| File name: | stage1.ps1 |
| Full analysis: | https://app.any.run/tasks/03c68d63-831b-41c6-b1c5-203af530f9f7 |
| Verdict: | Malicious activity |
| Analysis date: | January 29, 2025, 00:54:15 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text |
| MD5: | 406EA6B5F1E48ACF063DE5E03603F714 |
| SHA1: | 4B068CC5550C71107B8CE8F7C6CDAD0DB35DE9F6 |
| SHA256: | A1EF73CE71725489ED221105BBF808DDD8EF9D4AB03240DD2A5FD6C065762DB4 |
| SSDEEP: | 96:BRNW9VjInbrrUQAeu+iMZ9D9bOhg8LurJlFSmPEs5ficqPBPpHPoP1:BRwVjInrUQABPMZp9UDullFS4Es56cqk |
MALICIOUS
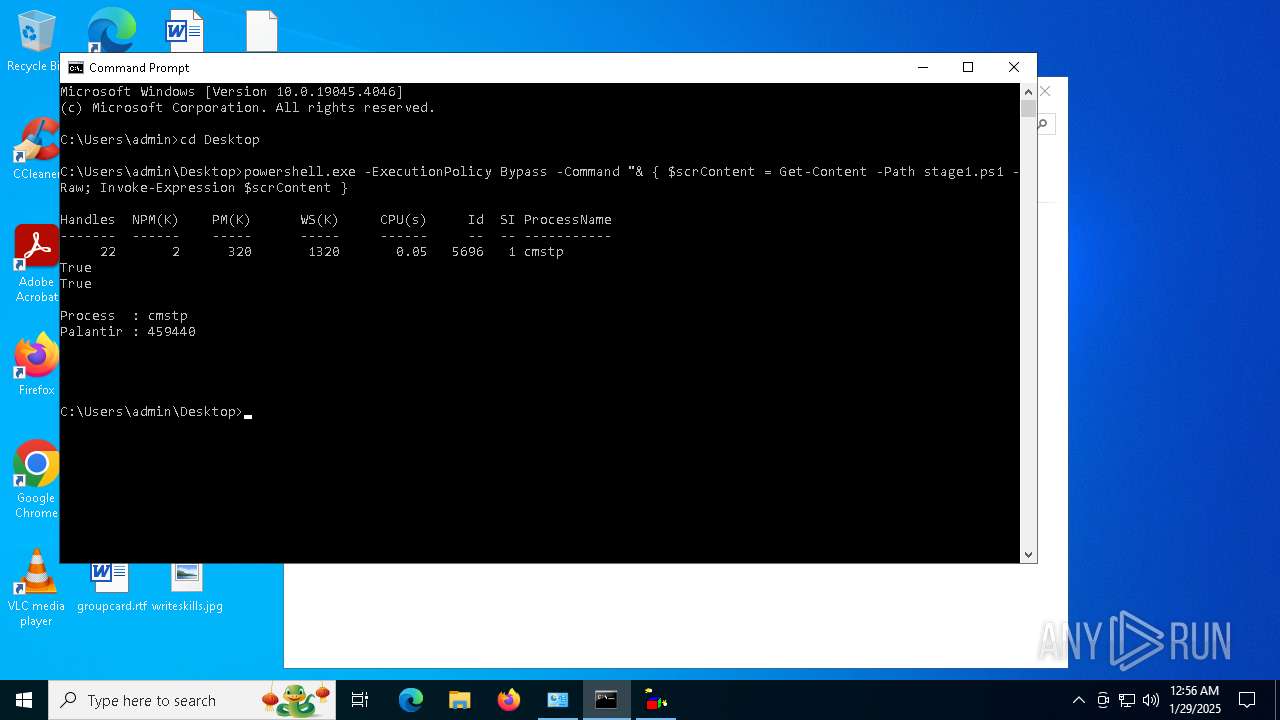
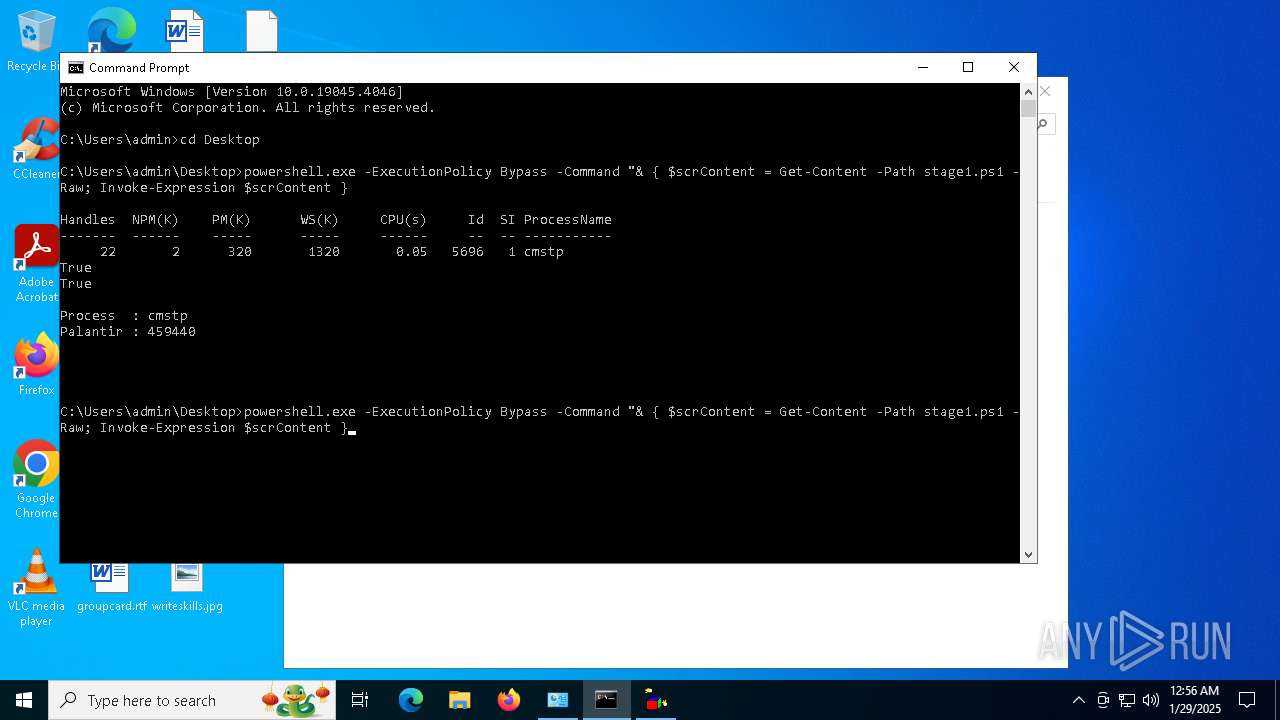
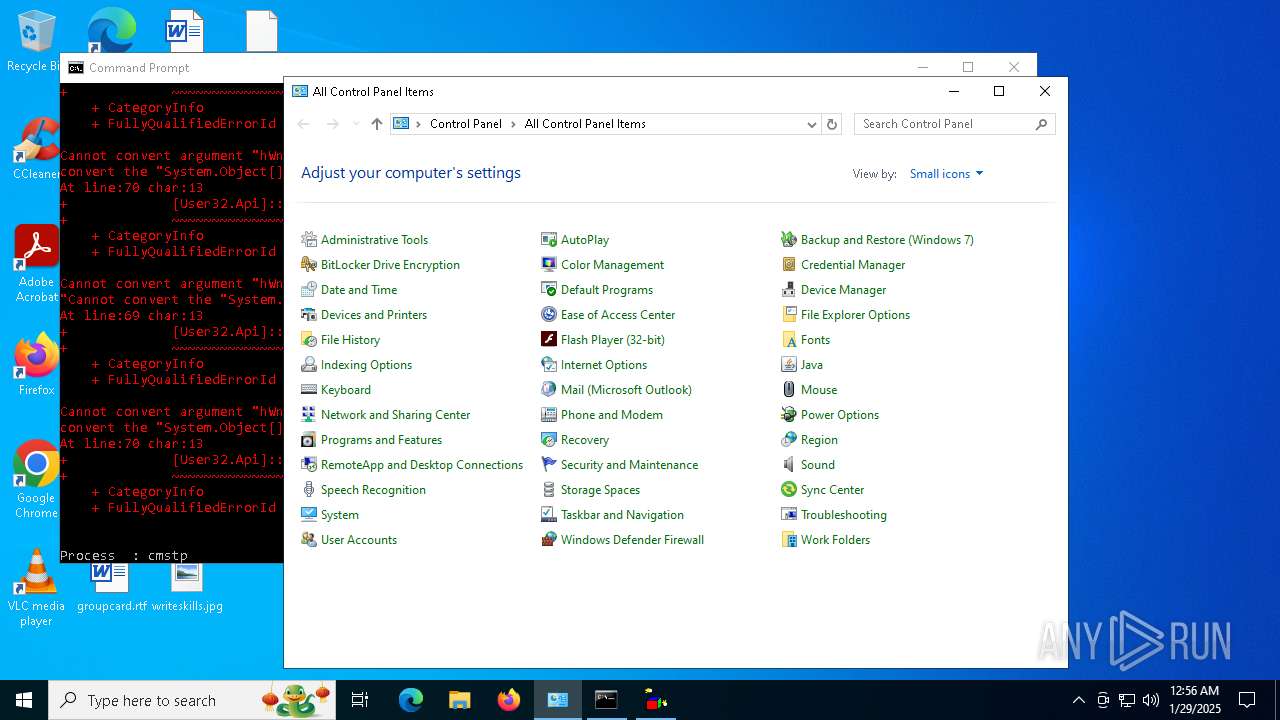
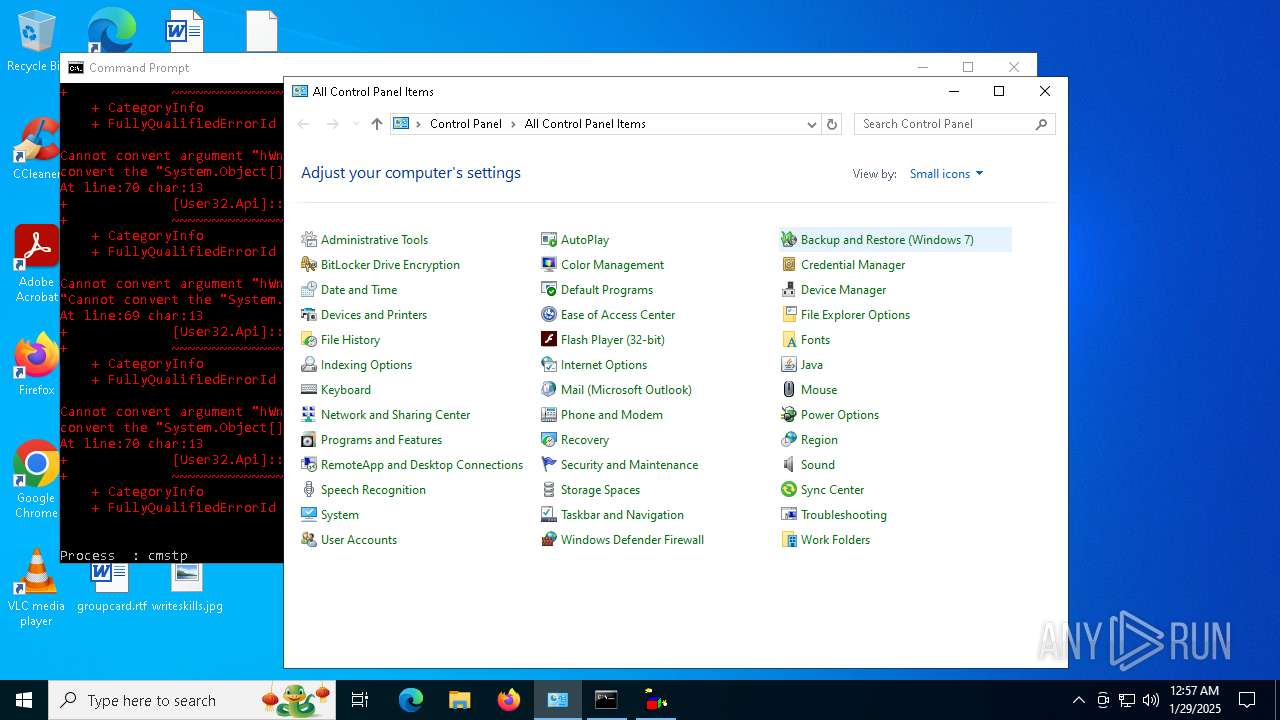
Bypass execution policy to execute commands
- powershell.exe (PID: 6092)
- powershell.exe (PID: 3076)
- powershell.exe (PID: 6160)
- powershell.exe (PID: 2292)
- powershell.exe (PID: 2144)
Known privilege escalation attack
- dllhost.exe (PID: 6716)
Changes powershell execution policy (Bypass)
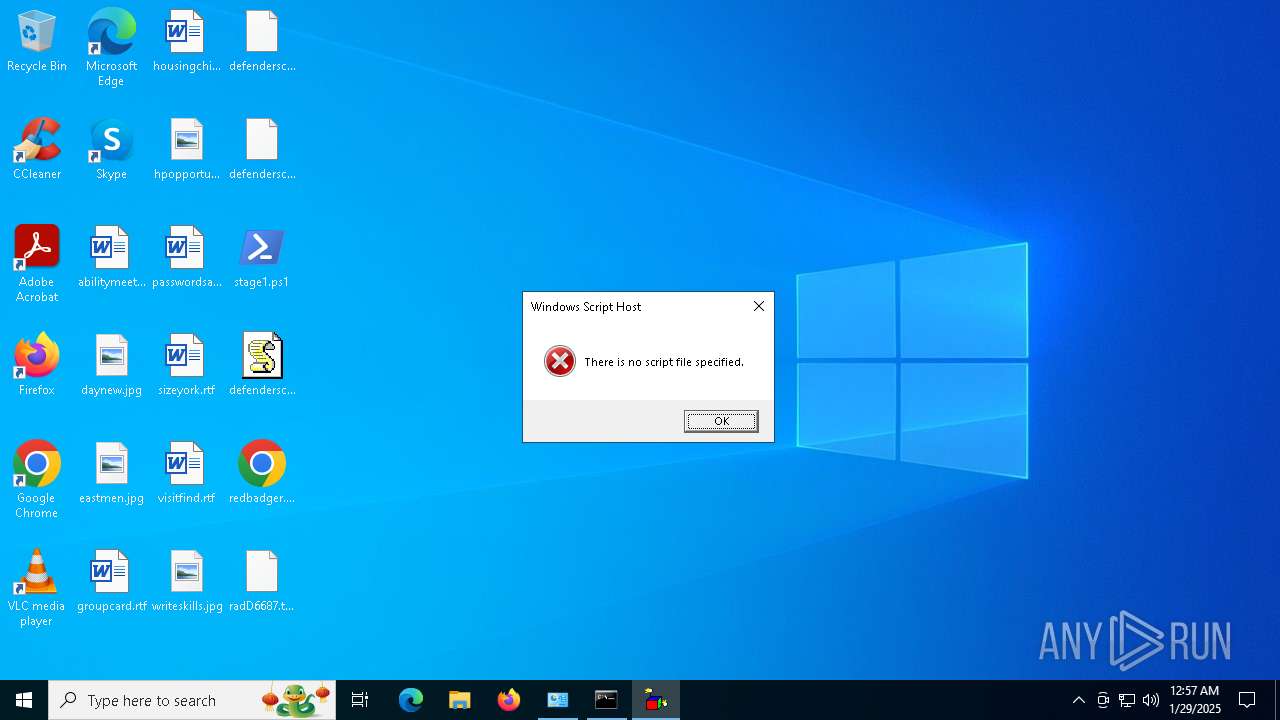
- cmd.exe (PID: 5736)
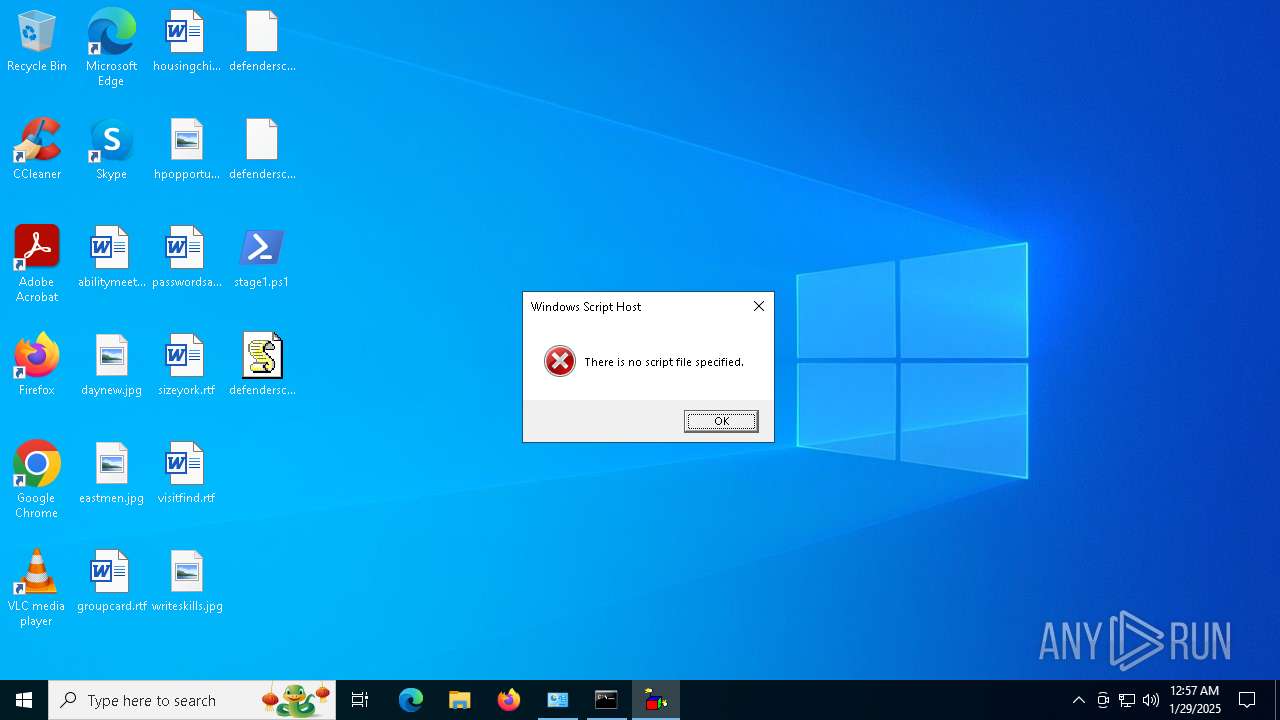
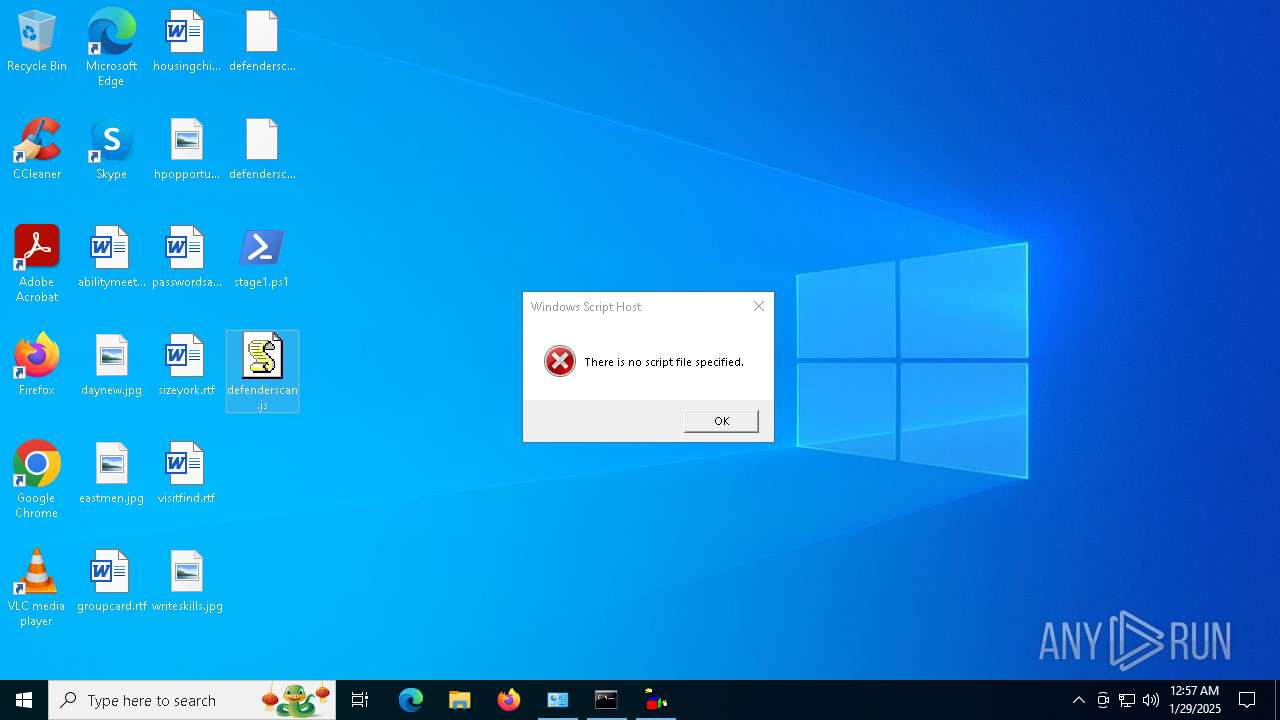
- wscript.exe (PID: 2460)
Uses base64 encoding (SCRIPT)
- wscript.exe (PID: 2460)
Gets a file object corresponding to the file in a specified path (SCRIPT)
- wscript.exe (PID: 2460)
Deletes a file (SCRIPT)
- wscript.exe (PID: 2460)
SUSPICIOUS
Checks a user's role membership (POWERSHELL)
- powershell.exe (PID: 6092)
- powershell.exe (PID: 3076)
- powershell.exe (PID: 2292)
- powershell.exe (PID: 6160)
- powershell.exe (PID: 2144)
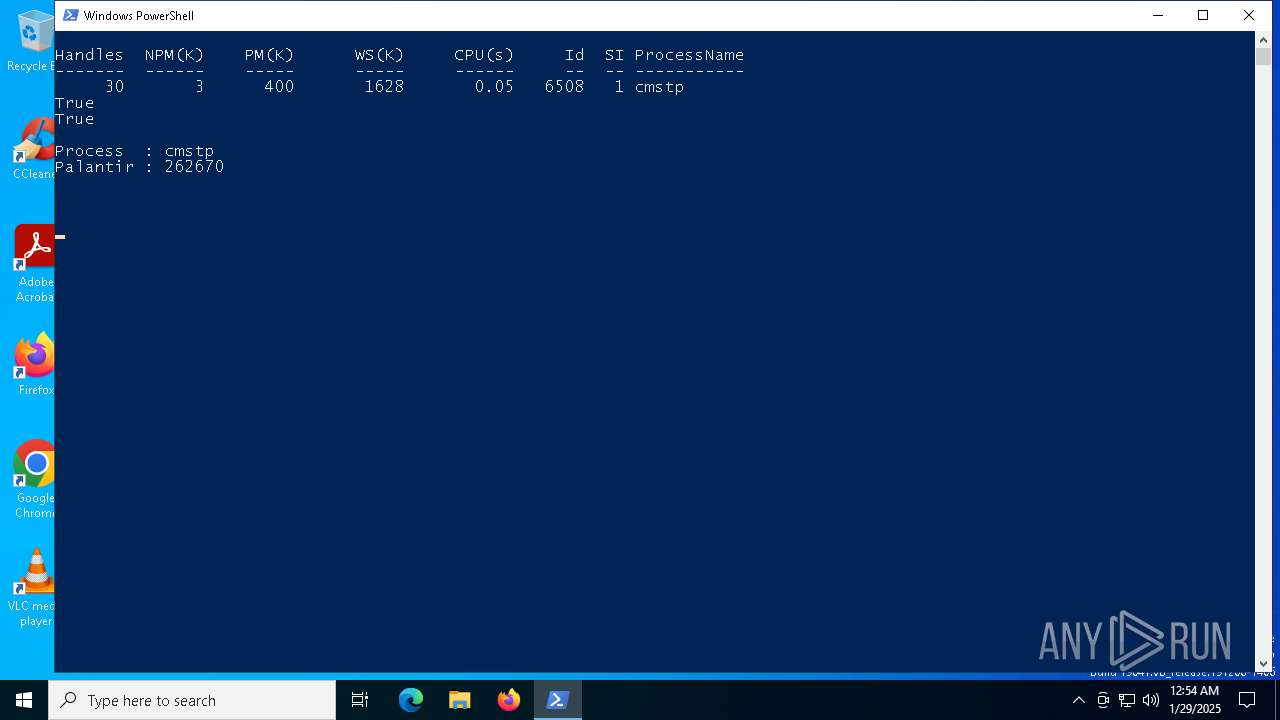
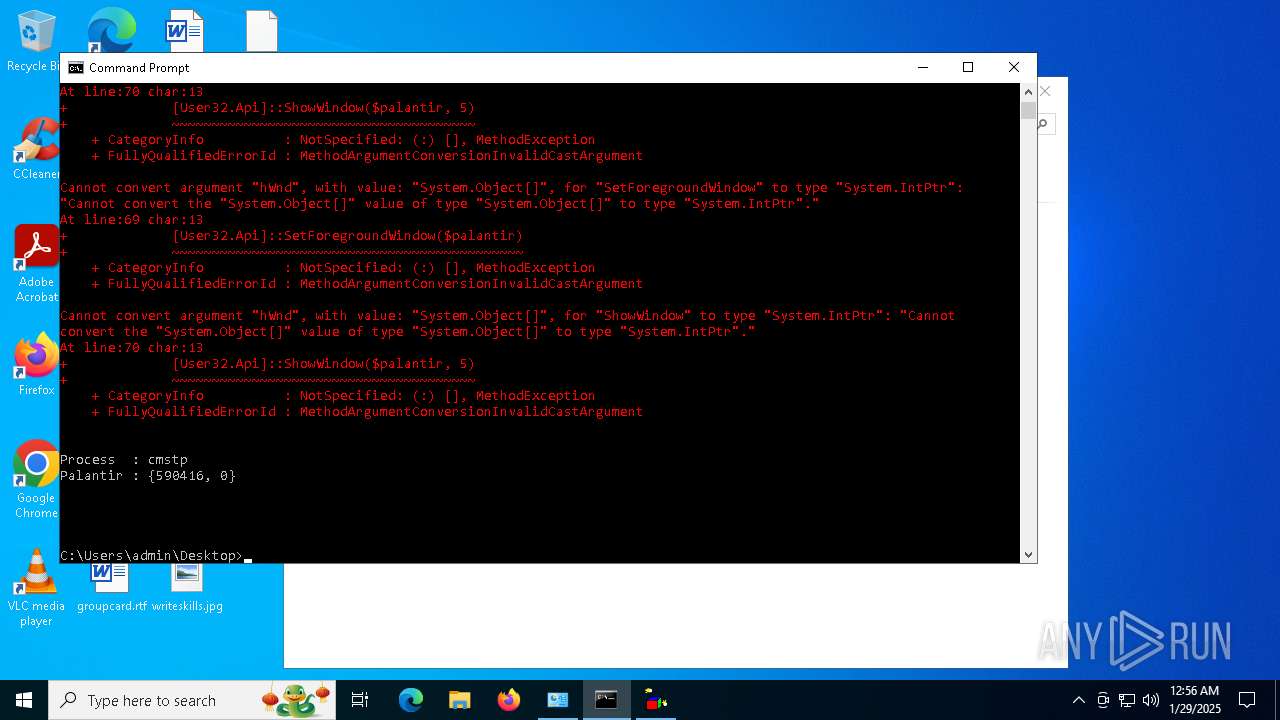
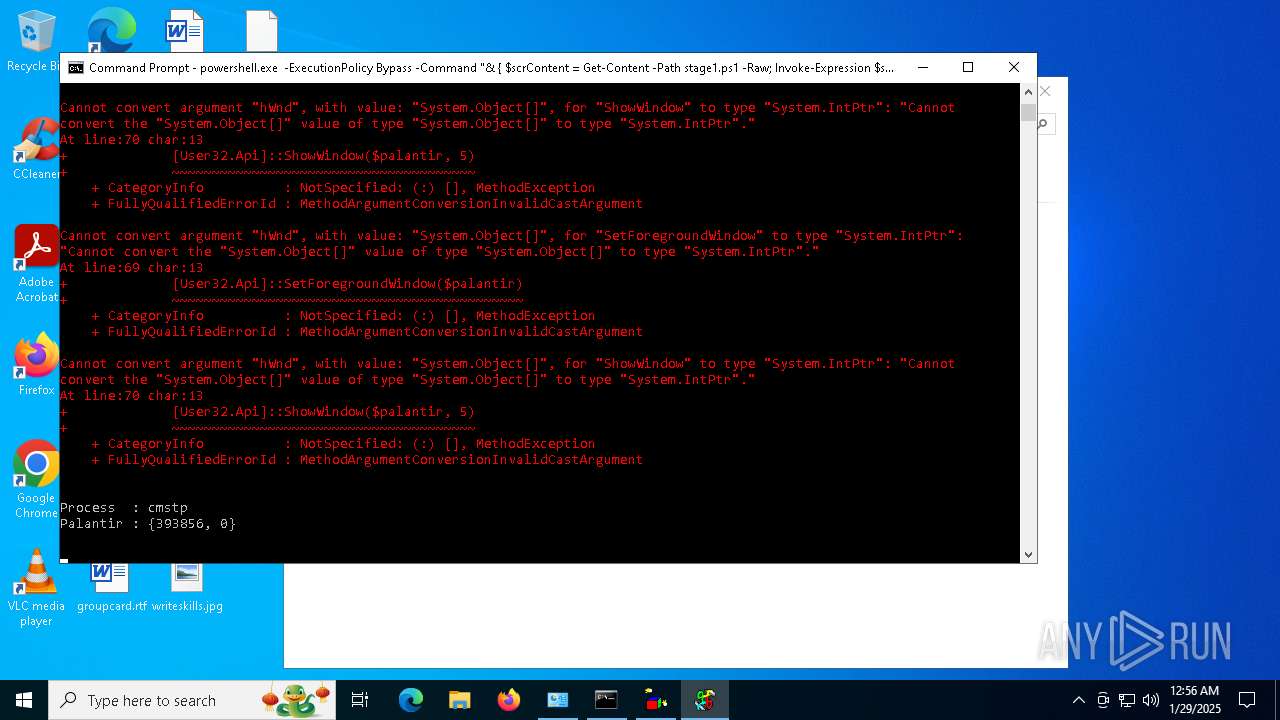
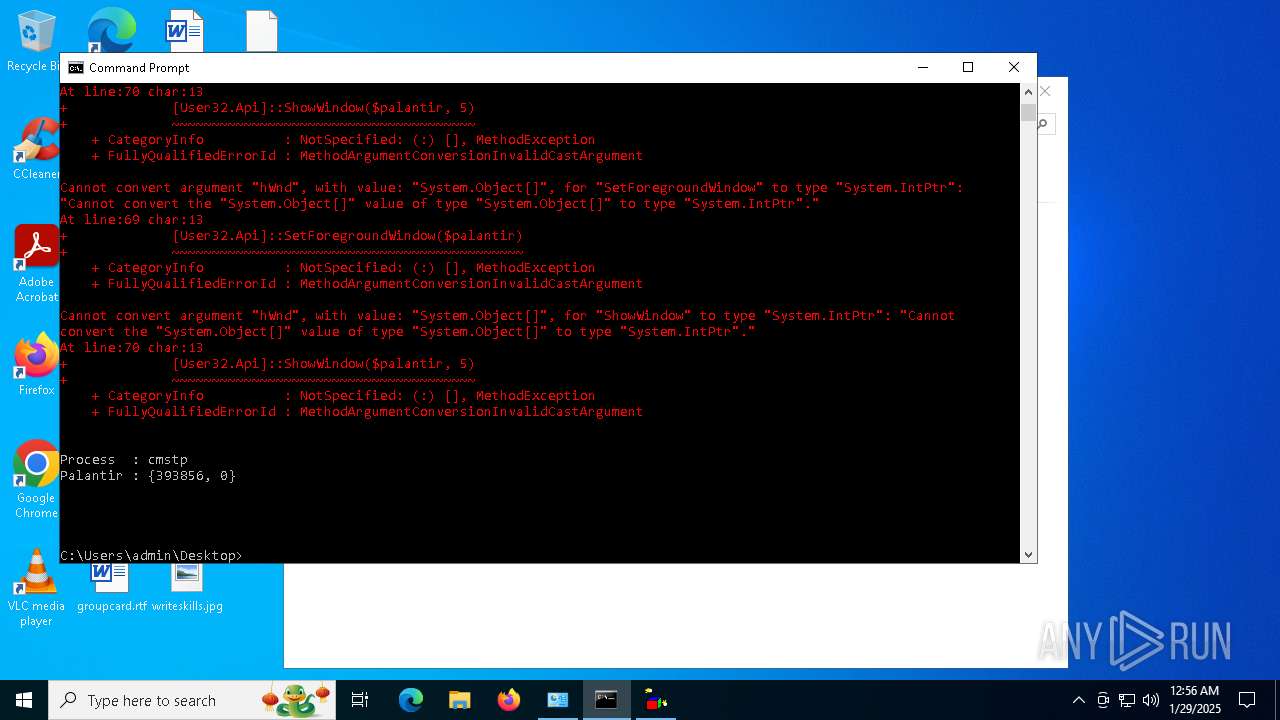
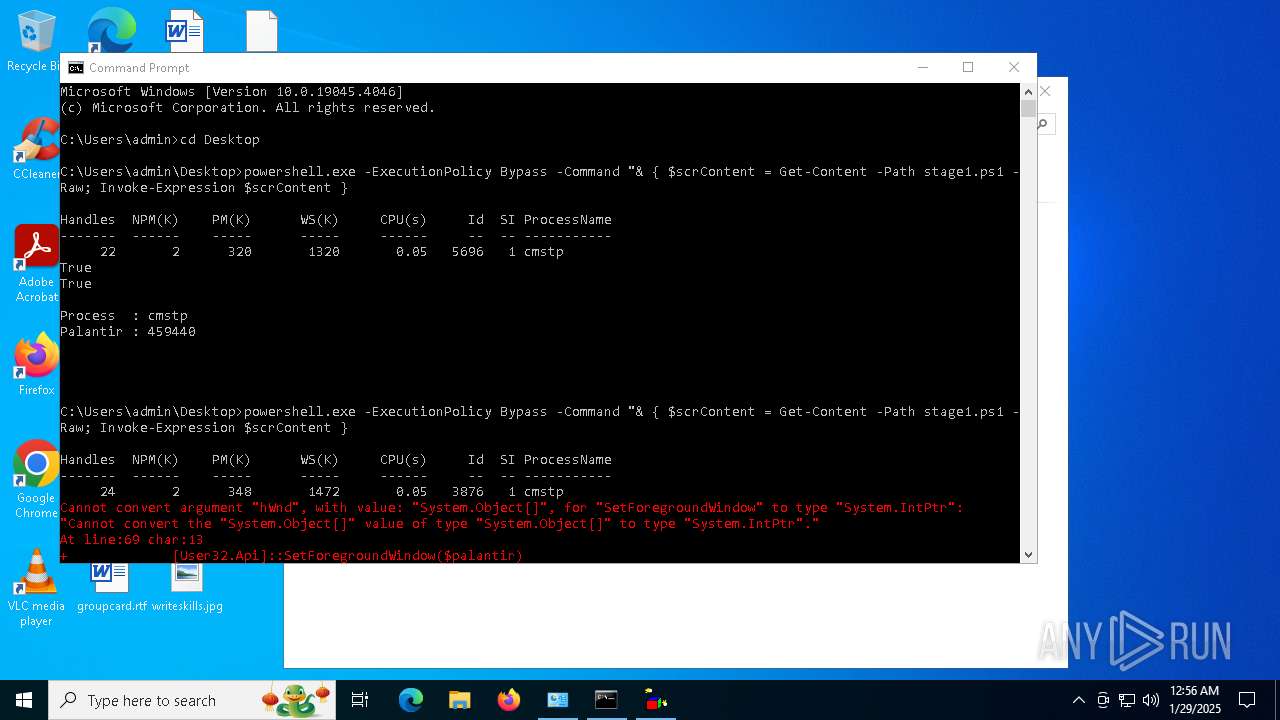
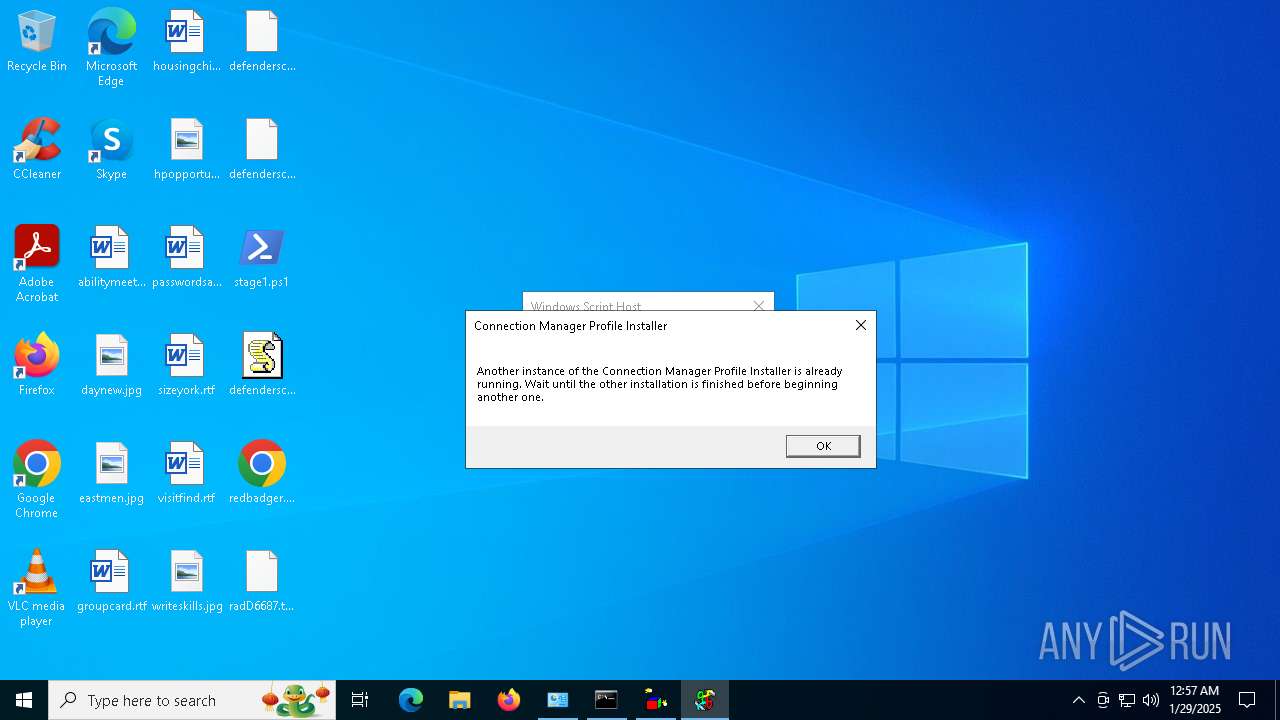
Probably UAC bypass using CMSTP.exe (Connection Manager service profile)
- powershell.exe (PID: 6092)
- powershell.exe (PID: 3076)
- powershell.exe (PID: 2292)
- powershell.exe (PID: 6160)
- powershell.exe (PID: 2144)
CSC.EXE is used to compile C# code
- csc.exe (PID: 6552)
- csc.exe (PID: 3420)
- csc.exe (PID: 6764)
- csc.exe (PID: 4912)
- csc.exe (PID: 3532)
Identifying current user with WHOAMI command
- powershell.exe (PID: 6092)
- powershell.exe (PID: 3076)
- powershell.exe (PID: 6160)
- powershell.exe (PID: 2292)
- powershell.exe (PID: 2144)
Executable content was dropped or overwritten
- csc.exe (PID: 6552)
- csc.exe (PID: 3420)
- csc.exe (PID: 6764)
- csc.exe (PID: 4912)
- csc.exe (PID: 3532)
Uses TASKKILL.EXE to kill process
- dllhost.exe (PID: 6716)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 5736)
- wscript.exe (PID: 2460)
The process executes Powershell scripts
- cmd.exe (PID: 5736)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 5736)
- wscript.exe (PID: 2460)
Script creates XML DOM node (SCRIPT)
- wscript.exe (PID: 2460)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 2460)
Sets XML DOM element text (SCRIPT)
- wscript.exe (PID: 2460)
Creates a Stream, which may work with files, input/output devices, pipes, or TCP/IP sockets (SCRIPT)
- wscript.exe (PID: 2460)
Creates XML DOM element (SCRIPT)
- wscript.exe (PID: 2460)
Writes binary data to a Stream object (SCRIPT)
- wscript.exe (PID: 2460)
Reads data from a binary Stream object (SCRIPT)
- wscript.exe (PID: 2460)
Saves data to a binary file (SCRIPT)
- wscript.exe (PID: 2460)
Changes charset (SCRIPT)
- wscript.exe (PID: 2460)
Gets full path of the running script (SCRIPT)
- wscript.exe (PID: 2460)
Runs shell command (SCRIPT)
- wscript.exe (PID: 2460)
INFO
Checks transactions between databases Windows and Oracle
- cmstp.exe (PID: 6508)
- cmstp.exe (PID: 5696)
Checks supported languages
- SearchApp.exe (PID: 5064)
- csc.exe (PID: 6552)
- cvtres.exe (PID: 6772)
- cvtres.exe (PID: 2100)
- csc.exe (PID: 3420)
- csc.exe (PID: 6764)
- cvtres.exe (PID: 372)
- csc.exe (PID: 4912)
- cvtres.exe (PID: 2124)
- csc.exe (PID: 3532)
- cvtres.exe (PID: 4548)
Disables trace logs
- cmstp.exe (PID: 6508)
- cmstp.exe (PID: 5696)
- cmstp.exe (PID: 3876)
- cmstp.exe (PID: 648)
- cmstp.exe (PID: 2216)
Reads the machine GUID from the registry
- csc.exe (PID: 6552)
- SearchApp.exe (PID: 5064)
- csc.exe (PID: 3420)
- csc.exe (PID: 4912)
- csc.exe (PID: 6764)
- csc.exe (PID: 3532)
Create files in a temporary directory
- csc.exe (PID: 6552)
- cvtres.exe (PID: 6772)
- cvtres.exe (PID: 2100)
- csc.exe (PID: 3420)
- cvtres.exe (PID: 372)
- csc.exe (PID: 6764)
- cvtres.exe (PID: 2124)
- csc.exe (PID: 4912)
- csc.exe (PID: 3532)
- cvtres.exe (PID: 4548)
Creates files in the program directory
- dllhost.exe (PID: 6716)
Process checks computer location settings
- SearchApp.exe (PID: 5064)
Reads the software policy settings
- SearchApp.exe (PID: 5064)
Manual execution by a user
- cmd.exe (PID: 5736)
- wscript.exe (PID: 2460)
- chrome.exe (PID: 3900)
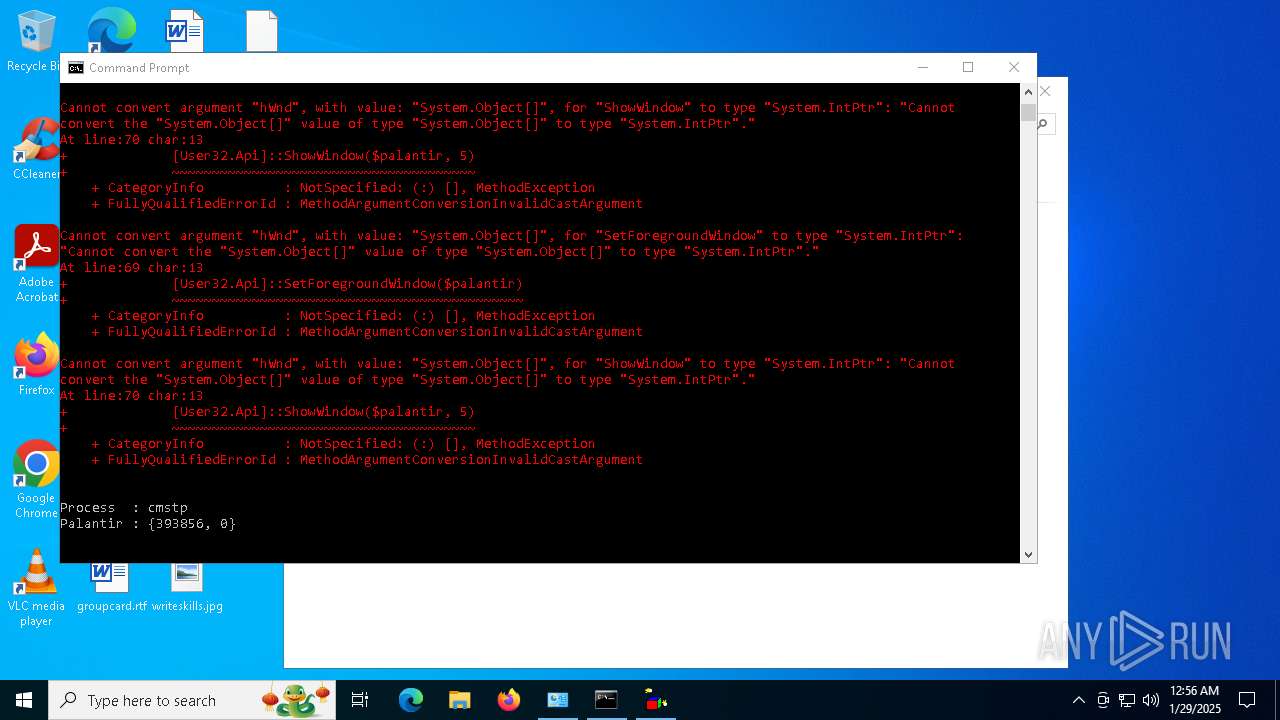
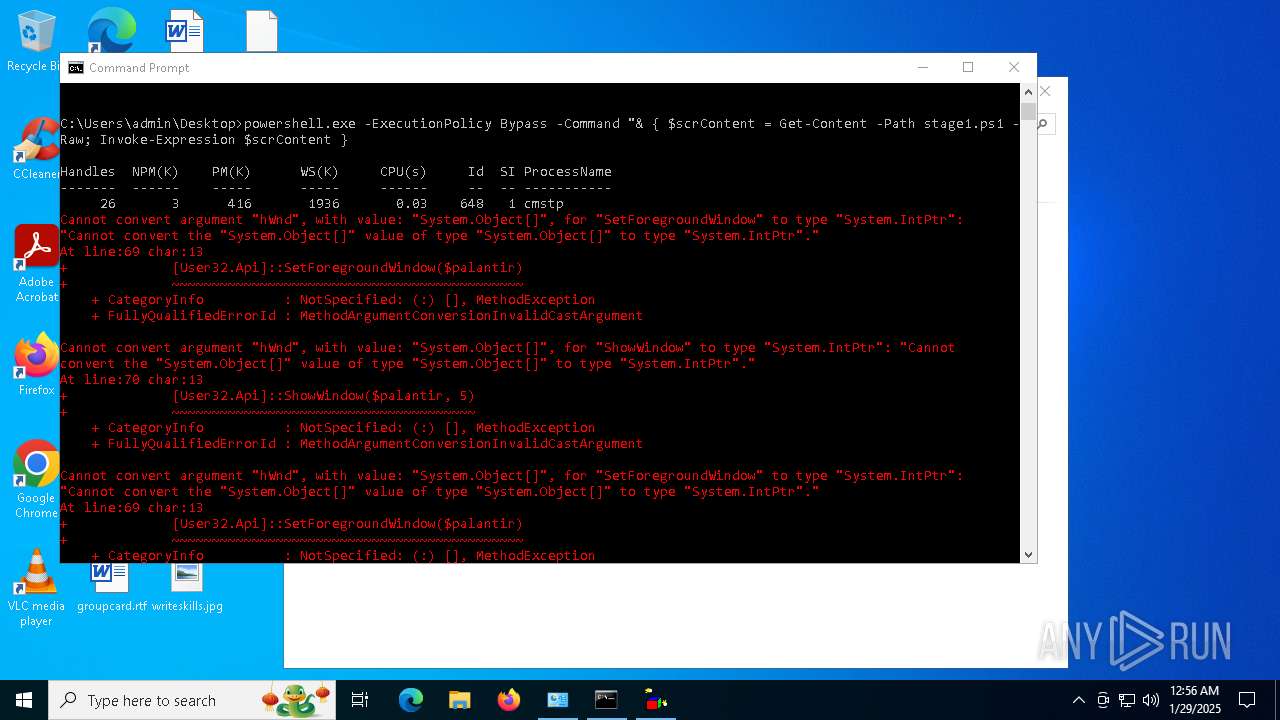
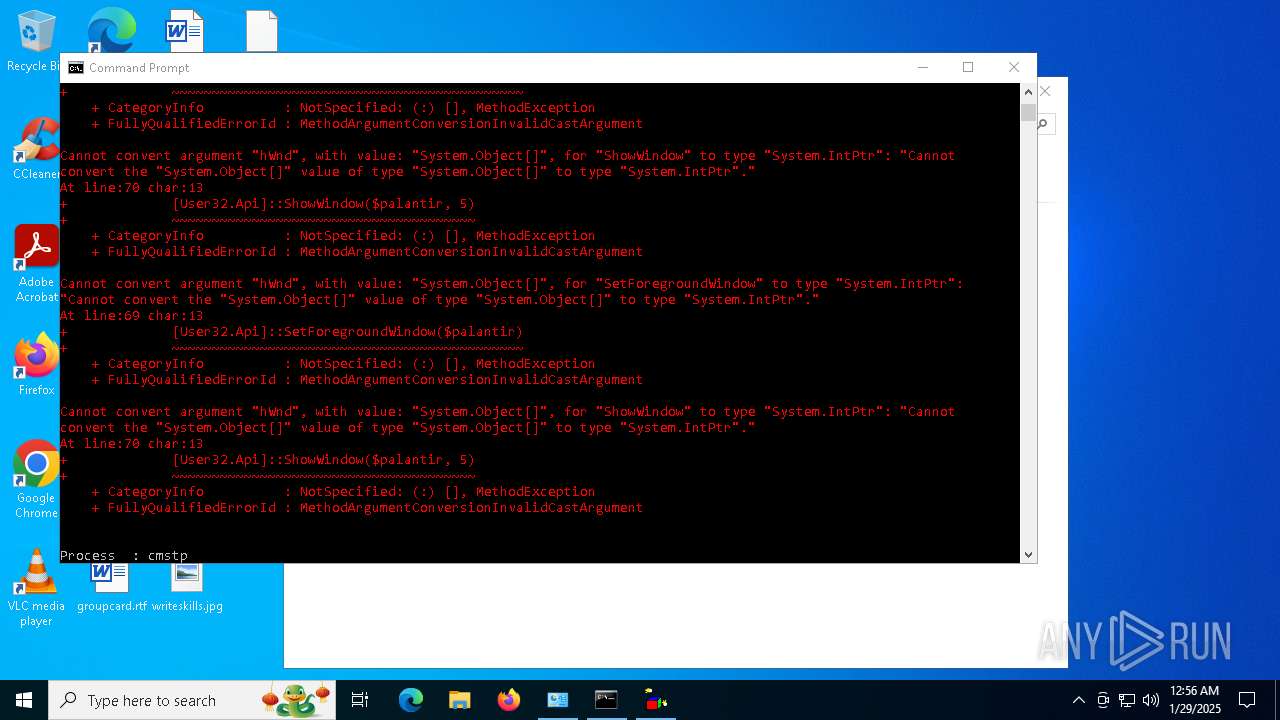
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 2292)
- powershell.exe (PID: 6160)
- powershell.exe (PID: 2144)
Application launched itself
- chrome.exe (PID: 3900)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
198
Monitored processes
63
Malicious processes
3
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 372 | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES459E.tmp" "c:\Users\admin\AppData\Local\Temp\CSCF11A13448A7F47B8A22786923D2D60E2.TMP" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 14.32.31326.0 Modules
| |||||||||||||||
| 372 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5652 --field-trial-handle=1940,i,5214472131177649609,16186631295709850380,262144 --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 648 | "c:\windows\system32\cmstp.exe" /au C:\Users\admin\AppData\Local\Temp\ScrollOfEru.inf | C:\Windows\System32\cmstp.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Connection Manager Profile Installer Exit code: 0 Version: 7.2.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 880 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1016 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5072 --field-trial-handle=1940,i,5214472131177649609,16186631295709850380,262144 --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1140 | taskkill /IM cmstp.exe /F | C:\Windows\System32\taskkill.exe | — | dllhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1796 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5500 --field-trial-handle=1940,i,5214472131177649609,16186631295709850380,262144 --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1876 | taskkill /IM cmstp.exe /F | C:\Windows\System32\taskkill.exe | — | dllhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2100 | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RESE425.tmp" "c:\Users\admin\AppData\Local\Temp\CSC540ED75551342649D98293B1C12886B.TMP" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 14.32.31326.0 Modules
| |||||||||||||||
| 2124 | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES6674.tmp" "c:\Users\admin\AppData\Local\Temp\CSC607EA0731C174827BC5117724A0A3D9.TMP" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 14.32.31326.0 Modules
| |||||||||||||||
Total events
49 028
Read events
48 874
Write events
151
Delete events
3
Modification events
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Feeds\DSB |
| Operation: | write | Name: | DynamicText |
Value: | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Feeds\DSB |
| Operation: | write | Name: | DynamicTextTruncated |
Value: | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | \REGISTRY\A\{ee080948-b2ea-145a-6870-f9164b908eb9}\LocalState\DynamicSearchBox |
| Operation: | write | Name: | TelemetryID |
Value: 00005AF8C154E871DB01 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | \REGISTRY\A\{ee080948-b2ea-145a-6870-f9164b908eb9}\LocalState\DynamicSearchBox |
| Operation: | write | Name: | TelemetryID |
Value: 0000BC5BC454E871DB01 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.search_cw5n1h2txyewy\Internet Explorer\DOMStorage\bing.com |
| Operation: | write | Name: | Total |
Value: 50667 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.search_cw5n1h2txyewy\Internet Explorer\DOMStorage\bing.com |
| Operation: | write | Name: | Total |
Value: 929 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | \REGISTRY\A\{ee080948-b2ea-145a-6870-f9164b908eb9}\LocalState\ConstraintIndex |
| Operation: | write | Name: | CurrentConstraintIndexCabPath |
Value: 43003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C005000610063006B0061006700650073005C004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E005300650061007200630068005F006300770035006E003100680032007400780079006500770079005C004C006F00630061006C00530074006100740065005C0043006F006E00730074007200610069006E00740049006E006400650078005C0049006E007000750074005F007B00380033003200620036003800640032002D0037006600650032002D0034006500370031002D0061003300610064002D003200360031003600360062003600350036006500630036007D00000061845D57E871DB01 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | \REGISTRY\A\{ee080948-b2ea-145a-6870-f9164b908eb9}\LocalState\AppsConstraintIndex |
| Operation: | write | Name: | LatestConstraintIndexFolder |
Value: 43003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C005000610063006B0061006700650073005C004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E005300650061007200630068005F006300770035006E003100680032007400780079006500770079005C004C006F00630061006C00530074006100740065005C0043006F006E00730074007200610069006E00740049006E006400650078005C0041007000700073005F007B00330039006600320035003400650063002D0037003500330039002D0034003100370038002D0061006500370062002D003800360065006500620065003400320036003000340063007D00000061845D57E871DB01 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | \REGISTRY\A\{ee080948-b2ea-145a-6870-f9164b908eb9}\LocalState\AppsConstraintIndex |
| Operation: | write | Name: | LastConstraintIndexBuildCompleted |
Value: 25595F57E871DB0161845D57E871DB01 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Search\Microsoft.Windows.Search_cw5n1h2txyewy\AppsConstraintIndex |
| Operation: | write | Name: | CurrentConstraintIndexCabPath |
Value: C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\LocalState\ConstraintIndex\Input_{832b68d2-7fe2-4e71-a3ad-26166b656ec6} | |||
Executable files
6
Suspicious files
124
Text files
162
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6092 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\7CTCW8S3AGSK9QCPTNL6.temp | binary | |
MD5:0AD956122332873E3E7EC505ECC2A94A | SHA256:09618F079912DCD4F7076E5CFD6A923F102335221D50F030B08B6DF9C5D7F690 | |||
| 6092 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_kib5li0r.hj5.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6092 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_0tbizrql.s24.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\LocalState\ConstraintIndex\Apps_{39f254ec-7539-4178-ae7b-86eebe42604c}\0.2.filtertrie.intermediate.txt | text | |
MD5:C204E9FAAF8565AD333828BEFF2D786E | SHA256:D65B6A3BF11A27A1CED1F7E98082246E40CF01289FD47FE4A5ED46C221F2F73F | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\LocalState\ConstraintIndex\Apps_{39f254ec-7539-4178-ae7b-86eebe42604c}\0.1.filtertrie.intermediate.txt | text | |
MD5:34BD1DFB9F72CF4F86E6DF6DA0A9E49A | SHA256:8E1E6A3D56796A245D0C7B0849548932FEE803BBDB03F6E289495830E017F14C | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\LocalState\ConstraintIndex\Apps_{39f254ec-7539-4178-ae7b-86eebe42604c}\Apps.ft | binary | |
MD5:AB5CF5D309581951ACE7978FF8DF0FF0 | SHA256:CA45CAA7DE38CB805EC43EDC8B9332E1E95124A27FBB6E5BD3DDD5E8A526AFC7 | |||
| 6092 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RF1355d4.TMP | binary | |
MD5:D040F64E9E7A2BB91ABCA5613424598E | SHA256:D04E0A6940609BD6F3B561B0F6027F5CA4E8C5CF0FB0D0874B380A0374A8D670 | |||
| 6092 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:0AD956122332873E3E7EC505ECC2A94A | SHA256:09618F079912DCD4F7076E5CFD6A923F102335221D50F030B08B6DF9C5D7F690 | |||
| 6772 | cvtres.exe | C:\Users\admin\AppData\Local\Temp\RES6A27.tmp | binary | |
MD5:00EE9C71A0728CDBAA22706E29ECDCBF | SHA256:8BE0CB366BE5EED79FD3EEBC84E582DD9290109D9432E1CF6748620F3B7C5C14 | |||
| 6552 | csc.exe | C:\Users\admin\AppData\Local\Temp\j1mb45bz.out | text | |
MD5:B6E1716B96F064B1E2682A04CDF27CCA | SHA256:9F0021A56A2679DE06E55E37E1C6A24FA4E5D574A6C8E32120D021D1ECE712FC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
55
DNS requests
38
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5064 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.78.32:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6180 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5536 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5536 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
132 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 104.126.37.131:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5064 | SearchApp.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 95.101.78.32:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1076 | svchost.exe | 184.30.18.9:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |