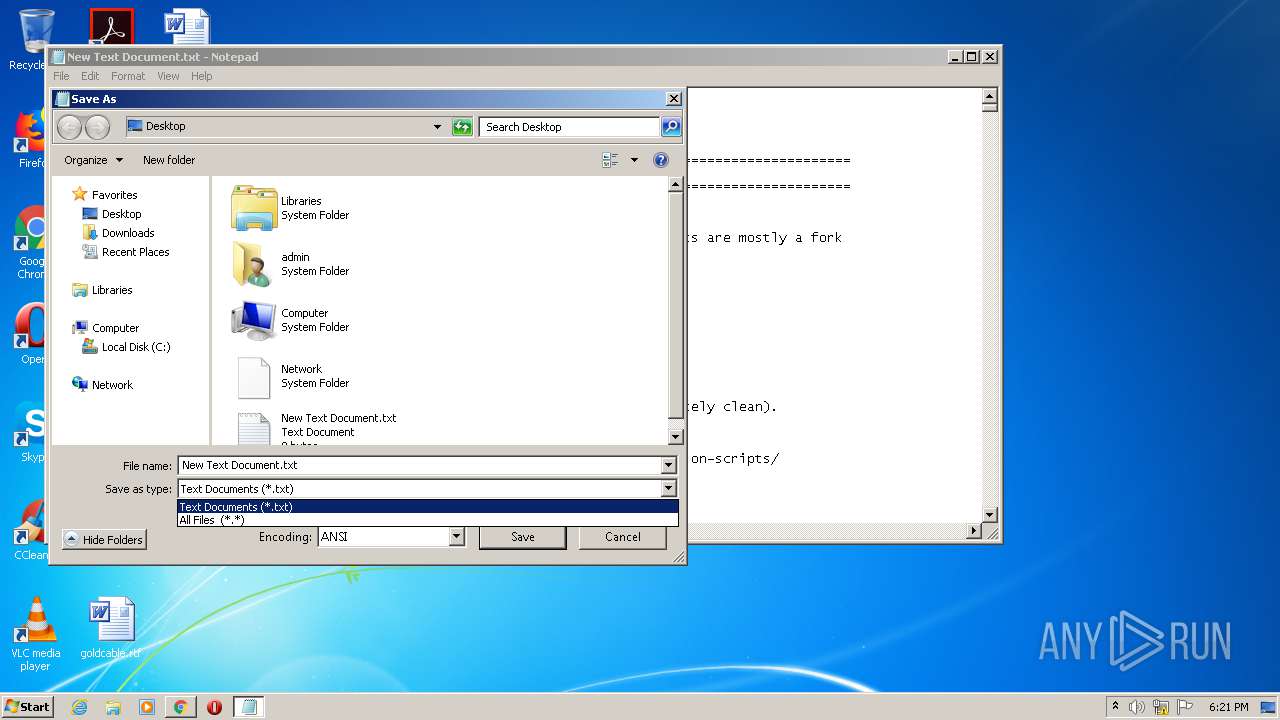
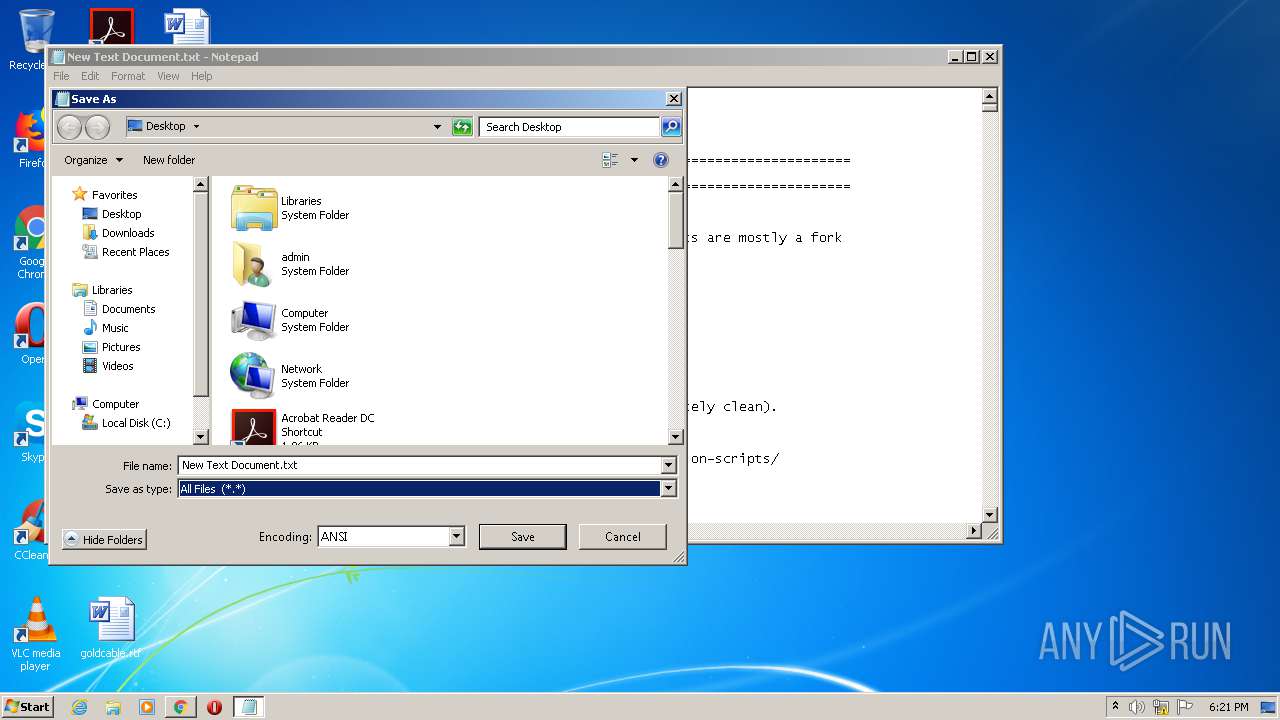
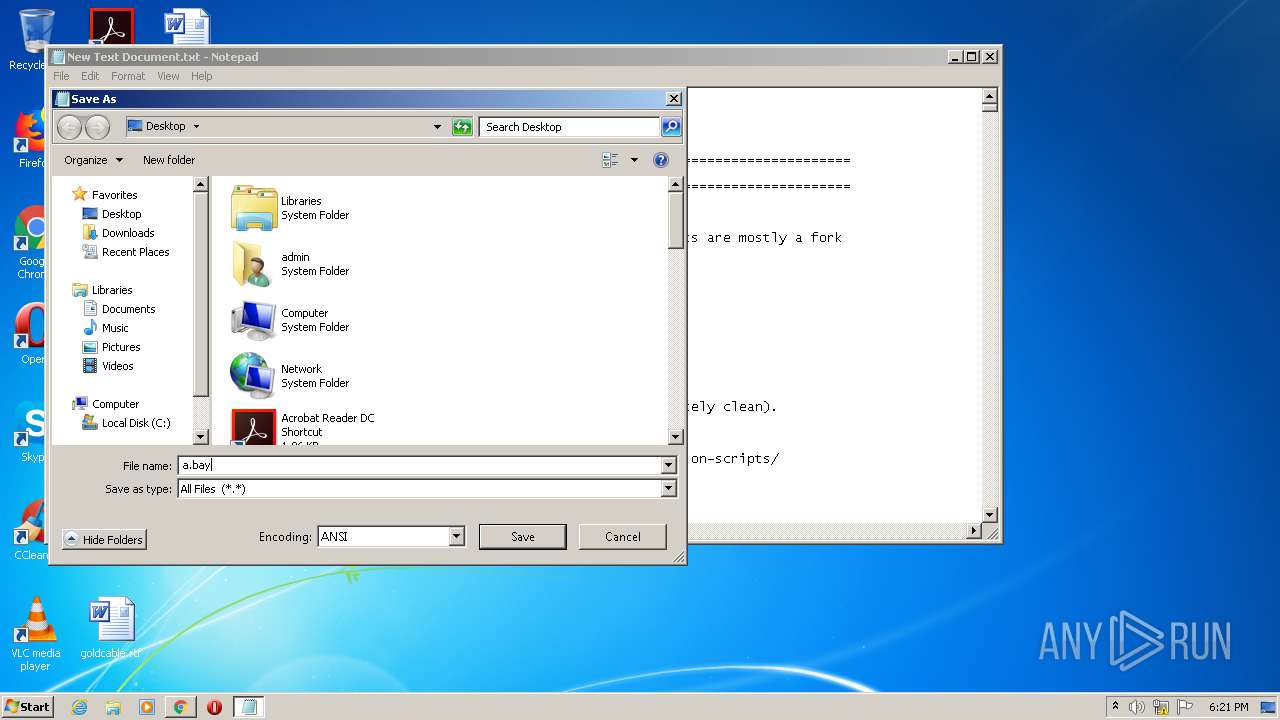
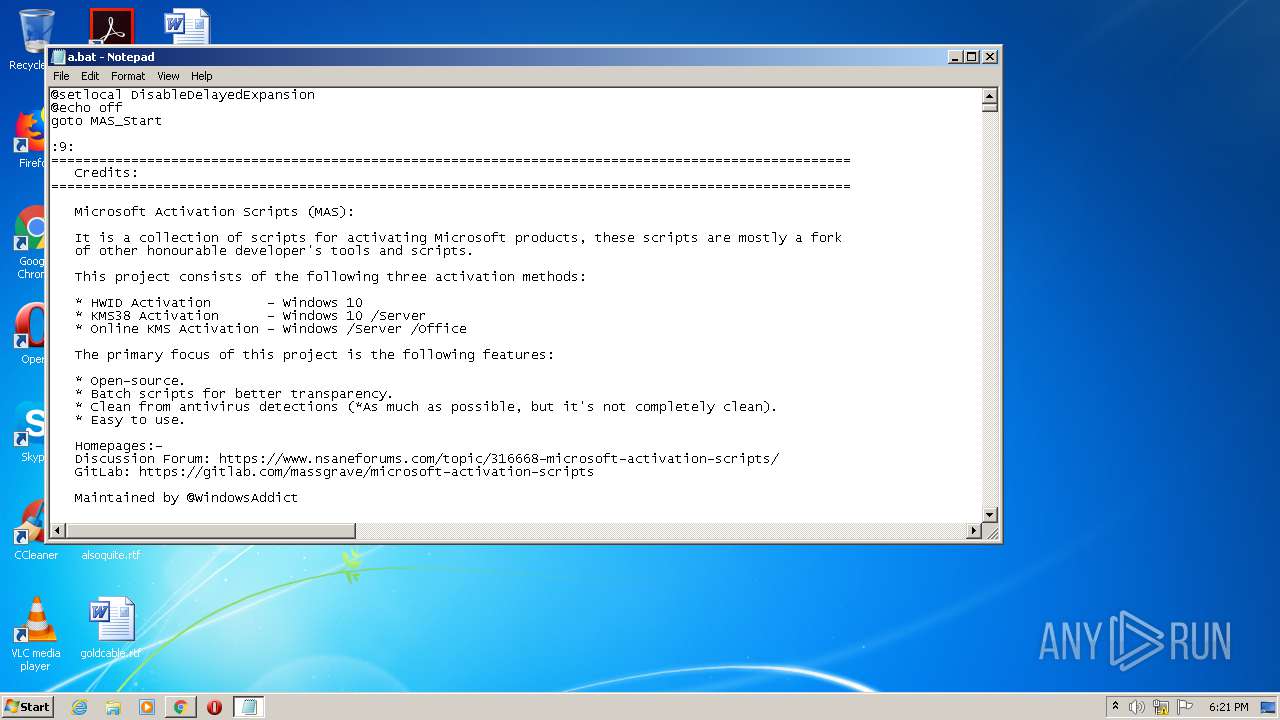
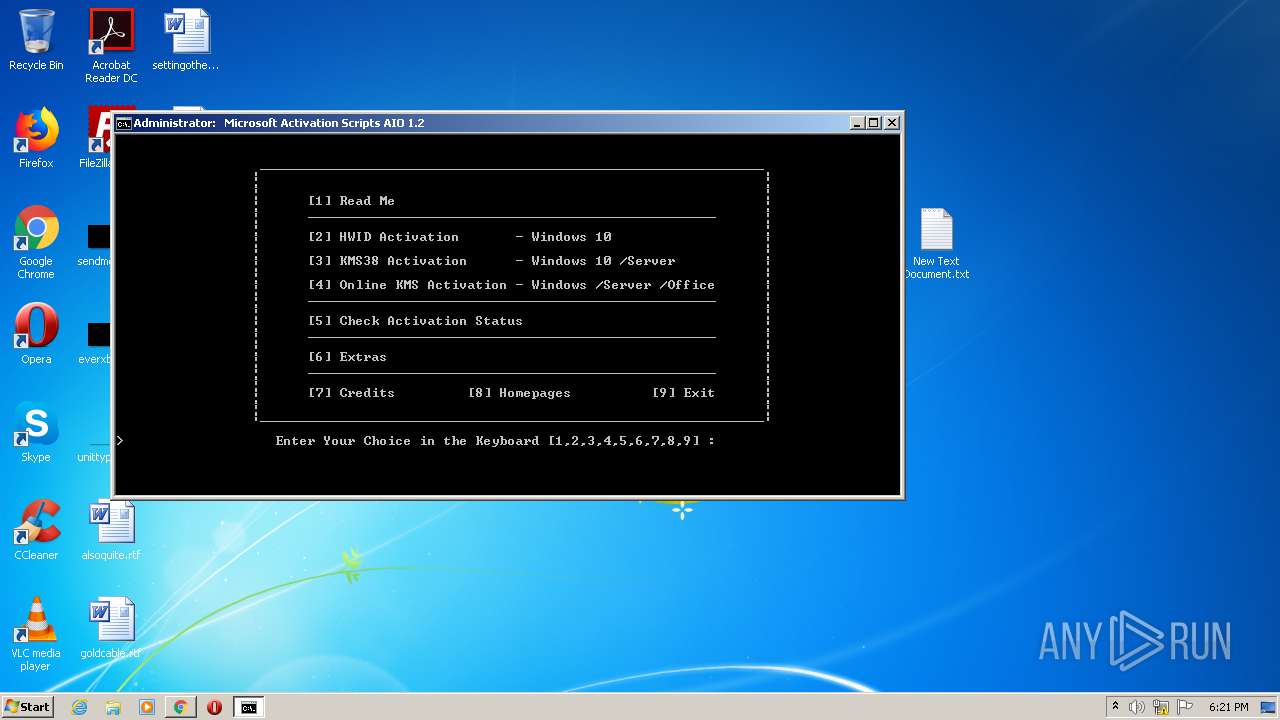
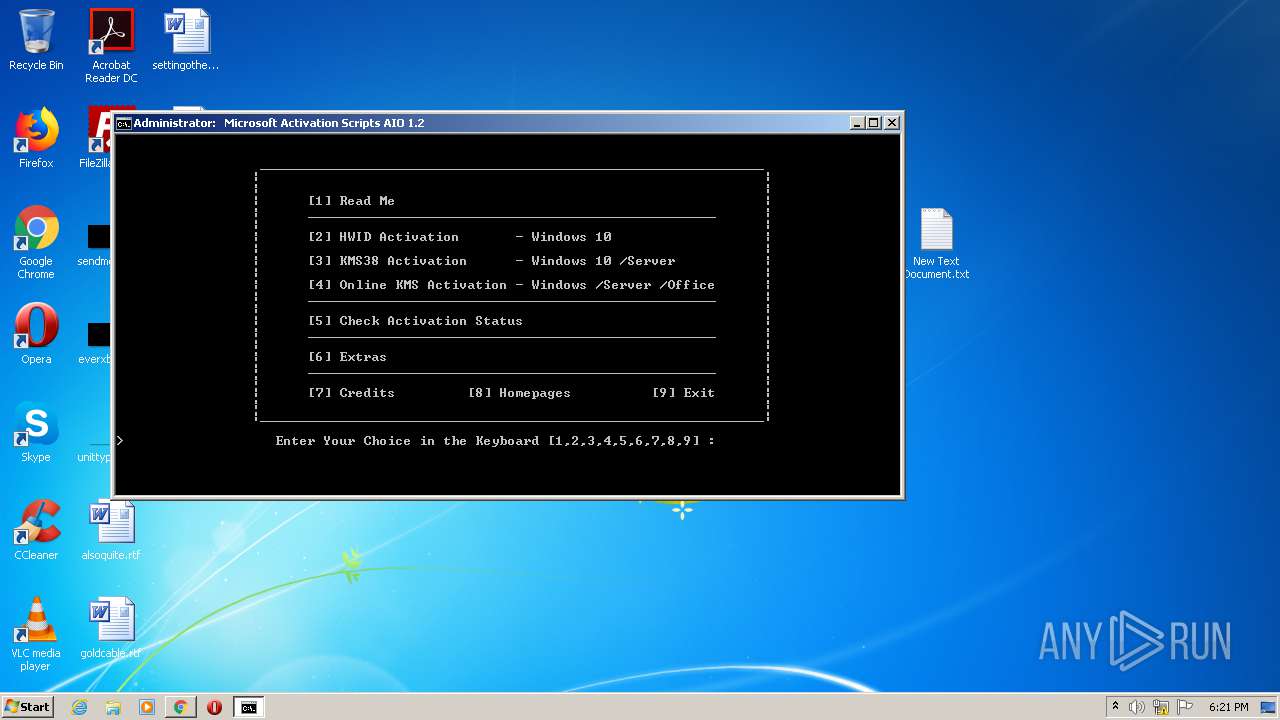
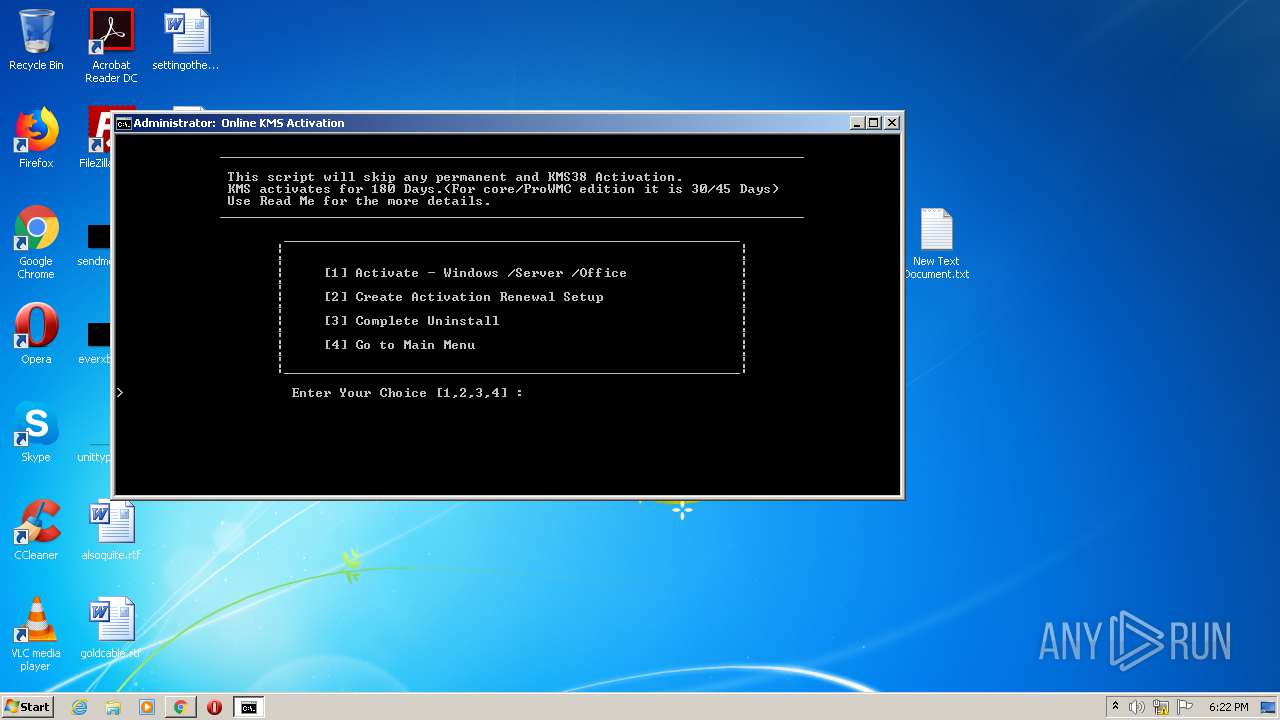
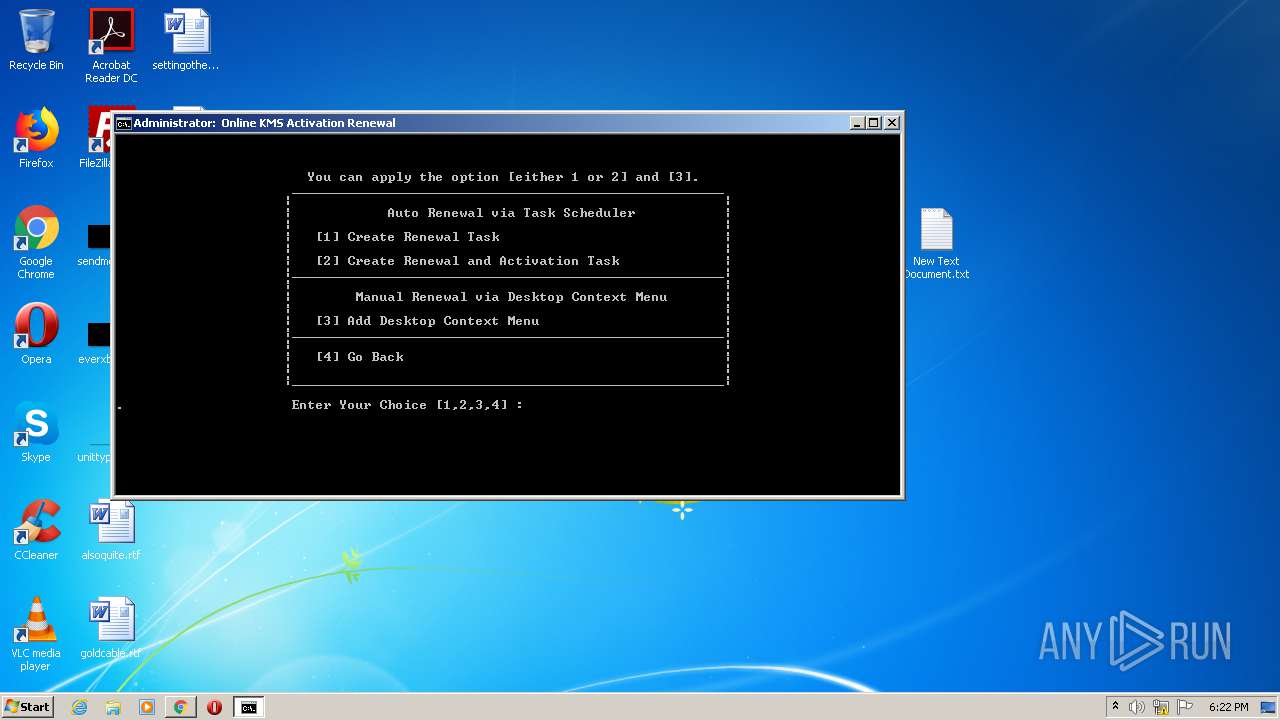
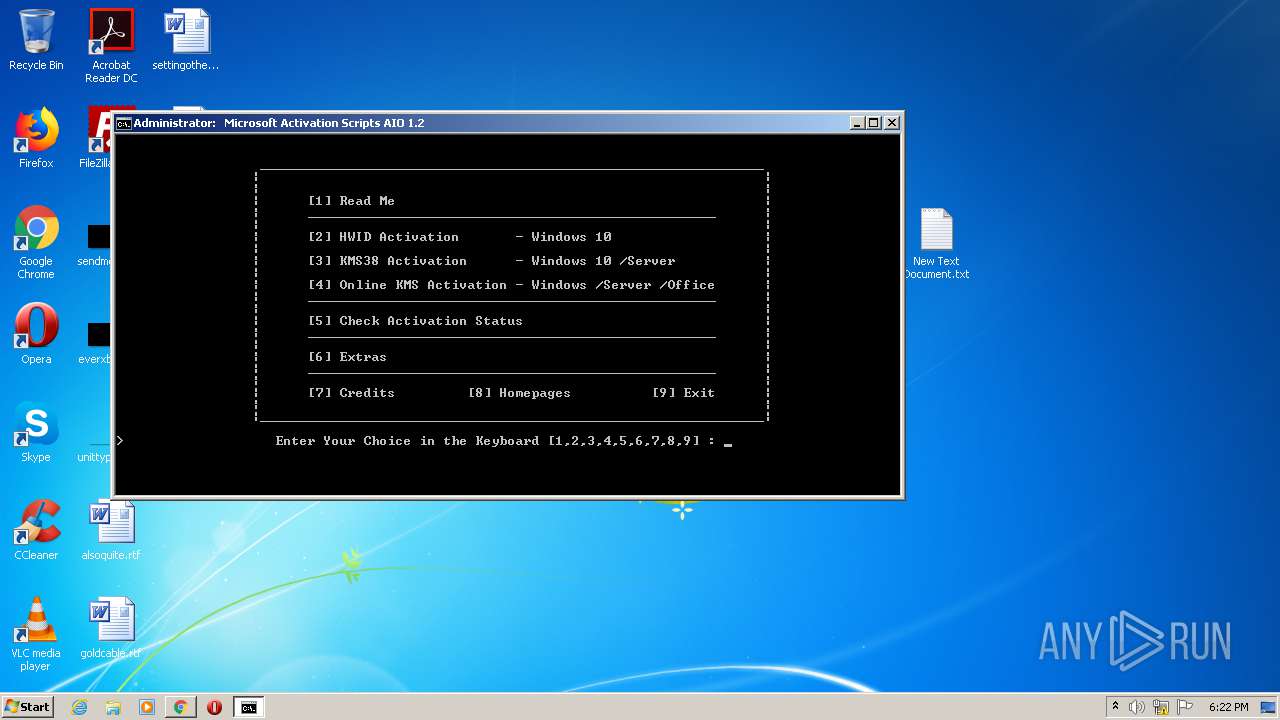
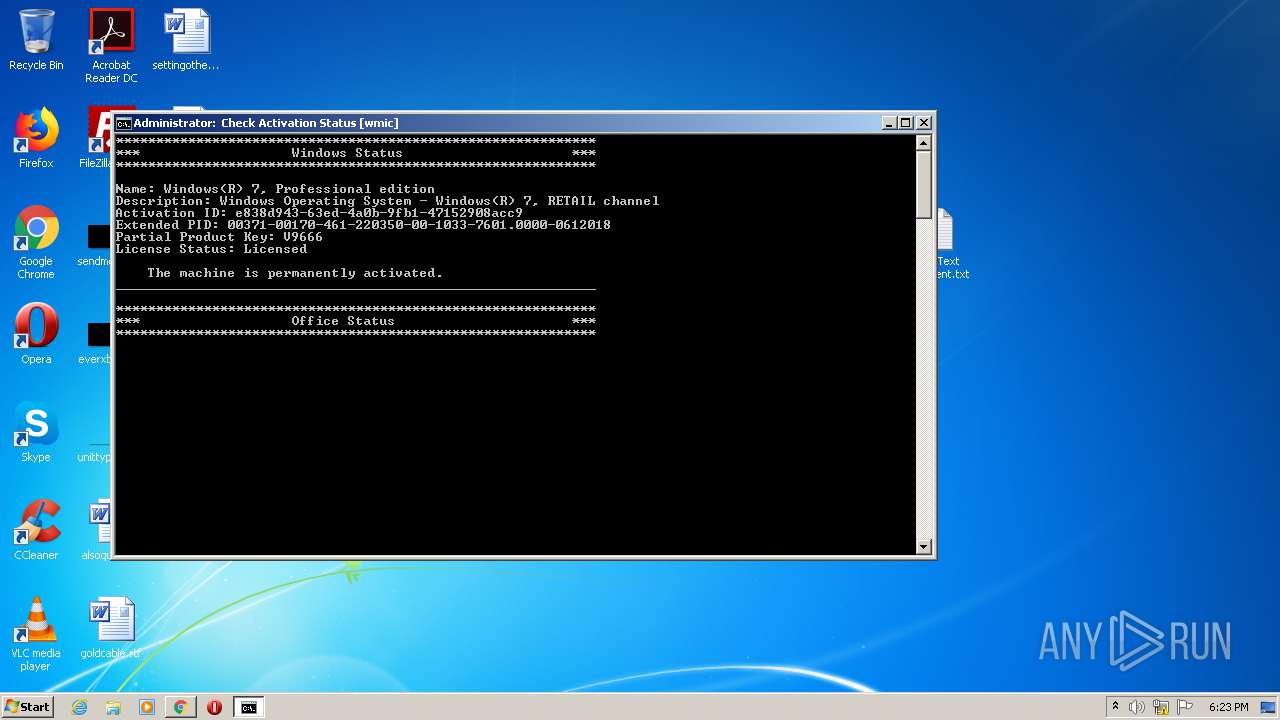
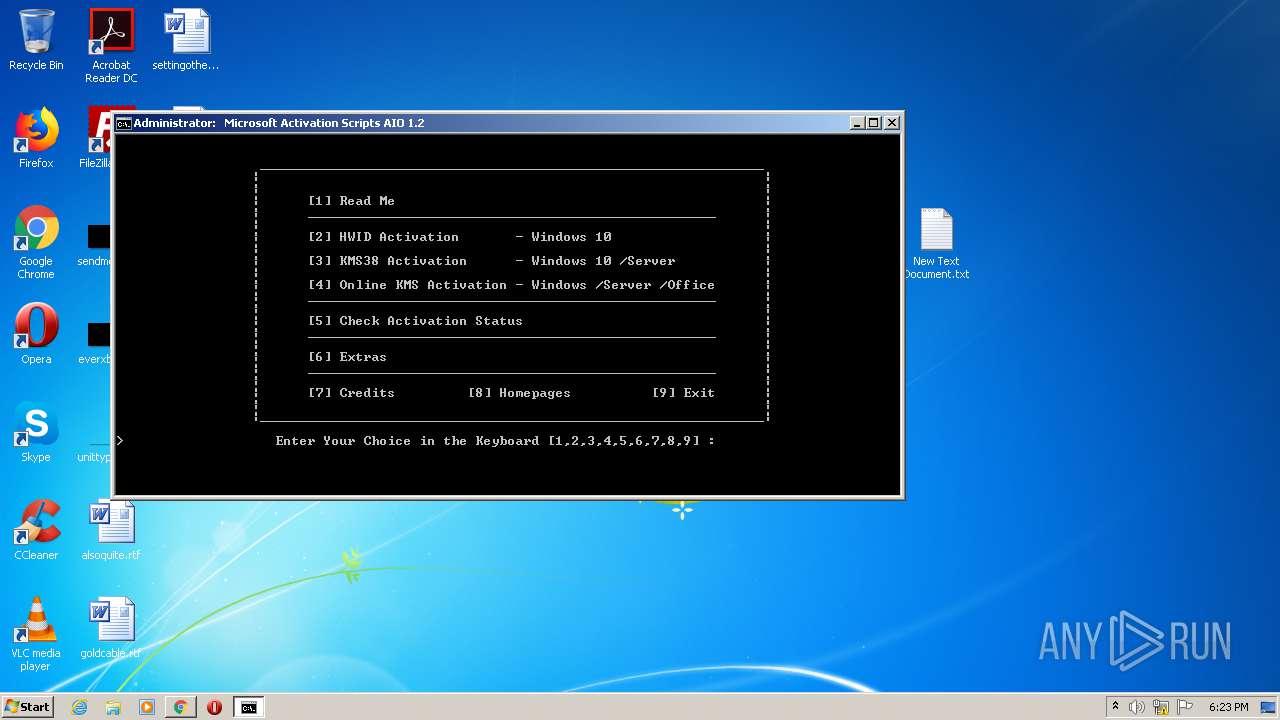
| URL: | https://github.com/massgravel/Microsoft-Activation-Scripts/tree/master/MAS_1.2/All-In-One-Version |
| Full analysis: | https://app.any.run/tasks/0acbf680-38f1-4f57-a790-e927cab95d21 |
| Verdict: | Malicious activity |
| Analysis date: | August 16, 2020, 17:19:48 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 43BF9C0D24C1EEC765C9A3FE3102C2FF |
| SHA1: | 7C0A5026C5A823152490E3525A5F536D6A9B5DDE |
| SHA256: | A169F3019A4F56E91871A1F1B20C8FFB5C61DCC9C84B9B77639F020702D336E1 |
| SSDEEP: | 3:N8tEd4PKoHXuukGR3RLLLGXUuvI+e0IqLAOAE:2uuPKzukGv/LGXUyI+es0vE |
MALICIOUS
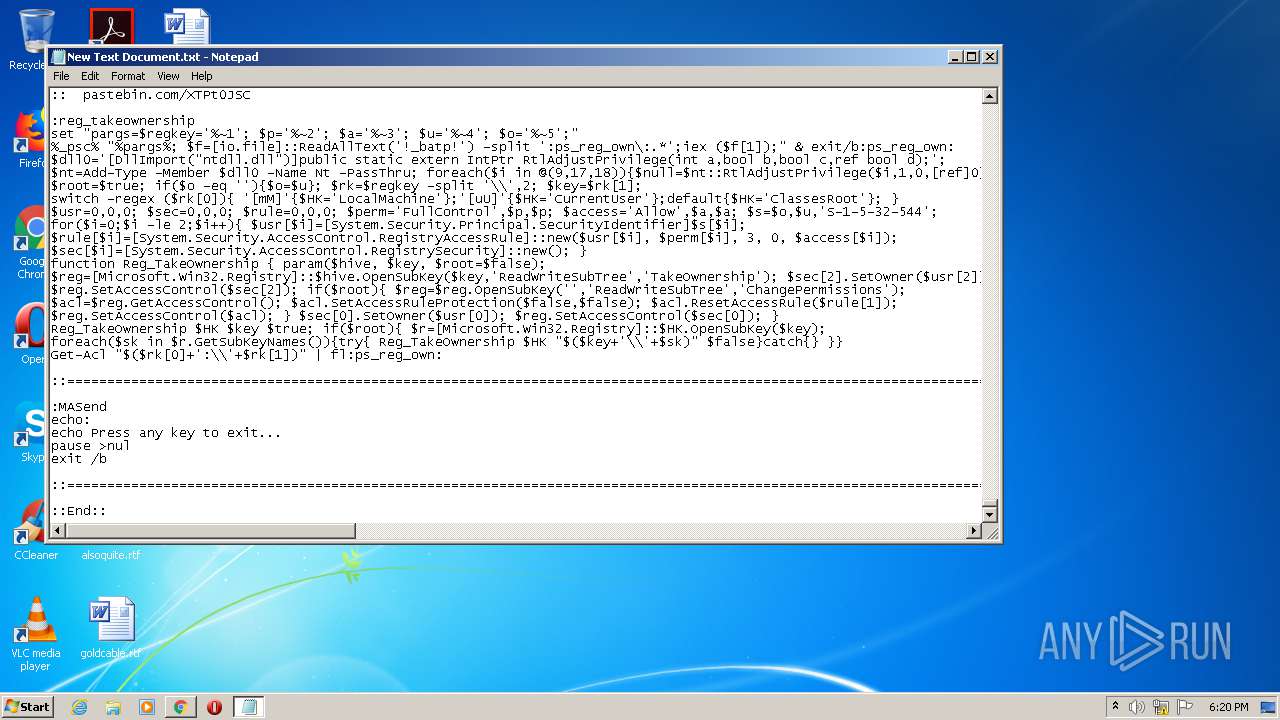
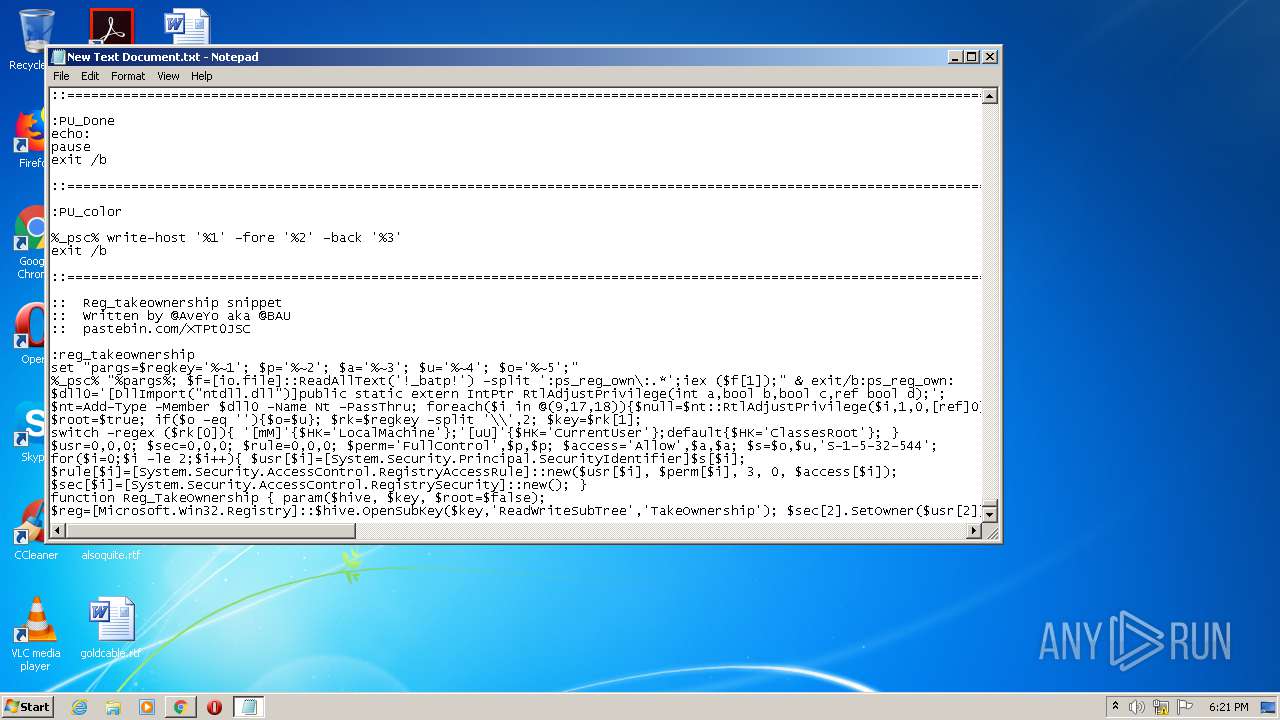
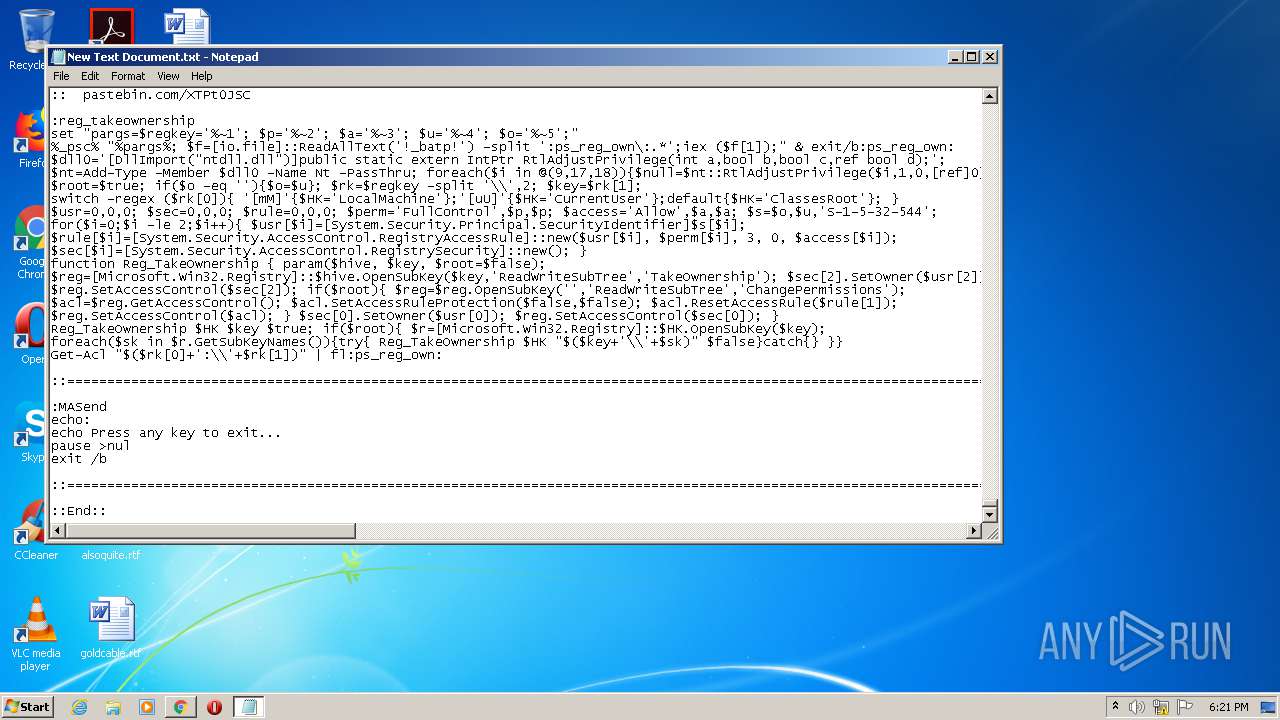
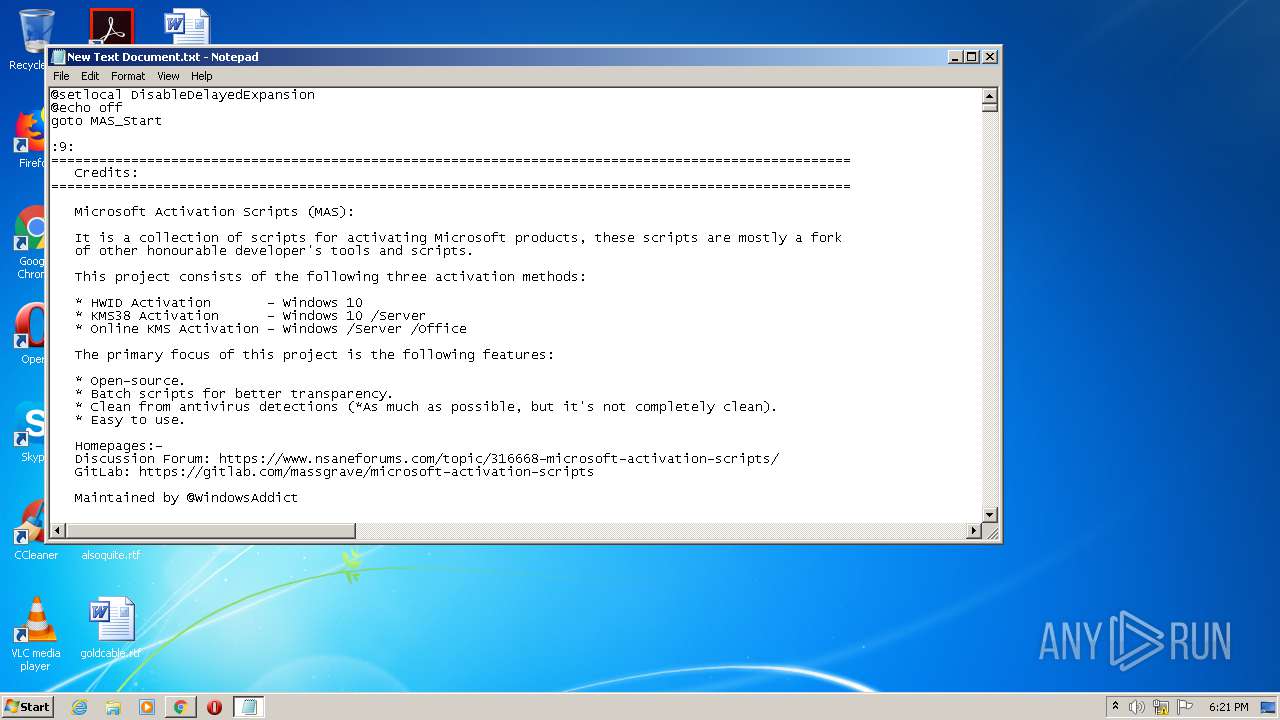
Executes PowerShell scripts
- cmd.exe (PID: 1820)
- cmd.exe (PID: 3884)
- cmd.exe (PID: 2400)
Starts Visual C# compiler
- powershell.exe (PID: 2224)
- powershell.exe (PID: 2496)
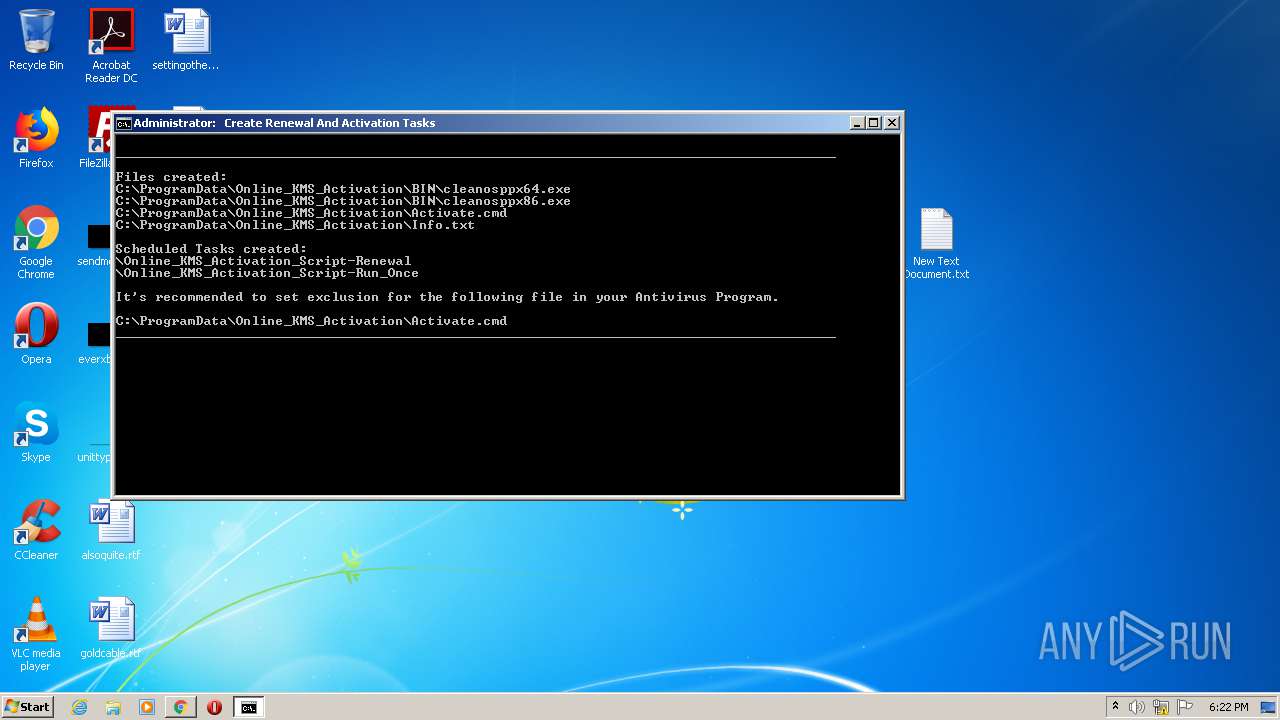
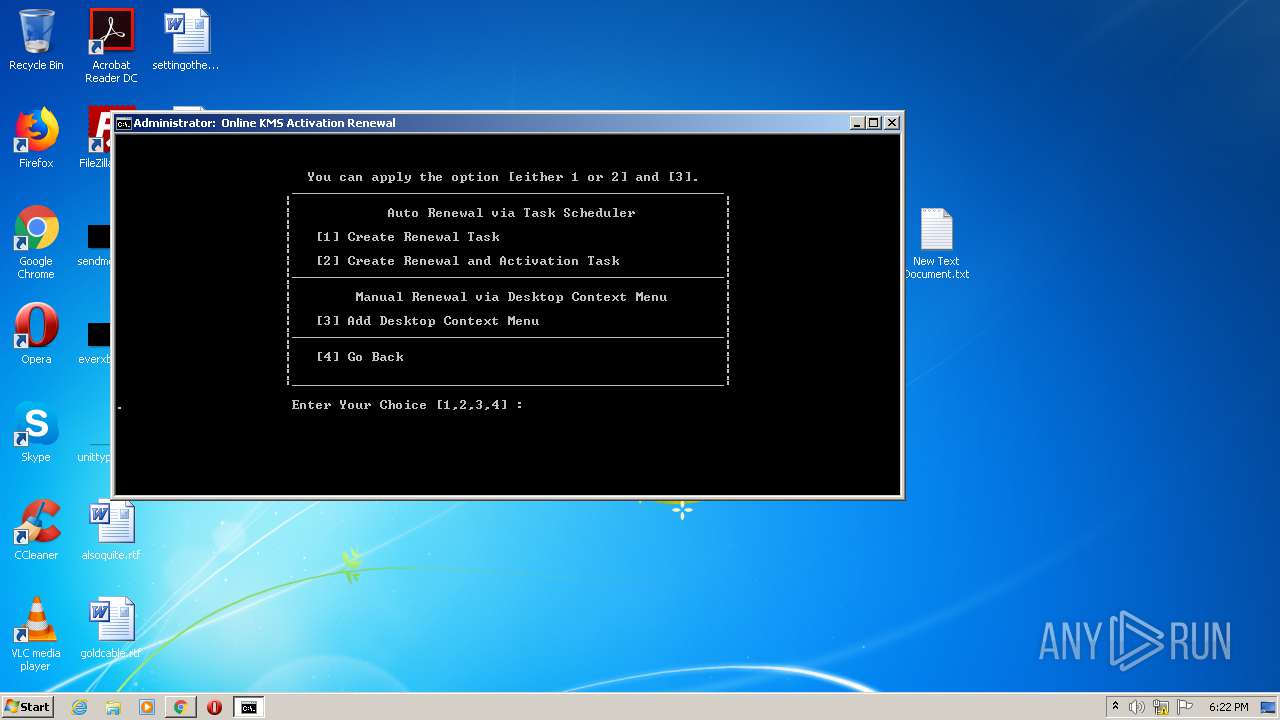
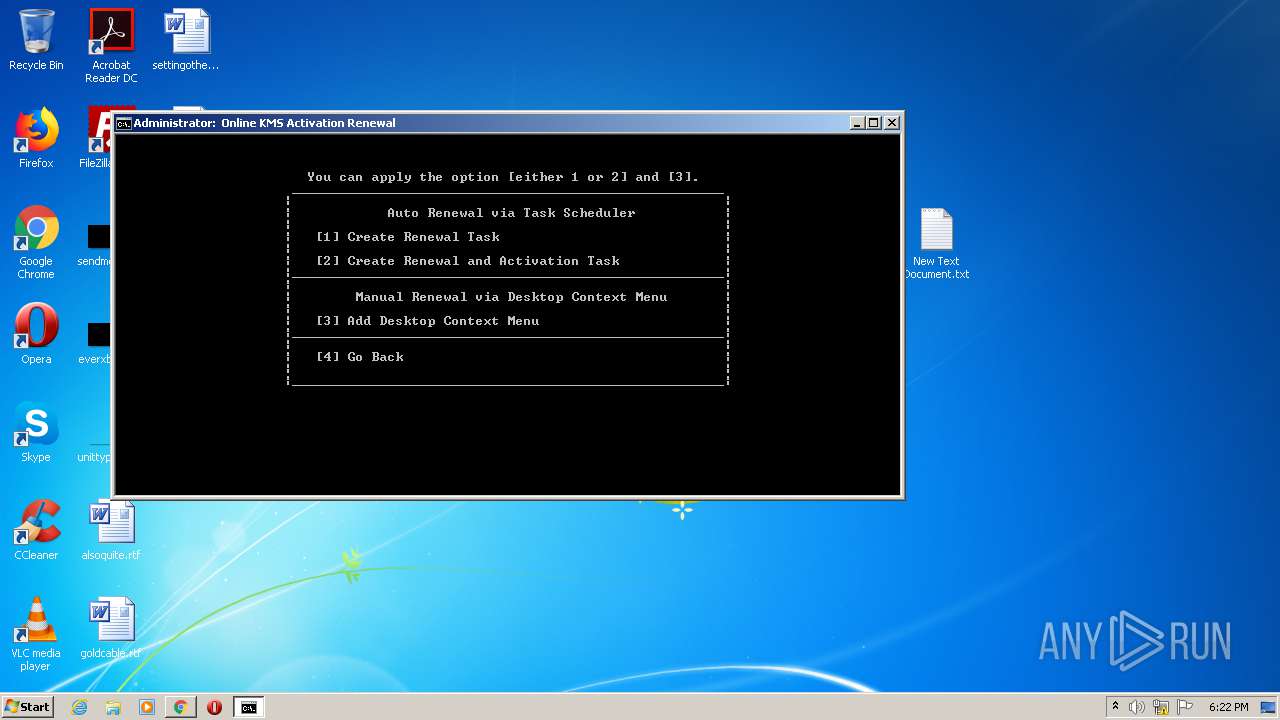
Uses Task Scheduler to run other applications
- cmd.exe (PID: 2400)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 2476)
- schtasks.exe (PID: 2480)
SUSPICIOUS
Starts CMD.EXE for commands execution
- cmd.exe (PID: 1668)
- cscript.exe (PID: 116)
- cmd.exe (PID: 1820)
- cmd.exe (PID: 3884)
- cmd.exe (PID: 2400)
Executes scripts
- cmd.exe (PID: 1668)
Creates files in the user directory
- powershell.exe (PID: 4000)
- powershell.exe (PID: 2436)
- powershell.exe (PID: 2224)
- powershell.exe (PID: 272)
- powershell.exe (PID: 2988)
- powershell.exe (PID: 3616)
- powershell.exe (PID: 3028)
- powershell.exe (PID: 2496)
- powershell.exe (PID: 3752)
- powershell.exe (PID: 2484)
- powershell.exe (PID: 2976)
- powershell.exe (PID: 4076)
- powershell.exe (PID: 2448)
- powershell.exe (PID: 3036)
- powershell.exe (PID: 4008)
- powershell.exe (PID: 1376)
- powershell.exe (PID: 3892)
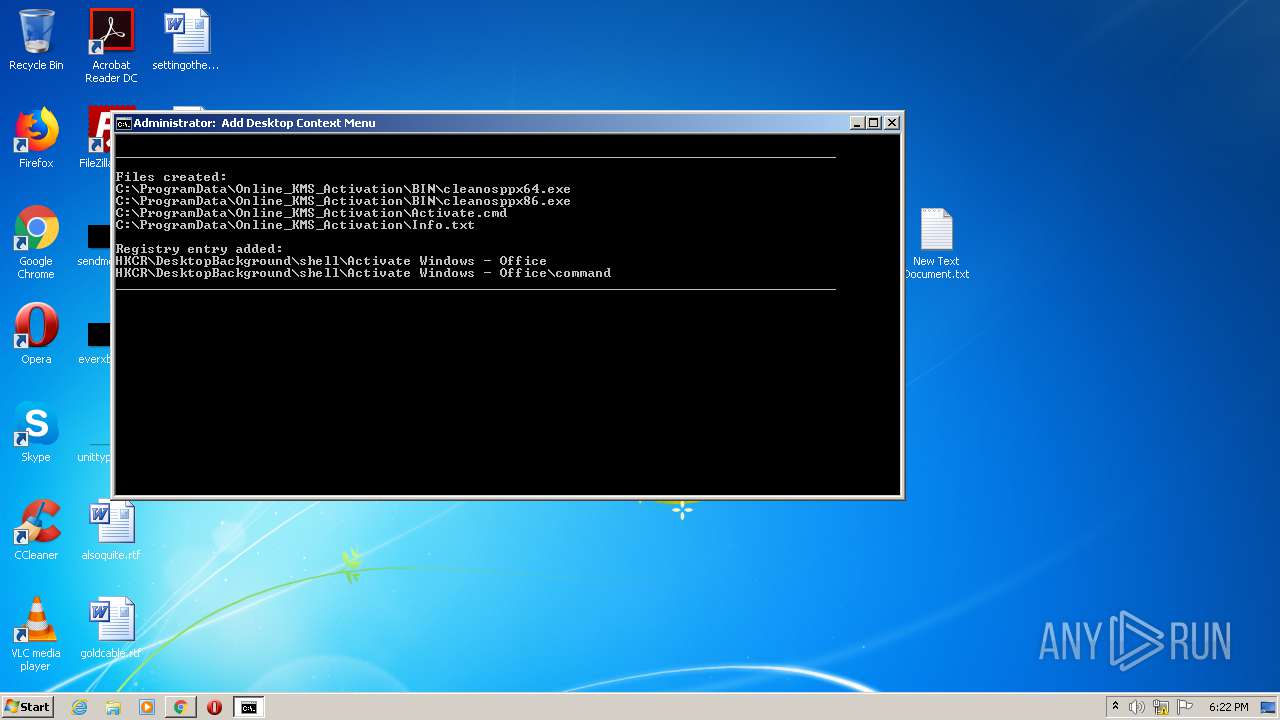
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 1668)
- cmd.exe (PID: 1820)
- cmd.exe (PID: 3884)
- cmd.exe (PID: 3784)
- cmd.exe (PID: 2400)
Application launched itself
- cmd.exe (PID: 1668)
- cmd.exe (PID: 1820)
- cmd.exe (PID: 3884)
- cmd.exe (PID: 2400)
Uses RUNDLL32.EXE to load library
- cscript.exe (PID: 116)
Starts CHOICE.EXE (used to create a delay)
- cmd.exe (PID: 1820)
- cmd.exe (PID: 2400)
Creates files in the Windows directory
- powershell.exe (PID: 3892)
- powershell.exe (PID: 2224)
- expand.exe (PID: 976)
- powershell.exe (PID: 2988)
- powershell.exe (PID: 3616)
- powershell.exe (PID: 2496)
- expand.exe (PID: 3020)
- powershell.exe (PID: 2484)
- powershell.exe (PID: 2976)
Executable content was dropped or overwritten
- expand.exe (PID: 976)
- expand.exe (PID: 3020)
- cmd.exe (PID: 2400)
Removes files from Windows directory
- expand.exe (PID: 976)
- powershell.exe (PID: 2224)
- cmd.exe (PID: 1820)
- expand.exe (PID: 3020)
- powershell.exe (PID: 2496)
- cmd.exe (PID: 2400)
Creates files in the program directory
- powershell.exe (PID: 4076)
- cmd.exe (PID: 2400)
- powershell.exe (PID: 2448)
Uses WMIC.EXE to obtain a system information
- cmd.exe (PID: 3400)
- cmd.exe (PID: 1820)
- cmd.exe (PID: 3016)
- cmd.exe (PID: 3252)
- cmd.exe (PID: 2360)
INFO
Reads the hosts file
- chrome.exe (PID: 2644)
- chrome.exe (PID: 2536)
Reads settings of System Certificates
- chrome.exe (PID: 2536)
Application launched itself
- chrome.exe (PID: 2644)
Manual execution by user
- cmd.exe (PID: 1668)
- NOTEPAD.EXE (PID: 2340)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
178
Monitored processes
129
Malicious processes
6
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | cscript //NoLogo "C:\Users\admin\AppData\Local\Temp\admin.vbs" /File:"C:\Users\admin\Desktop\a.bat" -el | C:\Windows\system32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 272 | powershell -nop -ep bypass -c "&{$H=get-host;$W=$H.ui.rawui;$B=$W.buffersize;$B.height=150;$W.buffersize=$B;}" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 308 | mode con cols=98 lines=30 | C:\Windows\system32\mode.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: DOS Device MODE Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 376 | reg query "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\taskcache\tasks" /f Path /s | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 612 | cmd /c exit /b 0 | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 624 | C:\Windows\system32\cmd.exe /c ver | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 664 | choice /C:1234 /N /M ". Enter Your Choice [1,2,3,4] : " | C:\Windows\system32\choice.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Offers the user a choice Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 684 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\g2fl8flx.cmdline" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Visual C# Command Line Compiler Exit code: 0 Version: 8.0.50727.4927 (NetFXspW7.050727-4900) Modules
| |||||||||||||||
| 940 | findstr /i VIRTUAL_MACHINE_ACTIVATION | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 944 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=2256 --on-initialized-event-handle=324 --parent-handle=328 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
5 523
Read events
4 456
Write events
1 061
Delete events
6
Modification events
| (PID) Process: | (944) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 2644-13242072004233625 |
Value: 259 | |||
| (PID) Process: | (2644) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2644) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2644) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (2644) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (2644) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2644) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (2644) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (2644) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 2832-13239195546717773 |
Value: 0 | |||
| (PID) Process: | (2644) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
Executable files
6
Suspicious files
77
Text files
104
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2644 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\129de084-3d41-44ef-839c-6cc92f070f9e.tmp | — | |
MD5:— | SHA256:— | |||
| 2644 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000032.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2644 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2644 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2644 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2644 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old~RFdbd26.TMP | text | |
MD5:— | SHA256:— | |||
| 2644 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Feature Engagement Tracker\EventDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2644 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2644 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old~RFdbf1a.TMP | — | |
MD5:— | SHA256:— | |||
| 2644 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
22
DNS requests
22
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2536 | chrome.exe | 172.217.23.131:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2536 | chrome.exe | 140.82.118.3:443 | github.com | — | US | malicious |
2536 | chrome.exe | 185.199.109.154:443 | github.githubassets.com | GitHub, Inc. | NL | suspicious |
2536 | chrome.exe | 172.217.16.141:443 | accounts.google.com | Google Inc. | US | suspicious |
2536 | chrome.exe | 151.101.0.133:443 | avatars1.githubusercontent.com | Fastly | US | malicious |
2536 | chrome.exe | 172.217.16.164:443 | www.google.com | Google Inc. | US | whitelisted |
2536 | chrome.exe | 172.217.22.110:443 | clients2.google.com | Google Inc. | US | whitelisted |
2536 | chrome.exe | 216.58.212.163:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
— | — | 172.217.22.110:443 | clients2.google.com | Google Inc. | US | whitelisted |
2536 | chrome.exe | 216.58.212.174:443 | clients1.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
github.com |
| malicious |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
github.githubassets.com |
| whitelisted |
safebrowsing.googleapis.com |
| whitelisted |
avatars1.githubusercontent.com |
| whitelisted |
avatars0.githubusercontent.com |
| whitelisted |
avatars2.githubusercontent.com |
| whitelisted |
avatars3.githubusercontent.com |
| whitelisted |
github-cloud.s3.amazonaws.com |
| shared |
Threats
Process | Message |
|---|---|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|