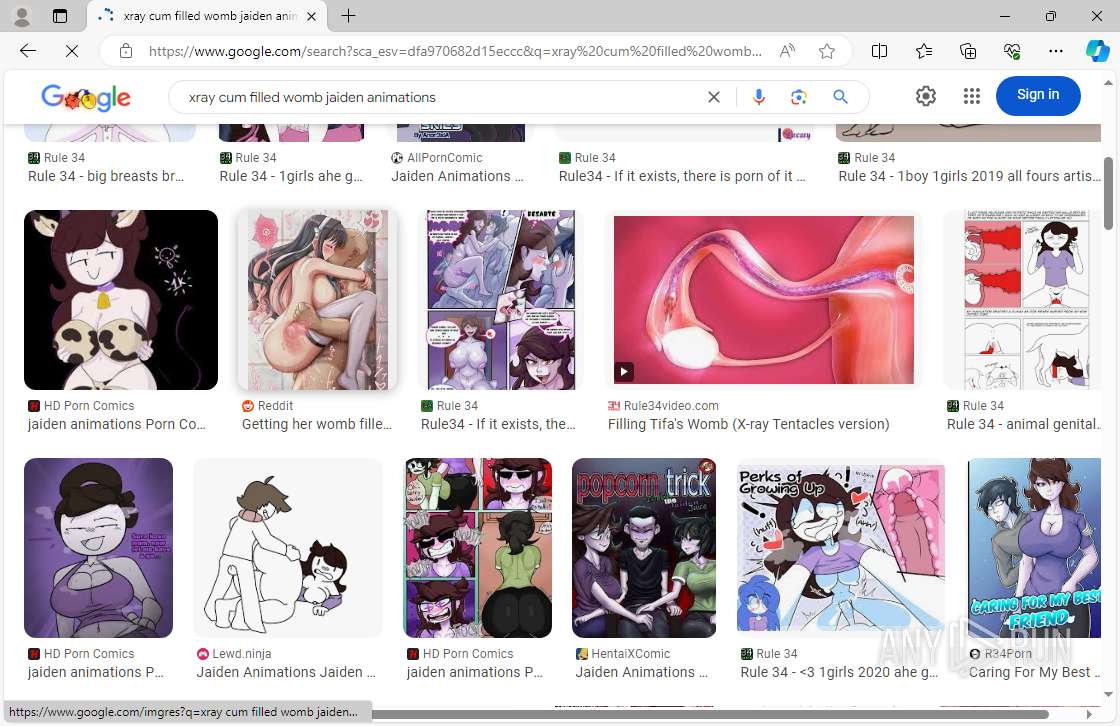
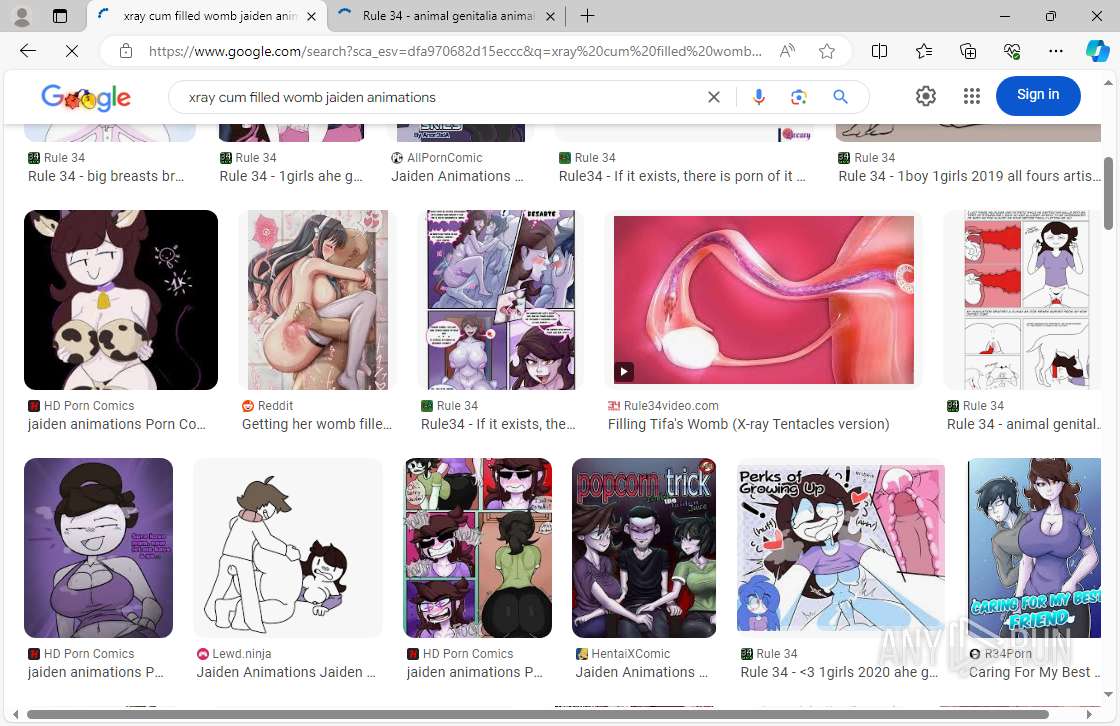
| URL: | Www.google.com |
| Full analysis: | https://app.any.run/tasks/af1e8aca-5031-41ba-a358-0b361b5c7ec0 |
| Verdict: | Malicious activity |
| Analysis date: | December 14, 2024, 02:38:26 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| MD5: | BD6CBA3DEF4501ECEC0CD849AC0BF345 |
| SHA1: | 422239DD4D6C992445D1AB8BE8DF829B5432C4D9 |
| SHA256: | A20F61D619B4A116E8AB9CCADAE0B3AC116E1C4C05B9402695C21A222B0F80FA |
| SSDEEP: | 3:8+K:DK |
MALICIOUS
No malicious indicators.SUSPICIOUS
Potential Corporate Privacy Violation
- msedge.exe (PID: 4792)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
153
Monitored processes
1
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 4792 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=2604 --field-trial-handle=2320,i,16194277592197507296,15814343983252007256,262144 --variations-seed-version /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 | ||||
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
89
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_0000bd | image | |
MD5:55653D73F359016F5BCB0B90183F61DF | SHA256:050CA6FB6DBFD30B004B5013CEF04BEF2739C3E8ED0D9D83B0DE95A9B3E4FEC5 | |||
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_0000c1 | compressed | |
MD5:D4C2E6DC5DF547E5D0D7C7202746A2BD | SHA256:B49954CA2713366FBBA0731D2F6857D6287034F1D44A4306699741FFBBB1E48F | |||
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Network\TransportSecurity~RF2b7118.TMP | binary | |
MD5:15D26FA4E16467BE658F42074AC0DBAA | SHA256:D287407BD901A32E3F38F4392984507184D596C3694FAA69DD0B2E68F9F3A8FE | |||
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_0000ba | compressed | |
MD5:F93F4135300EBBE8CE74C96A7E039ED6 | SHA256:721E1FB17C311FAC75F70A1B570DB30A3654F6F7AB636579166F4F820FC4445B | |||
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_0000bf | compressed | |
MD5:6D9B75A291598235298CFD81E16DFEEB | SHA256:5C3F13720D81AD23217AC20FE7E94C5B2D43A2E5781D64110323479016D07BF9 | |||
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Network\TransportSecurity | binary | |
MD5:0A18A15B13E8E4D2E58198B812D04A14 | SHA256:3A0E7566A9B82FE10546C84D0838784A890FDF1559AE8C40D96074295868028D | |||
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Network\b5e0a779-0ad8-48b1-b1b9-82b3a81fcc1d.tmp | binary | |
MD5:1AEF615DB04ECF2E06391B5591FFD298 | SHA256:696A1F29FF0E227513C47163D913324BCE28FC1EB5BDCD7C23D0DCC33F3E3983 | |||
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Network\4103de12-fb20-4fb2-aa26-12a10b283c91.tmp | binary | |
MD5:73F20165142B82ABC0AAF635F3E5BB2E | SHA256:3A24BA8C7C915967A94DB2141EBBC1B5C03E0E77DA4D590AA84FBD78B57EFB70 | |||
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Network\Network Persistent State | binary | |
MD5:73F20165142B82ABC0AAF635F3E5BB2E | SHA256:3A24BA8C7C915967A94DB2141EBBC1B5C03E0E77DA4D590AA84FBD78B57EFB70 | |||
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Network\b0a760f3-dd9d-47e3-8e2a-a61506b8f1c0.tmp | binary | |
MD5:564B2A43E887555421867881A85500CD | SHA256:6C35DC3F00E55F522EC36B6BBC441CE8646B0A92D4427046BE695A102D61B67E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
161
TCP/UDP connections
114
DNS requests
102
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | — | 216.58.206.36:443 | https://www.google.com/ | unknown | — | — | — |
— | — | HEAD | 200 | 184.30.17.174:443 | https://fs.microsoft.com/fs/windows/config.json | unknown | — | — | — |
6764 | RUXIMICS.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4304 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | — | 216.58.206.36:443 | https://www.google.com/ | unknown | — | — | — |
4304 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6764 | RUXIMICS.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | OPTIONS | 200 | 172.217.18.14:443 | https://play.google.com/log?format=json&hasfast=true | unknown | — | — | — |
— | — | OPTIONS | 200 | 142.250.185.106:443 | https://ogads-pa.googleapis.com/$rpc/google.internal.onegoogle.asyncdata.v1.AsyncDataService/GetAsyncData | unknown | — | — | — |
— | — | GET | 200 | 216.58.206.78:443 | https://apis.google.com/_/scs/abc-static/_/js/k=gapi.gapi.en.x7CxCIZpks8.O/m=gapi_iframes,googleapis_client/rt=j/sv=1/d=1/ed=1/am=AAAg/rs=AHpOoo8czmnaLIncRgBQP7N2THncpDJ9mQ/cb=gapi.loaded_0 | unknown | — | — | — |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4792 | msedge.exe | 13.69.116.107:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
— | — | 224.0.0.251:5353 | — | — | — | unknown |
6528 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6764 | RUXIMICS.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4304 | MoUsoCoreWorker.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5988 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4792 | msedge.exe | 2.23.209.182:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
4792 | msedge.exe | 142.250.185.132:443 | www.google.com | — | — | whitelisted |
6552 | svchost.exe | 184.28.90.27:443 | fs.microsoft.com | AKAMAI-AS | US | whitelisted |
6528 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
www.google.com |
| whitelisted |
fs.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
xpaywalletcdn.azureedge.net |
| whitelisted |
ogs.google.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potential Corporate Privacy Violation | ET POLICY DNS Query For XXX Adult Site Top Level Domain |
— | — | Potential Corporate Privacy Violation | ET POLICY DNS Query For XXX Adult Site Top Level Domain |
— | — | Potential Corporate Privacy Violation | ET POLICY DNS Query For XXX Adult Site Top Level Domain |
— | — | Potential Corporate Privacy Violation | ET POLICY DNS Query For XXX Adult Site Top Level Domain |
— | — | Potential Corporate Privacy Violation | ET POLICY DNS Query For XXX Adult Site Top Level Domain |
— | — | Potential Corporate Privacy Violation | ET POLICY DNS Query For XXX Adult Site Top Level Domain |
— | — | Potential Corporate Privacy Violation | ET POLICY DNS Query For XXX Adult Site Top Level Domain |
— | — | Potential Corporate Privacy Violation | ET POLICY DNS Query For XXX Adult Site Top Level Domain |