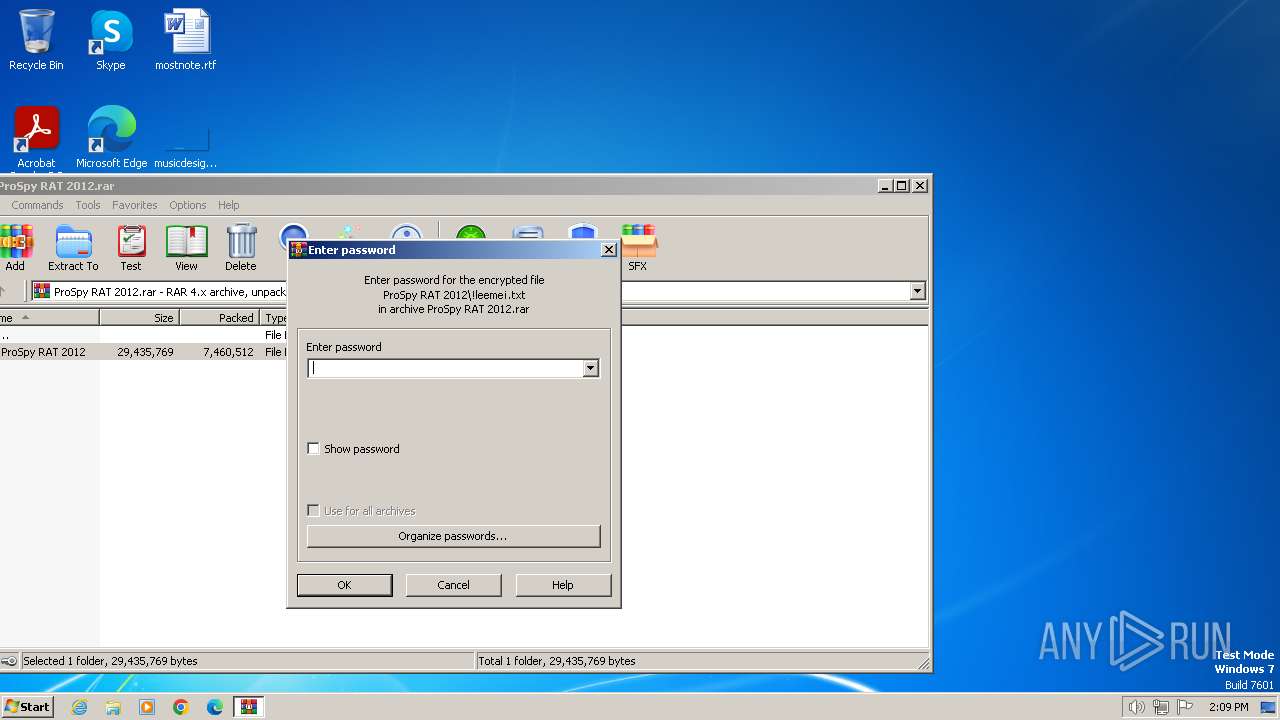
| File name: | ProSpy RAT 2012.rar |
| Full analysis: | https://app.any.run/tasks/16e4896f-db14-4d6f-88a3-ef1a6563722e |
| Verdict: | Malicious activity |
| Analysis date: | February 21, 2024, 14:09:05 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | 3B6AA29CFAE642AEE91C644A676E77CC |
| SHA1: | 6647B44CAA78F4C097725C4BE2377E620564304E |
| SHA256: | A1F89234306B972A6B97E1A68444F88A1A969CDA63BCF92AB00364C95ED984FC |
| SSDEEP: | 98304:qNnZW6XGD1rXogKsgAhIyE4EfOczYTnjc+zprbbXXCAmhEmXqJ+wILkVcUGJRLO2:Z8ehXkj0dlQBs09 |
MALICIOUS
Drops the executable file immediately after the start
- Server_Builder.exe (PID: 3932)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 3668)
Detected use of alternative data streams (AltDS)
- Server_Builder.exe (PID: 3932)
Executable content was dropped or overwritten
- Server_Builder.exe (PID: 3932)
Reads the Internet Settings
- Server_Builder.exe (PID: 3932)
Reads security settings of Internet Explorer
- Server_Builder.exe (PID: 3932)
INFO
Checks supported languages
- Server_Builder.exe (PID: 3932)
- pro-spy1.exe (PID: 2860)
- Server_Builder.exe (PID: 2580)
Manual execution by a user
- Server_Builder.exe (PID: 3932)
Reads the computer name
- Server_Builder.exe (PID: 3932)
- pro-spy1.exe (PID: 2860)
Reads the machine GUID from the registry
- Server_Builder.exe (PID: 3932)
- pro-spy1.exe (PID: 2860)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3668)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3668)
Reads Environment values
- Server_Builder.exe (PID: 3932)
Create files in a temporary directory
- Server_Builder.exe (PID: 3932)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 147 |
|---|---|
| UncompressedSize: | 256 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2013:09:25 21:38:36 |
| PackingMethod: | Good Compression |
| ArchivedFileName: | ProSpy RAT 2012\!leeme?.txt |
Total processes
45
Monitored processes
4
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2580 | "C:\Users\admin\AppData\Local\Temp\Server_Builder.exe" | C:\Users\admin\AppData\Local\Temp\Server_Builder.exe | — | Server_Builder.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2860 | "C:\Users\admin\AppData\Local\Temp\pro-spy1.exe" | C:\Users\admin\AppData\Local\Temp\pro-spy1.exe | Server_Builder.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 3668 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\ProSpy RAT 2012.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3932 | "C:\Users\admin\Desktop\ProSpy RAT 2012\Server_Builder.exe" | C:\Users\admin\Desktop\ProSpy RAT 2012\Server_Builder.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
7 025
Read events
7 005
Write events
20
Delete events
0
Modification events
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\ProSpy RAT 2012.rar | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
26
Suspicious files
0
Text files
5
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3668.7553\ProSpy RAT 2012\!leeme¡.txt | text | |
MD5:B978EF61E761B84DDF5FAF345A400CB7 | SHA256:229100E7818236813D9CD4C9557FA8B68892A161452F497527C4CBF01B107479 | |||
| 3668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3668.7553\ProSpy RAT 2012\CODEJOCK\Codejock.Controls.v13.0.0.Demo.ocx | executable | |
MD5:55494584D369F207E6E1B071E7168EC0 | SHA256:025EFDC63C61B3567DC8EB244517C715DDA12CF2AA4BC595E427E8D7B751FED7 | |||
| 3668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3668.7553\ProSpy RAT 2012\CODEJOCK\Codejock.SkinFramework.v13.0.0.Demo.ocx | executable | |
MD5:048B6FDDF7F896881EF9076067720E9C | SHA256:5FA198C49FAFE09DB574C4856A9A8ABBA999C9F05411FA5187757449AEC82BB5 | |||
| 3668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3668.7553\ProSpy RAT 2012\CODEJOCK\COD3EF~1.OCA | executable | |
MD5:B39C800840B7F88B3512B77BB95DF86C | SHA256:5E4D50E0BA13AB0845E58C4AE5E00C5F2B337EEA7CFE0F7F6958DBECC23E353F | |||
| 3668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3668.7553\ProSpy RAT 2012\CODEJOCK\Codejock.CommandBars.v13.0.0.Demo.ocx | executable | |
MD5:CF73808B6F9C7B52EFF7719BA909FED8 | SHA256:3C3BDA5BEC1868F44FD1F16E9364644DFAA4D196521AC35CB176EFE522AFC8BB | |||
| 3668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3668.7553\ProSpy RAT 2012\CODEJOCK\COAABA~1.OCA | executable | |
MD5:3CE9696BAAF1B02079961021DE9D75DB | SHA256:EF01940FC377C06FD1E11FFC7C251957995CF271C4B2D6634599AB1BFF8B04DC | |||
| 3668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3668.7553\ProSpy RAT 2012\CODEJOCK\Codejock.TaskPanel.v13.0.0.Demo.ocx | executable | |
MD5:49940553FFB43BD562286B32D6196C8B | SHA256:DD60482FDA3299418066C0536A3D0E54B3527D0292CC9368A7B8607BA92619FC | |||
| 3668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3668.7553\ProSpy RAT 2012\CODEJOCK\COMCTL32.OCX | executable | |
MD5:EB5F811C1F78005B3C147599A0CCCF51 | SHA256:BF4147F8A12BEC3D54E3EF941475E29D852A1876117C6CE88F47B882EF6D4A03 | |||
| 3668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3668.7553\ProSpy RAT 2012\CODEJOCK\MSWINSCK.OCX | executable | |
MD5:E8A2190A9E8EE5E5D2E0B599BBF9DDA6 | SHA256:80AB0B86DE58A657956B2A293BD9957F78E37E7383C86D6CD142208C153B6311 | |||
| 3668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3668.7553\ProSpy RAT 2012\CODEJOCK\MSFLXGRD.OCX | executable | |
MD5:06EE7BB3C681B9FA8AF4280A154EE133 | SHA256:F2A67EB2888D8889C45576C037197C310FBBB00BB79089760508FDB132C690D2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |