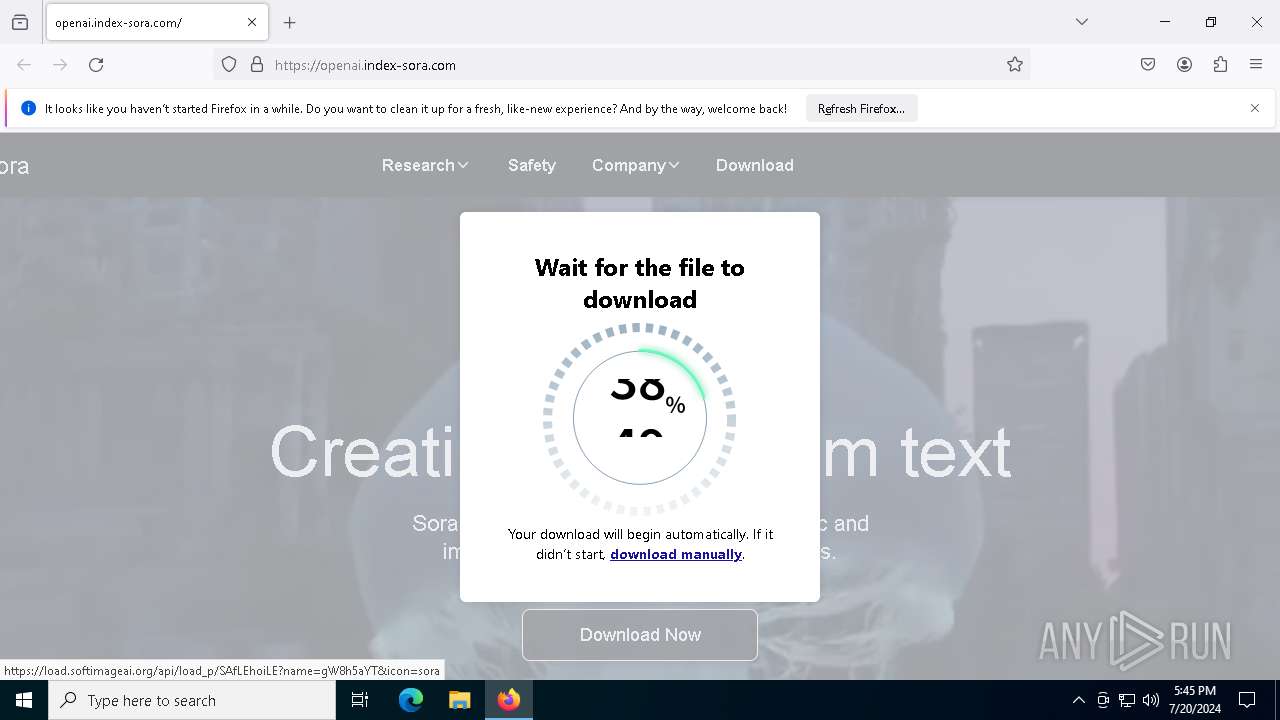
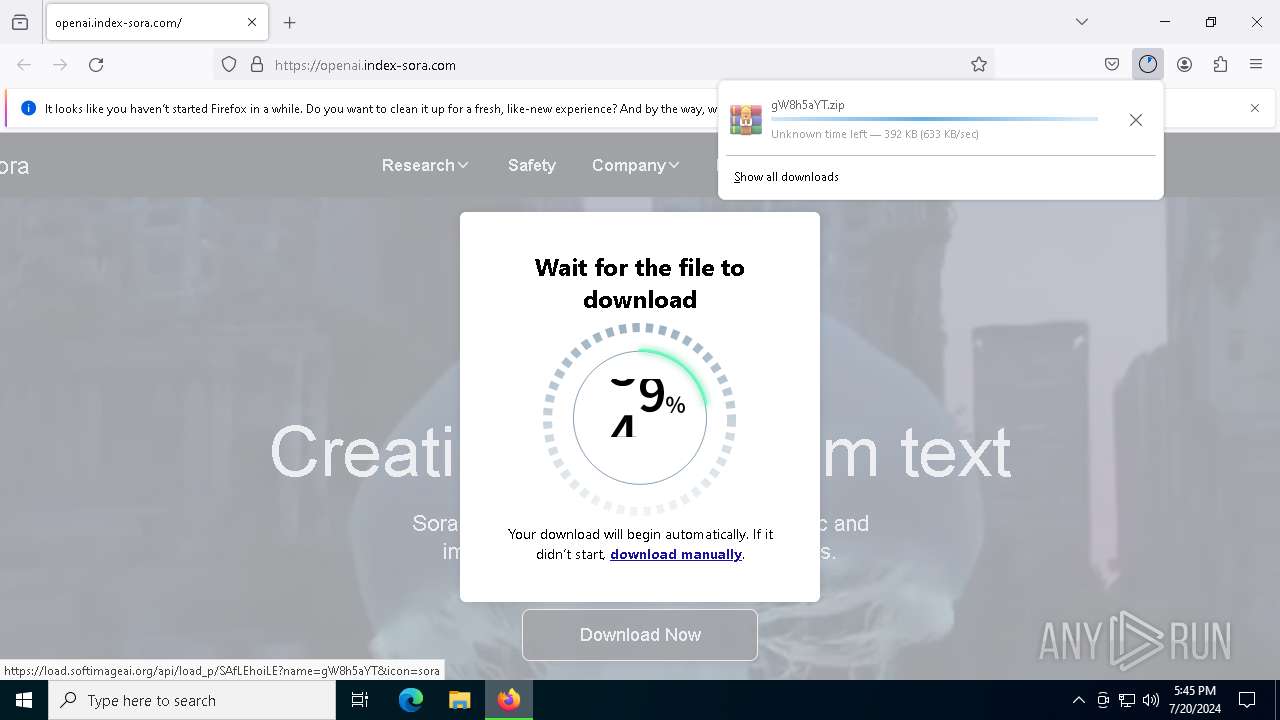
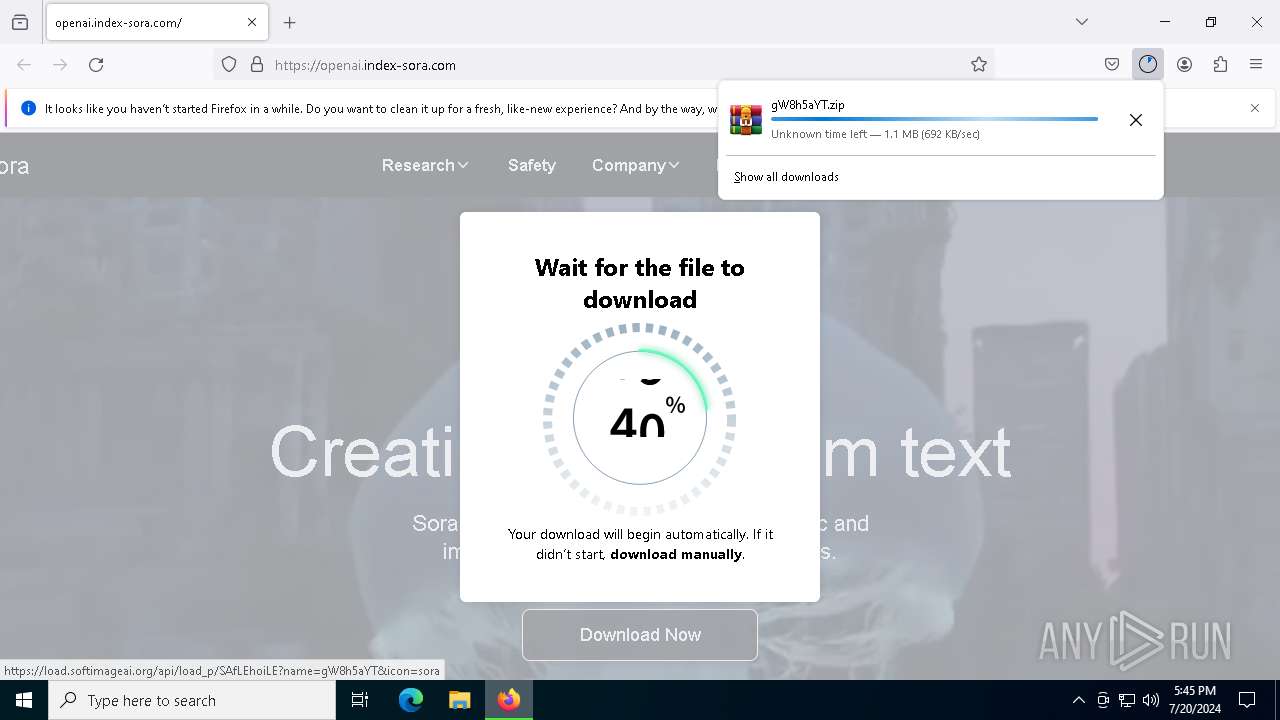
| URL: | https://openai.index-sora.com |
| Full analysis: | https://app.any.run/tasks/fd35a22b-9b08-475c-add8-581b9ee68ce5 |
| Verdict: | Malicious activity |
| Analysis date: | July 20, 2024, 17:44:52 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MD5: | D5DA44DA34E86624FF44191590BC118F |
| SHA1: | F57AB762A11E5FACFDEAD4678261170B0432C2C7 |
| SHA256: | A15F8A4726D3F7A7CFBEEB80B6D6CF8E0CAF796BDA03A29E5784A8E02AB20EBD |
| SSDEEP: | 3:N8cuEKaDiGT:2cuRaDiK |
MALICIOUS
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 796)
- cmd.exe (PID: 4896)
Bypass execution policy to execute commands
- powershell.exe (PID: 7444)
- powershell.exe (PID: 6028)
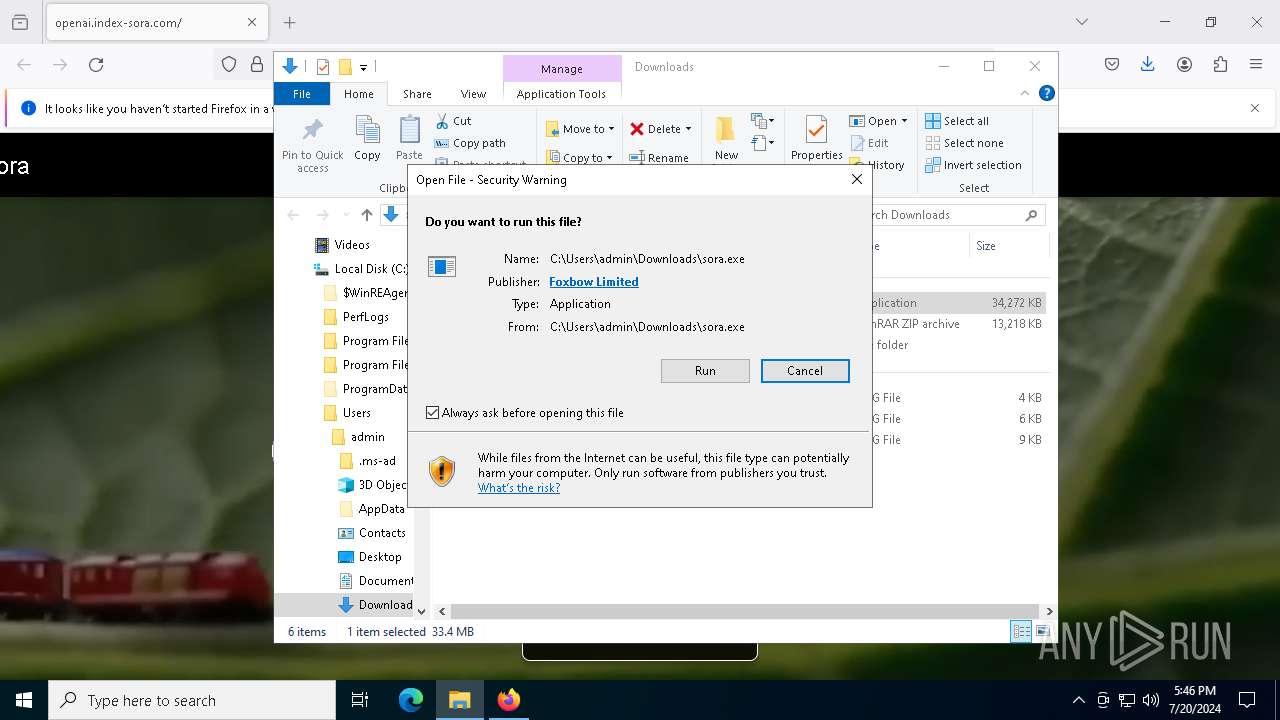
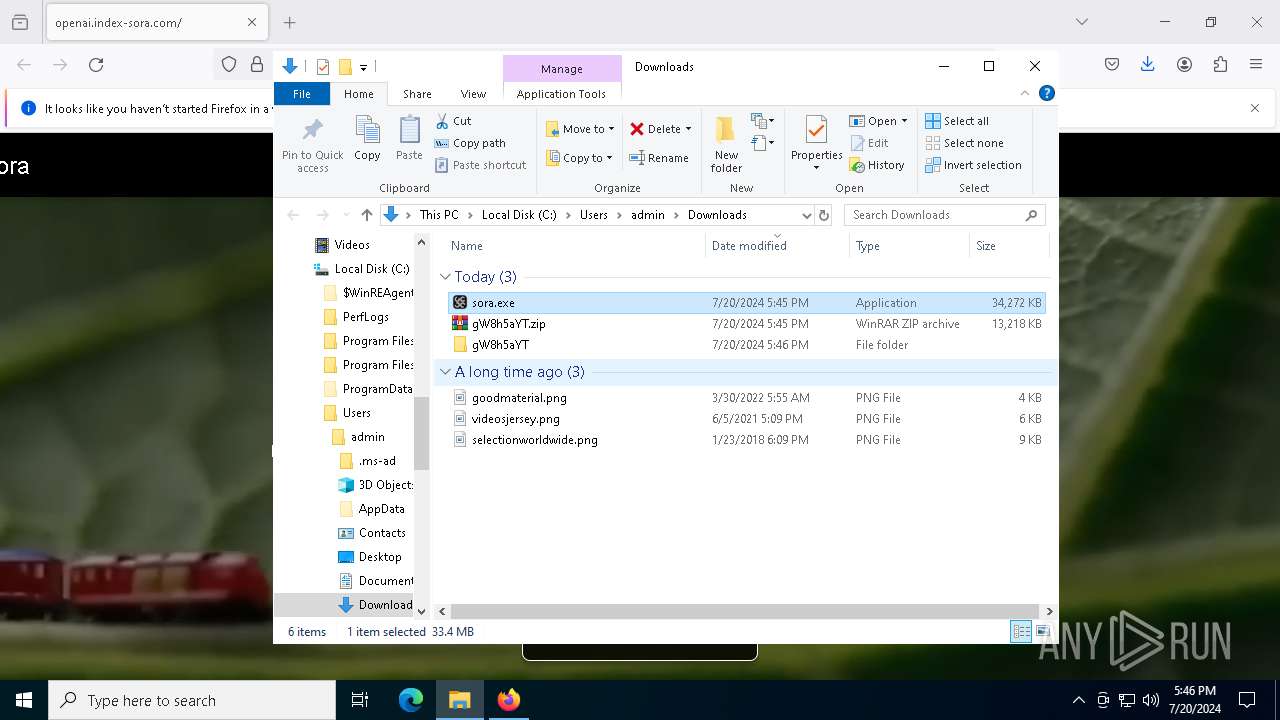
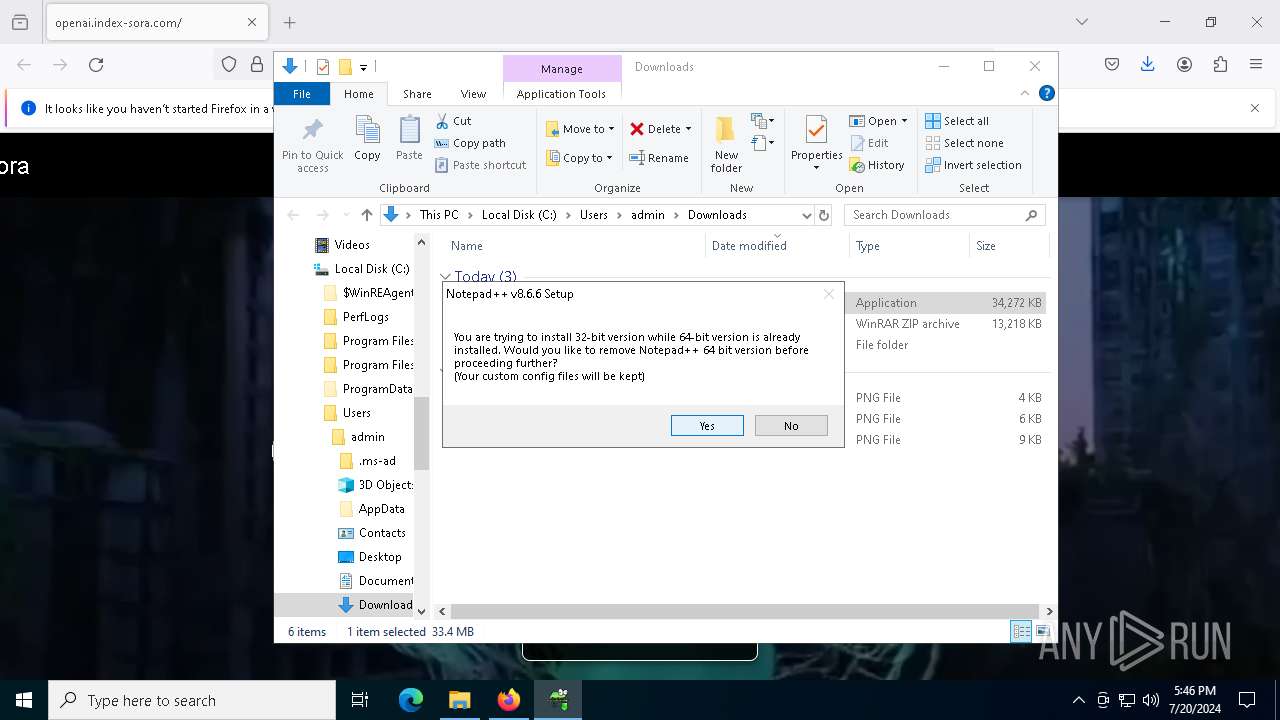
Drops the executable file immediately after the start
- sora.exe (PID: 7816)
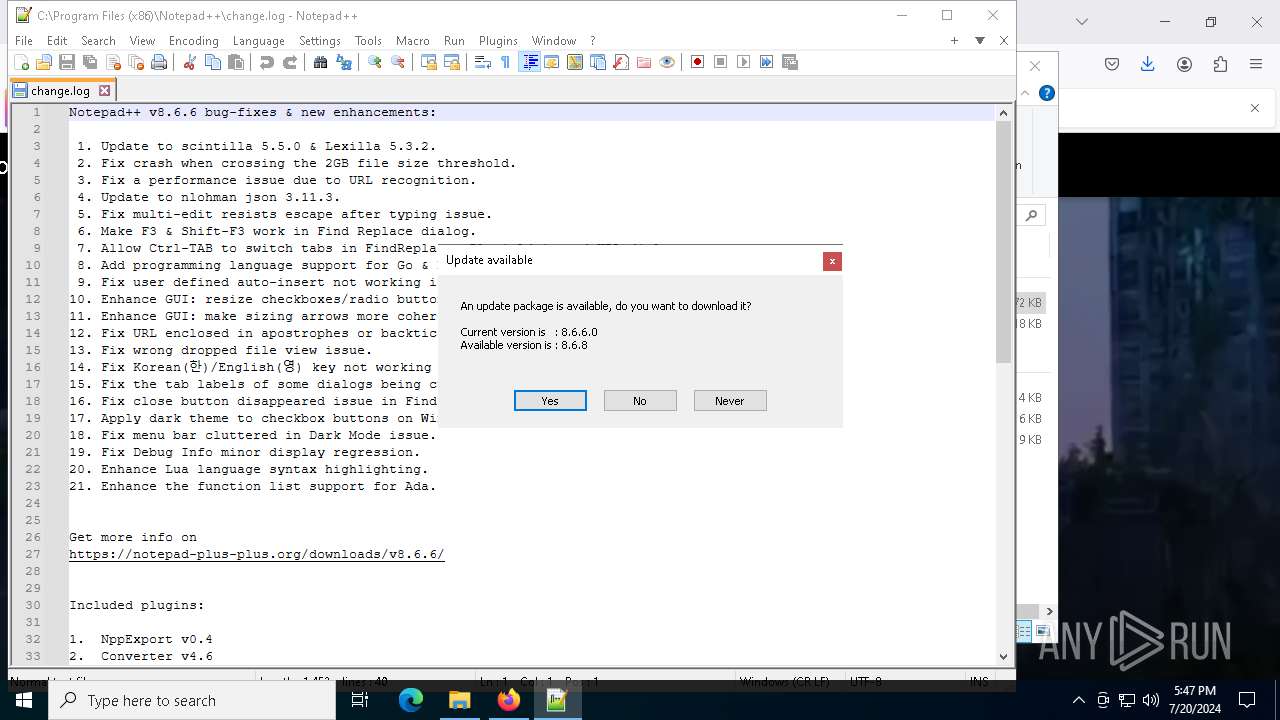
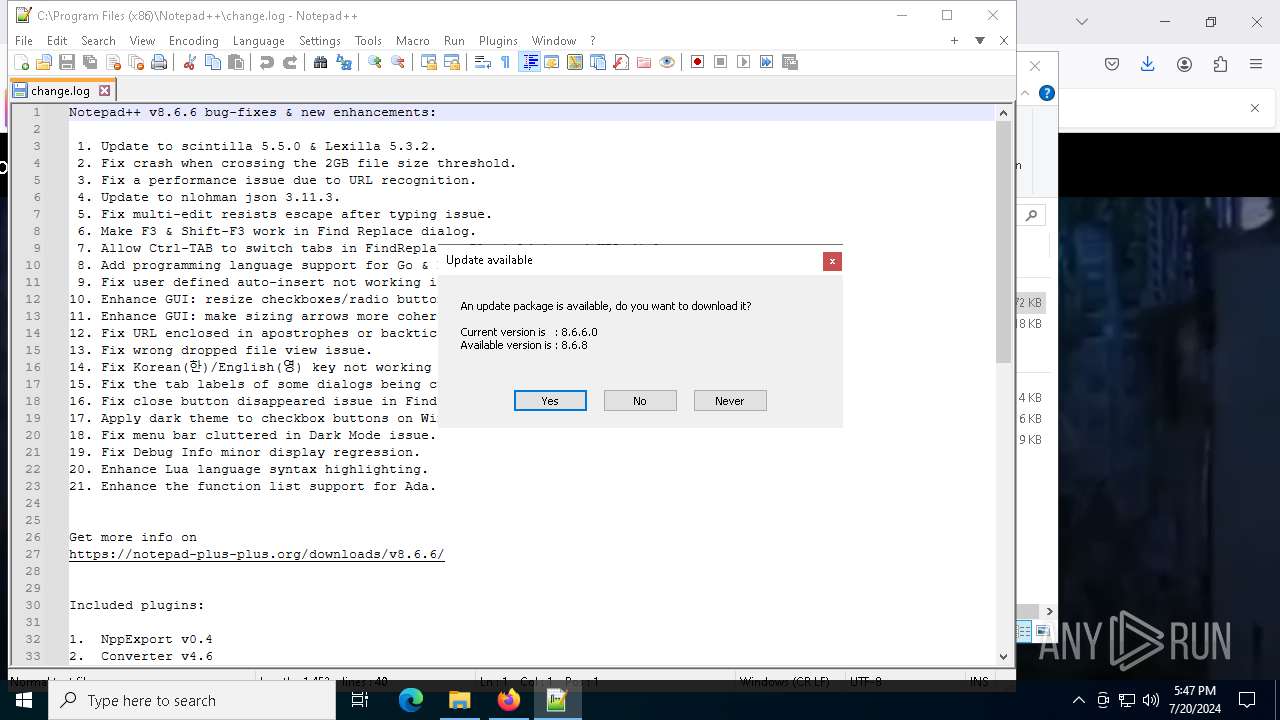
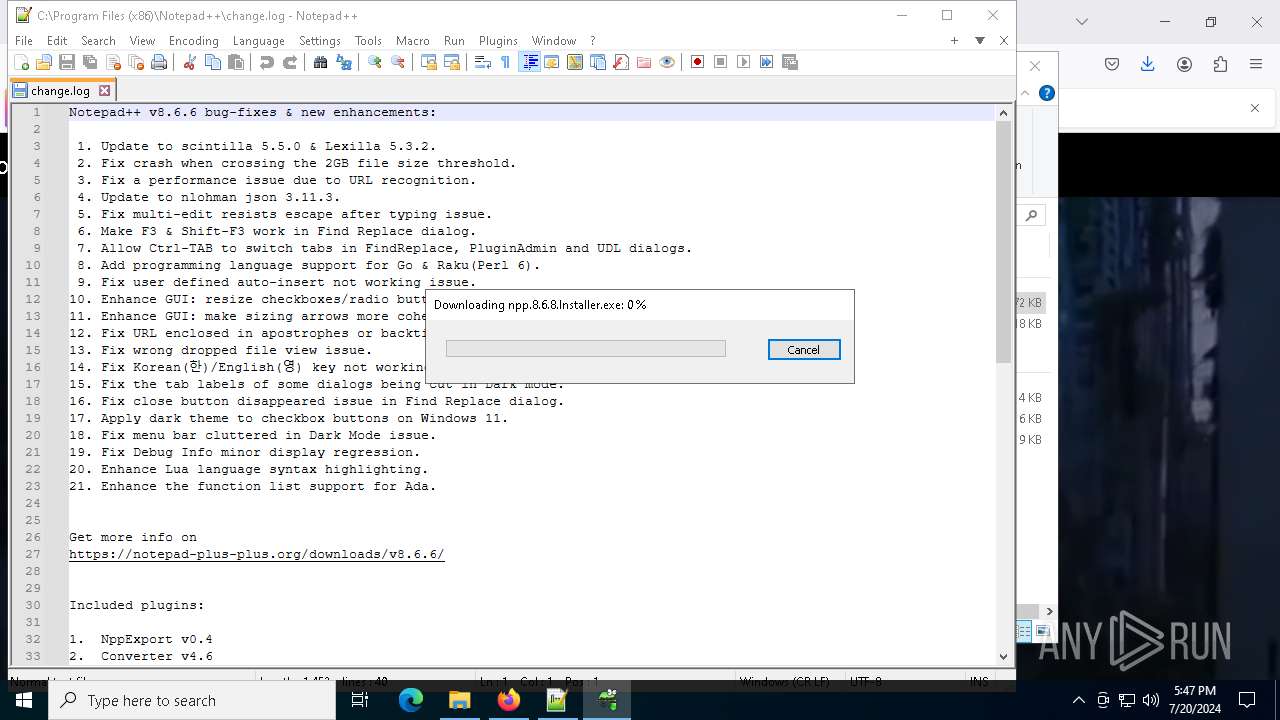
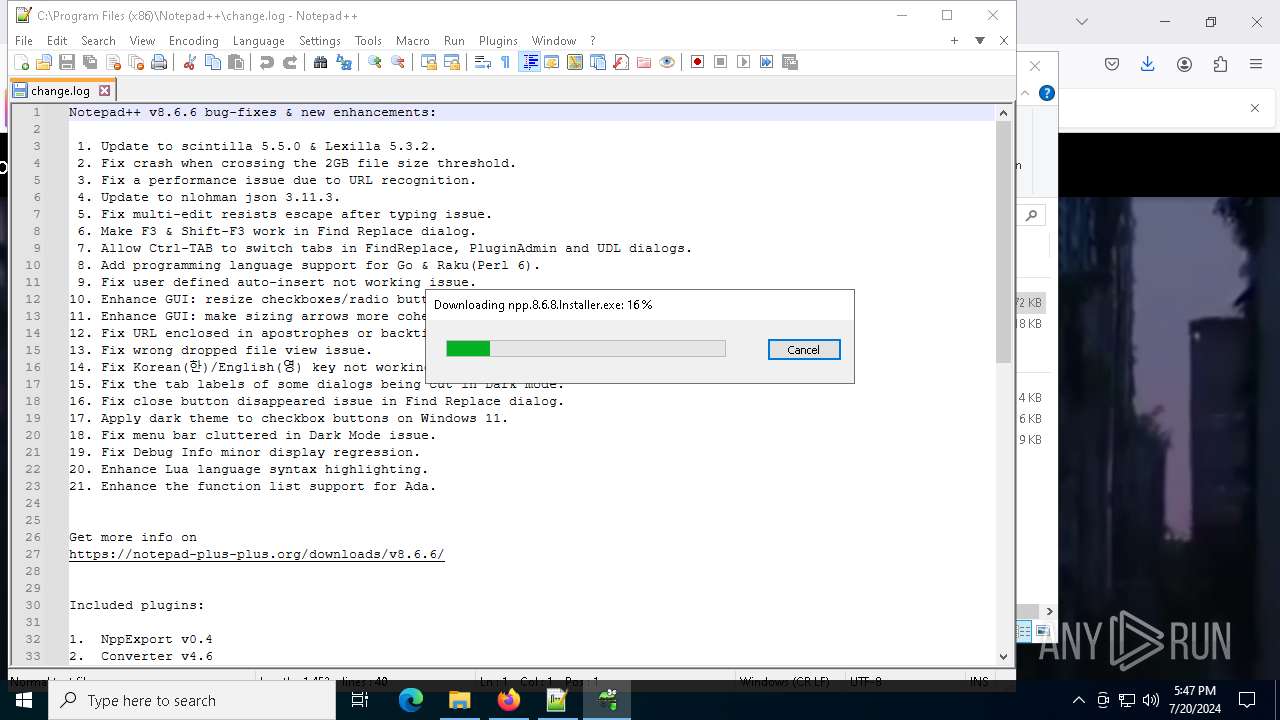
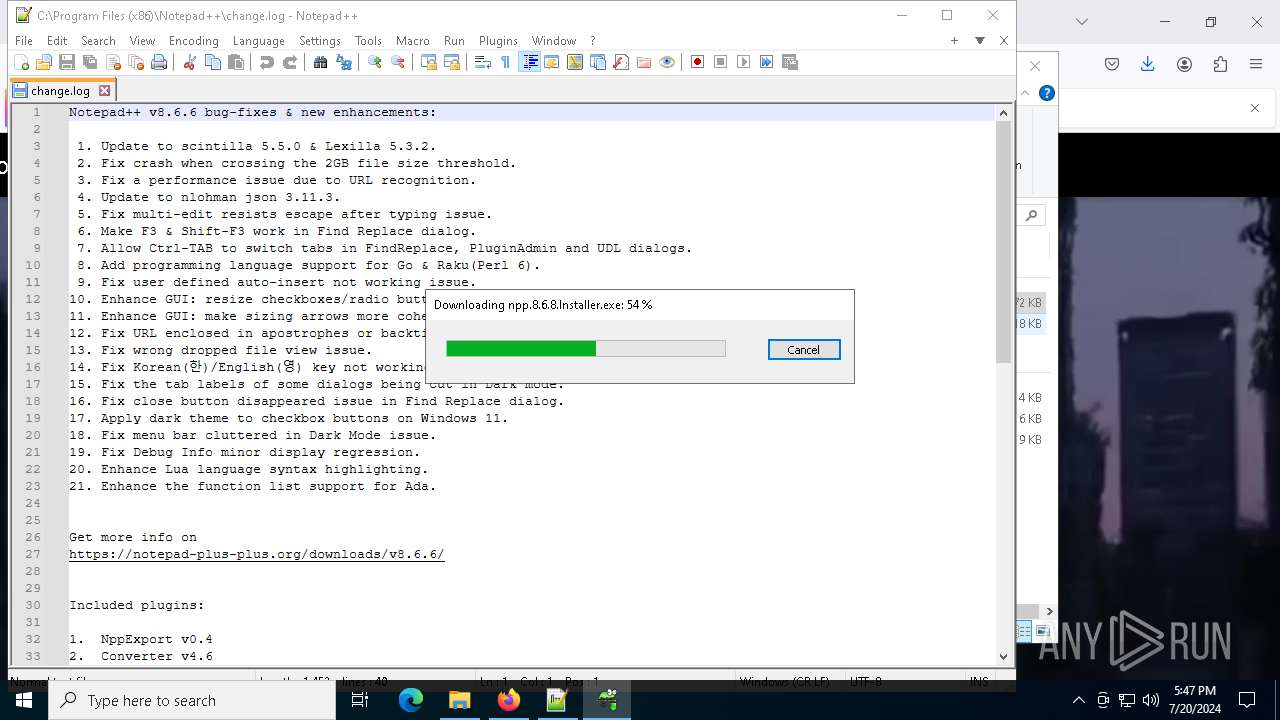
- npp.8.6.6.Installer.exe (PID: 6920)
- GUP.exe (PID: 6204)
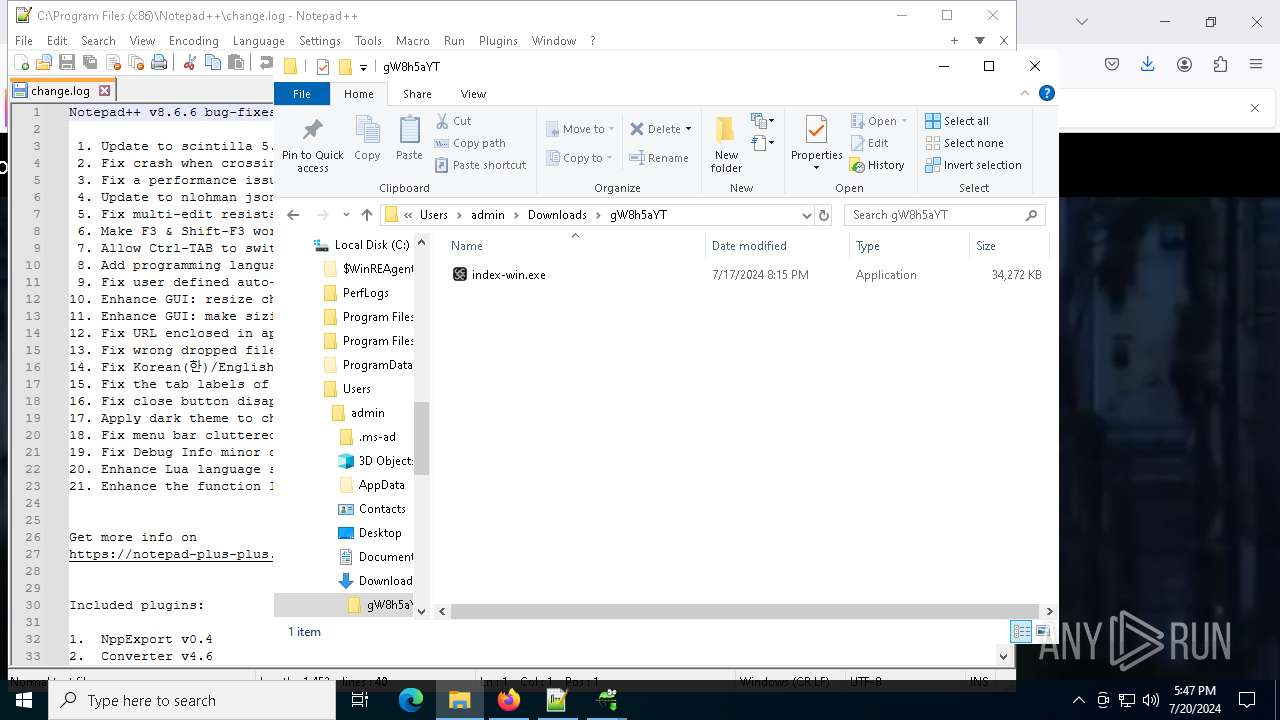
- index-win.exe (PID: 5124)
- npp.8.6.6.Installer.exe (PID: 4928)
Registers / Runs the DLL via REGSVR32.EXE
- npp.8.6.6.Installer.exe (PID: 6920)
SUSPICIOUS
Creates file in the systems drive root
- explorer.exe (PID: 4016)
Starts CMD.EXE for commands execution
- sora.exe (PID: 7816)
- index-win.exe (PID: 5124)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 796)
- cmd.exe (PID: 4896)
Executable content was dropped or overwritten
- sora.exe (PID: 7816)
- npp.8.6.6.Installer.exe (PID: 6920)
- GUP.exe (PID: 6204)
- index-win.exe (PID: 5124)
- npp.8.6.6.Installer.exe (PID: 4928)
The process executes Powershell scripts
- cmd.exe (PID: 796)
- cmd.exe (PID: 4896)
Malware-specific behavior (creating "System.dll" in Temp)
- npp.8.6.6.Installer.exe (PID: 6920)
- npp.8.6.6.Installer.exe (PID: 4928)
Creates/Modifies COM task schedule object
- regsvr32.exe (PID: 7564)
The process creates files with name similar to system file names
- npp.8.6.6.Installer.exe (PID: 6920)
- npp.8.6.6.Installer.exe (PID: 4928)
Explorer used for Indirect Command Execution
- explorer.exe (PID: 6560)
Reads security settings of Internet Explorer
- notepad++.exe (PID: 7628)
Reads the date of Windows installation
- notepad++.exe (PID: 7628)
Creates a software uninstall entry
- npp.8.6.6.Installer.exe (PID: 6920)
Searches for installed software
- npp.8.6.6.Installer.exe (PID: 4928)
INFO
The process uses the downloaded file
- explorer.exe (PID: 4016)
- WinRAR.exe (PID: 6560)
Reads security settings of Internet Explorer
- explorer.exe (PID: 4016)
Reads Microsoft Office registry keys
- explorer.exe (PID: 4016)
Checks proxy server information
- explorer.exe (PID: 4016)
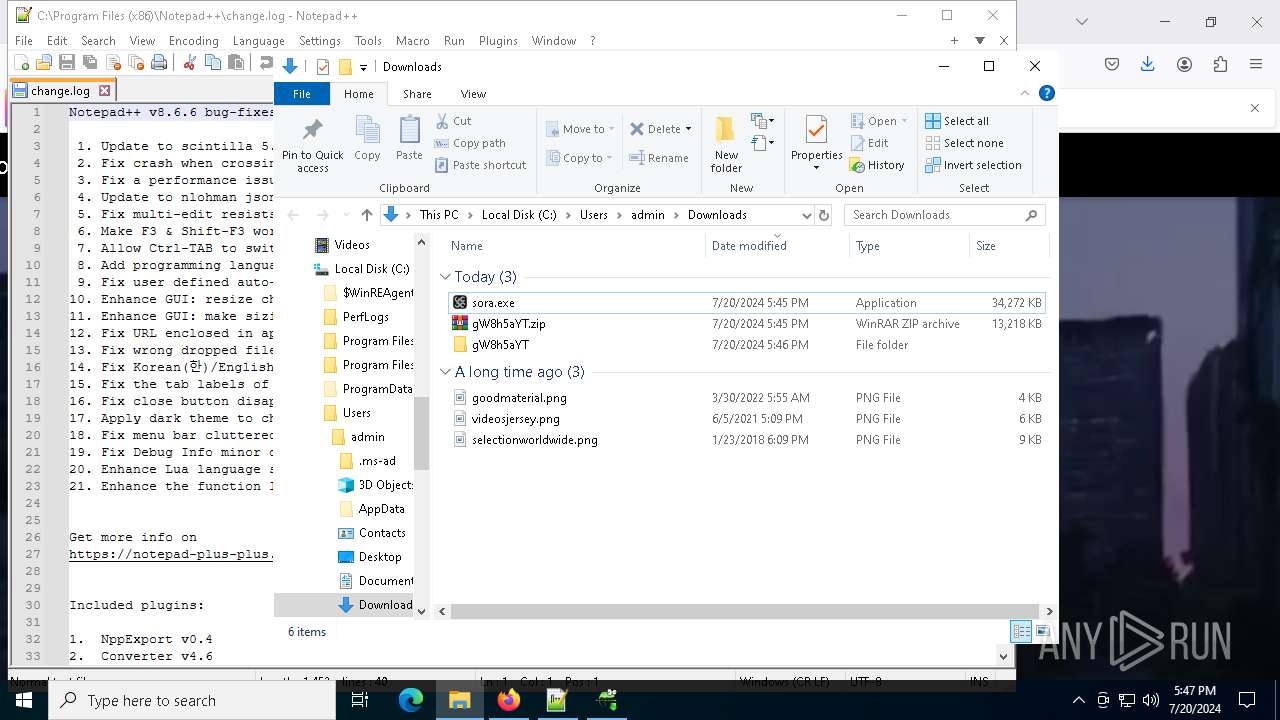
Creates files or folders in the user directory
- explorer.exe (PID: 4016)
- npp.8.6.6.Installer.exe (PID: 6920)
- sora.exe (PID: 7816)
- notepad++.exe (PID: 7628)
- index-win.exe (PID: 5124)
Reads the software policy settings
- explorer.exe (PID: 4016)
Checks supported languages
- sora.exe (PID: 7816)
- npp.8.6.6.Installer.exe (PID: 6920)
- GUP.exe (PID: 6204)
- notepad++.exe (PID: 7876)
- index-win.exe (PID: 5124)
- npp.8.6.6.Installer.exe (PID: 4928)
- notepad++.exe (PID: 7628)
Reads Environment values
- sora.exe (PID: 7816)
- npp.8.6.6.Installer.exe (PID: 6920)
- index-win.exe (PID: 5124)
- npp.8.6.6.Installer.exe (PID: 4928)
Process checks computer location settings
- sora.exe (PID: 7816)
- notepad++.exe (PID: 7628)
- index-win.exe (PID: 5124)
The executable file from the user directory is run by the Powershell process
- npp.8.6.6.Installer.exe (PID: 3108)
- npp.8.6.6.Installer.exe (PID: 6920)
- npp.8.6.6.Installer.exe (PID: 4928)
- npp.8.6.6.Installer.exe (PID: 6604)
Reads the computer name
- npp.8.6.6.Installer.exe (PID: 6920)
- sora.exe (PID: 7816)
- GUP.exe (PID: 6204)
- notepad++.exe (PID: 7628)
- index-win.exe (PID: 5124)
- npp.8.6.6.Installer.exe (PID: 4928)
Dropped object may contain TOR URL's
- npp.8.6.6.Installer.exe (PID: 6920)
Creates files in the program directory
- npp.8.6.6.Installer.exe (PID: 6920)
Create files in a temporary directory
- npp.8.6.6.Installer.exe (PID: 6920)
- GUP.exe (PID: 6204)
- npp.8.6.6.Installer.exe (PID: 4928)
Reads product name
- sora.exe (PID: 7816)
- index-win.exe (PID: 5124)
Reads the machine GUID from the registry
- notepad++.exe (PID: 7628)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
179
Monitored processes
20
Malicious processes
7
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 796 | C:\WINDOWS\system32\cmd.exe /d /s /c "powershell.exe -ExecutionPolicy Bypass -Command "& { . 'C:\Users\admin\AppData\Local\vdyqy\lono.ps1'; ODW -path "C:\Users\admin\AppData\Local\uchlnzuwtz\vdyqy\npp.8.6.6.Installer.exe" }"" | C:\Windows\System32\cmd.exe | — | sora.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3108 | "C:\Users\admin\AppData\Local\uchlnzuwtz\vdyqy\npp.8.6.6.Installer.exe" | C:\Users\admin\AppData\Local\uchlnzuwtz\vdyqy\npp.8.6.6.Installer.exe | — | powershell.exe | |||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 3221226540 Version: 8.6.6.0 Modules
| |||||||||||||||
| 4016 | C:\WINDOWS\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4076 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4896 | C:\WINDOWS\system32\cmd.exe /d /s /c "powershell.exe -ExecutionPolicy Bypass -Command "& { . 'C:\Users\admin\AppData\Local\ehlmm\gkky.ps1'; ODW -path "C:\Users\admin\AppData\Local\hjdwbxutnc\ehlmm\npp.8.6.6.Installer.exe" }"" | C:\Windows\System32\cmd.exe | — | index-win.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4928 | "C:\Users\admin\AppData\Local\hjdwbxutnc\ehlmm\npp.8.6.6.Installer.exe" | C:\Users\admin\AppData\Local\hjdwbxutnc\ehlmm\npp.8.6.6.Installer.exe | powershell.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: HIGH Description: Notepad++ : a free (GNU) source code editor Exit code: 1 Version: 8.6.6.0 Modules
| |||||||||||||||
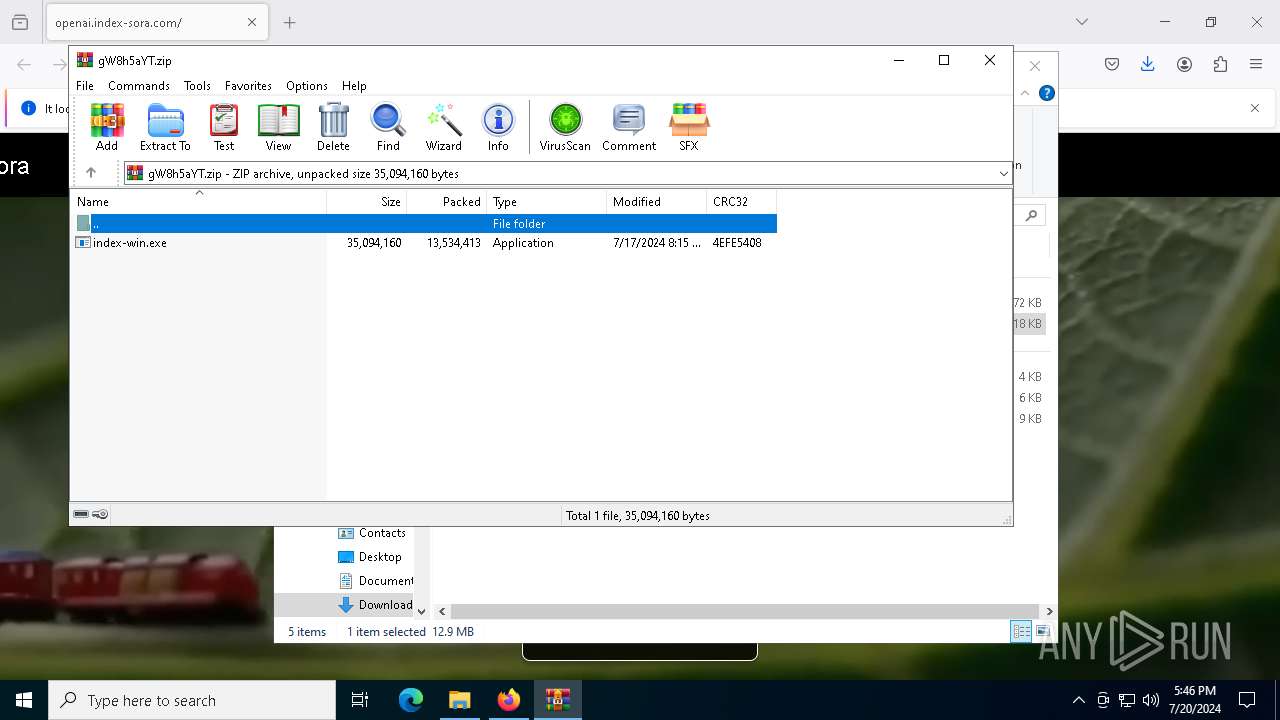
| 5124 | "C:\Users\admin\Downloads\gW8h5aYT\index-win.exe" | C:\Users\admin\Downloads\gW8h5aYT\index-win.exe | explorer.exe | ||||||||||||
User: admin Company: Node.js Integrity Level: MEDIUM Description: Sora creating video from text Exit code: 0 Version: 1.1.2.0 Modules
| |||||||||||||||
| 5772 | regsvr32 /s "C:\Program Files (x86)\Notepad++\contextMenu\NppShell.dll" | C:\Windows\SysWOW64\regsvr32.exe | — | npp.8.6.6.Installer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6028 | powershell.exe -ExecutionPolicy Bypass -Command "& { . 'C:\Users\admin\AppData\Local\ehlmm\gkky.ps1'; ODW -path "C:\Users\admin\AppData\Local\hjdwbxutnc\ehlmm\npp.8.6.6.Installer.exe" }" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6204 | "C:\Program Files (x86)\Notepad++\updater\gup.exe" -v8.66 | C:\Program Files (x86)\Notepad++\updater\GUP.exe | notepad++.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: WinGup for Notepad++ Version: 5.28 Modules
| |||||||||||||||
Total events
56 955
Read events
56 582
Write events
361
Delete events
12
Modification events
| (PID) Process: | (4016) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 0202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (4016) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 04000000000000000E000000030000000C0000000D0000000B000000050000000A000000090000000800000001000000070000000600000002000000FFFFFFFF | |||
| (PID) Process: | (4016) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\4\0\4\0 |
| Operation: | write | Name: | MRUListEx |
Value: 0100000000000000FFFFFFFF | |||
| (PID) Process: | (4016) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Toolbar |
| Operation: | write | Name: | Locked |
Value: 1 | |||
| (PID) Process: | (4016) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Ribbon |
| Operation: | write | Name: | MinimizedStateTabletModeOff |
Value: 0 | |||
| (PID) Process: | (4016) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Ribbon |
| Operation: | write | Name: | QatItems |
Value: 3C7369713A637573746F6D554920786D6C6E733A7369713D22687474703A2F2F736368656D61732E6D6963726F736F66742E636F6D2F77696E646F77732F323030392F726962626F6E2F716174223E3C7369713A726962626F6E206D696E696D697A65643D2266616C7365223E3C7369713A71617420706F736974696F6E3D2230223E3C7369713A736861726564436F6E74726F6C733E3C7369713A636F6E74726F6C206964513D227369713A3136313238222076697369626C653D2266616C73652220617267756D656E743D223022202F3E3C7369713A636F6E74726F6C206964513D227369713A3136313239222076697369626C653D2266616C73652220617267756D656E743D223022202F3E3C7369713A636F6E74726F6C206964513D227369713A3132333532222076697369626C653D2266616C73652220617267756D656E743D223022202F3E3C7369713A636F6E74726F6C206964513D227369713A3132333834222076697369626C653D22747275652220617267756D656E743D223022202F3E3C7369713A636F6E74726F6C206964513D227369713A3132333336222076697369626C653D22747275652220617267756D656E743D223022202F3E3C7369713A636F6E74726F6C206964513D227369713A3132333537222076697369626C653D2266616C73652220617267756D656E743D223022202F3E3C2F7369713A736861726564436F6E74726F6C733E3C2F7369713A7161743E3C2F7369713A726962626F6E3E3C2F7369713A637573746F6D55493E | |||
| (PID) Process: | (4016) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Toolbar\ShellBrowser |
| Operation: | write | Name: | ITBar7Layout |
Value: 13000000000000000000000020000000100000000000000001000000010700005E01000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4016) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\208\Shell |
| Operation: | write | Name: | SniffedFolderType |
Value: Downloads | |||
| (PID) Process: | (4016) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\208\Shell |
| Operation: | write | Name: | SniffedFolderType |
Value: Pictures | |||
| (PID) Process: | (4016) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\2\ApplicationViewManagement\W32:00000000000503C6 |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456A1F1CCF85B06E3419214046A96D63B00 | |||
Executable files
21
Suspicious files
13
Text files
233
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
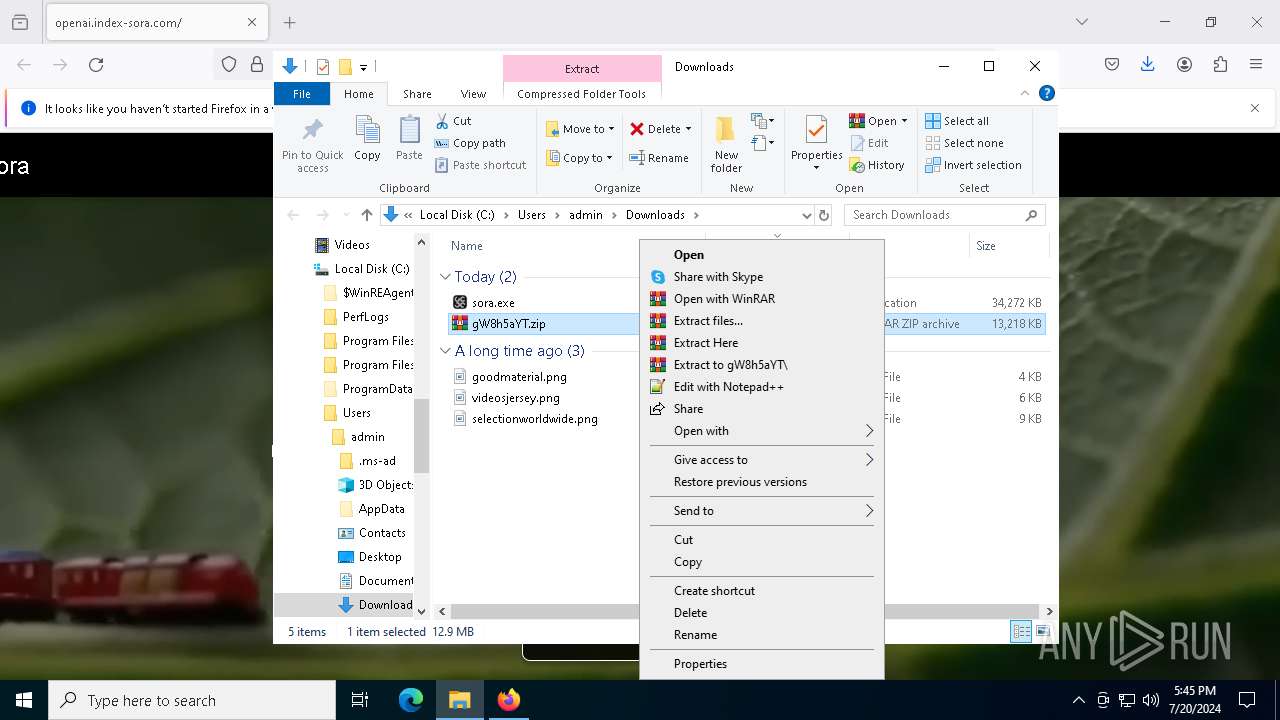
| 6560 | WinRAR.exe | C:\Users\admin\Downloads\gW8h5aYT\index-win.exe | — | |
MD5:— | SHA256:— | |||
| 7816 | sora.exe | C:\Users\admin\AppData\Local\uchlnzuwtz\vdyqy\npp.8.6.6.Installer.exe | executable | |
MD5:48563A2720422C9ACA0B0071C2947234 | SHA256:732574CD602BEB41C5BC74DA6D660B3CE0FE53DEED400E7D712073479129C99C | |||
| 7444 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_hkllayab.ene.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7444 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:26648D93878F068446A4175CF384AA22 | SHA256:617D287D93B103A7A76E2862A4833C2929CDA3D304879FB0B7A76784CBEA57BD | |||
| 4016 | explorer.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\248DDD9FCF61002E219645695E3FFC98_A760EAA2E953AFA35215FFF9ABFB1165 | binary | |
MD5:2EE81775C8E2B3A11C5C1BF55797A26F | SHA256:130B0796492BCFF548B9AFE27C61810DB2006B0BA54C367A4CF97F8C451EEAB2 | |||
| 7816 | sora.exe | C:\Users\admin\AppData\Local\vdyqy\lono.ps1 | text | |
MD5:EBCBA85EFC30CCEC90216D086749A4A1 | SHA256:A451FF841731F39F4BBDE60F25C2ABD8D3C8B2068A429CDBC59958BE679B9372 | |||
| 6920 | npp.8.6.6.Installer.exe | C:\Users\admin\AppData\Local\Temp\nsuF0C4.tmp\LangDLL.dll | executable | |
MD5:50016010FB0D8DB2BC4CD258CEB43BE5 | SHA256:32230128C18574C1E860DFE4B17FE0334F685740E27BC182E0D525A8948C9C2E | |||
| 6920 | npp.8.6.6.Installer.exe | C:\Users\admin\AppData\Local\Temp\nsuF0C4.tmp\modern-header.bmp | image | |
MD5:56DA15FDB8D96F8F5C649DCB5E79D775 | SHA256:BB90D4338D2474138473E6B16E94B0237EE847BEA45019ED0DD4439C71BD233E | |||
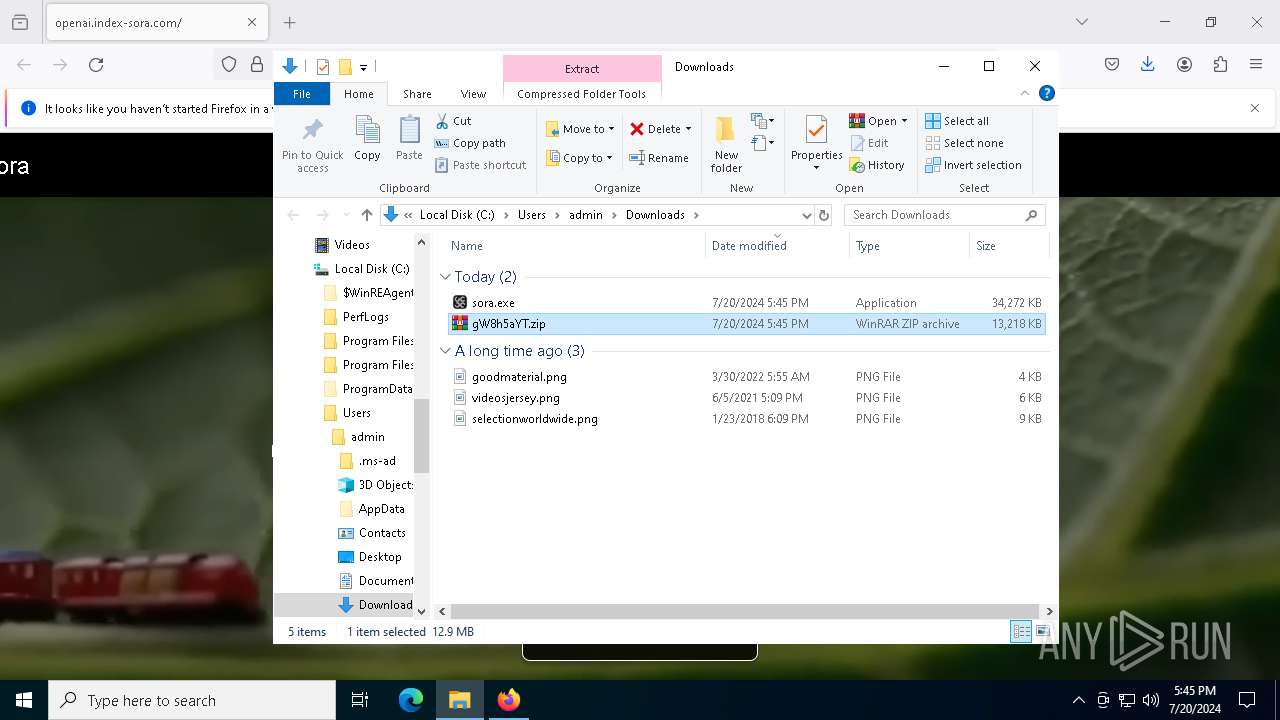
| 7816 | sora.exe | C:\Users\admin\AppData\Local\dtrc\olxgnw.zip | compressed | |
MD5:5BF4E16C2EB9AE256E65B16988D04301 | SHA256:9F8294C7E3FDE74834C1886AB57E54AE7BFC3DEF3544CB2A5635528D92EBA456 | |||
| 6920 | npp.8.6.6.Installer.exe | C:\Users\admin\AppData\Local\Temp\nsuF0C4.tmp\System.dll | executable | |
MD5:4ADD245D4BA34B04F213409BFE504C07 | SHA256:9111099EFE9D5C9B391DC132B2FAF0A3851A760D4106D5368E30AC744EB42706 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
37
TCP/UDP connections
121
DNS requests
162
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | POST | 200 | 142.250.184.227:80 | http://o.pki.goog/wr2 | unknown | — | — | unknown |
— | — | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
— | — | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
— | — | POST | 200 | 142.250.184.227:80 | http://o.pki.goog/wr2 | unknown | — | — | unknown |
— | — | POST | 200 | 95.101.54.99:80 | http://r10.o.lencr.org/ | unknown | — | — | unknown |
— | — | POST | 200 | 95.101.54.99:80 | http://r10.o.lencr.org/ | unknown | — | — | unknown |
— | — | POST | 200 | 142.250.184.227:80 | http://o.pki.goog/wr2 | unknown | — | — | unknown |
— | — | POST | 200 | 142.250.184.227:80 | http://o.pki.goog/wr2 | unknown | — | — | unknown |
— | — | POST | 200 | 95.101.54.203:80 | http://r11.o.lencr.org/ | unknown | — | — | unknown |
— | — | POST | 200 | 95.101.54.99:80 | http://r10.o.lencr.org/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.190.159.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 4.209.33.156:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
— | — | 172.67.133.33:443 | openai.index-sora.com | CLOUDFLARENET | US | unknown |
— | — | 34.117.188.166:443 | contile.services.mozilla.com | GOOGLE-CLOUD-PLATFORM | US | unknown |
— | — | 34.160.144.191:443 | content-signature-2.cdn.mozilla.net | GOOGLE | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
openai.index-sora.com |
| unknown |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
spocs.getpocket.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potential Corporate Privacy Violation | AV POLICY Observed TikTok Domain in TLS SNI (tiktok.com) |
2168 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
2116 | firefox.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 4 |
2168 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |