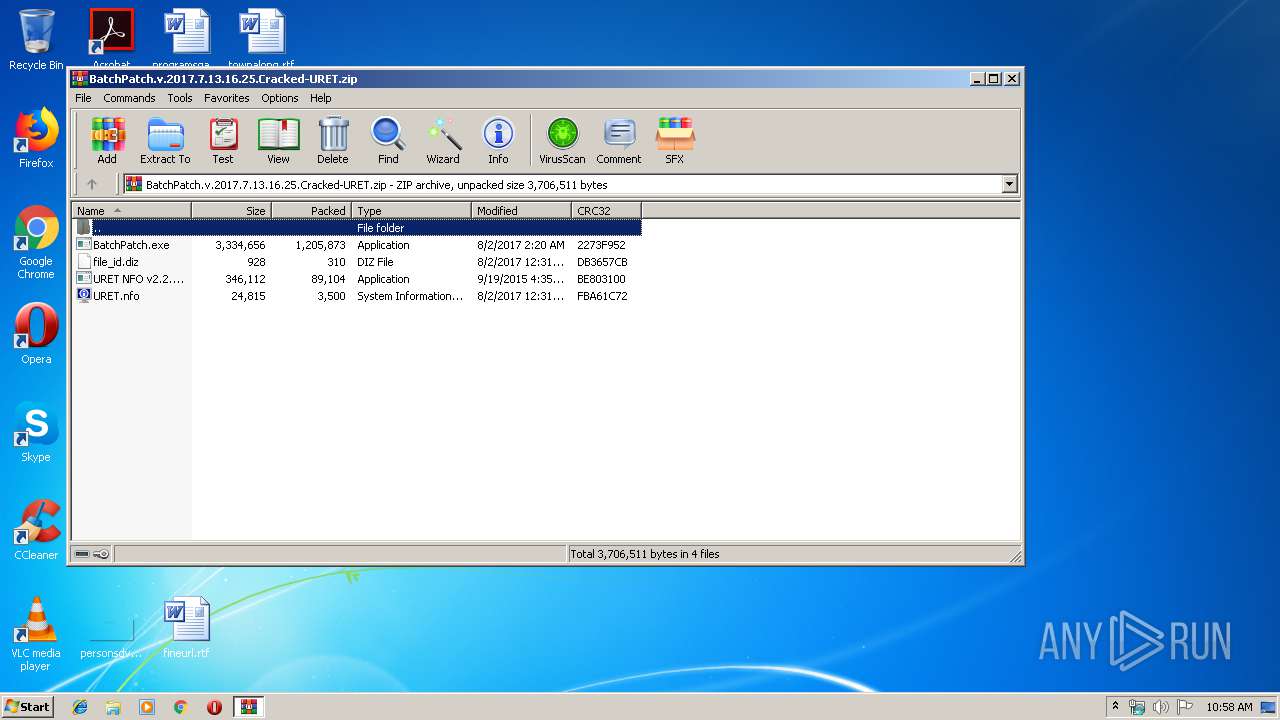
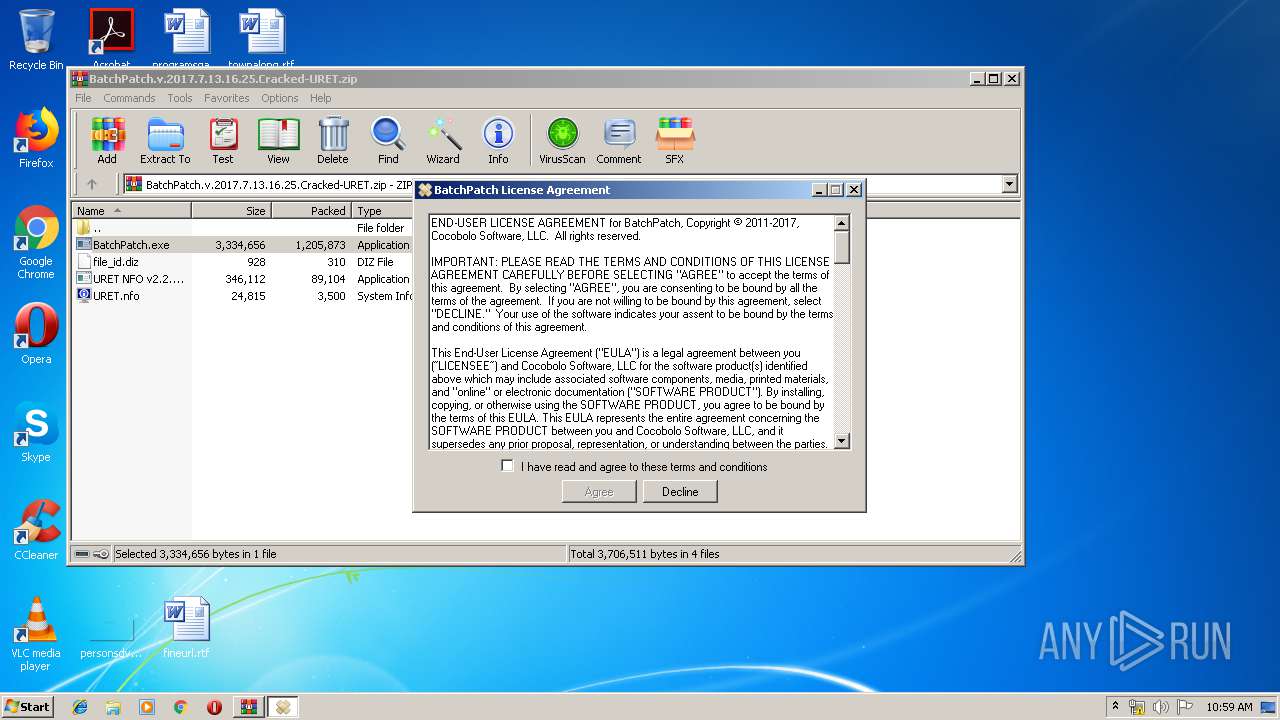
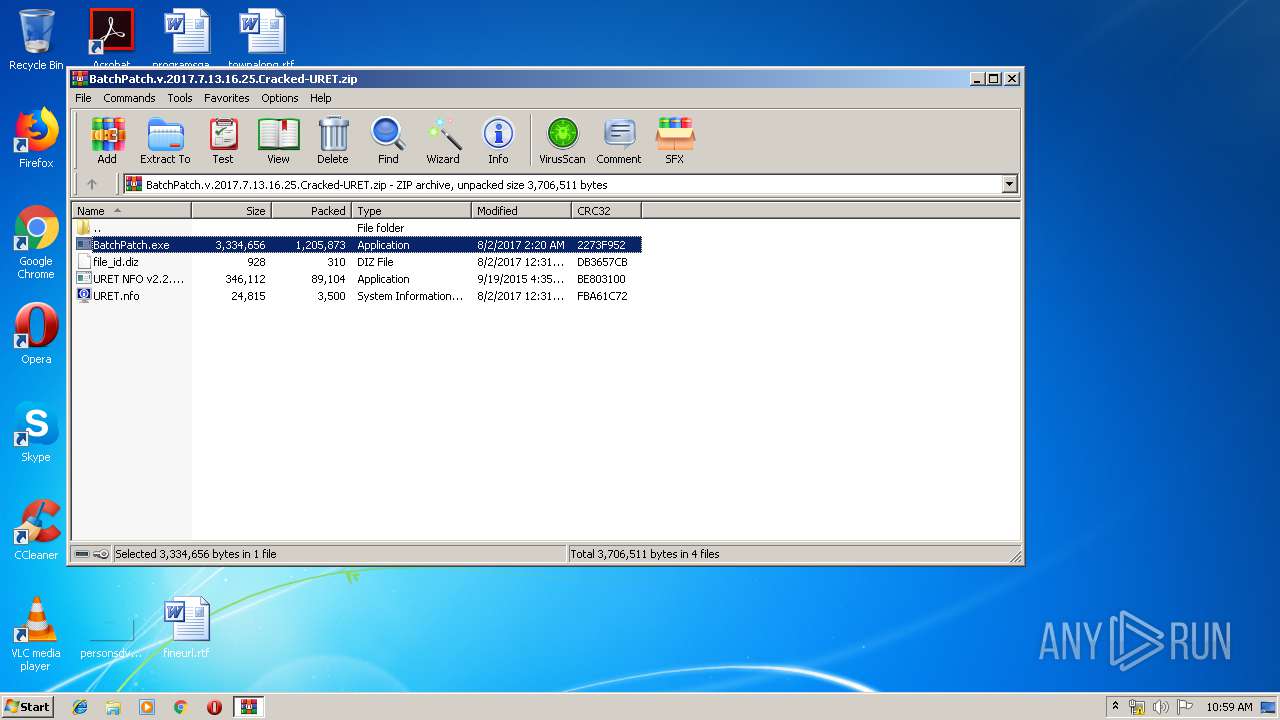
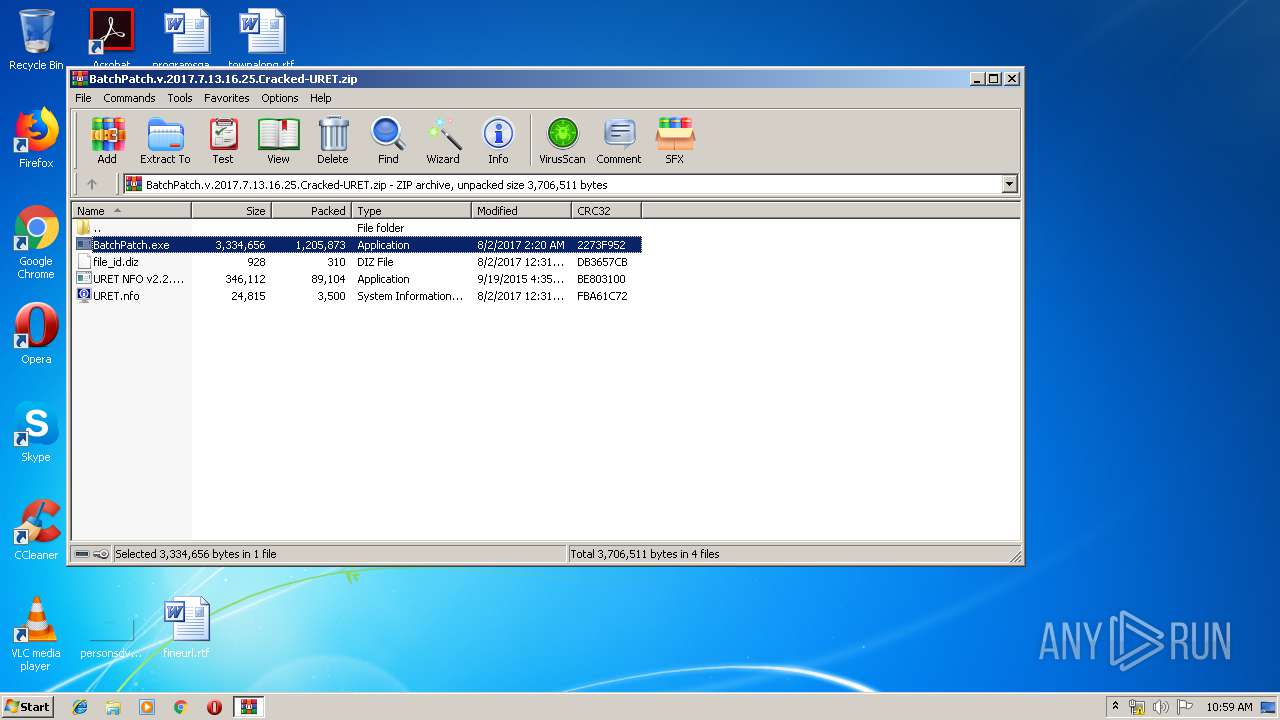
| File name: | BatchPatch.v.2017.7.13.16.25.Cracked-URET.zip |
| Full analysis: | https://app.any.run/tasks/0bbd90e6-d610-480e-a734-7dfeed078c7b |
| Verdict: | Malicious activity |
| Analysis date: | July 24, 2019, 09:58:09 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | EF3E1D9E4580A4AD7C40284F4088874D |
| SHA1: | C3D508E735EFACE7C83167771C72688653B88775 |
| SHA256: | A2BBB2ED427D37DE18A045712BD4E494C259499CAD6F2D6B460245D4409EE229 |
| SSDEEP: | 24576:PXSnH69/amOnZDEmal1m4EE5Eo7sN1kq3a1VdEwN/jZNt4JbNiasE+epeb0X:aH6wmOnBE1CpN1kq32VdEm/jZNWbN35T |
MALICIOUS
Application was dropped or rewritten from another process
- BatchPatch.exe (PID: 3708)
- URET NFO v2.2.exe (PID: 2208)
- URET NFO v2.2.exe (PID: 3172)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2844)
