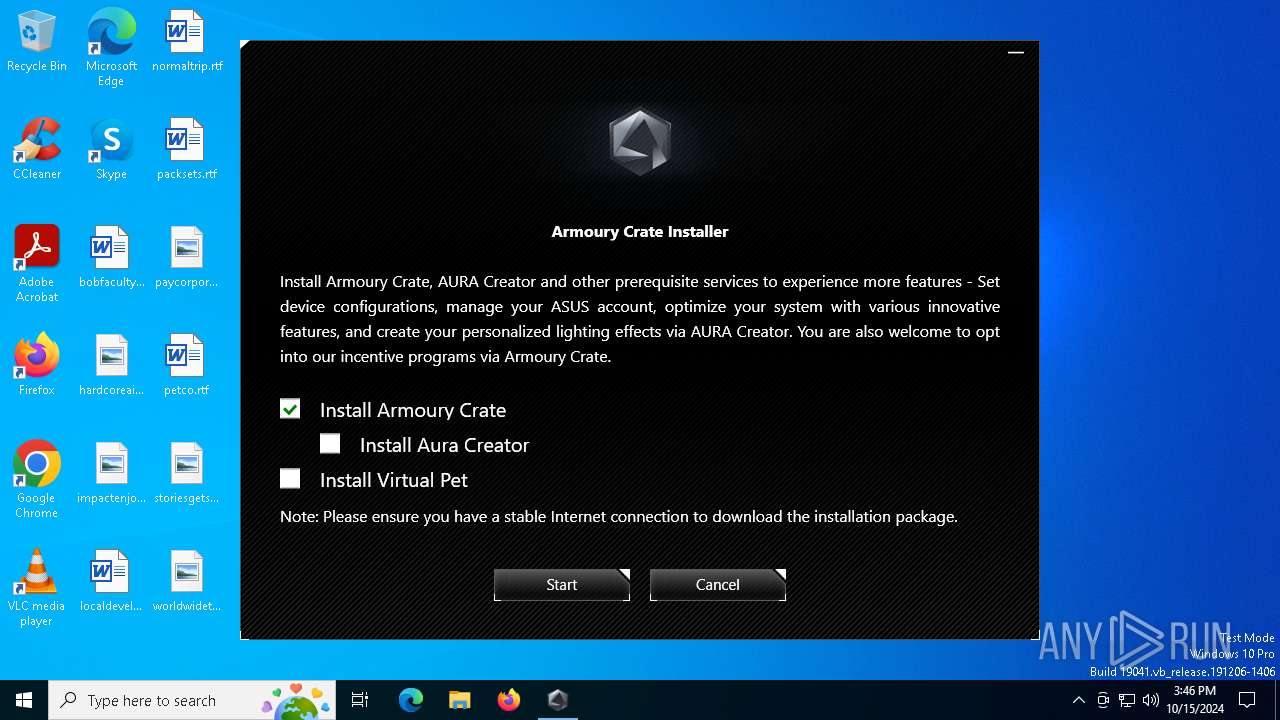
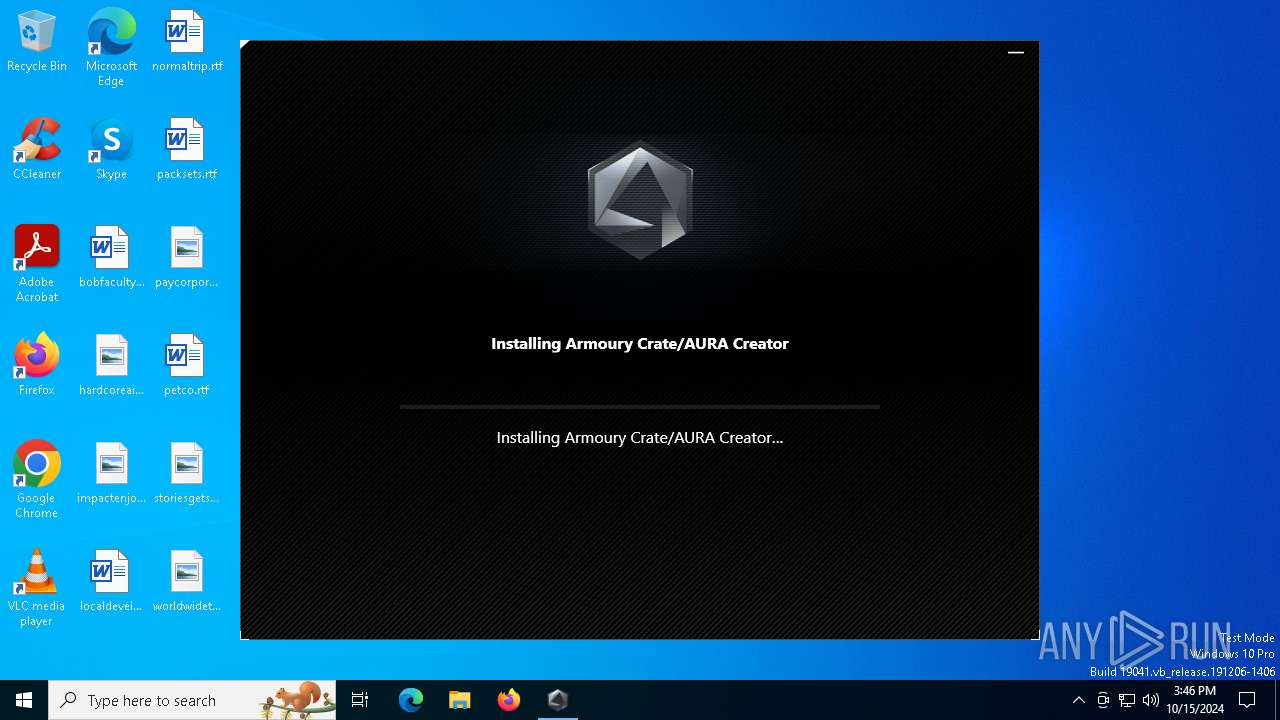
| File name: | ArmouryCrateInstaller.exe |
| Full analysis: | https://app.any.run/tasks/d64d97c5-55c5-4a03-9637-a4ba7c866e5d |
| Verdict: | Malicious activity |
| Analysis date: | October 15, 2024, 15:45:57 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (console) x86-64, for MS Windows |
| MD5: | 3F114BBE6506A8327F5898EBD896710A |
| SHA1: | 616F9289B6A38D4FDB1114A196813B054F885DFB |
| SHA256: | A29BEF43CC0D43EB5391CD402CC1E4B52E67BC0314476B9E4FDE7F13D32D5C00 |
| SSDEEP: | 49152:Hk/QVfJqVenLCOtjUifB3juwYph0Vk9ehjQOviDb9RM2HjYVV1BCjBsWCNEK:axymFifBTFYH0VTebNHjYPWCV |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- ArmouryCrateInstaller.exe (PID: 6680)
- AsZip.exe (PID: 3604)
The process drops C-runtime libraries
- AsusROGLSLService.exe (PID: 4348)
- AsZip.exe (PID: 3604)
Process drops legitimate windows executable
- AsusROGLSLService.exe (PID: 4348)
- AsZip.exe (PID: 3604)
Executes as Windows Service
- AsusROGLSLService.exe (PID: 4348)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 1008)
Starts CMD.EXE for commands execution
- QueryUWP.exe (PID: 1428)
INFO
Creates files in the program directory
- ArmouryCrateInstaller.exe (PID: 6680)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 EXE PECompact compressed (generic) (83) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (9) |
| .exe | | | Generic Win/DOS Executable (3.9) |
| .exe | | | DOS Executable Generic (3.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2023:03:13 10:14:40+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.16 |
| CodeSize: | 209920 |
| InitializedDataSize: | 3630592 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x13d94 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 3.2.6.1 |
| ProductVersionNumber: | 3.2.6.1 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral 2 |
| CharacterSet: | Unicode |
| CompanyName: | ASUS |
| FileVersion: | 3.2.6.1 |
| LegalCopyright: | Copyright (C) 2019 |
| ProductVersion: | 3.2.6.1 |
Total processes
160
Monitored processes
26
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1008 | C:\WINDOWS\system32\cmd.exe /c PowerShell "get-appxpackage | select-string B9ECED6F.ArmouryCrate" | C:\Windows\System32\cmd.exe | — | QueryUWP.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1008 | "C:\Program Files (x86)\ASUS\ROGLSLoader\Armoury Crate Installer.exe" -asusdownloadbar -bar_report 0 -interruptSatus interrupt_0 -barstyle armourycrate -barProduct "Armoury Crate" -progressbarstatus 2 | C:\Program Files (x86)\ASUS\ROGLSLoader\Armoury Crate Installer.exe | — | ROGLSLoader.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Armoury Crate Installer Version: 2.3.11.2 Modules
| |||||||||||||||
| 1428 | "C:\Program Files (x86)\ASUS\AsusROGLSLService\QueryUWP.exe" | C:\Program Files (x86)\ASUS\AsusROGLSLService\QueryUWP.exe | — | AsusROGLSLService.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 4294967295 Version: 1.0.0.3 Modules
| |||||||||||||||
| 1840 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1880 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | CheckTool.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2416 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2620 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | AsusROGLSLService.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3604 | "C:\Program Files (x86)\ASUS\AsusROGLSLService\AsZip.exe" "C:\Program Files (x86)\ASUS\ROGLSLoader.zip" | C:\Program Files (x86)\ASUS\AsusROGLSLService\AsZip.exe | AsusROGLSLService.exe | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Exit code: 0 Version: 1.0.0.2 Modules
| |||||||||||||||
| 3728 | "C:\Program Files (x86)\ASUS\AsusROGLSLService\Armoury Crate Installer.exe" -roglsloaderstart -win armourycrate -acinstaller | C:\Program Files (x86)\ASUS\AsusROGLSLService\Armoury Crate Installer.exe | AsusROGLSLService.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Armoury Crate Installer Exit code: 87394 Version: 2.3.6.1 Modules
| |||||||||||||||
| 3740 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | AsZip.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
11 742
Read events
11 717
Write events
23
Delete events
2
Modification events
| (PID) Process: | (6680) ArmouryCrateInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\ASUS\ROGLiveServicePackage |
| Operation: | write | Name: | ACInstallPath |
Value: C:\Users\admin\AppData\Local\Temp | |||
| (PID) Process: | (6680) ArmouryCrateInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\ASUS\ROGLiveServicePackage |
| Operation: | write | Name: | InstallFinish |
Value: 0 | |||
| (PID) Process: | (6680) ArmouryCrateInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\ASUS\ROGLiveServicePackage |
| Operation: | delete value | Name: | aaiu |
Value: | |||
| (PID) Process: | (6680) ArmouryCrateInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\ASUS\ROGLiveServicePackage |
| Operation: | delete value | Name: | InstallerSilentMode |
Value: | |||
| (PID) Process: | (6328) AsusROGLSLService.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\ASUS\ROGLiveServicePackage |
| Operation: | write | Name: | aaiu |
Value: 0 | |||
| (PID) Process: | (3728) Armoury Crate Installer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\CTF\CUAS\DefaultCompositionWindow |
| Operation: | write | Name: | Left |
Value: 0 | |||
| (PID) Process: | (3728) Armoury Crate Installer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\CTF\CUAS\DefaultCompositionWindow |
| Operation: | write | Name: | Top |
Value: 0 | |||
| (PID) Process: | (4348) AsusROGLSLService.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\ASUS\ROGLiveServicePackage |
| Operation: | write | Name: | InstallApp |
Value: 2 | |||
| (PID) Process: | (4348) AsusROGLSLService.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\ASUS\ROGLiveServicePackage |
| Operation: | write | Name: | InstallApp2 |
Value: 259 | |||
| (PID) Process: | (6224) CheckTool.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\CheckTool_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
Executable files
24
Suspicious files
12
Text files
16
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6680 | ArmouryCrateInstaller.exe | C:\Program Files (x86)\ASUS\AsusROGLSLService\AsusGCGridServiceSetup.exe | executable | |
MD5:242C0332DB5EBA361CC3628DFAB5CE56 | SHA256:BCC843B036C22AD4A1485E62C2ED5CA88F33688FA919C73276B93D4CDBE83347 | |||
| 6680 | ArmouryCrateInstaller.exe | C:\Program Files (x86)\ASUS\AsusROGLSLService\CheckTool.exe | executable | |
MD5:8AA543FC8E4B0B84D0B302516F11DAD3 | SHA256:4943A6745479A6741E4C6EC5648971E6EC33D18EE484CEECD2FB7B14C0B2DDA3 | |||
| 6680 | ArmouryCrateInstaller.exe | C:\Program Files (x86)\ASUS\AsusROGLSLService\Newtonsoft.Json.dll | executable | |
MD5:081D9558BBB7ADCE142DA153B2D5577A | SHA256:B624949DF8B0E3A6153FDFB730A7C6F4990B6592EE0D922E1788433D276610F3 | |||
| 6680 | ArmouryCrateInstaller.exe | C:\Program Files (x86)\ASUS\AsusROGLSLService\AsZip.exe | executable | |
MD5:9131A40E5770D1170C3093FB0D2F6F63 | SHA256:FCF8D154E6B37985434F991B048CEF457DE123DD5A553EF3C6B28A67FB8A3987 | |||
| 6680 | ArmouryCrateInstaller.exe | C:\Program Files (x86)\ASUS\AsusROGLSLService\AsZip.dll | executable | |
MD5:964068210EDCB3631F02E45856EB291E | SHA256:4CF079D4D7A154CD93F65934B5D115F07AF8F25EE24930E6CC606DFB0AEA2A4E | |||
| 6680 | ArmouryCrateInstaller.exe | C:\Program Files (x86)\ASUS\AsusROGLSLService\Armoury Crate Installer.exe | executable | |
MD5:0DB34D61E1748542D1A2C9948FB030C3 | SHA256:8590F8DF64BC9E1A8C0D4AE906354BE5E8DC63CFDE147F114C6CE707B70A66C6 | |||
| 6904 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_f0504qzk.og4.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3828 | AsusROGLSLService.exe | C:\ProgramData\ASUS\ALL\ACLoader\AsusROGLSLService.log | text | |
MD5:DC7A87483870EB6EFB7DBE6CE61C9BBF | SHA256:C918FE217F8B637E9E6F25F1FB20B45141E977F513F30D7032A8B6F12EF7D94A | |||
| 1428 | QueryUWP.exe | C:\ProgramData\ASUS\ALL\QueryUWP.idx | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 7056 | AsZip.exe | C:\Program Files (x86)\ASUS\ROGLSLoader2.dat | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
62
DNS requests
23
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6944 | svchost.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2724 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5604 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
7060 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7060 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6944 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.16.110.123:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
1252 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6944 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6944 | svchost.exe | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6944 | svchost.exe | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5488 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
www.asus.com |
| whitelisted |
Threats
Process | Message |
|---|---|
Armoury Crate Installer.exe | Failed to get baseboard manufacturer via WMI, get via registry. |
ROGLSLoader.exe | Failed to get baseboard manufacturer via WMI, get via registry. |