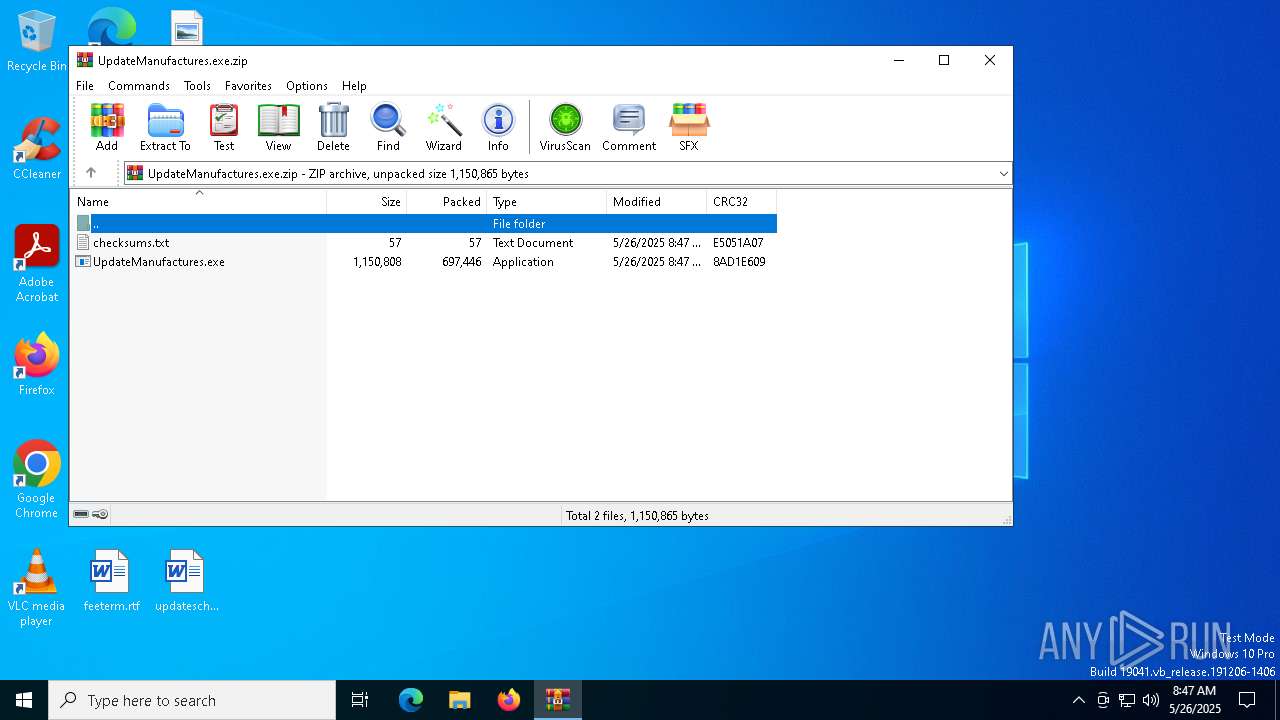
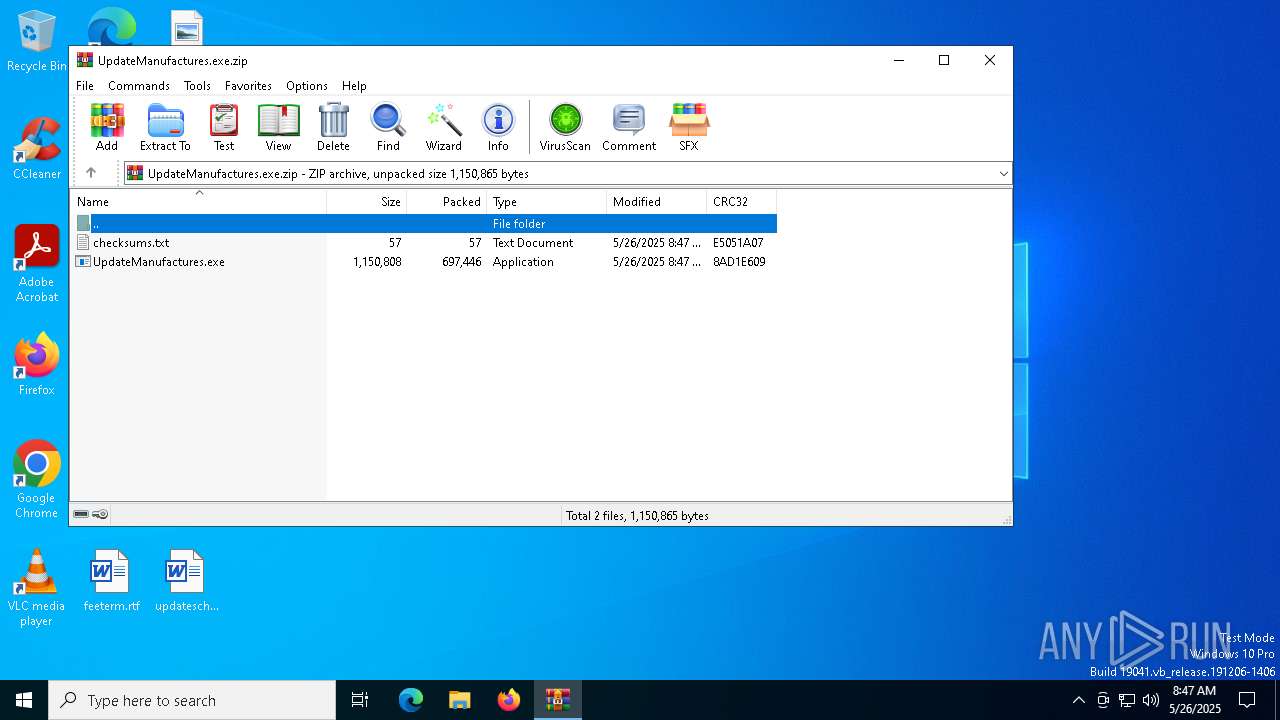
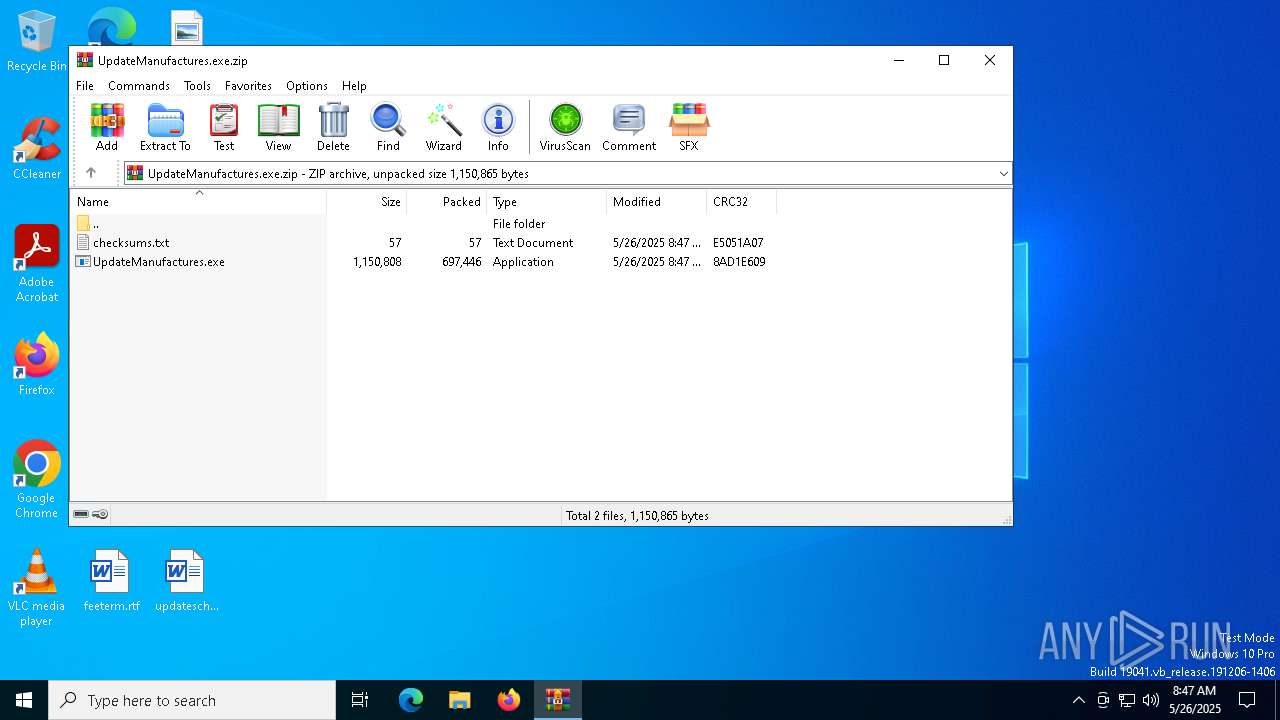
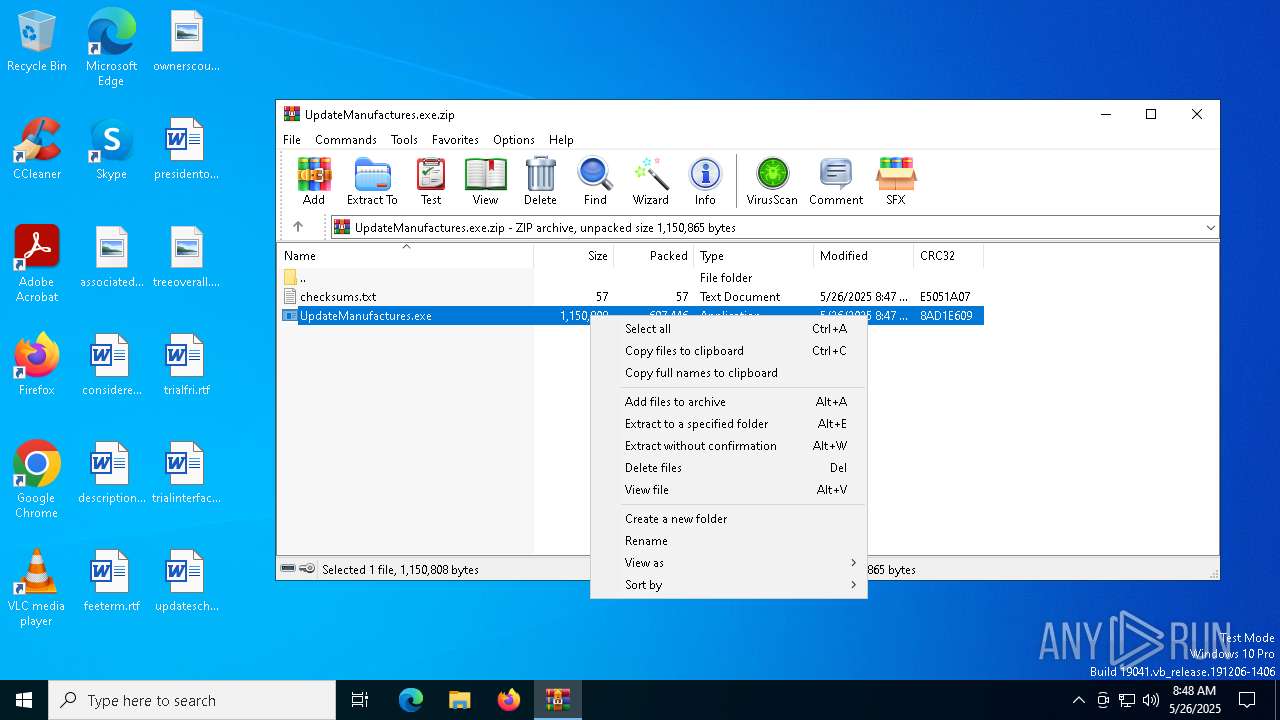
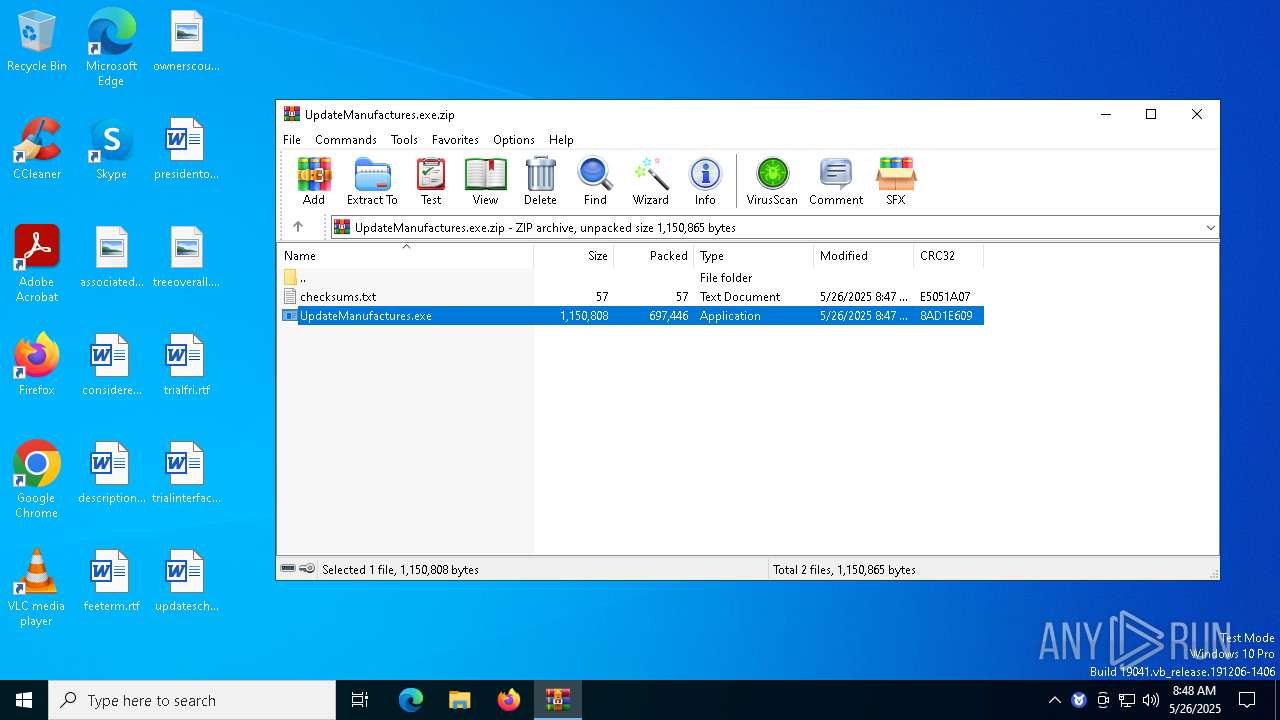
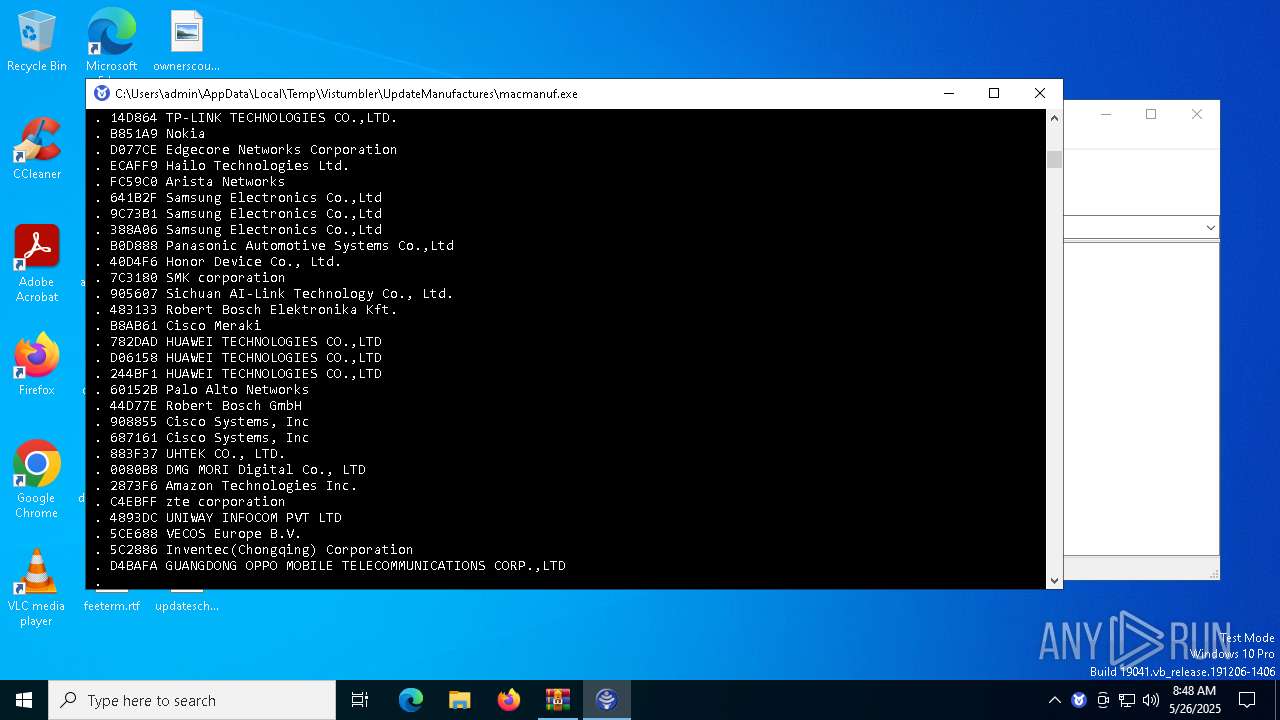
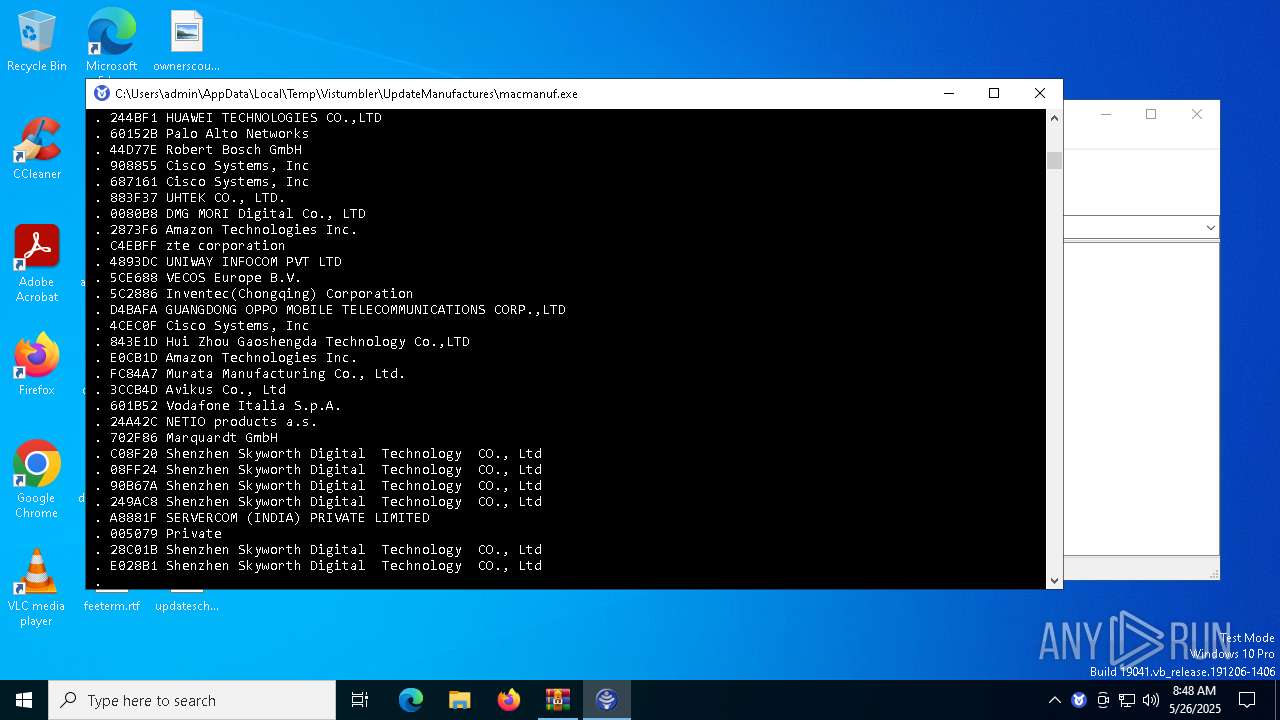
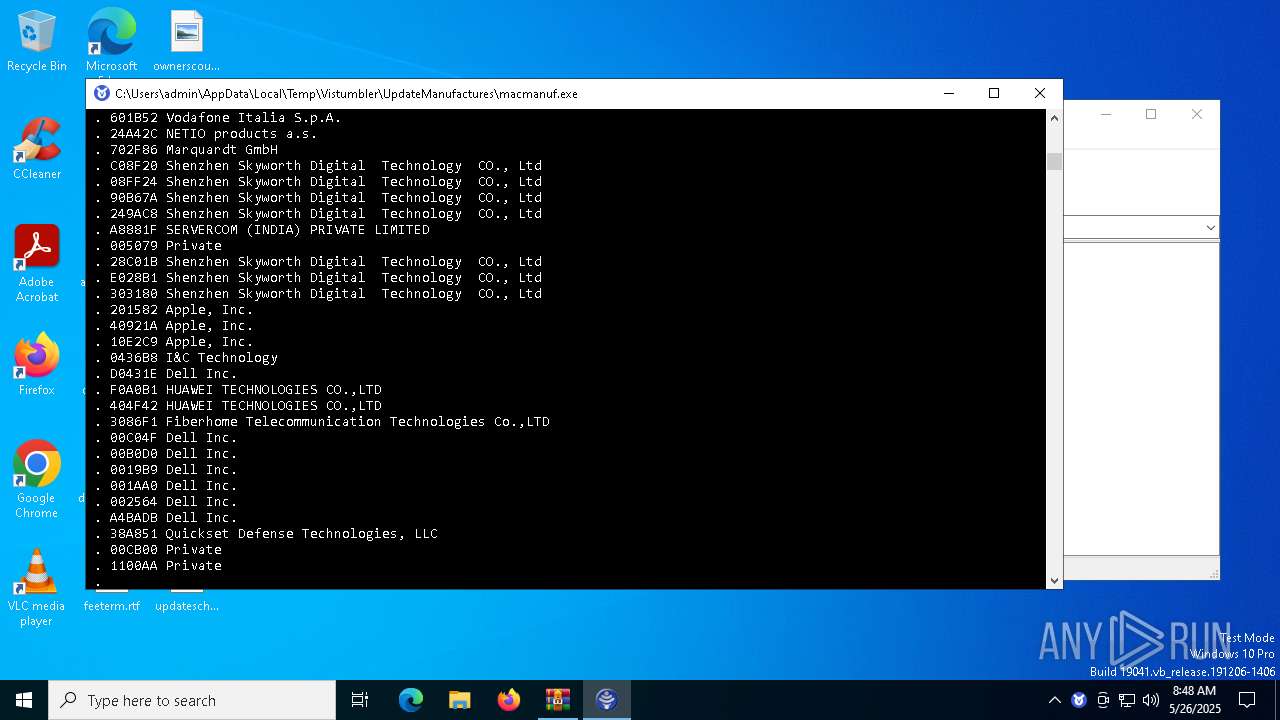
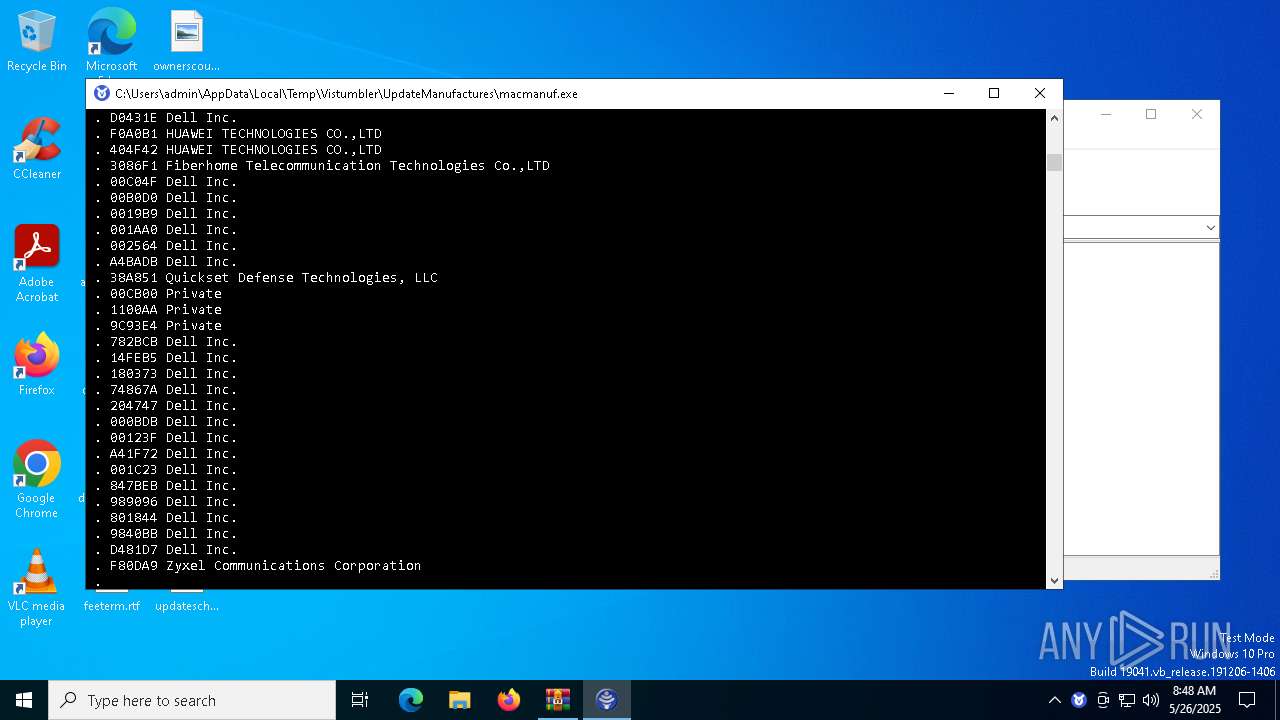
| File name: | UpdateManufactures.exe.zip |
| Full analysis: | https://app.any.run/tasks/24b826da-c625-4b0c-b130-682f3670da14 |
| Verdict: | Malicious activity |
| Analysis date: | May 26, 2025, 08:47:39 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 6FA09B4B0C2DF69479F27286A7F8847F |
| SHA1: | 29446E596563B58DAEFB6DD30EFA306C253EB10B |
| SHA256: | A1D1609707FE18E73157B3CDD2701429737F802E2F55155C61A9D8C6D544A967 |
| SSDEEP: | 24576:f+CEfe7q/RX9USaZ0op8EfXejDNKxz+pLTPexEoj18sBNuo27Ui:f+CEfe7q/RX9USaZ0op8gXeFQz+pLTPL |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 7364)
Executing a file with an untrusted certificate
- UpdateManufactures.exe (PID: 7996)
- UpdateManufactures.exe (PID: 8044)
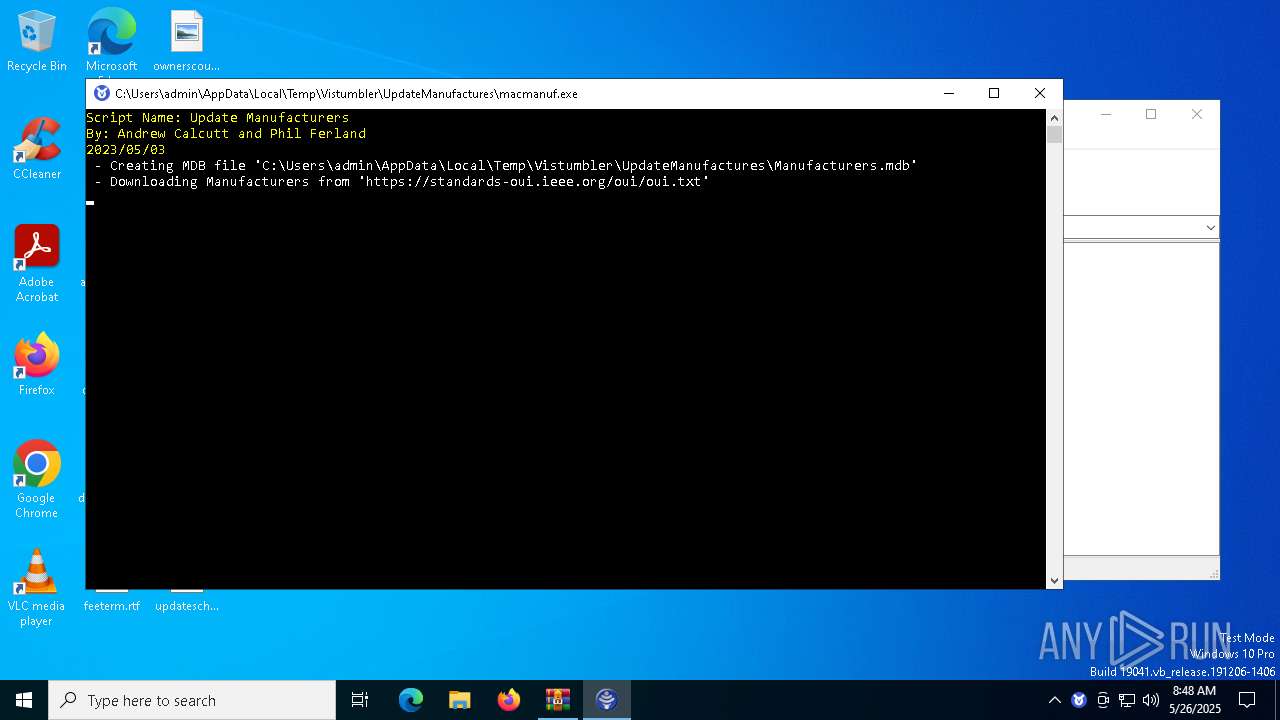
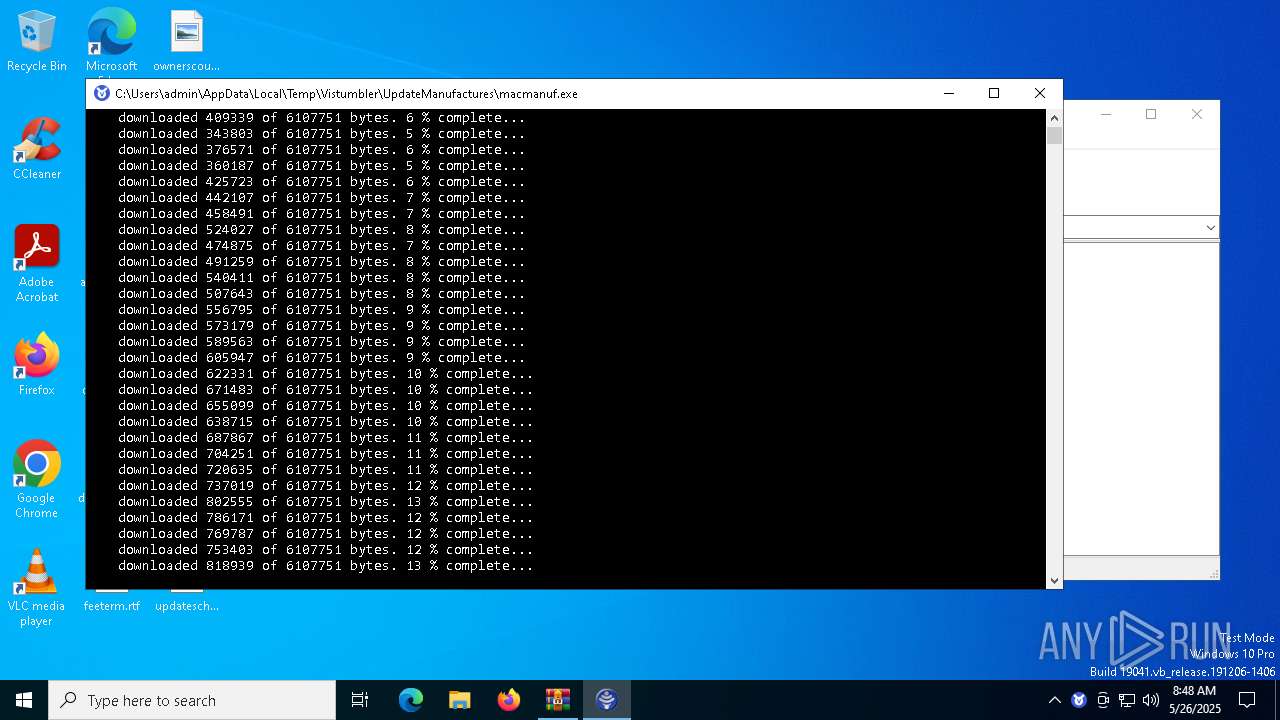
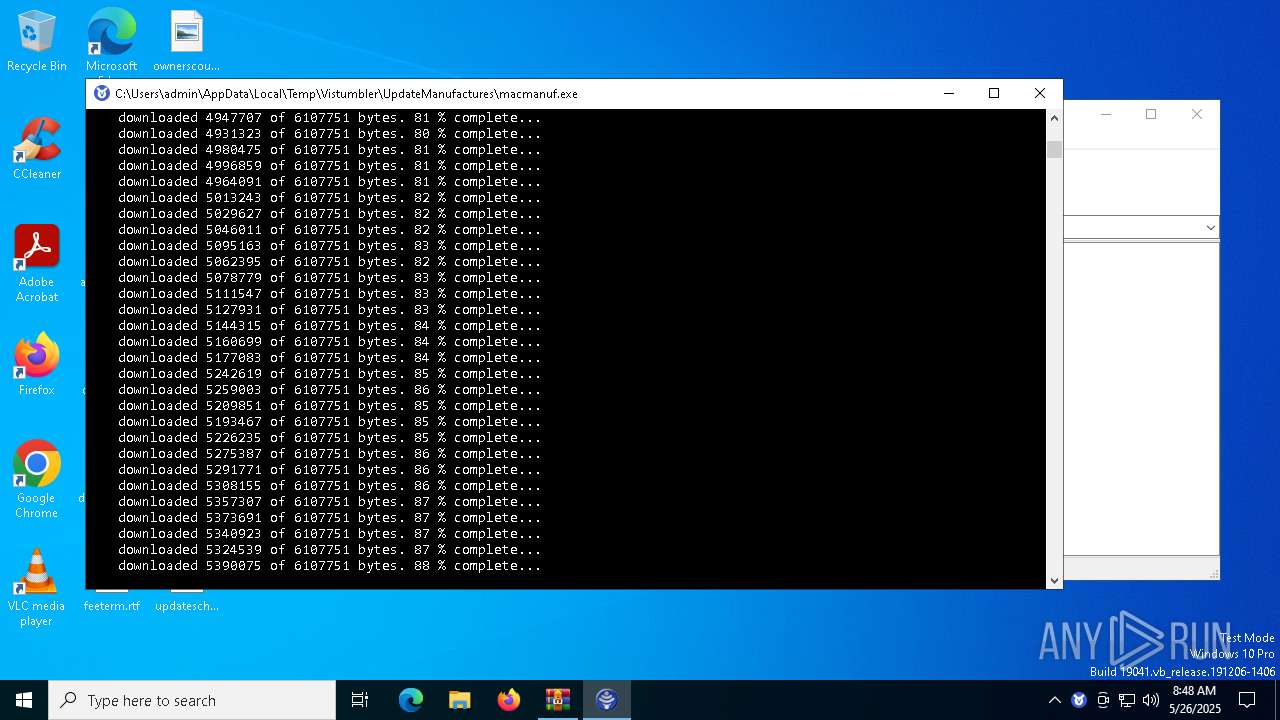
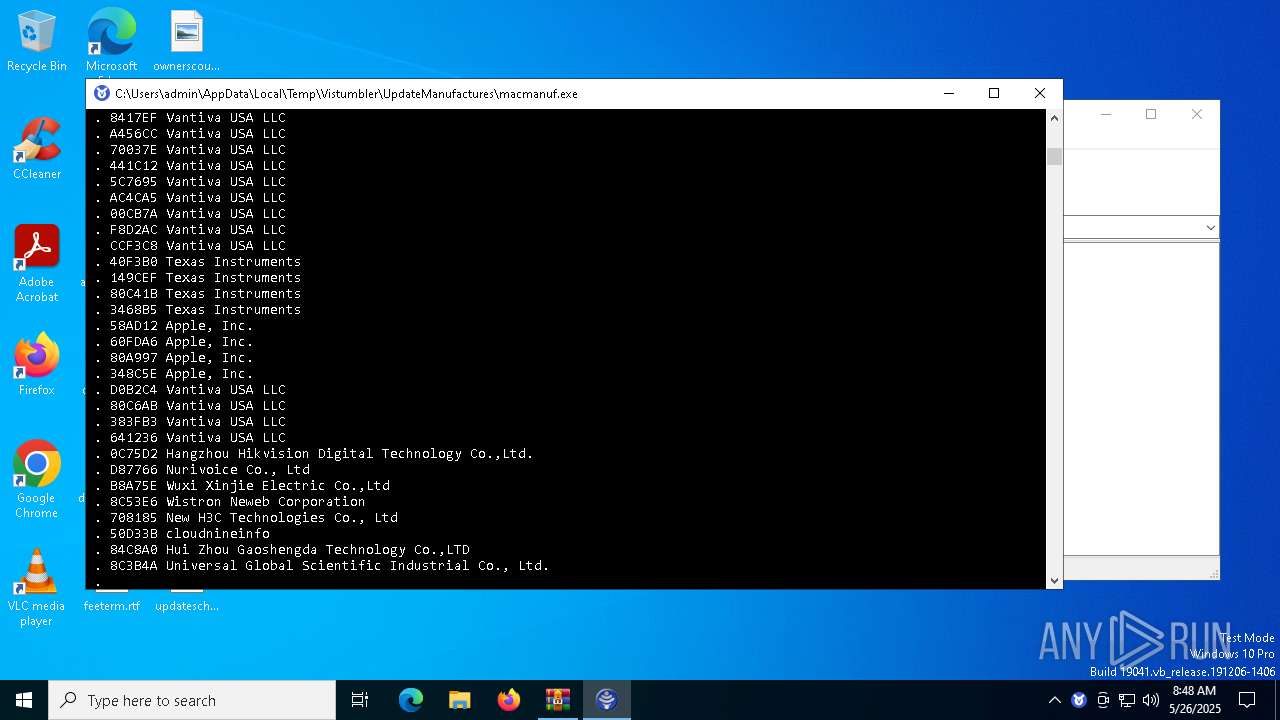
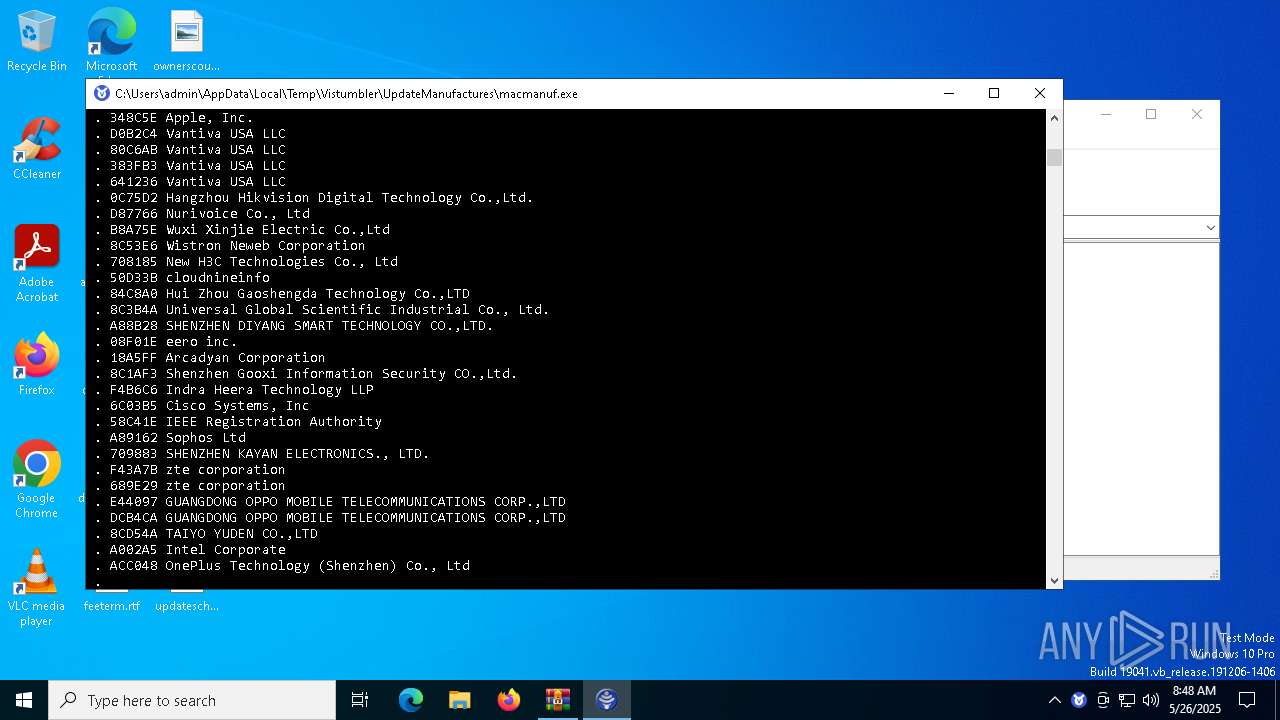
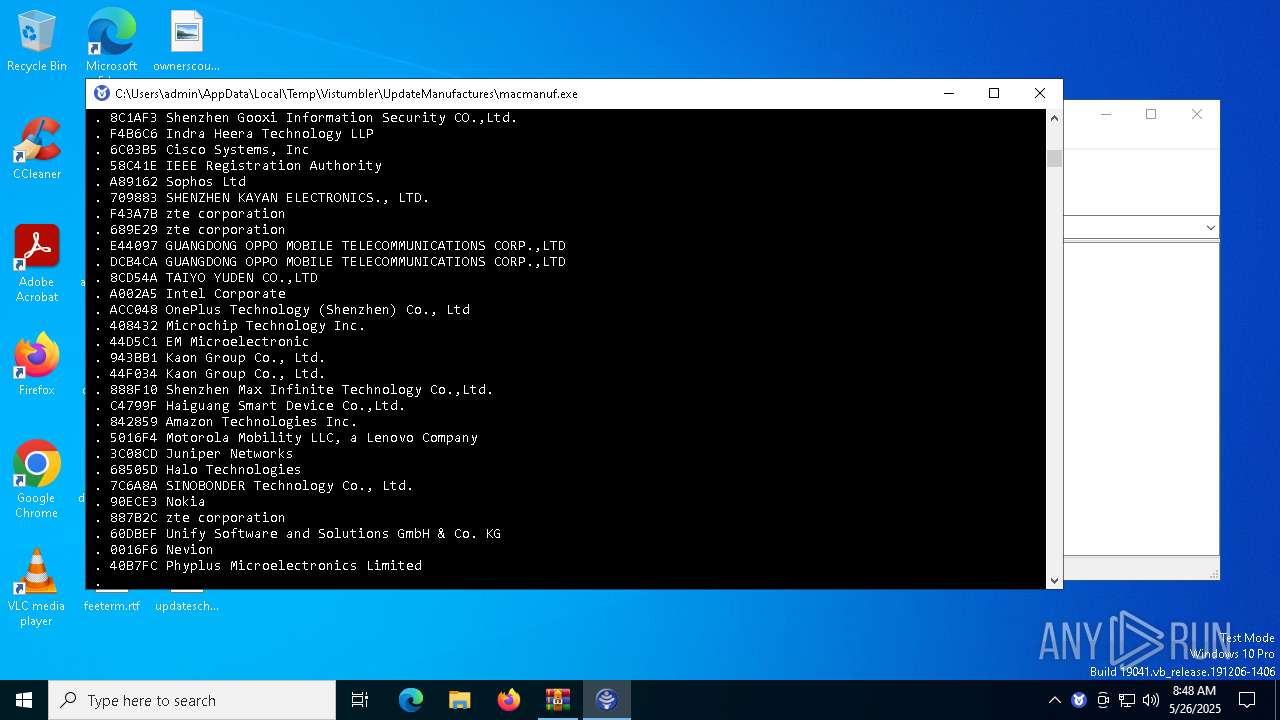
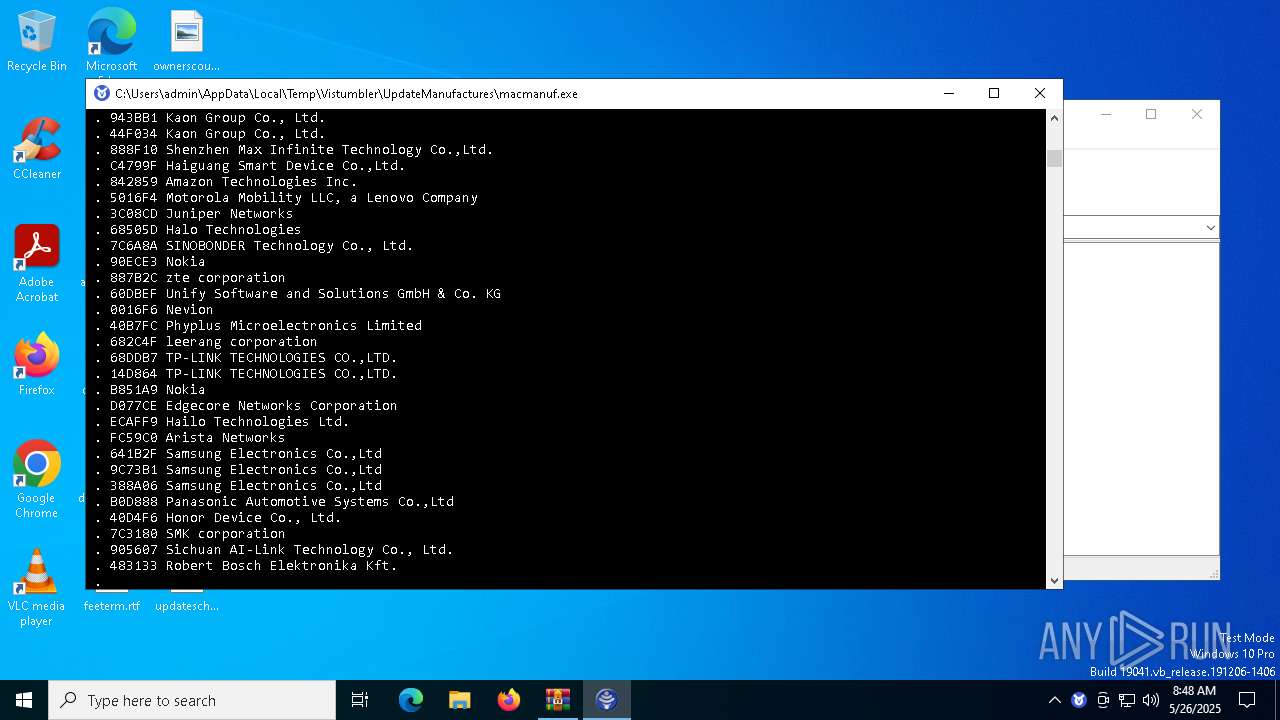
- macmanuf.exe (PID: 8068)
SUSPICIOUS
Executable content was dropped or overwritten
- UpdateManufactures.exe (PID: 8044)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7364)
There is functionality for taking screenshot (YARA)
