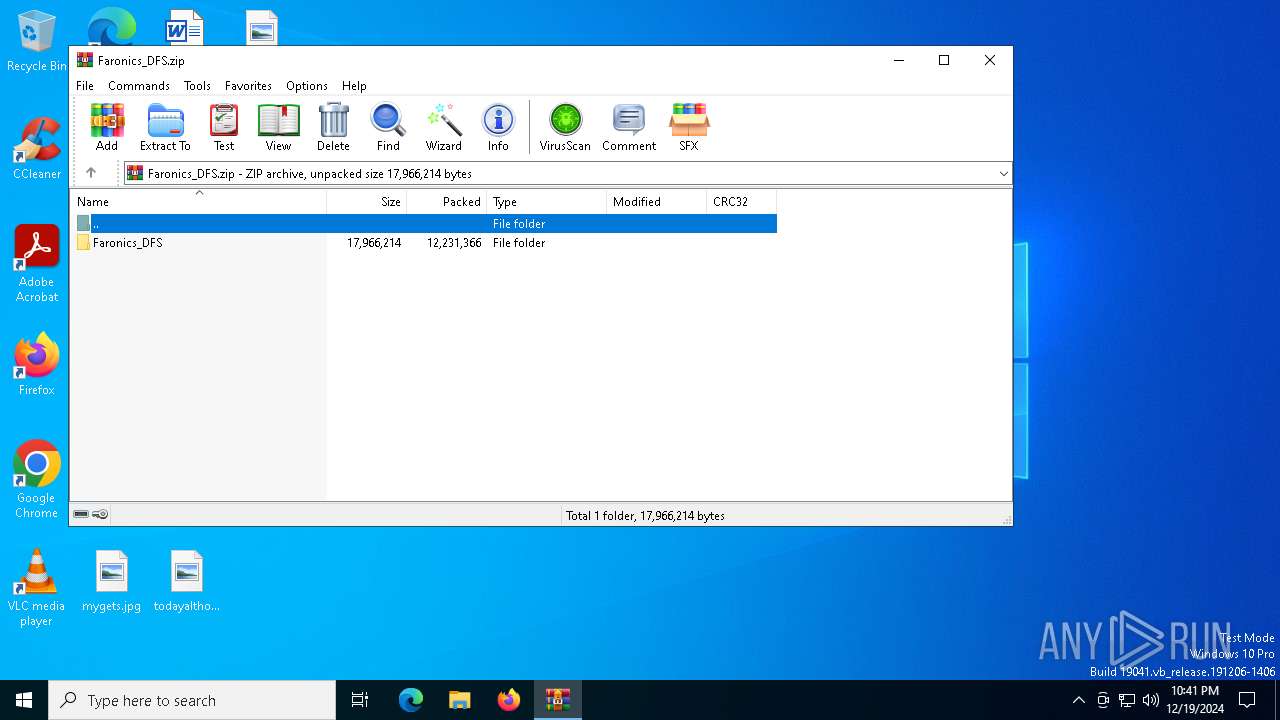
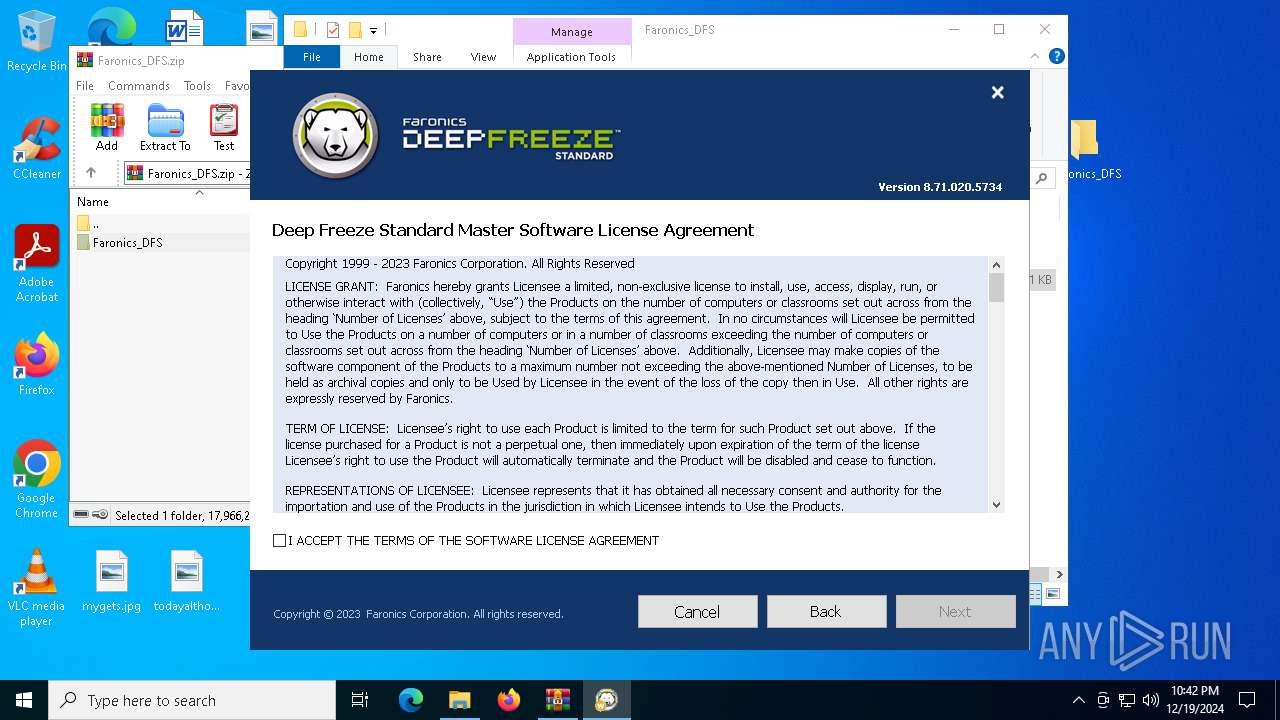
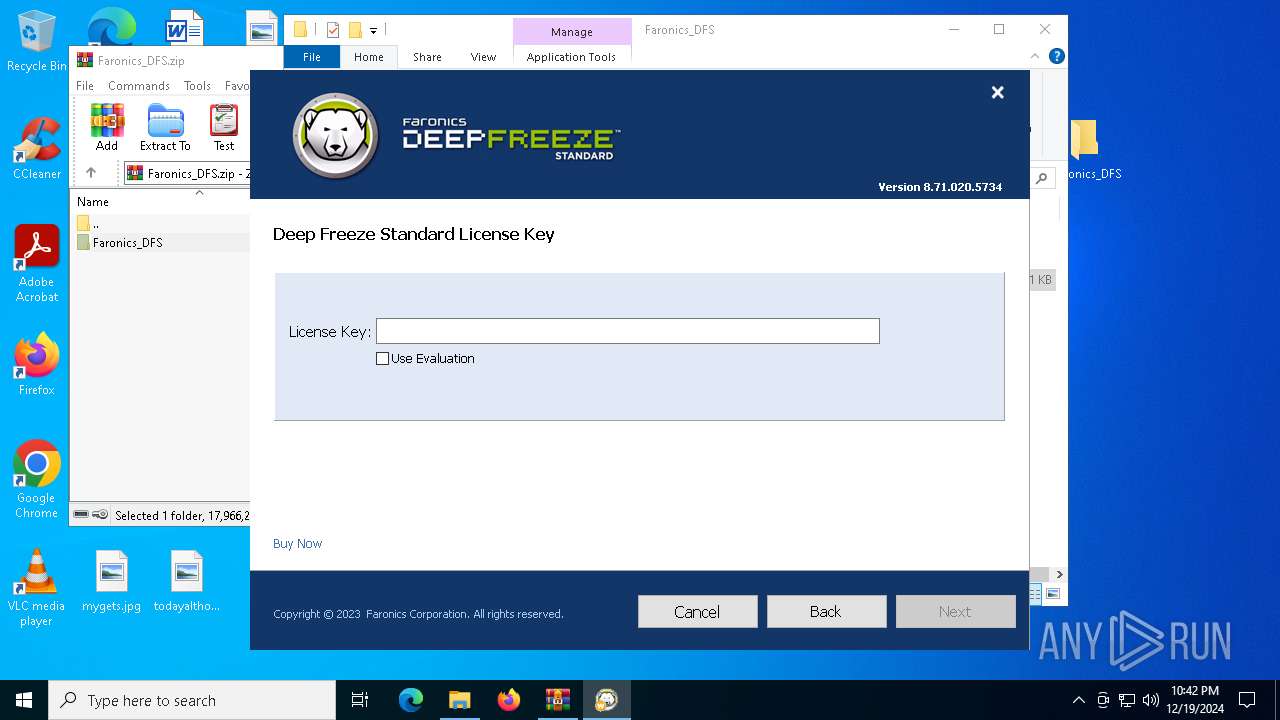
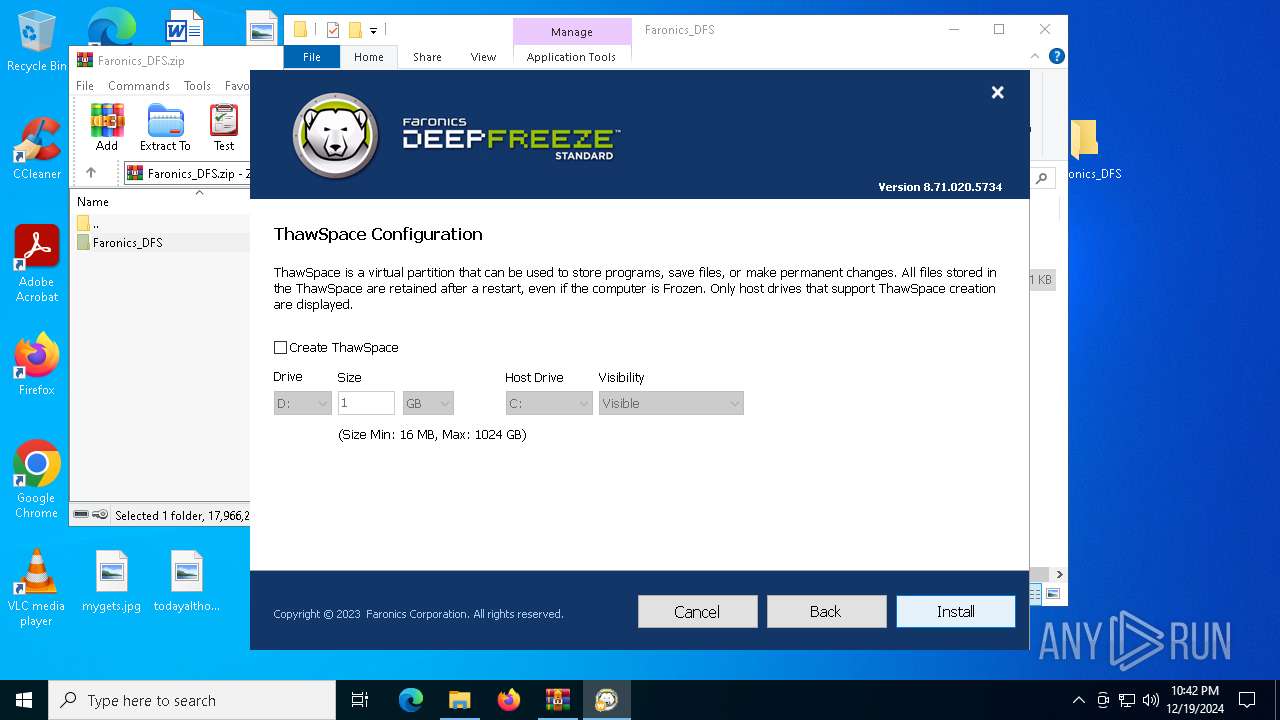
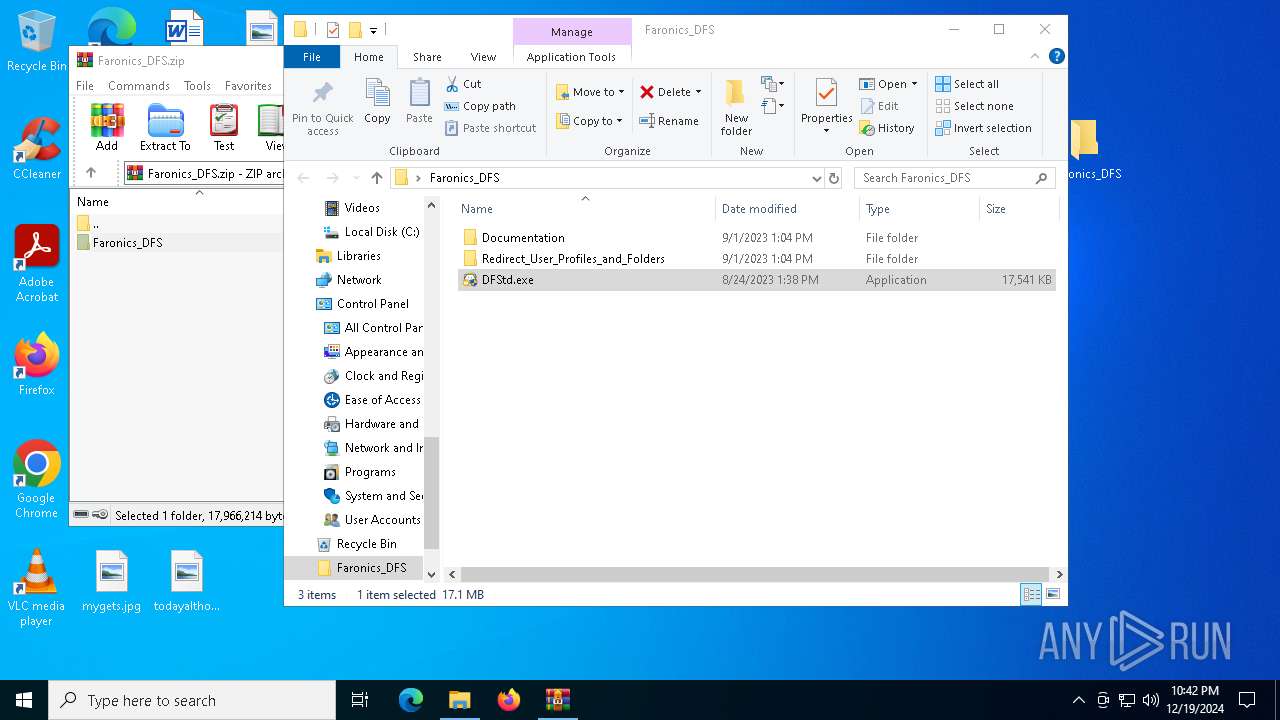
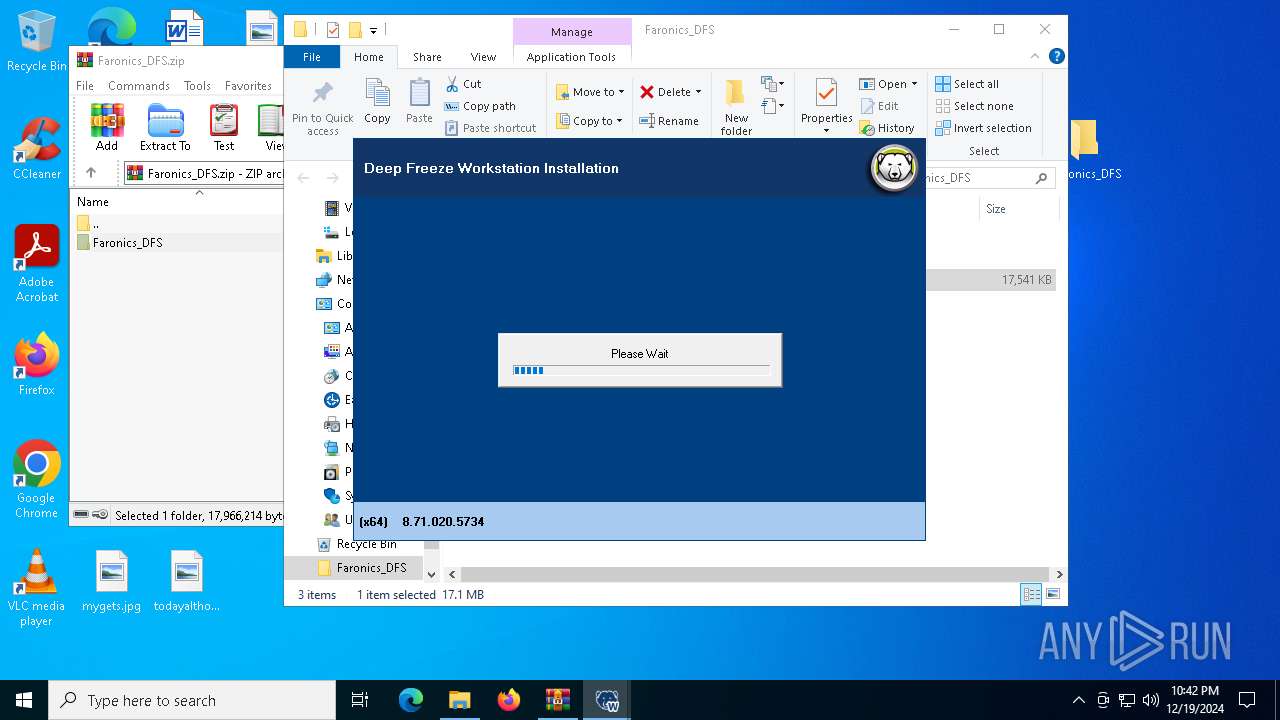
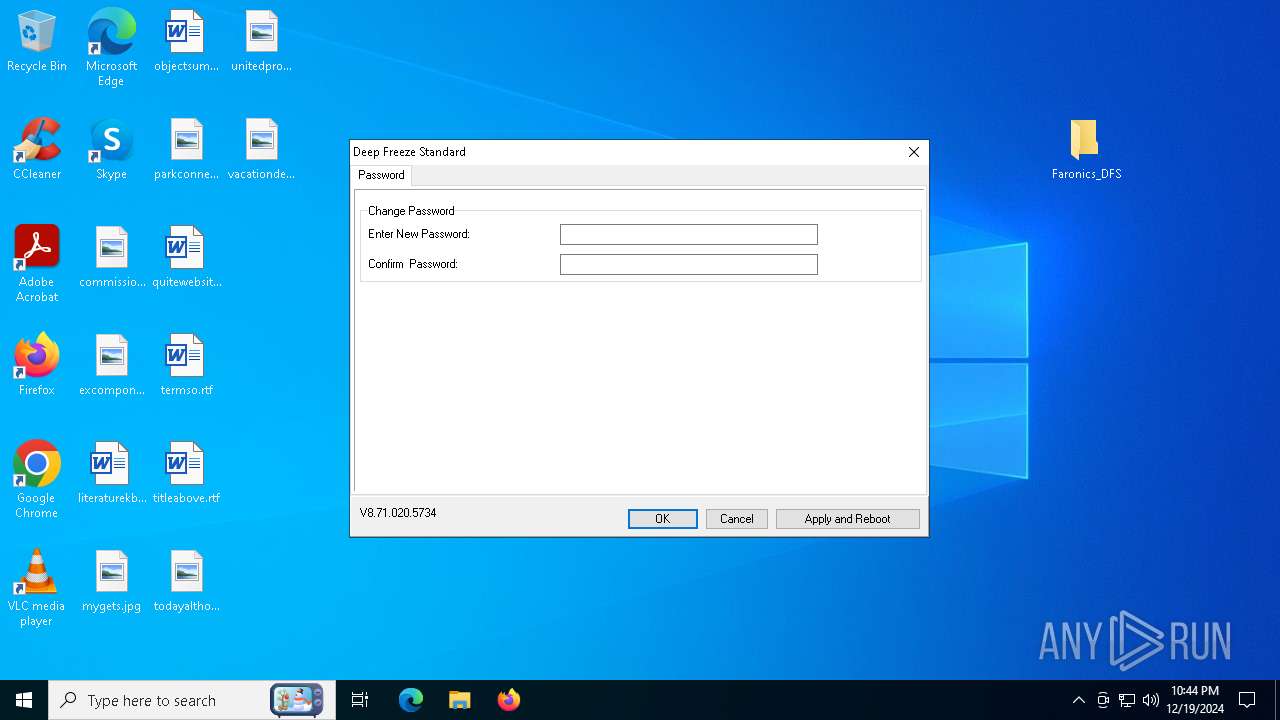
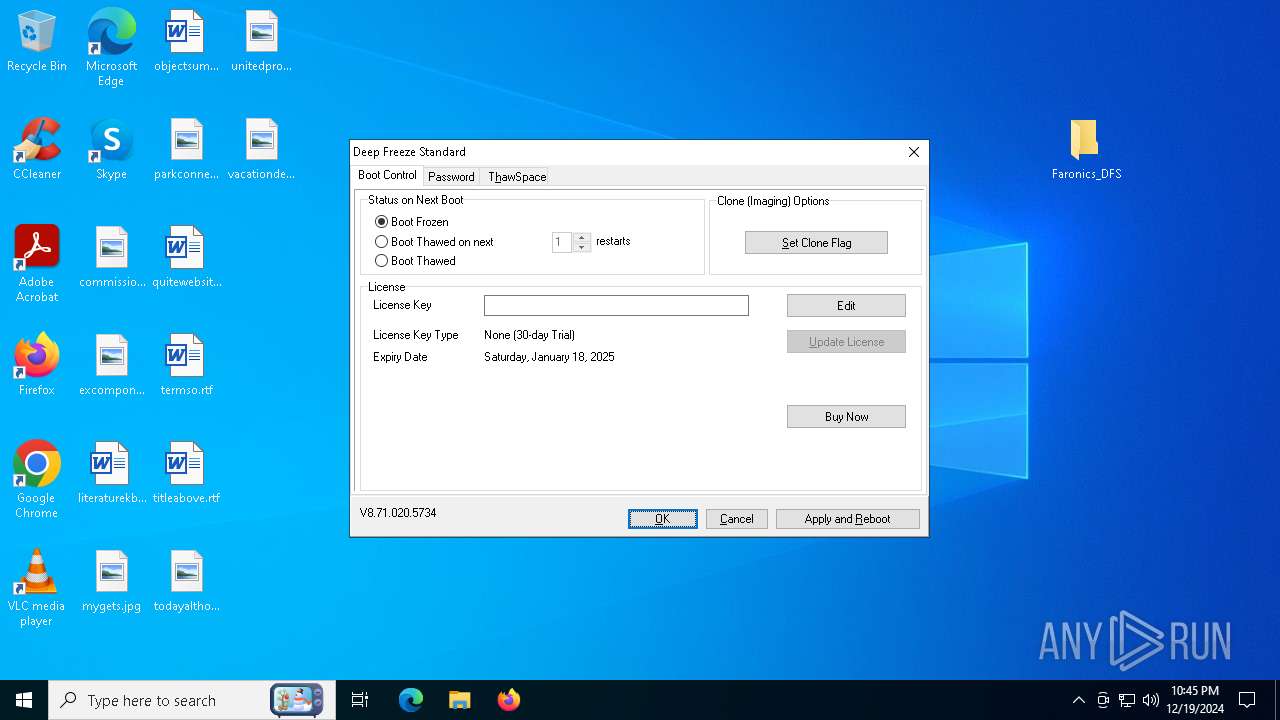
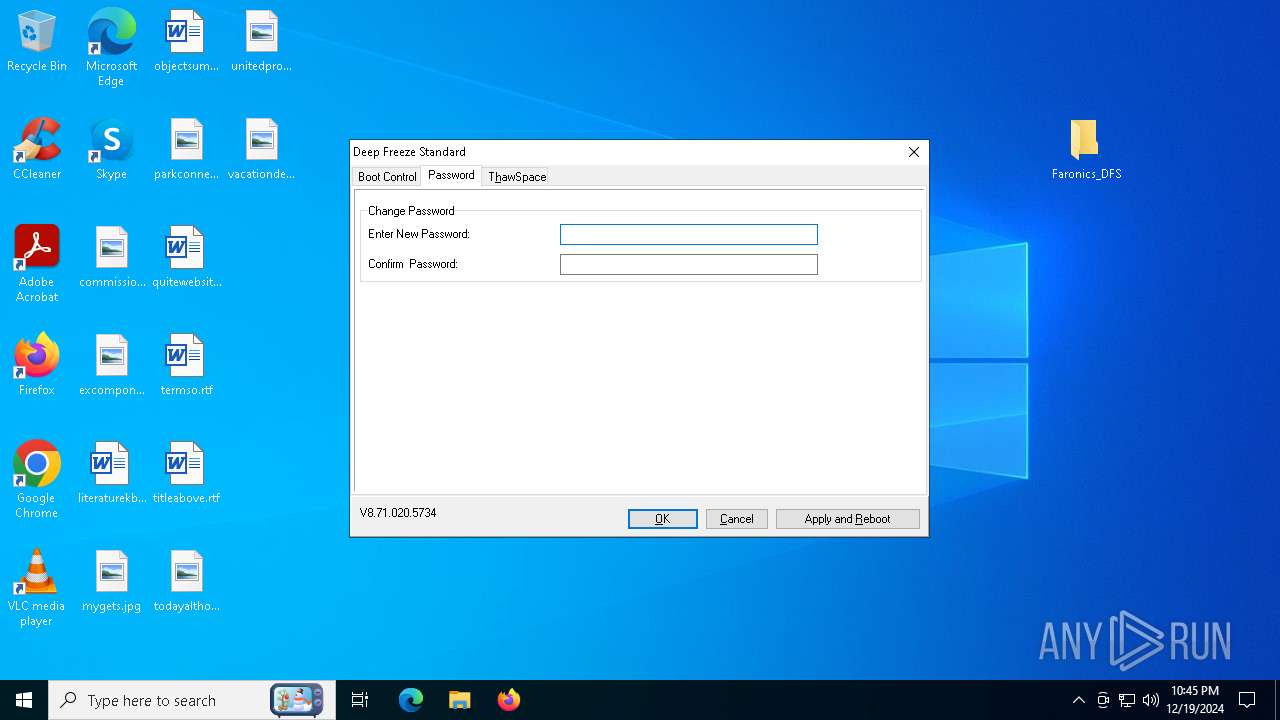
| File name: | Faronics_DFS.zip |
| Full analysis: | https://app.any.run/tasks/f6e20c87-b3f0-461a-9c00-0e3317e60b06 |
| Verdict: | Malicious activity |
| Analysis date: | December 19, 2024, 22:41:40 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 68DAE0B63E600D35F45979378C83343C |
| SHA1: | C289C2F6A6E42007F26262E9E6568D4CEE5CC655 |
| SHA256: | A18B25E22C36A51E84745023198A6B98E363CC72A1DA8FFEE89CB61D44E876C0 |
| SSDEEP: | 98304:c+OmPBb1CJY+Id80IjLleiaaNU/dK9iWXUesrNJU47cY1ioV2R0nwLmx3h906+mJ:+d/YDOoFl04gBuAIwUXm0 |
MALICIOUS
Registers / Runs the DLL via REGSVR32.EXE
- DeepFreeze_C.exe (PID: 4224)
Using BCDEDIT.EXE to modify recovery options
- DeepFreeze_C.exe (PID: 4224)
Starts REAGENTC.EXE to disable the Windows Recovery Environment
- ReAgentc.exe (PID: 6548)
SUSPICIOUS
Creates file in the systems drive root
- DFStd.exe (PID: 6920)
- _T~WUCLI.exe (PID: 6956)
- DeepFreeze_C.exe (PID: 4224)
- _T~WUCLI.exe (PID: 1412)
Detected use of alternative data streams (AltDS)
- _T~WUCLI.exe (PID: 6956)
- _T~WUCLI.exe (PID: 1412)
Executable content was dropped or overwritten
