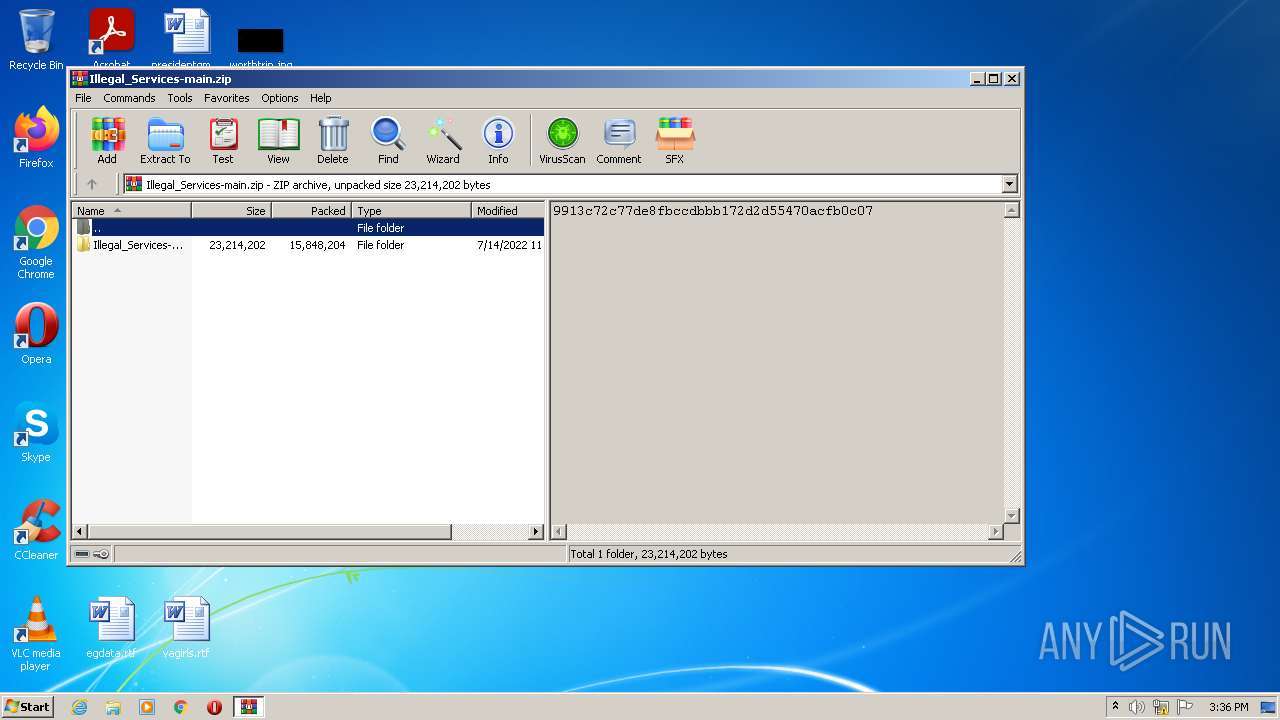
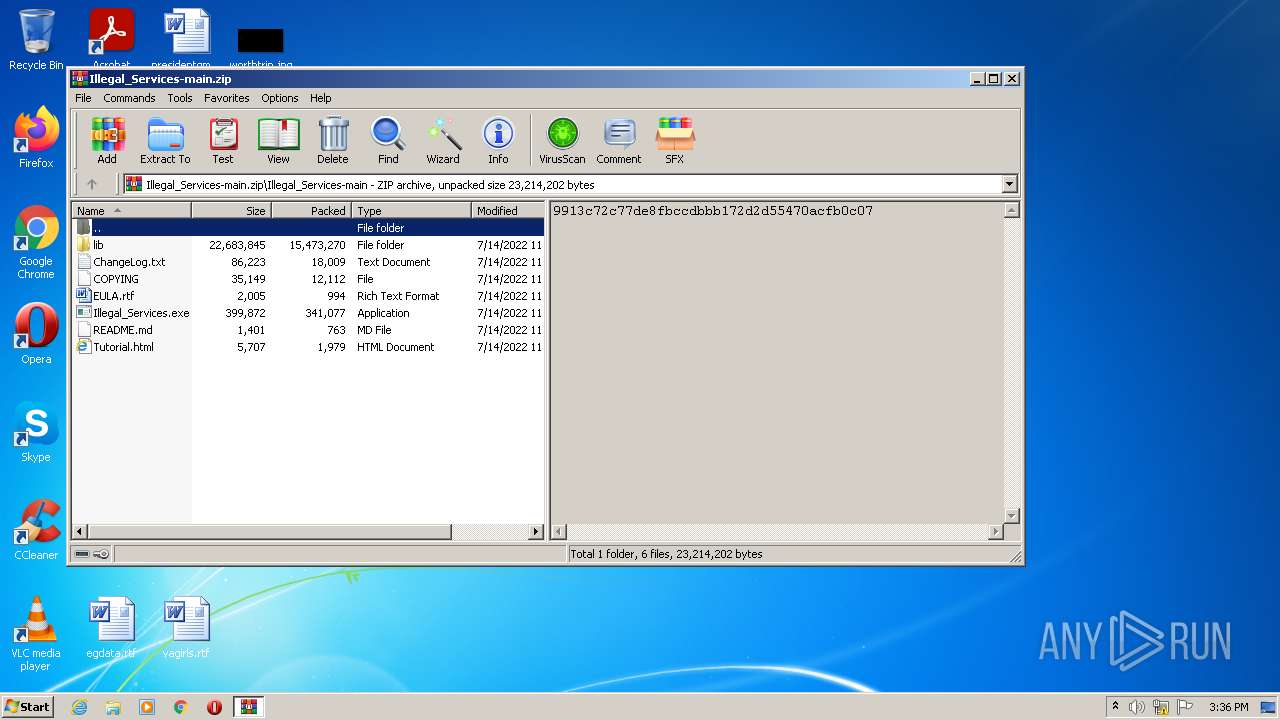
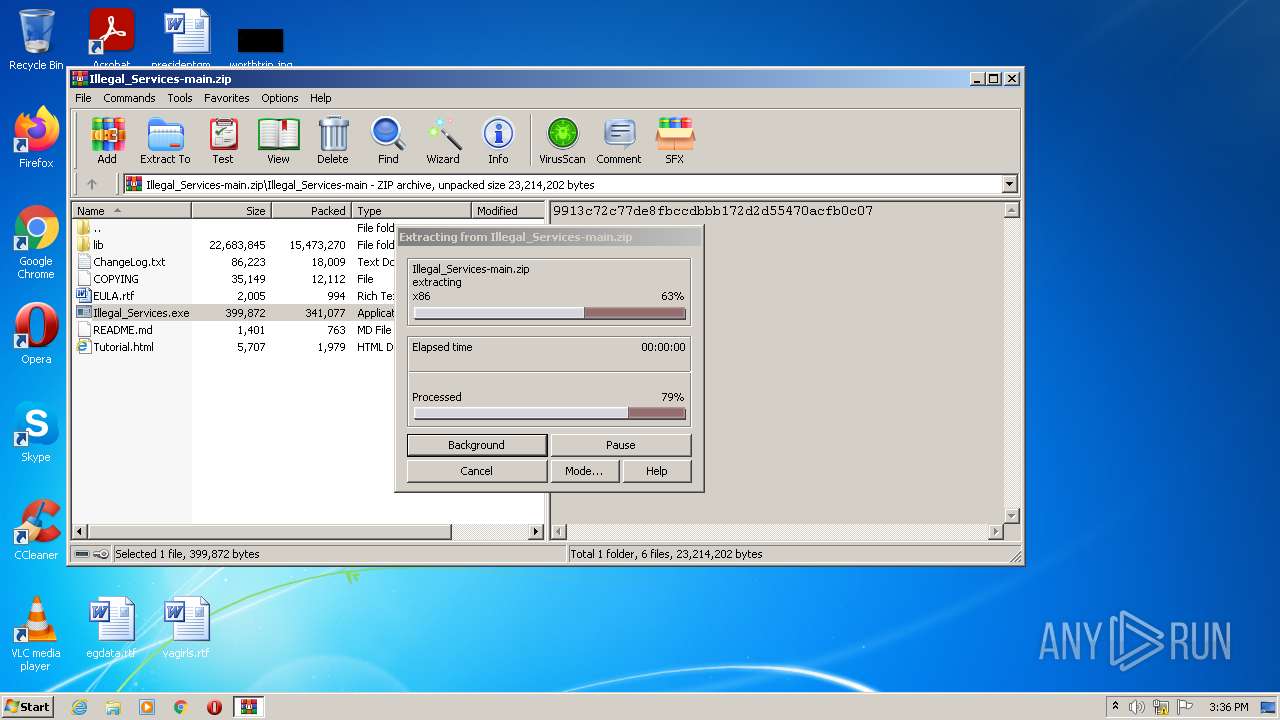
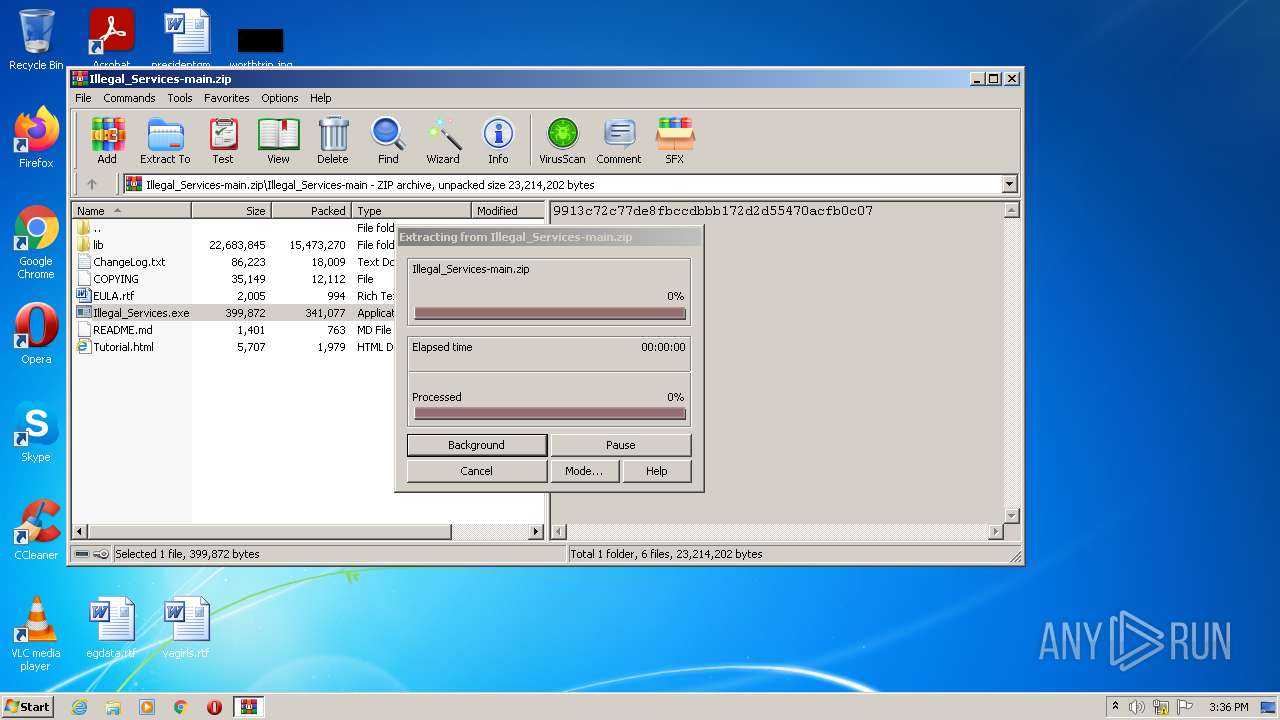
| File name: | Illegal_Services-main.zip |
| Full analysis: | https://app.any.run/tasks/0e16b94f-60f5-402b-a6dc-8118674a5e45 |
| Verdict: | Malicious activity |
| Analysis date: | August 12, 2022, 14:36:12 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | 06F7BF547914ED645C007627D82789A7 |
| SHA1: | 06D8260039B241A55E05520C341D35633FA2107E |
| SHA256: | A18B78BD9BAD355929B666C5A2224EC74718BF4B3A897AF173B358A9028D1B97 |
| SSDEEP: | 393216:tQaT7uZztcOKKMg+oSFkQRPtOHMmFqpA//3yUxMSLWO3qEv6eWxhl:L7W5cVKP+XFkQRPt8f/iUB6Ev6eWx/ |
MALICIOUS
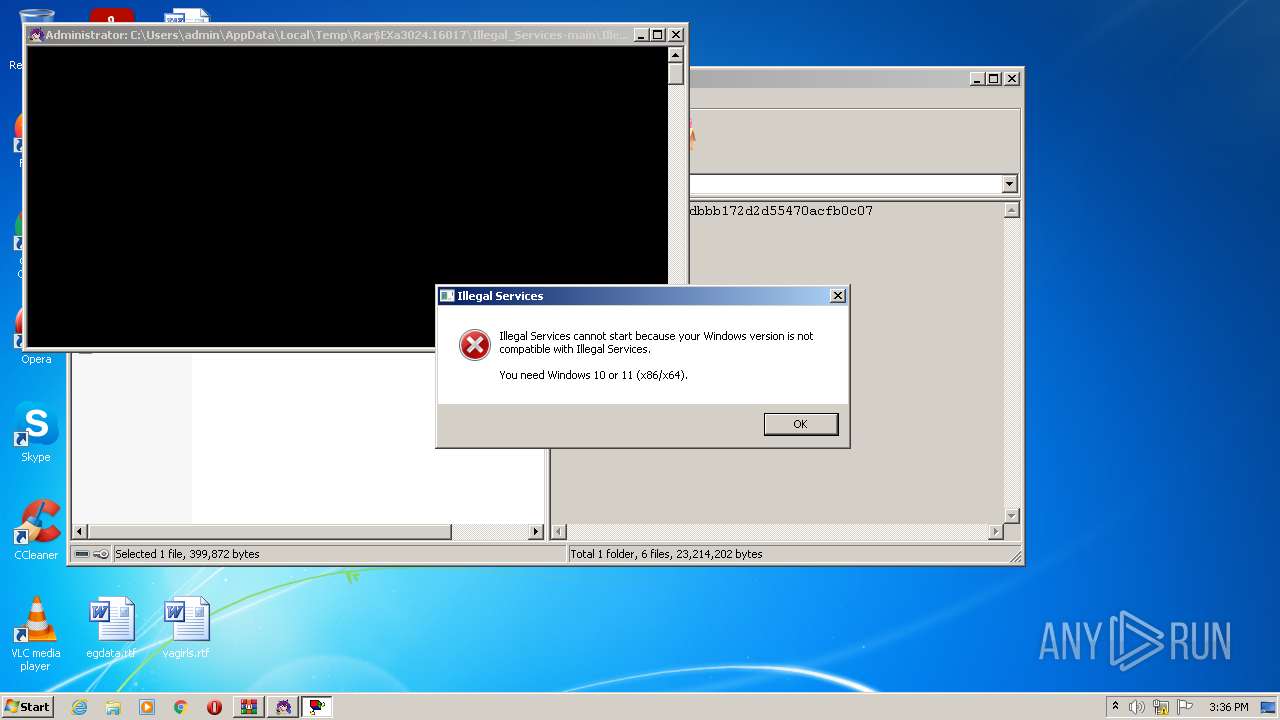
Application was dropped or rewritten from another process
- Illegal_Services.exe (PID: 3492)
- Illegal_Services.exe (PID: 2888)
- Illegal_Services.exe (PID: 964)
- Illegal_Services.exe (PID: 284)
Drops executable file immediately after starts
- WinRAR.exe (PID: 3024)
SUSPICIOUS
Reads the computer name
- WinRAR.exe (PID: 3024)
- powershell.exe (PID: 2776)
- WMIC.exe (PID: 3252)
- cscript.exe (PID: 4040)
- powershell.exe (PID: 2468)
- WMIC.exe (PID: 3940)
- cscript.exe (PID: 3328)
Checks supported languages
- WinRAR.exe (PID: 3024)
- cmd.exe (PID: 2408)
- cmd.exe (PID: 1976)
- cmd.exe (PID: 3828)
- cmd.exe (PID: 4024)
- chcp.com (PID: 2308)
- cmd.exe (PID: 2028)
- cmd.exe (PID: 1076)
- chcp.com (PID: 2660)
- cmd.exe (PID: 2236)
- powershell.exe (PID: 2776)
- chcp.com (PID: 1984)
- cmd.exe (PID: 2220)
- WMIC.exe (PID: 3252)
- cmd.exe (PID: 3084)
- cscript.exe (PID: 4040)
- Illegal_Services.exe (PID: 284)
- cmd.exe (PID: 3036)
- Illegal_Services.exe (PID: 2888)
- chcp.com (PID: 3972)
- cmd.exe (PID: 4020)
- cmd.exe (PID: 1788)
- chcp.com (PID: 1008)
- cmd.exe (PID: 344)
- powershell.exe (PID: 2468)
- WMIC.exe (PID: 3940)
- chcp.com (PID: 2792)
- cmd.exe (PID: 2892)
- cmd.exe (PID: 2968)
- cscript.exe (PID: 3328)
- cmd.exe (PID: 2184)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3024)
Application launched itself
- cmd.exe (PID: 1976)
- cmd.exe (PID: 3036)
Starts application with an unusual extension
- cmd.exe (PID: 1976)
- cmd.exe (PID: 3036)
Checks Windows language
- reg.exe (PID: 3208)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 3024)
INFO
Dropped object may contain TOR URL's
- Illegal_Services.exe (PID: 2888)
- Illegal_Services.exe (PID: 284)
Checks supported languages
- attrib.exe (PID: 3088)
- attrib.exe (PID: 2824)
- findstr.exe (PID: 3444)
- findstr.exe (PID: 3324)
- forfiles.exe (PID: 3660)
- cmd.exe (PID: 3808)
- reg.exe (PID: 312)
- reg.exe (PID: 1180)
- reg.exe (PID: 2548)
- reg.exe (PID: 3208)
- reg.exe (PID: 3984)
- reg.exe (PID: 2252)
- attrib.exe (PID: 2288)
- attrib.exe (PID: 1304)
- findstr.exe (PID: 3856)
- reg.exe (PID: 3208)
- findstr.exe (PID: 3720)
- forfiles.exe (PID: 3996)
- cmd.exe (PID: 2164)
- reg.exe (PID: 332)
Checks Windows Trust Settings
- powershell.exe (PID: 2776)
- cscript.exe (PID: 4040)
- cscript.exe (PID: 3328)
- powershell.exe (PID: 2468)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | Illegal_Services-main/ |
|---|---|
| ZipUncompressedSize: | - |
| ZipCompressedSize: | - |
| ZipCRC: | 0x00000000 |
| ZipModifyDate: | 2022:07:14 15:02:25 |
| ZipCompression: | None |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 10 |
Total processes
95
Monitored processes
53
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 284 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3024.16017\Illegal_Services-main\Illegal_Services.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3024.16017\Illegal_Services-main\Illegal_Services.exe | WinRAR.exe | ||||||||||||
User: admin Company: IB_U_Z_Z_A_R_Dl Integrity Level: HIGH Description: Illegal Services Exit code: 0 Version: 6. 1. 7. 5 Modules
| |||||||||||||||
| 312 | reg query "HKCU\SOFTWARE\IB_U_Z_Z_A_R_Dl\Illegal Services" /v "Language" | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 332 | reg query "HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders" /v "Personal" | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 344 | C:\Windows\system32\cmd.exe /c 2>nul reg query "HKCU\SOFTWARE\IB_U_Z_Z_A_R_Dl\Illegal Services" /v "Language" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
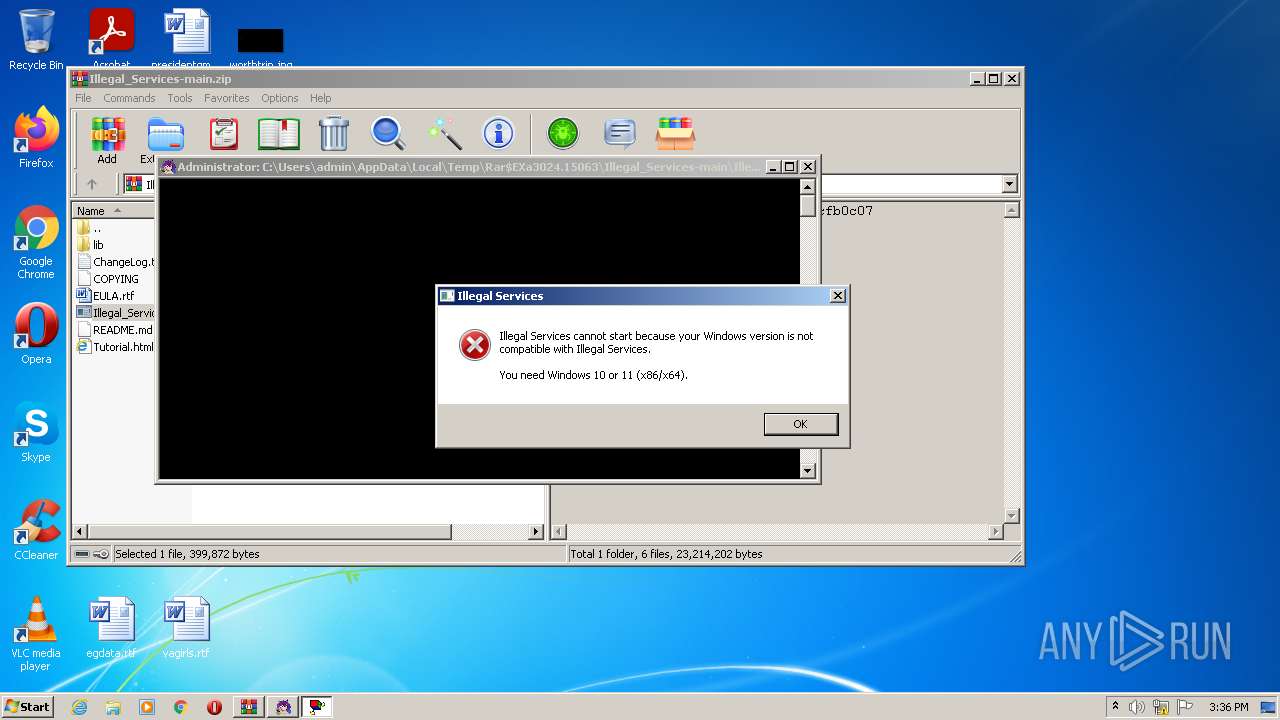
| 964 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3024.16017\Illegal_Services-main\Illegal_Services.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3024.16017\Illegal_Services-main\Illegal_Services.exe | — | WinRAR.exe | |||||||||||
User: admin Company: IB_U_Z_Z_A_R_Dl Integrity Level: MEDIUM Description: Illegal Services Exit code: 3221226540 Version: 6. 1. 7. 5 Modules
| |||||||||||||||
| 1008 | chcp 437 | C:\Windows\system32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Change CodePage Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1076 | C:\Windows\system32\cmd.exe /c 2>nul reg query "HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders" /v "Personal" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1180 | reg query "HKCU\SOFTWARE\IB_U_Z_Z_A_R_Dl\Illegal Services" /v "Language" | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1304 | attrib +s +h +i "C:\Users\admin\AppData\Local\Temp\C04IKG89.bat" | C:\Windows\system32\attrib.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Attribute Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1788 | C:\Windows\system32\cmd.exe /c set | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
2 058
Read events
2 036
Write events
22
Delete events
0
Modification events
| (PID) Process: | (3024) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3024) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3024) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3024) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3024) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3024) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Illegal_Services-main.zip | |||
| (PID) Process: | (3024) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3024) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3024) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3024) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
38
Suspicious files
0
Text files
44
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3024 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3024.15063\Illegal_Services-main\README.md | text | |
MD5:— | SHA256:— | |||
| 3024 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3024.15063\Illegal_Services-main\Illegal_Services.exe | executable | |
MD5:— | SHA256:— | |||
| 3024 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3024.15063\Illegal_Services-main\lib\7za\x86\7za.dll | executable | |
MD5:3107CAECF7EC7A7CE12D05F9C3AB078F | SHA256:BD377BA96FF8D3CBAEA98190C8A60F32DC9D64DD44EED9AADE05D3A74D935701 | |||
| 3024 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3024.15063\Illegal_Services-main\COPYING | text | |
MD5:1EBBD3E34237AF26DA5DC08A4E440464 | SHA256:3972DC9744F6499F0F9B2DBF76696F2AE7AD8AF9B23DDE66D6AF86C9DFB36986 | |||
| 3024 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3024.15063\Illegal_Services-main\lib\7za\x64\7za.dll | executable | |
MD5:5E79330DFA8F102DA34A4AE39B181DA1 | SHA256:F306D5766040C252E312893B232CD985B5BF8C7BB1856DB78CCE9FB2D4A4FF58 | |||
| 3024 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3024.15063\Illegal_Services-main\ChangeLog.txt | text | |
MD5:— | SHA256:— | |||
| 3024 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3024.15063\Illegal_Services-main\lib\7za\x64\7za.exe | executable | |
MD5:E86EFF95691B1C0E7E4F3E9CB1AE2E49 | SHA256:8117E40EE7F824F63373A4F5625BB62749F69159D0C449B3CE2F35AAD3B83549 | |||
| 3024 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3024.15063\Illegal_Services-main\lib\backgrounds\background-2.jpg | image | |
MD5:2192256D4F99534C591DB8BFA147D7CC | SHA256:D8BCF289EEAF135076D1CE5CFAEA19D2A845405959A50364A84312D3C6744295 | |||
| 3024 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3024.15063\Illegal_Services-main\lib\SaveFileBox.exe | executable | |
MD5:8108FF69B5760C8117563D6B10F77158 | SHA256:48EB5C03141732B810570B557FE148E3F76764DF3A632008972DE44BE88497E3 | |||
| 3024 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3024.15063\Illegal_Services-main\EULA.rtf | text | |
MD5:D637221F9CF08906BFBFBDFB5077AD8C | SHA256:196FA5F8A3072D18CA9497BCBCA24F89F2B7C63C1B3D6E9B39C0F529443ED273 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report