Reads Environment values
- BatchPatch.exe (PID: 3708)
Reads internet explorer settings
- BatchPatch.exe (PID: 3708)
INFO
Manual execution by user
- URET NFO v2.2.exe (PID: 3172)
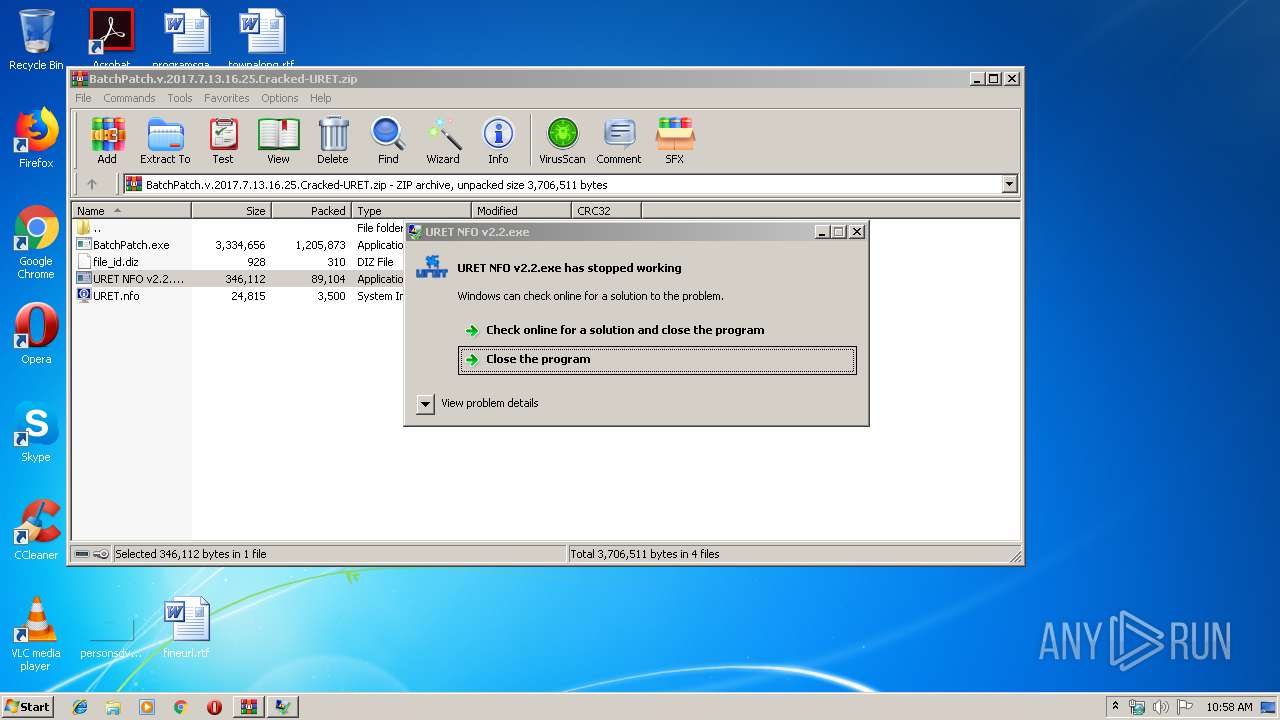
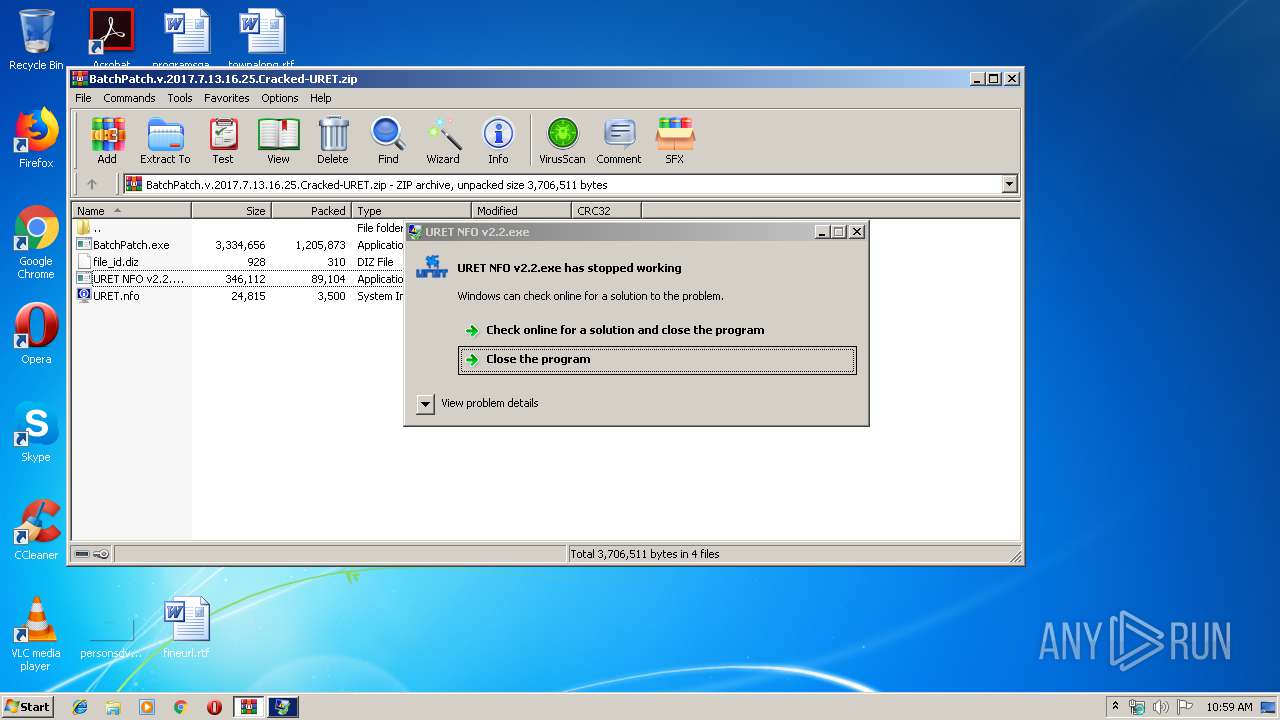
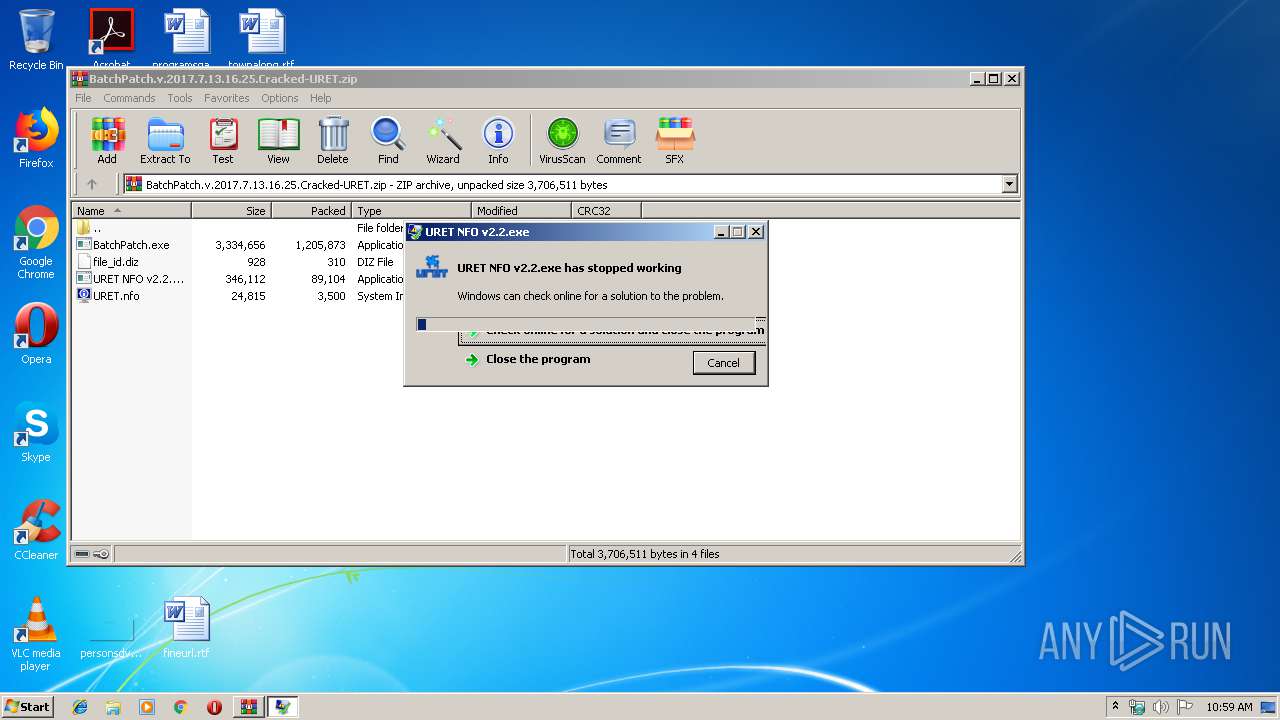
Application was crashed
- URET NFO v2.2.exe (PID: 3172)
- URET NFO v2.2.exe (PID: 2208)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2017:08:02 02:20:20 |
| ZipCRC: | 0x2273f952 |
| ZipCompressedSize: | 1205873 |
| ZipUncompressedSize: | 3334656 |
| ZipFileName: | BatchPatch.exe |
Total processes
42
Monitored processes
4
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2208 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2844.32556\URET NFO v2.2.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2844.32556\URET NFO v2.2.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225725 Modules
| |||||||||||||||
| 2844 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\BatchPatch.v.2017.7.13.16.25.Cracked-URET.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3172 | "C:\Users\admin\Desktop\URET NFO v2.2.exe" | C:\Users\admin\Desktop\URET NFO v2.2.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225477 Modules
| |||||||||||||||
| 3708 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2844.35809\BatchPatch.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2844.35809\BatchPatch.exe | WinRAR.exe | ||||||||||||
User: admin Company: Cocobolo Software, LLC Integrity Level: MEDIUM Description: BatchPatch Exit code: 0 Version: 2017.7.13.17.25 Modules
| |||||||||||||||
Total events
976
Read events
648
Write events
328
Delete events
0
Modification events
| (PID) Process: | (2844) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2844) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2844) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\70\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2844) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\BatchPatch.v.2017.7.13.16.25.Cracked-URET.zip | |||
| (PID) Process: | (2844) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2844) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2844) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2844) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2844) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\70\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\msinfo32.exe,-10001 |
Value: System Information File | |||
| (PID) Process: | (2844) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
6
Suspicious files
0
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2844 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2844.32556\file_id.diz | text | |
MD5:— | SHA256:— | |||
| 2844 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2844.32556\URET.nfo | text | |
MD5:— | SHA256:— | |||
| 2844 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2844.38323\BatchPatch.exe | executable | |
MD5:— | SHA256:— | |||
| 2844 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2844.38323\URET.nfo | text | |
MD5:— | SHA256:— | |||
| 2844 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2844.35809\URET NFO v2.2.exe | executable | |
MD5:FC26EDAA044131899060C8CB716496D9 | SHA256:F67131C08430A915E3A307758FDADB72672BA60C93F12F03DED0C43CECD6FEE0 | |||
| 2844 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2844.38323\URET NFO v2.2.exe | executable | |
MD5:FC26EDAA044131899060C8CB716496D9 | SHA256:F67131C08430A915E3A307758FDADB72672BA60C93F12F03DED0C43CECD6FEE0 | |||
| 2844 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2844.32556\URET NFO v2.2.exe | executable | |
MD5:FC26EDAA044131899060C8CB716496D9 | SHA256:F67131C08430A915E3A307758FDADB72672BA60C93F12F03DED0C43CECD6FEE0 | |||
| 2844 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2844.35809\BatchPatch.exe | executable | |
MD5:— | SHA256:— | |||
| 2844 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2844.32556\BatchPatch.exe | executable | |
MD5:— | SHA256:— | |||
| 2844 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2844.38323\file_id.diz | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
1
DNS requests
1
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3708 | BatchPatch.exe | GET | 200 | 208.113.192.87:80 | http://batchpatch.com/files/version.txt | US | text | 35 b | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3708 | BatchPatch.exe | 208.113.192.87:80 | batchpatch.com | New Dream Network, LLC | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
batchpatch.com |
| suspicious |