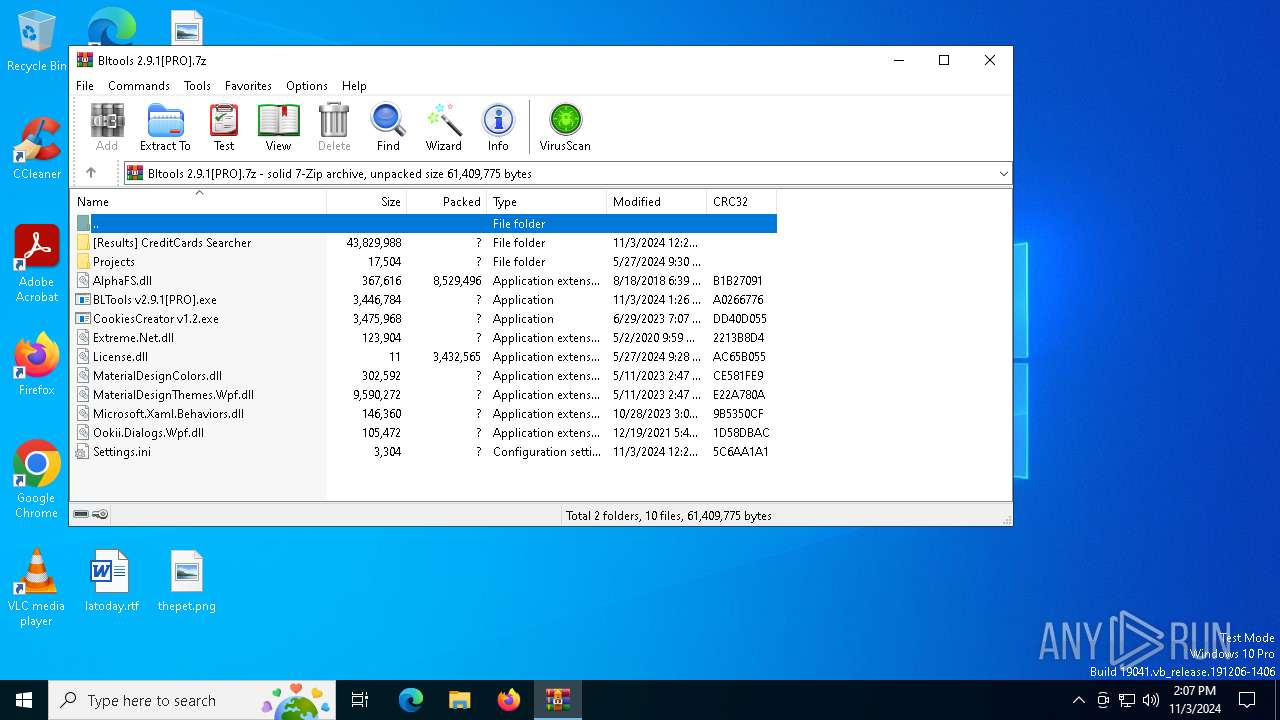
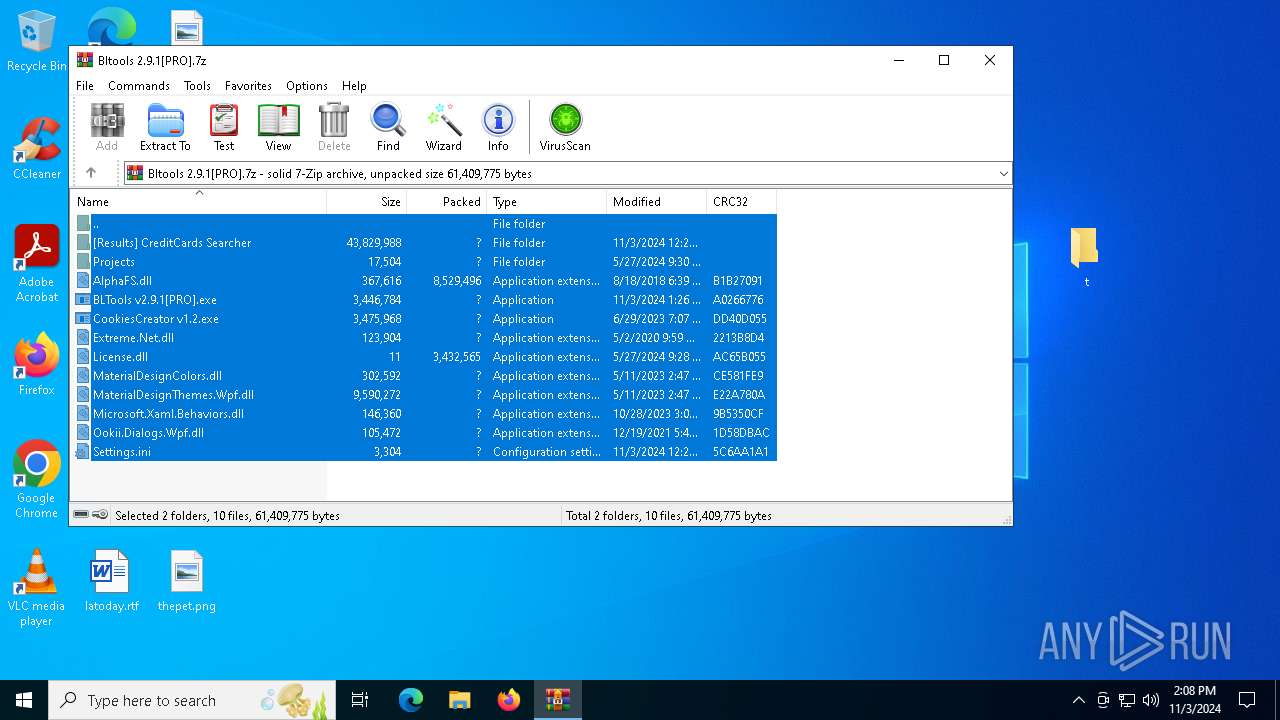
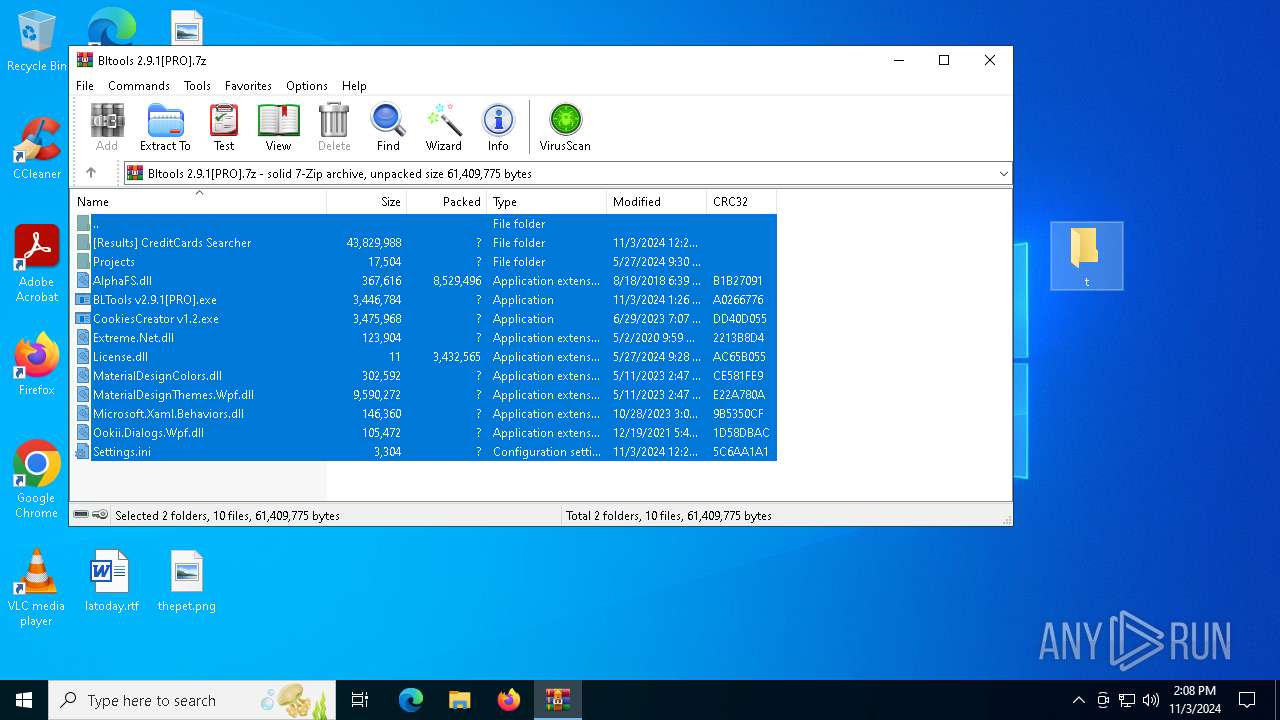
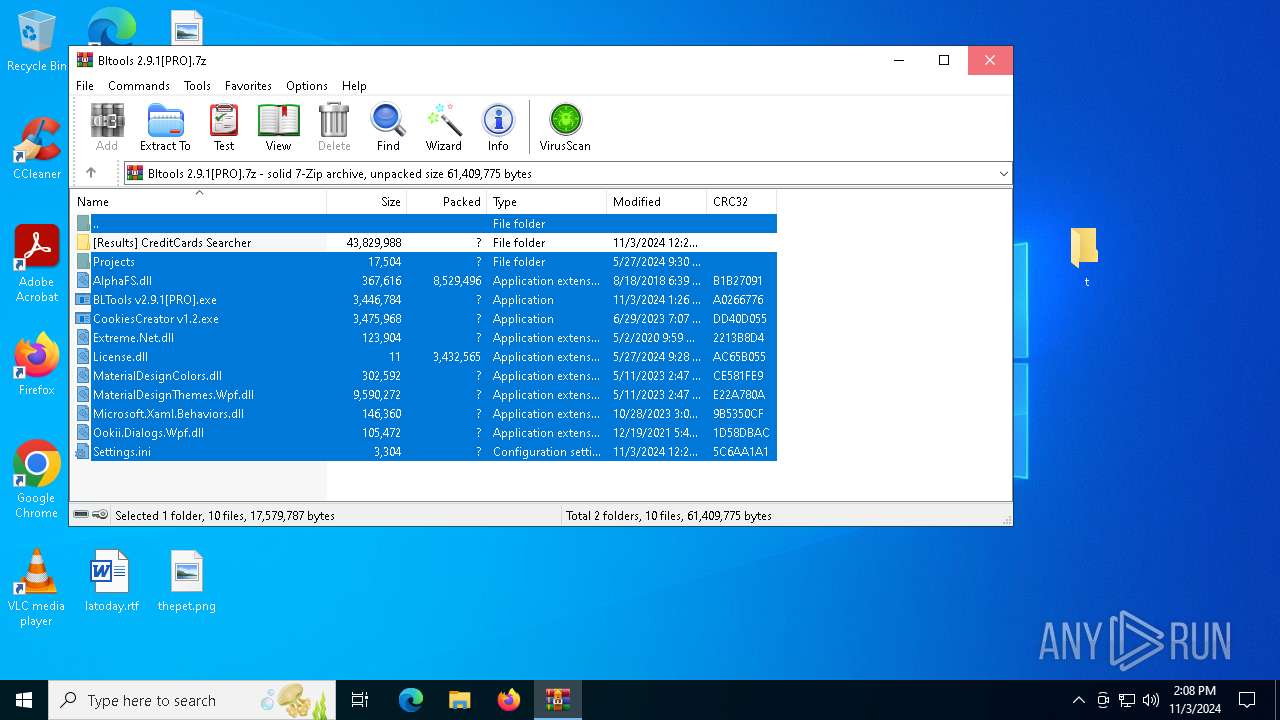
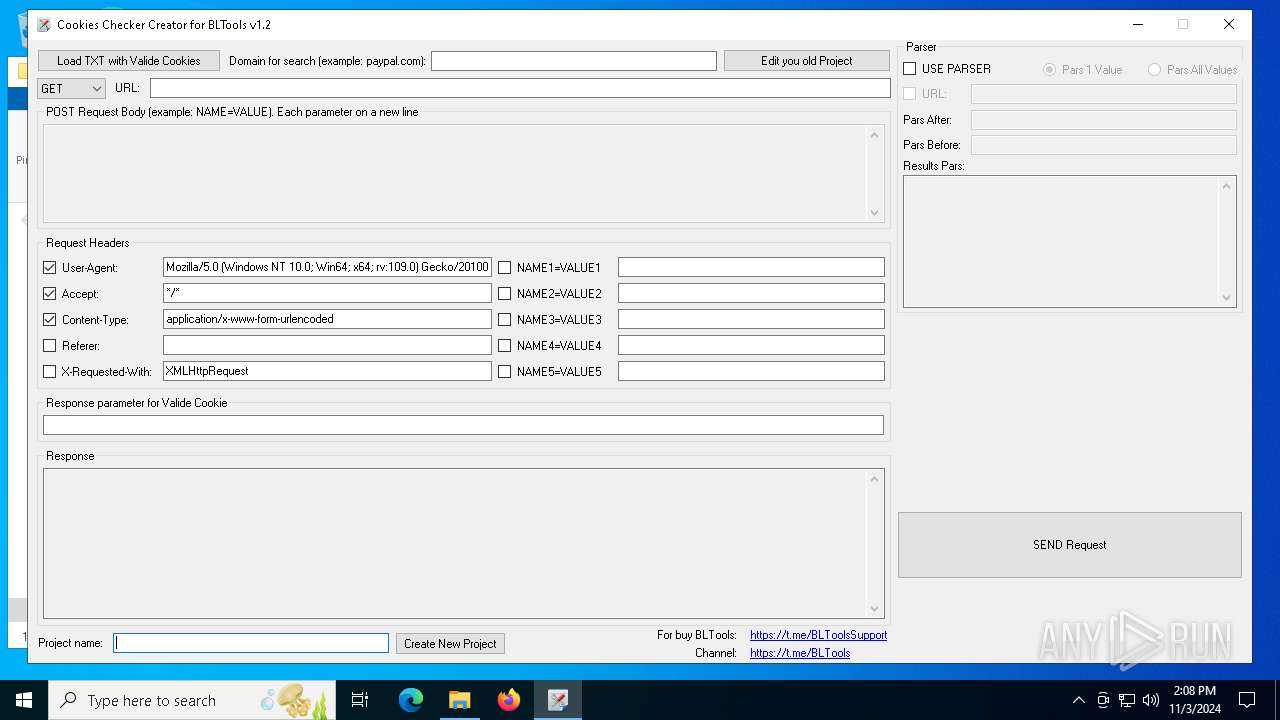
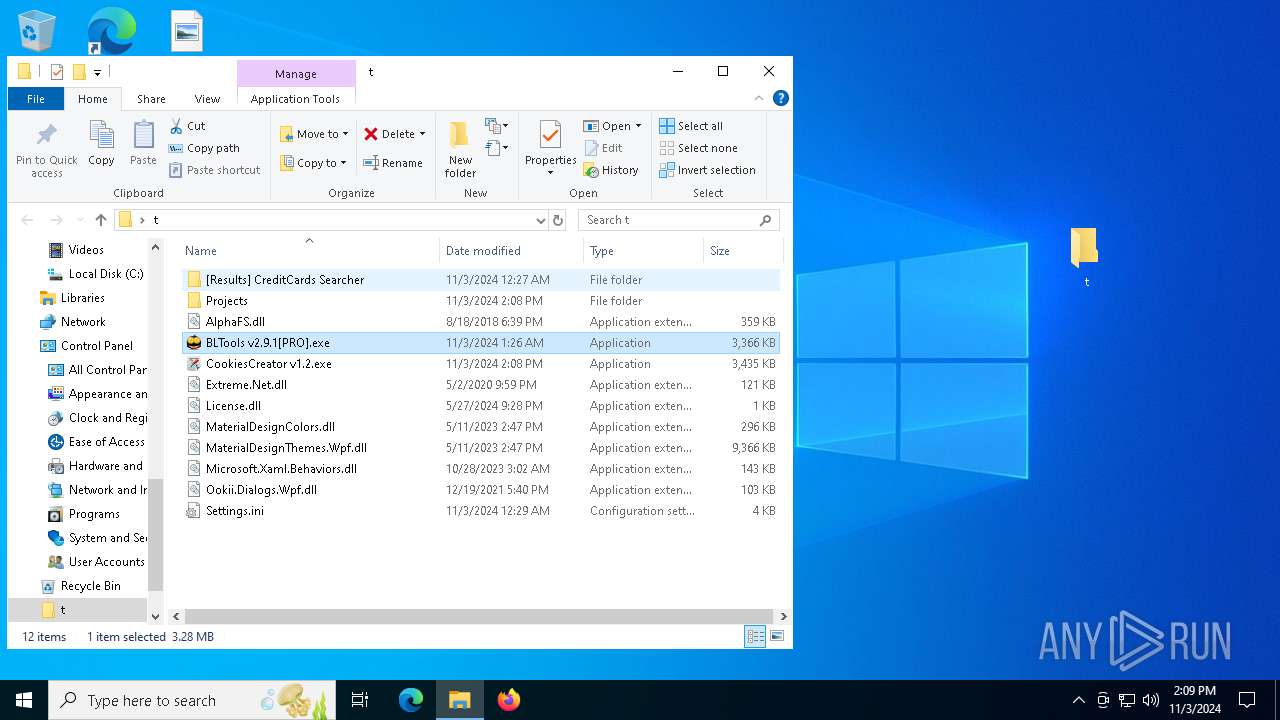
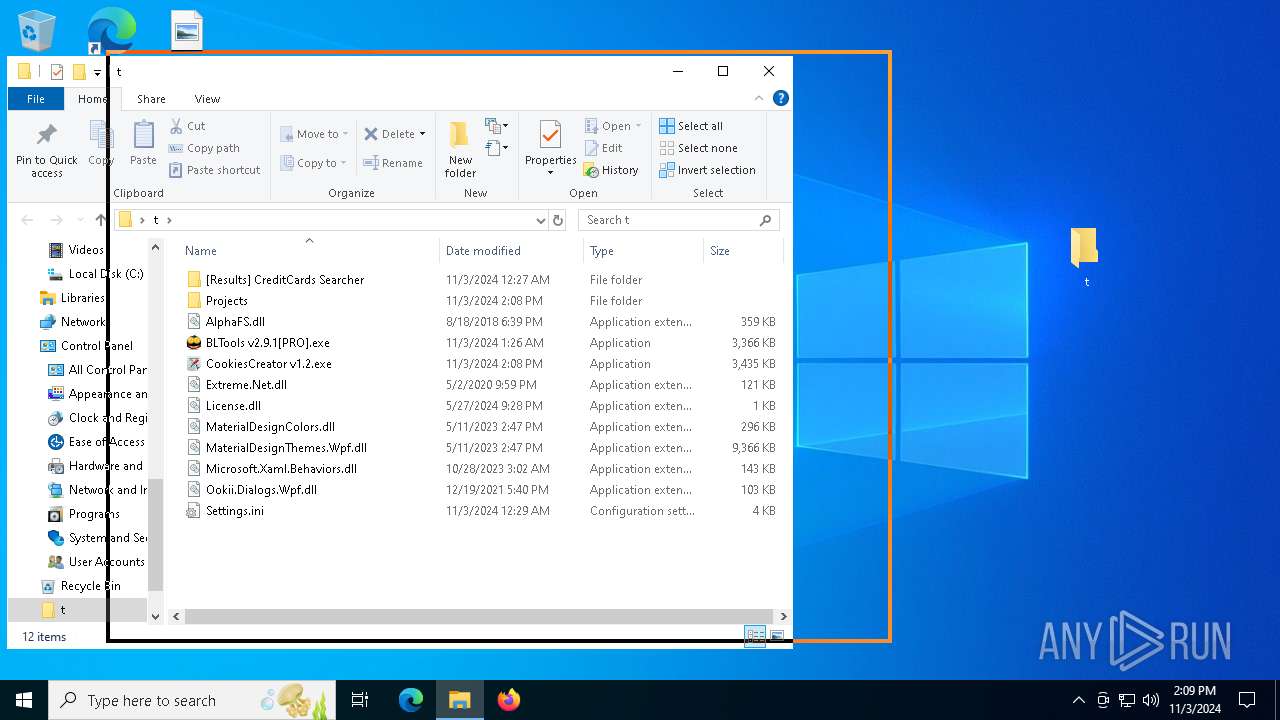
| File name: | Bltools 2.9.1[PRO].7z |
| Full analysis: | https://app.any.run/tasks/6b8e809c-ad98-4706-a955-7c2216a00b22 |
| Verdict: | Malicious activity |
| Analysis date: | November 03, 2024, 14:07:40 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 7711D07A88D364EC16CE541ACCFAEE1D |
| SHA1: | C78D954D3F8EACF972D2197162F3530D22DD2F0E |
| SHA256: | A296054BB4D289773A08C2678625715DC00DC386A11D1C312DEB9BA758F14F96 |
| SSDEEP: | 98304:xRQNnynRKLjwl1TG4VGbSLd4l1jKDgT3tXPyeScaQFWRy1iXhJeYjegAQZfDRThv:xNDKrBLHlEQB7XtG4Z4v5 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Generic archive extractor
- WinRAR.exe (PID: 700)
Process drops legitimate windows executable
- WinRAR.exe (PID: 700)
Executable content was dropped or overwritten
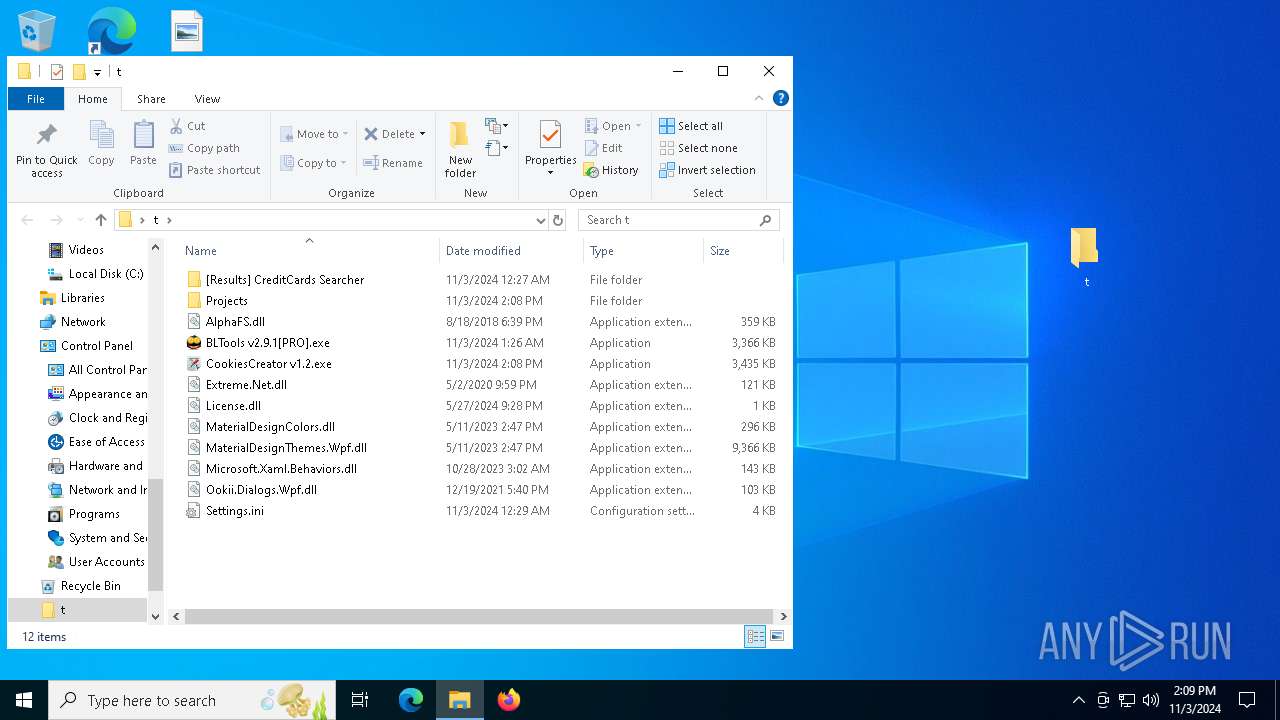
- CookiesCreator v1.2.exe (PID: 2652)
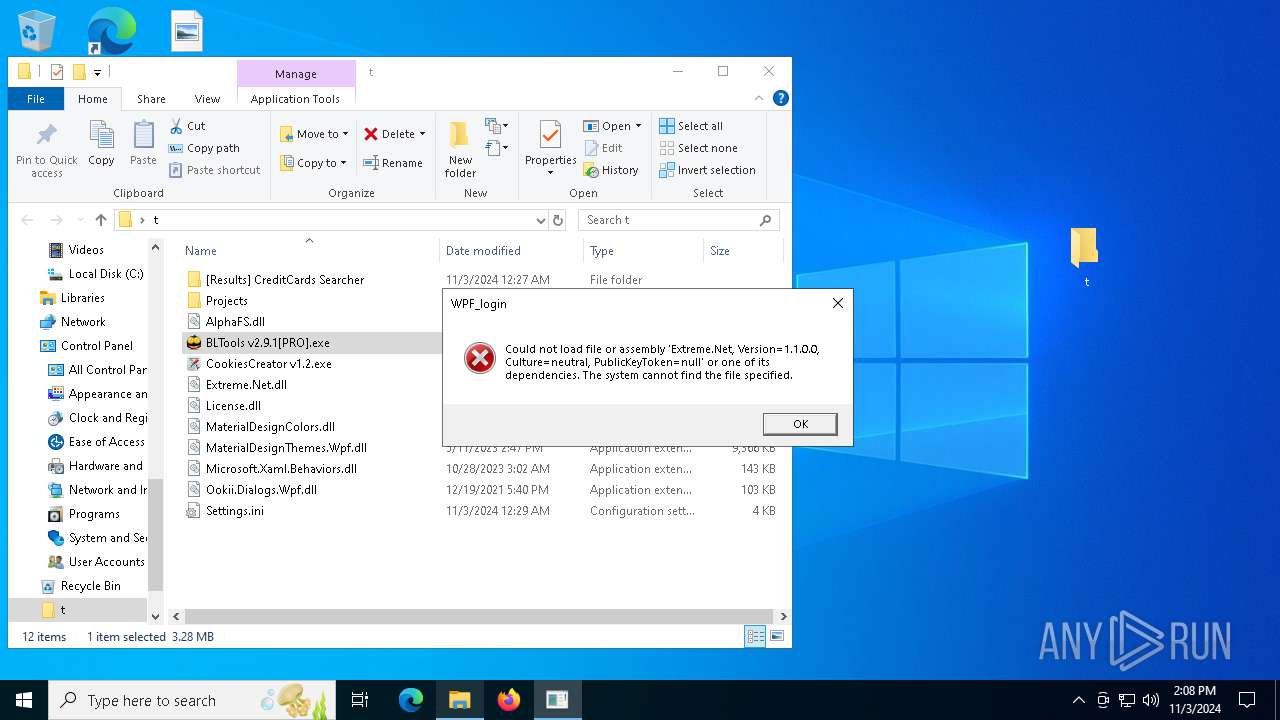
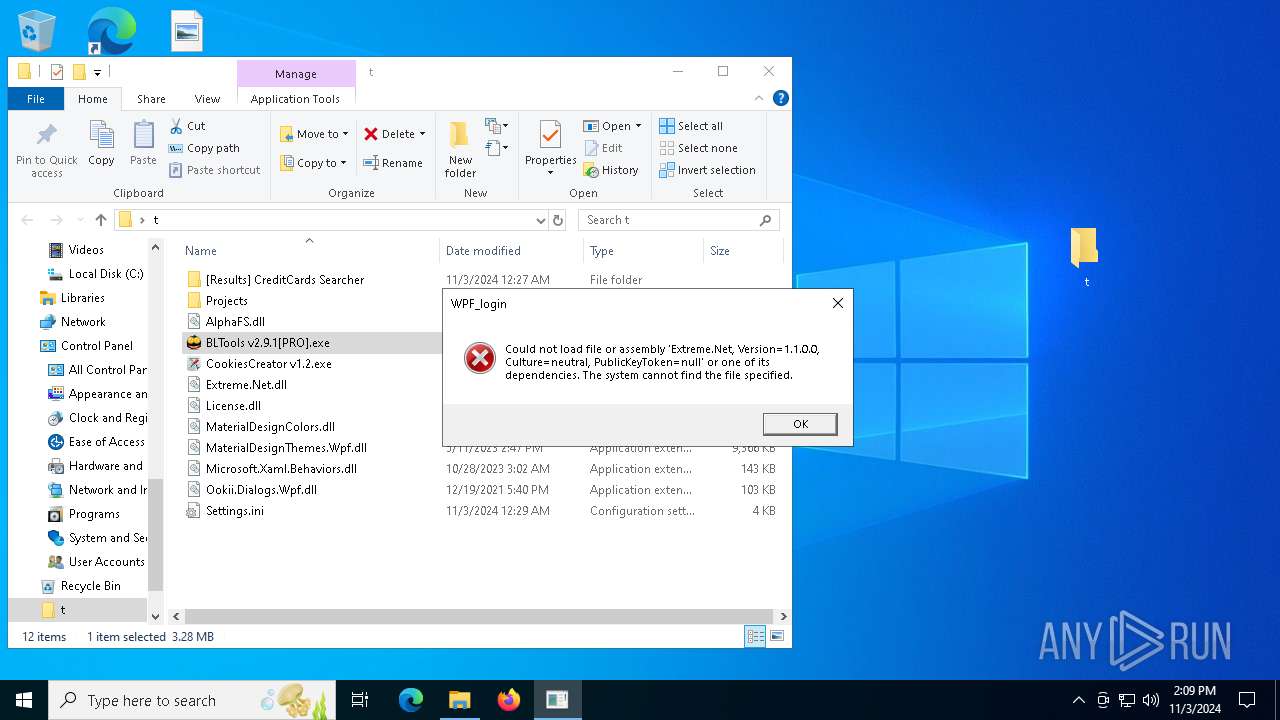
- BLTools v2.9.1[PRO].exe (PID: 3156)
- BLTools v2.9.1[PRO].exe (PID: 2648)
Possible usage of Discord/Telegram API has been detected (YARA)
- BLTools v2.9.1[PRO].exe (PID: 4868)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 700)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 700)
Manual execution by a user
- BLTools v2.9.1[PRO].exe (PID: 3156)
- BLTools v2.9.1[PRO].exe (PID: 2648)
- CookiesCreator v1.2.exe (PID: 2652)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
ims-api
(PID) Process(4868) BLTools v2.9.1[PRO].exe
Telegram-Tokens (1)6448011148:AAHcTB8GjoKK5nZce44buWa2oZ3D7kqBVPk
Telegram-Info-Links
6448011148:AAHcTB8GjoKK5nZce44buWa2oZ3D7kqBVPk
Get info about bothttps://api.telegram.org/bot6448011148:AAHcTB8GjoKK5nZce44buWa2oZ3D7kqBVPk/getMe
Get incoming updateshttps://api.telegram.org/bot6448011148:AAHcTB8GjoKK5nZce44buWa2oZ3D7kqBVPk/getUpdates
Get webhookhttps://api.telegram.org/bot6448011148:AAHcTB8GjoKK5nZce44buWa2oZ3D7kqBVPk/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot6448011148:AAHcTB8GjoKK5nZce44buWa2oZ3D7kqBVPk/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot6448011148:AAHcTB8GjoKK5nZce44buWa2oZ3D7kqBVPk/deleteWebhook?drop_pending_updates=true
Telegram-Requests
Token6448011148:AAHcTB8GjoKK5nZce44buWa2oZ3D7kqBVPk
End-PointsendMessage
Args
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 2024:05:27 21:30:18+00:00 |
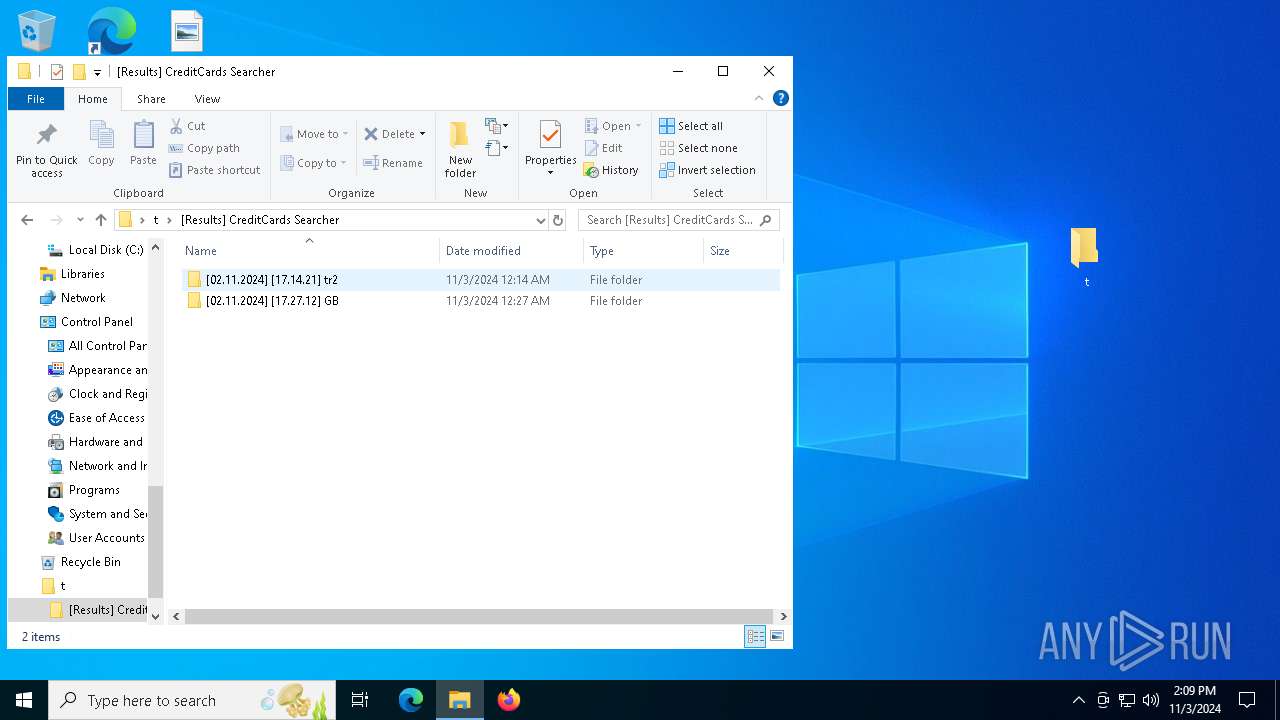
| ArchivedFileName: | Projects |
Total processes
136
Monitored processes
10
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 700 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Bltools 2.9.1[PRO].7z" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
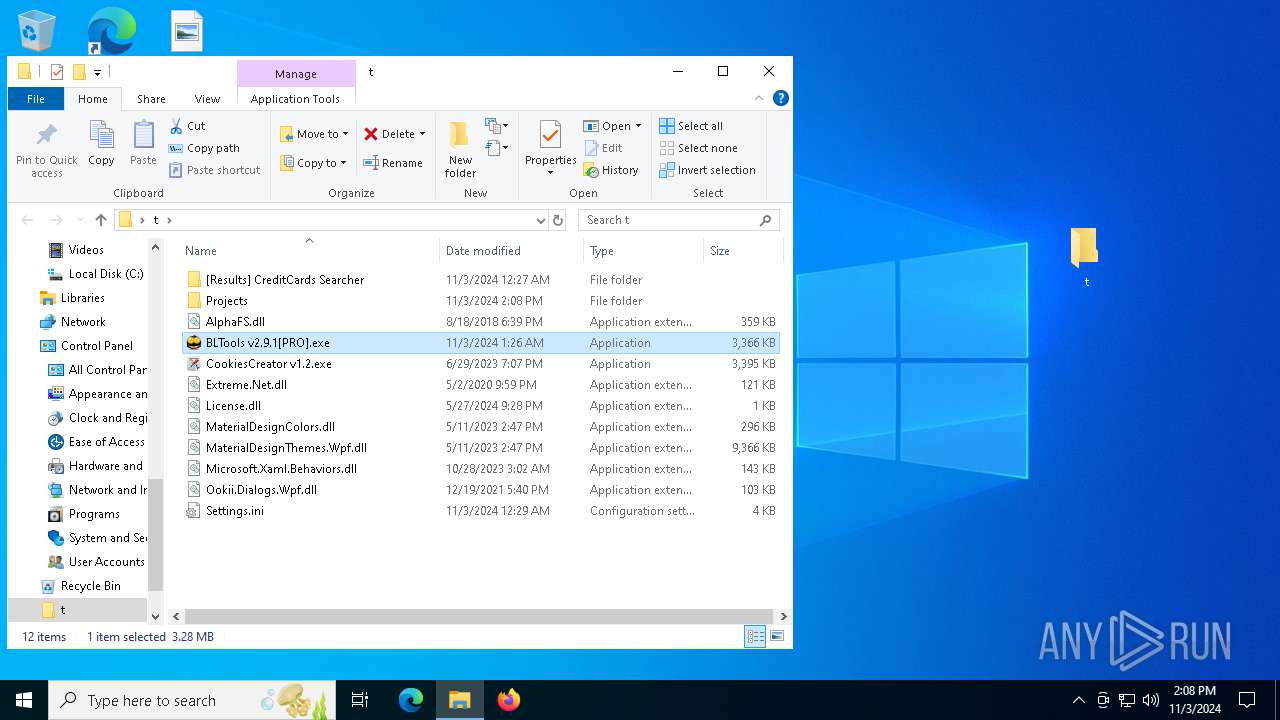
| 2648 | "C:\Users\admin\Desktop\t\BLTools v2.9.1[PRO].exe" | C:\Users\admin\Desktop\t\BLTools v2.9.1[PRO].exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2652 | "C:\Users\admin\Desktop\t\CookiesCreator v1.2.exe" | C:\Users\admin\Desktop\t\CookiesCreator v1.2.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2660 | C:\WINDOWS\explorer.exe /factory,{5BD95610-9434-43C2-886C-57852CC8A120} -Embedding | C:\Windows\explorer.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) | |||||||||||||||
