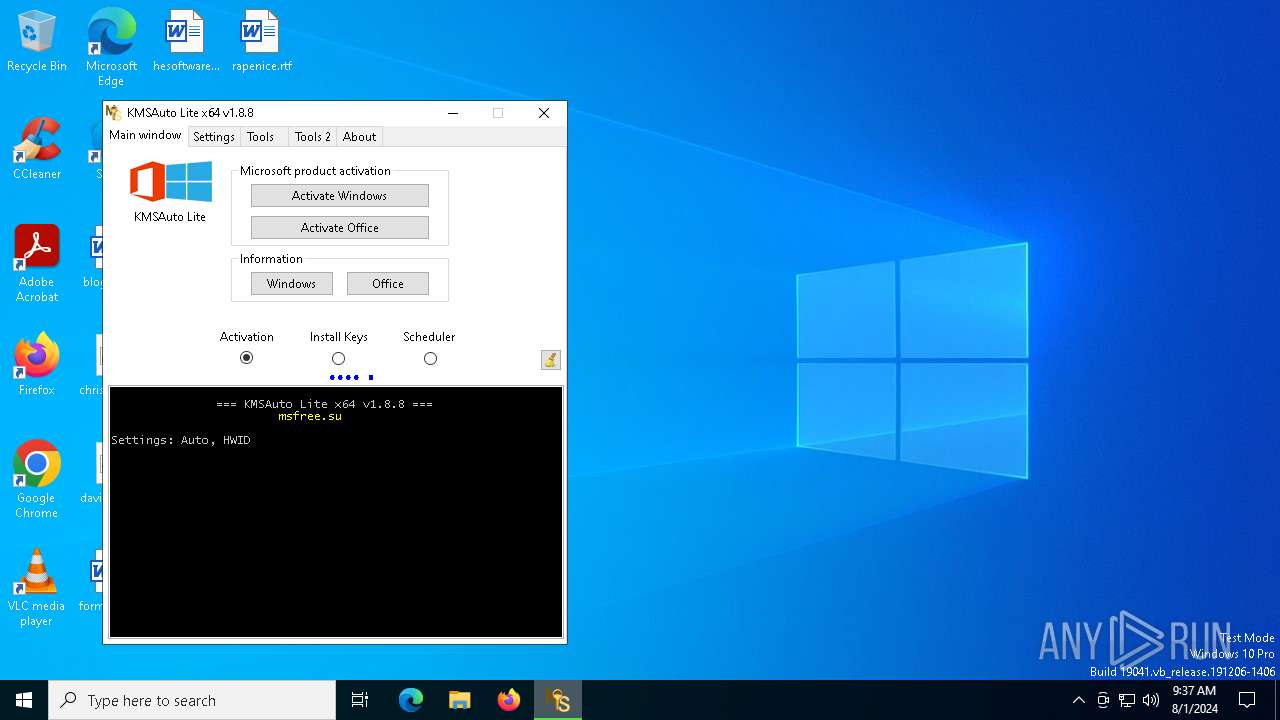
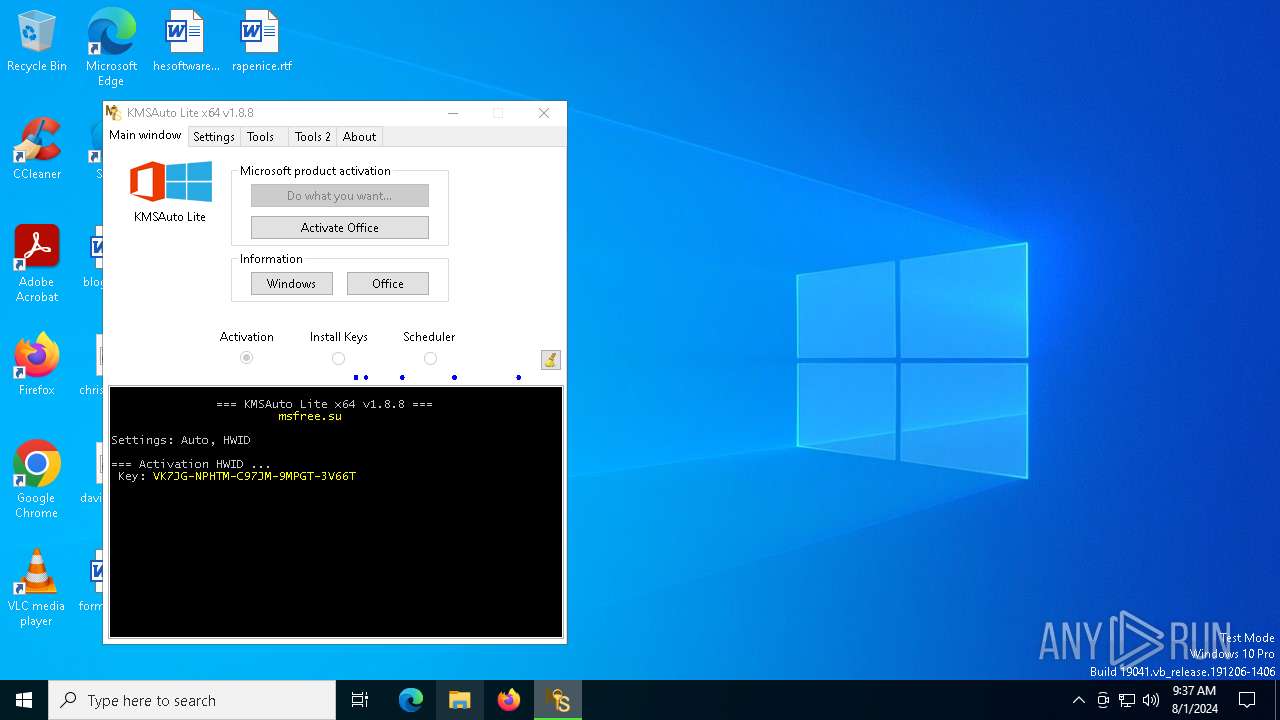
| File name: | KMSAuto.exe |
| Full analysis: | https://app.any.run/tasks/c0499aec-3b39-4cb2-9106-5656d584ef6e |
| Verdict: | Malicious activity |
| Analysis date: | August 01, 2024, 09:36:57 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows |
| MD5: | 0FCE66D54787A891A1CB5F06C09C5065 |
| SHA1: | 2AF683265C36B79F52C4B0828B9B8EE891726A6E |
| SHA256: | A11BFCBF566428E787E685FC1ABF67474777BD4160764AC4F34096E079B8B84D |
| SSDEEP: | 98304:HyrMhhfiev18iJKU6bqB1XAB2AUfLknlhaEs/Laln7Y61HR02TlpSpgRbgawNVDB:H9N9MHPXF |
MALICIOUS
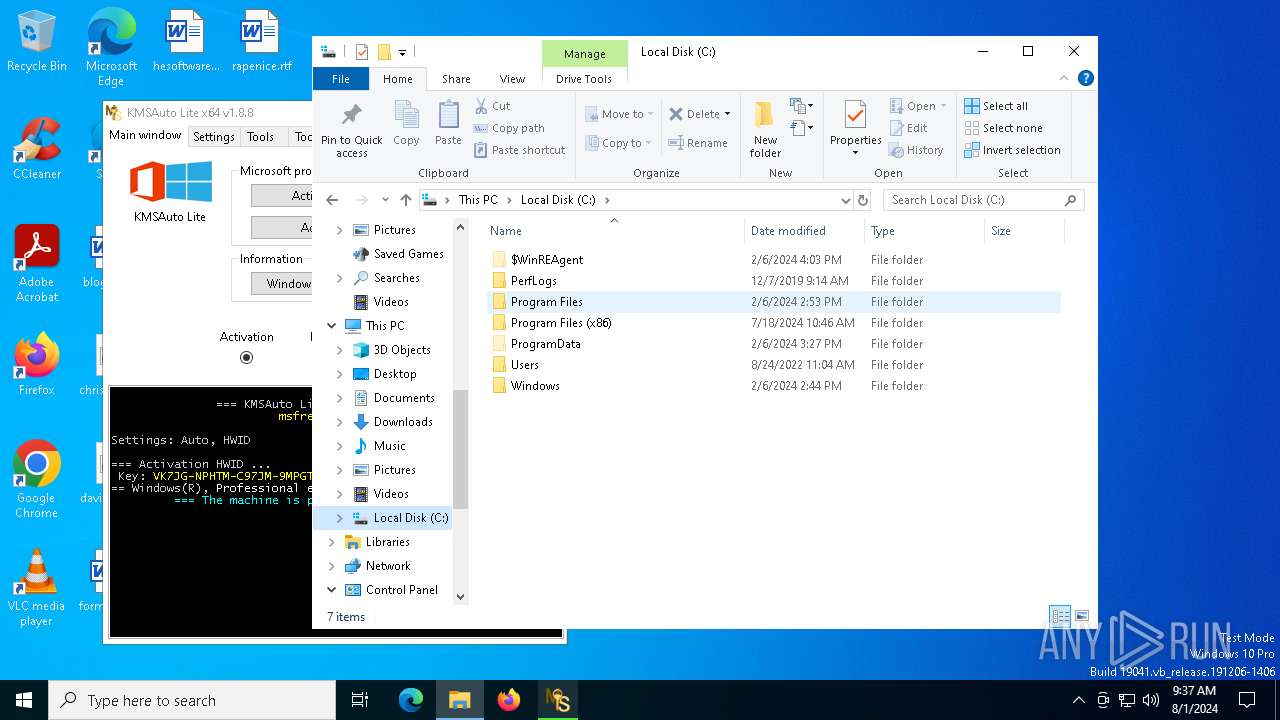
Drops the executable file immediately after the start
- KMSAuto.exe (PID: 6908)
SUSPICIOUS
The process executes VB scripts
- cmd.exe (PID: 6156)
- cmd.exe (PID: 7124)
- cmd.exe (PID: 6648)
Starts CMD.EXE for commands execution
- KMSAuto.exe (PID: 6908)
Uses WMIC.EXE
- KMSAuto.exe (PID: 6908)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- cscript.exe (PID: 6200)
- cscript.exe (PID: 6520)
- cscript.exe (PID: 6572)
Gets full path of the running script (SCRIPT)
- cscript.exe (PID: 6200)
- cscript.exe (PID: 6520)
- cscript.exe (PID: 6572)
Starts SC.EXE for service management
- KMSAuto.exe (PID: 6908)
INFO
Reads product name
- KMSAuto.exe (PID: 6908)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 3720)
- cscript.exe (PID: 6200)
- cscript.exe (PID: 6520)
- cscript.exe (PID: 6572)
Reads Environment values
- KMSAuto.exe (PID: 6908)
Create files in a temporary directory
- KMSAuto.exe (PID: 6908)
Reads the computer name
- KMSAuto.exe (PID: 6908)
Checks supported languages
- KMSAuto.exe (PID: 6908)
UPX packer has been detected
- KMSAuto.exe (PID: 6908)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (43.6) |
|---|---|---|
| .exe | | | UPX compressed Win32 Executable (42.8) |
| .exe | | | Win32 Executable (generic) (7.1) |
| .exe | | | Generic Win/DOS Executable (3.1) |
| .exe | | | DOS Executable Generic (3.1) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:03:01 06:20:29+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 2.5 |
| CodeSize: | 1407488 |
| InitializedDataSize: | 5230080 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1000 |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.8.8.0 |
| ProductVersionNumber: | 1.8.8.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
Total processes
154
Monitored processes
24
Malicious processes
1
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1020 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3720 | "wmic.exe" path Win32_NetworkAdapter get ServiceName /value /FORMAT:List | C:\Windows\System32\wbem\WMIC.exe | — | KMSAuto.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6156 | "C:\WINDOWS\System32\cmd.exe" /c cscript //nologo "C:\Users\admin\AppData\Local\Temp\slmgr.vbs" /ipk VK7JG-NPHTM-C97JM-9MPGT-3V66T | C:\Windows\System32\cmd.exe | — | KMSAuto.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6200 | cscript //nologo "C:\Users\admin\AppData\Local\Temp\slmgr.vbs" /ipk VK7JG-NPHTM-C97JM-9MPGT-3V66T | C:\Windows\System32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 6416 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | WMIC.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6452 | "C:\WINDOWS\System32\reg.exe" query "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender" /v DisableAntiSpyware | C:\Windows\System32\reg.exe | — | KMSAuto.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6460 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | reg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6472 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6496 | "C:\WINDOWS\System32\sc.exe" query SecurityHealthService | C:\Windows\System32\sc.exe | — | KMSAuto.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6508 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | sc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
2 960
Read events
2 957
Write events
3
Delete events
0
Modification events
| (PID) Process: | (6908) KMSAuto.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Script Host\Settings |
| Operation: | write | Name: | Enabled |
Value: 1 | |||
| (PID) Process: | (6908) KMSAuto.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\MediaResources\DirectSound\Speaker Configuration |
| Operation: | write | Name: | Speaker Configuration |
Value: 4 | |||
Executable files
0
Suspicious files
0
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6908 | KMSAuto.exe | C:\Users\admin\AppData\Local\Temp\slmgr.vbs | text | |
MD5:3903BCAB32A4A853DFA54962112D4D02 | SHA256:95FC646D222D324DB46F603A7F675C329FE59A567ED27FDAED2A572A19206816 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
41
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6856 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6932 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
3812 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2120 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3260 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5336 | SearchApp.exe | 95.100.146.17:443 | www.bing.com | Akamai International B.V. | CZ | unknown |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3812 | svchost.exe | 40.126.32.136:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
3812 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |