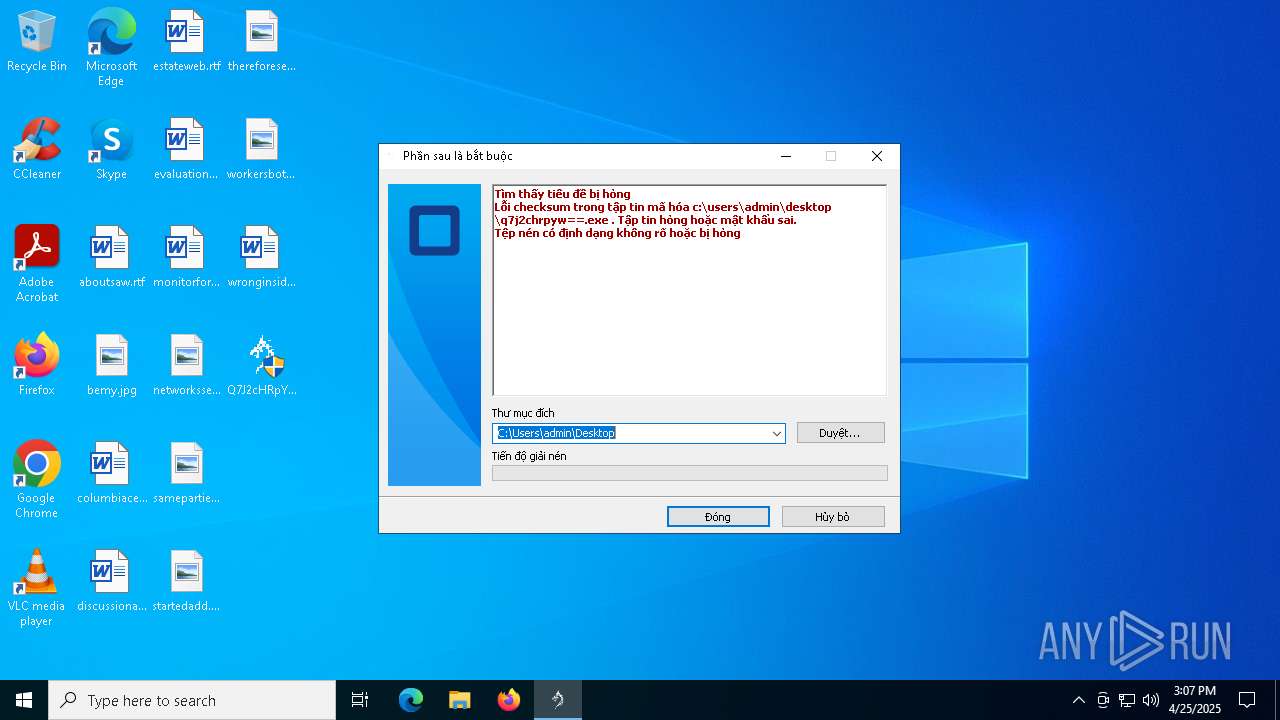
| File name: | Q7J2cHRpYw==.exe |
| Full analysis: | https://app.any.run/tasks/3529f8e3-6041-4306-9704-68e35af6e9f5 |
| Verdict: | Malicious activity |
| Analysis date: | April 25, 2025, 15:06:43 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 3 sections |
| MD5: | 28044DC7B6BB4DA91FCC3CADDBA99BA9 |
| SHA1: | FFCF5EF0D3FFFFE51326B42CD2F490A78B48E5D8 |
| SHA256: | A1CC95F939E5C7648B63DC8734F5DCEA8FBFE718C447D1811850E30E8F0543C0 |
| SSDEEP: | 98304:5cKM0F9Zo4tRDlocWQ1xIxy+DMwcc+rkOJUgbMgSwXefhoGlcY1hIqFLL2gcSlM:/As |
MALICIOUS
JEEFO has been detected
- Q7J2cHRpYw==.exe (PID: 6372)
- icsys.icn.exe (PID: 4560)
- explorer.exe (PID: 5116)
- svchost.exe (PID: 6148)
- Q7J2cHRpYw==.exe (PID: 4220)
- icsys.icn.exe (PID: 2392)
- explorer.exe (PID: 6808)
- icsys.icn.exe (PID: 632)
- Q7J2cHRpYw==.exe (PID: 7000)
- explorer.exe (PID: 1328)
- icsys.icn.exe (PID: 6036)
- explorer.exe (PID: 1764)
- Q7J2cHRpYw==.exe (PID: 5556)
Changes the autorun value in the registry
- explorer.exe (PID: 5116)
- svchost.exe (PID: 6148)
SUSPICIOUS
Starts application with an unusual extension
- Q7J2cHRpYw==.exe (PID: 6372)
- Q7J2cHRpYw==.exe (PID: 4220)
- Q7J2cHRpYw==.exe (PID: 7000)
- Q7J2cHRpYw==.exe (PID: 5556)
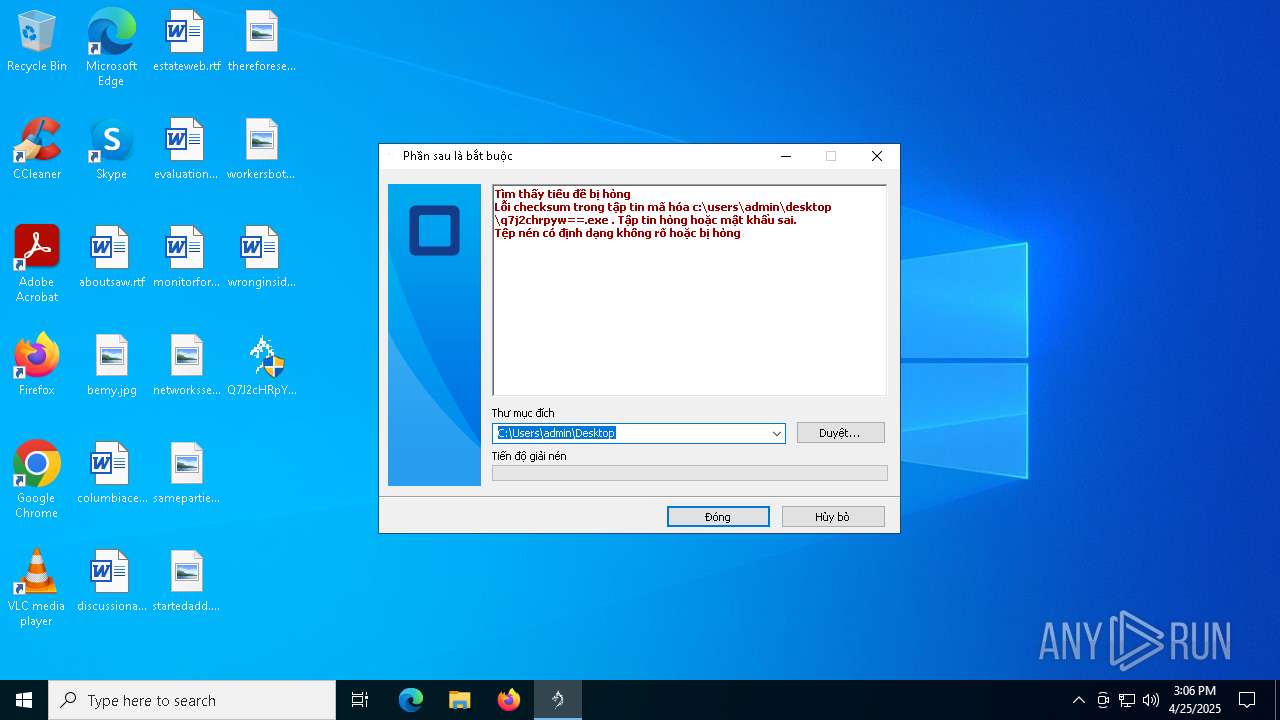
Executable content was dropped or overwritten
- Q7J2cHRpYw==.exe (PID: 6372)
- icsys.icn.exe (PID: 4560)
- explorer.exe (PID: 5116)
- spoolsv.exe (PID: 496)
- Q7J2cHRpYw==.exe (PID: 4220)
- Q7J2cHRpYw==.exe (PID: 7000)
- Q7J2cHRpYw==.exe (PID: 5556)
Starts itself from another location
- Q7J2cHRpYw==.exe (PID: 6372)
- icsys.icn.exe (PID: 4560)
- spoolsv.exe (PID: 496)
- svchost.exe (PID: 6148)
- explorer.exe (PID: 5116)
- Q7J2cHRpYw==.exe (PID: 4220)
- icsys.icn.exe (PID: 2392)
- Q7J2cHRpYw==.exe (PID: 7000)
- icsys.icn.exe (PID: 632)
- Q7J2cHRpYw==.exe (PID: 5556)
- icsys.icn.exe (PID: 6036)
The process creates files with name similar to system file names
- icsys.icn.exe (PID: 4560)
- spoolsv.exe (PID: 496)
Reads Microsoft Outlook installation path
- q7j2chrpyw==.exe (PID: 5988)
Reads security settings of Internet Explorer
- q7j2chrpyw==.exe (PID: 5988)
Reads Internet Explorer settings
- q7j2chrpyw==.exe (PID: 5988)
INFO
Checks supported languages
- Q7J2cHRpYw==.exe (PID: 6372)
- q7j2chrpyw==.exe (PID: 4200)
- icsys.icn.exe (PID: 4560)
- explorer.exe (PID: 5116)
- spoolsv.exe (PID: 496)
- spoolsv.exe (PID: 6036)
- svchost.exe (PID: 6148)
- Q7J2cHRpYw==.exe (PID: 4220)
- icsys.icn.exe (PID: 2392)
- q7j2chrpyw==.exe (PID: 5972)
- explorer.exe (PID: 6808)
- Q7J2cHRpYw==.exe (PID: 7000)
- q7j2chrpyw==.exe (PID: 2852)
- icsys.icn.exe (PID: 632)
- explorer.exe (PID: 1328)
- Q7J2cHRpYw==.exe (PID: 5556)
- q7j2chrpyw==.exe (PID: 5988)
- icsys.icn.exe (PID: 6036)
- explorer.exe (PID: 1764)
Create files in a temporary directory
- Q7J2cHRpYw==.exe (PID: 6372)
- icsys.icn.exe (PID: 4560)
- explorer.exe (PID: 5116)
- spoolsv.exe (PID: 496)
- svchost.exe (PID: 6148)
- spoolsv.exe (PID: 6036)
- Q7J2cHRpYw==.exe (PID: 7000)
- icsys.icn.exe (PID: 2392)
- explorer.exe (PID: 6808)
- Q7J2cHRpYw==.exe (PID: 4220)
- explorer.exe (PID: 1328)
- Q7J2cHRpYw==.exe (PID: 5556)
- icsys.icn.exe (PID: 632)
- icsys.icn.exe (PID: 6036)
- explorer.exe (PID: 1764)
The sample compiled with english language support
- Q7J2cHRpYw==.exe (PID: 6372)
- icsys.icn.exe (PID: 4560)
- explorer.exe (PID: 5116)
- spoolsv.exe (PID: 496)
- Q7J2cHRpYw==.exe (PID: 4220)
- Q7J2cHRpYw==.exe (PID: 7000)
- Q7J2cHRpYw==.exe (PID: 5556)
Reads the computer name
- q7j2chrpyw==.exe (PID: 4200)
- svchost.exe (PID: 6148)
- q7j2chrpyw==.exe (PID: 5972)
- q7j2chrpyw==.exe (PID: 2852)
- q7j2chrpyw==.exe (PID: 5988)
Manual execution by a user
- Q7J2cHRpYw==.exe (PID: 5408)
- Q7J2cHRpYw==.exe (PID: 4220)
- Q7J2cHRpYw==.exe (PID: 7144)
- Q7J2cHRpYw==.exe (PID: 7000)
- Q7J2cHRpYw==.exe (PID: 6040)
- Q7J2cHRpYw==.exe (PID: 5556)
Checks proxy server information
- q7j2chrpyw==.exe (PID: 5988)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2013:04:01 07:08:22+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 106496 |
| InitializedDataSize: | 12288 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x290c |
| OSVersion: | 4 |
| ImageVersion: | 1 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| ProductName: | Project1 |
| FileVersion: | 1 |
| ProductVersion: | 1 |
| InternalName: | TJprojMain |
| OriginalFileName: | TJprojMain.exe |
Total processes
160
Monitored processes
26
Malicious processes
14
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 456 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 496 | c:\windows\resources\spoolsv.exe SE | C:\Windows\Resources\spoolsv.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 632 | C:\Windows\Resources\Themes\icsys.icn.exe | C:\Windows\Resources\Themes\icsys.icn.exe | Q7J2cHRpYw==.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 1328 | c:\windows\resources\themes\explorer.exe | C:\Windows\Resources\Themes\explorer.exe | icsys.icn.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 1764 | c:\windows\resources\themes\explorer.exe | C:\Windows\Resources\Themes\explorer.exe | icsys.icn.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 2392 | C:\Windows\Resources\Themes\icsys.icn.exe | C:\Windows\Resources\Themes\icsys.icn.exe | Q7J2cHRpYw==.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 2852 | c:\users\admin\desktop\q7j2chrpyw==.exe | C:\Users\admin\Desktop\q7j2chrpyw==.exe | — | Q7J2cHRpYw==.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 3 Modules
| |||||||||||||||
| 4112 | "C:\Users\admin\Desktop\Q7J2cHRpYw==.exe" | C:\Users\admin\Desktop\Q7J2cHRpYw==.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Version: 1.00 Modules
| |||||||||||||||
| 4200 | c:\users\admin\desktop\q7j2chrpyw==.exe | C:\Users\admin\Desktop\q7j2chrpyw==.exe | — | Q7J2cHRpYw==.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 3 Modules
| |||||||||||||||
| 4220 | "C:\Users\admin\Desktop\Q7J2cHRpYw==.exe" | C:\Users\admin\Desktop\Q7J2cHRpYw==.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
Total events
1 563
Read events
1 541
Write events
16
Delete events
6
Modification events
| (PID) Process: | (5116) explorer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | Explorer |
Value: c:\windows\resources\themes\explorer.exe RO | |||
| (PID) Process: | (5116) explorer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | Svchost |
Value: c:\windows\resources\svchost.exe RO | |||
| (PID) Process: | (5116) explorer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | Explorer |
Value: | |||
| (PID) Process: | (5116) explorer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | Svchost |
Value: | |||
| (PID) Process: | (6148) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | Explorer |
Value: c:\windows\resources\themes\explorer.exe RO | |||
| (PID) Process: | (6148) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | Svchost |
Value: c:\windows\resources\svchost.exe RO | |||
| (PID) Process: | (6148) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | Explorer |
Value: | |||
| (PID) Process: | (6148) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | Svchost |
Value: | |||
| (PID) Process: | (6372) Q7J2cHRpYw==.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\VB and VBA Program Settings\Explorer\Process |
| Operation: | write | Name: | LO |
Value: 1 | |||
| (PID) Process: | (4560) icsys.icn.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\VB and VBA Program Settings\Explorer\Process |
| Operation: | write | Name: | LO |
Value: 1 | |||
Executable files
11
Suspicious files
13
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4560 | icsys.icn.exe | C:\Windows\Resources\Themes\explorer.exe | executable | |
MD5:739F7EE5FF805E7EC1FDFAA59849BFBC | SHA256:CED56A07A6767CF7B5008E44DCB2B0DFF273207BB906C1877824FFD44A74DF3C | |||
| 6372 | Q7J2cHRpYw==.exe | C:\Users\admin\Desktop\q7j2chrpyw==.exe | executable | |
MD5:D59C40C45FF520BD4748760F1E068663 | SHA256:A5E581B2977D28F975F664034ED5EFC0324A25993B7703406DEC81565445AFEF | |||
| 6036 | spoolsv.exe | C:\Users\admin\AppData\Local\Temp\~DF4429091B5E1744FB.TMP | binary | |
MD5:0AE5FA84A16EF83D753F24E7029A9FBD | SHA256:24D0618D3DF9B760EC0EDF6D63927859AFD2D8D4DF70E177EDB82F2475B9F5DA | |||
| 496 | spoolsv.exe | C:\Users\admin\AppData\Local\Temp\~DF736DBB8139074B9D.TMP | binary | |
MD5:4A9B42E37D5E5AA385CD9B93DBB4D7E0 | SHA256:65A7BCFA929C9F59A851510FAC1EC2D1B2034BAD7E0D3E0BF66F1A9A8AD766BA | |||
| 6372 | Q7J2cHRpYw==.exe | C:\Users\admin\AppData\Local\Temp\~DF640C8E4C166644B2.TMP | binary | |
MD5:561D5E97EE34B8375FF2A07599FDC263 | SHA256:512997842A672D688C373DA649AEC0C32852E0452659798BB45E05D4A3FB3199 | |||
| 4220 | Q7J2cHRpYw==.exe | C:\Windows\Resources\Themes\icsys.icn.exe | executable | |
MD5:09DFEBE76ACB6E32C195C18CE845DCB1 | SHA256:2B1A64C5947194E9CF863E07ACC3421FE7B0581FC37850867A4FC41130BB7075 | |||
| 4220 | Q7J2cHRpYw==.exe | C:\Users\admin\Desktop\q7j2chrpyw==.exe | executable | |
MD5:D59C40C45FF520BD4748760F1E068663 | SHA256:A5E581B2977D28F975F664034ED5EFC0324A25993B7703406DEC81565445AFEF | |||
| 6808 | explorer.exe | C:\Users\admin\AppData\Local\Temp\~DFA0A73CC07A6D8942.TMP | binary | |
MD5:04EA10A0DE42E07C777942406616F63E | SHA256:486422D2CA1BE7615A0694198E7FBFBD461A065A444F916469B77D32E08187E5 | |||
| 5116 | explorer.exe | C:\Windows\Resources\spoolsv.exe | executable | |
MD5:EFE3655EB771C2E5981B609FD0F6A07A | SHA256:40CD002D6D8B53BADD0063814218C70C2527C162E6EA5F4D2A0071241889F95A | |||
| 6372 | Q7J2cHRpYw==.exe | C:\Windows\Resources\Themes\icsys.icn.exe | executable | |
MD5:09DFEBE76ACB6E32C195C18CE845DCB1 | SHA256:2B1A64C5947194E9CF863E07ACC3421FE7B0581FC37850867A4FC41130BB7075 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
19
DNS requests
13
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
920 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
920 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.19.11.105:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.19.11.105:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
— | — | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
904 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 20.190.160.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |