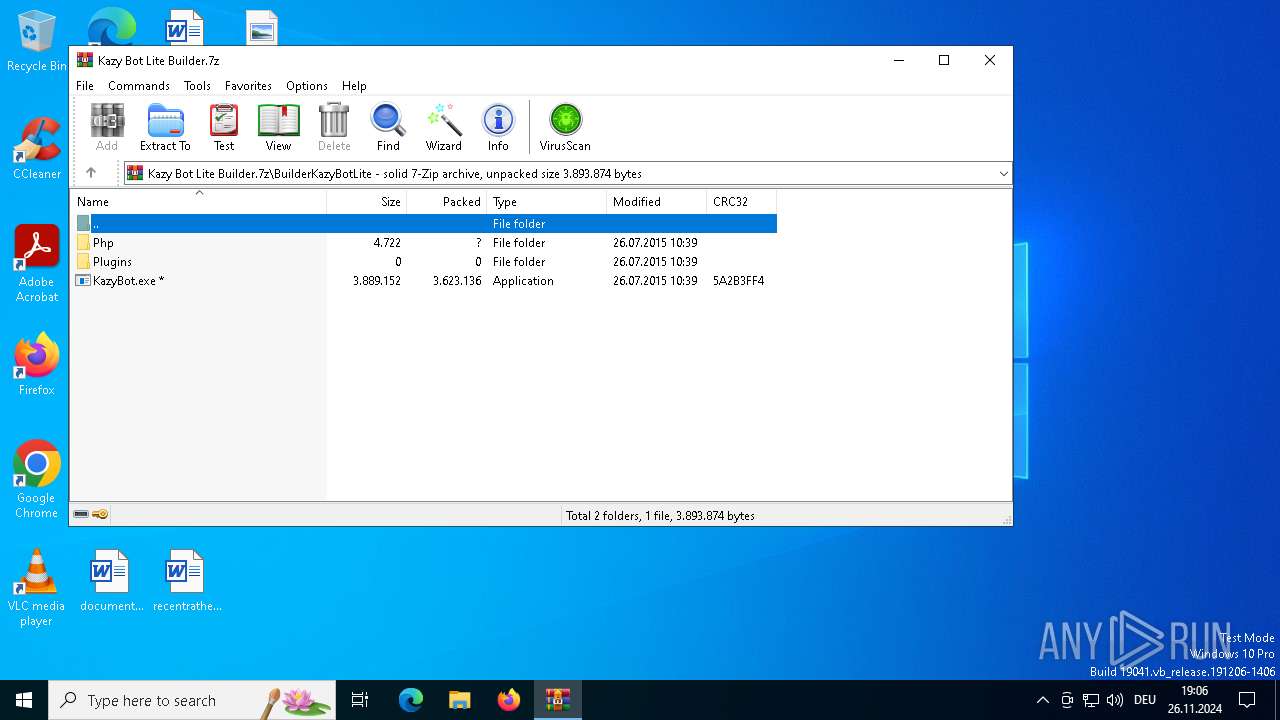
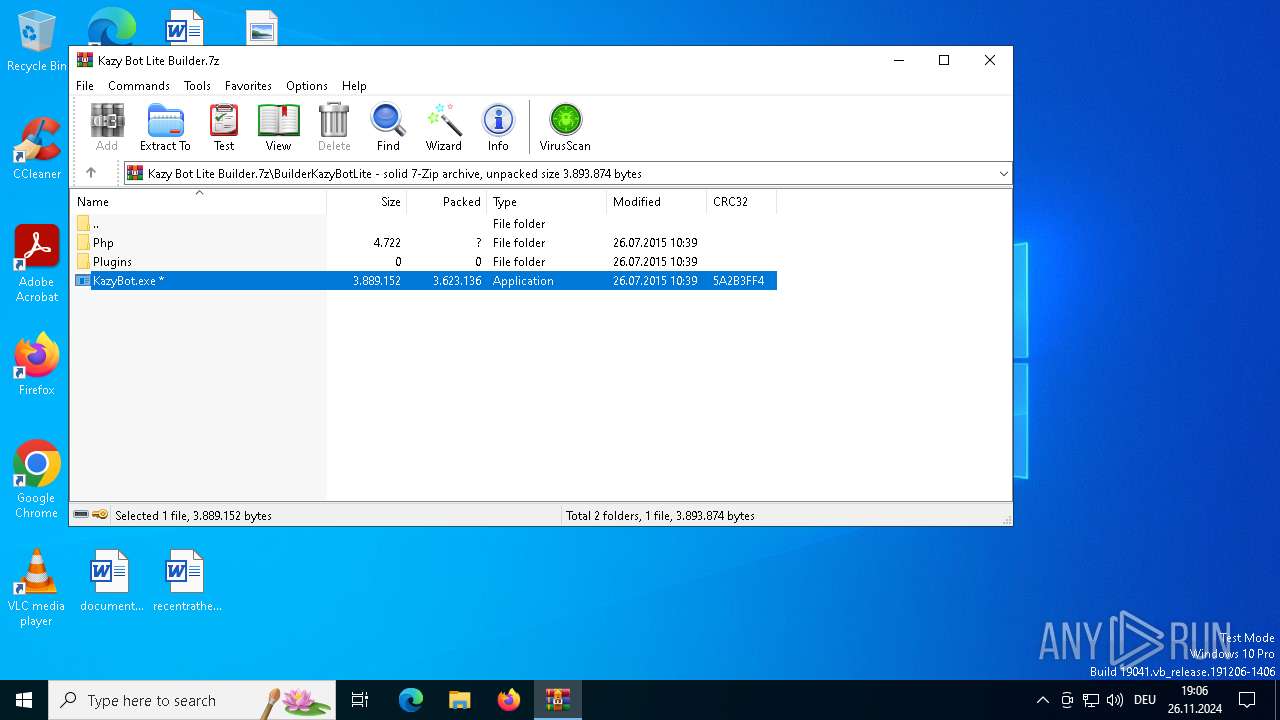
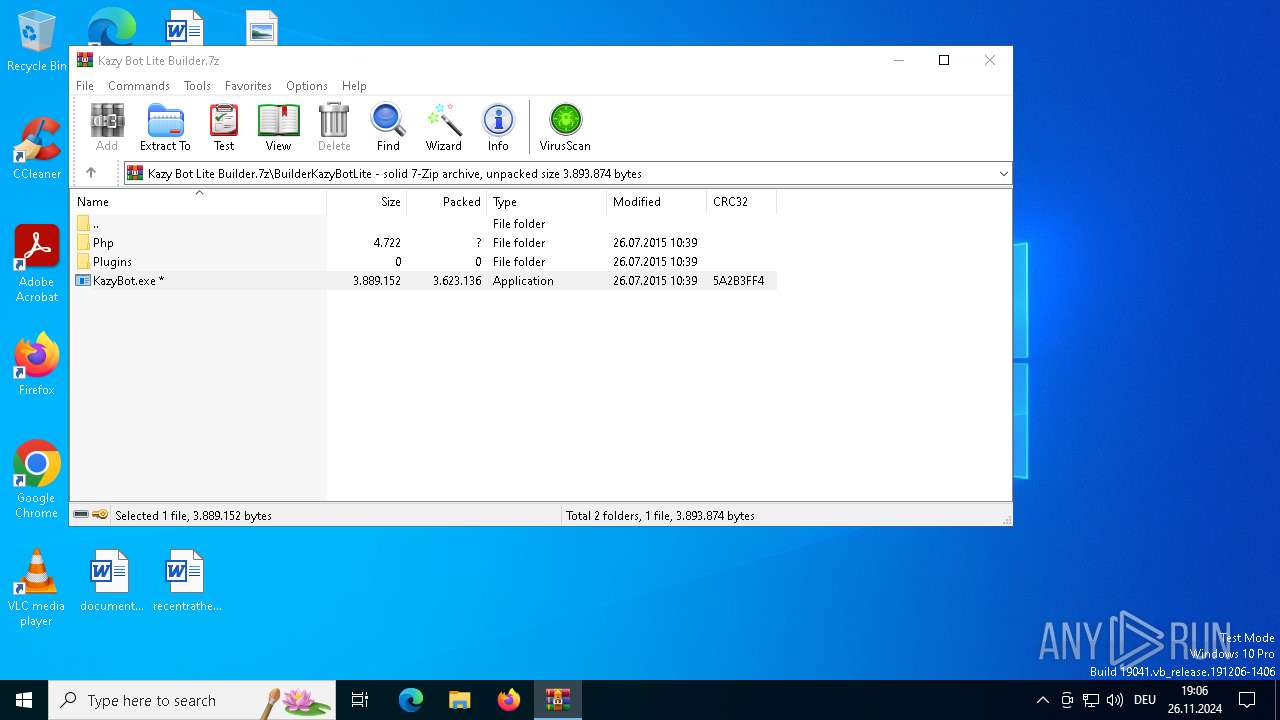
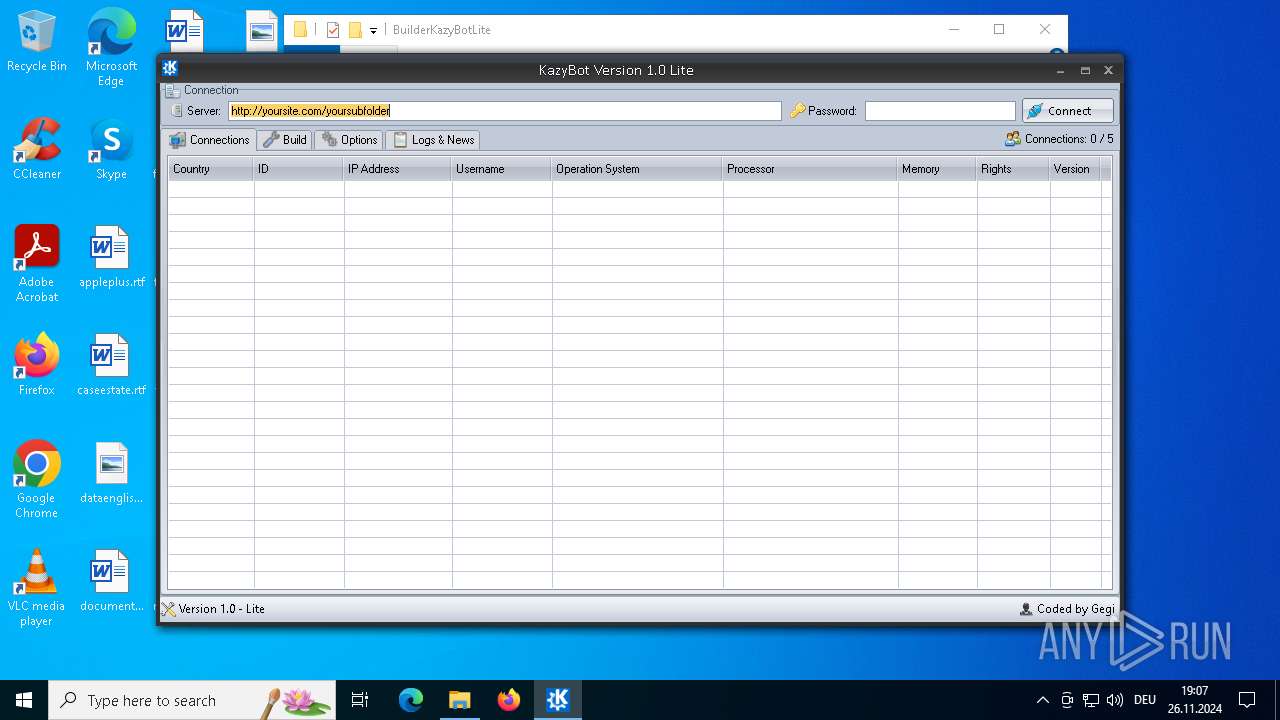
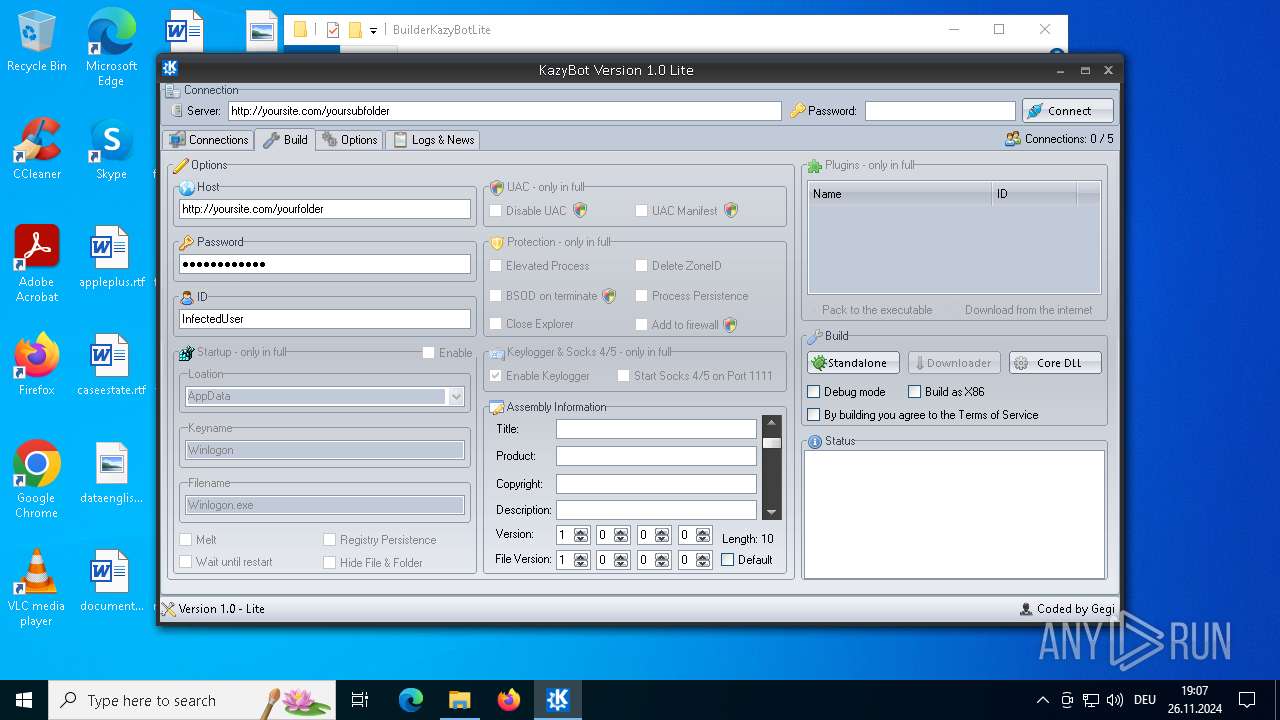
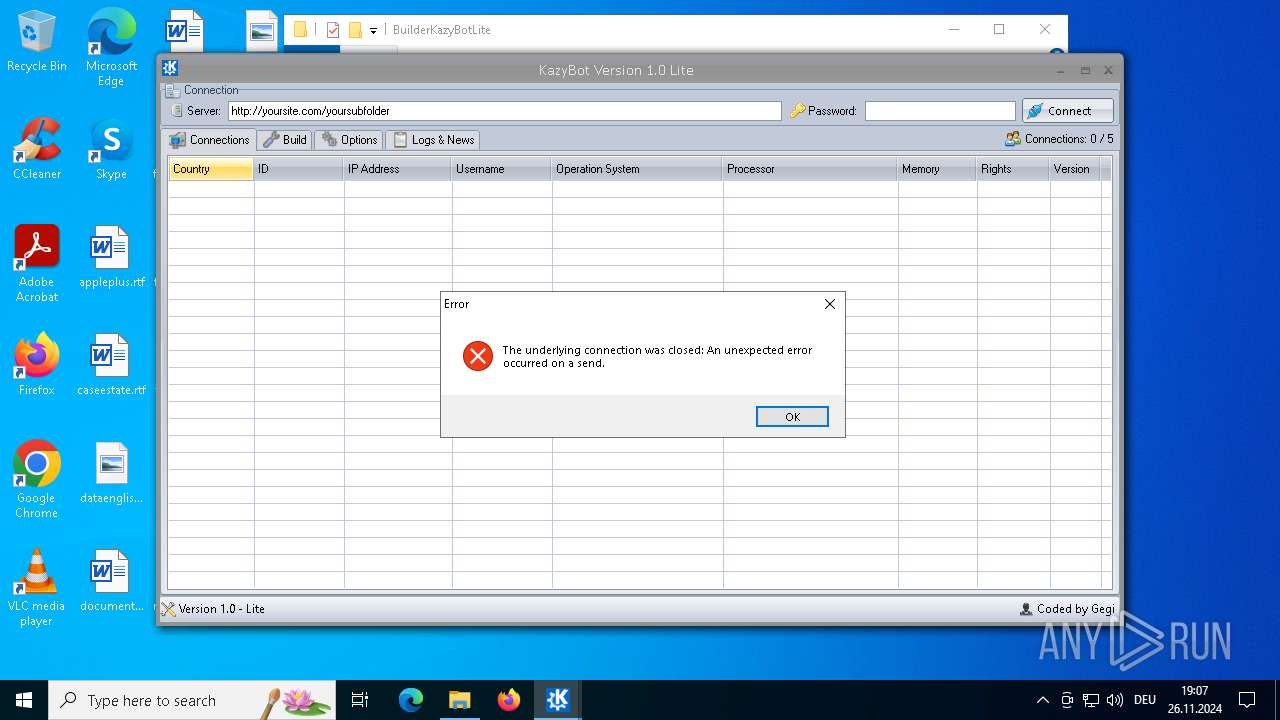
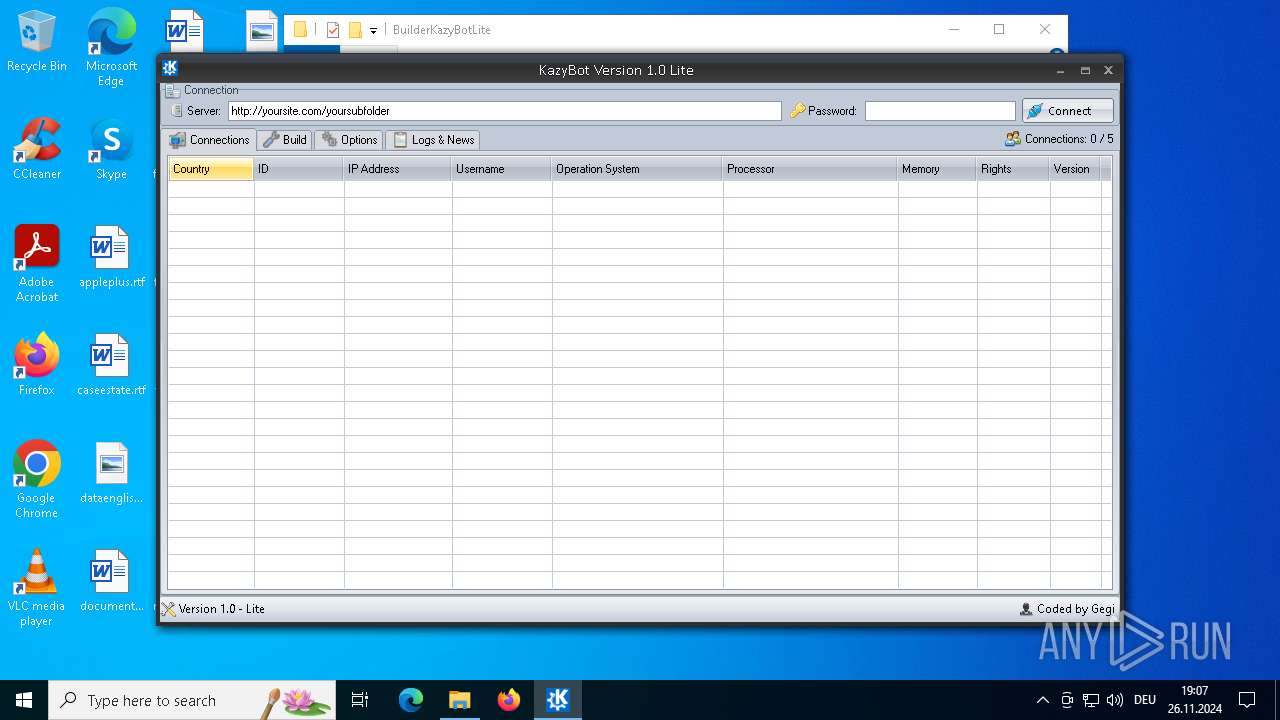
| File name: | Kazy Bot Lite Builder.7z |
| Full analysis: | https://app.any.run/tasks/b13893d7-f064-4706-a720-ab07b02612cb |
| Verdict: | Malicious activity |
| Analysis date: | November 26, 2024, 18:06:31 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | FB774614F3D5ACD38134746475C17A4F |
| SHA1: | E263015EE0698BB464F868BD86B6FE1E4C384438 |
| SHA256: | A25958672C2DEC8EFD37F353F0DB66EED662338566EBFC790BC3EBBFCBB0C433 |
| SSDEEP: | 98304:euusPJg9scnomQtgKZUykJMiOg4EWWEIl/kSWxDwClvwBBLdHkd8xU3mHY6wM3Nq:vvJvckTt |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3140)
Executable content was dropped or overwritten
- KazyBot.exe (PID: 4592)
There is functionality for taking screenshot (YARA)
- KazyBot.exe (PID: 4592)
The process connected to a server suspected of theft
- KazyBot.exe (PID: 4592)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4740)
- WinRAR.exe (PID: 3140)
.NET Reactor protector has been detected
- KazyBot.exe (PID: 4592)
The process uses the downloaded file
- WinRAR.exe (PID: 3140)
Confuser has been detected (YARA)
- KazyBot.exe (PID: 4592)
Manual execution by a user
- WinRAR.exe (PID: 4740)
UPX packer has been detected
- KazyBot.exe (PID: 4592)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|
Total processes
111
Monitored processes
4
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3140 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Kazy Bot Lite Builder.7z" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 4592 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb3140.22332\BuilderKazyBotLite\KazyBot.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb3140.22332\BuilderKazyBotLite\KazyBot.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: KazyBot Version: 1.0.0.0 Modules
| |||||||||||||||
| 4740 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\Kazy Bot Lite Builder.7z" C:\Users\admin\Desktop\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 5252 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
2 543
Read events
2 505
Write events
38
Delete events
0
Modification events
| (PID) Process: | (3140) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (3140) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (3140) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (3140) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (3140) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Kazy Bot Lite Builder.7z | |||
| (PID) Process: | (3140) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3140) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3140) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3140) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3140) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
Executable files
3
Suspicious files
0
Text files
14
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3140 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3140.22332\BuilderKazyBotLite\Php\users.php | text | |
MD5:D819248634F0856C4BA56DB15CC4C333 | SHA256:18E335E0F6F6CCC8F59962B35ED08B62F4917F6E551F5DB65FD2AFEAD36E1B0D | |||
| 3140 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3140.22332\BuilderKazyBotLite\Php\getdata.php | text | |
MD5:0FFA9FA97979E0BCAC27561BF3676BFA | SHA256:AE691991599D686EF5A2254777872E30B8ABE57C1261D42E083708B3391D16E7 | |||
| 4740 | WinRAR.exe | C:\Users\admin\Desktop\BuilderKazyBotLite\Php\add.php | text | |
MD5:EE25D4ACA2E21BA572BD9C448F09315E | SHA256:14A6A26D65168C4A9C8CE19903A8EA78311542BC99C8D79E7331F4B60594D5AF | |||
| 4740 | WinRAR.exe | C:\Users\admin\Desktop\BuilderKazyBotLite\Php\getdata.php | text | |
MD5:0FFA9FA97979E0BCAC27561BF3676BFA | SHA256:AE691991599D686EF5A2254777872E30B8ABE57C1261D42E083708B3391D16E7 | |||
| 3140 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3140.22332\BuilderKazyBotLite\Php\kazybot.sql | text | |
MD5:F4C55C88A8EA3D88CEA4FCBB3E07A58B | SHA256:76C5EEF061A420B010965BF77EB5B71136E86596B8296CF941DEF3656921C969 | |||
| 3140 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3140.22332\BuilderKazyBotLite\KazyBot.exe | executable | |
MD5:0CBDEAF27E298C9CD50EDC7DCEB34FE2 | SHA256:ED5E53C713EA77C67D988291475EB5A3E60B9ABAAEA280FBE2656E3F43A06160 | |||
| 4740 | WinRAR.exe | C:\Users\admin\Desktop\BuilderKazyBotLite\Php\data.php | text | |
MD5:303BE21C9B3A4A060B1FAF80159209B2 | SHA256:6F36F51E4F9899976BF8D1CF1AE5B3AA8B1632EFF533F2A5300682483EAA257E | |||
| 4740 | WinRAR.exe | C:\Users\admin\Desktop\BuilderKazyBotLite\Php\login.php | text | |
MD5:30FF72145A430127230DA2A8B1769043 | SHA256:14C2B10B6C8254D3C1F27724DE03065FD42E5D62D76542081E1F18D5124174B8 | |||
| 4740 | WinRAR.exe | C:\Users\admin\Desktop\BuilderKazyBotLite\Php\kazybot.sql | text | |
MD5:F4C55C88A8EA3D88CEA4FCBB3E07A58B | SHA256:76C5EEF061A420B010965BF77EB5B71136E86596B8296CF941DEF3656921C969 | |||
| 4740 | WinRAR.exe | C:\Users\admin\Desktop\BuilderKazyBotLite\Php\settings.php | text | |
MD5:C241D62D818E98F515F04CE609251A1E | SHA256:5316B9FE834812AA1711A07F3BE8F307C6717412FA5A8893D1EACBD285F79C69 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
30
DNS requests
8
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.53.42.33:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.37.237.227:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4592 | KazyBot.exe | POST | 301 | 104.143.9.110:80 | http://yoursite.com/yoursubdir/login.php | unknown | — | — | malicious |
4592 | KazyBot.exe | POST | 301 | 104.143.9.110:80 | http://yoursite.com/yoursubdir/login.php | unknown | — | — | malicious |
4592 | KazyBot.exe | POST | 301 | 104.143.9.110:80 | http://yoursite.com/yoursubdir/login.php | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.16.204.153:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.53.42.33:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.37.237.227:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4592 | KazyBot.exe | 104.143.9.110:80 | yoursite.com | TP | US | malicious |
4592 | KazyBot.exe | 64.190.63.222:443 | www.yourcompany.com | SEDO GmbH | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
yoursite.com |
| malicious |
www.yourcompany.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4592 | KazyBot.exe | Successful Credential Theft Detected | ET HUNTING Suspicious HTTP POST Only Containing Password - Possible Phishing |
4592 | KazyBot.exe | Successful Credential Theft Detected | ET HUNTING Suspicious HTTP POST Only Containing Password - Possible Phishing |
4592 | KazyBot.exe | Successful Credential Theft Detected | ET HUNTING Suspicious HTTP POST Only Containing Password - Possible Phishing |