| File name: | Discord.exe |
| Full analysis: | https://app.any.run/tasks/f8bb208f-fa62-4bdc-9f94-a183a8d4bbc9 |
| Verdict: | Malicious activity |
| Analysis date: | June 10, 2025, 06:14:56 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | FB7768E45CA83C71E95E3C09DEA0F75F |
| SHA1: | E1DD823096A8AC931AF0B0ADC084BC251EC7CF87 |
| SHA256: | A1598314EA680183E6630630E06D6784173BBF32BD895EAF3882D585E22609CB |
| SSDEEP: | 98304:0wD4OP19ciFbzH4gAiKZyJ8K7SWIyKVJ3p3SAbLRuAfZS7ySdj+Fdc:9 |
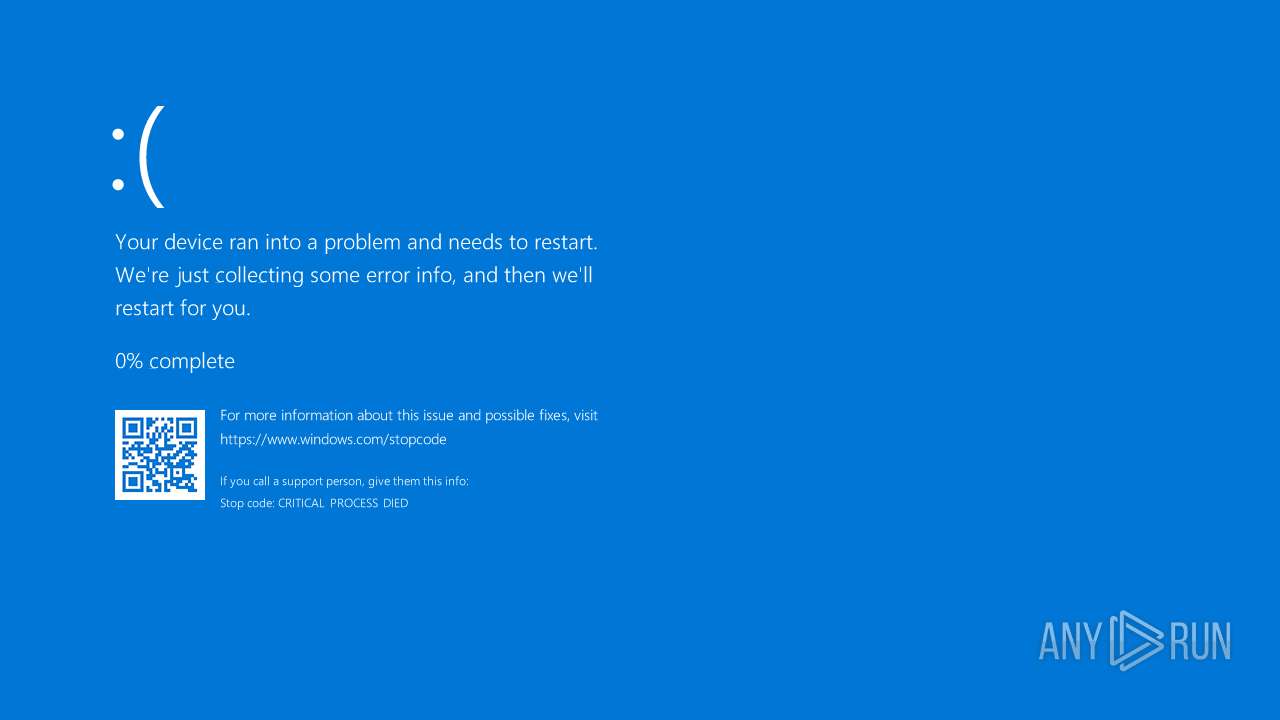
MALICIOUS
Bypass User Account Control (Modify registry)
- Discord.exe (PID: 5096)
Bypass User Account Control (fodhelper)
- fodhelper.exe (PID: 5228)
Execute application with conhost.exe as parent process
- cmd.exe (PID: 4404)
Uses Task Scheduler to autorun other applications
- Discord.exe (PID: 5568)
SUSPICIOUS
Reads the date of Windows installation
- Discord.exe (PID: 5096)
Reads security settings of Internet Explorer
- Discord.exe (PID: 5096)
Changes default file association
- Discord.exe (PID: 5096)
Executing commands from a ".bat" file
- conhost.exe (PID: 6700)
Starts CMD.EXE for commands execution
- conhost.exe (PID: 6700)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 4404)
The executable file from the user directory is run by the CMD process
- Discord.exe (PID: 5568)
Starts itself from another location
- Discord.exe (PID: 5568)
The process executes via Task Scheduler
- PLUGScheduler.exe (PID: 2968)
Executable content was dropped or overwritten
- Discord.exe (PID: 5568)
INFO
Reads Environment values
- Discord.exe (PID: 5096)
- Discord.exe (PID: 5568)
Reads the computer name
- Discord.exe (PID: 5096)
- Discord.exe (PID: 5568)
Reads the machine GUID from the registry
- Discord.exe (PID: 5096)
- Discord.exe (PID: 5568)
Create files in a temporary directory
- Discord.exe (PID: 5096)
Checks supported languages
- Discord.exe (PID: 5096)
- Discord.exe (PID: 5568)
Process checks computer location settings
- Discord.exe (PID: 5096)
Reads security settings of Internet Explorer
- fodhelper.exe (PID: 5228)
Manual execution by a user
- svchost.exe (PID: 4804)
- svchost.exe (PID: 5440)
- svchost.exe (PID: 6228)
- svchost.exe (PID: 5796)
- svchost.exe (PID: 6132)
- svchost.exe (PID: 2544)
- svchost.exe (PID: 3720)
- svchost.exe (PID: 1596)
- svchost.exe (PID: 6344)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (63.1) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (23.8) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.6) |
| .exe | | | Win32 Executable (generic) (3.8) |
| .exe | | | Generic Win/DOS Executable (1.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2060:10:19 20:23:20+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 1996800 |
| InitializedDataSize: | 289280 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1e973e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.6.3.0 |
| ProductVersionNumber: | 1.6.3.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | - |
| FileVersion: | 1.6.3 |
| InternalName: | Client.exe |
| LegalCopyright: | - |
| LegalTrademarks: | - |
| OriginalFileName: | Client.exe |
| ProductName: | - |
| ProductVersion: | 1.6.3 |
| AssemblyVersion: | 1.6.3.0 |
Total processes
267
Monitored processes
25
Malicious processes
3
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1596 | C:\WINDOWS\system32\svchost.exe -k wusvcs -p -s WaaSMedicSvc | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2544 | C:\WINDOWS\system32\svchost.exe -k netsvcs -p -s UsoSvc | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2568 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | schtasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2968 | "C:\Program Files\RUXIM\PLUGscheduler.exe" | C:\Program Files\RUXIM\PLUGScheduler.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Update LifeCycle Component Scheduler Exit code: 0 Version: 10.0.19041.3623 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3720 | C:\WINDOWS\system32\svchost.exe -k netsvcs -p -s wuauserv | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4404 | C:\WINDOWS\system32\cmd.exe /c C:\Users\admin\AppData\Local\Temp\uacbypass.bat | C:\Windows\System32\cmd.exe | — | conhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4652 | "C:\WINDOWS\system32\Discord\Discord.exe" | C:\Windows\System32\Discord\Discord.exe | — | Discord.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.6.3 | |||||||||||||||
| 4804 | C:\WINDOWS\System32\svchost.exe -k wsappx -p -s ClipSVC | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4908 | %ProgramFiles%\RUXIM\RUXIMICS.EXE /onlyloadcampaigns | C:\Program Files\RUXIM\RUXIMICS.exe | PLUGScheduler.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Reusable UX Interaction Manager Exit code: 0 Version: 10.0.19041.3623 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5096 | "C:\Users\admin\AppData\Local\Temp\Discord.exe" | C:\Users\admin\AppData\Local\Temp\Discord.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 5 Version: 1.6.3 Modules
| |||||||||||||||
Total events
6 794
Read events
6 701
Write events
60
Delete events
33
Modification events
| (PID) Process: | (5096) Discord.exe | Key: | HKEY_CLASSES_ROOT\ms-settings\Shell\Open\command |
| Operation: | write | Name: | DelegateExecute |
Value: | |||
| (PID) Process: | (5228) fodhelper.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (5096) Discord.exe | Key: | HKEY_CLASSES_ROOT\ms-settings\Shell\Open\command |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (5096) Discord.exe | Key: | HKEY_CLASSES_ROOT\ms-settings\Shell\Open |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (5096) Discord.exe | Key: | HKEY_CLASSES_ROOT\ms-settings\Shell |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (5096) Discord.exe | Key: | HKEY_CLASSES_ROOT\ms-settings |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (5228) fodhelper.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (5228) fodhelper.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (5228) fodhelper.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (5096) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\Windows Live ID Token Issuer\Certificates\2C85006A1A028BCC349DF23C474724C055FDE8B6 |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
1
Suspicious files
133
Text files
2
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2968 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.049.etl | binary | |
MD5:C8834D365FAE073DEDE1F1620454CE71 | SHA256:C6DD793EEE1D5551CA507A3C5BFFECA82DD3E29C63C2C6DD218A7D4BFB37046B | |||
| 2968 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.040.etl | binary | |
MD5:09359EE89B0634478ADFF73CDA7BFB12 | SHA256:4D800AC7C55960B107C9D3E40F63130407835E69DF4F5C558C500FC0BD20D8ED | |||
| 2968 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.036.etl | binary | |
MD5:B787593A02A4E0A601164A65952D0CB9 | SHA256:3594AD496D8E1771BCC3E8B6F68B4C2B4190A9A331FB43F068A7DF4E1894E2CF | |||
| 2968 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.045.etl | binary | |
MD5:A7A21FBC9D00F33F186B34A50E170C13 | SHA256:64CAC91E46D4FC832958232A658431CBF9D8D9F265653ACA2BEB32428D4688EC | |||
| 2968 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.047.etl | binary | |
MD5:A23907B6FDD47DCABFDFD7CF2FCD7671 | SHA256:0C9C33FE9E984A2E5A70EBA51F36B9929A86199E424AF2F8080E1267B87DC970 | |||
| 2968 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.046.etl | binary | |
MD5:FED961067F664B5381B65A534B7AB728 | SHA256:652F31A8284AE812D1D9D24192BC800976BF74C240591C6AC443A28C4709FB7C | |||
| 2968 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.038.etl | binary | |
MD5:0DE8B8CBE71A7CD60D67AFE279E1ACB9 | SHA256:D17A442ABEB021BFA77E5EDAB3D7F3C6FFEA9C33B8D04409D149B518C5FDB57C | |||
| 2968 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.041.etl | binary | |
MD5:C1F87CF12DD702D2185E703BA004D216 | SHA256:9D993487866C9538DC19F281A6346E1796E7478C7C164D61437AF6E698C66125 | |||
| 2968 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.048.etl | binary | |
MD5:5EA68411BF8E9EAF4621BAF73F61449E | SHA256:9D4CA5A1D871F819C139A498BB910A63576C2FE6367853544F8D172D8B6EBFF7 | |||
| 2968 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.044.etl | binary | |
MD5:89BD161BF7B46C9078937CF832786737 | SHA256:2B83DF5532E9F54ED301C8F82E2CDD489799C8D5222A2D44C97DCB151A96FAA9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
32
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3860 | SearchApp.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5176 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5176 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.19.11.120:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
— | — | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
3176 | RUXIMICS.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4164 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.251:5353 | — | — | — | unknown |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
2952 | OfficeClickToRun.exe | 52.109.32.97:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
th.bing.com |
| whitelisted |