- _T~WUCLI.exe (PID: 6956)
- DFStd.exe (PID: 6920)
- DeepFreeze_C.exe (PID: 4224)
- _T~WUCLI.exe (PID: 1412)
The process creates files with name similar to system file names
- _T~WUCLI.exe (PID: 6956)
- _T~WUCLI.exe (PID: 1412)
Starts a Microsoft application from unusual location
- DismHost.exe (PID: 7044)
- DismHost.exe (PID: 6260)
Creates files in the driver directory
- DeepFreeze_C.exe (PID: 4224)
Starts CMD.EXE for commands execution
- DeepFreeze_C.exe (PID: 4224)
Process drops legitimate windows executable
- _T~WUCLI.exe (PID: 1412)
- _T~WUCLI.exe (PID: 6956)
Drops a system driver (possible attempt to evade defenses)
- DeepFreeze_C.exe (PID: 4224)
The process executes via Task Scheduler
- PLUGScheduler.exe (PID: 4268)
Creates or modifies Windows services
- DeepFreeze_C.exe (PID: 4224)
INFO
Manual execution by a user
- DFStd.exe (PID: 6868)
- DFStd.exe (PID: 6920)
The process uses the downloaded file
- WinRAR.exe (PID: 6356)
The sample compiled with english language support
- WinRAR.exe (PID: 6356)
- DFStd.exe (PID: 6920)
- _T~WUCLI.exe (PID: 6956)
- _T~WUCLI.exe (PID: 1412)
- DeepFreeze_C.exe (PID: 4224)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6356)
Checks supported languages
- DFStd.exe (PID: 6920)
- _T~WUCLI.exe (PID: 6956)
- DismHost.exe (PID: 7044)
- _T~WUCLI.exe (PID: 1412)
- DismHost.exe (PID: 6260)
- DFServ.exe (PID: 6844)
- PLUGScheduler.exe (PID: 4268)
Reads the computer name
- _T~WUCLI.exe (PID: 6956)
- DFStd.exe (PID: 6920)
- DismHost.exe (PID: 7044)
- DismHost.exe (PID: 6260)
- DFServ.exe (PID: 6844)
- FrzState2k.exe (PID: 6908)
- PLUGScheduler.exe (PID: 4268)
Sends debugging messages
- _T~WUCLI.exe (PID: 6956)
- _T~WUCLI.exe (PID: 1412)
- DismHost.exe (PID: 7044)
- DismHost.exe (PID: 6260)
Create files in a temporary directory
- DFStd.exe (PID: 6920)
- DeepFreeze_C.exe (PID: 4224)
- _T~WUCLI.exe (PID: 1412)
- mofcomp.exe (PID: 2632)
- mofcomp.exe (PID: 6736)
- _T~WUCLI.exe (PID: 6956)
Reads Environment values
- DismHost.exe (PID: 7044)
UPX packer has been detected
- DFStd.exe (PID: 6920)
- DeepFreeze_C.exe (PID: 4224)
Creates files in the program directory
- DFStd.exe (PID: 6920)
- DeepFreeze_C.exe (PID: 4224)
- PLUGScheduler.exe (PID: 4268)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2023:08:24 13:38:04 |
| ZipCRC: | 0xf799afb8 |
| ZipCompressedSize: | 12229092 |
| ZipUncompressedSize: | 17961904 |
| ZipFileName: | Faronics_DFS/DFStd.exe |
Total processes
291
Monitored processes
31
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 132 | mofcomp FaronicsWebProduct.mof | C:\Windows\SysWOW64\wbem\mofcomp.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: The Managed Object Format (MOF) Compiler Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1412 | "C:\Users\admin\AppData\Local\Temp\_T~WUCLI.exe" -q -text -logfile "C:\DFInstall.log" | C:\Users\admin\AppData\Local\Temp\_T~WUCLI.exe | DeepFreeze_C.exe | ||||||||||||
User: admin Company: Faronics Corporation Integrity Level: HIGH Description: Deep Freeze Windows Update Command Line Utility Exit code: 0 Version: 8,71,220,5734 Modules
| |||||||||||||||
| 2088 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2448 | C:\WINDOWS\system32\regsvr32.exe /s /u "C:\Program Files (x86)\Faronics\Deep Freeze\Install C-0\DeepFreezeAdapter.dll" | C:\Windows\SysWOW64\regsvr32.exe | — | DeepFreeze_C.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 5 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2556 | "C:\WINDOWS\TEMP\DFLocker64.exe" | C:\Windows\Temp\DFLocker64.exe | — | DFServ.exe | |||||||||||
User: SYSTEM Company: Faronics Corporation Integrity Level: SYSTEM Description: Deep Freeze Show Message Helper Exit code: 0 Version: 8,71,20,5734 Modules
| |||||||||||||||
| 2632 | mofcomp FaronicsWebProduct_v1.mof | C:\Windows\SysWOW64\wbem\mofcomp.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: The Managed Object Format (MOF) Compiler Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3992 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | bcdedit.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
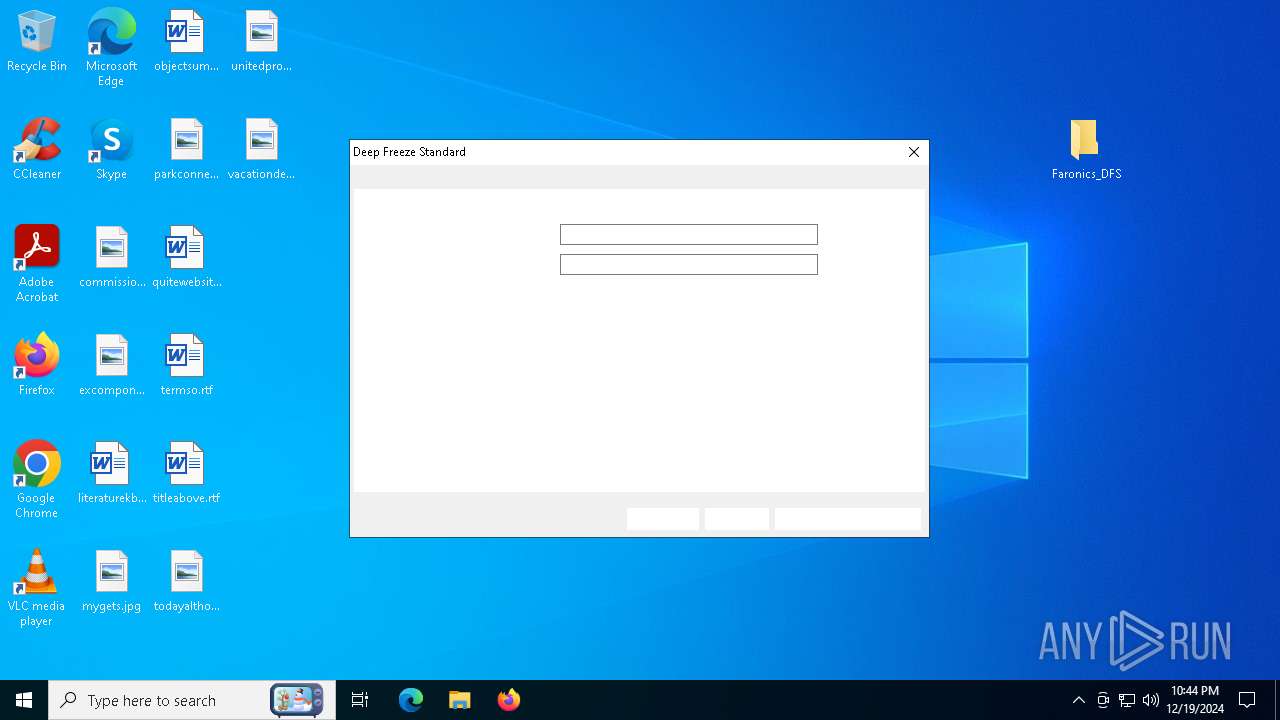
| 4224 | C:\WINDOWS\Temp\DeepFreeze_C.exe /silent /nocloudagent | C:\Windows\Temp\DeepFreeze_C.exe | DFStd.exe | ||||||||||||
User: admin Company: Faronics Corporation Integrity Level: HIGH Description: Workstation install program for Deep Freeze Cloud Exit code: 1073807364 Version: 8,71,20,5734 Modules
| |||||||||||||||
| 4268 | "C:\Program Files\RUXIM\PLUGscheduler.exe" | C:\Program Files\RUXIM\PLUGScheduler.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Update LifeCycle Component Scheduler Exit code: 0 Version: 10.0.19041.3623 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4872 | cmd.exe /c cd "C:\Program Files (x86)\Faronics\Deep Freeze\Install C-0" & mofcomp FaronicsWebProduct.mof >> "%TEMP%\mof.log" & mofcomp FaronicsWebProduct_v1.mof >> "%TEMP%\mof.log" & mofcomp DeepFreezeWorkstation.mof >> "%TEMP%\mof.log" | C:\Windows\SysWOW64\cmd.exe | — | DeepFreeze_C.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
71 161
Read events
70 982
Write events
66
Delete events
113
Modification events
| (PID) Process: | (6356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Faronics_DFS.zip | |||
| (PID) Process: | (6356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7120) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | SessionIdHigh |
Value: 31150695 | |||
| (PID) Process: | (7120) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | SessionIdLow |
Value: | |||
Executable files
117
Suspicious files
56
Text files
18
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6356 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6356.42990\Faronics_DFS\Documentation\Deutsch\Data Igloo Benutzerhandbuch.url | url | |
MD5:A120FBA0F516B4652BB7F57DC9EE8F39 | SHA256:CAD41215863779C97D96C3D209F7AB5C82BF5F92323F68122BF3B405CAC22A77 | |||
| 6356 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6356.42990\Faronics_DFS\Documentation\Espanol\Deep Freeze Standard Guiüa de usuario.url | url | |
MD5:632D44C61955F3DB1680529FDBF077B4 | SHA256:79BABE9CD9DAF02AE2BED1A6A4196EEBB49FE4748845B00674D18A32DF3CBE25 | |||
| 6356 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6356.42990\Faronics_DFS\Documentation\Francais\Deep Freeze Standard Manuel de l'utilisateur.url | binary | |
MD5:5C078540122FEC4C04685284BC39D691 | SHA256:5A9E03416841356767528DCC9F68C622FA531C3D2AC6DB1822A3E9272E3884EB | |||
| 6356 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6356.42990\Faronics_DFS\Documentation\Japanese\Data Igloo User Guide.url | url | |
MD5:93DFF501D597EBDF8141B6C5F267EA2F | SHA256:E09937D664933D16F2CBC5958D046B6DBC0527C5BCE3D87D21CCDFE3D706A569 | |||
| 6356 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6356.42990\Faronics_DFS\Documentation\Francais\Data Igloo Manuel de l'utilisateur.url | binary | |
MD5:872381DC88E9248E51ECD9B8602D3935 | SHA256:3ED7D402D7F754FA4D774D47521CBBDEA734AED37E54FBA4D3AE32A59AC08AB2 | |||
| 6356 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6356.42990\Faronics_DFS\Documentation\Japanese\Deep Freeze Standard User Guide.url | url | |
MD5:F143037F4CDAD5E228840F4C855D8DA6 | SHA256:4BAA1E3D54352386C5B9D62DEFA3989D7CB46D290BACD8E0FC3D4AEC51B823BE | |||
| 6920 | DFStd.exe | C:\DFInstall.log | text | |
MD5:8958AD5928EF887F23DDB8213D3B6D9C | SHA256:B2F49197CCB8EC96942A303C52B6FCD2F691258EB82319746109AA2579966CBE | |||
| 6356 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6356.42990\Faronics_DFS\Redirect_User_Profiles_and_Folders\Faronics_Data_Igloo_README.txt | text | |
MD5:66D53F40679AED7EEC9C87EFB38E60DB | SHA256:43CDE118DDF08402731C1E769EB65C787200193E1DE1F2E2B5376A97185BB6F6 | |||
| 6956 | _T~WUCLI.exe | C:\Users\admin\AppData\Local\Temp\FC175909-2947-4542-8B76-6665104B4900\AppxProvider.dll | executable | |
MD5:396C483D62FEA5FA0FD442C8DC99D4EF | SHA256:36F2AF43F10FD76FEEF65BF574D79D3E27FD40DAF61249880511543C1F17AD91 | |||
| 6356 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6356.42990\Faronics_DFS\Documentation\Simplified Chinese\Deep Freeze Standard User Guide.url | url | |
MD5:2654FEF42E9D23CEE31239C354FE7507 | SHA256:94B5520D0C93263E00E11C5493D9634EAA344A7D31270F660F13EDA7E4A86A18 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
56
DNS requests
33
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5564 | svchost.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5564 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5728 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5072 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3420 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5728 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1140 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5564 | svchost.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5564 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 2.23.209.133:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
_T~WUCLI.exe | PID=6956 TID=6960 DismApi.dll: Parent process command line: "C:\Users\admin\AppData\Local\Temp\_T~WUCLI.exe" -q -text -logfile "C:\DFInstall.log" - DismInitializeInternal
|
_T~WUCLI.exe | PID=6956 TID=6960 Input parameters: LogLevel: 0, LogFilePath: (null), ScratchDirectory: (null) - DismInitializeInternal
|
_T~WUCLI.exe | PID=6956 TID=6960 DismApi.dll: - DismInitializeInternal
|
_T~WUCLI.exe | PID=6956 TID=6960 DismApi.dll: <----- Starting DismApi.dll session -----> - DismInitializeInternal
|
_T~WUCLI.exe | PID=6956 TID=6960 Enter DismInitializeInternal - DismInitializeInternal
|
_T~WUCLI.exe | PID=6956 TID=6960 DismApi.dll: - DismInitializeInternal
|
_T~WUCLI.exe | PID=6956 TID=6960 DismApi.dll: Host machine information: OS Version=10.0.19045, Running architecture=x86, Number of processors=4 - DismInitializeInternal
|
_T~WUCLI.exe | PID=6956 TID=6960 DismApi.dll: API Version 10.0.19041.3758 - DismInitializeInternal
|
_T~WUCLI.exe | PID=6956 TID=6960 Initialized SessionTable - DismInitializeInternal
|
_T~WUCLI.exe | PID=6956 TID=6960 Initialized GlobalConfig - DismInitializeInternal
|