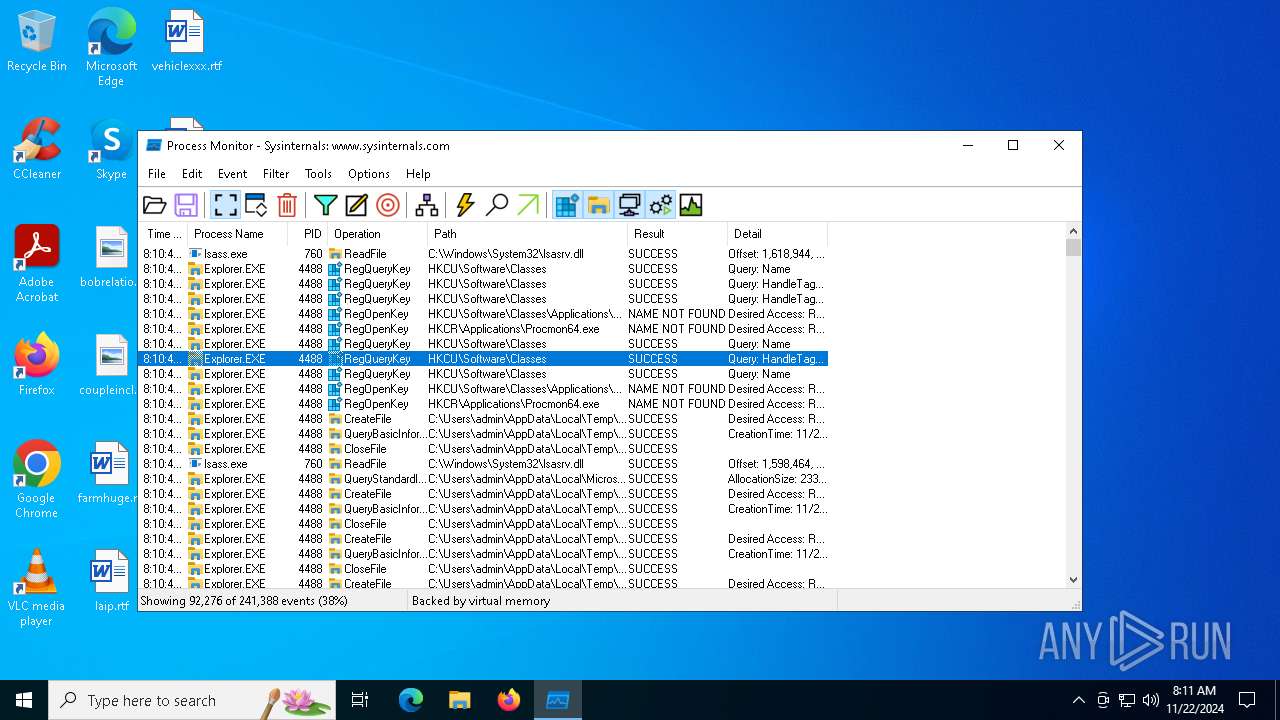
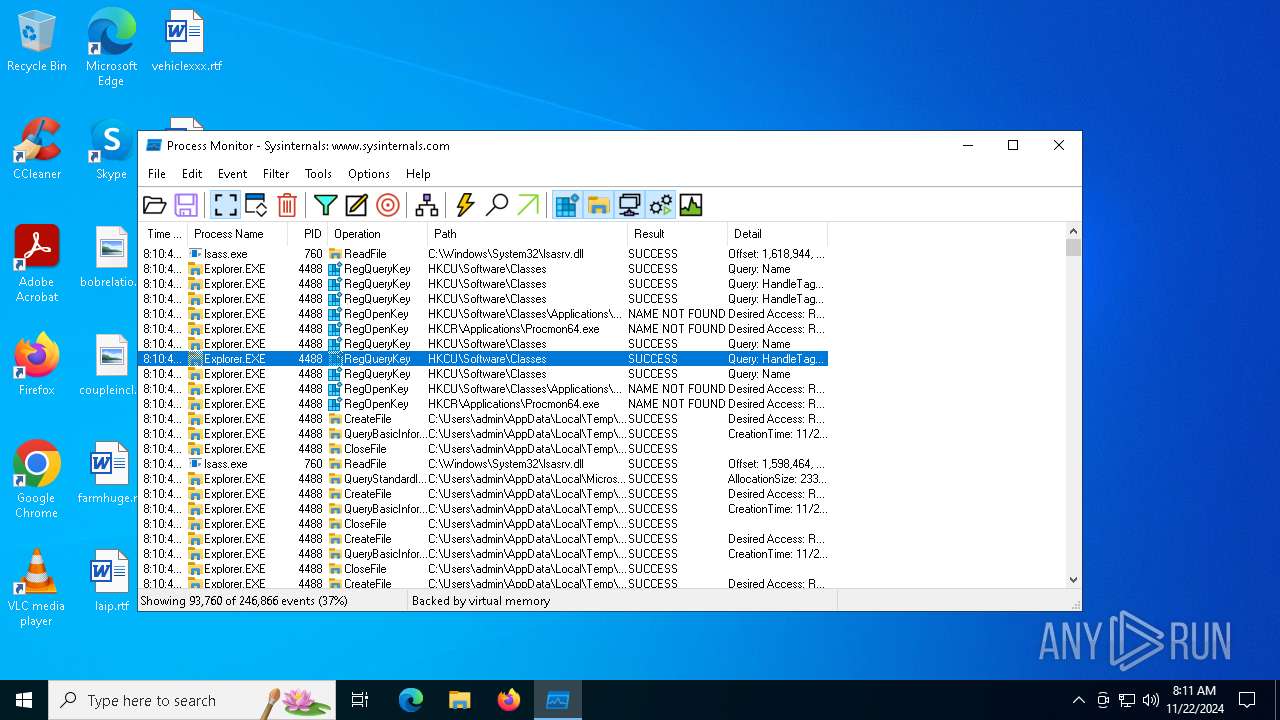
| File name: | Procmon64.exe |
| Full analysis: | https://app.any.run/tasks/7e96c03e-3b69-4c23-93af-aa24bdb2d8bd |
| Verdict: | Malicious activity |
| Analysis date: | November 22, 2024, 08:10:38 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 9 sections |
| MD5: | 6B3A6712990ED09DD166C281EC7BEE30 |
| SHA1: | 8A85F03252D045009CE0B90ADAAC537E17F89167 |
| SHA256: | A1B8C40F6DA56961081DFEE34A252FC667D22C7A22F30269D51F3F409111E787 |
| SSDEEP: | 49152:xhegl6nLmEM1JWgQh09tVPIwkxdHWiAxMSi/aDqwXyQIOxoHtP9ON:qLmb8WLDGdHWiA7EOxSx8N |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
- Procmon64.exe (PID: 4300)
Reads the date of Windows installation
- Procmon64.exe (PID: 4300)
Application launched itself
- Procmon64.exe (PID: 4300)
Creates files in the driver directory
- Procmon64.exe (PID: 848)
Executable content was dropped or overwritten
- Procmon64.exe (PID: 848)
Drops a system driver (possible attempt to evade defenses)
- Procmon64.exe (PID: 848)
Creates or modifies Windows services
- Procmon64.exe (PID: 848)
INFO
Reads product name
- Procmon64.exe (PID: 4300)
Reads the computer name
- Procmon64.exe (PID: 4300)
- Procmon64.exe (PID: 848)
Checks supported languages
- Procmon64.exe (PID: 4300)
- Procmon64.exe (PID: 848)
Process checks whether UAC notifications are on
- Procmon64.exe (PID: 4300)
Reads Environment values
- Procmon64.exe (PID: 4300)
The process uses the downloaded file
- Procmon64.exe (PID: 4300)
Process checks computer location settings
- Procmon64.exe (PID: 4300)
Reads CPU info
- Procmon64.exe (PID: 848)
Reads the time zone
- Procmon64.exe (PID: 848)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2023:09:20 14:50:05+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.35 |
| CodeSize: | 970752 |
| InitializedDataSize: | 1746944 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb6394 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.96.0.0 |
| ProductVersionNumber: | 3.96.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Sysinternals - www.sysinternals.com |
| FileDescription: | Process Monitor |
| FileVersion: | 3.96 |
| InternalName: | Process Monitor |
| LegalCopyright: | Copyright © 1996-2023 Mark Russinovich |
| OriginalFileName: | Process Monitor |
| ProductName: | Sysinternals Procmon |
| ProductVersion: | 3.96 |
Total processes
115
Monitored processes
2
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 848 | "C:\Users\admin\AppData\Local\Temp\Procmon64.exe" | C:\Users\admin\AppData\Local\Temp\Procmon64.exe | Procmon64.exe | ||||||||||||
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: HIGH Description: Process Monitor Version: 3.96 Modules
| |||||||||||||||
| 4300 | "C:\Users\admin\AppData\Local\Temp\Procmon64.exe" | C:\Users\admin\AppData\Local\Temp\Procmon64.exe | — | explorer.exe | |||||||||||
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: MEDIUM Description: Process Monitor Version: 3.96 Modules
| |||||||||||||||
Total events
861
Read events
846
Write events
11
Delete events
4
Modification events
| (PID) Process: | (4300) Procmon64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Sysinternals\Process Monitor |
| Operation: | write | Name: | EulaAccepted |
Value: 1 | |||
| (PID) Process: | (848) Procmon64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Sysinternals\Process Monitor |
| Operation: | write | Name: | EulaAccepted |
Value: 1 | |||
| (PID) Process: | (848) Procmon64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 18 | |||
| (PID) Process: | (848) Procmon64.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\PROCMON24 |
| Operation: | write | Name: | Type |
Value: 2 | |||
| (PID) Process: | (848) Procmon64.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\PROCMON24 |
| Operation: | write | Name: | ErrorControl |
Value: 1 | |||
| (PID) Process: | (848) Procmon64.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\PROCMON24 |
| Operation: | write | Name: | Start |
Value: 3 | |||
| (PID) Process: | (848) Procmon64.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\PROCMON24 |
| Operation: | write | Name: | ImagePath |
Value: \??\C:\WINDOWS\system32\Drivers\PROCMON24.SYS | |||
| (PID) Process: | (848) Procmon64.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\PROCMON24 |
| Operation: | write | Name: | SupportedFeatures |
Value: 15 | |||
| (PID) Process: | (848) Procmon64.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\PROCMON24\Instances |
| Operation: | write | Name: | DefaultInstance |
Value: Process Monitor 24 Instance | |||
| (PID) Process: | (848) Procmon64.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\PROCMON24\Instances\Process Monitor 24 Instance |
| Operation: | write | Name: | Altitude |
Value: 385200 | |||
Executable files
1
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 848 | Procmon64.exe | C:\Windows\System32\drivers\PROCMON24.SYS | executable | |
MD5:CBAED2F7F40A71A0F65CA1D7599CA530 | SHA256:650B91475689539B99DB6499E3DF2C300AD15A0C70BB33F9470C8401E3248A45 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
42
DNS requests
19
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4932 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.2:137 | — | — | — | whitelisted |
5064 | SearchApp.exe | 2.16.204.155:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5064 | SearchApp.exe | 204.79.197.222:443 | fp.msedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
255.100.168.192.in-addr.arpa |
| unknown |
250.255.255.239.in-addr.arpa |
| unknown |
2.0.0.0.1.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.2.0.f.f.ip6.arpa |
| unknown |
2.100.168.192.in-addr.arpa |
| whitelisted |
7.7.f.d.4.d.7.e.6.d.5.9.5.2.c.a.0.0.0.0.0.0.0.0.0.0.0.0.0.8.e.f.ip6.arpa |
| unknown |
b.f.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.2.0.f.f.ip6.arpa |
| unknown |
e.6.5.f.2.8.0.9.5.8.8.f.a.c.f.3.0.0.0.0.0.0.0.0.0.0.0.0.0.8.e.f.ip6.arpa |
| unknown |
3.0.0.0.1.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.2.0.f.f.ip6.arpa |
| unknown |