| File name: | Windows Update Blocker v1.7 Wub_v1.7.zip |
| Full analysis: | https://app.any.run/tasks/5d6d6a2a-73a0-43d0-9c5f-11cc6cbe97f1 |
| Verdict: | Malicious activity |
| Analysis date: | January 13, 2024, 18:33:44 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | 41315752DE5F1627677FC8F74B0AA23E |
| SHA1: | D4886E859ABE641072C412F0704815C5BFA5390A |
| SHA256: | A1BFB707B3642A0A7900FB981B7799118ACA30C1F2F6058019B9080469EE7198 |
| SSDEEP: | 49152:AuSbOU/iTpqAEZSGWHlTiQzdEgV5NJs+Sv5/mPSgUofzmkE/Ibn+SkAW9/XL8OW7:AOU6TbEZRClTiQzy85NK+s5/magrmHgX |
MALICIOUS
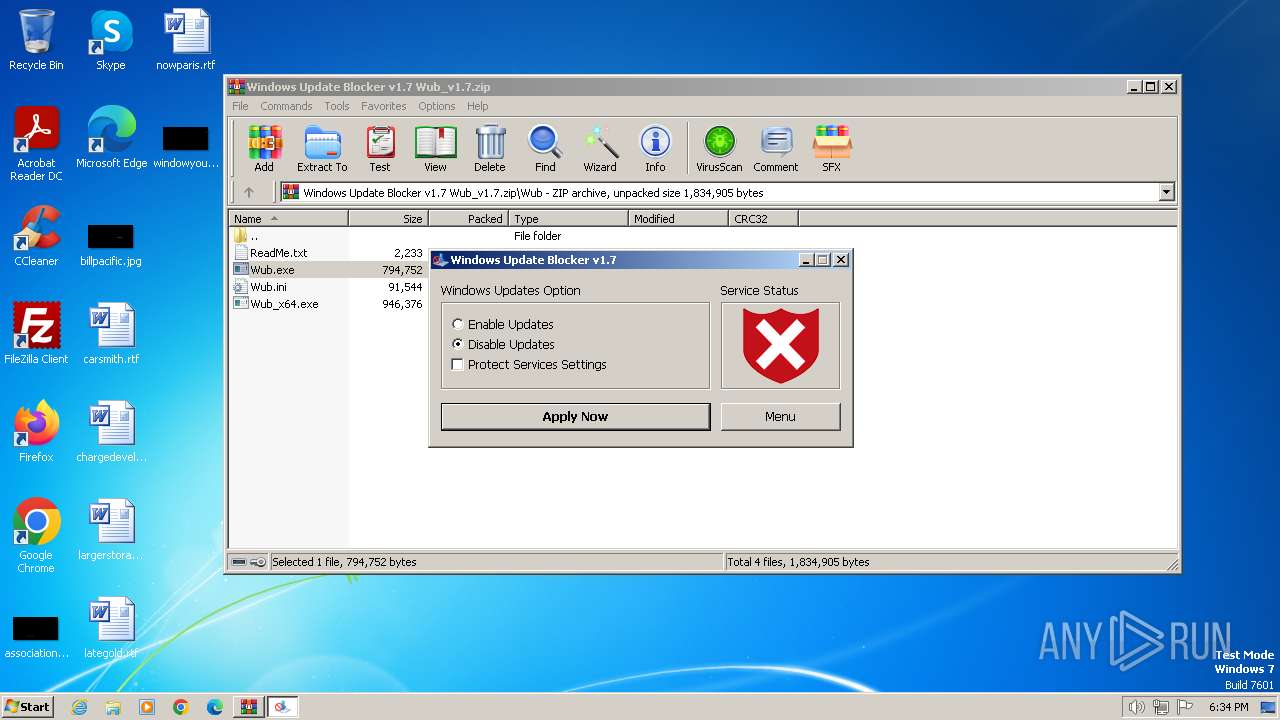
Creates or modifies Windows services
- Wub.exe (PID: 316)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2040)
SUSPICIOUS
No suspicious indicators.INFO
Reads mouse settings
- Wub.exe (PID: 316)
Checks supported languages
- Wub.exe (PID: 316)
Create files in a temporary directory
- Wub.exe (PID: 316)
Reads the computer name
- Wub.exe (PID: 316)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2040)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2022:01:28 18:20:24 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Wub/ |
Total processes
38
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 316 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2040.34427\Wub\Wub.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2040.34427\Wub\Wub.exe | WinRAR.exe | ||||||||||||
User: admin Company: www.sordum.org Integrity Level: HIGH Description: Windows Update Blocker Exit code: 0 Version: 1.7.0.0 Modules
| |||||||||||||||
| 1056 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2040.34427\Wub\Wub.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2040.34427\Wub\Wub.exe | — | WinRAR.exe | |||||||||||
User: admin Company: www.sordum.org Integrity Level: MEDIUM Description: Windows Update Blocker Exit code: 3221226540 Version: 1.7.0.0 Modules
| |||||||||||||||
| 2040 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Windows Update Blocker v1.7 Wub_v1.7.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
1 087
Read events
1 055
Write events
32
Delete events
0
Modification events
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
2
Suspicious files
4
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2040.34427\Wub\Wub_x64.exe | executable | |
MD5:418DFF42EEA894A227F78935FBD8B059 | SHA256:BF79BB5DA35061353485C7369CC5ECC9CECC79DE7543BD71CE73F7192D0F6EC3 | |||
| 2040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2040.34427\Wub\Wub.ini | text | |
MD5:7A7BBE82AA1A7F46AEBE4818800FBC03 | SHA256:2E0F9C20004D0987FCA33E68BF952A67E86BD71F55738DD3F979C6959ED5B370 | |||
| 2040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2040.34427\Wub\ReadMe.txt | text | |
MD5:EA77A7336F78B35C8E3AAFC22572CDA7 | SHA256:B765D4CA1333AE9B750005E5E8236E7CCE66E249C965E1F2A956DE38C381747A | |||
| 316 | Wub.exe | C:\Users\admin\AppData\Local\Temp\aut6FCD.tmp | binary | |
MD5:B6E44B6487FA30BC17ABEE8DBCF82CC9 | SHA256:E05CD49495C972BC56C89536ED40F43AFC47A5601CF69ADAB2F684D7E2F04B3F | |||
| 316 | Wub.exe | C:\Windows\System32\GroupPolicy\Machine\Registry.pol | binary | |
MD5:DB4A7ED73D5AF65FC281002CD6F2D1D9 | SHA256:32F4408D218A4644B98DDCEE2919DC8B185A7551C6E59D9A66ADFDC871B32E3D | |||
| 316 | Wub.exe | C:\Users\admin\AppData\Local\Temp\aut6FDE.tmp | binary | |
MD5:3CB2A4B882558785B7E42A5911ED466B | SHA256:2A68E7C8F18DB1DED5B42880792C46DFC8D2D22B864A8630BEDF879FA67B8914 | |||
| 316 | Wub.exe | C:\Users\admin\AppData\Local\Temp\6nyu3q1c.tmp | text | |
MD5:B04BCEC7DC7556B020986516FD55180D | SHA256:977466519E4153B8E60DB781294FF53BA529E66325CFA39C6CBA31975DF1DD5D | |||
| 2040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2040.34427\Wub\Wub.exe | executable | |
MD5:585C5000D1A851B295FF295389D7AA1A | SHA256:15FCCF8C018BBBED14664D5A5528CDF087B9032543BE2169D78AB25D141D2B2C | |||
| 316 | Wub.exe | C:\Users\admin\AppData\Local\Temp\aut6FDD.tmp | binary | |
MD5:1AC691FDD79F8692A85A0A6FB99B4802 | SHA256:7E1947BE4292199A16E59052DBA6C746B2235BAD9BD055CCC301DFE8F9B1B750 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |