| File name: | a2aac45b6ae5a09bfa9e4ecdd90c5caa42acbe53588160fa6aa3f357ec6035bf |
| Full analysis: | https://app.any.run/tasks/6e54106b-b708-4bef-9748-2090accf4cf7 |
| Verdict: | Malicious activity |
| Analysis date: | October 05, 2022, 07:50:22 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 2C1C93A93645D3DEB11692760A713DF4 |
| SHA1: | 9178AC91EB42073926397CAE1E6109B95A4AC35F |
| SHA256: | A2AAC45B6AE5A09BFA9E4ECDD90C5CAA42ACBE53588160FA6AA3F357EC6035BF |
| SSDEEP: | 24576:n4nXubIQGyxbPV0db26Wmd0l4sv1Et9uGpckT52zedlq89Ws5uIzk5aM/phdOi:nqe3f61mZSffPMWrQ0Zkd |
MALICIOUS
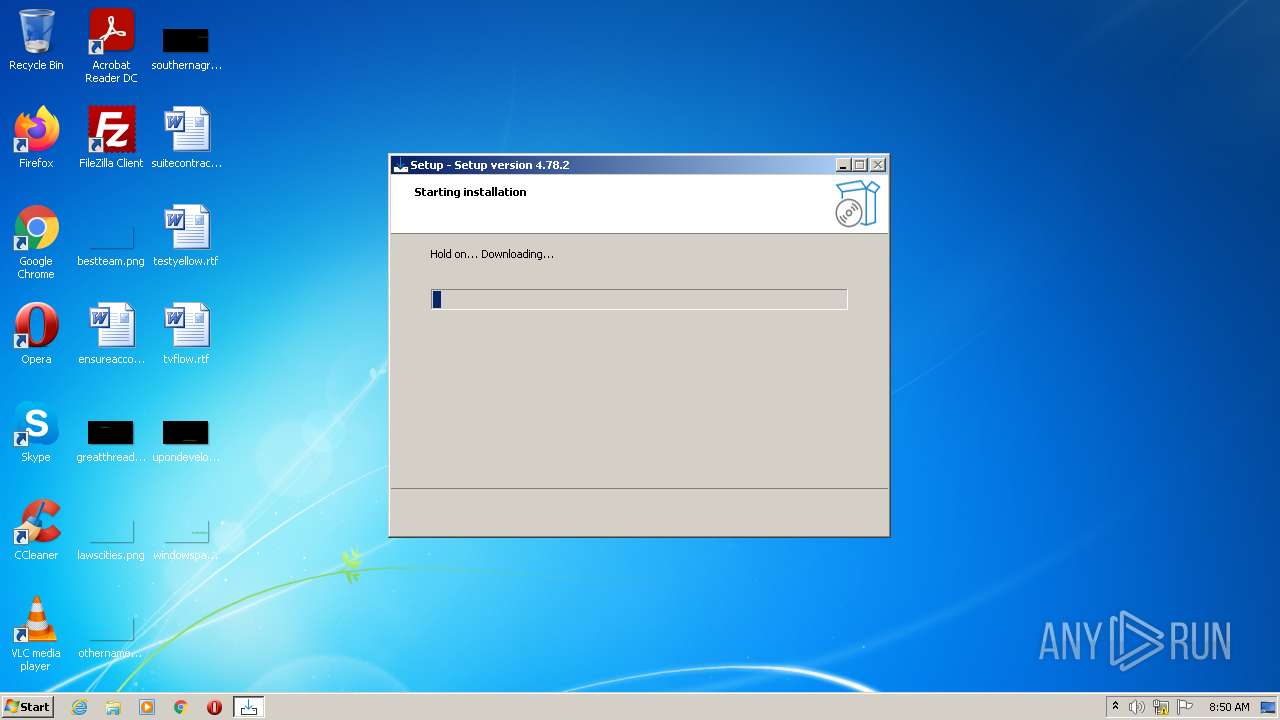
Drops the executable file immediately after the start
- a2aac45b6ae5a09bfa9e4ecdd90c5caa42acbe53588160fa6aa3f357ec6035bf.exe (PID: 3240)
- a2aac45b6ae5a09bfa9e4ecdd90c5caa42acbe53588160fa6aa3f357ec6035bf.tmp (PID: 368)
- file_.exe (PID: 3976)
- a2aac45b6ae5a09bfa9e4ecdd90c5caa42acbe53588160fa6aa3f357ec6035bf.exe (PID: 1844)
- file_.tmp (PID: 3428)
SUSPICIOUS
Executable content was dropped or overwritten
- a2aac45b6ae5a09bfa9e4ecdd90c5caa42acbe53588160fa6aa3f357ec6035bf.exe (PID: 3240)
- a2aac45b6ae5a09bfa9e4ecdd90c5caa42acbe53588160fa6aa3f357ec6035bf.exe (PID: 1844)
- a2aac45b6ae5a09bfa9e4ecdd90c5caa42acbe53588160fa6aa3f357ec6035bf.tmp (PID: 368)
- file_.exe (PID: 3976)
- file_.tmp (PID: 3428)
Reads the machine GUID from the registry
- a2aac45b6ae5a09bfa9e4ecdd90c5caa42acbe53588160fa6aa3f357ec6035bf.tmp (PID: 368)
- file_.tmp (PID: 3428)
Reads Internet Settings
- a2aac45b6ae5a09bfa9e4ecdd90c5caa42acbe53588160fa6aa3f357ec6035bf.tmp (PID: 368)
- file_.tmp (PID: 3428)
Reads the Windows owner or organization settings
- a2aac45b6ae5a09bfa9e4ecdd90c5caa42acbe53588160fa6aa3f357ec6035bf.tmp (PID: 368)
- file_.tmp (PID: 3428)
Drops a file that was compiled in debug mode
- file_.tmp (PID: 3428)
Drops a file with too old compile date
- file_.tmp (PID: 3428)
Reads settings of System Certificates
- a2aac45b6ae5a09bfa9e4ecdd90c5caa42acbe53588160fa6aa3f357ec6035bf.tmp (PID: 368)
- file_.tmp (PID: 3428)
INFO
Reads the computer name
- a2aac45b6ae5a09bfa9e4ecdd90c5caa42acbe53588160fa6aa3f357ec6035bf.tmp (PID: 3500)
- a2aac45b6ae5a09bfa9e4ecdd90c5caa42acbe53588160fa6aa3f357ec6035bf.tmp (PID: 368)
- file_.tmp (PID: 3428)
Checks supported languages
- a2aac45b6ae5a09bfa9e4ecdd90c5caa42acbe53588160fa6aa3f357ec6035bf.exe (PID: 3240)
- a2aac45b6ae5a09bfa9e4ecdd90c5caa42acbe53588160fa6aa3f357ec6035bf.tmp (PID: 3500)
- a2aac45b6ae5a09bfa9e4ecdd90c5caa42acbe53588160fa6aa3f357ec6035bf.exe (PID: 1844)
- a2aac45b6ae5a09bfa9e4ecdd90c5caa42acbe53588160fa6aa3f357ec6035bf.tmp (PID: 368)
- file_.exe (PID: 3976)
- file_.tmp (PID: 3428)
Process checks LSA protection
- a2aac45b6ae5a09bfa9e4ecdd90c5caa42acbe53588160fa6aa3f357ec6035bf.tmp (PID: 3500)
- a2aac45b6ae5a09bfa9e4ecdd90c5caa42acbe53588160fa6aa3f357ec6035bf.tmp (PID: 368)
- file_.tmp (PID: 3428)
Creates a file in a temporary directory
- a2aac45b6ae5a09bfa9e4ecdd90c5caa42acbe53588160fa6aa3f357ec6035bf.exe (PID: 3240)
- a2aac45b6ae5a09bfa9e4ecdd90c5caa42acbe53588160fa6aa3f357ec6035bf.exe (PID: 1844)
- a2aac45b6ae5a09bfa9e4ecdd90c5caa42acbe53588160fa6aa3f357ec6035bf.tmp (PID: 368)
- file_.exe (PID: 3976)
- file_.tmp (PID: 3428)
Application was dropped or rewritten from another process
- a2aac45b6ae5a09bfa9e4ecdd90c5caa42acbe53588160fa6aa3f357ec6035bf.tmp (PID: 3500)
- a2aac45b6ae5a09bfa9e4ecdd90c5caa42acbe53588160fa6aa3f357ec6035bf.tmp (PID: 368)
- file_.exe (PID: 3976)
- file_.tmp (PID: 3428)
Loads dropped or rewritten executable
- file_.tmp (PID: 3428)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (53.5) |
|---|---|---|
| .exe | | | InstallShield setup (21) |
| .exe | | | Win32 EXE PECompact compressed (generic) (20.2) |
| .exe | | | Win32 Executable (generic) (2.1) |
| .exe | | | Win16/32 Executable Delphi generic (1) |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 2021-Jun-03 08:09:11 |
| Detected languages: |
|
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | - |
| FileDescription: | Setup |
| FileVersion: | 4.78.2 |
| LegalCopyright: | - |
| OriginalFileName: | - |
| ProductName: | Setup |
| ProductVersion: | 4.78.2 |
DOS Header
| e_magic: | MZ |
|---|---|
| e_cblp: | 80 |
| e_cp: | 2 |
| e_crlc: | - |
| e_cparhdr: | 4 |
| e_minalloc: | 15 |
| e_maxalloc: | 65535 |
| e_ss: | - |
| e_sp: | 184 |
| e_csum: | - |
| e_ip: | - |
| e_cs: | - |
| e_ovno: | 26 |
| e_oemid: | - |
| e_oeminfo: | - |
| e_lfanew: | 256 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| NumberofSections: | 10 |
| TimeDateStamp: | 2021-Jun-03 08:09:11 |
| PointerToSymbolTable: | - |
| NumberOfSymbols: | - |
| SizeOfOptionalHeader: | 224 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 4096 | 734748 | 735232 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.35606 |
.itext | 741376 | 5768 | 6144 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 5.97275 |
.data | 749568 | 14244 | 14336 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 5.0444 |
.bss | 765952 | 28136 | 0 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | |
.idata | 794624 | 3894 | 4096 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.8987 |
.didata | 798720 | 420 | 512 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 2.75636 |
.edata | 802816 | 154 | 512 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 1.87222 |
.tls | 806912 | 24 | 0 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | |
.rdata | 811008 | 93 | 512 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 1.38389 |
.rsrc | 815104 | 69120 | 69120 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 3.71008 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 1.74641 | 2664 | UNKNOWN | English - United States | RT_ICON |
2 | 1.98658 | 1640 | UNKNOWN | English - United States | RT_ICON |
3 | 2.01586 | 744 | UNKNOWN | English - United States | RT_ICON |
4 | 2.1704 | 296 | UNKNOWN | English - United States | RT_ICON |
5 | 1.912 | 5672 | UNKNOWN | English - United States | RT_ICON |
6 | 1.8663 | 3752 | UNKNOWN | English - United States | RT_ICON |
7 | 1.49649 | 2216 | UNKNOWN | English - United States | RT_ICON |
8 | 0.972379 | 1384 | UNKNOWN | English - United States | RT_ICON |
9 | 7.68913 | 4837 | UNKNOWN | English - United States | RT_ICON |
10 | 2.03031 | 16936 | UNKNOWN | English - United States | RT_ICON |
Imports
advapi32.dll |
comctl32.dll |
kernel32.dll |
kernel32.dll (delay-loaded) |
netapi32.dll |
oleaut32.dll |
user32.dll |
version.dll |
Exports
Title | Ordinal | Address |
|---|---|---|
dbkFCallWrapperAddr | 1 | 779836 |
__dbk_fcall_wrapper | 2 | 53408 |
TMethodImplementationIntercept | 3 | 344160 |
Total processes
41
Monitored processes
6
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 368 | "C:\Users\admin\AppData\Local\Temp\is-ERJVC.tmp\a2aac45b6ae5a09bfa9e4ecdd90c5caa42acbe53588160fa6aa3f357ec6035bf.tmp" /SL5="$2013A,831488,831488,C:\Users\admin\AppData\Local\Temp\a2aac45b6ae5a09bfa9e4ecdd90c5caa42acbe53588160fa6aa3f357ec6035bf.exe" /SPAWNWND=$20130 /NOTIFYWND=$20138 | C:\Users\admin\AppData\Local\Temp\is-ERJVC.tmp\a2aac45b6ae5a09bfa9e4ecdd90c5caa42acbe53588160fa6aa3f357ec6035bf.tmp | a2aac45b6ae5a09bfa9e4ecdd90c5caa42acbe53588160fa6aa3f357ec6035bf.exe | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 1844 | "C:\Users\admin\AppData\Local\Temp\a2aac45b6ae5a09bfa9e4ecdd90c5caa42acbe53588160fa6aa3f357ec6035bf.exe" /SPAWNWND=$20130 /NOTIFYWND=$20138 | C:\Users\admin\AppData\Local\Temp\a2aac45b6ae5a09bfa9e4ecdd90c5caa42acbe53588160fa6aa3f357ec6035bf.exe | a2aac45b6ae5a09bfa9e4ecdd90c5caa42acbe53588160fa6aa3f357ec6035bf.tmp | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: Setup Exit code: 0 Version: 4.78.2 Modules
| |||||||||||||||
| 3240 | "C:\Users\admin\AppData\Local\Temp\a2aac45b6ae5a09bfa9e4ecdd90c5caa42acbe53588160fa6aa3f357ec6035bf.exe" | C:\Users\admin\AppData\Local\Temp\a2aac45b6ae5a09bfa9e4ecdd90c5caa42acbe53588160fa6aa3f357ec6035bf.exe | Explorer.EXE | ||||||||||||
User: admin Company: Integrity Level: MEDIUM Description: Setup Exit code: 0 Version: 4.78.2 Modules
| |||||||||||||||
| 3428 | "C:\Users\admin\AppData\Local\Temp\is-496R8.tmp\file_.tmp" /SL5="$201AA,1577628,798720,C:\Users\admin\AppData\Local\Temp\is-1KE2K.tmp\file_.exe" /LANG=en /NA=Rh85hR64 | C:\Users\admin\AppData\Local\Temp\is-496R8.tmp\file_.tmp | file_.exe | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: Setup/Uninstall Exit code: 1 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 3500 | "C:\Users\admin\AppData\Local\Temp\is-J5G82.tmp\a2aac45b6ae5a09bfa9e4ecdd90c5caa42acbe53588160fa6aa3f357ec6035bf.tmp" /SL5="$20138,831488,831488,C:\Users\admin\AppData\Local\Temp\a2aac45b6ae5a09bfa9e4ecdd90c5caa42acbe53588160fa6aa3f357ec6035bf.exe" | C:\Users\admin\AppData\Local\Temp\is-J5G82.tmp\a2aac45b6ae5a09bfa9e4ecdd90c5caa42acbe53588160fa6aa3f357ec6035bf.tmp | — | a2aac45b6ae5a09bfa9e4ecdd90c5caa42acbe53588160fa6aa3f357ec6035bf.exe | |||||||||||
User: admin Company: Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 3976 | "C:\Users\admin\AppData\Local\Temp\is-1KE2K.tmp\file_.exe" /LANG=en /NA=Rh85hR64 | C:\Users\admin\AppData\Local\Temp\is-1KE2K.tmp\file_.exe | a2aac45b6ae5a09bfa9e4ecdd90c5caa42acbe53588160fa6aa3f357ec6035bf.tmp | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: setup Exit code: 1 Version: 2.3.4 Modules
| |||||||||||||||
Total events
6 580
Read events
6 542
Write events
34
Delete events
4
Modification events
| (PID) Process: | (368) a2aac45b6ae5a09bfa9e4ecdd90c5caa42acbe53588160fa6aa3f357ec6035bf.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 70010000C6E84E248FD8D801 | |||
| (PID) Process: | (368) a2aac45b6ae5a09bfa9e4ecdd90c5caa42acbe53588160fa6aa3f357ec6035bf.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 43AA3601ADEC2DFDD22765AE5FA564FE99C2F80CCEA2E061FE8D098DC9A27E9B | |||
| (PID) Process: | (368) a2aac45b6ae5a09bfa9e4ecdd90c5caa42acbe53588160fa6aa3f357ec6035bf.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (368) a2aac45b6ae5a09bfa9e4ecdd90c5caa42acbe53588160fa6aa3f357ec6035bf.tmp | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3428) file_.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0001 |
| Operation: | write | Name: | Owner |
Value: 640D00002CD0BA2E8FD8D801 | |||
| (PID) Process: | (3428) file_.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0001 |
| Operation: | write | Name: | SessionHash |
Value: BD33C9285D156A2245727D0646EEE291B61F01B33D15DEAEFF92EAE5C0E1887D | |||
| (PID) Process: | (3428) file_.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0001 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (3428) file_.tmp | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3428) file_.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0001 |
| Operation: | delete value | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (3428) file_.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0001 |
| Operation: | delete value | Name: | SessionHash |
Value: BD33C9285D156A2245727D0646EEE291B61F01B33D15DEAEFF92EAE5C0E1887D | |||
Executable files
7
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 368 | a2aac45b6ae5a09bfa9e4ecdd90c5caa42acbe53588160fa6aa3f357ec6035bf.tmp | C:\Users\admin\AppData\Local\Temp\is-1KE2K.tmp\file_.exe | executable | |
MD5:— | SHA256:— | |||
| 368 | a2aac45b6ae5a09bfa9e4ecdd90c5caa42acbe53588160fa6aa3f357ec6035bf.tmp | C:\Users\admin\AppData\Local\Temp\is-1KE2K.tmp\is-0O9KJ.tmp | executable | |
MD5:— | SHA256:— | |||
| 3976 | file_.exe | C:\Users\admin\AppData\Local\Temp\is-496R8.tmp\file_.tmp | executable | |
MD5:— | SHA256:— | |||
| 3428 | file_.tmp | C:\Users\admin\AppData\Local\Temp\is-U6TUQ.tmp\botva2.dll | executable | |
MD5:67965A5957A61867D661F05AE1F4773E | SHA256:450B9B0BA25BF068AFBC2B23D252585A19E282939BF38326384EA9112DFD0105 | |||
| 3240 | a2aac45b6ae5a09bfa9e4ecdd90c5caa42acbe53588160fa6aa3f357ec6035bf.exe | C:\Users\admin\AppData\Local\Temp\is-J5G82.tmp\a2aac45b6ae5a09bfa9e4ecdd90c5caa42acbe53588160fa6aa3f357ec6035bf.tmp | executable | |
MD5:0C229CD26910820581B5809C62FE5619 | SHA256:ABFA49A915D2E0A82561CA440365E6A2D59F228533B56A8F78ADDF000A1081B3 | |||
| 3428 | file_.tmp | C:\Users\admin\AppData\Local\Temp\is-U6TUQ.tmp\Helper.dll | executable | |
MD5:4EB0347E66FA465F602E52C03E5C0B4B | SHA256:C73E53CBB7B98FEAFE27CC7DE8FDAD51DF438E2235E91891461C5123888F73CC | |||
| 1844 | a2aac45b6ae5a09bfa9e4ecdd90c5caa42acbe53588160fa6aa3f357ec6035bf.exe | C:\Users\admin\AppData\Local\Temp\is-ERJVC.tmp\a2aac45b6ae5a09bfa9e4ecdd90c5caa42acbe53588160fa6aa3f357ec6035bf.tmp | executable | |
MD5:0C229CD26910820581B5809C62FE5619 | SHA256:ABFA49A915D2E0A82561CA440365E6A2D59F228533B56A8F78ADDF000A1081B3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
2
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3428 | file_.tmp | 18.66.17.223:443 | d1pqn6m5ywnw3a.cloudfront.net | — | US | unknown |
368 | a2aac45b6ae5a09bfa9e4ecdd90c5caa42acbe53588160fa6aa3f357ec6035bf.tmp | 13.225.84.202:443 | d3fzprifddppqn.cloudfront.net | AMAZON-02 | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
d3fzprifddppqn.cloudfront.net |
| suspicious |
d1pqn6m5ywnw3a.cloudfront.net |
| unknown |