- UpdateManufactures.exe (PID: 8044)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 7364)
Reads mouse settings
- UpdateManufactures.exe (PID: 8044)
Create files in a temporary directory
- UpdateManufactures.exe (PID: 8044)
- macmanuf.exe (PID: 8068)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7364)
Checks supported languages
- UpdateManufactures.exe (PID: 8044)
- macmanuf.exe (PID: 8068)
Reads the computer name
- macmanuf.exe (PID: 8068)
Reads the machine GUID from the registry
- macmanuf.exe (PID: 8068)
Disables trace logs
- macmanuf.exe (PID: 8068)
Checks proxy server information
- macmanuf.exe (PID: 8068)
Reads the software policy settings
- macmanuf.exe (PID: 8068)
The process uses AutoIt
- UpdateManufactures.exe (PID: 8044)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:05:26 08:47:14 |
| ZipCRC: | 0x8ad1e609 |
| ZipCompressedSize: | 697446 |
| ZipUncompressedSize: | 1150808 |
| ZipFileName: | UpdateManufactures.exe |
Total processes
137
Monitored processes
7
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 7364 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\UpdateManufactures.exe.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | |
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 | ||||
| 7564 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe |
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) | ||||
| 7596 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe |
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||
| 7996 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa7364.10627\UpdateManufactures.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa7364.10627\UpdateManufactures.exe | — | WinRAR.exe |
User: admin Integrity Level: MEDIUM Exit code: 3221226540 | ||||
| 8044 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa7364.10627\UpdateManufactures.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa7364.10627\UpdateManufactures.exe | WinRAR.exe | |
User: admin Integrity Level: HIGH | ||||
| 8068 | C:\Users\admin\AppData\Local\Temp\Vistumbler\UpdateManufactures\\macmanuf.exe | C:\Users\admin\AppData\Local\Temp\Vistumbler\UpdateManufactures\macmanuf.exe | UpdateManufactures.exe | |
User: admin Integrity Level: HIGH Description: macmanuf Version: 1.0.0.0 | ||||
| 8076 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | macmanuf.exe |
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
3
Suspicious files
3
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
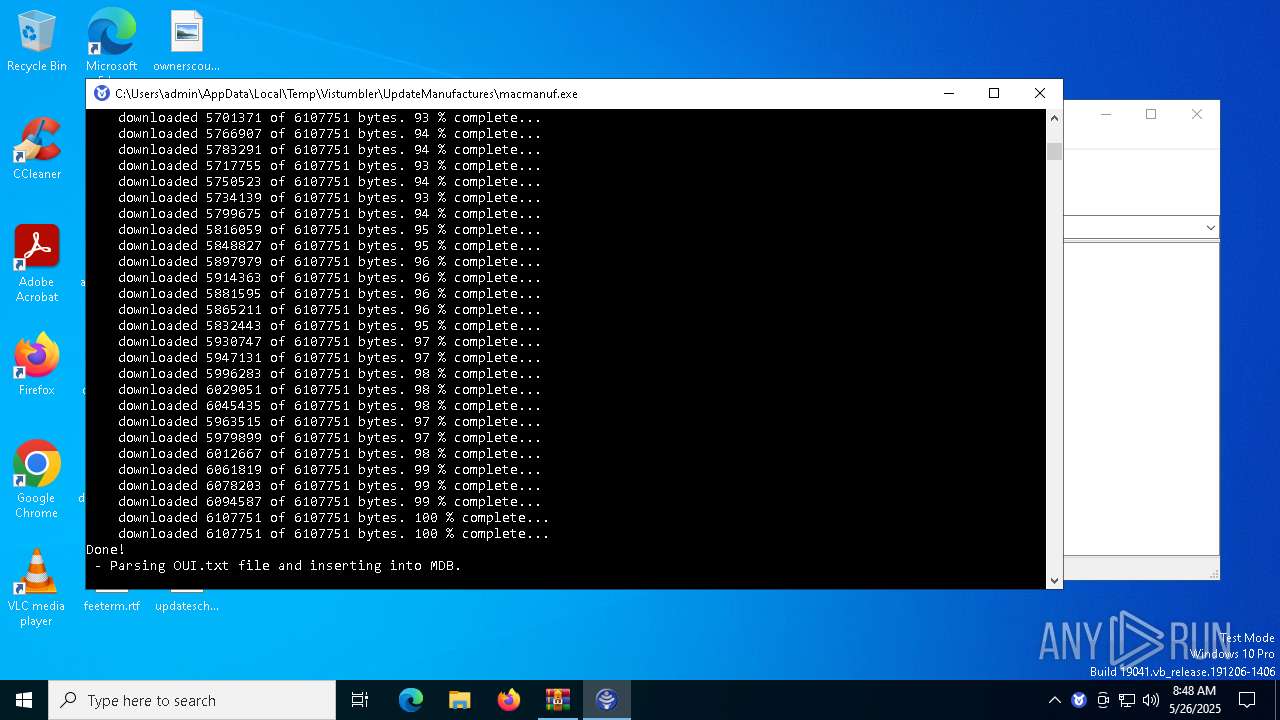
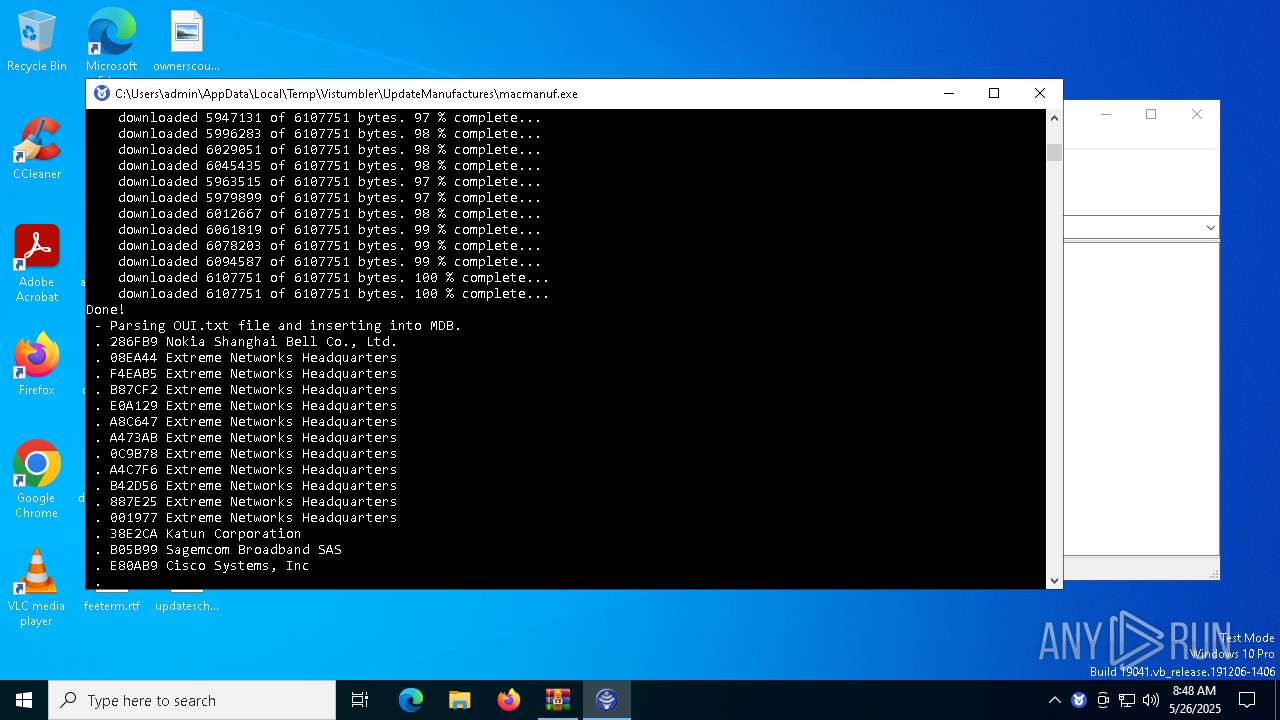
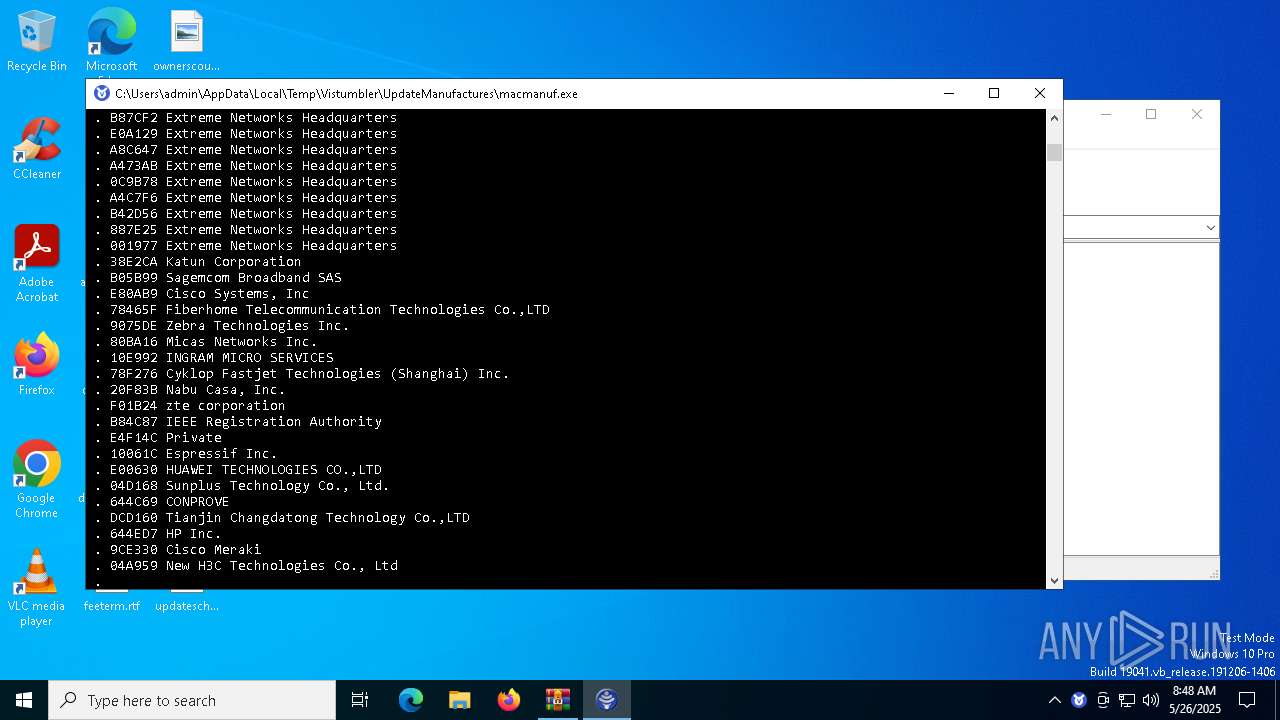
| 8068 | macmanuf.exe | C:\Users\admin\AppData\Local\Temp\Vistumbler\UpdateManufactures\oui.txt | — | |
MD5:— | SHA256:— | |||
| 7364 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\UpdateManufactures.exe\UpdateManufactures.exe | executable | |
MD5:7814D57F6FC87A3CEE370FAB4E70F4BB | SHA256:3C047980CD5D2B43065A55802F1DD953D7CACA6D08D27183E95CD80B2201E060 | |||
| 7364 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7364.10627\UpdateManufactures.exe | executable | |
MD5:7814D57F6FC87A3CEE370FAB4E70F4BB | SHA256:3C047980CD5D2B43065A55802F1DD953D7CACA6D08D27183E95CD80B2201E060 | |||
| 7364 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7364.10627\checksums.txt | text | |
MD5:C72F0CF0396974F13972BDFE292BABA0 | SHA256:AEDBF762B36541427998602F02A254F8E4C59CC34C0D003668A53181DCDE0736 | |||
| 8068 | macmanuf.exe | C:\Users\admin\AppData\Local\Temp\Vistumbler\UpdateManufactures\Manufacturers.ldb | binary | |
MD5:D2997E653249DCDA82A9508E13E1A0DD | SHA256:0626CD23F403884D3B0F0D540A2FFCAA9CF2E128F1E80E6B80671B4EE3228D5F | |||
| 8044 | UpdateManufactures.exe | C:\Users\admin\AppData\Local\Temp\aut2930.tmp | binary | |
MD5:6E4FE8241BCB28034797F3DD12EA874F | SHA256:02C03C603879984287354A47B7259301826EE323CCB5FA00233CECECCF6D8F58 | |||
| 8068 | macmanuf.exe | C:\Users\admin\AppData\Local\Temp\Vistumbler\UpdateManufactures\Manufacturers.mdb | binary | |
MD5:4626E590D8839D4CE589E74308266C9F | SHA256:B1C872BB527997911CABAB3A648D355051B2A44E30E56476ED78FF9D43C8EE58 | |||
| 8044 | UpdateManufactures.exe | C:\Users\admin\AppData\Local\Temp\Vistumbler\UpdateManufactures\macmanuf.exe | executable | |
MD5:8D44B706F88990FABA3E45BA208A0047 | SHA256:51B87B1A5E0CC797E59966A82BC28C1E427812DAD6B408D93E421FB2200B1236 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
19
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7796 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7796 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1196 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5796 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 40.126.32.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
standards-oui.ieee.org |
| whitelisted |