| File name: | Windows Loader 2.2.2 by Daz.rar |
| Full analysis: | https://app.any.run/tasks/73d73361-91b1-4e2e-ad8e-6df2eb29da1c |
| Verdict: | Malicious activity |
| Analysis date: | June 02, 2024, 15:53:35 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | 648BA0D75B726E29ACF4E7A372D29DD9 |
| SHA1: | FDBFBBD51887AAE295A6C87621E94F7F0F5D320B |
| SHA256: | A2511F4D76A101305D5B10648320D1AB64ADFC099F0CEDA8C52B21619D19BAB5 |
| SSDEEP: | 49152:lwh3gi6ttnRxdlkB4woZLj66B+DfaJ1aDO+QvQoXVGBFuxmMtzhr/gTQhMXaQJHP:iii6t7vlkBr4Lp+DyJQaooXViE/fdQxb |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3956)
Opens a text file (SCRIPT)
- cscript.exe (PID: 1928)
- cscript.exe (PID: 2020)
SUSPICIOUS
Reads the BIOS version
- Windows Loader.exe (PID: 1876)
Application launched itself
- cmd.exe (PID: 1836)
- cmd.exe (PID: 616)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 616)
- cmd.exe (PID: 1836)
- Windows Loader.exe (PID: 1876)
Takes ownership (TAKEOWN.EXE)
- cmd.exe (PID: 1588)
- cmd.exe (PID: 1852)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 2240)
- cmd.exe (PID: 1988)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- cscript.exe (PID: 1928)
- cscript.exe (PID: 2020)
The process executes VB scripts
- cmd.exe (PID: 824)
- cmd.exe (PID: 2512)
Creates FileSystem object to access computer's file system (SCRIPT)
- cscript.exe (PID: 1928)
- cscript.exe (PID: 2020)
Checks whether a specific file exists (SCRIPT)
- cscript.exe (PID: 1928)
- cscript.exe (PID: 2020)
Creates a Stream, which may work with files, input/output devices, pipes, or TCP/IP sockets (SCRIPT)
- cscript.exe (PID: 1928)
Changes charset (SCRIPT)
- cscript.exe (PID: 1928)
Executes WMI query (SCRIPT)
- cscript.exe (PID: 1928)
- cscript.exe (PID: 2020)
Reads data from a binary Stream object (SCRIPT)
- cscript.exe (PID: 1928)
- cscript.exe (PID: 2020)
Gets full path of the running script (SCRIPT)
- cscript.exe (PID: 2020)
- cscript.exe (PID: 1928)
Reads data from a file (SCRIPT)
- cscript.exe (PID: 1928)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3956)
Checks supported languages
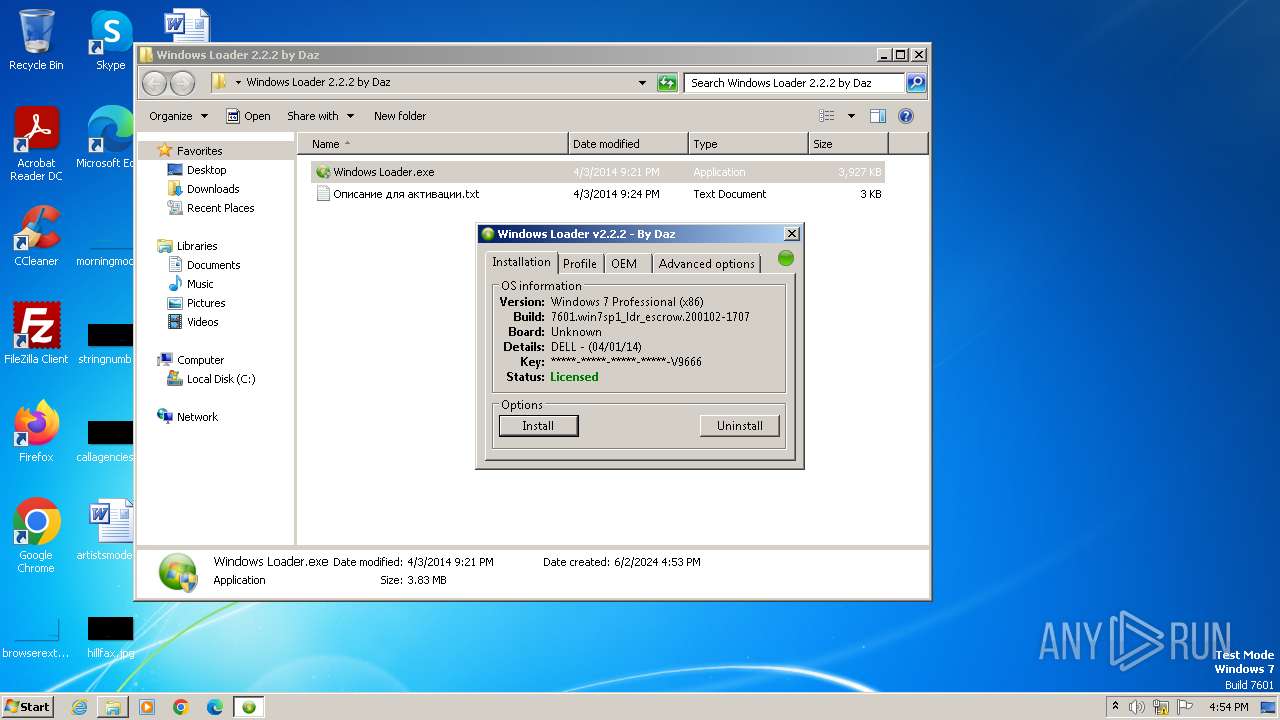
- Windows Loader.exe (PID: 1876)
Manual execution by a user
- Windows Loader.exe (PID: 1876)
- Windows Loader.exe (PID: 4080)
Reads the computer name
- Windows Loader.exe (PID: 1876)
Reads the machine GUID from the registry
- Windows Loader.exe (PID: 1876)
Reads security settings of Internet Explorer
- cscript.exe (PID: 1928)
- cscript.exe (PID: 2020)
Reads product name
- Windows Loader.exe (PID: 1876)
Reads Environment values
- Windows Loader.exe (PID: 1876)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 1518952 |
|---|---|
| UncompressedSize: | 4021049 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2014:04:03 21:21:06 |
| PackingMethod: | Normal |
| ArchivedFileName: | Windows Loader 2.2.2 by Daz\Windows Loader.exe |
Total processes
60
Monitored processes
17
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 580 | takeown /f C:\ldrscan\bootwin | C:\Windows\System32\takeown.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Takes ownership of a file Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 616 | cmd.exe /A /C "cmd.exe /c takeown /f C:\ldrscan\bootwin" | C:\Windows\System32\cmd.exe | — | Windows Loader.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 824 | cmd.exe /A /C "C:\Windows\System32\cscript.exe //nologo C:\Windows\System32\slmgr.vbs -ilc "C:\Dell.XRM-MS"" | C:\Windows\System32\cmd.exe | — | Windows Loader.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1588 | cmd.exe /c takeown /f C:\ldrscan\bootwin | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1836 | cmd.exe /A /C "cmd.exe /c takeown /f C:\ldrscan\bootwin" | C:\Windows\System32\cmd.exe | — | Windows Loader.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1852 | cmd.exe /c takeown /f C:\ldrscan\bootwin | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1876 | "C:\Users\admin\Desktop\Windows Loader 2.2.2 by Daz\Windows Loader.exe" | C:\Users\admin\Desktop\Windows Loader 2.2.2 by Daz\Windows Loader.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 1928 | C:\Windows\System32\cscript.exe //nologo C:\Windows\System32\slmgr.vbs -ilc "C:\Dell.XRM-MS" | C:\Windows\System32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 1988 | cmd.exe /A /C "icacls C:\ldrscan\bootwin /grant *S-1-1-0:(F)" | C:\Windows\System32\cmd.exe | — | Windows Loader.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2012 | takeown /f C:\ldrscan\bootwin | C:\Windows\System32\takeown.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Takes ownership of a file Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
4 617
Read events
4 595
Write events
22
Delete events
0
Modification events
| (PID) Process: | (3956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3956) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Windows Loader 2.2.2 by Daz.rar | |||
| (PID) Process: | (3956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
1
Suspicious files
0
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1876 | Windows Loader.exe | C:\Dell.XRM-MS | xml | |
MD5:18B1E45BF56F40C3C4BBE65831178216 | SHA256:D072A059D3ED3E75C98B85B41E4319E8D5CFAE0E0C239B62436A3AD34003AB4A | |||
| 3956 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3956.43610\Windows Loader 2.2.2 by Daz\Описание для активации.txt | text | |
MD5:3E69EC1F24483713D082F90198C14929 | SHA256:BC4BFB73C60F84842B6515041D3FCE56CF68D2510AF069782DD8B1EADDE81234 | |||
| 3956 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3956.43610\Windows Loader 2.2.2 by Daz\Windows Loader.exe | executable | |
MD5:323C0FD51071400B51EEDB1BE90A8188 | SHA256:2F2ABA1E074F5F4BAA08B524875461889F8F04D4FFC43972AC212E286022AB94 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
3
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |