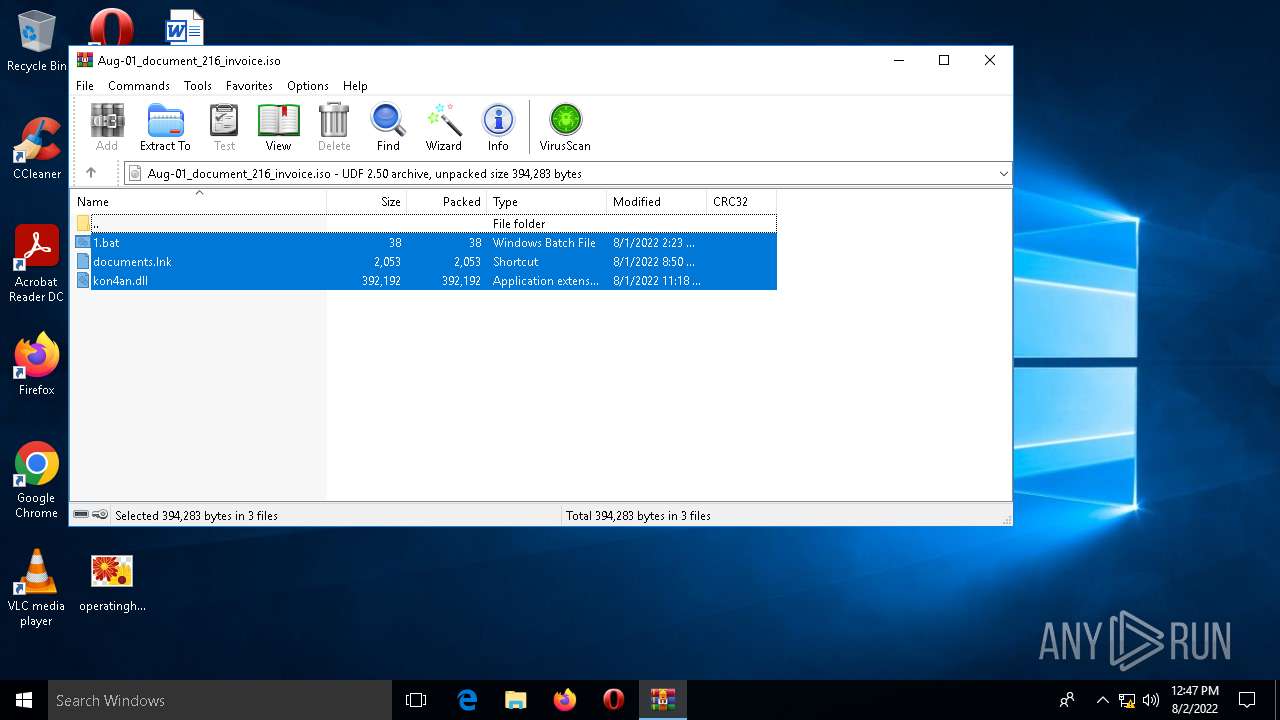
| File name: | Aug-01_document_216_invoice.iso |
| Full analysis: | https://app.any.run/tasks/d940462c-5f2b-42d9-855f-6be912d4b3b7 |
| Verdict: | Malicious activity |
| Threats: | IcedID is a banking trojan-type malware which allows attackers to utilize it to steal banking credentials of the victims. IcedID aka BokBot mainly targets businesses and steals payment information, it also acts as a loader and can deliver another viruses or download additional modules. |
| Analysis date: | August 02, 2022, 12:47:08 |
| OS: | Windows 10 Professional (build: 16299, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/octet-stream |
| File info: | data |
| MD5: | EC615F811768887D52D3B3BE15833A4F |
| SHA1: | EB52588FC49FFB9542F5D61A883D8FF213926C65 |
| SHA256: | A166838747E0D344F1C774AFB255E55E8CEF10DF860422ABD26CA69FC3F28704 |
| SSDEEP: | 12288:GecD+XL6rAT+eFlOnO9dwn3l8iAi8UQIiuRFn3:GLD/rm+1WGnSi8UQJK3 |
MALICIOUS
Drops executable file immediately after starts
- WinRAR.exe (PID: 6116)
ICEDID was detected
- rundll32.exe (PID: 2728)
Loads dropped or rewritten executable
- rundll32.exe (PID: 2728)
ICEDID detected by memory dumps
- rundll32.exe (PID: 2728)
SUSPICIOUS
Checks supported languages
- WinRAR.exe (PID: 6116)
- conhost.exe (PID: 3720)
- cmd.exe (PID: 3804)
- conhost.exe (PID: 5896)
- cmd.exe (PID: 2124)
Reads the computer name
- WinRAR.exe (PID: 6116)
- conhost.exe (PID: 3720)
- conhost.exe (PID: 5896)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 6116)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6116)
Application launched itself
- cmd.exe (PID: 3804)
INFO
Reads the computer name
- Explorer.exe (PID: 5972)
- rundll32.exe (PID: 2728)
Checks supported languages
- Explorer.exe (PID: 5972)
- rundll32.exe (PID: 2728)
Manual execution by user
- WinRAR.exe (PID: 6116)
- cmd.exe (PID: 3804)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
IcedId
(PID) Process(2728) rundll32.exe
Campaign ID380031663
C2sortswiminboard.com
TRiD
| .atn | | | Photoshop Action (37.5) |
|---|---|---|
| .gmc | | | Game Music Creator Music (8.4) |
| .abr | | | Adobe PhotoShop Brush (7.5) |
Total processes
94
Monitored processes
7
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2124 | C:\WINDOWS\system32\cmd.exe /K 1.bat | C:\WINDOWS\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2728 | RunDll32 kon4an.dll, PluginInit | C:\WINDOWS\system32\rundll32.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
IcedId(PID) Process(2728) rundll32.exe Campaign ID380031663 C2sortswiminboard.com | |||||||||||||||
| 3720 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | \??\C:\WINDOWS\system32\conhost.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3804 | "C:\Windows\System32\cmd.exe" /C start 1.bat | C:\Windows\System32\cmd.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5896 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | \??\C:\WINDOWS\system32\conhost.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 5972 | "C:\WINDOWS\Explorer.exe" | C:\WINDOWS\Explorer.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6116 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Aug-01_document_216_invoice.iso" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
Total events
8 294
Read events
8 262
Write events
32
Delete events
0
Modification events
| (PID) Process: | (6116) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6116) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6116) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\64\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (6116) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\SpybotAntiBeaconPortable-safer-networking.org_3.7.0.paf.zip | |||
| (PID) Process: | (6116) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\MicrosoftEdgePolicyTemplates.cab | |||
| (PID) Process: | (6116) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\MicrosoftEdgePolicyTemplates.zip | |||
| (PID) Process: | (6116) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Aug-01_document_216_invoice.iso | |||
| (PID) Process: | (6116) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6116) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6116) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
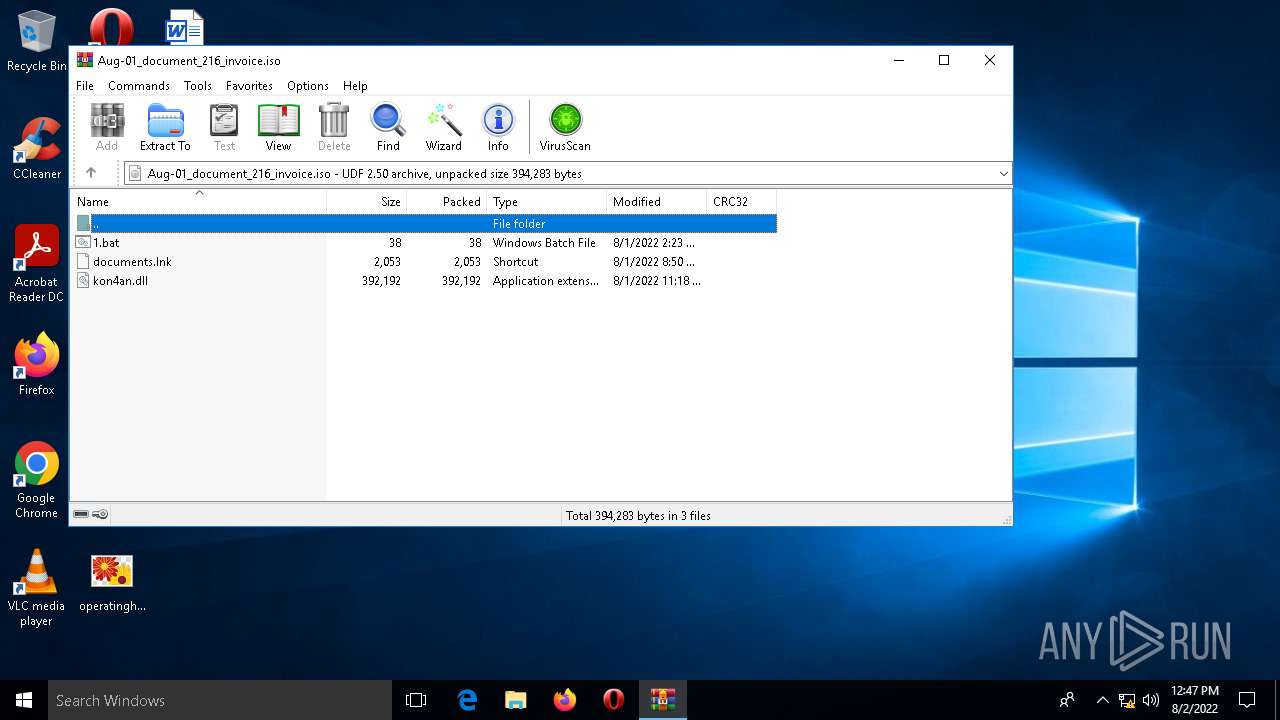
Executable files
1
Suspicious files
0
Text files
1
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6116 | WinRAR.exe | C:\Users\admin\Desktop\documents.lnk | lnk | |
MD5:890E24B463F18B1D0B3768AB9F591C56 | SHA256:2F9A1948F05E7089217FA9A2F4B6E9AD937FF23F503A68994CB0481F21699DFF | |||
| 6116 | WinRAR.exe | C:\Users\admin\Desktop\1.bat | text | |
MD5:1F434861EA0659593C3E437DCB19A0BC | SHA256:0C95DE224223005498384A3DD58FA34F6DFB27F3F28CF0C6F296262C33B66797 | |||
| 6116 | WinRAR.exe | C:\Users\admin\Desktop\kon4an.dll | executable | |
MD5:09A9F7A32210C90E1FA37012DE92EB3B | SHA256:9BECE7F8D5FEABA8AE050D5126AC81600A1767809382263B7E1C370D1A448195 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
4
DNS requests
2
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2728 | rundll32.exe | GET | — | 157.245.211.193:80 | http://sortswiminboard.com/ | US | — | — | malicious |
5556 | sihclient.exe | GET | 200 | 2.18.233.62:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Secure%20Server%20CA%202.1.crl | unknown | der | 821 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5556 | sihclient.exe | 2.18.233.62:80 | www.microsoft.com | Akamai International B.V. | — | whitelisted |
2728 | rundll32.exe | 157.245.211.193:80 | sortswiminboard.com | — | US | malicious |
5556 | sihclient.exe | 23.216.77.6:80 | — | NTT DOCOMO, INC. | US | whitelisted |
— | — | 23.216.77.28:80 | — | NTT DOCOMO, INC. | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.microsoft.com |
| whitelisted |
sortswiminboard.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2728 | rundll32.exe | A Network Trojan was detected | ET TROJAN Win32/IcedID Request Cookie |
Process | Message |
|---|---|
conhost.exe | InitSideBySide failed create an activation context. Error: 1814 |
conhost.exe | InitSideBySide failed create an activation context. Error: 1814 |