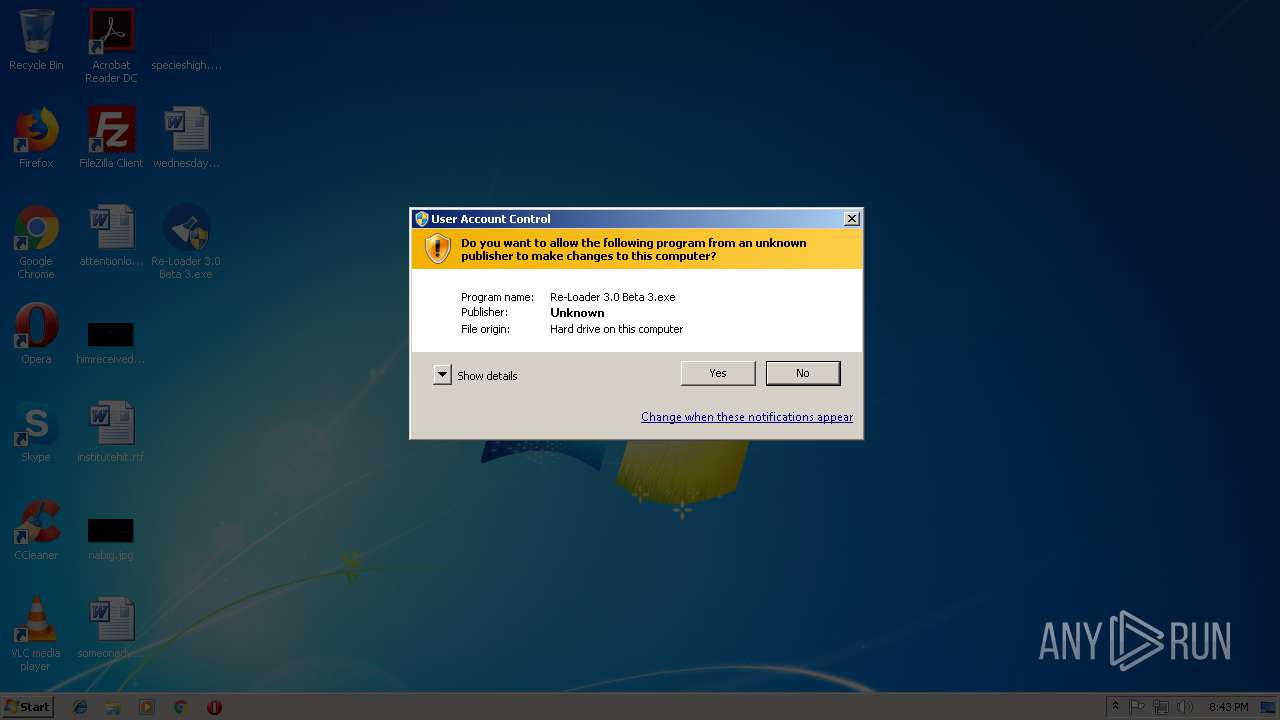
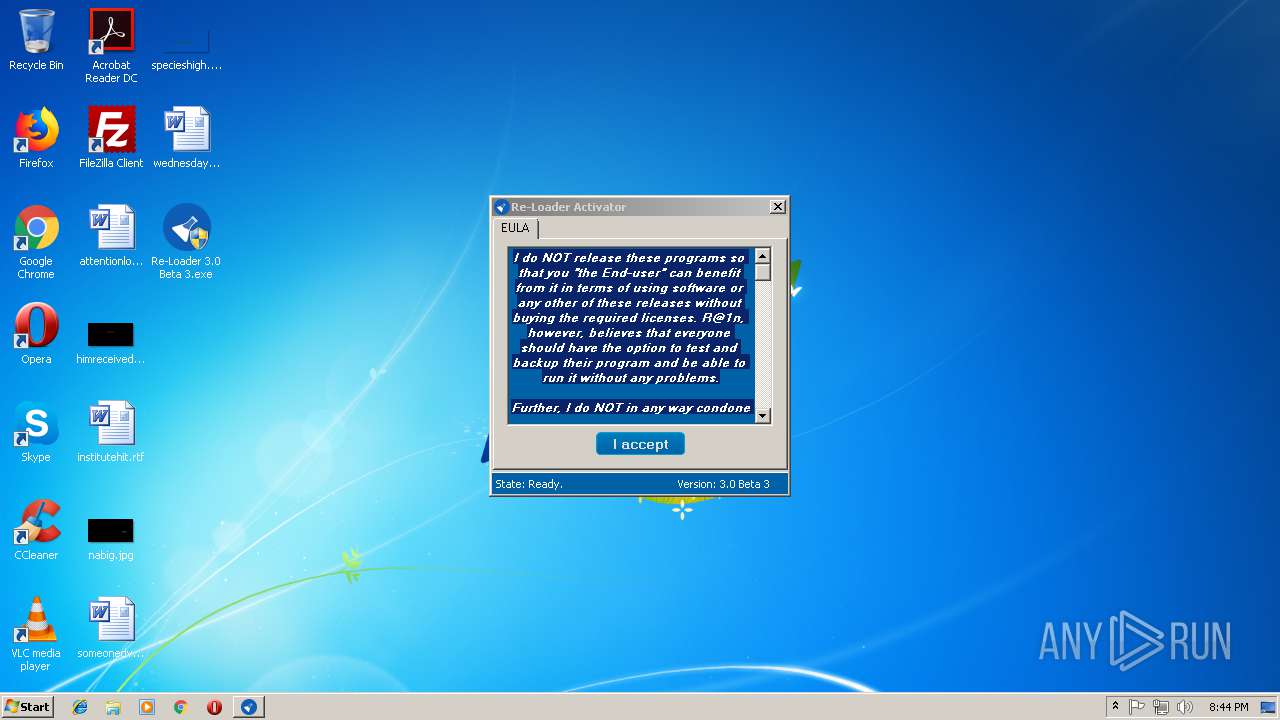
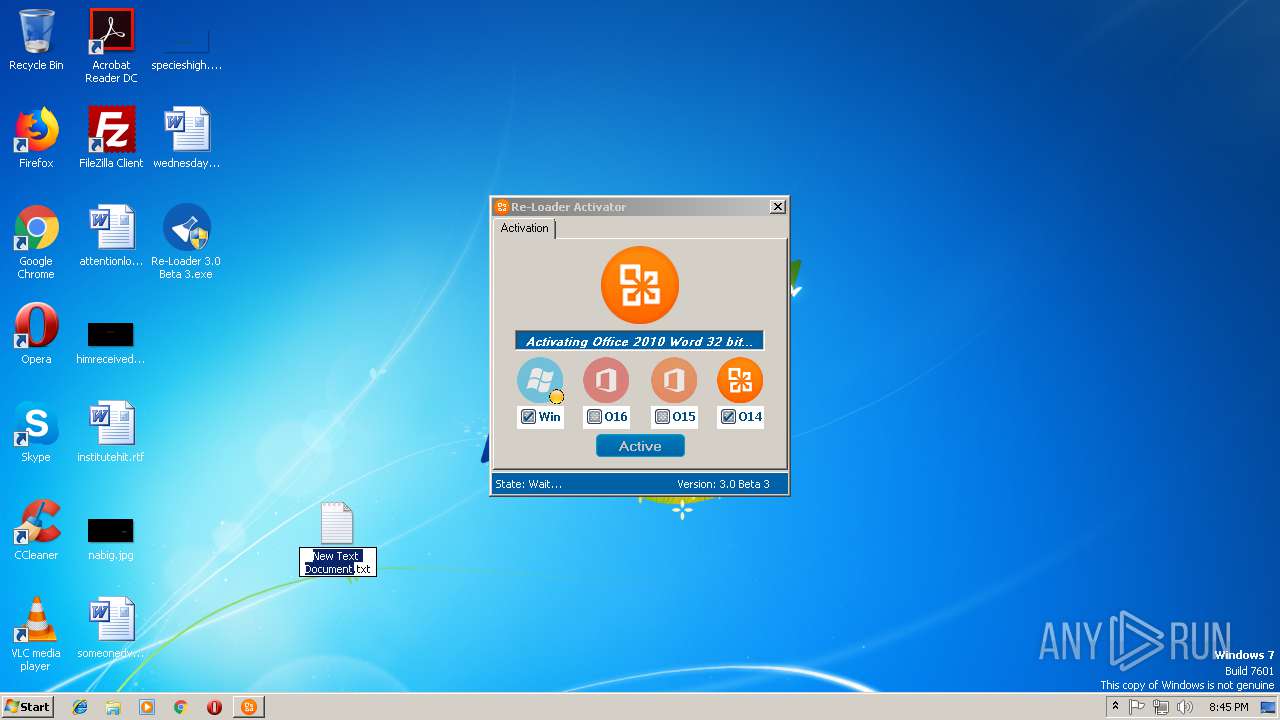
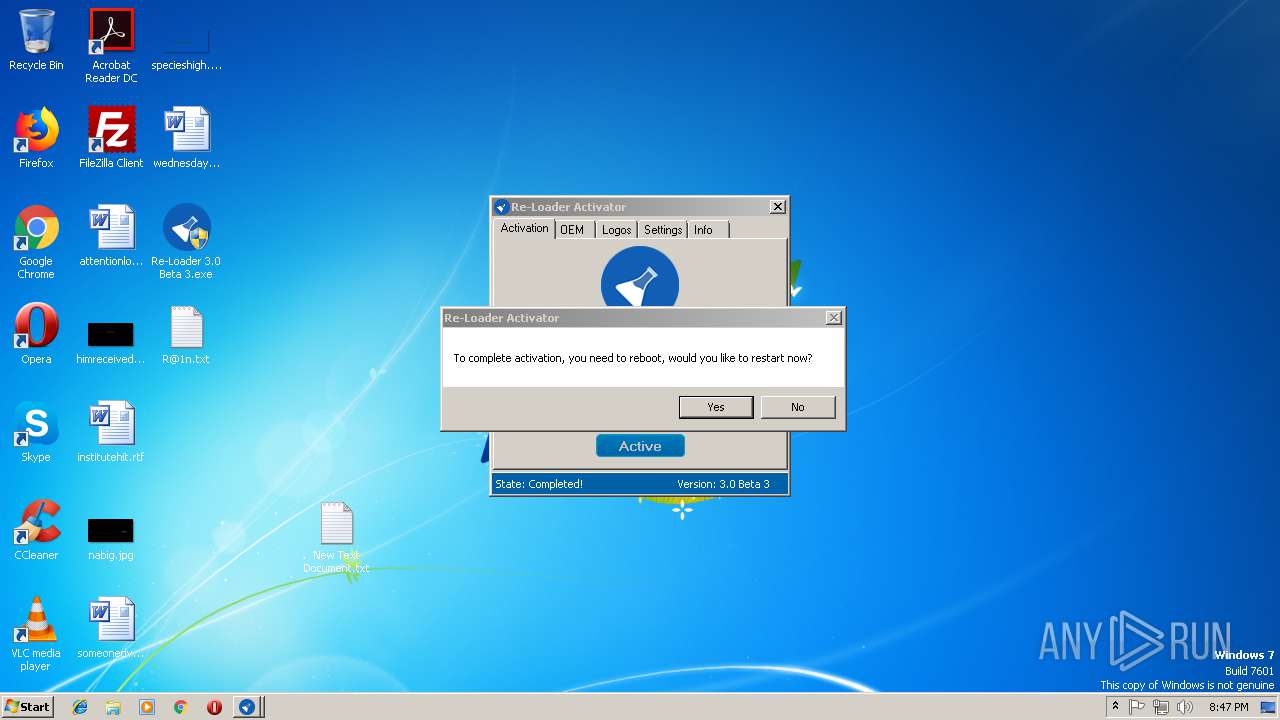
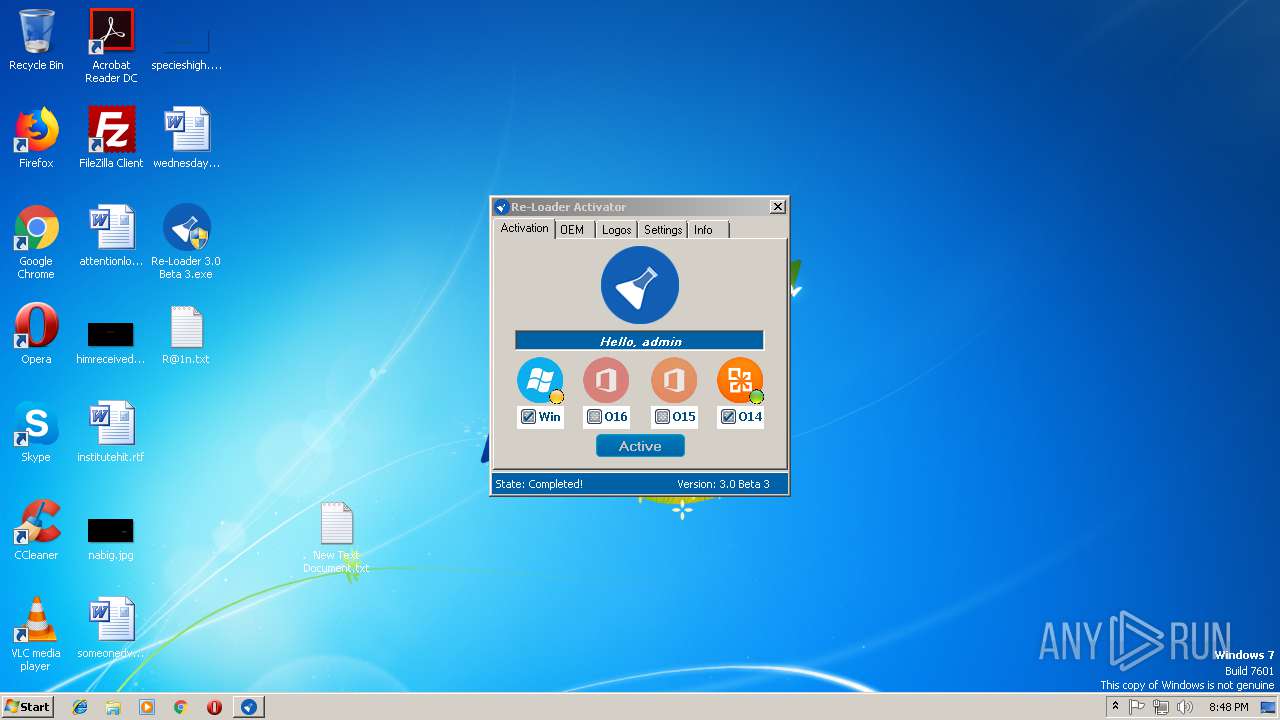
| File name: | Re-Loader 3.0 Beta 3.exe |
| Full analysis: | https://app.any.run/tasks/2e358488-57e5-4e9a-aaf5-b3212b7e74dc |
| Verdict: | Malicious activity |
| Analysis date: | October 06, 2018, 19:43:21 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | MS-DOS executable, MZ for MS-DOS |
| MD5: | F7B368A33EA9CA184679E132806B414F |
| SHA1: | 08D3F435B52559CB0E0D10C862E1F1E13E92936D |
| SHA256: | A18DB5954DFB60064EA28F49810FE20B40CDF81B484B05B0DB167C33AD134FED |
| SSDEEP: | 49152:ATE9cVpsKl0bT+r8wCtU3VvryekimJ2nvu8:AgGVzURoVy9i1n3 |
MALICIOUS
Application was dropped or rewritten from another process
- bootsect.exe (PID: 3360)
- brset.exe (PID: 1304)
- KMS-R@1nHook.exe (PID: 2112)
- KMS-R@1n.exe (PID: 1488)
- KMS-R@1nHook.exe (PID: 1180)
Adds new firewall rule via NETSH.EXE
- Re-Loader 3.0 Beta 3.exe (PID: 3868)
Loads dropped or rewritten executable
- OSPPSVC.EXE (PID: 2132)
- sppsvc.exe (PID: 2452)
Changes Image File Execution Options
- Re-Loader 3.0 Beta 3.exe (PID: 3868)
Loads the Task Scheduler COM API
- OSPPSVC.EXE (PID: 2132)
- sppsvc.exe (PID: 2452)
- schtasks.exe (PID: 3468)
- schtasks.exe (PID: 3708)
Uses Task Scheduler to run other applications
- Re-Loader 3.0 Beta 3.exe (PID: 3868)
SUSPICIOUS
Creates or modifies windows services
- DllHost.exe (PID: 1352)
Executable content was dropped or overwritten
- Re-Loader 3.0 Beta 3.exe (PID: 3868)
Low-level read access rights to disk partition
- brset.exe (PID: 1304)
- bootsect.exe (PID: 3360)
Searches for installed software
- DllHost.exe (PID: 1352)
Starts SC.EXE for service management
- Re-Loader 3.0 Beta 3.exe (PID: 3868)
Uses NETSH.EXE for network configuration
- Re-Loader 3.0 Beta 3.exe (PID: 3868)
Creates files in the Windows directory
- Re-Loader 3.0 Beta 3.exe (PID: 3868)
Uses TASKKILL.EXE to kill process
- Re-Loader 3.0 Beta 3.exe (PID: 3868)
Creates files in the program directory
- OSPPSVC.EXE (PID: 2132)
INFO
Reads Microsoft Office registry keys
- Re-Loader 3.0 Beta 3.exe (PID: 3868)
Low-level read access rights to disk partition
- vssvc.exe (PID: 2124)
Dropped object may contain Bitcoin addresses
- sppsvc.exe (PID: 2452)
Application launched itself
- chrome.exe (PID: 3632)
Creates or modifies windows services
- vssvc.exe (PID: 2124)
Dropped object may contain TOR URL's
- chrome.exe (PID: 3632)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2010:12:09 19:58:13+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 8 |
| CodeSize: | 4096 |
| InitializedDataSize: | 2048 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x2e5e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.0.1.3 |
| ProductVersionNumber: | 3.0.1.3 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | Activator |
| FileVersion: | 3.0.1.3 |
| InternalName: | Activator.exe |
| LegalCopyright: | Copyright © By R@1n 2015 |
| LegalTrademarks: | - |
| OriginalFileName: | Activator.exe |
| ProductName: | Re-Loader By R@1n |
| ProductVersion: | 3.0.1.3 |
| AssemblyVersion: | 3.0.1.3 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 09-Dec-2010 18:58:13 |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | Activator |
| FileVersion: | 3.0.1.3 |
| InternalName: | Activator.exe |
| LegalCopyright: | Copyright © By R@1n 2015 |
| LegalTrademarks: | - |
| OriginalFilename: | Activator.exe |
| ProductName: | Re-Loader By R@1n |
| ProductVersion: | 3.0.1.3 |
| Assembly Version: | 3.0.1.3 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0040 |
| Pages in file: | 0x0001 |
| Relocations: | 0x0000 |
| Size of header: | 0x0002 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0xB400 |
| OEM information: | 0xCD09 |
| Address of NE header: | 0x00000040 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 3 |
| Time date stamp: | 09-Dec-2010 18:58:13 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00002000 | 0x00000E64 | 0x00001000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 5.26751 |
.rsrc | 0x00004000 | 0x00008FA8 | 0x00009000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.4353 |
.reloc | 0x0000E000 | 0x0000000C | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 6.34573 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.00727 | 3463 | UNKNOWN | UNKNOWN | RT_MANIFEST |
2 | 3.8639 | 4264 | UNKNOWN | UNKNOWN | RT_ICON |
3 | 4.0782 | 9640 | UNKNOWN | UNKNOWN | RT_ICON |
4 | 3.60895 | 16936 | UNKNOWN | UNKNOWN | RT_ICON |
32512 | 2.62308 | 62 | UNKNOWN | UNKNOWN | RT_GROUP_ICON |
Imports
mscoree.dll |
Total processes
114
Monitored processes
48
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | "C:\Windows\System32\netsh.exe" advfirewall firewall delete rule name="KMS-R@1n" | C:\Windows\System32\netsh.exe | — | Re-Loader 3.0 Beta 3.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 312 | DrvInst.exe "1" "200" "STORAGE\VolumeSnapshot\HarddiskVolumeSnapshot18" "" "" "6792c44eb" "00000000" "000005C4" "000003BC" | C:\Windows\system32\DrvInst.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 384 | C:\Windows\System32\Wbem\wmic.EXE path OfficeSoftwareProtectionProduct where (ID="2d0882e7-a4e7-423b-8ccc-70d91e0158b1") call Activate | C:\Windows\System32\Wbem\wmic.EXE | — | taskeng.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 476 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=896,4621253942184902158,8194191451928864652,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=E1815E9D2106E15E3C7645C4115A7922 --mojo-platform-channel-handle=2108 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 476 | "C:\Windows\System32\sc.exe" description "KMS-R@1n" "v3.0 Beta 3" | C:\Windows\System32\sc.exe | — | Re-Loader 3.0 Beta 3.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 684 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=896,4621253942184902158,8194191451928864652,131072 --enable-features=PasswordImport --disable-gpu-sandbox --gpu-preferences=KAAAAAAAAACAAwBAAQAAAAAAAAAAAGAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --service-request-channel-token=F89DDE95DA8C349C95566BFB024CBD53 --mojo-platform-channel-handle=3740 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 736 | C:\Windows\System32\Wbem\wmic.EXE path OfficeSoftwareProtectionProduct where (ID="ab586f5c-5256-4632-962f-fefd8b49e6f4") call Activate | C:\Windows\System32\Wbem\wmic.EXE | — | taskeng.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 912 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=896,4621253942184902158,8194191451928864652,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=C6B41BEA8EFDA804F017F2CDAD36AB13 --mojo-platform-channel-handle=3692 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 1180 | KMS-R@1nHook.exe C:\Windows\system32\sppsvc.exe | C:\Windows\KMS-R@1nHook.exe | — | services.exe | |||||||||||
User: NETWORK SERVICE Integrity Level: SYSTEM Exit code: 0 Modules
| |||||||||||||||
| 1216 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=896,4621253942184902158,8194191451928864652,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=7AB2506CFB10C51B2F24EF8C2A1A1DC0 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=7AB2506CFB10C51B2F24EF8C2A1A1DC0 --renderer-client-id=10 --mojo-platform-channel-handle=4220 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
Total events
1 815
Read events
886
Write events
879
Delete events
50
Modification events
| (PID) Process: | (3868) Re-Loader 3.0 Beta 3.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3868) Re-Loader 3.0 Beta 3.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (1352) DllHost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 40000000000000004BB324F5AC5DD40148050000B0070000D0070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1352) DllHost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 20 | |||
| (PID) Process: | (1352) DllHost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 40000000000000003FC375F5AC5DD40148050000B0070000D3070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1352) DllHost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000992578F5AC5DD40148050000400D0000E8030000010000000000000000000000FBDD7D6C177C9349BCBACFC82D45422B0000000000000000 | |||
| (PID) Process: | (2124) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 400000000000000069388BF5AC5DD4014C08000088020000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2124) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000C39A8DF5AC5DD4014C08000054050000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2124) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000C39A8DF5AC5DD4014C080000E80B0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2124) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000C39A8DF5AC5DD4014C08000050080000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
4
Suspicious files
104
Text files
252
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1352 | DllHost.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 1352 | DllHost.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:— | SHA256:— | |||
| 1304 | brset.exe | \\?\Volume{e1a82db3-a9f0-11e7-b142-806e6f6e6963} | — | |
MD5:— | SHA256:— | |||
| 3868 | Re-Loader 3.0 Beta 3.exe | C:\Users\admin\AppData\Local\Temp\Re-Loader\OEM\SLIC\GH70H | — | |
MD5:— | SHA256:— | |||
| 3868 | Re-Loader 3.0 Beta 3.exe | C:\Users\admin\AppData\Local\Temp\Re-Loader\OEM\bootsect.exe | — | |
MD5:— | SHA256:— | |||
| 3360 | bootsect.exe | \\?\Volume{e1a82db3-a9f0-11e7-b142-806e6f6e6963} | — | |
MD5:— | SHA256:— | |||
| 2124 | vssvc.exe | C: | — | |
MD5:— | SHA256:— | |||
| 312 | DrvInst.exe | C:\Windows\INF\setupapi.dev.log | ini | |
MD5:— | SHA256:— | |||
| 312 | DrvInst.exe | C:\Windows\INF\setupapi.ev3 | binary | |
MD5:— | SHA256:— | |||
| 1352 | DllHost.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{6c7dddfb-7c17-4993-bcba-cfc82d45422b}_OnDiskSnapshotProp | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
38
DNS requests
17
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3632 | chrome.exe | 172.217.18.163:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
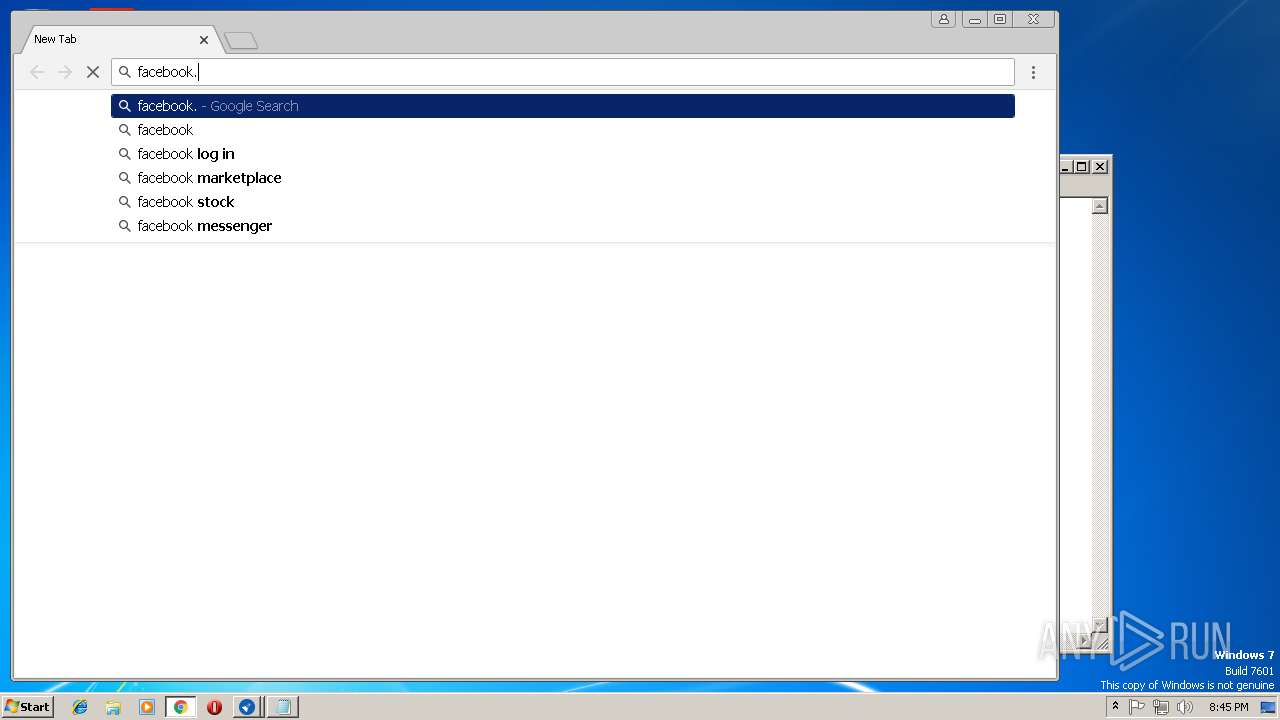
3632 | chrome.exe | 31.13.64.35:443 | www.facebook.com | Facebook, Inc. | IE | whitelisted |
3632 | chrome.exe | 172.217.21.227:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
3632 | chrome.exe | 172.217.21.237:443 | accounts.google.com | Google Inc. | US | whitelisted |
3632 | chrome.exe | 173.194.73.94:443 | www.google.de | Google Inc. | US | whitelisted |
3632 | chrome.exe | 31.13.90.6:443 | scontent-lhr3-1.xx.fbcdn.net | Facebook, Inc. | IE | whitelisted |
3632 | chrome.exe | 157.240.1.36:443 | pixel.facebook.com | Facebook, Inc. | US | whitelisted |
3632 | chrome.exe | 216.58.198.202:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
3632 | chrome.exe | 216.58.198.206:443 | clients1.google.com | Google Inc. | US | whitelisted |
3632 | chrome.exe | 179.60.192.36:443 | facebook.com | Facebook, Inc. | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.de |
| whitelisted |
www.google.com |
| malicious |
ssl.gstatic.com |
| whitelisted |
safebrowsing.googleapis.com |
| whitelisted |
www.facebook.com |
| whitelisted |
scontent-lhr3-1.xx.fbcdn.net |
| whitelisted |
static.xx.fbcdn.net |
| whitelisted |
facebook.com |
| whitelisted |