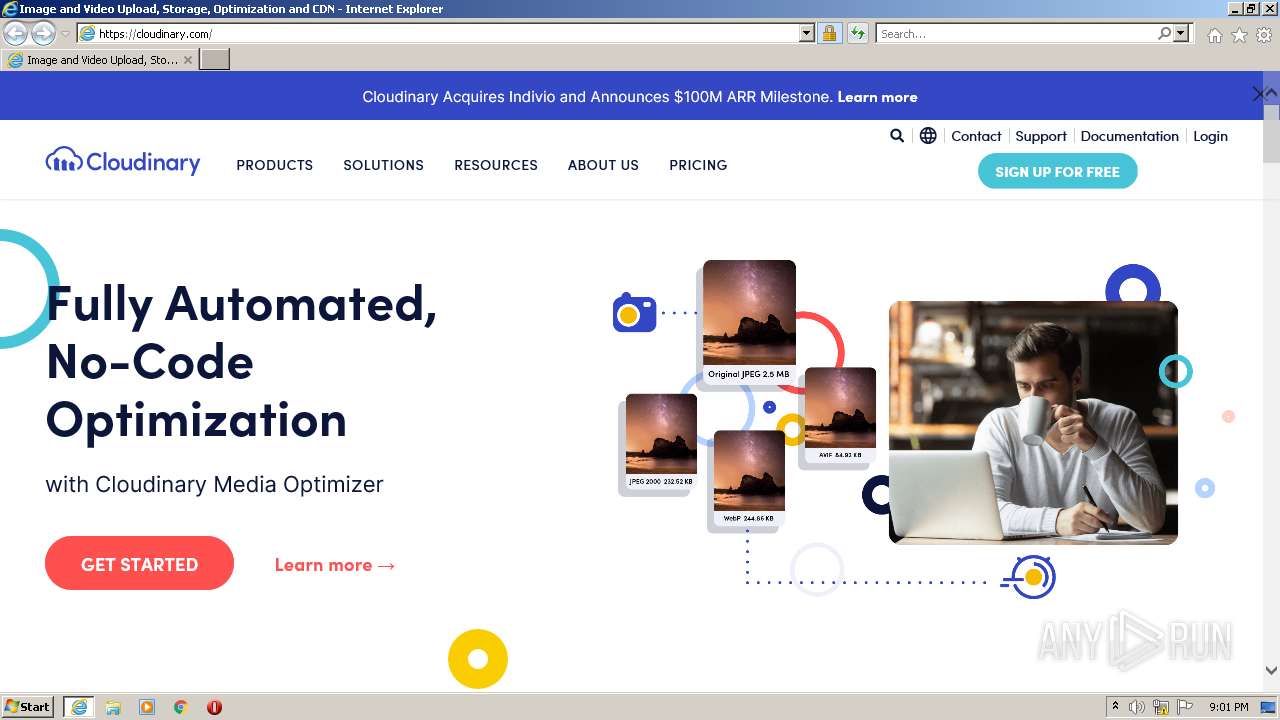
| URL: | https://img1.hscicdn.com |
| Full analysis: | https://app.any.run/tasks/11f738eb-7076-4920-885f-5ef52f9acb61 |
| Verdict: | Malicious activity |
| Analysis date: | January 14, 2022, 21:00:25 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 9AA67FC3B07ED56912E05623477B5467 |
| SHA1: | 092B776A2687AFC96F0DDACE9035DD4491F87849 |
| SHA256: | A2197F988E424337CA6453285A9065BC73CA378EF5E678C8BD194D33D62F1791 |
| SSDEEP: | 3:N8TLUG92n:2HUGY |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 3652)
INFO
Application launched itself
- iexplore.exe (PID: 3088)
Reads the computer name
- iexplore.exe (PID: 3652)
- iexplore.exe (PID: 3088)
Checks supported languages
- iexplore.exe (PID: 3088)
- iexplore.exe (PID: 3652)
Changes internet zones settings
- iexplore.exe (PID: 3088)
Checks Windows Trust Settings
- iexplore.exe (PID: 3652)
- iexplore.exe (PID: 3088)
Creates files in the user directory
- iexplore.exe (PID: 3652)
Reads settings of System Certificates
- iexplore.exe (PID: 3652)
- iexplore.exe (PID: 3088)
Reads internet explorer settings
- iexplore.exe (PID: 3652)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
36
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3088 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://img1.hscicdn.com" | C:\Program Files\Internet Explorer\iexplore.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3652 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3088 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
13 955
Read events
13 832
Write events
123
Delete events
0
Modification events
| (PID) Process: | (3088) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3088) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3088) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30935433 | |||
| (PID) Process: | (3088) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3088) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30935433 | |||
| (PID) Process: | (3088) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3088) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3088) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3088) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3088) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
29
Text files
107
Unknown types
61
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3652 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\EB2C4AB8B68FFA4B7733A9139239A396_D76DB901EE986B889F30D8CC06229E2D | der | |
MD5:— | SHA256:— | |||
| 3652 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\settings-15f5ebe93913b9a96dabe3aeab5003d5[1].js | text | |
MD5:— | SHA256:— | |||
| 3652 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\7423F88C7F265F0DEFC08EA88C3BDE45_D975BBA8033175C8D112023D8A7A8AD6 | binary | |
MD5:— | SHA256:— | |||
| 3652 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\52MGEK67.htm | html | |
MD5:— | SHA256:— | |||
| 3652 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\EB2C4AB8B68FFA4B7733A9139239A396_D76DB901EE986B889F30D8CC06229E2D | binary | |
MD5:— | SHA256:— | |||
| 3652 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\223DE96EE265046957A660ED7C9DD9E7_EFF9B9BA98DEAA773F261FA85A0B1771 | der | |
MD5:— | SHA256:— | |||
| 3652 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B039FEA45CB4CC4BBACFC013C7C55604_ACB084F1532E23E916946A083A45F6BF | binary | |
MD5:— | SHA256:— | |||
| 3652 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B039FEA45CB4CC4BBACFC013C7C55604_ACB084F1532E23E916946A083A45F6BF | der | |
MD5:— | SHA256:— | |||
| 3652 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:F7DCB24540769805E5BB30D193944DCE | SHA256:6B88C6AC55BBD6FEA0EBE5A760D1AD2CFCE251C59D0151A1400701CB927E36EA | |||
| 3652 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\EDC238BFF48A31D55A97E1E93892934B_C20E0DA2D0F89FE526E1490F4A2EE5AB | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
29
TCP/UDP connections
124
DNS requests
47
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3652 | iexplore.exe | GET | — | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEATh56TcXPLzbcArQrhdFZ8%3D | US | — | — | whitelisted |
3652 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAH9o%2BtuynXIiEOLckvPvJE%3D | US | der | 471 b | whitelisted |
3652 | iexplore.exe | GET | 200 | 104.18.21.226:80 | http://ocsp2.globalsign.com/rootr3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT1nGh%2FJBjWKnkPdZIzB1bqhelHBwQUj%2FBLf6guRSSuTVD6Y5qL3uLdG7wCEHgDGCDPAjbzpoUYuu%2B39wE%3D | US | der | 1.40 Kb | whitelisted |
3652 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTPJvUY%2Bsl%2Bj4yzQuAcL2oQno5fCgQUUWj%2FkK8CB3U8zNllZGKiErhZcjsCEAhFMjccjkHQHxWs2V0z2XQ%3D | US | der | 471 b | whitelisted |
3652 | iexplore.exe | GET | 200 | 142.250.186.35:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | US | der | 724 b | whitelisted |
3652 | iexplore.exe | GET | 200 | 142.250.186.35:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEGmSmALa8169CgAAAAEn3NM%3D | US | der | 471 b | whitelisted |
3088 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://crl3.digicert.com/Omniroot2025.crl | US | der | 7.68 Kb | whitelisted |
3652 | iexplore.exe | GET | 200 | 142.250.186.35:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDR1%2F9RZzWDFAoAAAABJ9zo | US | der | 472 b | whitelisted |
3652 | iexplore.exe | GET | 200 | 192.124.249.23:80 | http://ocsp.godaddy.com//MEQwQjBAMD4wPDAJBgUrDgMCGgUABBTkIInKBAzXkF0Qh0pel3lfHJ9GPAQU0sSw0pHUTBFxs2HLPaH%2B3ahq1OMCAxvnFQ%3D%3D | US | der | 1.66 Kb | whitelisted |
3652 | iexplore.exe | GET | 200 | 104.18.21.226:80 | http://ocsp.globalsign.com/ca/gsatlasr3dvtlsca2020/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQT6XbZiiF%2BR%2FUEno7LSD4H4YmN6gQUQm1XLU8fJnd0pidk9oD6j0ho%2FnwCEAFBzoxjwZqoSoGmuZC0ryI%3D | US | der | 1.42 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3652 | iexplore.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
3652 | iexplore.exe | 162.159.137.83:443 | cloudinary.com | Cloudflare Inc | — | unknown |
3652 | iexplore.exe | 151.101.65.137:443 | cloudinary-res.cloudinary.com | Fastly | US | unknown |
— | — | 151.101.65.137:443 | cloudinary-res.cloudinary.com | Fastly | US | unknown |
3652 | iexplore.exe | 151.101.1.137:443 | cloudinary-res.cloudinary.com | Fastly | US | suspicious |
3652 | iexplore.exe | 142.250.185.200:443 | www.googletagmanager.com | Google Inc. | US | suspicious |
3652 | iexplore.exe | 185.60.216.19:443 | connect.facebook.net | Facebook, Inc. | IE | whitelisted |
3652 | iexplore.exe | 104.18.21.226:80 | ocsp2.globalsign.com | Cloudflare Inc | US | shared |
3652 | iexplore.exe | 142.250.186.35:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
3652 | iexplore.exe | 151.101.1.100:443 | cldmo.mo.cloudinary.net | Fastly | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
img1.hscicdn.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
cloudinary.com |
| unknown |
ocsp.godaddy.com |
| whitelisted |
cloudinary-res.cloudinary.com |
| suspicious |
res.cloudinary.com |
| whitelisted |
cldmo.mo.cloudinary.net |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3652 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
3652 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
3652 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
3652 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
3652 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
3652 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |