| File name: | Soar.Launcher.V1.zip |
| Full analysis: | https://app.any.run/tasks/8467086d-3690-4214-8619-143d5d4761ec |
| Verdict: | Malicious activity |
| Analysis date: | May 21, 2022, 00:22:29 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 60280521BBFD36C93A325BD978D87735 |
| SHA1: | 3FF95EFF4D43D94B9FB6789AA28AEAB819E0DBF2 |
| SHA256: | A29B78612233387EA983280821FDBC76F8D72F4DE76E9CDAD3B70F66B3587E12 |
| SSDEEP: | 24576:U0bMgNTm9OF/mS6uJY9FvlUsj8uhz23zO18xw5TZU7nkn0j:U0lREuJuFvlUsoO6zOOw5y7nk0j |
MALICIOUS
Application was dropped or rewritten from another process
- SoarLauncher.exe (PID: 684)
- SoarLauncher.exe (PID: 888)
- SoarLauncher.exe (PID: 3428)
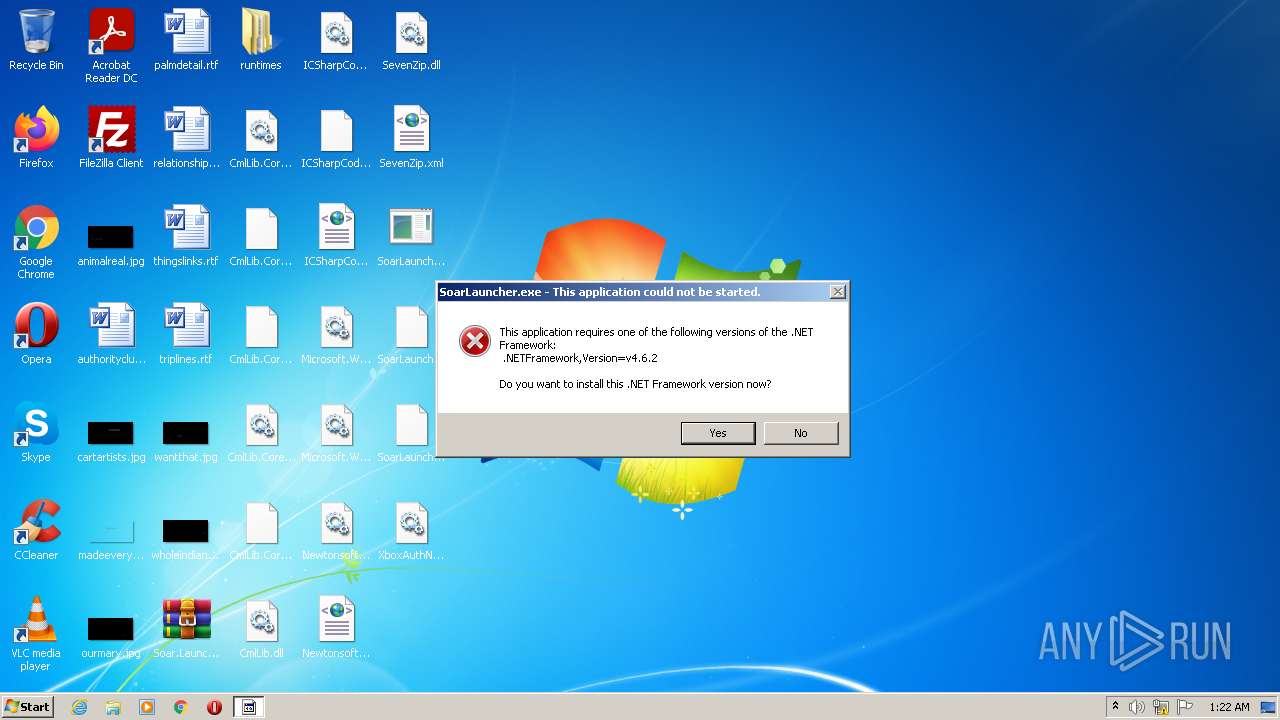
- ndp48-web.exe (PID: 1144)
- ndp48-web.exe (PID: 3828)
- Setup.exe (PID: 1516)
- SetupUtility.exe (PID: 3744)
- SetupUtility.exe (PID: 2108)
- ServiceModelReg.exe (PID: 3384)
- regtlibv12.exe (PID: 432)
- regtlibv12.exe (PID: 2672)
- regtlibv12.exe (PID: 2584)
- regtlibv12.exe (PID: 3104)
- regtlibv12.exe (PID: 632)
- regtlibv12.exe (PID: 3112)
- aspnet_regiis.exe (PID: 2504)
- regtlibv12.exe (PID: 3680)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3448)
- Setup.exe (PID: 1516)
- SoarLauncher.exe (PID: 888)
- SoarLauncher.exe (PID: 3428)
- SoarLauncher.exe (PID: 684)
- svchost.exe (PID: 2000)
- aspnet_regiis.exe (PID: 2504)
Drops executable file immediately after starts
- WinRAR.exe (PID: 2764)
- iexplore.exe (PID: 2288)
- iexplore.exe (PID: 1884)
- ndp48-web.exe (PID: 3828)
- msiexec.exe (PID: 2324)
Actions looks like stealing of personal data
- ndp48-web.exe (PID: 3828)
Changes settings of System certificates
- Setup.exe (PID: 1516)
SUSPICIOUS
Checks supported languages
- WinRAR.exe (PID: 2764)
- SoarLauncher.exe (PID: 684)
- SoarLauncher.exe (PID: 3428)
- SoarLauncher.exe (PID: 888)
- ndp48-web.exe (PID: 3828)
- Setup.exe (PID: 1516)
- SetupUtility.exe (PID: 3744)
- SetupUtility.exe (PID: 2108)
- TMP4B16.tmp.exe (PID: 3620)
- msiexec.exe (PID: 2324)
- MsiExec.exe (PID: 1148)
- MsiExec.exe (PID: 1964)
- ServiceModelReg.exe (PID: 3384)
- regtlibv12.exe (PID: 432)
- regtlibv12.exe (PID: 2584)
- mofcomp.exe (PID: 2876)
- regtlibv12.exe (PID: 3104)
- regtlibv12.exe (PID: 632)
- regtlibv12.exe (PID: 3112)
- mofcomp.exe (PID: 2816)
- regtlibv12.exe (PID: 2672)
- regtlibv12.exe (PID: 3680)
- mofcomp.exe (PID: 3636)
- aspnet_regiis.exe (PID: 2504)
Reads the computer name
- WinRAR.exe (PID: 2764)
- SoarLauncher.exe (PID: 684)
- SoarLauncher.exe (PID: 3428)
- ndp48-web.exe (PID: 3828)
- Setup.exe (PID: 1516)
- SetupUtility.exe (PID: 3744)
- SetupUtility.exe (PID: 2108)
- TMP4B16.tmp.exe (PID: 3620)
- msiexec.exe (PID: 2324)
- MsiExec.exe (PID: 1148)
- MsiExec.exe (PID: 1964)
- ServiceModelReg.exe (PID: 3384)
- mofcomp.exe (PID: 2876)
- mofcomp.exe (PID: 2816)
- aspnet_regiis.exe (PID: 2504)
- mofcomp.exe (PID: 3636)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2764)
- iexplore.exe (PID: 2288)
- iexplore.exe (PID: 1884)
- ndp48-web.exe (PID: 3828)
- TMP4B16.tmp.exe (PID: 3620)
- Setup.exe (PID: 1516)
- msiexec.exe (PID: 2324)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 2764)
- iexplore.exe (PID: 1884)
- iexplore.exe (PID: 2288)
- ndp48-web.exe (PID: 3828)
- msiexec.exe (PID: 2324)
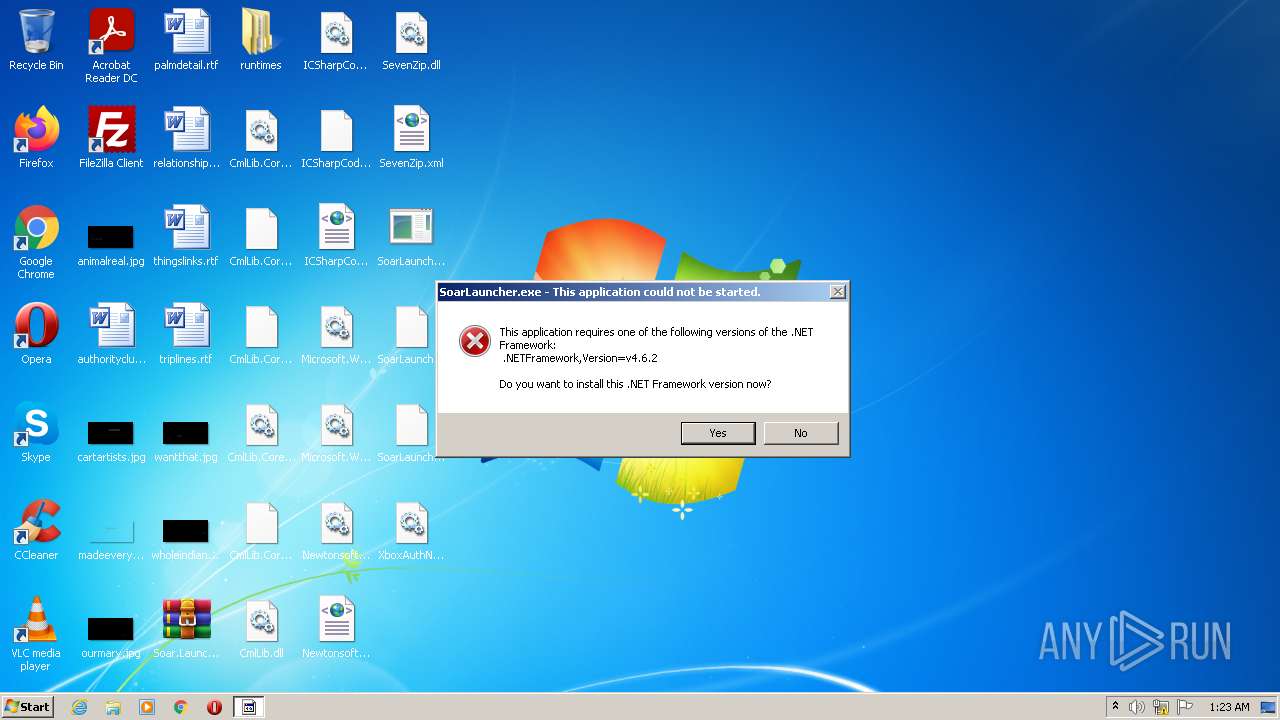
Starts Internet Explorer
- SoarLauncher.exe (PID: 684)
- SoarLauncher.exe (PID: 3428)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 1380)
- iexplore.exe (PID: 2288)
Reads CPU info
- Setup.exe (PID: 1516)
Reads Environment values
- Setup.exe (PID: 1516)
Reads Windows owner or organization settings
- msiexec.exe (PID: 2324)
Reads the Windows organization settings
- msiexec.exe (PID: 2324)
Creates/Modifies COM task schedule object
- msiexec.exe (PID: 2324)
- aspnet_regiis.exe (PID: 2504)
Changes the autorun value in the registry
- msiexec.exe (PID: 2324)
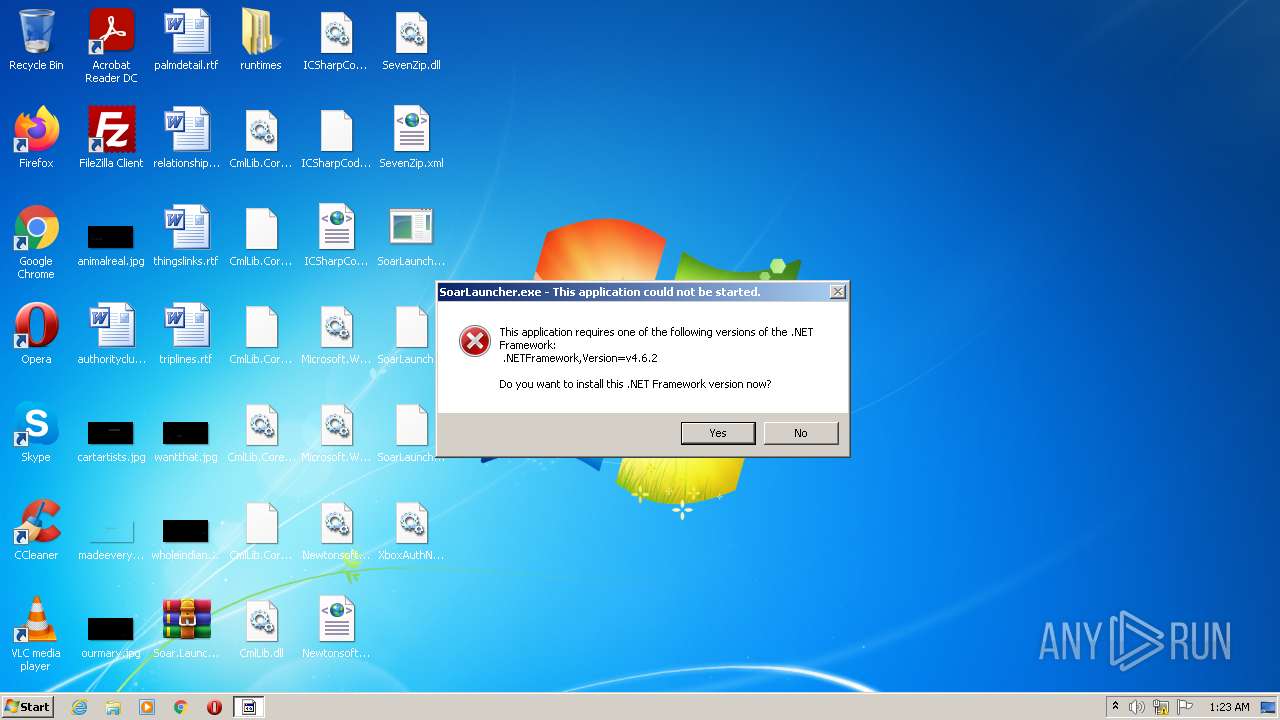
Checks for the .NET to be installed
- msiexec.exe (PID: 2324)
Creates files in the Windows directory
- msiexec.exe (PID: 2324)
- lodctr.exe (PID: 2264)
- aspnet_regiis.exe (PID: 2504)
Removes files from Windows directory
- msiexec.exe (PID: 2324)
- lodctr.exe (PID: 2264)
- aspnet_regiis.exe (PID: 2504)
INFO
Manual execution by user
- SoarLauncher.exe (PID: 684)
- SoarLauncher.exe (PID: 888)
- SoarLauncher.exe (PID: 3428)
Checks supported languages
- iexplore.exe (PID: 1116)
- iexplore.exe (PID: 1380)
- iexplore.exe (PID: 1884)
- iexplore.exe (PID: 2288)
- wevtutil.exe (PID: 3724)
- wevtutil.exe (PID: 3676)
- lodctr.exe (PID: 2264)
Reads the computer name
- iexplore.exe (PID: 1116)
- iexplore.exe (PID: 1380)
- iexplore.exe (PID: 1884)
- iexplore.exe (PID: 2288)
- wevtutil.exe (PID: 3676)
- wevtutil.exe (PID: 3724)
- lodctr.exe (PID: 2264)
Application launched itself
- iexplore.exe (PID: 1116)
- iexplore.exe (PID: 1884)
- msiexec.exe (PID: 2324)
Changes internet zones settings
- iexplore.exe (PID: 1116)
- iexplore.exe (PID: 1884)
Reads settings of System Certificates
- iexplore.exe (PID: 1380)
- iexplore.exe (PID: 1116)
- iexplore.exe (PID: 2288)
- iexplore.exe (PID: 1884)
- Setup.exe (PID: 1516)
- msiexec.exe (PID: 2324)
Checks Windows Trust Settings
- iexplore.exe (PID: 1380)
- iexplore.exe (PID: 1116)
- iexplore.exe (PID: 2288)
- iexplore.exe (PID: 1884)
- Setup.exe (PID: 1516)
- msiexec.exe (PID: 2324)
Creates files in the user directory
- iexplore.exe (PID: 1380)
- iexplore.exe (PID: 2288)
Reads internet explorer settings
- iexplore.exe (PID: 1380)
- iexplore.exe (PID: 2288)
Dropped object may contain Bitcoin addresses
- iexplore.exe (PID: 1116)
- SetupUtility.exe (PID: 3744)
- svchost.exe (PID: 2000)
- Setup.exe (PID: 1516)
- msiexec.exe (PID: 2324)
Adds / modifies Windows certificates
- iexplore.exe (PID: 1116)
Reads the date of Windows installation
- iexplore.exe (PID: 1116)
- iexplore.exe (PID: 1884)
Changes settings of System certificates
- iexplore.exe (PID: 1116)
Modifies the phishing filter of IE
- iexplore.exe (PID: 1884)
Loads dropped or rewritten executable
- MsiExec.exe (PID: 1148)
- MsiExec.exe (PID: 1964)
- msiexec.exe (PID: 2324)
Creates or modifies windows services
- msiexec.exe (PID: 2324)
Searches for installed software
- msiexec.exe (PID: 2324)
Creates a software uninstall entry
- msiexec.exe (PID: 2324)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | CmlLib.Core.Auth.Microsoft.dll |
|---|---|
| ZipUncompressedSize: | 11776 |
| ZipCompressedSize: | 5080 |
| ZipCRC: | 0xc8311ec5 |
| ZipModifyDate: | 2022:05:15 12:15:05 |
| ZipCompression: | Deflated |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 20 |
Total processes
86
Monitored processes
34
Malicious processes
14
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 432 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\regtlibv12.exe" "C:\Windows\Microsoft.NET\Framework\v4.0.30319\Microsoft.JScript.tlb" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\regtlibv12.exe | — | MsiExec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: RegTLib Exit code: 0 Version: 14.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
| 632 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\regtlibv12.exe" "C:\Windows\Microsoft.NET\Framework\v4.0.30319\System.EnterpriseServices.tlb" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\regtlibv12.exe | — | MsiExec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: RegTLib Exit code: 0 Version: 14.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
| 684 | "C:\Users\admin\Desktop\SoarLauncher.exe" | C:\Users\admin\Desktop\SoarLauncher.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Description: SoarLauncher Exit code: 2148734720 Version: 1.0.0.0 Modules
| |||||||||||||||
| 888 | "C:\Users\admin\Desktop\SoarLauncher.exe" | C:\Users\admin\Desktop\SoarLauncher.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Description: SoarLauncher Exit code: 2148734720 Version: 1.0.0.0 Modules
| |||||||||||||||
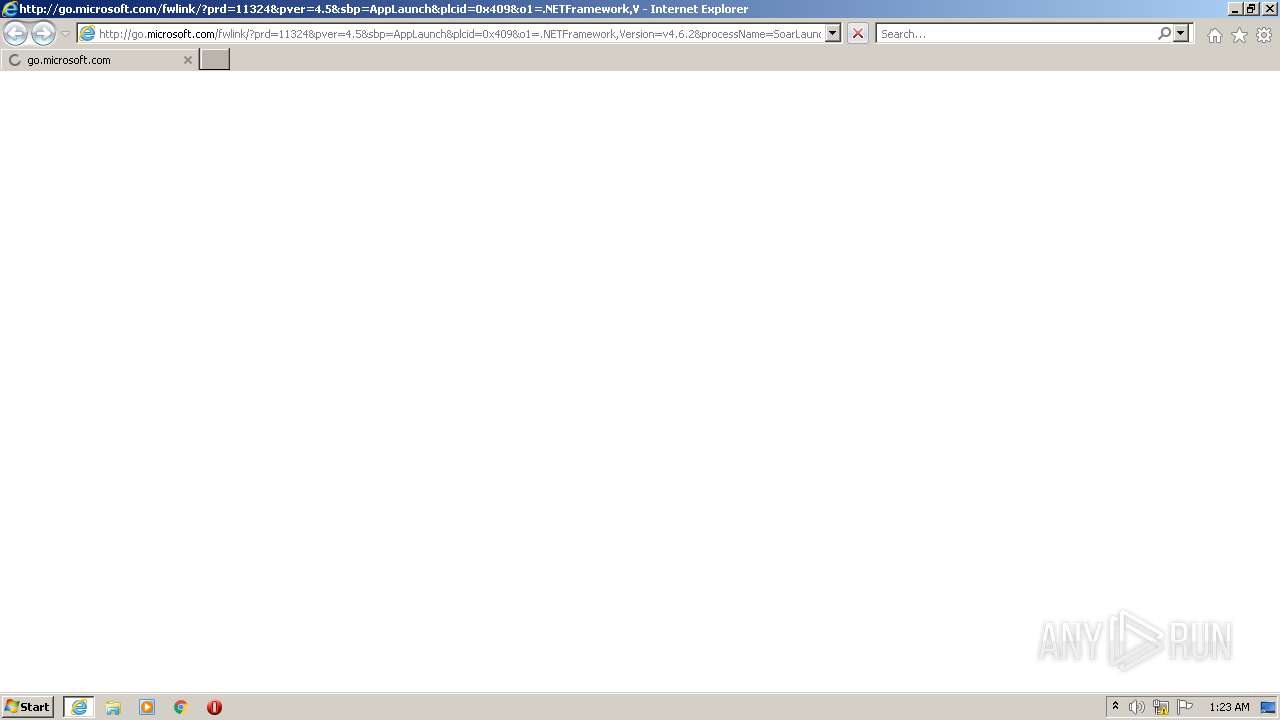
| 1116 | "C:\Program Files\Internet Explorer\iexplore.exe" http://go.microsoft.com/fwlink/?prd=11324&pver=4.5&sbp=AppLaunch&plcid=0x409&o1=.NETFramework,Version=v4.6.2&processName=SoarLauncher.exe&platform=0000&osver=5&isServer=0&shimver=4.0.30319.34209 | C:\Program Files\Internet Explorer\iexplore.exe | SoarLauncher.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
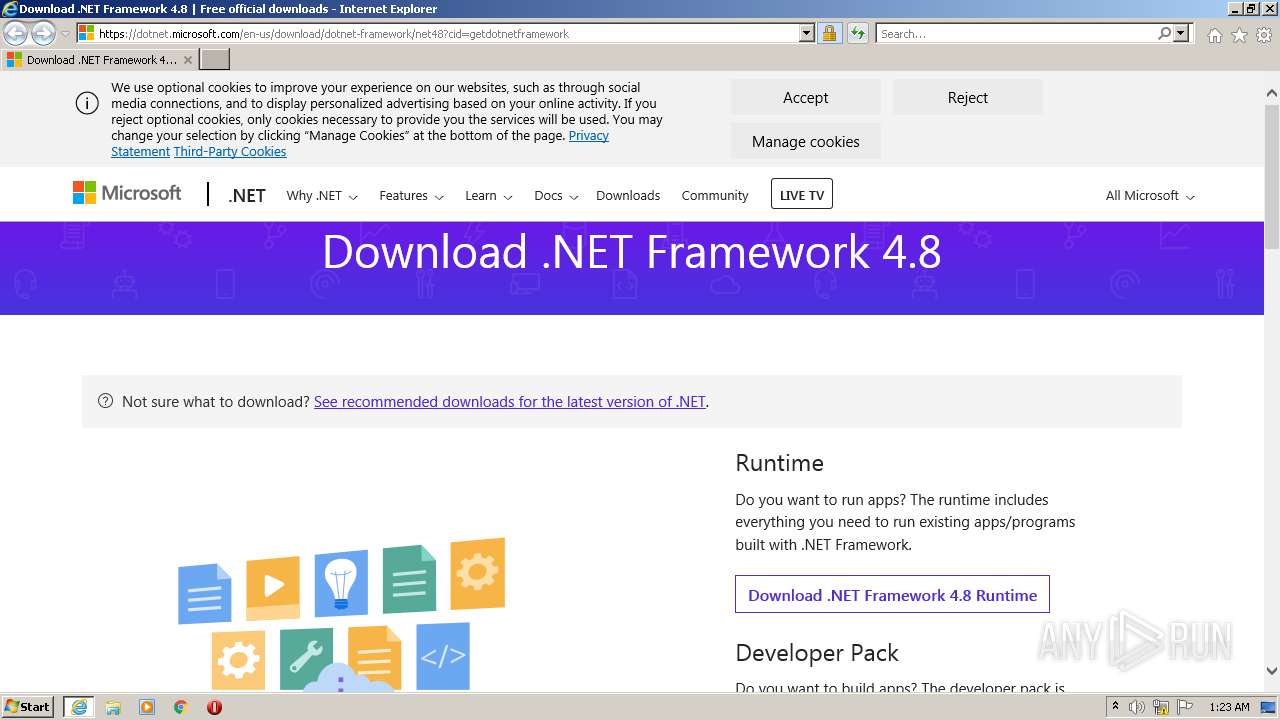
| 1144 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\ndp48-web.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\ndp48-web.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Framework 4.8 Setup Exit code: 3221226540 Version: 4.8.04115.00 Modules
| |||||||||||||||
| 1148 | C:\Windows\system32\MsiExec.exe -Embedding 00D7B68127810371ADA8D989A387DD47 | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1380 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1116 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1516 | C:\45ce8c0674495f90b9869896803a\\Setup.exe /x86 /x64 /web | C:\45ce8c0674495f90b9869896803a\Setup.exe | ndp48-web.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Setup Installer Exit code: 0 Version: 14.8.4110.0 built by: NET48REL1LAST_B Modules
| |||||||||||||||
| 1884 | "C:\Program Files\Internet Explorer\iexplore.exe" http://go.microsoft.com/fwlink/?prd=11324&pver=4.5&sbp=AppLaunch&plcid=0x409&o1=.NETFramework,Version=v4.6.2&processName=SoarLauncher.exe&platform=0000&osver=5&isServer=0&shimver=4.0.30319.34209 | C:\Program Files\Internet Explorer\iexplore.exe | SoarLauncher.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
92 554
Read events
78 785
Write events
12 121
Delete events
1 648
Modification events
| (PID) Process: | (2764) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2764) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2764) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2764) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2764) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2764) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Soar.Launcher.V1.zip | |||
| (PID) Process: | (2764) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2764) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2764) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2764) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
2 298
Suspicious files
78
Text files
449
Unknown types
27
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2764 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2764.21653\CmlLib.Core.Auth.Microsoft.pdb | binary | |
MD5:— | SHA256:— | |||
| 2764 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2764.21653\CmlLib.Core.Auth.Microsoft.dll | executable | |
MD5:— | SHA256:— | |||
| 2764 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2764.21653\CmlLib.Core.Auth.Microsoft.UI.WinForm.dll | executable | |
MD5:— | SHA256:— | |||
| 2764 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2764.21653\CmlLib.Core.Auth.Microsoft.UI.WinForm.pdb | binary | |
MD5:— | SHA256:— | |||
| 2764 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2764.21653\SoarLauncher.exe | executable | |
MD5:— | SHA256:— | |||
| 2764 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2764.21653\SoarLauncher.exe.config | xml | |
MD5:— | SHA256:— | |||
| 2764 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2764.21653\ICSharpCode.SharpZipLib.xml | xml | |
MD5:5C154669300FED0DE91C91B4CC1D8D0A | SHA256:ED45BCBC288668CF5C992A609E81B416832B5CDC972080137C6DD95E4FF368E0 | |||
| 2764 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2764.21653\runtimes\win-x64\native\WebView2Loader.dll | executable | |
MD5:87ABCE99CF0336FA7D874D55FC7D1578 | SHA256:6D0804B37A498A3ECDD317896F6C9E9C759566574E86A8E045FEAD5E9CB20106 | |||
| 2764 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2764.21653\runtimes\win-arm64\native\WebView2Loader.dll | executable | |
MD5:C1C1CDC80DB0DEA9D2E2C8347553B7AB | SHA256:7ACE4A6C7BB2585131C14951C6E6FE270D8067FD481DE718FFA968645BE948E3 | |||
| 2764 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2764.21653\ICSharpCode.SharpZipLib.pdb | binary | |
MD5:779D8237C1BB0A2896B2B8415AB6E556 | SHA256:CEF7890C128FD3D563E0ADEA3BBA414A66542C4563B745896BA4242F279DC6B9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
26
TCP/UDP connections
53
DNS requests
27
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
880 | svchost.exe | GET | 302 | 104.90.179.99:80 | http://go.microsoft.com/fwlink/?prd=11324&pver=netfx&sbp=Net48Rel1&plcid=0x409&clcid=0x409&ar=03761.00&sar=amd64&o1=netfx_Full_x86.msi | NL | — | — | whitelisted |
880 | svchost.exe | HEAD | 302 | 104.90.179.99:80 | http://go.microsoft.com/fwlink/?prd=11324&pver=netfx&sbp=Net48Rel1&plcid=0x409&clcid=0x409&ar=03761.00&sar=x86&o1=netfx_Full.mzz | NL | — | — | whitelisted |
880 | svchost.exe | HEAD | 302 | 104.90.179.99:80 | http://go.microsoft.com/fwlink/?prd=11324&pver=netfx&sbp=Net48Rel1&plcid=0x409&clcid=0x409&ar=03761.00&sar=amd64&o1=netfx_Full_x86.msi | NL | — | — | whitelisted |
1380 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEALnkXH7gCHpP%2BLZg4NMUMA%3D | US | der | 471 b | whitelisted |
1380 | iexplore.exe | GET | 200 | 204.79.197.203:80 | http://oneocsp.microsoft.com/ocsp/MFQwUjBQME4wTDAJBgUrDgMCGgUABBQN1VoiX40jVOMldh7uDThi9DqeewQU1cFnOsKjnfR3UltZEjgp5lVou6UCEzMAHEqTV2OkE3jHH8YAAAAcSpM%3D | US | der | 1.74 Kb | whitelisted |
1380 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
1380 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
1380 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA9bw6F2y3ieICDHiTyBZ7Q%3D | US | der | 1.47 Kb | whitelisted |
1380 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAH9o%2BtuynXIiEOLckvPvJE%3D | US | der | 471 b | whitelisted |
1380 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAH9o%2BtuynXIiEOLckvPvJE%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1380 | iexplore.exe | 104.90.179.99:443 | go.microsoft.com | Akamai Technologies, Inc. | NL | malicious |
1380 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
1380 | iexplore.exe | 13.107.246.45:443 | dotnet.microsoft.com | Microsoft Corporation | US | malicious |
1380 | iexplore.exe | 204.79.197.203:80 | oneocsp.microsoft.com | Microsoft Corporation | US | malicious |
1380 | iexplore.exe | 184.30.21.171:443 | www.microsoft.com | GTT Communications Inc. | US | suspicious |
1380 | iexplore.exe | 92.123.195.75:443 | statics-marketingsites-wcus-ms-com.akamaized.net | Akamai International B.V. | — | unknown |
1380 | iexplore.exe | 152.199.19.161:443 | az416426.vo.msecnd.net | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
1380 | iexplore.exe | 92.123.195.73:443 | img-prod-cms-rt-microsoft-com.akamaized.net | Akamai International B.V. | — | whitelisted |
1116 | iexplore.exe | 13.107.21.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
1380 | iexplore.exe | 20.189.173.2:443 | browser.events.data.microsoft.com | Microsoft Corporation | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
go.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
dotnet.microsoft.com |
| whitelisted |
oneocsp.microsoft.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
statics-marketingsites-wcus-ms-com.akamaized.net |
| whitelisted |
az416426.vo.msecnd.net |
| whitelisted |