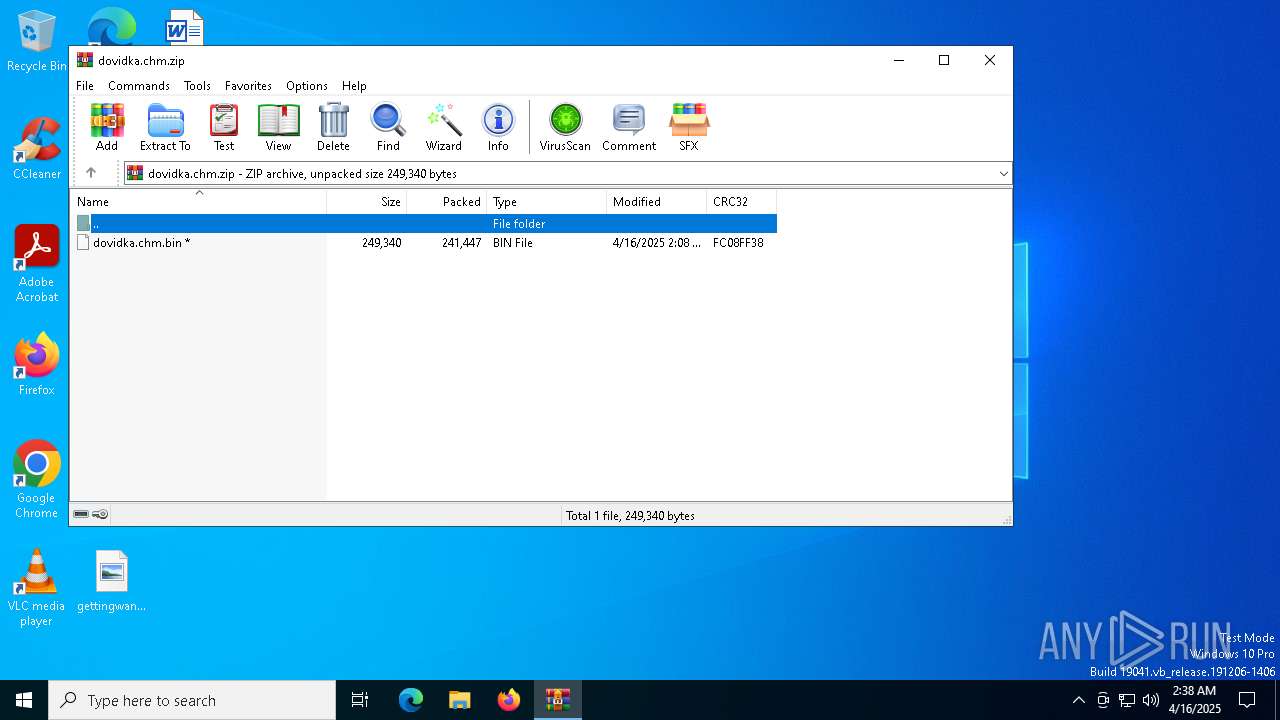
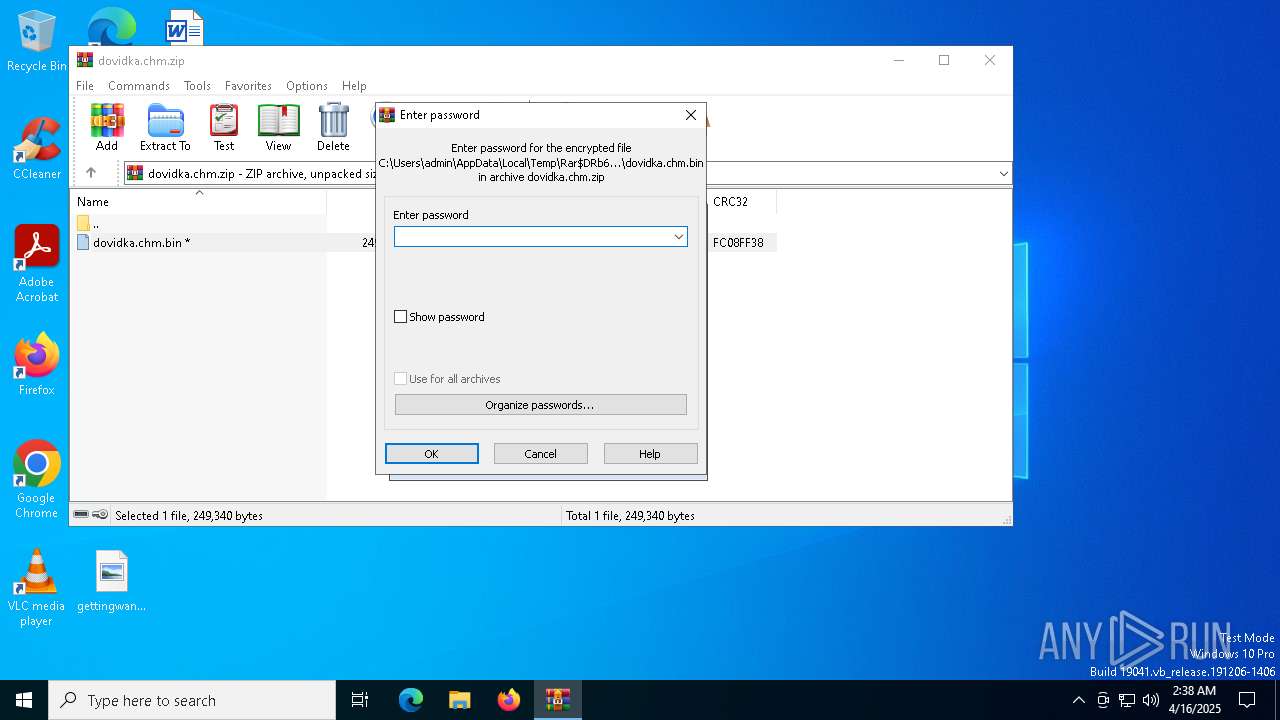
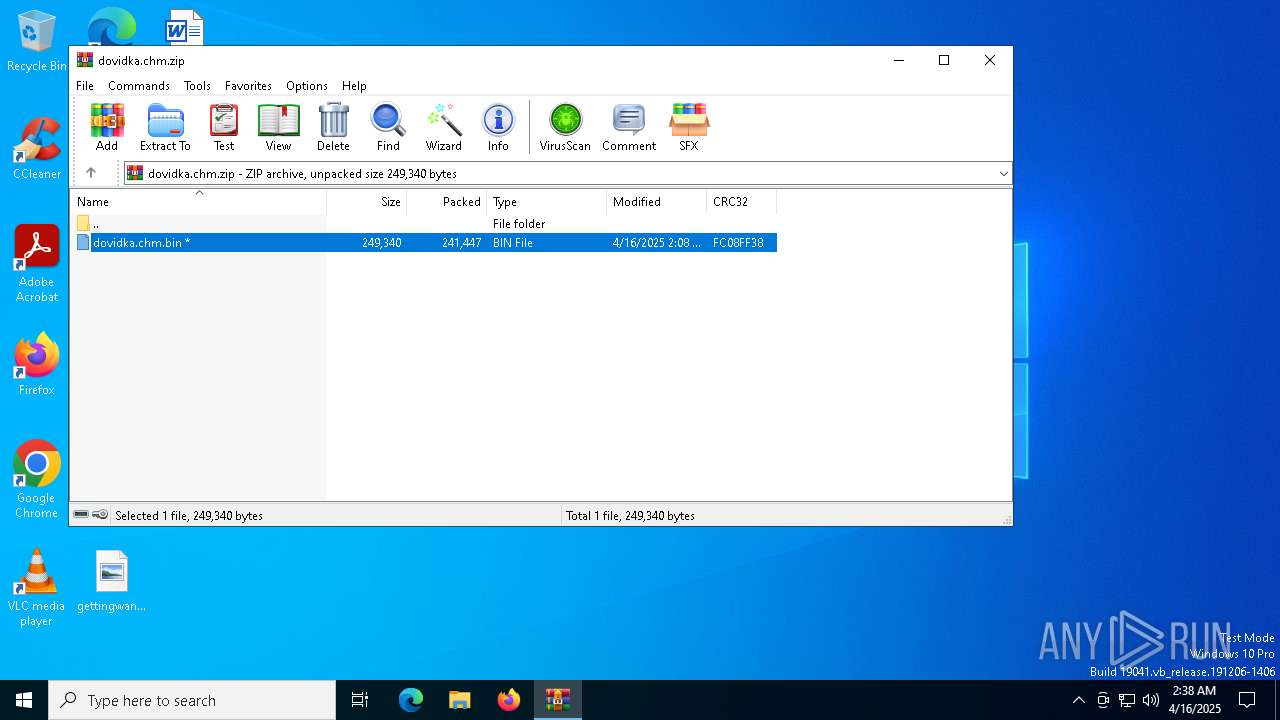
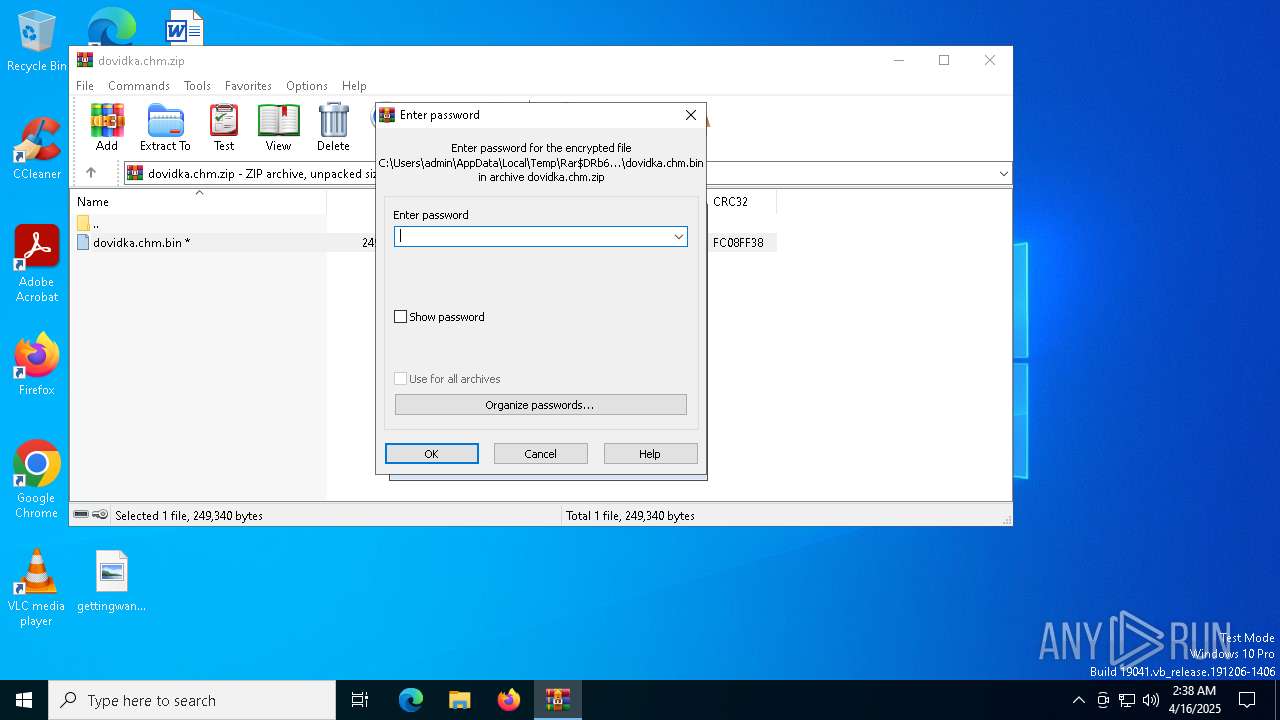
| File name: | dovidka.chm.zip |
| Full analysis: | https://app.any.run/tasks/2457d449-d20f-4a8e-98f7-3af9417db9d4 |
| Verdict: | Malicious activity |
| Analysis date: | April 16, 2025, 02:38:31 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | B412BCD1E624F37C5D69EAA08A755CBF |
| SHA1: | 1C3478FD2854D45D14360B992C31B7E19E533D7F |
| SHA256: | A1950BAD44958519EED30F0507E5A6744A698923BF48251D45526585938876BD |
| SSDEEP: | 6144:9yY7XBEL0z2dRH/KDMEVVJHgJLJUp/ajFmfa7nqGx:9ygRELxdRSDMEV/g5eIma75 |
MALICIOUS
Creates a new folder (SCRIPT)
- hh.exe (PID: 2268)
Create files in the Startup directory
- wscript.exe (PID: 2984)
Deletes a file (SCRIPT)
- hh.exe (PID: 2268)
SUSPICIOUS
Reads Internet Explorer settings
- hh.exe (PID: 2268)
Reads Microsoft Outlook installation path
- hh.exe (PID: 2268)
Creates FileSystem object to access computer's file system (SCRIPT)
- hh.exe (PID: 2268)
- wscript.exe (PID: 2984)
- wscript.exe (PID: 5228)
Writes binary data to a Stream object (SCRIPT)
- hh.exe (PID: 2268)
- wscript.exe (PID: 2984)
The process executes VB scripts
- hh.exe (PID: 2268)
Likely accesses (executes) a file from the Public directory
- wscript.exe (PID: 2984)
- wscript.exe (PID: 5228)
- RegAsm.exe (PID: 3020)
Write to the desktop.ini file (may be used to cloak folders)
- wscript.exe (PID: 2984)
Executable content was dropped or overwritten
- wscript.exe (PID: 2984)
Runs shell command (SCRIPT)
- wscript.exe (PID: 2984)
- hh.exe (PID: 2268)
- wscript.exe (PID: 5228)
Reads security settings of Internet Explorer
- RegAsm.exe (PID: 3020)
Connects to unusual port
- RegAsm.exe (PID: 3020)
INFO
Manual execution by a user
- hh.exe (PID: 2268)
The sample compiled with english language support
- WinRAR.exe (PID: 6324)
Checks proxy server information
- hh.exe (PID: 2268)
- RegAsm.exe (PID: 3020)
Create files in a temporary directory
- hh.exe (PID: 2268)
Reads security settings of Internet Explorer
- hh.exe (PID: 2268)
Reads Microsoft Office registry keys
- hh.exe (PID: 2268)
Creates files or folders in the user directory
- hh.exe (PID: 2268)
Checks supported languages
- RegAsm.exe (PID: 3020)
Reads the computer name
- RegAsm.exe (PID: 3020)
Reads the machine GUID from the registry
- RegAsm.exe (PID: 3020)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2025:04:16 02:08:00 |
| ZipCRC: | 0xfc08ff38 |
| ZipCompressedSize: | 241447 |
| ZipUncompressedSize: | 249340 |
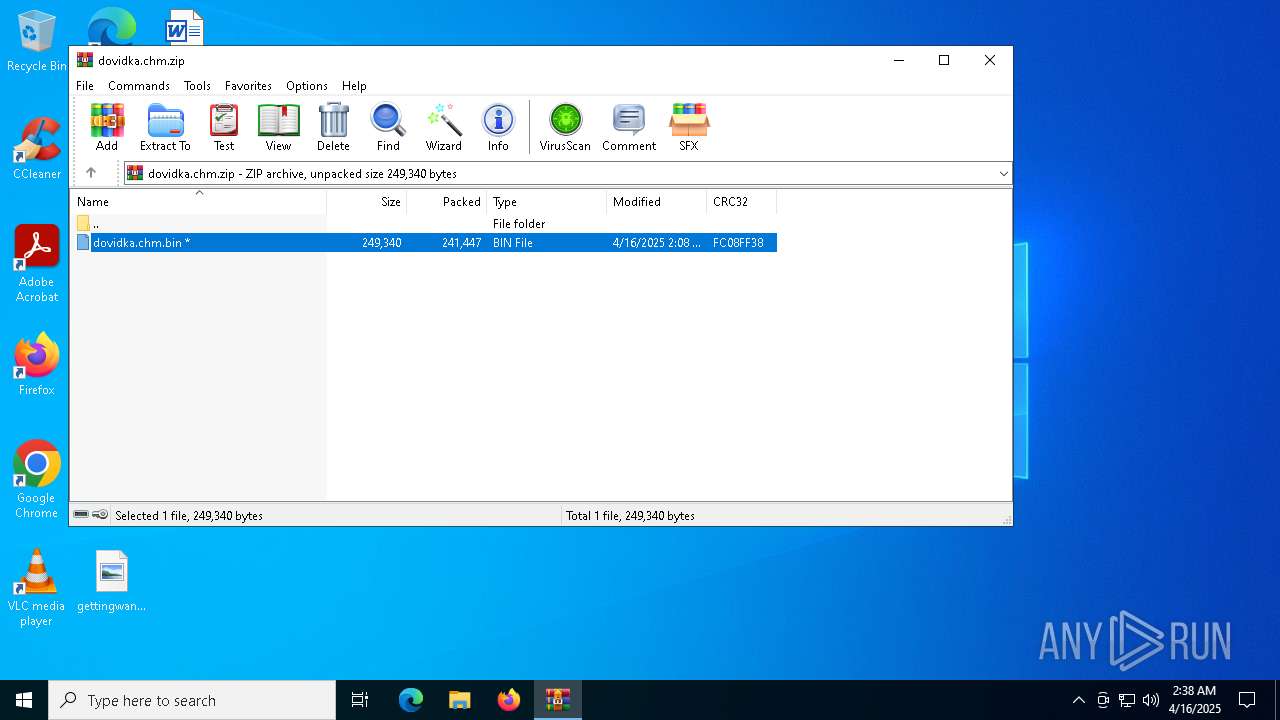
| ZipFileName: | dovidka.chm.bin |
Total processes
136
Monitored processes
8
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2268 | "C:\WINDOWS\hh.exe" C:\Users\admin\Desktop\dovidka.chm | C:\Windows\hh.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® HTML Help Executable Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2960 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | RegAsm.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2984 | "C:\WINDOWS\System32\WScript.exe" "C:\Users\Public\ignit.vbs" | C:\Windows\System32\wscript.exe | hh.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 3020 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\regasm.exe" /U C:\Users\Public\Libraries\core.dll | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe | wscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Assembly Registration Utility Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 4996 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5228 | "C:\Windows\System32\wscript.exe" //B //E:vbs C:\Users\Public\Favorites\desktop.ini | C:\Windows\System32\wscript.exe | — | hh.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 5576 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6324 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\dovidka.chm.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
4 362
Read events
4 338
Write events
24
Delete events
0
Modification events
| (PID) Process: | (6324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\dovidka.chm.zip | |||
| (PID) Process: | (6324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (6324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General\Toolbar\Layout |
| Operation: | write | Name: | Band76_2 |
Value: 4C000000730100000400000000000000F0F0F0000000000000000000000000000000000000000000440304000000000000000000180000006400000000000000000000000000000003000000 | |||
Executable files
1
Suspicious files
2
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6324 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6324.44118\dovidka.chm.bin | binary | |
MD5:2556A9E1D5E9874171F51620E5C5E09A | SHA256:7F0511B09B1AB3A64C8827DD8AF017ACBF7D2688DB31A5D98FEA8A5029A89D56 | |||
| 2984 | wscript.exe | C:\Users\Public\Libraries\core.dll | executable | |
MD5:D2A795AF12E937EB8A89D470A96F15A5 | SHA256:E97F1D6EC1AA3F7C7973D57074D1D623833F0E9B1C1E53F81AF92C057A1FDD72 | |||
| 2984 | wscript.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Windows Prefetch.lNk | binary | |
MD5:FB418BB5BD3E592651D0A4F9AE668962 | SHA256:C76FB28B6910BB0714FAB5B84363EBF2082FD59DDB0BB95166635583554D7AB4 | |||
| 2984 | wscript.exe | C:\Users\Public\Favorites\desktop.ini | text | |
MD5:A9DCAF1C709F96BC125C8D1262BAC4B6 | SHA256:570EBD7F9951485B7415F685AE3349E62580309C9955B14DDA4734A318EDECA9 | |||
| 2268 | hh.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\image[1].jpg | image | |
MD5:9CF2EE018A565C00E811897E6056A5A2 | SHA256:CFD05F02C88A5E0385580E4DCE40F346713C6949DB34AC99E1AE15BB5B1591DD | |||
| 2268 | hh.exe | C:\Users\Public\ignit.vbs | text | |
MD5:BD65D0D59F6127B28F0AF8A7F2619588 | SHA256:92F69DE0D45AD88654A6EEF720A6F6B6DB090AFB67BA0EBA5F9B77F504EA6280 | |||
| 3020 | RegAsm.exe | C:\Users\admin\AppData\Local\Temp\Tmp45D0.tmp | text | |
MD5:990E17CD51D14BBEACEE89F21B28705D | SHA256:DE22544C2A009F4ED7FAA2645CB6A4B889B81B1852F3FECDFEBB2D63A2078D72 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
20
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.42:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5936 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5936 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.216.77.42:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6544 | svchost.exe | 20.190.160.66:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2112 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
xbeta.online |
| unknown |