| 3156 | "C:\Users\admin\Desktop\t\BLTools v2.9.1[PRO].exe" | C:\Users\admin\Desktop\t\BLTools v2.9.1[PRO].exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 4448 | "C:\Users\admin\AppData\Local\Temp\3582-490\CookiesCreator v1.2.exe" | C:\Users\admin\AppData\Local\Temp\3582-490\CookiesCreator v1.2.exe | — | CookiesCreator v1.2.exe | |||||||||||
User: admin Company: by boyring Integrity Level: MEDIUM Description: CookiesCreator Exit code: 0 Version: 1.2.0.0 Modules
| |||||||||||||||
| 4868 | "C:\Users\admin\AppData\Local\Temp\3582-490\BLTools v2.9.1[PRO].exe" | C:\Users\admin\AppData\Local\Temp\3582-490\BLTools v2.9.1[PRO].exe | BLTools v2.9.1[PRO].exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: BLTools Cookies Checker Exit code: 1 Version: 2.9.1.0 Modules
ims-api(PID) Process(4868) BLTools v2.9.1[PRO].exe Telegram-Tokens (1)6448011148:AAHcTB8GjoKK5nZce44buWa2oZ3D7kqBVPk Telegram-Info-Links 6448011148:AAHcTB8GjoKK5nZce44buWa2oZ3D7kqBVPk Get info about bothttps://api.telegram.org/bot6448011148:AAHcTB8GjoKK5nZce44buWa2oZ3D7kqBVPk/getMe Get incoming updateshttps://api.telegram.org/bot6448011148:AAHcTB8GjoKK5nZce44buWa2oZ3D7kqBVPk/getUpdates Get webhookhttps://api.telegram.org/bot6448011148:AAHcTB8GjoKK5nZce44buWa2oZ3D7kqBVPk/getWebhookInfo Delete webhookhttps://api.telegram.org/bot6448011148:AAHcTB8GjoKK5nZce44buWa2oZ3D7kqBVPk/deleteWebhook Drop incoming updateshttps://api.telegram.org/bot6448011148:AAHcTB8GjoKK5nZce44buWa2oZ3D7kqBVPk/deleteWebhook?drop_pending_updates=true Telegram-Requests Token6448011148:AAHcTB8GjoKK5nZce44buWa2oZ3D7kqBVPk End-PointsendMessage Args | |||||||||||||||
| 5948 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6588 | C:\WINDOWS\SysWOW64\DllHost.exe /Processid:{06622D85-6856-4460-8DE1-A81921B41C4B} | C:\Windows\SysWOW64\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) | |||||||||||||||
| 7072 | "C:\Users\admin\AppData\Local\Temp\3582-490\BLTools v2.9.1[PRO].exe" | C:\Users\admin\AppData\Local\Temp\3582-490\BLTools v2.9.1[PRO].exe | — | BLTools v2.9.1[PRO].exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: BLTools Cookies Checker Exit code: 1 Version: 2.9.1.0 Modules
| |||||||||||||||
Total events
5 077
Read events
5 061
Write events
16
Delete events
0
Modification events
| (PID) Process: | (700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Bltools 2.9.1[PRO].7z | |||
| (PID) Process: | (700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | psize |
Value: 80 | |||
Executable files
17
Suspicious files
45
Text files
493
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa700.19480\Projects\carousell_MY.proj | text | |
MD5:A7DC8AAB3EFB58C1A60353B56CE70C1E | SHA256:8DD192EAC540FB29B60327B3A911CF27C13E846924B2BD83D7D2534DCEC69E8B | |||
| 700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa700.19480\Projects\Etsy.proj | text | |
MD5:7044889592BA5079CC545F9026317CF2 | SHA256:649ADB7B32110F4A158549B7BFB48F6712E04BA02952EA51F947C263D193FB7F | |||
| 700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa700.19480\Projects\2dehands.be.proj | text | |
MD5:C83ECFBF6D3A250D9D928DF23D069E0C | SHA256:8F63F6C77EED61B0698665F1FCA117B77C7807384310E50C29194D2A3D822689 | |||
| 700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa700.19480\Projects\carousell_SG.proj | text | |
MD5:C9E038B00F09D559AE137ADAFFD1BA91 | SHA256:EBB25FBF252E0769D66447F885B2B047DFFCD3EEFD715300E5978F1BA13B4F17 | |||
| 700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa700.19480\Projects\Ebay.proj | text | |
MD5:A57E89250A50C010B2B6EDD2EFD0B39F | SHA256:51314174405FE1D723621C67C12C03550426F07A83DDCAB9E36E6D992498D899 | |||
| 700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa700.19480\Projects\Office365.proj | text | |
MD5:3366C42396C1CD1C22CB7E7A0AD73888 | SHA256:30160CDC6EAAD941EA0EE5E231DA3286CDC54026763F0F4D0159F06D363604EB | |||
| 700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa700.19480\License.dll | text | |
MD5:D76BF73F3D3768A4589E72A7B2B83088 | SHA256:EAAB53F4B23C3CC9E3C9D4D5D4689438146519E69C7063F4F15B0A43DD861F7B | |||
| 700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa700.19480\Projects\finn.no.proj | html | |
MD5:B8C4F5D353086244CE76FFA07FBB0AF0 | SHA256:CD35AD207032BF3937B6DCC05CB58F9602D5ABAD3402A1A5E96F2172F47764FE | |||
| 700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa700.19480\Projects\otto.de.proj | text | |
MD5:EEB103CCFB368A4416529080DEE90398 | SHA256:BB442306B2AD57A7E1C56D081F9294BB53759184DFF93E478FA0D4751BB940D9 | |||
| 700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa700.19480\Projects\njuskalo.hr.proj | text | |
MD5:4917107F6C496D8B34142302012C1E3E | SHA256:E63A4F090FEEE04B2A396586073A9E8CFC646DE0DF52384773F2F768827E00FD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
38
DNS requests
21
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.164.106:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.32.185.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6740 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
2364 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2684 | SIHClient.exe | GET | 200 | 23.32.185.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2684 | SIHClient.exe | GET | 200 | 23.32.185.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5488 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.16.164.106:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 23.32.185.131:80 | www.microsoft.com | AKAMAI-AS | BR | whitelisted |
4360 | SearchApp.exe | 2.23.209.160:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
6944 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6944 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |