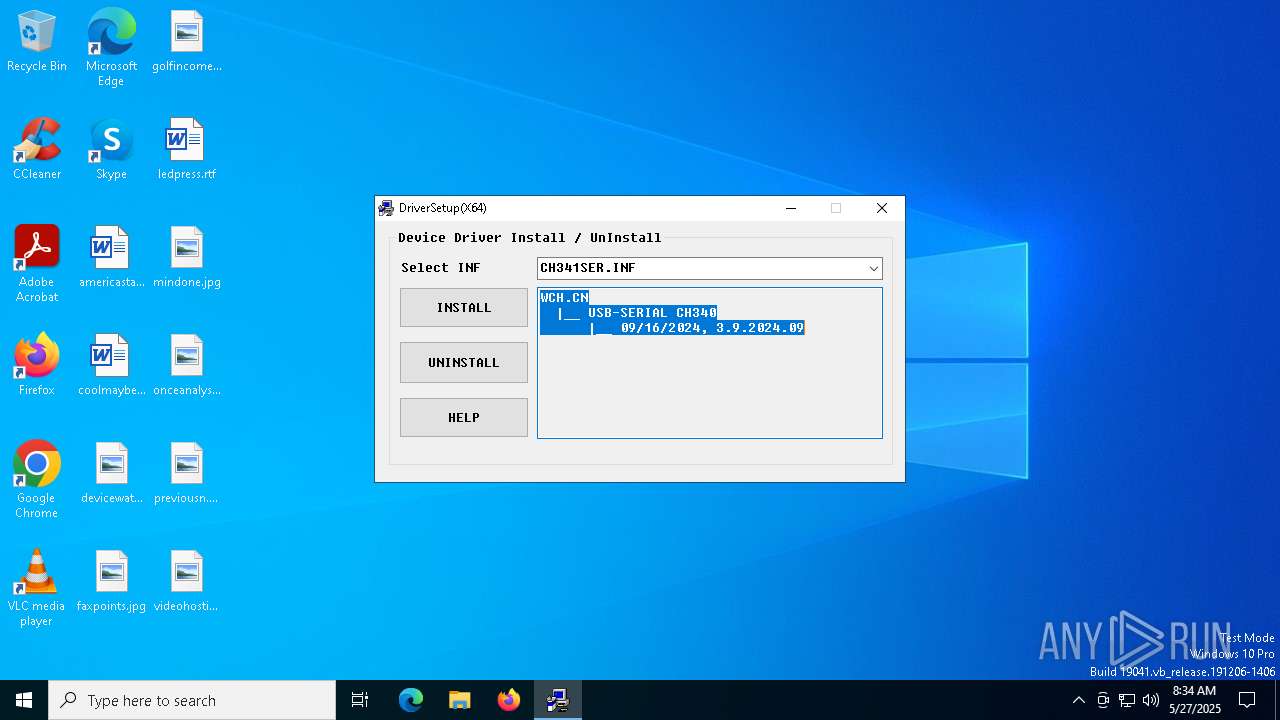
| File name: | CH341SER.exe |
| Full analysis: | https://app.any.run/tasks/c1fe6b33-8af3-476a-a39e-03cd1c0577b4 |
| Verdict: | Malicious activity |
| Analysis date: | May 27, 2025, 08:34:24 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, RAR self-extracting archive, 4 sections |
| MD5: | 17501FBA8A991F5656CFB52C4469283E |
| SHA1: | 59089B4E112664DC7AE0049544B2AFAFD6D2CFFE |
| SHA256: | A2BB1C04F2519788346EE08790AE2D3E3A49DDE4F49997BF6E81D8301CCF5123 |
| SSDEEP: | 24576:Md8uGXZfSHjokacRfQ10lVOjiEp53cRudbbc18RIMsOjmVfyrlG+WOu6/Ry5fQMo:Y0SHjokacRfQ10lVOjiC1cRwbbc18RIm |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- CH341SER.exe (PID: 7320)
- DRVSETUP64.exe (PID: 7536)
- drvinst.exe (PID: 7784)
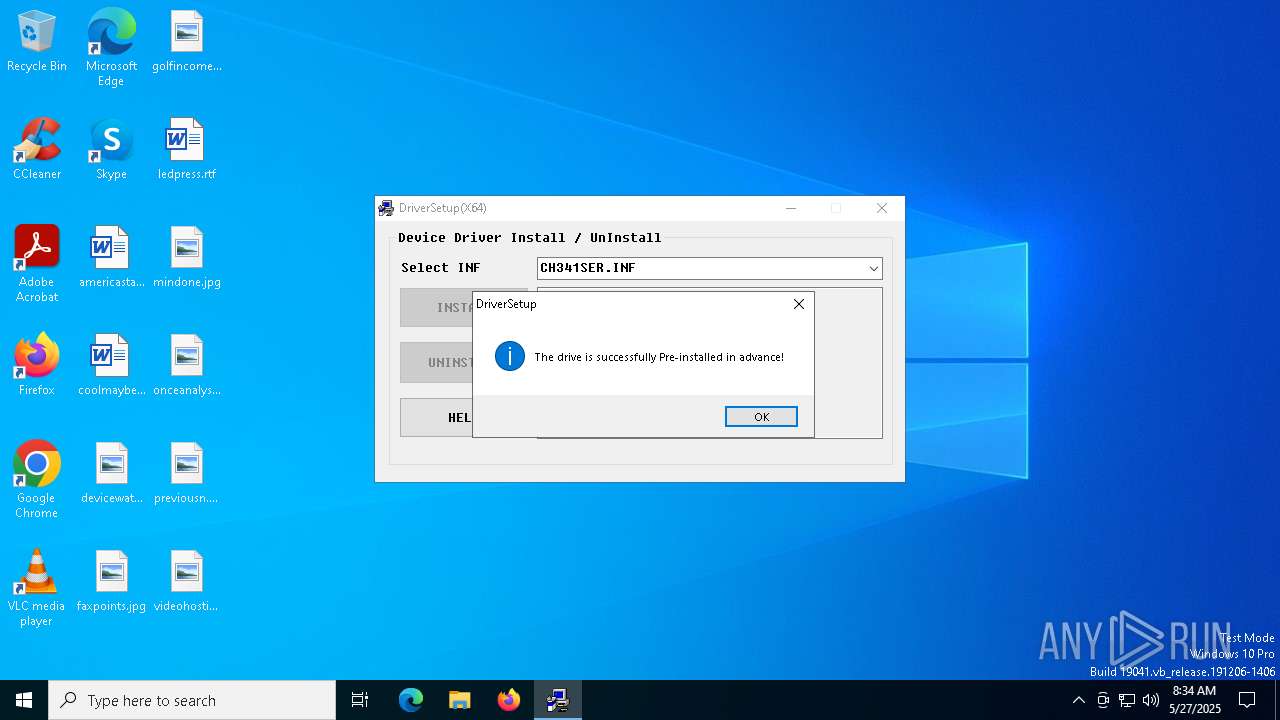
Drops a system driver (possible attempt to evade defenses)
- DRVSETUP64.exe (PID: 7536)
- CH341SER.exe (PID: 7320)
- drvinst.exe (PID: 7784)
Creates files in the driver directory
- drvinst.exe (PID: 7784)
- DRVSETUP64.exe (PID: 7536)
Creates file in the systems drive root
- CH341SER.exe (PID: 7320)
Reads security settings of Internet Explorer
- CH341SER.exe (PID: 7320)
INFO
Checks supported languages
- CH341SER.exe (PID: 7320)
- drvinst.exe (PID: 7784)
The sample compiled with english language support
- CH341SER.exe (PID: 7320)
- drvinst.exe (PID: 7784)
- DRVSETUP64.exe (PID: 7536)
Process checks computer location settings
- CH341SER.exe (PID: 7320)
Reads the computer name
- CH341SER.exe (PID: 7320)
- drvinst.exe (PID: 7784)
Reads the machine GUID from the registry
- drvinst.exe (PID: 7784)
The sample compiled with chinese language support
- CH341SER.exe (PID: 7320)
Create files in a temporary directory
- DRVSETUP64.exe (PID: 7536)
Reads the software policy settings
- drvinst.exe (PID: 7784)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | WinRAR Self Extracting archive (94.8) |
|---|---|---|
| .scr | | | Windows screen saver (2.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (1.2) |
| .exe | | | Win32 Executable (generic) (0.8) |
| .exe | | | Generic Win/DOS Executable (0.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2007:05:22 04:59:14+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 5 |
| CodeSize: | 81920 |
| InitializedDataSize: | 17920 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
136
Monitored processes
6
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 7320 | "C:\Users\admin\AppData\Local\Temp\CH341SER.exe" | C:\Users\admin\AppData\Local\Temp\CH341SER.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
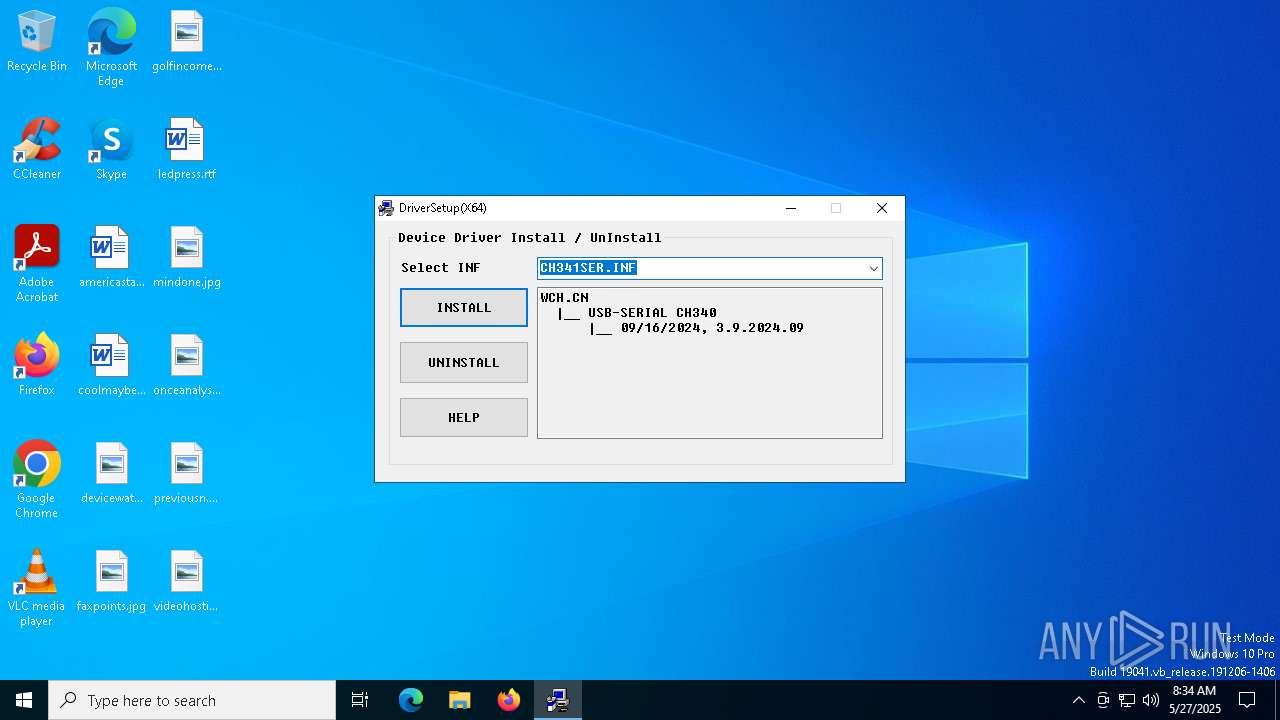
| 7396 | "C:\WCH.CN\CH341SER\SETUP.EXE" | C:\WCH.CN\CH341SER\SETUP.EXE | — | CH341SER.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: EXE For Driver Installation Version: 1, 7, 2, 0 Modules
| |||||||||||||||
| 7536 | C:\WCH.CN\CH341SER\DRVSETUP64\DRVSETUP64.EXE | C:\WCH.CN\CH341SER\DRVSETUP64\DRVSETUP64.exe | — | — | |||||||||||
User: admin Integrity Level: HIGH Description: EXE For Driver Installation Version: 1, 7, 2, 0 Modules
| |||||||||||||||
| 7560 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7596 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7784 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{3c499dc9-9211-ba43-b175-95ff5bbe1ebd}\CH341SER.INF" "9" "4c9e2e733" "00000000000001C8" "WinSta0\Default" "00000000000001DC" "208" "C:\WCH.CN\CH341SER\WIN 1X" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 701
Read events
3 699
Write events
2
Delete events
0
Modification events
| (PID) Process: | (7320) CH341SER.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR SFX |
| Operation: | write | Name: | C%%WCH.CN%CH341SER |
Value: C:\WCH.CN\CH341SER | |||
| (PID) Process: | (7536) DRVSETUP64.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\Setup\SetupapiLogStatus |
| Operation: | write | Name: | setupapi.dev.log |
Value: 4096 | |||
Executable files
77
Suspicious files
14
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7320 | CH341SER.exe | C:\WCH.CN\CH341SER\CH341PORTSA64.DLL | executable | |
MD5:9DAFB3192514248CD4E65407658FF874 | SHA256:DEE3D7C686C343B3B770E0238E27EE4D987AAB9A02C24002E2FA332586B1819B | |||
| 7320 | CH341SER.exe | C:\WCH.CN\CH341SER\CH341PORTS.DLL | executable | |
MD5:4135FFB3AFE5F16BC4018ABB7806992F | SHA256:729C8EA399523369AA5B99AE07277AEDD7FCC1C83F62618DC2683152B3D077FD | |||
| 7320 | CH341SER.exe | C:\WCH.CN\CH341SER\WIN 1X\CH341M64.sys | executable | |
MD5:E4482D22A65F0DFAB2B8DE7BD76ACB78 | SHA256:FC6C7CA345FA54C90B08B734D64148D02D08CC0696F084CA0AA93863BFD18813 | |||
| 7320 | CH341SER.exe | C:\WCH.CN\CH341SER\WIN 1X\CH341PTA64.DLL | executable | |
MD5:BE3D086D30A5EDFF8F2BAAEEE0D4B521 | SHA256:FA3FC85D3AD02E9C1958BF7ACF93C4F2E3741A88F9D2BFA68DA52997ED5D1D1B | |||
| 7320 | CH341SER.exe | C:\WCH.CN\CH341SER\CH341PTA64.DLL | executable | |
MD5:CB90FE7684489BC20AEC4D1A6F28FD6D | SHA256:656846E40F9D68AD10FDF0764A25322AE963E6B9C8715B40C87799B27711E907 | |||
| 7320 | CH341SER.exe | C:\WCH.CN\CH341SER\WIN 1X\CH341PORTSA64.DLL | executable | |
MD5:4950E5F9E7FCE8173F28914629576C79 | SHA256:26C0CCDCE0FC3819B370D253429FBEBDE613849DF4C801B074F9C77A85F3D6C0 | |||
| 7320 | CH341SER.exe | C:\WCH.CN\CH341SER\WIN 1X\CH341SER.CAT | binary | |
MD5:DC3F938D1A9005E6CEFCA5245FD3CC55 | SHA256:C583A330380B3D44C5609D5D0911A269217F2DF482018614FB5D77553D310521 | |||
| 7320 | CH341SER.exe | C:\WCH.CN\CH341SER\DRVSETUP64\DRVSETUP64.exe | executable | |
MD5:79D15141E52EE992E30A719ED72CABA0 | SHA256:14CAF1A64FA15DE0D1152B9EC589A569896112BF7DC457D9BDCF31BFA09254F0 | |||
| 7320 | CH341SER.exe | C:\WCH.CN\CH341SER\WIN 1X\CH341SER.INF | binary | |
MD5:867D71937AC1F93DBEB22E7DE5CF677C | SHA256:FB573086EE1B6F65D68A330CC4B48350439E3327C85292FC455B3588DFF053A3 | |||
| 7320 | CH341SER.exe | C:\WCH.CN\CH341SER\WIN 1X\CH341S64.sys | executable | |
MD5:CF4E1D3D91BC7AAB133040108C3B89EF | SHA256:C778DA857321E2745FDB85949E6FA3BB999729B8999C71792671D4AB35A8DF5E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
19
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
8084 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
8084 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2112 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.159.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
5796 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |